A Reuse-Oriented Visual Smart Contract Code Generator for Efficient Development of Complex Multi-Party Interaction Scenarios
Abstract
:1. Introduction
- RQ1: How can we model the requirement scenarios and interaction relationships of SCs so that they can be easily understood and used by both business personnel and developers?
- RQ2: How can we automatically generate SC codes based on the process and interaction models in a reusable way?
- RQ3: How can reusable libraries be maintained in an efficient, low-barrier way to support RQ2’s automatic code generation?
1.1. The Model Based on BPMN Integrated SC Interaction
1.2. Multi-Layer Reusable Library and Mapping Rules
1.3. Visual Maintenance of Multi-Layer Reusable Library
2. Related Work
2.1. Business Modeling Based on BPMN for SC
2.2. Automatic Code Generation of SC
3. Method
3.1. Model Based on BPMN-Integrated SC Interaction
- Activity There are three types of activities:
- -
- UserTask: This represents the users’ actions in external systems, which do not occur on the blockchain, and some of these tasks will invoke the current SC.
- -
- ScriptTask: This action is performed by the current SC, and it corresponds to a composite function.
- -
- ServiceTask: This action needs to invoke behaviors in other SCs, and it can be regarded as an interaction within the blockchain.
- SwimlaneWe design three types of swimlanes, i.e., Participant, Current SC, and External SC. As shown in Figure 2, at the top of the swimlane is the behavior of the Participant. User tasks are modeled in the Participant swimlane; because this type of task is run in an external system, it will not be resolved. Service tasks are modeled in the external SC swimlane, which represents the external SC behavior that the current SC needs to call. The middle part is the current SC swimlane, which is the core of the BPMN model, storing all script tasks of the current SC.
- Connecting Objects
- -
- Message Flow: There are two types of message flow. The first type is the interaction between the user task and script task, which describes the interaction between the user and the SC. The second type is the information interaction between the script task and service task, which represents the invocation of external SCs, as shown in the message flow on the left side of Figure 3.
- -
- Sequence Flow: There are two types of sequence flow. The first type is used to specify the order in which activities are executed. The second type is the interaction between two script tasks in the same swimlane, representing the call relationship. It should be noted that when two script tasks interact, the number on the task flow indicates the execution order of the invocation relationship, and the small number indicates the initiator of the invocation behavior, as shown in the sequence flow on the right side of Figure 3.

3.2. Multi-Layer Reusable Library and Mapping Rules
- script-common: This task is the current SC task and does not invoke any other task—for example, the Cancel the insurance task in Figure 4. When parsing such tasks, the developers only need to form a mapping to the composite functions in the reusable code library.
- script-extra-replaced: This task is a task of the current SC and it invokes a task of an external SC—for example, the Check validity and cancellation conditions of the insurance task in Figure 4. In addition to forming a mapping of the task to the composite functions in the reusable code library, its parsing process also requires the introduction of the function name and address of the external SC being invoked.
- script-intern-replaced: This task belongs to the current SC, and it invokes another task of the current SC. When parsing such tasks, in addition to forming a mapping to the composite functions in the reusable code library, the developers also need to introduce the name of the called function. This type of task is not commonly used because functions with call relationships are usually written in a task.
- service: This task is an external contract task invoked by the current SC task—for example, the Determine whether the cancellation time limit is exceeded task in Figure 4. Since this type of task is an external task, we do not need to form a mapping to the composite functions in the reusable code library; we only need to obtain the function name and contract name.
