Bell-State-Exchange-Parity-Based Protocol for Efficient Autocompensation of Quantum Key Distribution Encoded in Polarization or Spatial Modes
Abstract
:1. Introduction
2. BBM92 Protocol in 2D Subspace Fiber Encodings
2.1. Bell States for BBM92 Protocol
2.2. Perturbations in Quantum Light States
2.3. The Autocompensation Problem
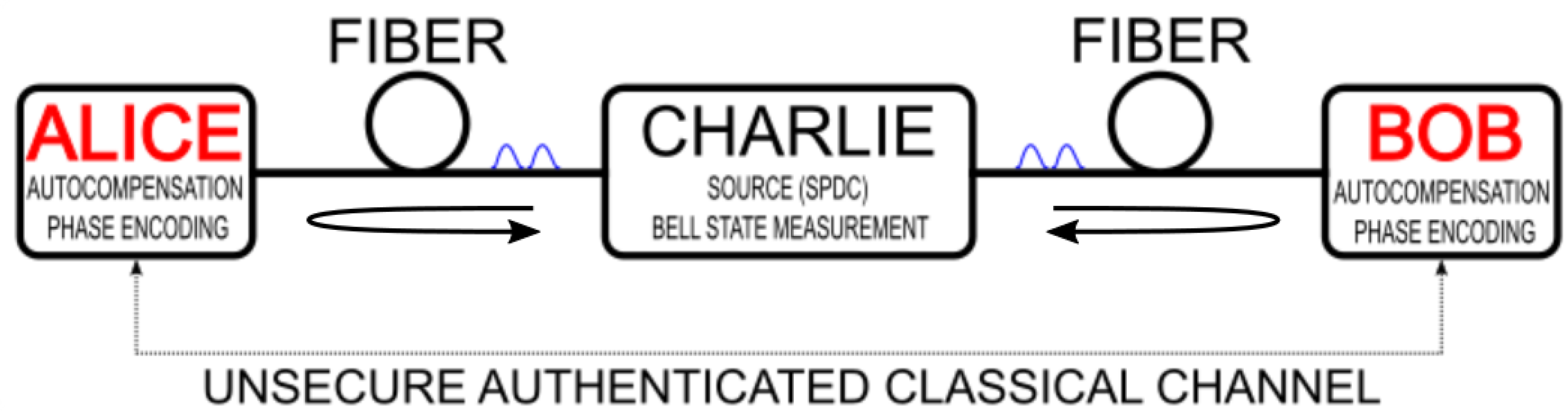
3. Bell State Exchange Parity Protocol and Intrinsic Autocompensation
3.1. BSEP Protocol with Polarization Modes
3.2. Autocompensating BSEP Protocol with Polarization Modes
3.3. Autocompensating BSEP Protocol with Spatial Modes
- For collinear modes , for example, HG modes, we use an arrangement of Dove prisms (DPs) rotated suitably, that is, DP, to implement the autocompensating matrix . The arrangement of DPs, as shown in Figure 4c, is as follows: First, we have DP, that is, a DP with its normal forming an angle equal to 0 with respect to direction Y, producing a phase retarder , that is, implementing a Z transformation. Next, we have a DP implementing a -X transformation; therefore, the total transformation is as required. We must stress that cylindrical lens converters (CLCs) can also be used. A CLC is formed by two cylindrical lenses separated by an appropriate distance in such a way that introduces a selective Gouy phase in each spatial direction and therefore a relative phase between modes. For HG modes, the design is quite simple [38,39]; however, for other type of modes, the design becomes more complex.
- For the case of codirectional modes, counter-circulation of the modes plus a -phase on one of them is enough to produce the desired autocompensating transformation , as indicated in Figure 4b; that is, it can be implemented by using two optical circulators and an isotropic -phase shifter.
