Improving the IoT Attack Classification Mechanism with Data Augmentation for Generative Adversarial Networks
Abstract
:1. Introduction
2. Related Works
2.1. Network-Based IDS [1,4]
2.2. Host-Based IDS [5,6]
2.3. Deep Learning Classification
2.4. Generative Adversarial Network
2.5. Summary
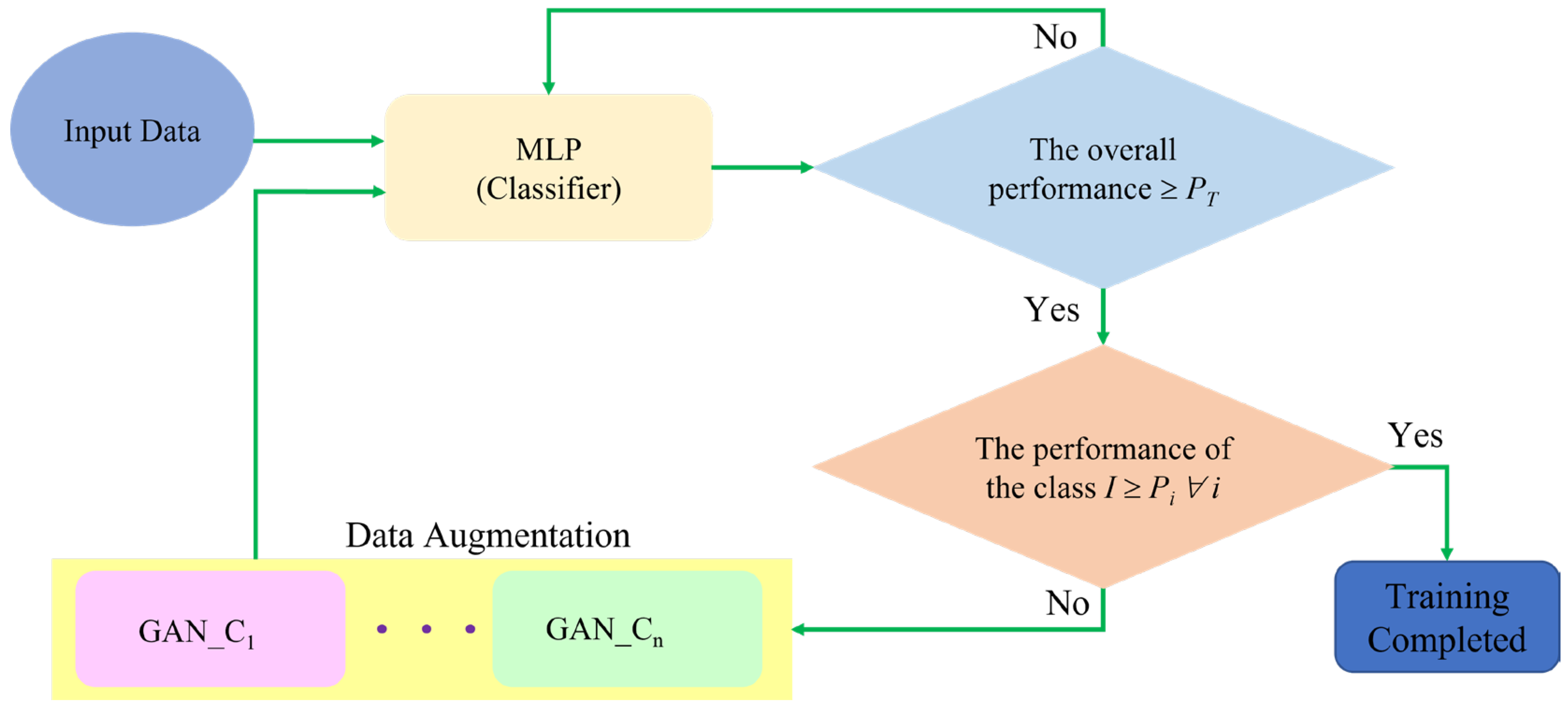
3. IoT Attack Classification Mechanism
3.1. Dataset Collection
- Denial of service (DoS) attack [1]: A DoS attack is a malicious attempt to disrupt the normal functioning of a network, system, or online service by overwhelming it with a flood of illegitimate traffic or requests. The primary objective of a DoS attack is to make the targeted resource unavailable to its intended users, causing a denial of service. The two key characteristics of DoS attacks are overloaded resources and various attack vectors. An overload of resources refers to DoS attacks that typically involve sending a large volume of traffic, data, or requests to the target system. This overwhelms the system’s capacity to handle incoming requests, causing it to become slow or unresponsive. A variety of attack vectors means that DoS attacks can take various forms, including flooding a network with traffic, sending a high number of connection requests, exploiting vulnerabilities in software, or depleting system resources like CPU, memory, or bandwidth;
- Distributed denial of service (DDoS) attack [1]: A DDoS attack is a type of cyberattack in which multiple compromised computers, often referred to as a botnet, are used to flood a target system, network, or service with a massive volume of traffic