A Real-Time Hybrid Approach to Combat In-Browser Cryptojacking Malware
Abstract
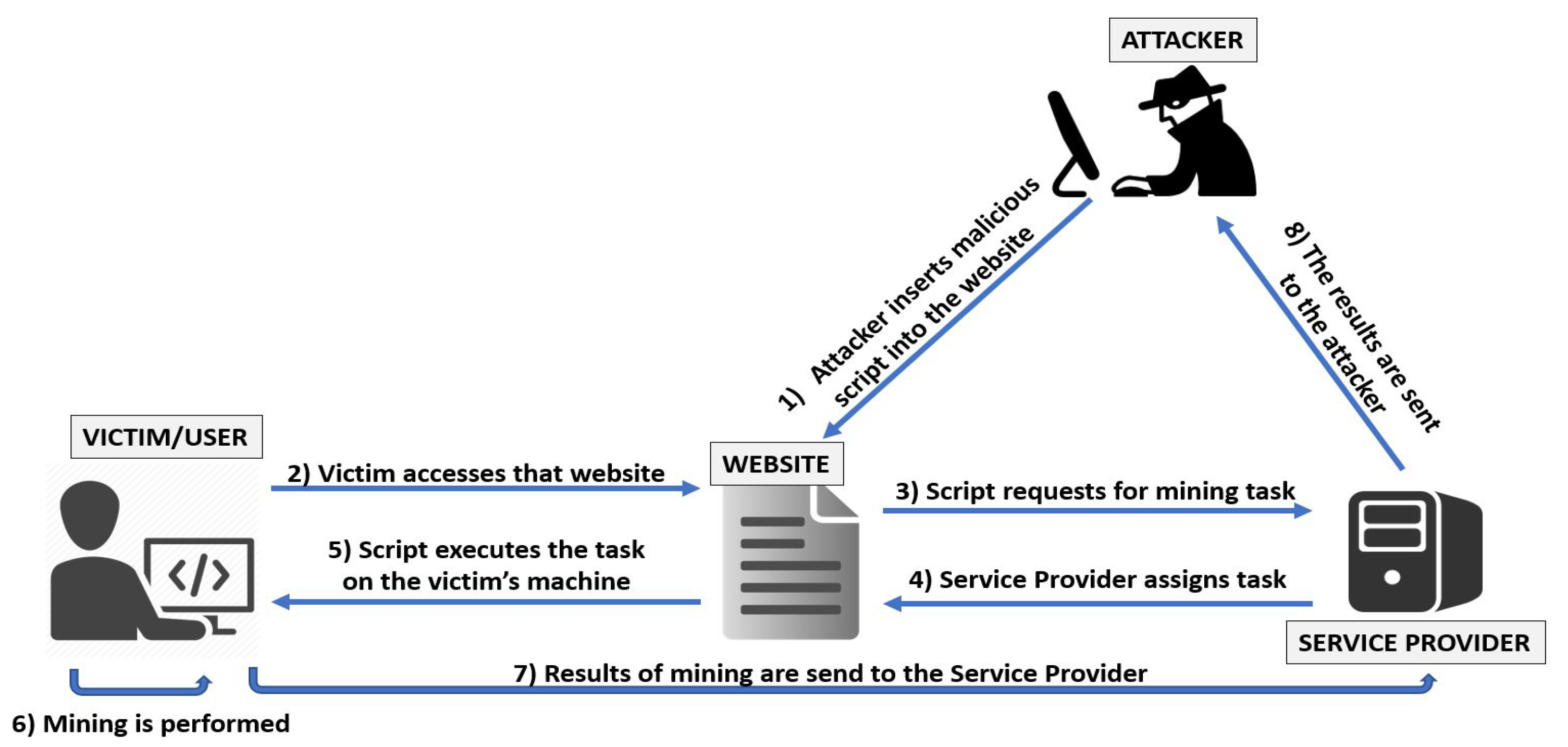
:1. Introduction
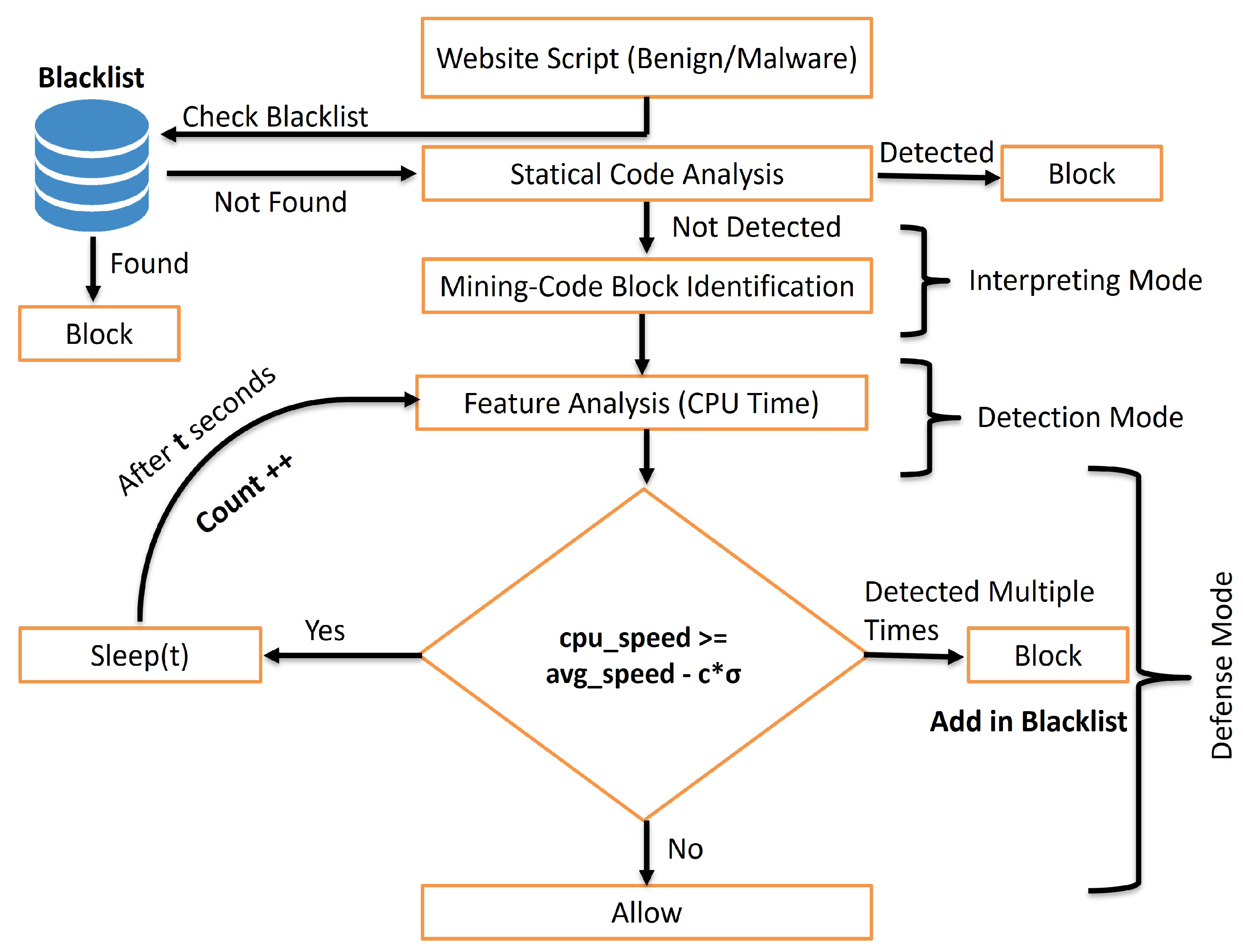
- The proposal of a novel hybrid approach—combining blacklisting detection (as the 1st), signature-based detection (as the 2nd), and a dynamic approach (as the 3rd) defensive layer.
- The advancement of the state of the art in terms of the detection accuracy (from 97% to 99.6%).
- An extension of the malware protection to non-WASM cryptojacking.
2. Literature Review
2.1. Static Approaches
2.2. Dynamic Approaches
2.3. Hybrid Approaches
| Ref. No | Approach | Dataset | Features | Prevention Method | Result |
|---|---|---|---|---|---|
| [15] | Static | Alexa: 33k | JS API consumption of resources | N/A | TPR: 95.95% |
| [16] | Alexa 1 Million | WASM signatures | N/A | ||
| [19] | Dynamic | PublicWWW | Images frames of cryptojacking | Accuracy: 98.97 % | |
| [20] | Alexa 1 Million | Web socket training | N/A | ||
| [21] | Network Traffic (Stratum) | Network’s metadata | Recall: 91 % | ||
| [22] | Alexa 1 Million | CPU usage | N/A | ||
| [23] | Memory of Browser (1160 snapshots) | Stack features, heap snapshots | Precision: 95% | ||
| [24] | N/A | Network features | TPR: 92% | ||
| [18] | Alexa: 100k | CPU memory | Accuracy: 97% | ||
| [25] | N/A | Hardware cache events | Precision: 97.9% | ||
| [26] | Manually created dataset (420 instances) | HPC values | Precision: 100% | ||
| [27] | Alexa: 1 M | CPU and WASM based | N/A | ||
| [28] | Alexa: 600,000 | JavaScript execution/compilation | TPR: 97.9% | ||
