Analysis of Cyber-Intelligence Frameworks for AI Data Processing
Abstract
:1. Introduction
- The provision of a detailed explanation and the current status of the state of the art of the three most relevant cyber-intelligence frameworks: Diamond Model, Cyberkill Chain, and Mitre Att&ck.
- A case study of a real cyberattack for the three mentioned frameworks, emphasising the strengths, weaknesses, and best perspective offered by each one of them.
- The definition of seventeen variables of interest in order to compare, among other characteristics, the efficacy, adaptability, and simplicity of the frameworks.
- An analysis, based on these seventeen characteristics, of the most appropriate framework to combine with AI methods and, more specifically, machine-learning models. With this analysis, we also conclude the suitability of each framework depending on the specific situation and knowledge of interest.
2. Background of Cyber Intelligence
2.1. Concept and Characteristics
2.2. Levels and Typologies
- The strategic level is focused on supporting decision making on the policies and objectives of an organisation. In this sense, the knowledge, study, and possible evolution of the malicious actors involved that can influence the organisation’s risks are essential. An example is the analysis of the organisation’s exposure to the main groups that exploit ransomware-type malware or carry out Advanced Persistent Threat (APT) actions.
- The tactical level is aimed at supporting the planning of specific actions that enable the achievement of the organisation’s strategic objectives, for example, the analysis of the attack Tactics, Techniques, and Procedures (TTPs) of a given malicious actor.
- The operational level refers to the knowledge that allows decisions to be taken in a short space of time in the framework of the actions necessary to prevent a given attack or incident, e.g., the analysis of indicators of compromise (IOCs) that represent a threat to the organisation.
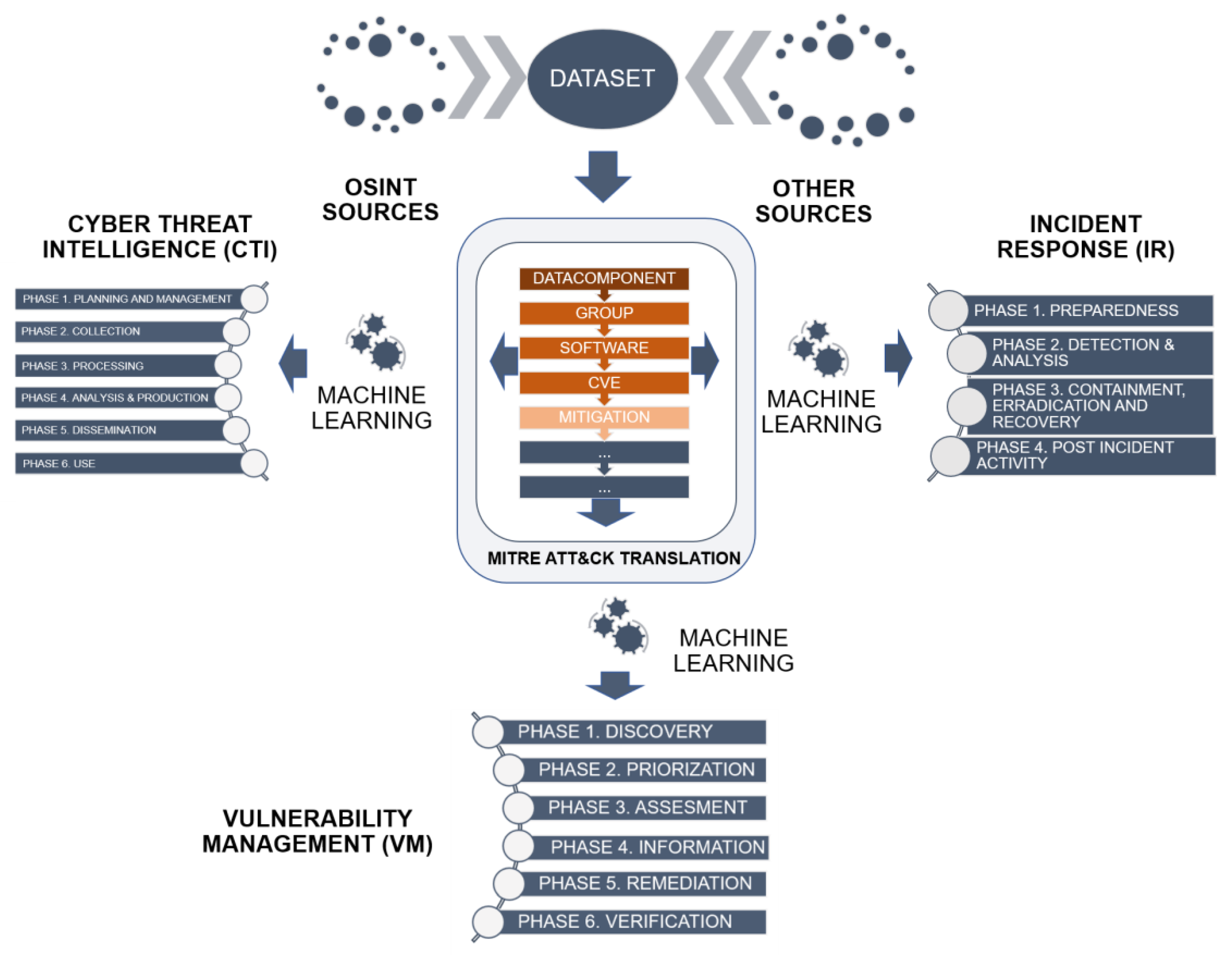
- Phase 1. Planning and management. In this phase, the RPIs are identified based on the prior definition of critical assets and relevant threats whose exploitation generates an impact.
