1. Introduction
In recent years, intelligent manufacturing, with digitalization, informatization, and networking as the main features, has become the main direction for the future development of the manufacturing industry. With the impetus of the digital economy, AI, industrial internet, digital twins, and other emerging technologies, intelligent manufacturing has gradually gained the attention of governments and has become important to them. As a product with high integration of the IoT, big data, blockchain, AI and advanced manufacturing technology, intelligent manufacturing helps to realize the intelligence of the whole process, from product design to production, and promotes the continuous upgrading of the manufacturing industry [
1,
2,
3].
The industrial IoT is an important part of intelligent manufacturing, which gives the IoT network connection the capability to be used with mechanical equipment, whereby enterprises can collect data from the whole generation process for real-time analysis and processing, and for process visualization. The collection, transmission, and storage of large amounts of IoT data enables intelligent manufacturing capabilities, but also poses security risks. The IoT is not a simple superposition of sensors, communication interfaces, and communication devices, but a variety of instruments and devices in different networks and fields that are interconnected and collaborated. As the scale of the IoT continues to grow, the probability of collaboration scenarios between devices is increasing [
4], especially in the process of digital twin technology. A large number of applications, the entire intelligent manufacturing model, integrate a large number of historical and real-time process data from physical systems. Digital agency needs to monitor the production system or the state of the process, predict the performance of the system, and generate the system behavior or control action; data exchange and data access control put forward higher requirements [
5]. Blockchain-based and green Internet of Things’ UAV applications [
6], as well as blockchain-based face monitoring by drones (used during COVID-19), also face a lot of data access control requirements [
7]. In order to ensure security, collaboration between different types of devices should be performed with appropriate access control, according to the security and privacy protection characteristics of the devices.
As a basic mechanism for achieving security in information systems, access control (AC) determines the communication rights between authorized subjects and objects, according to specific security models and policies [
8]. An effective access control mechanism can meet the information security requirements, such as system confidentiality, integrity, and availability. For the scenario of the collaboration of IoT devices in intelligent manufacturing, this paper proposes an AC method applicable to the IoT environment. The access control policy is described in a fine-grained manner, using attributes that support complex logic operations in the policy and enhance the expressiveness of the model; the distributed access control determination decision, using smart contracts deployed on the blockchain, improves the decision-making efficiency of the model AC and enhances the IoT data security. Lightweight nodes in the blockchain are introduced to adapt to the complex and diverse heterogeneous devices in the IoT, to enhance the scalability of the system [
9].
This article analyzes the deficiencies of access control technology research in the current intelligent manufacturing Internet of Things environment. We propose a distributed, dynamic, fine-grained data access control method, applicable to IoT device terminals in the intelligent manufacturing process. The model has the following characteristics: (1) After registering with the attribute authorization authority, the IoT device will apply to the attribute authorization authority for access control attribute value pairs. The attribute authorization authority will formulate appropriate access control policies, according to the specific functions of the IoT device, in accordance with the attribute-based access control method and will assign them to the IoT device. These policies will be submitted to the blockchain for consensus and saved to the blockchain after the consensus is passed. (2) All access control determination is conducted by the smart contract (chaincode) deployed on the Fabric, which ensures that the access control determination function is distributed and can avoid the single point issue of the access control determination node.
This manuscript is organized as follows:
Section 2 introduces the work related to access control and blockchain technology in the Internet of Things. Next, in
Section 3, we focus on the access control model, integrating blockchain and big data cloud platforms.
Section 4 describes the distributed access control scheme of the Internet of Things, based on blockchain, which mainly involves system initialization, device registration, blockchain address generation, attribute value pair application, access control policy generation, access control policy cancellation, and other processes.
Section 5 describes the access control process management, taking Alice and Bob as examples to describe the access control process between the Internet of Things’ terminals.
Section 6 analyzes the security and performance of the access control method described in this article. Finally,
Section 7 summarizes the research content of this paper.