3.3. Visual Maintenance of Multi-Layer Reusable Library
3.3.1. Solidity Logical Structure Based on Google Blockly to Generate Functions
3.3.2. Code Configurator Based on Web Form to Generate New Composite Functions
3.3.3. Code Generator Based on Google Blockly to Generate SC Code
3.4. The Overall Architecture of the SC Code Generator
3.4.1. Business Process Modeling
3.4.2. Reusable Function Management
3.4.3. Code Generation
3.4.4. Security Checking and Deployment
4. Experiment and Comparison
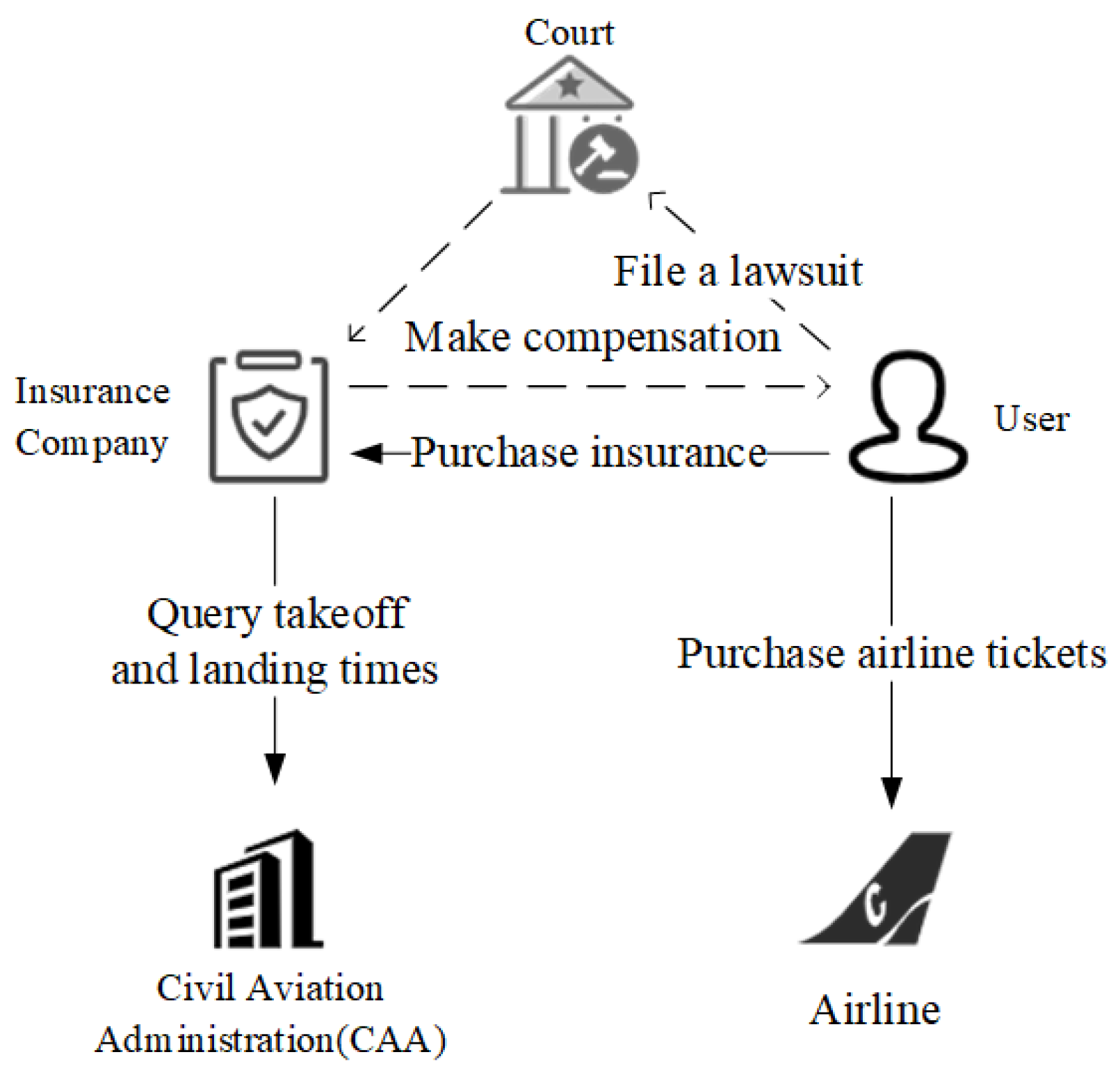
4.1. Use Cases for Evaluation
- -
- Voting and Election Contract [21]: This case is one of the earliest applications of SCs and reflects the idea of decentralization. Therefore, this application is taken as one of our cases. The sponsor of a poll can register both the voters and the candidates, and, within a specific time, the voters can choose a candidate to vote for. After the polls close, everyone can view the results.
- -
- Voting Result Notification Contract [22]: The contract involves the originator, voter, and candidate who is registered. When the number of votes reaches a specified number, messages are sent to other contracts.