or requests, overwhelming its capacity, and causing a denial of service. DDoS attacks are a more sophisticated and powerful form of the basic denial of service (DoS) attack. DDoS attacks are more powerful and difficult to stop than DoS attacks and can cause long-term and severe service disruptions. Identifying DDoS attacks becomes more complex because attackers often use compromised systems from different locations;
- Reconnaissance attack [24]: A reconnaissance attack is the initial stage of a cyberattack in which an attacker gathers information about a target system, network, or organization. The primary objective of reconnaissance is to collect data that can be used to plan and launch a more focused and effective attack in the future. It is essentially the process of “scouting” or “surveying” the target to identify vulnerabilities and weaknesses. Reconnaissance serves as the basis for subsequent stages of a cyberattack, such as exploitation and intrusion. Armed with the knowledge gained during reconnaissance, attackers can tailor their attack strategies to maximize their chances of success. For this reason, organizations place a strong emphasis on detecting and mitigating reconnaissance activities as part of their cybersecurity measures. Common defense mechanisms include network monitoring, intrusion detection systems (IDS) [4], and security information and event management (SIEM) [27] solutions to spot and respond to suspicious reconnaissance attempts;
- Theft attack [24]: A theft attack is used to describe attempts by attackers to gain unauthorized access to confidential information belonging to others. This type of attack often involves various methods and techniques, including phishing, advanced persistent threats (APTs), malware, and other cyberattacks aimed at stealing sensitive data. Phishing attacks involve sending deceptive emails or messages that appear to come from trusted sources. These emails typically contain links or attachments designed to trick recipients into revealing sensitive information, such as login credentials or personal data. Advanced persistent threats (APTs) are long-term, sophisticated cyberattacks in which attackers gain unauthorized access to a network or system, often using advanced techniques to remain undetected. APTs are typically conducted by well-funded and motivated attackers who aim to steal valuable information over an extended period. Malicious software, including viruses, Trojans, spyware, and ransomware, can be used to compromise systems and steal data. Malware can be delivered by various means, including infected email attachments, malicious downloads, or compromised websites;
3.2. Data Pre-Processing
- Data cleaning: This substep will delete low-relevance feature IDs 1, 4, 6, 7, 17, and 19. For example, Feature ID 1 is the row identifier, and ID7 is the serial number of any starting value. Feature IDs 17, 18, and 19 are label fields. According to the needs of this paper, they are not used as input data. Only feature ID 18 is retained as a label field to evaluate classification performance. Feature IDs 4 and 6 are port numbers, which range from 1 to 65,535. However, attackers can set them arbitrarily without