- Phase 2. Collection. Data collection is carried out following structured methods based on the requirements of the previous phase.
- Phase 3. Processing. The collected data are processed with appropriate techniques.
- Phase 4. Analysis and production. This is a critical phase of the cycle in which the information obtained in previous phases is transformed into intelligence. Today, it requires the presence of the human factor.
- Phase 5. Dissemination. This is the stage in which the intelligence is provided to decision-makers so that they have the appropriate knowledge.
- Phase 6. Utilisation. Decision making based on the delivered product is considered another critical and decisive moment in the cycle.
- Phase 1. Preparedness. This phase consists of establishing and forming an incident response team and acquiring the necessary tools and resources.
- Phase 2. Detection and analysis. The aim at this stage is to limit the number of incidents that will occur by selecting and implementing a set of controls based on the results of the risk assessments and, where appropriate, dealing with residual risks in the first instance.
- Phase 3. Containment, eradication, and recovery. Once it is known that an incident has been affected, the response actions are included in this phase in order to minimise the damage and try to facilitate business continuity in the shortest possible time.
- Phase 4. Post-incident activity. In this phase, the relevant reports are drawn up, and the incident is analysed ex post with a view to obtaining lessons learned and generating good practices.
- Phase 1. Discovery. Take inventory of the assets to be protected in the organisation.
- Phase 2. Prioritisation. Analyse the risks associated with the commitment of each asset and its criticality for the provision of the service.
- Phase 3. Assessment. Determine a baseline risk profile to be acted upon.
- Phase 4. Information. Monitor assets and describe vulnerabilities.
- Phase 5. Remediation. Prioritise and remediate vulnerabilities according to the associated risk profile.
- Phase 6. Verification. Execute controls that verify that threats have been eliminated.
3. Related Work: Cyber-Intelligence Frameworks
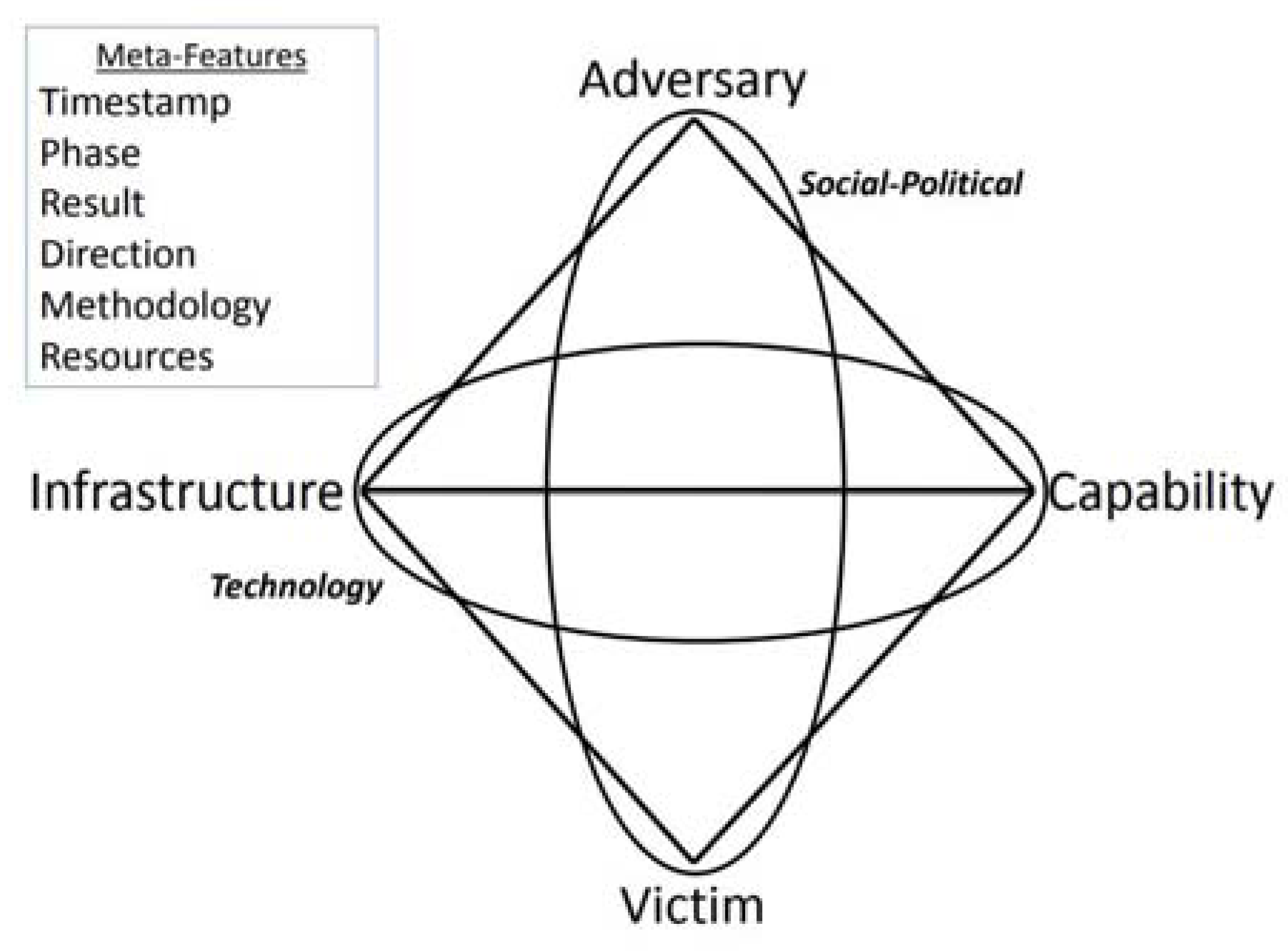
3.1. Diamond Model
3.2. Cyberkill Chain
- Early warning or prevention, analysing potential weaknesses in the technological infrastructure at each stage of a potential attack before it can take place.
- Optimisation of resources, focusing investments and efforts on the most vulnerable stages in the infrastructure.
- Raising awareness of workers who do not have knowledge of cybersecurity, offering a graphic and consecutive structure that allows a better understanding of what a cyberattack is and the risks it generates in the organisation.

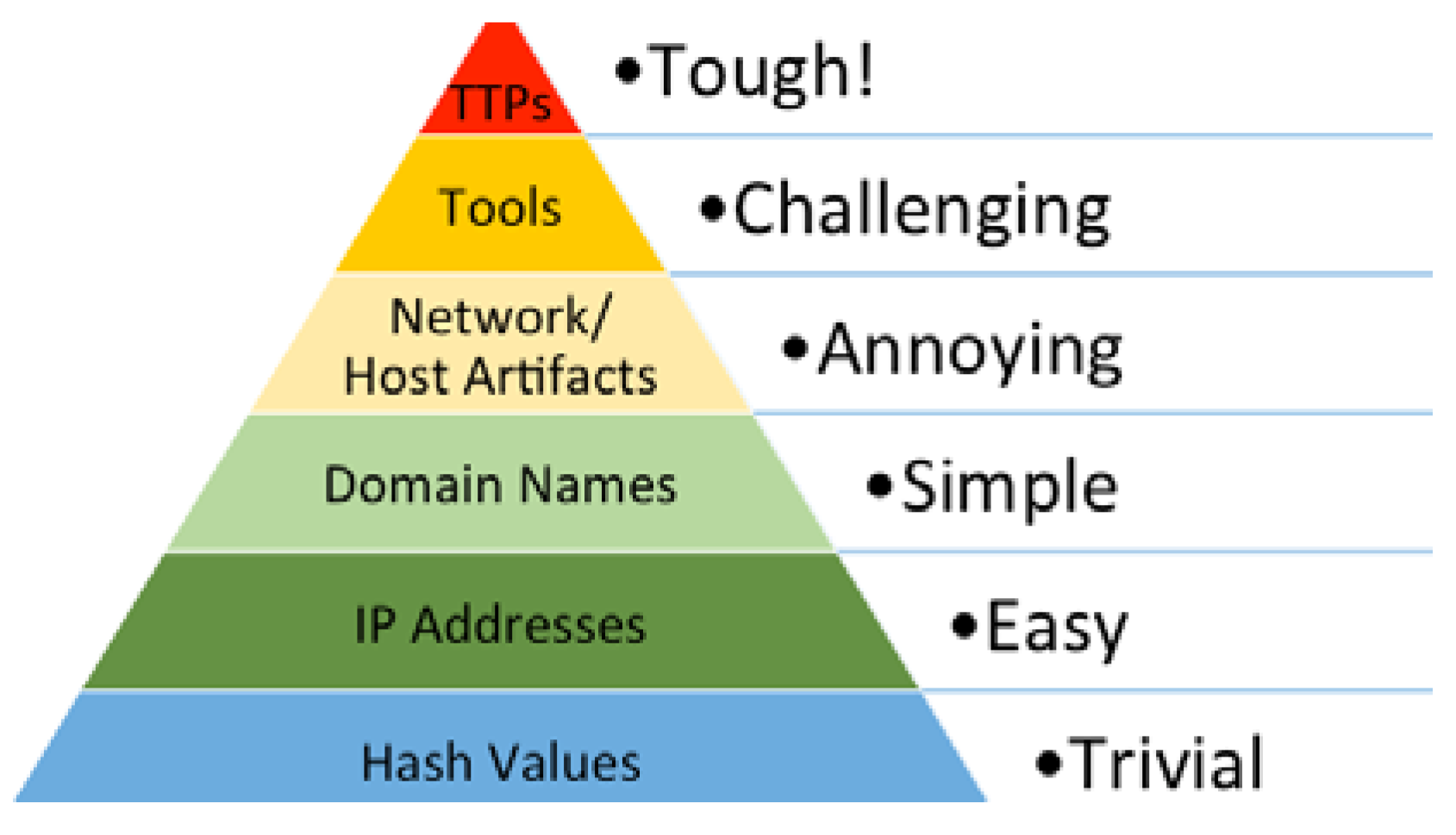
- Atomic: indicators that cannot be broken down into smaller parts and retain their meaning in the context of an attack (IP, domains, etc.);
- Computational: derived from the data obtained in an incident (hash);
- Behavioural: collections of atomic and computational indicators (TTPs).