- -
- Crowdfunding Contract [23]: The contract covers the crowdfunding originator and shareholders. The user becomes a crowdfunding shareholder when money is transferred from a user’s account to a crowdfunding project. A crowdfunding project is established if it is successfully raised within the specified time, and the shareholders in the project have the right to vote on all proposals. All money will be refunded unless the fund is raised successfully.
- -
- Supply Chain Contract [24]: The contract involves buyers, manufacturers, intermediaries, carriers, and suppliers. The buyer places an order with the manufacturer, who sets delivery dates and compensation for overdue payments. Manufacturers contact intermediaries, who identify suppliers and carriers. After receiving the raw materials from the supplier, the manufacturer produces goods. After the manufacturer has delivered the goods to the buyer, the compensation clause will be enforced if the delivery time is exceeded.
- -
- Buying and Selling Contract [25]: The contract involves buyers and sellers. Sellers can register goods for buyers to view and purchase. After the buyer buys the goods, the seller will determine the delivery time and overdue compensation. The indemnity clause will be applied if the delivery time exceeds the agreed time.
4.2. Evaluation
4.3. Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 2008, 1. [Google Scholar]
- Szabo, N. Smart contracts: Building blocks for digital markets. EXTROPY J. Transhumanist Thought 1996, 18, 28. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Air France-KLM/Simplon.co. Fizzy White Paper. 2018. Available online: https://www.axa.com/en/news/axa-goes-blockchain-with-fizzy (accessed on 15 March 2023).
- Dwivedi, V.; Norta, A. Auto-generation of smart contracts from a domain-specific XML-based language. In Intelligent Data Engineering and Analytics, Proceedings of the 9th International Conference on Frontiers in Intelligent Computing: Theory and Applications (FICTA 2021), Aizawl, India, 25–26 June 2021; Springer: Berlin/Heidelberg, Germany, 2022; pp. 549–564. [Google Scholar]
- Dannen, C. Introducing Ethereum and Solidity; Springer: Berlin/Heidelberg, Germany, 2017; Volume 1. [Google Scholar]
- Boudjema, E.H.; Verlan, S.; Mokdad, L.; Faure, C. VYPER: Vulnerability detection in binary code. Secur. Priv. 2020, 3, e100. [Google Scholar] [CrossRef] [Green Version]
- Xu, T.A.; Xu, J. A short survey on business models of decentralized finance (DeFi) protocols. arXiv 2022, arXiv:2202.07742. [Google Scholar]
- Panayides, P.M.; Lun, Y.V. The impact of trust on innovativeness and supply chain performance. Int. J. Prod. Econ. 2009, 122, 35–46. [Google Scholar] [CrossRef]
- Weber, I.; Xu, X.; Riveret, R.; Governatori, G.; Ponomarev, A.; Mendling, J. Untrusted business process monitoring and execution using blockchain. In Proceedings of the International Conference on Business Process Management, Rio de Janeiro, Brazil, 18–22 September 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 329–347. [Google Scholar]
- Skotnica, M.; Klicpera, J.; Pergl, R. towards model-driven smart contract systems–code generation and improving expressivity of smart contract modeling. In Proceedings of the EEWC, Bolzano, Italy, 9–10 November 2020; pp. 1–15. [Google Scholar]
- Qin, P.; Tan, W.; Guo, J.; Shen, B. Intelligible description language contract (IDLC)—A novel smart contract model. Inf. Syst. Front. 2021, 1–18. [Google Scholar] [CrossRef]
- Wöhrer, M.; Zdun, U. Domain specific language for smart contract development. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 3–6 May 2020; pp. 1–9. [Google Scholar]
- Tateishi, T.; Yoshihama, S.; Sato, N.; Saito, S. Automatic smart contract generation using controlled natural language and template. IBM J. Res. Dev. 2019, 63, 1–12. [Google Scholar] [CrossRef]
- Google Blockly. Available online: https://developers.google.com/blockly (accessed on 1 December 2022).