following the protocol specifications, so the relevance of this feature is low. To simplify the complexity, consider an environment where IPv4 is used at the network layer, and TCP or UDP is used at the transport layer. Therefore, the Address Resolution Protocol and the Internet Control Message Protocol in Feature ID 2 and IPv6 in Feature IDs 3 and 5 will not be included in the scope of this article;
- Data standardization [28,29]: This substep is mainly to reduce the complexity of model training and accelerate the convergence speed of the model to prevent problems such as gradient explosion during model training. Feature ID 2 uses the label encoding method to set Proto’s TCP and UDP to 0 and 1, respectively. Feature ID 18 also uses label encoding to set each class to a value from 1 to 5. Feature ID 18 also uses label encoding to set each class to a value from 1 to 5. After feature IDs 8 to 16 are normalized using Equation (4), their values will be in the [0, 1] interval. Note that the Xnorm is the normalization value of each feature; X is the original value of the current feature; Xmin is the minimum value of the feature field; and Xmax is the maximum value of the feature field;
- Functions ID 3 and ID 5 are IP addresses. Since an IP address is a combination of four sets of numbers, normalization directly will not effectively reflect this characteristic. Therefore, each number of the IP address is independently decomposed into a sub-feature, and each sub-feature is encoded in an 8-bit binary format. Therefore, there are a total of 64 features.
3.3. Classification Model Establishment
