Security Risk Analysis in IoT Systems through Factor Identification over IoT Devices
Abstract
:1. Introduction
- Identify the most relevant factors that allow the definition of the security risk level of an Internet of Things system.
- Evaluate the relationships between the factors of the Internet of Things.
- Establish a method to calculate an approximate value of the security risk level of an IoT system.
- Which factors of IoT devices should be considered to define an adequate security level for low cyber risk?
- For which factors of IoT devices should risk assessment methodologies be considered?
- Which factors of IoT devices could define a risk’s profile?
- Identify the most relevant factors that allow the definition of the security risk level of an IoT device.
- Evaluate the relationships between the factors of IoT devices and security risk.
- Establish a method to calculate an approximate value of the security risk level of an IoT system.
2. Background and Related Works
- Short assessment periods: Risk methodologies are not usually designed to be performed in short periods of time; however, the IoT ecosystem is continuously changing because of the addition of new devices.
- Limited knowledge of IoT systems: Most risk assessments are focused on traditional systems and do not include the IoT ecosystem.
- Connections to other systems: IoT devices connect to other systems or technologies such as cloud computing, big data and traditional systems. This situation expands the attack surface of IoT ecosystems.
- Not considering the asset as an attack platform: IoT devices can perform new attacks.
- wd—level of risk impact;
- nwt—network type;
- prt—protocol type;
- het—heterogeneous systems involved;
- des—level of device security;
- cia—level of impact on cia components.
- pat—weight of past attacks;
- lyr—weight IoT layer;
- scr—weight of sector of IoT;
- drf—risk factor.
- Dev—number of devices connected to the network;
- Sor—number of sensors;
- Svs—number of services and processes;
- Int—number of interfaces;
- Met—number of reports;
- Dat—number of data structures;
- Scf—number of smart contract functions;
- Prot—number of protocols or standards adopted.
- ri—level of risk;
- S—total weight of score of all components;
- Ci—subcomponents of IoT system.
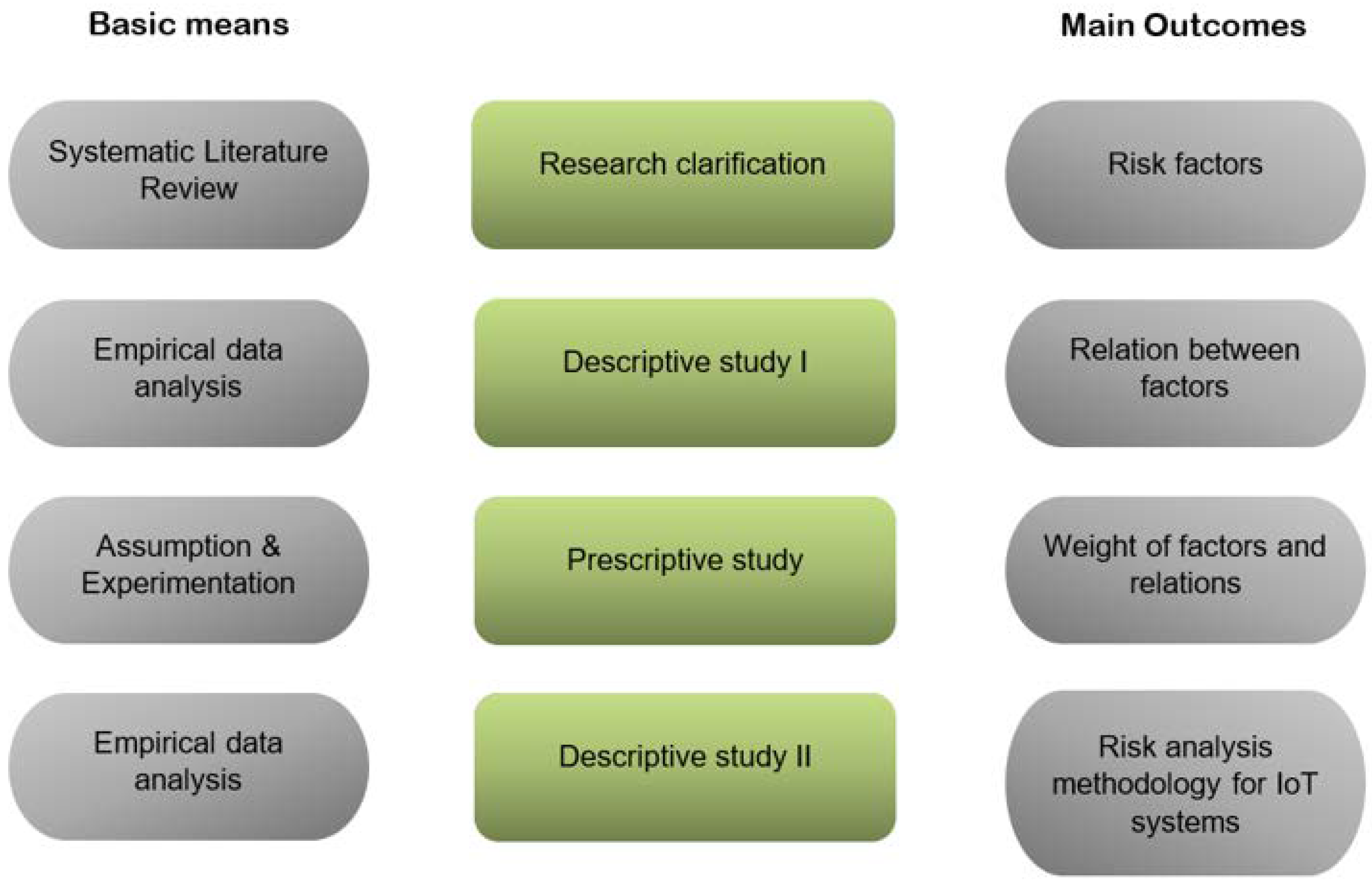
3. Materials and Methods
3.1. Research Clarification
Systematic Literature Review
3.2. Descriptive Study I
4. Results
4.1. Prescriptive Study
- Effect on economic, social, environmental domains.
- Number of IoT devices.
- Effect of shock on the market.
- Security configurations of IoT devices.
- Vulnerabilities of IoT devices.
- Effect of the relation between IT/OT/IoT systems.
- Number of IoT devices increase the probability of attack.
- Previous attacks allow new attacks.
- Short times to propagate attacks.
- Attacks from one layer to other layers of IoT system.
- IoT devices number increase attack surface.
- Attacks could be on different IoT layers.
- Attacks could be on different domains.
- Effect on CIA.