2. Related Technologies
2.1. Access Control in the IoT
With the continuous development of IoT technologies and applications, the IoT has evolved from an industrial network, based on RFID technology in the early days, to a smart planet, where everything can be connected; access control in the IoT environment has also evolved. Due to the specificity of the IoT, in addition to security and privacy requirements, access control should also consider scalability, flexibility, and lightweight nodes to fit in the IoT environment. Access control methods applied in the IoT include role-based AC (RBAC), attribute-based AC (ABAC), and rights-based AC, etc. [
10]. RBAC maps users to roles through which they can enjoy permission. The model defines the different roles, their inheritance relationships, the connections between roles, and the restrictions to which the roles are subject, and regulates the user’s behavior [
11]. ABAC is a dynamic access control model that uses attributes as the key element of access control. Because attributes are inherent to the subject and object, ABAC can mine independent and complete sets of attributes without manual input from the administrator, by means of the attribute discovery mechanism, and can quickly mine (attributes and permissions) relationships by means of an automated attribute–permission association discovery mechanism [
12,
13]. The framework of attribute-based access control is shown in
Figure 1.
2.2. Blockchain and Internet of Things Technology
Blockchain was first used in the underlying bookkeeping system of Bitcoin [
14]. Blockchain includes not only the structure of chained data blocks, but also the product of a combination of P2P network technology, consensus mechanisms, cryptography technology, and a series of other technologies [
15]. Blockchain is a chained block data structure with traceable functions established in a distributed network environment, based on trustworthy and transparent rules. The typical characteristics of blockchain include the following six aspects: decentralization, openness, autonomy, distrust, immutability, and anonymity. The application capabilities provided by blockchain include providing infrastructure, such as computing, storage, network and platform resources, through distributed networks or peer-to-peer networks; managing, querying and analyzing data in distributed networks or peer-to-peer networks; and relying on blockchain networks to provide application services, such as digital asset transactions and security certifications [
16].
The unique technical characteristics of blockchain enable it to solve the problems of massive data processing, privacy security and trust management, faced in the construction and development of the Internet of Things, thereby promoting the evolution of the Internet of Things to a distributed and intelligent advanced form, such as the following:
- (1)
In view of the network security architecture, authentication, design authorization, privacy protection and other issues related to the Internet of Things, the security and privacy of the Internet of Things can be ensured in regard to the aspects of storage and information transmission, through authentication and authorization mechanisms.
- (2)
In view of problems such as the difficulty in ensuring the authenticity of the information obtained by the Internet of Things, the authenticity of the information can be ensured through blockchain traceability.
- (3)
In view of the problems concerning the multi-network integration of the Internet of Things and intelligent network management, different protocols and devices can be connected through the blockchain, and the ability to manage, query, and analyze data in peer-to-peer networks can be provided.
- (4)
In view of the fact that the Internet of Things has not yet formed an effective mechanism to open up all links, it can effectively open up all links by providing computing, storage, network, and platform resources through peer-to-peer networks.
3. Attribute-Based AC Method Incorporating Blockchain and CSP
Based on the attribute-based AC method, this paper proposes a distributed AC method based on blockchain and Internet of Things technology, as shown in
Figure 2.
In this model, the following entities are mainly included: an attribute authorization authority (AAA), an IBC (identity-based cryptograph) [
17] server, a cloud service provider (CSP), an IoT gateway, an IoT device, and a federated blockchain network.
The attribute authorization authority (AAA): The AAA is an attribute authorizer of IoT devices. It authorizes i attribute value pairs for each sensing layer terminal, based on its role, identity, etc. Attribute value pairs (prop_ni, prop_vi) constitute the set S of attribute value pairs of the device, and the set S is submitted to the blockchain for consensus in the form of transactions, which will be permanently stored on the federated chain after the consensus is passed. The whole system can have multiple attribute authorization authorities.
The IBC server: Every IoT device must complete registration with the IBC server in advance, before joining the system. After successful registration, the device will receive a pair of IBC-based public–private key pairs.
Cloud service provider (CSP): The CSP mainly provides cloud computing and storage services for IoT devices; the IoT data are usually stored with encryption.
The IoT gateway: With strong computing and storage capabilities, it is directly connected to the IoT sensing layer device, and is the intermediary between the IoT terminal and the blockchain and cloud service providers. This largely solves the problem of the limited computing and storage resources in the IoT terminal.
IoT devices: IoT perception layer devices that collect, process, and transmit various device-generated data.
Federated blockchain network: this gives consensus, confirms and stores the transactions submitted to the Fabric network, and also provides a smart contract function to realize the access control function.