3.3. Mitre Att&ck
3.4. Framework Comparison
- The NIST Cybersecurity Framework [32] is a framework that focuses on cybersecurity risk management and provides guidelines in areas such as identification, protection, detection, response, and recovery. Although it is widely used, it is not focused on cyber-intelligence analysis but rather on the risk analysis of entities.
- DREAD (Damage, Reproducibility, Exploitability, Affected Users, Discoverability) [33] is another method developed by Microsoft to assess and classify the risks associated with security threats in software and information technology systems.
4. Materials and Methods
4.1. Application of the Diamond Model
- Victim: The public entity analysed (RASK) is a victim of the Public Administration sector in Spain, with a geographical location distributed throughout the Spanish territory. Its popularity is high, and its political positioning is neutral. The economic capacity is low, as it does not have its own resources. The maturity of the organisation is low, as demonstrated by subsequent audits. The organisation is highly critical, as it is an essential entity for the exercise of the functions of the Spanish state. The types of systems affected are desktops and servers, including the five domain controllers. The information is not classified, but it is personal information subject to legislation. The organisation is not known to have exposed CVEs. The victim belongs to the Spanish Administration Sector, which is seriously lacking in cybersecurity, as shown in successive national reports on the state of security of ICT systems published by the national CSIRT [38].
- Capability: The malware used was at least Cobalt Strike, Ryuk, Bazar Loader, and SystemBC. There is no evidence of vulnerability exploitation because it was not necessary, as the attacker had administrator credentials. The malware used does not reflect great sophistication as they are evolutions of known malware widely used by cybercriminals in their attacks. It requires the intervention of the adversary, but no victims for the attack. Although the initial method of obtaining credentials is unknown, there is no evidence of the application of social engineering techniques. It is not part of any campaign to exploit or distribute malware through phishing or other types of attacks.
- Infrastructure: Once the information had been analysed from a technical point of view, the following IP addresses and domains that made up the main C2s were provided:
- ---.26.29[.]242 (Media Land LLC- Saint Petersburg 09-09-2020) culunk[.]com resolutions (registration 22/02/2021)
- --.141.84[.]190 (Media Land LLC- Saint Petersburg 14-11-2019) resolutions by smadst[.]com (registration 22/02/2021)
- ---.26.29[.]245 (Media Land LLC- Saint Petersburg 09-09-2020) eochea[.]com resolutions (registration 03/02/2021)
- --.141.87[.]76 (Media Land LLC- Saint Petersburg 25-12-2020) dorkedit[.]com resolutions (registration 03/03/2021)
- Adversary: Probable attribution by identifying TTPs, as well as by matching IP ranges and domains with Cobalt Strike servers, can presumably be associated with UNC1878, an Eastern European cybercriminal group with connections to Ukraine and Russia, whose purpose is economic. UNC groups can evolve, eventually merging with other groups and potentially drifting into actors with recognised threat names such as “Advanced Persistent Threats” (APTs) or “Financially-Motivated Hacking Groups” (FINs) [40]. Some expert research has attributed the name “Group One” to the UNCT1878 actor, stating that its targets are “indiscriminate” and its infections are “opportunistic” and assigning it the following characteristics [41]:
- Infection vector: phishing emails, usually containing links.
- Speed of execution: the time between initial infection and encryption has recently been reduced from around 2–5 days to between 3 and 6 hours.
- Consistent use of self-signed Cobalt Strike samples.
- Use of legitimate tools along the post-engagement infection chain: Cobalt Strike, Empire, Meterpreter, Mimikatz, Kerbrute, Kerberoast, BloodHound, AdFind.
- Absence of exfiltration or publication of information about their victims.