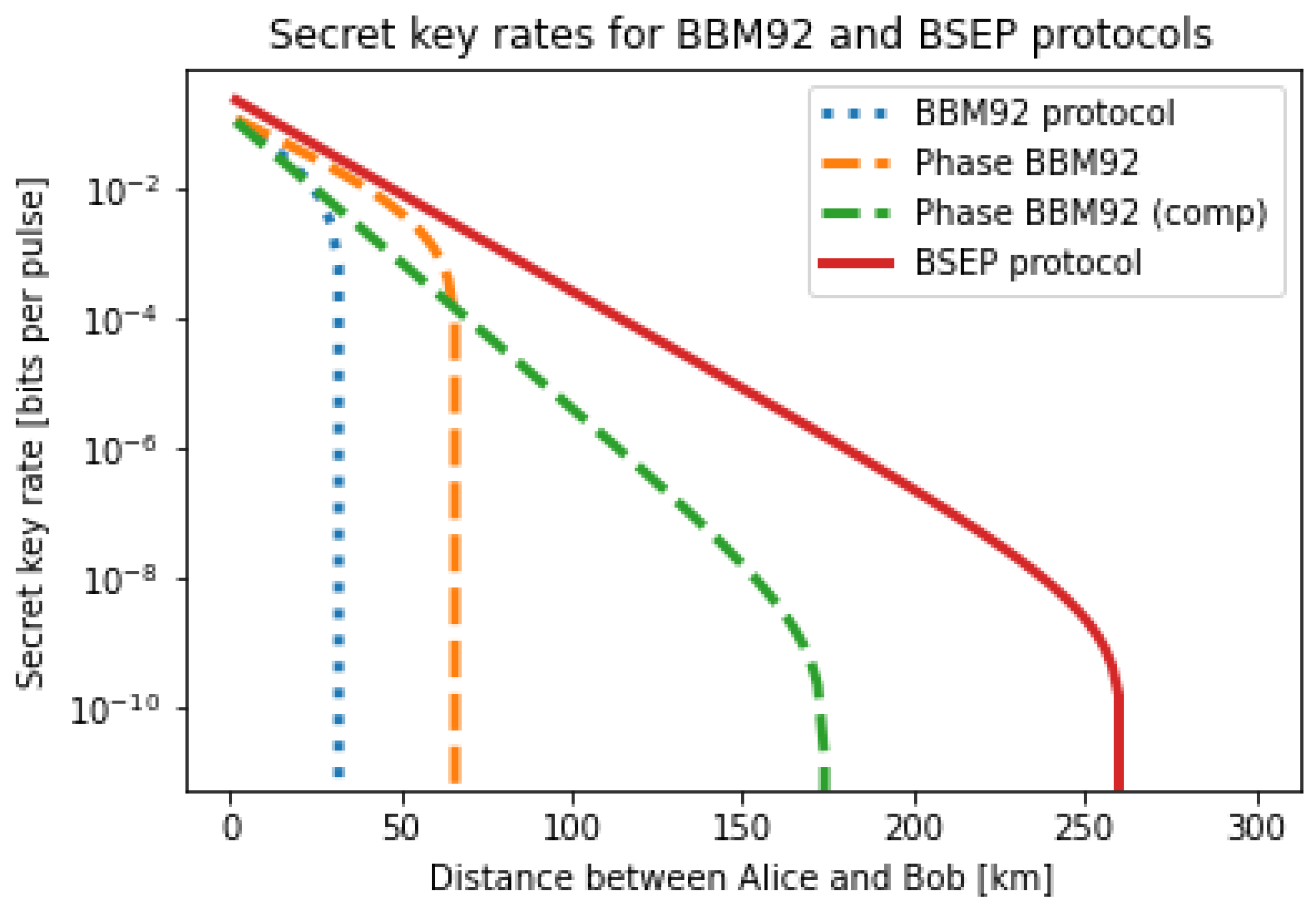
4. Performance Comparison between Protocols
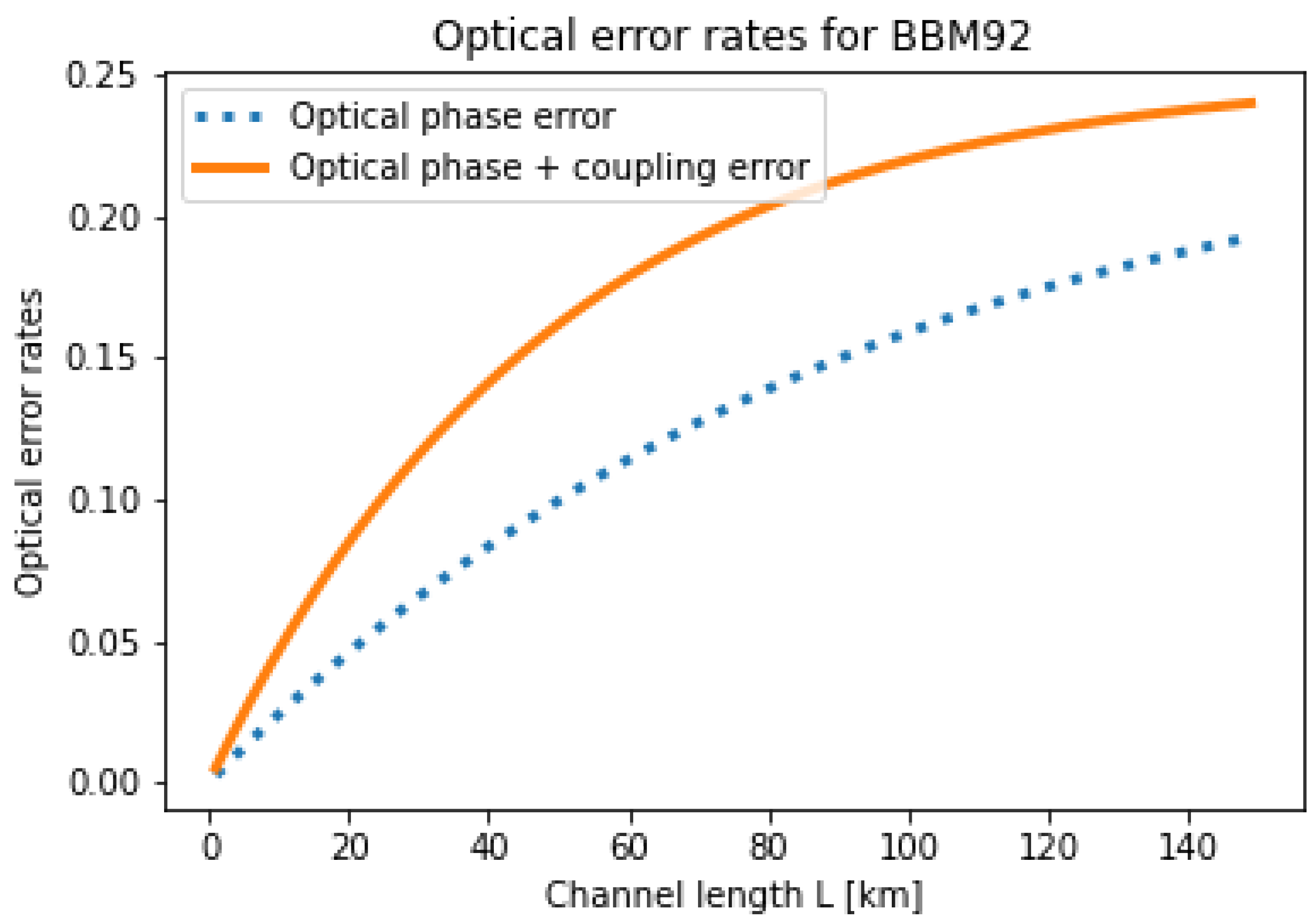
4.1. Optical Perturbation Statistics
4.2. Simplified Security Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| BS | Beam Splitter |
| BSEP | Bell State Exchange Parity |
| CLC | Cylindrical Lens Converter |
| DC | Directional Coupler |
| DP | Dove Prism |
| MCF | Multicore Optical Fiber |
| MDI | Measurement Device Independent |
| MZI | Mach–Zehnder Interferometer |
| PBS | Polarizing Beam Splitter |
| Probability Distribution Function | |
| PM | Phase Modulator |
| QKD | Quantum Key Distribution |
| RDC | Reconfigurable Directional Coupler |
| SMF | Single-Mode Fiber |
| SPDC | Spontaneous Parametric Down-Conversion |
References
- Saitoh, K.; Matsuo, S. Multicore Fiber Technology. J. Light. Technol. 2016, 34, 55–66. [Google Scholar] [CrossRef]
- Berdagué, S.; Facq, P. Mode division multiplexing in optical fibers. Appl. Opt. 1982, 21, 1950–1955. [Google Scholar] [CrossRef] [PubMed]
- Sillard, P.; Bigot-Astruc, M.; Molin, D. Few-Mode Fibers for Mode-Division-Multiplexed Systems. J. Light. Technol. 2014, 32, 2824–2829. [Google Scholar] [CrossRef]
- Shor, P. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145–195. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photon. 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Kelly, S.P.; Poschinger, U.; Schmidt-Kaler, F.; Fisher, M.P.A.; Marino, J. Coherence requirements for quantum communication from hybrid circuit dynamics. arXiv 2023, arXiv:2210.11547. [Google Scholar]
- Bashir, A.I. Quantum coherence-assisted secure communication of internet of things information via Landau-quantized graphene. Opt. Quantum Electron. 2023, 55, 983. [Google Scholar] [CrossRef]
- Xavier, G.B.; Lima, G. Quantum information processing with space-division multiplexing optical fibres. Commun. Phys. 2020, 3, 9. [Google Scholar] [CrossRef]
- Boosting Subsea Cables with Multi-Core Fiber Technology. Available online: https://cloud.google.com/blog/products/infrastructure/delivering-multi-core-fiber-technology-in-subsea-cables (accessed on 13 September 2023).