3.4. Classification Model Evaluation
- Accuracy (PAccuracy): To evaluate the proportion of correct predictions among all classification results;
- Precision (PPrecision): To evaluate the proportion of actual classifications that correctly predict a single classification result;
- Recall (PRecall): To evaluate the proportion of actual single classification results with correctly predicted classifications;
- F1-score (PF1-score): To evaluate the performance of the overall model, the sum of precision and recall is the average.
4. Experimental Results
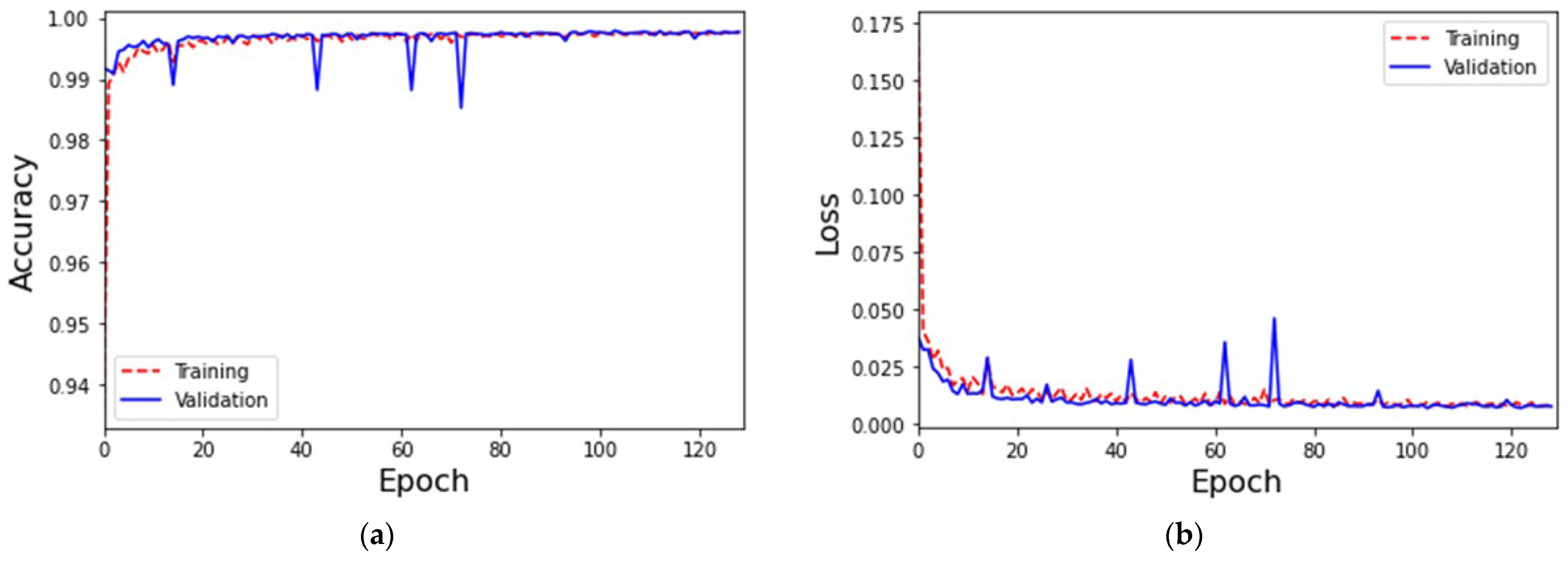
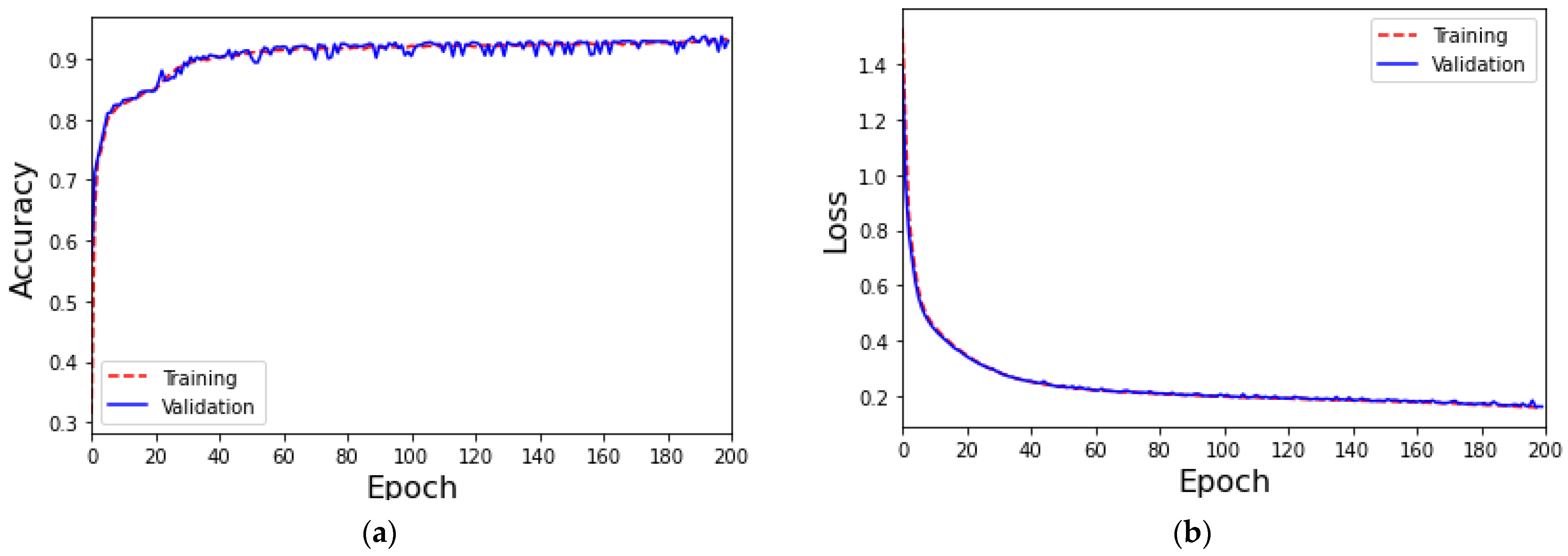
4.1. MLP-Based IoT Attack Classification Mechanism
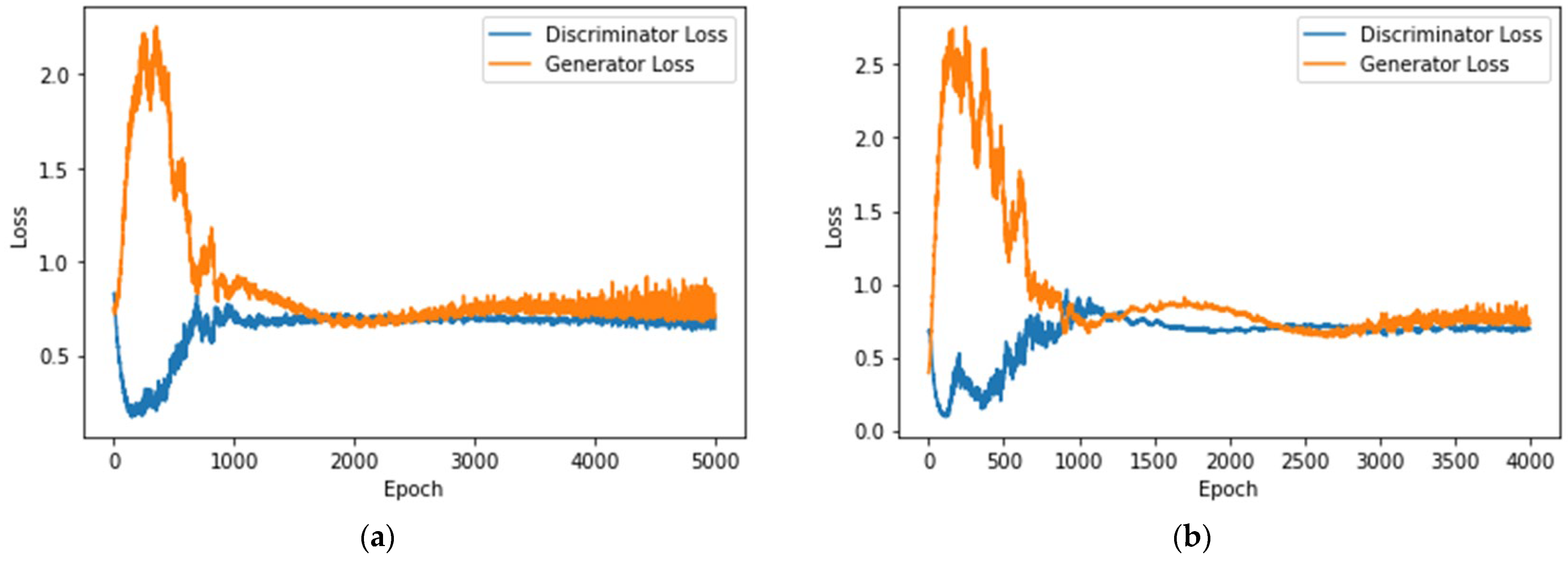
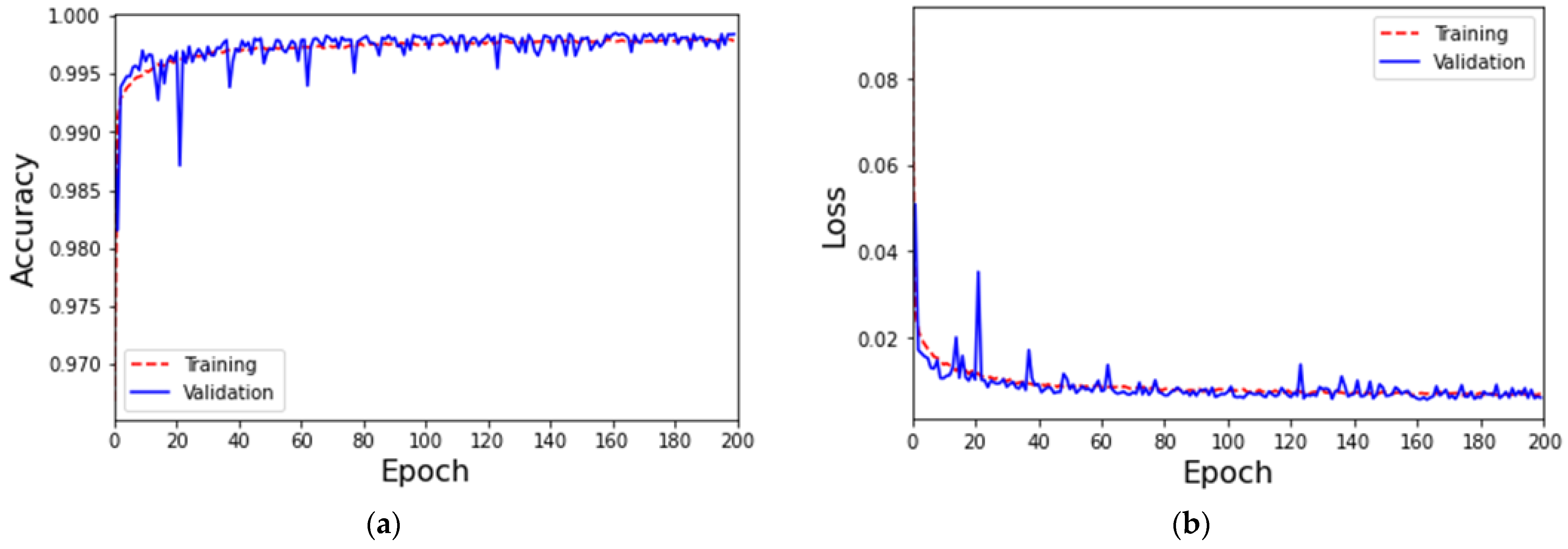
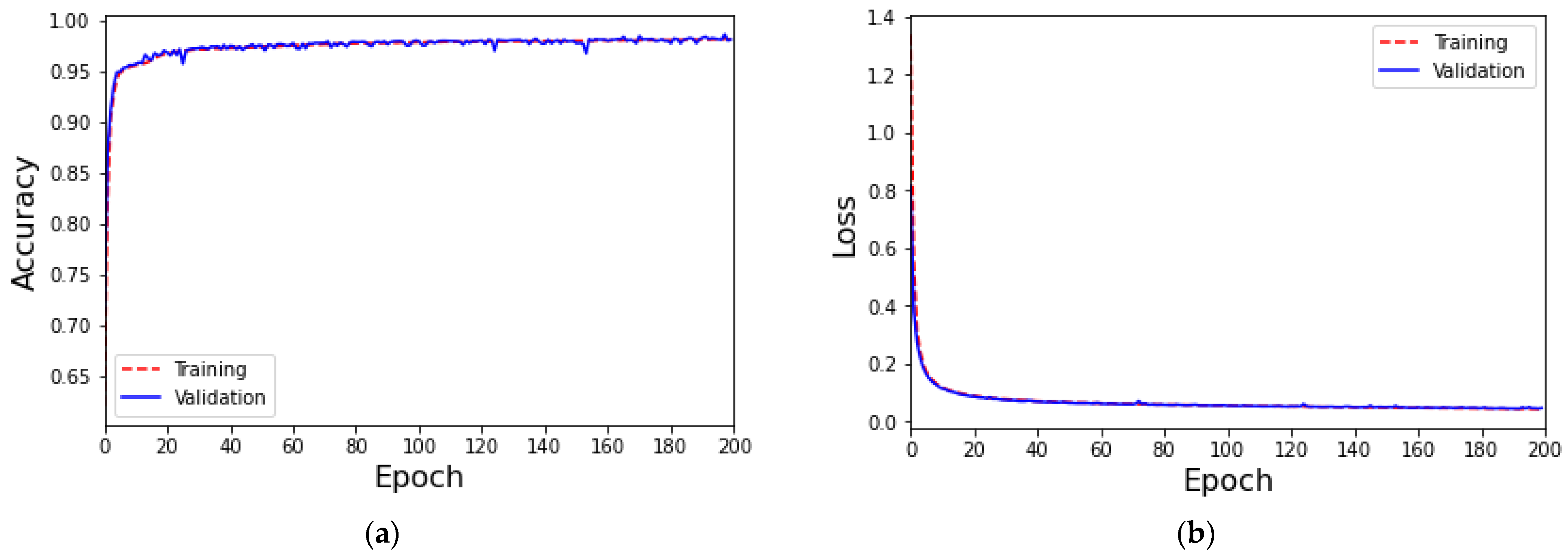
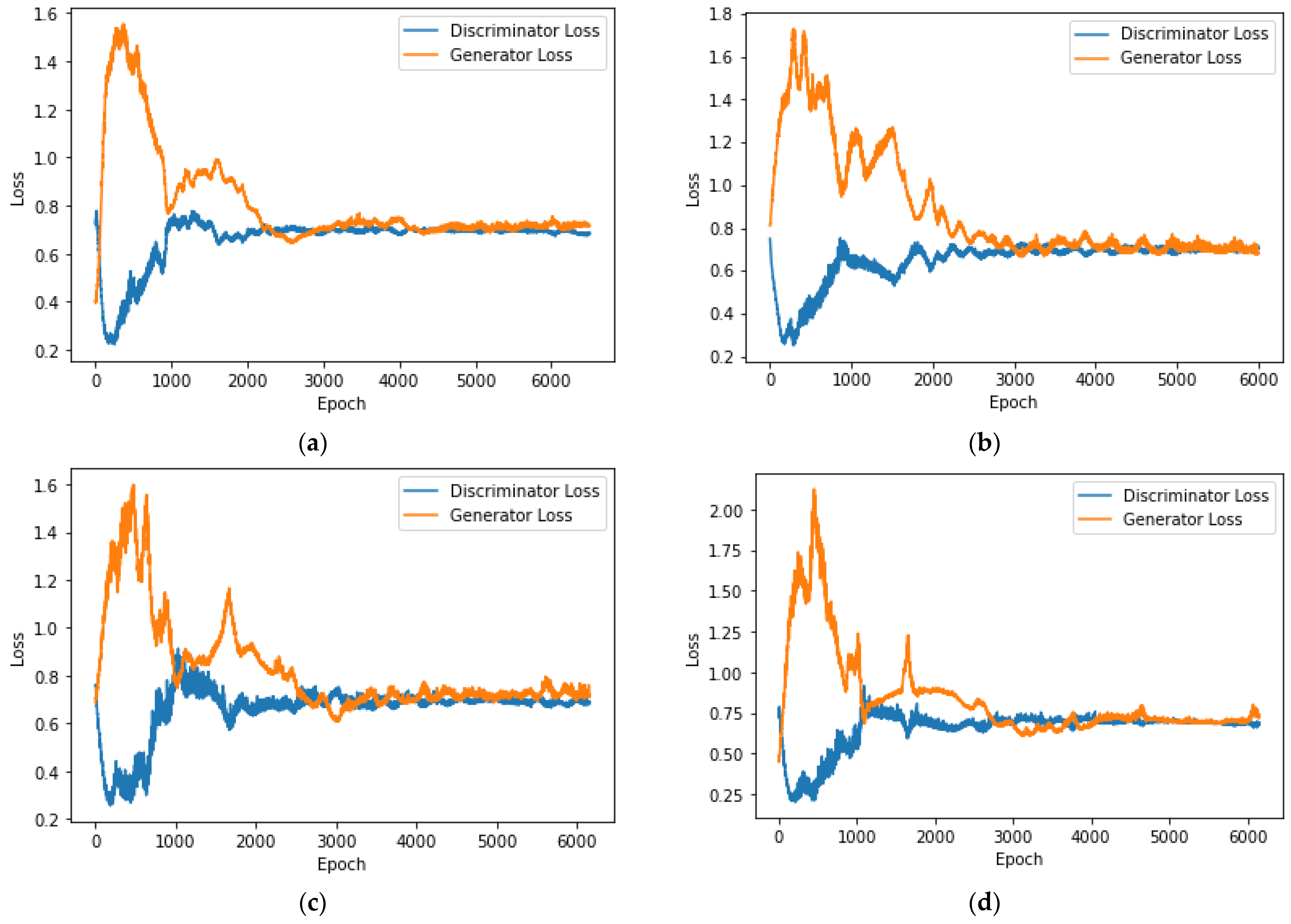
4.2. MLP-Based IoT Attack Classification with Data Augmentation for Generative Adversarial Networks
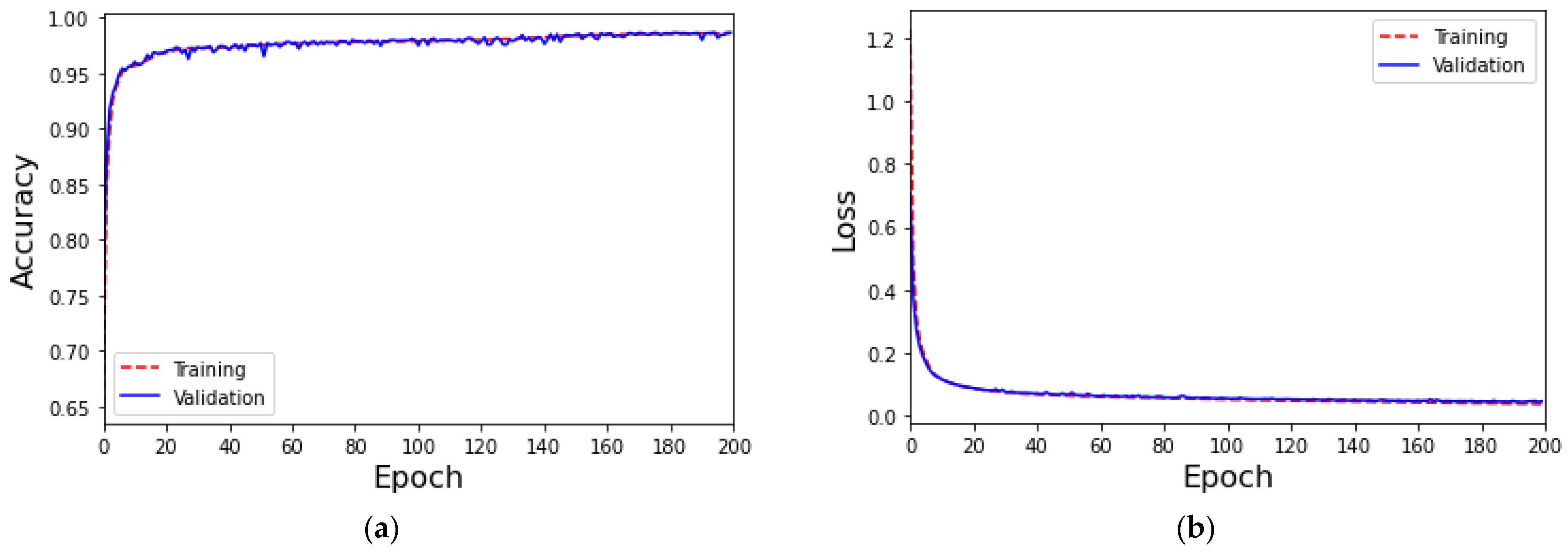
4.3. Validate Data Augmentation Mechanisms Using ToN-IoT Dataset
4.4. Comparison with Other Methods
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mishra, N.; Pandya, S. Internet of Things Applications, Security Challenges, Attacks, Intrusion Detection, and Future Visions: A Systematic Review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- State of IoT 2022: Number of Connected IoT Devices Growing 18% to 14.4 Billion Globally. Available online: https://iotbusinessnews.com/2022/05/19/70343-state-of-iot-2022-number-of-connected-iot-devices-growing-18-to-14-4-billion-globally (accessed on 20 July 2022).