4.2. Application of the Cyberkill Chain Model
4.3. Application of the Mitre Att&ck Model
5. Results
- Maturity: reflects that the development of the standard has reached a sufficient degree.
- Flexibility: refers to the capacity to adapt to other environments outside the framework.
- Popularity: relative to the extent and use in the global community.
- Own taxonomy: existence of the framework’s own categorisation of its characteristics.
- Datasets: existence of open sources of data repositories referring to that framework.
- Proprietary software: development of native tools that allow its application.
- Adaptation to different attacks: indicates whether the framework can be used for different types of attacks (ransomware, APT attacks, DDoS, etc.).
- Update: whether there is constant updating by the community or developer.
- Ease of use: usability of the framework by inexperienced users.
- Parameterisation: indicates the creation of variables or arguments to define the most relevant points of interest of an attack.
- Granularity: indicates whether the level of detail of the model is high.
- Visualisation: indicates whether the information can be viewed in graphical form.
- Easy integration with other systems: reflects possible integration with identification or protection systems (e.g., IDS/IPS or AntiVirus)
- Orientation: indicates which parameter is the primary focus: the attackers, the organisation’s assets, or the software used in the attack.
- Scalability: indicates whether a framework has the ability to keep properly functioning when the amount of data changes in size or volume.
- Interoperability: the capacity of a framework to share data and facilitate information and knowledge exchange with other tools.
- Performance: indicates whether a framework is efficient in working with large-scale data.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yan, K.; Liu, L.; Xiang, Y.; Jin, Q. Guest Editorial: AI and Machine Learning Solution Cyber Intelligence Technologies: New Methodologies and Applications. IEEE Trans. Ind. Inform. 2020, 16, 6626–6631. [Google Scholar] [CrossRef]
- Kemmerer, R.A. Cybersecurity. In Proceedings of the 25th International Conference on Software Engineering, Portland, OR, USA, 3–10 May 2003; pp. 705–715. [Google Scholar] [CrossRef]
- Kim, S.H.; Wang, Q.-H.; Ullrich, J.B. A comparative study of cyberattacks. Commun. ACM 2012, 55, 66–73. [Google Scholar] [CrossRef]
- Ludwick, M.; McAllister, J.; Mellinger, A.O.; Sereno, K.A.; Townsend, T. Cyber Intelligence Tradecraft Project: Summary of Key Findings; Software Engineering Institute: Pittsburgh, PA, USA, 2013; Available online: https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=40201 (accessed on 4 August 2023).
- Preuveneers, D.; Joosen, W.; Bernabe, J.B.; Skarmeta, A. Distributed Security Framework for Reliable Threat Intelligence Sharing. Secur. Commun. Netw. 2020, 2020, 8833765. [Google Scholar] [CrossRef]
- Gordon, L.A.; Loeb, M.P.; Zhou, L. Integrating cost–benefit analysis into the NIST Cybersecurity Framework via the Gordon–Loeb Model. J. Cybersecur. 2020, 6, tyaa005. [Google Scholar] [CrossRef]
- ISO/IEC 27000:2018; Information Security, Cybersecurity and Privacy Protection. International Organization of Standards: Geneva, Switzerland, 2018. Available online: https://www.iso.org/standard/73906.htmlg (accessed on 4 August 2023).
- National Institute of Standards and Technology. Guide for Conducting Risk Assessments. 2012. Available online: https://doi.org/10.6028/NIST.SP.800-30r1 (accessed on 4 August 2023).
- López-Muñoz, J. Manual de Inteligencia; Tirant Lo Blanch: València, Spain, 2019. [Google Scholar]
- Centro Criptológico Nacional. Guía de Seguridad de las Tic (CCN-STIC-480A) Seguridad en el Control de Procesos y Scada Guia de Buenas Prácticas. February 2010. Available online: https://www.ccn-cert.cni.es/series-ccn-stic/guias-de-acceso-publico-ccn-stic/209-ccn-stic-480a-seguridad-en-sistemas-scada-guia-de-buenas-practicas/file.html (accessed on 1 May 2022).
- Bautista, W. Practical Cyberintelligence; Packt Publishing: Birmingham, UK, 2018. [Google Scholar]
- Bishop, C.M. Pattern Recognition and Machine Learning. In Information Science and Statistics; Springer: New York, NY, USA, 2006. [Google Scholar]
- Glassman, M.; Kang, M.J. Intelligence in the internet age: The emergence and evolution of Open Source Intelligence (OSINT). Comput. Hum. Behav. 2012, 28, 673–682. [Google Scholar] [CrossRef]
- The MITRE Corporation. Structured Threat Information eXpression (STIXTM). Available online: https://makingsecuritymeasurable.mitre.org/docs/stix-intro-handout.pdf (accessed on 22 June 2023).
- The MITRE Corporation. Trusted Automated eXchange of Indicator Information—TAXIITM. Available online: https://makingsecuritymeasurable.mitre.org/docs/taxii-intro-handout.pdf (accessed on 22 June 2023).