- Takeshita, H.; Nakamura, K.; Matsuo, Y.; Inoue, T.; Masuda, D.; Hiwatashi, T.; Hosokawa, K.; Inada, Y.; de Gabory, E.L.T. First Demonstration of Uncoupled 4-Core Multicore Fiber in a Submarine Cable Prototype with Integrated Multicore EDFA. In Proceedings of the Optical Fiber Communication Conference (OFC) 2022, San Diego, CA, USA, 6–10 March 2022; p. M4B.1. [Google Scholar] [CrossRef]
- Muller, A.; Herzog, T.; Huttner, B.; Tittel, W.; Zbinden, H.; Gisin, N. “Plug and play” systems for quantum cryptography. Appl. Phys. Lett. 1997, 70, 793–795. [Google Scholar] [CrossRef]
- Bethune, D.S.; Risk, W.P. Autocompensating quantum cryptography. New J. Phys. 2002, 4, 42. [Google Scholar] [CrossRef]
- Balado, D.; Liñares, J.; Prieto-Blanco, X.; Barral, D. Phase and polarization autocompensating N-dimensional quantum cryptography in multicore optical fibers. J. Opt. Soc. Am. B 2019, 36, 2793–2803. [Google Scholar] [CrossRef]
- Liñares, J.; Prieto-Blanco, X.; Balado, D.; Carral, G.M. Fully autocompensating high-dimensional quantum cryptography by quantum degenerate four-wave mixing. Phys. Rev. A 2021, 103, 043710. [Google Scholar] [CrossRef]
- Zapatero, V.; Wang, W.; Curty, M. A fully passive transmitter for decoy-state quantum key distribution. Quantum Sci. Technol. 2023, 8, 025014. [Google Scholar] [CrossRef]
- Ma, X.; Fung, C.H.F.; Lo, H.K. Quantum key distribution with entangled photon sources. Phys. Rev. A 2007, 76, 012307. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G.; Mermin, N.D. Quantum cryptography without Bell’s theorem. Phys. Rev. Lett. 1992, 68, 557–559. [Google Scholar] [CrossRef] [PubMed]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-Device-Independent Quantum Key Distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [PubMed]
- Ma, X.; Razavi, M. Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A 2012, 86, 062319. [Google Scholar] [CrossRef]
- Liñares, J.; Carral, G.M.; Prieto-Blanco, X.; Balado, D. Autocompensating measurement-device-independent quantum cryptography in space division multiplexing optical fibers. J. Eur. Opt. Soc. Rapid Publ. 2021, 17, 19. [Google Scholar] [CrossRef]
- Park, C.H.; Woo, M.K.; Park, B.K.; Lee, M.S.; Kim, Y.S.; Cho, Y.W.; Kim, S.; Han, S.W.; Moon, S. Practical Plug-and-Play Measurement-Device-Independent Quantum Key Distribution With Polarization Division Multiplexing. IEEE Access 2018, 6, 58587–58593. [Google Scholar] [CrossRef]