- Impact depends on type of attack.
- Vulnerabilities in IoT devices.
- IoT devices could be susceptible to attacks.
- Attacks could be on different IoT layers.
- Frequency of attacks.
- Attacks could be on different domains.
- Short time between attacks.
- Interdependency with other IT/OT/IoT systems increases the severity of attacks.
- Attacks could be on different domains.
- Interdependency with other IT/OT/IoT systems increases the severity of attacks.
- Attacks could be on different IoT layers.
- Security configurations of IoT devices.
- Frequency of attacks.
- Attack surface.
- Security configurations of IoT devices.
- Number of IoT devices.
- Interdependency with other IT/OT/IoT systems increases the severity of attacks.
4.2. Descriptive Study II
- Define the aim—in our case, the risk value.
- Define the criteria—in our case, the seven constructs.
- Weighting the criteria—the weight of constructs
- Define the sub-criteria—in our case, factors of IoT devices associated with the constructs
- Weighting the sub-criteria—the weight of factors of IoT devices.
- List of options—in our case, the features of the factors associated with each of the sub-criteria.
- Weighting of options—the weight of features of the factors of IoT devices.
- 1.
- Organization domain. The domain covers the organizational aspects of the organization (city, campus, enterprise, home) where IoT systems are implemented. The domain includes the evaluation of the security configurations according to policies or regulations related with cybersecurity in the different sectors, such as energy, traffic, health and home. The domain includes the analysis of the vulnerabilities that could affect the compliance of the policies or regulations of cybersecurity. This domain comprises three components:
- −
- Pillars: Represents the social, environmental, and economic contexts that encompass IoT systems.
- −
- Application domains: Represents the application domains that are covered by the IoT system such as agriculture, health and traffic.
- −
- Systems: Includes the IT/OT/IoT systems that support the development of the IoT system, to support the pillars and domains.
- 2.
- Dependency/interdependency domain: Include the upstream, downstream, functional, geographic or cyber dependencies that exist between IoT, OT and IT systems.
- 3.
- Attack surface domain: Include the natural (earthquakes, floods) and human (cyberattacks) hazards, or failures (configuration errors, system malfunctions) that may affect the operation of IoT systems. It includes the analysis of attacks that may occur in the layers of the IoT system.
- 4.
- Susceptibility domain: This domain includes the analysis of factors that could render IoT devices more vulnerable to attacks.
- 5.
- Severity domain: This domain includes the analysis of impact on CIA, traceability and authenticity of IoT devices.
- 6.
- Risk behaviors domain: This domain analyzes the factors that may affect the value at risk, including:
- −
- Impact: Represents the value of damage that an IoT system may suffer because of threats.