- Mattern, T.; Felker, J.; Borum, R.; Bamford, G. Operational Levels of Cyber Intelligence. Int. J. Intell. CounterIntell. 2014, 27, 702–719. [Google Scholar] [CrossRef]
- Bianco, D.J. Enterprise Detection & Response: The Pyramid of Pain. Enterprise Detection & Response. 1 March 2013. Available online: http://detect-respond.blogspot.com/2013/03/the-pyramid-of-pain.html (accessed on 22 June 2023).
- NIST SP 800-61r2; Computer Security Incident Handling Guide: Recommendations of the National Institute of Standards and Technology. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012. [CrossRef]
- NIST SP 800-40ver2; Creating a Patch and Vulnerability Management Program. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2005. [CrossRef]
- Vulnerability Management Life Cycle|NPCR|CDC. 20 January 2021. Available online: https://www.cdc.gov/cancer/npcr/tools/security/vmlc.htm (accessed on 22 March 2022).
- Naik, N.; Jenkins, P.; Grace, P.; Song, J. Comparing Attack Models for IT Systems: Lockheed Martin’s Cyber Kill Chain, MITRE ATT&CK Framework and Diamond Model. In Proceedings of the 2022 IEEE International Symposium on Systems Engineering (ISSE), Vienna, Austria, 24–26 October 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Caltagirone, S.; Pendergast, A.; Betz, C. The Diamond Model of Intrusion Analysis; Center for Cyber Threat Intelligence and Threat Research: Hanover, MD, USA, 2013; p. 62. [Google Scholar]
- Shin, Y.; Lim, C.; Park, M.; Cho, S.; Han, I.; Oh, H.; Lee, K. Alert correlation using diamond model for cyber threat intelligence. In Proceedings of the European Conference on Cyber Warfare and Security; Academic Conferences International Limited: Oxfordshire, UK, 2019; pp. 444–450. [Google Scholar]
- Hutchins, E.M.; Cloppert, M.J.; Amin, R.M. Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains. Lead. Issues Inf. Warf. Secur. Res. 2011, 1, 80. [Google Scholar]
- Means, C.D. Applying Cognitive Work Analysis to Time Critical Targeting Functionality; Defense Technical Information Center: Fort Belvoir, VA, USA, 2004; p. 161. [Google Scholar]
- Lockheed Martin. Cyber Kill Chain®. Available online: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html (accessed on 26 June 2023).
- Ahmed, Y.; Taufiq, A.; Arafatur, R.M. A cyber kill chain approach for detecting advanced persistent threats. Comput. Mater. Contin. 2021, 67, 2497–2513. [Google Scholar] [CrossRef]
- Strom, B.E.; Applebaum, A.; Miller, D.P.; Nickels, K.C.; Pennington, A.G.; Thomas, C.B. Mitre Att&ck: Design and Philosophy; Technical Report; The MITRE Corporation: Bedford, MA, USA, 2018. [Google Scholar]
- Al-Shaer, R.; Spring, J.M.; Christou, E. Learning the Associations of MITRE ATT&CK Adversarial Techniques. arXiv 2020, arXiv:2005.01654. [Google Scholar]
- Nisioti, A.; Loukas, G.; Rass, S.; Panaousis, E. Game-Theoretic Decision Support for Cyber Forensic Investigations. Sensors 2021, 21, 5300. [Google Scholar] [CrossRef] [PubMed]
- Alavizadeh, H.; Jang-Jaccard, J.; Alpcan, T.; Camtepe, S.A. A Markov Game Model for AI-based Cyber Security Attack Mitigation. arXiv 2021, arXiv:2107.09258. [Google Scholar]
- NIST CSWP 04162018; Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [CrossRef]
- Shostack, A. Experiences Threat Modeling at Microsoft; Shostack + Associates: Seattle, WA, USA, 2008. [Google Scholar]
- Wynn, J. Threat Assessment and Remediation Analysis (TARA); MITRE Corporation: Bedford, MA, USA, 2014; Available online: https://apps.dtic.mil/sti/pdfs/AD1016629.pdf (accessed on 4 August 2023).
- Kanakogi, K.; Washizaki, H.; Fukazawa, Y.; Ogata, S.; Okubo, T.; Kato, T.; Kanuka, H.; Hazeyama, A.; Yoshioka, N. Comparative Evaluation of NLP-Based Approaches for Linking CAPEC Attack Patterns from CVE Vulnerability Information. Appl. Sci. 2022, 12, 3400. [Google Scholar] [CrossRef]
- Kaloroumakis, P.E.; Smith, M.J. Toward a Knowledge Graph of Cybersecurity Countermeasures; MITRE Corporation: Bedford, MA, USA, 2020; p. 11. [Google Scholar]
- Al-Mohannadi, H.; Mirza, Q.; Namanya, A.; Awan, I.; Cullen, A.; Disso, J. Cyber-Attack Modeling Analysis Techniques: An Overview. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; pp. 69–76. [Google Scholar] [CrossRef]
- Centro Criptológico Nacional. Resultados Informe INES CCN. Available online: https://www.ccn-cert.cni.es/soluciones-seguridad/ines/resultado-general.html (accessed on 29 March 2022).