- Hu, M.; Zhang, L.; Guo, B.; Li, J. Polarization-based plug-and-play measurement-device-independent quantum key distribution. Opt. Quantum Electron. 2019, 51, 22. [Google Scholar] [CrossRef]
- Fung, C.H.F.; Qi, B.; Tamaki, K.; Lo, H.K. Phase-remapping attack in practical quantum-key-distribution systems. Phys. Rev. A 2007, 75, 032314. [Google Scholar] [CrossRef]
- Yang, Y.; Gao, J.; Fu, S.; Zhang, X.; Tang, M.; Tong, W.; Liu, D. PANDA Type Four-Core Fiber With the Efficient Use of Stress Rods. IEEE Photonics J. 2019, 11, 1–9. [Google Scholar] [CrossRef]
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661–663. [Google Scholar] [CrossRef] [PubMed]
- Bennet, C.H.; Brassard, G. Quantum Cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Kwiat, P.G.; Waks, E.; White, A.G.; Appelbaum, I.; Eberhard, P.H. Ultrabright source of polarization-entangled photons. Phys. Rev. A 1999, 60, R773–R776. [Google Scholar] [CrossRef]
- Liñares, J.; Prieto-Blanco, X.; Moreno, V.; Montero-Orille, C.; Mouriz, D.; Nistal, M.C.; Barral, D. Interferometric space-mode multiplexing based on binary phase plates and refractive phase shifters. Opt. Express 2017, 25, 10925–10938. [Google Scholar] [CrossRef] [PubMed]
- Understanding the Haar Measure. Available online: https://pennylane.ai/qml/demos/tutorial_haar_measure.html#understanding-the-haar-measure (accessed on 19 April 2023).
- Wang, X.B.; Yu, Z.W.; Hu, X.L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 2018, 98, 062323. [Google Scholar] [CrossRef]
- Mattle, K.; Weinfurter, H.; Kwiat, P.G.; Zeilinger, A. Dense Coding in Experimental Quantum Communication. Phys. Rev. Lett. 1996, 76, 4656–4659. [Google Scholar] [CrossRef]
- Weihs, G.; Zeilinger, A. Photon Statistics at Beam Splitters: An Essential Tool in Quantum Information and Teleportation; 2001. Available online: https://api.semanticscholar.org/CorpusID:174794052 (accessed on 9 October 2023).
- Wu, W.; Zhou, G.; Zhao, Y.; Zhang, H. New Quantum Private Comparison Protocol Without a Third Party. Int. J. Theor. Phys. 2020, 59, 1866–1875. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.B.; Chang, Y.; Hou, M.; Cheng, W. Efficient Quantum Private Comparison Based on Entanglement Swapping of Bell States. Int. J. Theor. Phys. 2021, 60, 3783–3796. [Google Scholar] [CrossRef]