- −
- Probability: Represents the occurrence that a threat may occur.
- −
- Propagation time: Represents the time it takes for a threat to propagate and cause medium or high damage.
- −
- Propagation coverage: Represents the area of compromise (IT, IoT, OT systems) because of a threat.
- 7.
- Uncertainty domain: This domain covers the address of unknown factors that could contribute to security risk in a spatial and temporal axis.
Benchmark for IoT Security Risk Methodology
- Establishing the context
- Risk identification
- Risk analysis
- Risk evaluation
- Risk treatment
5. Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Lytras, M.D.; Visvizi, A.; Torres-Ruiz, M.; Damiani, E.; Jin, P. IEEE Access Special Section Editorial: Urban Computing and Well-Being in Smart Cities: Services, Applications, Policymaking Considerations. IEEE Access 2020, 8, 72340–72346. [Google Scholar] [CrossRef]
- Sivrikaya, F.; Ben-Sassi, N.; Dang, X.-T.; Gorur, O.C.; Kuster, C. Internet of Smart City Objects: A Distributed Framework for Service Discovery and Composition. IEEE Access 2019, 7, 14434–14454. [Google Scholar] [CrossRef]
- Andrade, R.O.; Yoo, S.G. A Comprehensive Study of the Use of LoRa in the Development of Smart Cities. Appl. Sci. 2019, 9, 4753. [Google Scholar] [CrossRef] [Green Version]
- Lopez-Vargas, A.; Fuentes, M.; Vivar, M. Challenges and Opportunities of the Internet of Things for Global Development to Achieve the United Nations Sustainable Development Goals. IEEE Access 2020, 8, 37202–37213. [Google Scholar] [CrossRef]
- Andrade, R.O.; Yoo, S.G.; Tello-Oquendo, L.; Ortiz-Garces, I. A Comprehensive Study of the IoT Cybersecurity in Smart Cities. IEEE Access 2020, 8, 228922–228941. [Google Scholar] [CrossRef]
- Xiaojian, Z.; Liandong, C.; Jie, F.; Xiangqun, W.; Qi, W. Power IoT security protection architecture based on zero trust framework. In Proceedings of the 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP), Zhuhai, China, 8–10 January 2021; pp. 166–170. [Google Scholar]
- Kulik, T.; Tran-Jørgensen, P.W.V.; Boudjadar, J.; Schultz, C. A Framework for Threat-Driven Cyber Security Verification of IoT Systems. In Proceedings of the 2018 IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Västerås, Sweden, 9–13 April 2018; pp. 89–97. [Google Scholar]
- Khatun, M.; Glass, M.; Jung, R. An Approach of Scenario-Based Threat Analysis and Risk Assessment over-the-Air updates for an Autonomous Vehicle. In Proceedings of the 2021 7th International Conference on Automation, Robotics and Applications (ICARA), Prague, Czech Republic, 4–6 February 2021; pp. 122–127. [Google Scholar]
- Kandasamy, K.; Srinivas, S.; Achuthan, K.; Rangan, V.P. IoT cyber risk: A holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process. EURASIP J. Inf. Secur. 2020, 2020, 8. [Google Scholar] [CrossRef]
- Nurse, J.; Creese, S.; De Roure, D. Security Risk Assessment in Internet of Things Systems. IT Prof. 2017, 19, 20–26. [Google Scholar] [CrossRef]
- Moreira, F.R.; Filho, D.A.D.S.; Nze, G.D.A.; Junior, R.T.D.S.; Nunes, R.R. Evaluating the Performance of NIST’s Framework Cybersecurity Controls Through a Constructivist Multicriteria Methodology. IEEE Access 2021, 9, 129605–129618. [Google Scholar] [CrossRef]
- Proenca, D.; Estevens, J.; Vieira, R.; Borbinha, J. Risk Management: A Maturity Model Based on ISO 31000. In Proceedings of the 2017 IEEE 19th Conference on Business Informatics (CBI), Thessaloniki, Greece, 24–27 July 2017; Volume 1, pp. 99–108. [Google Scholar]
- Garcia, F.Y.H.; Moreta, L.M.L. Maturity Model for the Risk Analysis of Information Assets based on Methodologies MAGERIT, OCTAVE y MEHARI; focused on Shipping Companies. In Proceedings of the 2018 7th International Conference on Software Process Improvement (CIMPS), Guadalajara, Mexico, 17–19 October 2018; pp. 29–39. [Google Scholar]
- Kieras, T.; Farooq, M.J.; Zhu, Q. RIoTS: Risk Analysis of IoT Supply Chain Threats. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 5–9 April 2020; pp. 1–6. [Google Scholar]