- 2023 SonicWall Cyber Threat Report. Available online: https://www.sonicwall.com/2023-cyber-threat-report/ (accessed on 10 March 2023).
- Dini, P.; Elhanashi, A.; Begni, A.; Saponara, S.; Zheng, Q.; Gasmi, K. Overview on Intrusion Detection Systems Design Exploiting Machine Learning for Networking Cybersecurity. Appl. Sci. 2023, 13, 7507. [Google Scholar] [CrossRef]
- Martins, I.; Resende, J.S.; Sousa, P.R.; Silva, S.; Antunes, L.; Gama, J. Host-based IDS: A review and open issues of an anomaly detection system in IoT. Future Gener. Comput. Syst. 2022, 133, 95–113. [Google Scholar] [CrossRef]
- Tudor, D. What Is a Host Intrusion Detection System (HIDS) and How It Works. Available online: https://heimdalsecurity.com/blog/host-intrusion-detection-system-hids/ (accessed on 17 December 2021).
- Cil, A.E.; Yildiz, K.; Buldu, A. Detection of DDoS attacks with feed forward based deep neural network model. Expert Syst. Appl. 2021, 169, 114520. [Google Scholar] [CrossRef]
- Vishwakarma, M.; Kesswani, N. DIDS: A Deep Neural Network based real-time Intrusion detection system for IoT. Decis. Anal. J. 2022, 5, 100142. [Google Scholar] [CrossRef]
- Li, Y.; Xu, Y.; Liu, Z.; Hou, H.; Zheng, Y.; Xin, Y.; Zhao, Y.; Cui, L. Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 2020, 154, 107450. [Google Scholar] [CrossRef]
- Khan, M.A. HCRNNIDS: Hybrid Convolutional Recurrent Neural Network-Based Network Intrusion Detection System. Processes 2021, 9, 834. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. Design and development of a deep learning-based model for anomaly detection in IoT networks. IEEE Access 2021, 9, 103906–103926. [Google Scholar] [CrossRef]
- Tareq, I.; Elbagoury, B.M.; El-Regaily, S.; El-Horbaty, E.S.M. Analysis of ToN-IoT, UNW-NB15, and Edge-IIoT datasets using dl in cybersecurity for IoT. Appl. Sci. 2022, 12, 9572. [Google Scholar] [CrossRef]
- Yin, C.; Zhu, Y.; Fei, J.; He, X. A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 2017, 5, 21954–21961. [Google Scholar] [CrossRef]
- Zeeshan, M.; Riaz, Q.; Bilal, M.A.; Shahzad, M.K.; Jabeen, H.; Haider, S.A.; Rahim, A. Protocol-Based Deep Intrusion Detection for DoS and DDoS Attacks Using UNSW-NB15 and Bot-IoT Data-Sets. IEEE Access 2021, 10, 2269–2283. [Google Scholar] [CrossRef]
- Gaur, V.; Kumar, R. DDoSLSTM: Detection of Distributed Denial of Service Attacks on IoT Devices using LSTM Model. In Proceedings of the 2022 International Conference on Communication, Computing and Internet of Things (IC3IoT), Chennai, India, 10–11 March 2022; pp. 1–7. [Google Scholar]
- Rehman, S.U.; Khaliq, M.; Imtiaz, S.I.; Rasool, A.; Shafiq, M.; Javed, A.R.; Jalil, Z.; Bashir, A.K. DIDDOS: An approach for detection and identification of Distributed Denial of Service (DDoS) cyberattacks using Gated Recurrent Units (GRU). Future Gener. Comput. Syst. 2021, 118, 453–466. [Google Scholar] [CrossRef]
- Yao, W.; Hu, L.; Hou, Y.; Li, X. A Lightweight Intelligent Network Intrusion Detection System Using One-Class Autoencoder and Ensemble Learning for IoT. Sensors 2023, 23, 4141. [Google Scholar] [CrossRef]
- Zhang, H.; Zhang, B.; Huang, L.; Zhang, Z.; Huang, H. An Efficient Two-Stage Network Intrusion Detection System in the Internet of Things. Information 2023, 14, 77. [Google Scholar] [CrossRef]
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative Adversarial Nets. In Advances in Neural Information Processing Systems; Ghahramani, Z., Welling, M., Cortes, C., Lawrence, N., Weinberger, K.Q., Eds.; Neural Information Processing Systems Foundation, Inc.: La Jolla, CA, USA, 2014; pp. 2672–2680. [Google Scholar]
- Zixu, T.; Liyanage, K.S.K.; Gurusamy, M. Generative Adversarial Network and Auto Encoder based Anomaly Detection in Distributed IoT Networks. In Proceedings of the GLOBECOM 2020-2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–7. [Google Scholar]
- Ullah, I.; Mahmoud, Q.H. A Framework for Anomaly Detection in IoT Networks Using Conditional Generative Adversarial Networks. IEEE Access 2021, 9, 165907–165931. [Google Scholar] [CrossRef]
- Park, C.; Lee, J.; Kim, Y.; Park, J.G.; Kim, H.; Hong, D. An enhanced ai-based network intrusion detection system using generative adversarial networks. IEEE Internet Things J. 2022, 10, 2330–2345. [Google Scholar] [CrossRef]
- Chu, H.C.; Lin, Y.J. IoT Attack Classification Based on Generative Adversarial Networks. In Proceedings of the 6th IEEE International Conference on Knowledge Innovation and Invention, Sapporo, Japan, 11–13 August 2023. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Foundation, T.O. Node-Red: Low-Code Programming for Event-Driven Applications. Available online: https://nodered.org/ (accessed on 15 March 2022).
- Jekyll. Ostinato Traffic Generator for Network Engineers. Available online: https://ostinato.org/ (accessed on 16 March 2022).