4. Blockchain-Based Distributed AC Model for the IoT
The blockchain technology-based distributed AC model for the IoT has the following main steps:
4.1. System Initialization
Generate (
1,
2,
e) with
as input parameters, where
1 and
2 are the order groups of
e and
q, respectively, and satisfy
1 ×
2→
2; randomly select the master key
, two secure hash functions defined by the system [
17,
18,
19].
In addition, the master private key SKm is stored in the IBC server, and the public key generation is executed by the user generation to generate the public key Pubm.
4.2. Equipment Registration
When an IoT device needs to join the system, it must apply for the private identity key from the attribute authority it belongs to. The IoT device needs to provide the identity ID to the IBC server it belongs to, and this ID can be used as the device’s public key. The IBC server will use its master private key and the identity ID of the IoT device to generate the identity private key and send the identity private key to the IoT device in a secure way.
4.3. Blockchain Address Generation
Each IoT device in the system is allowed to request an attribute value pair (
prop_
ni,
prop_
vi) from the AAA using a self-generated address and the identity flag ID of the device. The IoT device first randomly selects
as the key
SKi of the device, then the public key corresponding to this key
PKi = kG. To obtain the blockchain address corresponding to this public key, the IoT device can hash the
PKi‖
IDdev‖timestamp, and finally use the
Base58Check function to encode the blockchain address obtained, as follows:
This address is used to request an attribute value pair from an attribute authorization authority for an IoT device.
4.4. Attribute Value Pair Application
When an IoT device needs to request an attribute value pair (
prop_
ni,
prop_
vi), the corresponding attribute authorization authority must verify whether the IoT device can have the attribute value pair on a case-by-case basis. If this verification passes, this attribute authority immediately generates an authorization transaction for the attribute value pair, concatenates the transaction with the current timestamp, performs a hash operation to obtain a hash value, and then signs the hash value, as follows:
Finally, this attribute authorization authority packages the signature value, transaction, and current timestamp together, and submits it to the federated blockchain.
4.5. Access Control Policy Generation
When an IoT device is registered to an attribute authorization authority, a reasonable access control policy file must be developed by the attribute authorization authority, according to the specific situation, and then the transaction and the current timestamp are concatenated and hashed, followed by signing the hash value, as follows:
Finally, the AAA will pack the signature value, transaction, and current timestamp together into Fabric.
4.6. Access Control Revocation
Since the IoT system is dynamic and evolving, the access control policies for the IoT terminal may fail, due to the change in business requirements, then it is necessary to revoke the AC policy of the IoT device by connecting the transaction with the current timestamp for the operation and hashing it, followed by signing the hash value, as follows:
Finally, the attribute authorizer will package the signature value, transaction, and current timestamp together, and submit it to the federated blockchain.
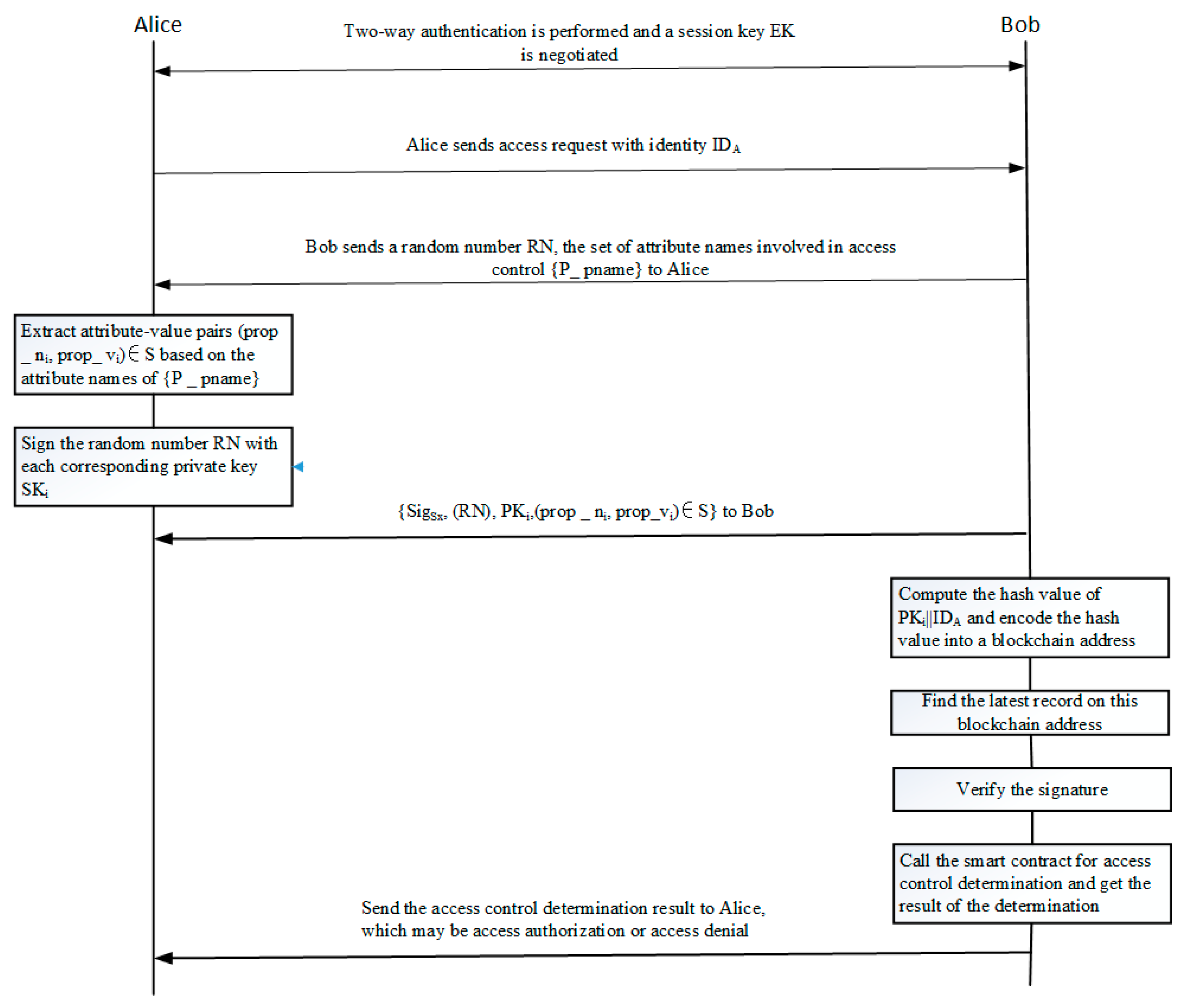
5. Access Control Process Management
Suppose there are two IoT devices, one of which is Bob, the data resource owner, and the other is Alice, the data resource requester. When Alice needs to request Bob’s data resources, Bob must implement access controls on the data resources owned by him, to block unauthorized IoT devices from illegally accessing the resources of his device, etc. In general, Alice can only gain access to Bob’s data resources if the set of attribute value pairs owned by Alice and the current environment attributes, etc., can meet the access control policy requirements set by Bob. The execution flow of the access control protocol between these two IoT devices is shown in
Figure 3.
(1) Alice first sends the request message for data resource access to Bob, using the identity information IDA, and then Alice and Bob obtain a session key Km, using standard identity-based authentication and key negotiation protocols, which is used for identification and encryption when data are exchanged between the data requester and the data owner.
(2) Bob generates a random number (RN ∈ Zr) and sends it to Alice by merging its own set of access control policy attribute names {P_pname}, where {P_pname} defines the set of attribute names to be used to access the data resources of the device.
(3) Alice looks up the subset of attribute value pairs (prop_ni, prop_vi) ∈ S from the set of attributes owned by the IoT device, as maintained by the attribute names in {P_pname}, where the information of the attribute value pairs in this subset is authorized by the attribute authorization authority to the blockchain address that Alice submitted during the access control request. Alice signs the random number (RN) using the private key corresponding to each blockchain address in turn, and then sends the random number (RN), together with its own signature and its corresponding public key pair {SigSK (RN), PKi, (prop_ni, prop_vi) ∈ S}, corresponding to each attribute value pair in the attribute value pair set S, to Bob.