- Toapanta, S.M.T.; Pesantes, R.P.R.; Gallegos, L.E.M. Impact of Cybersecurity Applied to IoT in Public Organizations in Latin America. In Proceedings of the 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 154–161. [Google Scholar]
- Aydos, M.; Vural, Y.; Tekerek, A. Assessing risks and threats with layered approach to Internet of Things security. Meas. Control 2019, 52, 338–353. [Google Scholar] [CrossRef]
- Popescu, T.; Popescu, A.; Prostean, G. IoT Security Risk Management Strategy Reference Model (IoTSRM2). Future Internet 2021, 13, 148. [Google Scholar] [CrossRef]
- Levitsky, D. Assessing Risk in IoT Systems. Ph.D. Thesis, California Polytechnic State University, San Luis Obispo, CA, USA, 2018. [Google Scholar]
- Sardjono, W.; Cholik, M.I. Information Systems Risk Analysis Using Octave Allegro Method Based at Deutsche Bank. In Proceedings of the 2018 International Conference on Information Management and Technology (ICIMTech), Jakarta, Indonesia, 3–5 September 2018; pp. 38–42. [Google Scholar]
- Blessing, L.; Chakrabarti, A. DRM: A Design Research Methodology; Springer: Berlin/Heidelberg, Germany, 2009; pp. 13–42. [Google Scholar]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. PLoS Med. 2009, 6, e1000097. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Agus, Y.M.; Falih, M.D.; Satrya, G.B. On the Possibilities of Cybercrime in IoT Devices. Test Eng. Manag. 2020, 83, 8231–8238. [Google Scholar]
- Tubaishat, A.; Al Jouhi, M. Building a Security Framework for Smart Cities: A Case Study from UAE. In Proceedings of the 2020 5th International Conference on Computer and Communication Systems (ICCCS), Shanghai, China, 22–24 February 2020; pp. 477–481. [Google Scholar]
- Barreto, L.; Amaral, A. Smart Farming: Cyber Security Challenges. In Proceedings of the 2018 International Conference on Intelligent Systems (IS), Phuket, Thailand, 17–19 November 2018; pp. 870–876. [Google Scholar]
- Ghirardello, K.; Maple, C.; Ng, D.; Kearney, P. Cyber security of smart homes: Development of a reference architecture for attack surface analysis. In Living in the Internet of Things: Cybersecurity of the IoT—2018; Institution of Engineering and Technology: London, UK, 2018; pp. 1–10. [Google Scholar]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A Survey of IIoT Protocols: A Measure of Vulnerability Risk Analysis Based on CVSS. ACM Comput. Surv. 2021, 53, 1–53. [Google Scholar] [CrossRef]
- Niu, W.; Zhang, X.; Du, X.; Zhao, L.; Cao, R.; Guizani, M. A deep learning based static taint analysis approach for IoT software vulnerability location. Measurement 2020, 152, 107139. [Google Scholar] [CrossRef]
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the Internet of Things (IoT): A Security Taxonomy for IoT. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, New York, NY, USA, 1–3 August 2018; pp. 163–168. [Google Scholar] [CrossRef]
- Khor, J.H.; Sidorov, M. Weakness of Ultra-Lightweight Mutual Authentication PRotocol for IoT Devices Using RFlD Tags. In Proceedings of the 2018 Eighth International Conference on Information Science and Technology (ICIST), Cordoba, Spain, 6–30 July 2018; pp. 91–97. [Google Scholar]
- Obaidat, M.A.; Obeidat, S.; Holst, J.; Al Hayajneh, A.; Brown, J. A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures. Computers 2020, 9, 44. [Google Scholar] [CrossRef]
- Ali, S.; Khan, M.A.; Ahmad, J.; Malik, A.W.; Rehman, A.U. Detection and prevention of Black Hole Attacks in IOT & WSN. In Proceedings of the 2018 Third International Conference on Fog and Mobile Edge Computing (FMEC), Barcelona, Spain, 23–26 April 2018; pp. 217–226. [Google Scholar]
- Abdalla, P.A.; Varol, C. Testing IoT Security: The Case Study of an IP Camera. In Proceedings of the 2020 8th International Symposium on Digital Forensics and Security (ISDFS), Beirut, Lebanon, 1–2 June 2020; pp. 1–5. [Google Scholar]
- Abhijith, V.S.; Sowmiya, B.; Sudersan, S.; Thangavel, M.; Varalakshmi, P. A Review on Security Issues in Healthcare Cyber-Physical Systems. In Cyber Intelligence and Information Retrieval; Springer: Singapore, 2022. [Google Scholar]
- Martinez, J.B. Medical Device Security in the IoT Age. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 128–134. [Google Scholar]