- González-Granadillo, G.; González-Zarzosa, S.; Diaz, R. Security Information and Event Management (SIEM): Analysis, Trends, and Usage in Critical Infrastructures. Sensors 2021, 21, 4759. [Google Scholar] [CrossRef]
- Li, Z.; Usman, M.; Tao, R.; Xia, P.; Wang, C.; Chen, H.; Li, B. A systematic survey of regularization and normalization in GANs. ACM Comput. Surv. 2023, 55, 1–37. [Google Scholar] [CrossRef]
- Singh, D.; Singh, B. Investigating the impact of data normalization on classification performance. Appl. Soft Comput. 2020, 97, 105524. [Google Scholar] [CrossRef]
- Zhang, T.; Zhu, T.; Gao, K.; Zhou, W.; Philip, S.Y. Balancing learning model privacy, fairness, and accuracy with early stopping criteria. IEEE Trans. Neural Netw. Learn. Syst. 2021, 34, 5557–5569. [Google Scholar] [CrossRef]
- Chicco, D.; Jurman, G. The advantages of the Matthews correlation coefficient (MCC) over F1 score and accuracy in binary classification evaluation. BMC Genom. 2020, 21, 6. [Google Scholar] [CrossRef] [PubMed]
- Chicco, D.; Tötsch, N.; Jurman, G. The Matthews correlation coefficient (MCC) is more reliable than balanced accuracy, bookmaker informedness, and markedness in two-class confusion matrix evaluation. BioData Mining 2021, 14, 13. [Google Scholar] [CrossRef] [PubMed]
- Moustafa, N. A new distributed architecture for evaluating AI-based security systems at the edge: Network TON_IoT datasets. Sustain. Cities Soc. 2021, 72, 102994. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]


| Reference | Dataset | Method | Accuracy * | Remark |
|---|---|---|---|---|
| [7] | CIC DDoS 2019 | DNN | 94.57% (M) | Analyze the statistical characteristics of packet traffic |
| [8] | UNSW-NB15 BoT-IoT ToN-IoT CSE-CIC-IDS2018 | DNN | UNSW-NB15: 97.48% (M) BoT-IoT: 83.82% (M) ToN-IoT: 69.53% (M) CSE-CIC-IDS2018: 97.21% (M) | Multivariate classification of four datasets based on the DNN model |
| [9] | NSL-KDD | CNN | KDD Test+: 81.33% (M) KDD Test-21: 64.81% (M) KDD Test+: 86.95.33% (B) KDD Test-21: 76.37% (B) | The analysis is mainly based on four parts: Basic packet information Packet connection information Time-based network traffic statistics Host-based network traffic statistics |
| [10] | CSE-CIC-IDS2018 | CNN + RNN | 97.75% (B) | Use CNN to capture local features and RNN to capture temporal features of packets. |
| [11] | BoT-IoT IOT Network Intrusion MQTT-IOT-IDS2020 IOT-23 | CNN | 1D CNN: 99.74% (M) 2D CNN: 99.42% (M) 3D CNN: 99.03% (M) | All datasets are integrated into two new datasets, transfer learning concepts are used to change the network architecture of different CNNs, and detailed category analysis is performed on each dataset. |
| [12] | ToN-IoT Edge-IIoT UNSW-NB15 | DenseNet | ToN-IoT: 99.65 (M) Edge-IIoT: 94.94% (M) UNSW-NB15: 98.4% (M) | Based on the one-dimensional 1-D CNN in the DenseNet architecture and setting different window sizes for multivariate classification. |
| [13] | NSL-KDD | RNN | 83.28% (B) 81.29% (M) | Set different layers based on the RNN model to evaluate the effectiveness of the model in classification. |
| [14] | UNSW-NB15 BoT-IoT | LSTM*2 | 96.3% (B) | Based on the two datasets, the DDoS and DoS attack categories of the TCP protocol are captured and merged into new data, and the output is alert, DDoS, and DoS. |
| [15] | CIC DDoS-2019 | LSTM LSTM*2 | LSTM: 99.46% (B) LSTM: 99.16% (M) | Based on different LSTM layers, the impact of binary classification and multivariate classification is analyzed. |
| [16] | CIC DDoS-2019 | GRU | 99.7% (M) | Analyze different DDoS attack categories based on GRU. |
| [17] | WSN-DS UNSW-NB15 KDD CUP99 | GRU | WSN-DS: 97.91% (B) UNSW-NB15: 98.92% (B) KDD CUP99: 98.23% (B) | Zero-day attack binary classification analysis based on bidirectional GRU analysis. |
| [18] | CSE-CIC-IDS2018 | LightGBM + CNN | 99.896% (M) | LightGBM: binary classification of categories. CNN: First perform IR-SMOTE on the data to balance the categories of the multivariate classification. |
| [20] | BoT-IoT | GANs + AE | AE: 92.97% (B) AE + GAN: 97.11% (B) | Anomaly detection is based on the merger of GANs and AE. |
| [21] | KDD99 NSL-KDD BoT-IoT IOT Network Intrusion MQTT-IOT-IDS2020 MQTT set IOT-23 | CGANs + FNN | KDD99: 95.90% (M) NSL-KDD: 95.46% (M) BoT-IoT: 77.01% (M) IOT Network Intrusion: 79.21% (M) MQTT-IOT-IDS2020: 93.40 (M) MQTT set: 97.30% (M) IOT-23: 64.17% (M) | Based on the CGAN architecture, data augmentation of imbalanced data is performed, and then FNN is used for multivariate classification. |
| [22] | USNW-NB15 NSL-KDD CTU-IoT Real-word data | WGAN + DNN WGAN + CNN WGAN + LSTM DNN + AE CNN + AE | USNW NB15: 87% (M) NSL-KDD: 93.2% (M) | GSNs based on Wasserstein distance are used to improve imbalanced data and are used together with AE to analyze and evaluate the performance of each model. |
| [23] | BoT-IoT | GAN + MLP | 82.25% (M) | GAN-based methods can generate features similar to real data and compare them with MLP models in deep learning, reducing the training time of large amounts of data in the past. |
| Classes | Number of Records (Before) | Number of Records (After) |
|---|---|---|
| DoS | 1,320,148 | 1,320,098 |
| DDoS | 1,541,315 | 1,541,278 |
| Reconnaissance | 72,919 | 65,653 |