- Guida, L.; Daniel, F. Supporting reuse of smart contracts through service orientation and assisted development. In Proceedings of the 2019 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPCON), Newark, CA, USA, 5–9 April 2019; pp. 59–68. [Google Scholar]
- Mao, D.; Wang, F.; Wang, Y.; Hao, Z. Visual and user-defined smart contract designing system based on automatic coding. IEEE Access 2019, 7, 73131–73143. [Google Scholar] [CrossRef]
- DuPont, Q. Experiments in algorithmic governance: A history and ethnography of “The DAO”, a failed decentralized autonomous organization. In Bitcoin and Beyond; Routledge: London, UK, 2017; pp. 157–177. [Google Scholar]
- Feist, J.; Grieco, G.; Groce, A. Slither: A static analysis framework for smart contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; pp. 8–15. [Google Scholar]
- Mohanty, D. Frameworks: Truffle and embark. In Ethereum for Architects and Developers; Springer: Berlin/Heidelberg, Germany, 2018; pp. 181–195. [Google Scholar]
- Daramola, O.; Thebus, D. Architecture-centric evaluation of blockchain-based smart contract e-voting for national elections. Informatics 2020, 7, 16. [Google Scholar] [CrossRef]
- Frantz, C.K.; Nowostawski, M. From institutions to code: Towards automated generation of smart contracts. In Proceedings of the 2016 IEEE 1st International Workshops on Foundations and Applications of Self* Systems (FAS* W), Augsburg, Germany, 12–16 September 2016; pp. 210–215. [Google Scholar]
- He, H.; Yan, A.; Chen, Z. Review of smart contract technology and application based on block chain. Comput. Res. Dev. 2018, 55, 2452–2466. [Google Scholar]
- Fdhila, W.; Rinderle-Ma, S.; Knuplesch, D.; Reichert, M. Change and compliance in collaborative processes. In Proceedings of the 2015 IEEE International Conference on Services Computing, New York, NY, USA, 27 June–2 July 2015; pp. 162–169. [Google Scholar]
- Weingaertner, T.; Rao, R.; Ettlin, J.; Suter, P.; Dublanc, P. Smart contracts using blockly: Representing a purchase agreement using a graphical programming language. In Proceedings of the Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018; pp. 55–64. [Google Scholar]









| Contract | Total Code Lines | Reused Code Lines | Number of State Variables | Number of Reused Fields | Number of Functions | Number of Reused Function | Reused Code Rate |
|---|---|---|---|---|---|---|---|
| Crowdfunding | 130 | 55 | 15 | 6 | 11 | 4 | 40.74% |
| Voting Result Notification | 80 | 39 | 9 | 6 | 8 | 4 | 48.75% |
| Election | 58 | 58 | 7 | 7 | 5 | 5 | 100% |
| Supply Chain | 150 | 65 | 19 | 8 | 11 | 6 | 43.30% |
| Buying and Selling | 87 | 65 | 11 | 8 | 7 | 6 | 74.71% |
| Method | Model | Business Processes | Interactive Relationship | Code Reuse | Visual Interface | Security Checking | Complete Smart Contract |
|---|---|---|---|---|---|---|---|
| Proposed Method | BPMN + Blockly | YES | YES | YES | YES | YES | YES |
| Skotnica [11] | BPMN | YES | NO | NO | YES | NO | NO |
| Qin [12] | IDLC | NO | NO | NO | NO | NO | NO |
| Guida [16] | SC Descriptor Model | NO | NO | YES | YES | NO | YES |
| Wöhrer [13] | CML | NO | NO | NO | NO | NO | YES |
| Mao [17] | Char-RNN + Blockly | NO | NO | YES | YES | NO | YES |
| Ingo [10] | BPMN | YES | NO | YES | YES | NO | NO |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shen, X.; Li, W.; Xu, H.; Wang, X.; Wang, Z. A Reuse-Oriented Visual Smart Contract Code Generator for Efficient Development of Complex Multi-Party Interaction Scenarios. Appl. Sci. 2023, 13, 8094. https://doi.org/10.3390/app13148094
Shen X, Li W, Xu H, Wang X, Wang Z. A Reuse-Oriented Visual Smart Contract Code Generator for Efficient Development of Complex Multi-Party Interaction Scenarios. Applied Sciences. 2023; 13(14):8094. https://doi.org/10.3390/app13148094
Chicago/Turabian StyleShen, Xinzhe, Wenyu Li, Hanchuan Xu, Xiao Wang, and Zhongjie Wang. 2023. "A Reuse-Oriented Visual Smart Contract Code Generator for Efficient Development of Complex Multi-Party Interaction Scenarios" Applied Sciences 13, no. 14: 8094. https://doi.org/10.3390/app13148094