- Luo, J.-Z.; Shan, C.; Cai, J.; Liu, Y. IoT Application-Layer Protocol Vulnerability Detection using Reverse Engineering. Symmetry 2018, 10, 561. [Google Scholar] [CrossRef] [Green Version]
- Yu, M.; Zhuge, J.; Cao, M.; Shi, Z.; Jiang, L. A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices. Futur. Internet 2020, 12, 27. [Google Scholar] [CrossRef] [Green Version]
- Patnaik, R.; Padhy, N.; Raju, K.S. A Systematic Survey on IoT Security Issues, Vulnerability and Open Challenges. In Intelligent System Design. Advances in Human Error, Reliability, Resilience, and Performance; Satapathy, S., Bhateja, V., Janakiramaiah, B., Chen, Y.W., Eds.; Springer: Singapore, 2021; Volume 1171, pp. 723–730. [Google Scholar]
- Jiang, X.; Lora, M.; Chattopadhyay, S. An Experimental Analysis of Security Vulnerabilities in Industrial IoT Devices. ACM Trans. Internet Technol. 2020, 20, 1–24. [Google Scholar] [CrossRef]
- Anand, P.; Singh, Y.; Selwal, A.; Singh, P.; Felseghi, R.; Raboaca, M. IoVT: Internet of Vulnerable Things? Threat Architecture, Attack Surfaces, and Vulnerabilities in Internet of Things and Its Applications towards Smart Grids. Energies 2020, 13, 4813. [Google Scholar] [CrossRef]
- Shakdher, A.; Agrawal, S.; Yang, B. Security Vulnerabilities in Consumer IoT Applications. In Proceedings of the 2019 IEEE 5th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing, (HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS), Washington, DC, USA, 27–29 May 2019; pp. 1–6. [Google Scholar]
- Santos, L.; Rabadao, C.; Goncalves, R. Intrusion detection systems in Internet of Things: A literature review. In Proceedings of the 13th Iberian Conference on Information Systems and Technologies (CISTI), Caceres, Spain, 13–16 June 2018. [Google Scholar] [CrossRef]
- Garcia, S.; Parmisano, A.; Erquiaga, M.J. Zenodo, IoT-23: A Labeled Dataset with Malicious and Benign IoT Network Traffic [Data set]; Stratosphere Laboratory: Praha, Czech Republic, 2020. [Google Scholar]
- Herrera, J.; Andrade, R.; Flores, M.; Cadena, S. Anomaly detection under cognitive security model. LAJC 2020, 7, 34–47. [Google Scholar]
- Ibrahim, M.; Al-Hindawi, Q.; Elhafiz, R.; Alsheikh, A.; Alquq, O. Attack Graph Implementation and Visualization for Cyber Physical Systems. Processes 2019, 8, 12. [Google Scholar] [CrossRef] [Green Version]
- Tarka, P. An overview of structural equation modeling: Its beginnings, historical development, usefulness and controversies in the social sciences. Qual. Quant. 2018, 52, 313–354. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kline, R.B. Principles and Practice of Structural Equation Modeling; Guilford Press: New York, NY, USA, 2011. [Google Scholar]
- Rahman, H.U.; Raza, M.; Afsar, P.; Alharbi, A.; Ahmad, S.; Alyami, H. Multi-Criteria Decision Making Model for Application Maintenance Offshoring Using Analytic Hierarchy Process. Appl. Sci. 2021, 11, 8550. [Google Scholar] [CrossRef]
- Patton, R.J. A benchmark study approach to fault diagnosis of industrial process control systems. In Proceedings of the IEE Seminar on Control Loop Assessment and Diagnosis, London, UK, 16 August 2005. [Google Scholar]
- Jeppsson, U.; Pons, M.-N.; Nopens, I.; Alex, J.; Copp, J.; Gernaey, K.; Rosen, C.; Steyer, J.-P.; Vanrolleghem, P. Benchmark simulation model no 2: General protocol and exploratory case studies. Water Sci. Technol. 2007, 56, 67–78. [Google Scholar] [CrossRef] [PubMed]
- Lueckmann, J.; Boelts, J.; Greenberg, D.; Gonçalves, P.; Macke, J. Benchmarking simulation-based inference. In Proceedings of the International Conference on Artificial Intelligence and Statistics, Suzhou, China, 15–17 October 2021. [Google Scholar]





















| Methodologies | Focus On | Strength | Weakness |
|---|---|---|---|
| NIST [11] | Security controls | Guidelines to execute security controls according to risk assessment. | Needs work with other standards to address compliance. |
| ISO [12] | Compliance of security controls | Analysis of information security risks according to specific criteria. | Coordination and integration to remember to update the standard. |