- ThreatConnect IOCs Wizard Spider. Available online: https://threatconnect.com/blog/threatconnect-research-roundup-threat-intelligence-update/ (accessed on 29 March 2022).
- Mandiant. Going ATOMIC: Clustering and Associating Attacker Activity at Scale. Available online: https://www.mandiant.com/resources/clustering-and-associating-attacker-activity-at-scale (accessed on 29 March 2022).
- ANSSI. Ryuk Ransomware. Available online: https://www.cert.ssi.gouv.fr/uploads/CERTFR-2021-CTI-006.pdf (accessed on 29 March 2022).
- CISA. Alert. Ransomware Activity Targeting the Healthcare and Public Health Sector. Available online: https://www.cisa.gov/uscert/ncas/alerts/aa20-302a (accessed on 29 March 2022).
- Fact Sheet: Trickbot Malware. Available online: https://www.cisa.gov/uscert/sites/default/files/publications/TrickBot_Fact_Sheet_508.pdf (accessed on 29 March 2022).
- Thai CERT EDTA. Threat Group Cards: A Threat Actor Encyclopedia; Thai CERT EDTA: Bangkok, Thailand, 2019. [Google Scholar]
- Tatam, M.; Shanmugam, B.; Azam, S.; Kannoorpatti, K. A review of threat modelling approaches for APT-style attacks. Heliyon 2021, 7, e05969. [Google Scholar] [CrossRef] [PubMed]
- Hernández-Álvarez, L.; Barbierato, E.; Caputo, S.; Mucchi, L.; Encinas, L.H. EEG Authentication System Based on One- and Multi-Class Machine Learning Classifiers. Sensors 2023, 23, 186. [Google Scholar] [CrossRef] [PubMed]
- Zeng, J.; Wang, F.; Deng, J.; Qin, C.; Zhai, Y.; Gan, J.; Piuri, V. Finger Vein Verification Algorithm Based on Fully Convolutional Neural Network and Conditional Random Field. IEEE Access 2020, 8, 65402–65419. [Google Scholar] [CrossRef]
- Lu, X.; Xiao, L.; Xu, T.; Zhao, Y.; Tang, Y.; Zhuang, W. Reinforcement Learning Based PHY Authentication for VANETs. IEEE Trans. Veh. Technol. 2020, 69, 3068–3079. [Google Scholar] [CrossRef]
- Yang, H.; Jia, Y.; Han, W.-H.; Nie, Y.-P.; Li, S.-D.; Zhao, X.-J. Calculation of Network Security Index Based on Convolution Neural Networks. In Artificial Intelligence and Security; Sun, X., Pan, Z., Bertino, E., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2019; pp. 530–540. [Google Scholar] [CrossRef]
- Li, X.; Zhang, X.; Wang, D. Spatiotemporal Cyberspace Situation Awareness Mechanism for Backbone Networks. In Proceedings of the 2018 4th International Conference on Big Data Computing and Communications (BIGCOM), Chicago, IL, USA, 7–9 August 2018; pp. 168–173. [Google Scholar] [CrossRef]
- Marir, N.; Wang, H.; Feng, G.; Li, B.; Jia, M. Distributed Abnormal Behavior Detection Approach Based on Deep Belief Network and Ensemble SVM Using Spark. IEEE Access 2018, 6, 59657–59671. [Google Scholar] [CrossRef]
- Aljamal, I.; Tekeoğlu, A.; Bekiroglu, K.; Sengupta, S. Hybrid Intrusion Detection System Using Machine Learning Techniques in Cloud Computing Environments. In Proceedings of the 2019 IEEE 17th International Conference on Software Engineering Research, Management and Applications (SERA), Honolulu, HI, USA, 29–31 May 2019; pp. 84–89. [Google Scholar] [CrossRef]
- Kong, L.; Huang, G.; Wu, K.; Tang, Q.; Ye, S. Comparison of Internet Traffic Identification on Machine Learning Methods. In Proceedings of the 2018 International Conference on Big Data and Artificial Intelligence (BDAI), Beijing, China, 22–24 June 2018; pp. 38–41. [Google Scholar] [CrossRef]
- Kong, L.; Huang, G.; Zhou, Y.; Ye, J. Fast Abnormal Identification for Large Scale Internet Traffic. In Proceedings of the 8th International Conference on Communication and Network Security, in ICCNS ’18, Qingdao, China, 2–4 November 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 117–120. [Google Scholar] [CrossRef]
| ATTACK PHASE | INDICATORS |
|---|---|