| Theft | 370 | 316 |
| Normal | 65 | 62 |
| ID | Feature | Description | ID | Feature | Description |
|---|---|---|---|---|---|
| 1 | pkSeqID | Row Identifier | 11 | state_number | Numerical representation of feature state |
| 2 | Proto | Textual representation of transaction protocols present in network flow | 12 | Mean | Average duration of aggregated records |
| 3 | Saddr | Source IP address | 13 | N_IN_Conn_P_DstIP | Number of inbound connections per destination IP. |
| 4 | Sport | Source port number | 14 | Drate | Destination-to-source packets per second |
| 5 | Daddr | Destination IP address | 15 | Srate | Source-to-destination packets per second |
| 6 | Dport | Destination port number | 16 | Max | Maximum duration of aggregated records |
| 7 | Seq | Argus sequence number | 17 | Attack | Class label: 0 for Normal traffic, 1 for Attack Traffic |
| 8 | Stddev | Standard deviation of aggregated records | 18 | Category | Traffic category |
| 9 | N_IN_Conn_P_SrcIP | Number of inbound connections per source IP | 19 | Subcategory | Traffic subcategory |
| 10 | Min | Minimum duration of aggregated records |
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| Input (Features) | 74 | Dense | 64, 64, 64 |
| Batch Size | 1024 | Dense Activation | LeakReLU |
| Epochs | 200 | Activation Value | 0.2 |
| Optimizer | Adam | Output Activation | Softmax |
| Learning Rate | 0.001, 0.5 | Output Activation Value | 5 |
| Loss Function | Sparse categorical cross-entropy |
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| Z | 100 | Loss Function | Binary cross-entropy |
| Input (Features) | 74 | Generator Dense | 256, 128, 64 |
| Batch Size | 64 | Generator Activation | LeakReLU |
| Epochs | 10,000 | Generator Activation Value | 0.2 |
| Optimizer | Adam | Generator Batch Normalization | 0.8 |
| Learning Rate | 0.002, 0.5 | Discriminator Dense | 64, 128, 256 |
| Classes | Precision | Recall | F1-Score |
|---|---|---|---|
| DoS | 100% | 100% | 100% |
| DDoS | 100% | 100% | 100% |
| Reconnaissance | 99.06% | 98.37% | 98.71% |
| Theft | 75.23% | 62.33% | 68.18% |
| Normal | 100% | 88.22% | 93.74% |
| Classes | Precision | Recall | F1-Score |
|---|---|---|---|
| DoS | 100% | 99% | 99.50% |
| DDoS | 100% | 100% | 100% |
| Reconnaissance | 96.06% | 94.73% | 95.39% |
| Theft | 92.22% | 90.69% | 91.45% |
| Normal | 99.81% | 92.07% | 95.78% |
| Classes | Number of Records |
|---|---|
| DoS | 20,000 |
| DDoS | 20,000 |
| Backdoor | 20,000 |
| Password | 20,000 |
| Scanning | 20,000 |
| Injection | 20,000 |
| Mitm | 985 |
| Normal | 289,827 |
| Ransomware | 19,901 |
| Xss | 20,000 |
| Classes | Precision | Recall | F1-Score |
|---|---|---|---|
| DoS | 94.28% | 93.23% | 93.75% |
| DDoS | 91.01% | 99% | 94.83% |
| Backdoor | 98.21% | 90.05% | 93.95% |
| Password | 100% | 100% | 100% |
| Scanning | 100% | 100% | 100% |
| Classes | Precision | Recall | F1-Score |
|---|---|---|---|
| DoS | 84.19% | 78.21% | 81.09% |
| DDoS | 80.02% | 97.06% | 87.72% |
| Backdoor | 100% | 100% | 100% |
| Password | 98.22% | 88.26% | 92.97% |
| Scanning | 100% | 99.53% | 99.76% |
| Injection | 100% | 99.23% | 99.61% |
| Mitm | 96.31% | 67.23% | 79.18% |
| Normal | 100% | 100% | 100% |
| Ransomware | 100% | 100% | 100% |
| Xss | 100% | 100% | 100% |
| Classes | Precision | Recall | F1-Score |
|---|---|---|---|
| DoS | 92.68% | 90.16% | 91.40% |
| DDoS | 93.27% | 96.26% | 94.74% |
| Backdoor | 100% | 100% | 100% |
| Password | 99.31% | 92.19% | 95.62% |
| Scanning | 98.12% | 97.26% | 97.69% |
| Injection | 100% | 99.23% | 99.61% |
| Mitm | 97.56% | 91.33% | 94.34% |
| Normal | 100% | 100% | 100% |
| Ransomware | 99.06% | 97.14% | 98.09% |
| Xss | 99.92% | 98.29% | 99.10% |
| Method | Dataset | Accuracy | Precision | Recall | F1-Score | Remark |
|---|---|---|---|---|---|---|
| GANs + AE [20] | BoT-IoT | 97.11% | 99.33% | 97.33% | 98.31% | Binary classification |
| CGANs + FNN [21] | BoT-IoT | 77.01% | 77.74% | 77.00% | 76.56% | Average of multivariate classification |
| Proposed | BoT-IoT | 98.83% | 97.62% | 95.30% | 96.42% | Average of multivariate classification |
| DNN [8] | ToN-IoT | 69.53% | 56.84% | 69.53% | 61.96% | Average of multivariate classification |
| Proposed | ToN-IoT | 98.53% | 97.99% | 97.99% | 97.36% | Average of multivariate classification |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chu, H.-C.; Lin, Y.-J. Improving the IoT Attack Classification Mechanism with Data Augmentation for Generative Adversarial Networks. Appl. Sci. 2023, 13, 12592. https://doi.org/10.3390/app132312592
Chu H-C, Lin Y-J. Improving the IoT Attack Classification Mechanism with Data Augmentation for Generative Adversarial Networks. Applied Sciences. 2023; 13(23):12592. https://doi.org/10.3390/app132312592
Chicago/Turabian StyleChu, Hung-Chi, and Yu-Jhe Lin. 2023. "Improving the IoT Attack Classification Mechanism with Data Augmentation for Generative Adversarial Networks" Applied Sciences 13, no. 23: 12592. https://doi.org/10.3390/app132312592
APA StyleChu, H.-C., & Lin, Y.-J. (2023). Improving the IoT Attack Classification Mechanism with Data Augmentation for Generative Adversarial Networks. Applied Sciences, 13(23), 12592. https://doi.org/10.3390/app132312592