(4) Bob first hashes the
PKi||
IDA submitted by Alice, and, by running the
Base58Check function to encode it, Bob then obtains the blockchain address corresponding to this hash value. Then, Bob looks up the Fabric ledger to obtain the latest data corresponding to the blockchain address, and, if the blockchain address has, indeed, been distributed with attribute value pairs (
prop_
ni,
prop_
vi) by the Authorization Authority, Bob immediately uses this corresponding public key
PKi submitted by Alice to verify the validity and legitimacy of the signature value,
SigSK (
R), as follows:
(5) If all of the above holds, it shows that Alice is, indeed, the owner of the blockchain address, and the attribute value pairs (prop_ni, prop_vi) corresponding to the blockchain address are declared in advance by the attribute authority. Bob takes the verified set of attribute value pairs (S, PKB) and his own identity (IDB) sent by Alice and invokes the access control determination smart contract on the block to make the determination.
6. Security and Performance Analysis
6.1. Confidentiality
The encrypted transmission of data is achieved with a symmetric cryptographic algorithm [
20]. The data resource owner and the data requester use an identification password for authentication and implement the necessary key negotiation to generate a session key;
Km,
Km is a symmetric key that is used to encrypt the transmission of the interaction information between the two parties during the subsequent interaction.
6.2. Performance Analysis Experiment
In order to verify the performance and effectiveness of the proposed solution, this paper analyzed and evaluated the computing and storage performance of the access control scheme. These experiments were conducted under Ubuntu OS. Hyperledger Fabric version 2.0 was used to build the federated chain, and the smart contract algorithm for access control was programmed in Go/Java language. The start operations for the orderer node and peer node are shown in
Figure 4.
Since most of the devices in IoT systems have extremely limited storage resources, the size of the data storage space and the data access performance required for this scenario are important factors to consider. In the scheme proposed in this paper, the IoT devices must store at least four additional types of data locally, including global parameters of the whole system, session keys between the IoT devices, salt values used to generate symmetric keys, and access control policies.
(1) Global parameters of the whole system: The blockchain-based IoT access control system has corresponding global parameters, through which all entities within the system can share data, which contain security parameters, elliptic curves, secure hash functions, authorization authorities for attributes that need to be interacted with, and public keys of the IoT devices. The size of the global parameters is determined after the initialization of the system, and this part of the storage overhead is measured in bytes, which is certainly within the acceptable range.
(2) Session key between IoT devices: To improve the performance of access control across the system, while still ensuring security, a suitable expiration period can be set for the session key of both communication parties. The number of this session key is determined by the number of individual IoT devices and other devices that need to communicate, and, in general, the session key is used as a symmetric key, if the state-secure SM9 encryption algorithm [
21] is used. The storage overhead of this part is very small.
(3) Access control policy: A single device keeps an access control policy file, which can be defined based on the Casbin [
22] model, and supports common arithmetic, relational and logical operators when defining the matching rules of the policy, making the policy supportive of fine-grained description and powerful expression.
The storage overhead of the file is related to the number of access control policy attributes. In practice, the number of attributes designed for the access control policy of a single device does not exceed 15, and, in this case, only about 200 bytes of space are required, which is obviously an acceptable storage overhead.
The results are shown in
Figure 5, which compares the storage overhead with two similar recent solutions.
From
Figure 5, we can observe that the storage performance of the access control methods mentioned in this paper is better than that of schemes such as those in [
23]. However, because the scheme of this paper uses attribute value pairs, that is, conditions to describe the ACP policy, while schemes such as those in [
24] use attributes to describe the ACP policy, the scheme of this paper is worse than schemes such as those in [
24], in terms of the storage overhead, but it is well within the acceptable range.
Compared with two similar schemes, in terms of time cost, the comparison results are shown in
Table 1 below.
In terms of the time overhead, this method is significantly better than the other methods because it uses a light-weight access control mechanism and does not involve complex operations; n indicates the number of attributes in the access control policy, and m indicates the number of attribute value pairs or conditions in the access control policy.
7. Conclusions
The IoT access control system, based on the smart contracts designed in this article, combines blockchain with access control technology, solves the problem of centralized trust of central nodes in traditional access control, and improves the reliability and security of access control. The access control model designed in this article can set access control policies for each IoT terminal device, to achieve fine-grained access control and prevent over authorization and unauthorized access. At the same time, the super ledger is used as the blockchain platform to execute smart contracts. Under the condition of retaining the characteristics of blockchain, the system is more flexible and easier to deploy and use, which can meet the needs of large-scale intelligent manufacturing Internet of Things scenarios.