| 1. RECOGNITION | Target recognition and access Purchase of access credentials in underground forums: vtagex.rask[.].co.uk (users 08s-in08 and admdp08) myhours.rask[.].co.uk:1124 (user 08s-in08) intraprod.rask.co.uk (user PROD08) e-mail.rask[.]es (users admdp08, 08s-in08 and 08dpucr) supportcx.rask[.]es (user admdp08) Office 365 by RASK (user 08s-in08@rask[.]es) |
| 2. WEAPONISATION | DLL_Bazar Loader file: “desktop.dll” DLL_CobaltStrike file “qws.dll” (08/07/2021 21:31) DLL_CobaltStrike file “test.dll” (06/07/2021 17:31) Ryuk file “82.exe” Ryuk file “6hr.exe” Ryuk file “6hr.exe” (06/07/2021 17:31) Cobalt Strike Beacon Cobalt Strike 87fb204.exe Beacon Cobalt Stike f59173f.exe […] |
| 3. DEPLOYMENT | Access with administrator credentials admdp08 PsExec lateral movements (since 01/07/2021 12:05) Deployment of Cobalt Strike Beacons (since 06/07/2021 17:21) Access to Domain Controller (DC) listings (06/07/2021 18:14) […] |
| 4. EXPLOITATION | Displays BazarLoader “desktop.dll” in DC and executes SystemBC and Cobalt Strike malware (08/07/2021 21:27 21:31) |
| 5. INSTALLATION | Malware Ryuk “82.exe” (09/07/2021 19:24) and “6hr.exe” (09/07/2021 4:17) in C:\Windows. |
| 6. C2 | Cobalt Strike and SystemBC connections to the following C2: IP Address-Domain ---.26.29.242-culunk[.]com IP Address-Domain ---.26.29[.]245-eochea[.]com IP Address-Domain --.141.84[.]190-smadst[.]com IP address-Domain --.141.210[.]78-choopa[.]com IP address-Domain --.141.87[.]60-vultr[.]com IP address-Domain --.141.87[.]76-dorkedit[.]com […] |
| 7. ACTIONS TO OBJECTIVES | Massive encryption of information on computers with AES256 symmetric algorithm, and subsequent encryption of AES key with RSA asymmetric algorithm. |
| TACTICS | TECHNIQUES |
| T1589: Gather Victim Identity Information; T1591: Gather Victim Org Information. |
| T1584: Compromise Infrastructure; T1588: Obtain Capabilities. |
| T1078: Valid Accounts |
| - |
| T1078: Valid Accounts |
| T1078: Valid Accounts |
| T1078: Valid Accounts |
| - |
| T1069: Permission Groups Discovery |
| T1210: Exploitation of Remote Services; T1021: Remote Services |
| T1005: Data from Local System |
| T1071: Application Layer Protocol |
| T1041: Exfiltration Over C2 Channel |
| T1486: Data Encrypted for Impact |
| DIAMOND MODEL | CYBERKILL CHAIN | MITRE ATT&CK | |
|---|---|---|---|
| MATURITY | YES | YES | YES |
| FLEXIBILITY | NO | NO | YES |
| POPULARITY | NO | YES | YES |
| OWN TAXONOMY | NO | NO | YES |
| DATASETS | NO | NO | YES |
| PROPRIETARY SOFTWARE | NO | NO | YES |
| ADAPTATION TO DIFFERENT ATTACKS | YES | NO | YES |
| UPDATE | NO | NO | YES |
| EASE OF USE | YES | NO | NO |
| PARAMETERISATION | NO | NO | YES |
| GRANULARITY | YES | NO | YES |
| VISUALISATION | YES | YES | YES |
| EASY INTEGRATION WITH OTHER SYSTEMS | NO | YES | YES |
| ORIENTATION | ACTIVE ATTACKERS | ATTACKERS | ACTIVE ATTACKERS SOFTWARE |
| SCALABILITY | NO | NO | YES |
| INTEROPERABILITY | YES | YES | YES |
| PERFORMANCE | NO | NO | YES |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sánchez del Monte, A.; Hernández-Álvarez, L. Analysis of Cyber-Intelligence Frameworks for AI Data Processing. Appl. Sci. 2023, 13, 9328. https://doi.org/10.3390/app13169328
Sánchez del Monte A, Hernández-Álvarez L. Analysis of Cyber-Intelligence Frameworks for AI Data Processing. Applied Sciences. 2023; 13(16):9328. https://doi.org/10.3390/app13169328
Chicago/Turabian StyleSánchez del Monte, Alberto, and Luis Hernández-Álvarez. 2023. "Analysis of Cyber-Intelligence Frameworks for AI Data Processing" Applied Sciences 13, no. 16: 9328. https://doi.org/10.3390/app13169328
APA StyleSánchez del Monte, A., & Hernández-Álvarez, L. (2023). Analysis of Cyber-Intelligence Frameworks for AI Data Processing. Applied Sciences, 13(16), 9328. https://doi.org/10.3390/app13169328