- Martinelli, M. A universal compensator for polarization changes induced by birefringence on a retracing beam. Opt. Commun. 1989, 72, 341–344. [Google Scholar] [CrossRef]
- Bhandari, R. A useful generalization of the Martinelli effect. Opt. Commun. 1992, 88, 1–5. [Google Scholar] [CrossRef]
- Beijersbergen, M.; Allen, L.; van der Veen, H.; Woerdman, J. Astigmatic laser mode converters and transfer of orbital angular momentum. Opt. Commun. 1993, 96, 123–132. [Google Scholar] [CrossRef]
- Liñares, J.; Prieto-Blanco, X.; Montero-Orille, C.; Moreno, V. Spatial mode multiplexing/demultiplexing by Gouy phase interferometry. Opt. Lett. 2017, 42, 93–96. [Google Scholar] [CrossRef] [PubMed]
- Dellantonio, L.; Sorensen, A.S.; Bacco, D. High-dimensional measurement-device-independent quantum key distribution on two-dimensional subspaces. Phys. Rev. A 2018, 98, 062301. [Google Scholar] [CrossRef]
- Ng, K.; Nazarov, V.; Kuchinsky, S.; Zakharian, A.; Li, M.J. Analysis of Crosstalk in Multicore Fibers: Statistical Distributions and Analytical Expressions. Photonics 2023, 10, 174. [Google Scholar] [CrossRef]
- Goodman, J.W. Statistical Optics/Joseph W. Goodman, 2nd ed.; Wiley series in pure and applied optics; John Wiley and Sons Inc.: Hoboken, NJ, USA, 2015. [Google Scholar]
- Imai, T.; Matsumoto, T. Polarization fluctuations in a single-mode optical fiber. J. Light. Technol. 1988, 6, 1366–1375. [Google Scholar] [CrossRef]
- Puttnam, B.J.; Luís, R.S.; Rademacher, G.; Alfredsson, A.; Klaus, W.; Sakaguchi, J.; Awaji, Y.; Agrell, E.; Wada, N. Characteristics of homogeneous multi-core fibers for SDM transmission. APL Photonics 2018, 4, 022804. [Google Scholar] [CrossRef]
- Gottesman, D.; Lo, H.K.; Lutkenhaus, N.; Preskill, J. Security of quantum key distribution with imperfect devices. In Proceedings of the International Symposium on Information Theory, ISIT 2004, Chicago, IL, USA, 27 June–2 July 2004; p. 136. [Google Scholar] [CrossRef]