| MAGERIT [13] | Assets values | Assessments of critical assets, and the mitigation of threats and risks that could degrade them. | Requires time for identification of critical assets. |
| TARA [14] | Attacks | Definition of a list of attacks. | Does not quantify risk impact. |
| Label for Hypothesis | Factors |
|---|---|
| Conferences | 807 |
| Journal article | 559 |
| Series | 215 |
| Chapter | 23 |
| Book | 3 |
| Label for Hypothesis | Factors | Density |
|---|---|---|
| H1 | Vulnerabilities | 17 |
| H2 | Type of attack | 10 |
| H3 | Attack surface | 8 |
| H4 | Interdependency | 7 |
| H5 | Severity | 5 |
| H6 | Application domain | 4 |
| H7 | Scalability | 4 |
| H8 | Type of device | 3 |
| H9 | Susceptibility | 2 |
| H10 | Type of information | 1 |
| H11 | Uncertainty | 0 |
| Proposals\Factors | Kandasamy | Toapanta | Aydos | Popescus | Levitsky |
|---|---|---|---|---|---|
| Application domain | Partially Covered | Not covered | Not covered | Not covered | Not covered |
| Attack surface | Covered | Covered | Covered | Covered | Covered |
| Interdependency | Covered | Covered | Not covered | Not covered | Not covered |
| Scalability | Not covered | Not covered | Not covered | Not covered | Not covered |
| Severity | Covered | Not covered | Not covered | Not covered | Covered |
| Susceptibility | Not covered | Not covered | Not covered | Not covered | Not covered |
| Type of attack | Not covered | Not covered | Covered | Covered | Covered |
| Type of device | Covered | Not covered | Not covered | Not covered | Not covered |
| Type of information | Not covered | Not covered | Not covered | Not covered | Not covered |
| Uncertainty | Not covered | Not covered | Not covered | Not covered | Covered |
| Vulnerabilities | Not covered | Not covered | Not covered | Covered | Not covered |
| Hypothesis (Risk Factors) | Code | Research Items |
|---|---|---|
| H6. Application domain | S-A | Cyberattacks on IoT systems could affect economic, social or environmental domains. |
| S-A-P | Cyberattacks on IoT systems could be targeted at IoT solutions to health, energy, traffic and agriculture. | |
| H4. Interdependency | S-I-Sys | Cyberattacks on IoT systems could be affected by other IoT, IT and OT systems. |
| S-I-nd | The growth of the number of IoT devices could increase the probability of cyberattacks. | |
| H7. Level of scalability | S-Scl | Cyberattacks on IoT systems could generate shock on markets or risk systemic events. |
| H9. Level of susceptibility | S-Sc | Security configurations on IoT devices depend on domains or pillars where IoT devices will be used. |
| H4. Interdependency | Sc-I-Sys | Interdependency of IoT device with other IoT, IT and OT systems could increase the probability of attacks on IoT systems and cause bigger damage. |
| H4. Attack surface | Sc-As-nd | The growth in the number of IoT devices could increase organizations’ susceptibility to suffering cyberattacks because of the large attack surface. |
| H1. Vulnerabilities | Sc-V | Vulnerabilities of IoT devices could increase the probability of cyberattacks on IoT systems. |
| H9. Level of susceptibility | Sc-Ta | IoT devices are susceptible to specific types of cyberattacks. |
| H2. Types of attacks | Sc-Ta2 | Previous attack allows the execution of new attacks. |
| H2. Types of attacks | Sc-Ta-L | Attacks could be executed in different layers. |
| H8. Type of IoT device | Sc-Td | Security configurations on IoT devices could increase their susceptibility to being attacked. |
| H5. Severity | Rb-Sv-Ta | Cyberattacks could generate degradation in the operation of IoT devices. |
| H5. Severity | Rb-Sv-Sr | Cyberattacks could affect CIA on IoT systems. |
| H7. Level of scalability | Rb-Scl | Cyberattacks could be scaled from one layer of an IoT system to another one. |
| H11. Factors not known | Rb-U-f | The frequency of cyberattacks could increase their success. |
| H11. Factors not known | Rb-U-Tp | Short times of the propagation of cyberattacks could increase their damage. |