- Ursin, R.; Tiefenbacher, F.; Schmitt-Manderbach, T.; Weier, H.; Scheidl, T.; Lindenthal, M.; Blauensteiner, B.; Jennewein, T.; Perdigues, J.; Trojek, P.; et al. Entanglement-based quantum communication over 144 km. Nat.Phys. 2007, 3, 481–486. [Google Scholar] [CrossRef]
- Lütkenhaus, N. Security against individual attacks for realistic quantum key distribution. Phys. Rev. A 2000, 61, 052304. [Google Scholar] [CrossRef]
- Jain, N.; Stiller, B.; Khan, I.; Elser, D.; Marquardt, C.; Leuchs, G. Attacks on practical quantum key distribution systems (and how to prevent them). Contemp. Phys. 2016, 57, 366–387. [Google Scholar] [CrossRef]
- Zapatero, V.; van Leent, T.; Arnon-Friedman, R.; Liu, W.Z.; Zhang, Q.; Weinfurter, H.; Curty, M. Advances in device-independent quantum key distribution. npj Quantum Inf. 2023, 9, 10. [Google Scholar] [CrossRef]



| Basis | Alice’s Outcome | Bob’s Outcome | Bit Agreement |
|---|---|---|---|
| Z | H | V | Correct (bit = 0) |
| Z | H | H | Error |
| Z | V | V | Correct (bit = 1) |
| Z | V | H | Error |
| X | + | + | Correct (bit = 0) |
| X | + | − | Error |
| X | − | − | Correct (bit = 1) |
| X | − | + | Error |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Carral, G.M.; Liñares, J.; Mateo, E.F.; Prieto-Blanco, X. Bell-State-Exchange-Parity-Based Protocol for Efficient Autocompensation of Quantum Key Distribution Encoded in Polarization or Spatial Modes. Appl. Sci. 2023, 13, 12907. https://doi.org/10.3390/app132312907
Carral GM, Liñares J, Mateo EF, Prieto-Blanco X. Bell-State-Exchange-Parity-Based Protocol for Efficient Autocompensation of Quantum Key Distribution Encoded in Polarization or Spatial Modes. Applied Sciences. 2023; 13(23):12907. https://doi.org/10.3390/app132312907
Chicago/Turabian StyleCarral, Gabriel M., Jesús Liñares, Eduardo F. Mateo, and Xesús Prieto-Blanco. 2023. "Bell-State-Exchange-Parity-Based Protocol for Efficient Autocompensation of Quantum Key Distribution Encoded in Polarization or Spatial Modes" Applied Sciences 13, no. 23: 12907. https://doi.org/10.3390/app132312907
APA StyleCarral, G. M., Liñares, J., Mateo, E. F., & Prieto-Blanco, X. (2023). Bell-State-Exchange-Parity-Based Protocol for Efficient Autocompensation of Quantum Key Distribution Encoded in Polarization or Spatial Modes. Applied Sciences, 13(23), 12907. https://doi.org/10.3390/app132312907