| H7. Level of scalability | Rb-Scl-L | Cyberattack could affect different layers of IoT systems and increase the surface of damage. |
| Research Items | Verifiable Means | Relation |
|---|---|---|
| Cyberattacks on IoT systems could affect economic, social or environmental domains. | Experiment 1 Experiment 2 | S-A |
| Cyberattacks on IoT systems could be targeted at IoT solutions to health, energy, traffic, agriculture. | Experiment 1 Experiment 2 | S-A-P |
| Cyberattacks on IoT systems could be affected by other IoT, IT and OT systems. | Experiment 1 | S-I-Sys |
| The growth of the number of IoT devices could increase the probability of cyberattacks. | Experiment 1 | S-I-nd |
| Cyberattacks on IoT systems could generate shock in markets or risk systemic events. | Not verifiable | S-Scl |
| Security configurations on IoT devices depends on domains or pillars where IoT devices will be used. | Experiment 1 Experiment 3 | S-Sc |
| Interdependency of IoT device with other IoT, IT and OT systems could increase the probability of an attack on IoT systems and cause bigger damage. | Experiment 3 Experiment 4 Experiment 5 | Sc-I-Sys |
| The growth of the number of IoT devices could increase organizations’ susceptibility to suffering cyberattacks because of the large attack surface. | Not verifiable | Sc-As-nd |
| Vulnerabilities in IoT devices could increase the probability of cyberattacks on IoT systems. | Experiment 4 Experiment 5 | Sc-V |
| IoT devices are susceptible to specific type of cyberattacks. | Experiment 1 Experiment 3 | Sc-Ta |
| Previous attack allows the execution of new attacks. | Experiment 3 | Sc-Ta2 |
| Attacks could be executed in different layers. | Experiment 4 | Sc-Ta-L |
| Security configurations on IoT device could increase susceptibility to being attacked. | Experiment 4 Experiment 5 | Sc-Td |
| Cyberattacks could generate degradation in the operation of IoT devices. | No verificable | Rb-Sv-Ta |
| Cyberattacks could affect CIA on IoT systems. | Experiment 3 Experiment 4 Experiment 5 | Rb-Sv-Sr |
| Cyberattacks could be scaled from one layer of an IoT system to another one. | Experiment 4 | Rb-Scl |
| The frequency of cyberattacks could increase their success. | No verificable | Rb-U-f |
| Short times of the propagation of cyberattacks could increase their damage. | Not verifiable | Rb-U-Tp |
| Cyberattacks could affect different layers of IoT systems and increase the surface of damage. | Experiment 1 Experiment 2 Experiment 3 | Rb-Scl-L |
| Total Variance Explained | |||||
|---|---|---|---|---|---|
| Component | Initial Eigenvalues | Extraction Sums of Squared Loadings | |||
| Total | % of Variance | Cumulative % | Total | % of Variance | |
| 1 | 14,822 | 54,895 | 54,895 | 14,822 | 54,895 |
| 2 | 3344 | 12,385 | 67,280 | 3344 | 12,385 |
| 3 | 3218 | 11,918 | 79,197 | 3218 | 11,918 |
| 4 | 1938 | 7178 | 86,375 | 1938 | 7178 |
| 5 | 1671 | 6190 | 92,565 | 1671 | 6190 |
| 6 | 1219 | 4516 | 97,081 | 1219 | 4516 |
| 7 | 0.788 | 2919 | 100,000 | 0.788 | 2919 |
| 8 | 1321 × 10−15 | 4892 × 10−15 | 100,000 | 1321 × 10−15 | 4892 × 10−15 |
| 9 | 1228 × 10−15 | 4547 × 10−15 | 100,000 | 1228 × 10−15 | 4547 × 10−15 |
| Components | Organization (54.9%) | ||||
| Domains | Pillars | Systems | Security configurations | Vulnerabilities | |
| Weight | 30% | 20% | 20% | 10% | 20% |
| Components | Scalability (12.39%) | ||||
| Impact/degradation | P. Ocurrence | P.time | P.coverage | Previous Attacks | |
| Weight | 40% | 30% | 10% | 10% | 10% |
| Components | Attack Surface (11.92%) | Susceptibility (6.19%) | |||
| Number IoT dev. | Threats | Number IoT layers | No extra components | ||
| Weight | 40% | 40% | 40% | 100% | |
| Components | Severity (7.18%) | ||||
| Confidenciality | Integrity | Avalability | Trazability | Authenticity | |
| Weight | 40% | 20% | 20% | 10% | 10% |
| Components | Interdependency (4.52%) | ||||
| Upstream | Downstream | Functional | Geographical | Cybernetic | |
| Weight | 20% | 20% | 20% | 20% | 20% |
| Components | Uncertainity (2.9%) | ||||
| No extra components | |||||
| Weight | 100% | ||||
| Domain (30 %) | Economic | Social | Environmental | ||
| Weight | 60% | 25% | 15% | ||
| IoT System | Severity | Susceptibility | Risk Behaviours | Risk Total (/10) |
|---|---|---|---|---|
| 0.6 | 0.3 | 0.1 | ||
| IoTX | 1.44 | 2.10 | 0.49 | 4.03 |
| IoTY | 0.70 | 0.77 | 0.21 | 1.68 |
| IoTZ | 2.29 | 1.01 | 0.31 | 3.61 |
| Performance Indices | ||||
|---|---|---|---|---|
| Label for Hypothesis | Factors | Constructs | Input Variables | Output Variables |
| H1 | Vulnerabilities | Organization, Attack Surface, Severity | (a) Values of vulnerabilities | |
| H2 | Type of attack | Organization, Risk Behavior, Severity, Uncertainty | (a) Value of attack per layer | |
| H3 | Attack surface | Organization, Risk Behavior, Attack Surface, Interdependency | (a) Number of IoT devices (b) Security configurations (c) Values of vulnerabilities | |
| H4 | Interdependency | Organization, Risk Behavior, Attack Surface, Susceptibility, Interdependency, Uncertainty | (a) Values of interdependency | |
| H5 | Severity | Severity | (a) Values of degradation of CIA | |
| H6 | Application domain | Organization, Attack surface, Susceptibility, Interdependency | (a) Value of economic impact (b) Value of economic impact (c) Value of economic impact | |
| H7 | Scalability | Risk behavior | (a) Number of IoT devices, (b) Historical attack, (c) Time between attacks | |
| H8 | Type of device | Severity, Interdependency, Uncertainty | (a) Security level of CIA | |
| H9 | Susceptibility | Organization, Susceptibility | (a) Frequency of attack (b) Time between attacks (c) Security levels | |
| H 10 | Type information | Organization | (a) Security configurations | |
| H 11 | Uncertainty | Attack Surface, Susceptibility, Interdependency, Uncertainty | (a) Number of IoT devices (b) Security configurations (c) Values of interdependency | |
| IoT Factors (Input Variables) | Impact (Output Variables) | |||||
|---|---|---|---|---|---|---|
| Vulnerabilities | Susceptibility | Attack Surface | Interdependency | Economic | Social | Environmental |
| 70% | 50% | 60% | 60% | 70.77% | 63.98% | 55.90% |
| 100% | 50% | 50% | 60% | 73.12% | 66.04% | 57.66% |
| 100% | 100% | 50% | 60% | 76.56% | 69.08% | 60.26% |
| 100% | 100% | 100% | 60% | 77.91% | 70.25% | 61.26% |
| 100% | 100% | 100% | 100% | 86.05% | 77.15% | 67.28% |
| 70% | 100% | 50% | 60% | 73.40% | 66.30% | 57.88% |
| 70% | 50% | 50% | 100% | 84.86% | 76.22% | 66.43% |
| Methodology | Computer Security Risk Analysis (MAGERIT) | IoT Risk |
|---|---|---|
| Focus on | Assets | Context (social, environmental, economic) |
| Priority | Top of critical assets | Top of group of critical assets |
| Dependency of | Assets | Assets/threats |
| Type Assets | Individual critical assets | Grouped critical assets (based on classes or security levels) |
| Security factors on the assets | Confidentiality, Integrity, Availability, Traceability and Authenticity | Confidentiality, integrity and availability (Based on classes) |
| Vulnerabilities | Overall approach | Based on IoT layers (application, communication, and device) |
| Attack surface | Not included in the methodology. | Based on relationships among systems. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Andrade, R.O.; Yoo, S.G.; Ortiz-Garces, I.; Barriga, J. Security Risk Analysis in IoT Systems through Factor Identification over IoT Devices. Appl. Sci. 2022, 12, 2976. https://doi.org/10.3390/app12062976
Andrade RO, Yoo SG, Ortiz-Garces I, Barriga J. Security Risk Analysis in IoT Systems through Factor Identification over IoT Devices. Applied Sciences. 2022; 12(6):2976. https://doi.org/10.3390/app12062976
Chicago/Turabian StyleAndrade, Roberto Omar, Sang Guun Yoo, Iván Ortiz-Garces, and Jhonattan Barriga. 2022. "Security Risk Analysis in IoT Systems through Factor Identification over IoT Devices" Applied Sciences 12, no. 6: 2976. https://doi.org/10.3390/app12062976
APA StyleAndrade, R. O., Yoo, S. G., Ortiz-Garces, I., & Barriga, J. (2022). Security Risk Analysis in IoT Systems through Factor Identification over IoT Devices. Applied Sciences, 12(6), 2976. https://doi.org/10.3390/app12062976