| [29] | Alexa: 100,000 | Hashes based | TPR: 100% | ||
| [30] | Alexa: 500 | WASM | F1 score: 98% | ||
| [33] | Hybrid | Alexa 8000, 8156 samples from Coinhive, etc. | Network traffic, CPU speed, subprocesses | F1 score: 99.25% | |
| [34] | 1200 samples | CPU features and HPC | Precision: 96% | ||
| [10] | PublicWWW | CPU usage, code analysis | Notification | N/A | |
| [11] | In-browser cryptojacking samples | Blacklist behavior | Kills the process | N/A | |
| [12] | Alexa 1 M | Code analysis + CPU usage | Suspension of process | FNR 1.83% FPR 0% |
3. Proposed Approach
4. Implementation Details
4.1. Datasets
4.2. Evaluation Metrics
- (1)
- Accuracy:
- (2)
- False Positive Rate:
- (3)
- False Negative Rate:
5. Experimental Evaluation
5.1. Performance Evaluation
5.2. Discussion
Comparison with the State of the Art
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. [Google Scholar]
- Sakas, D.P.; Giannakopoulos, N.T.; Reklitis, D.P.; Dasaklis, T.K. The Effects of Cryptocurrency Trading Websites on Airlines’ Advertisement Campaigns. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 3099–3119. [Google Scholar] [CrossRef]
- Number of Cryptocoins. Available online: https://coinmarketcap.com/ (accessed on 31 May 2022).
- Dospinescu, O.; Caramangiu, M.E. The Key Success Factors for an M-Learning Cryptocurrency Application. Inform. Econ. 2018, 22, 14–24. [Google Scholar] [CrossRef]
- Mestiri, H.; Barraj, I.; Alsir Mohamed, A.; Machhout, M. An efficient AES 32-bit architecture resistant to fault attacks. Comput. Mater. Contin. 2022, 70, 3667–3683. [Google Scholar] [CrossRef]
- Saad, M.; Khormali, A.; Mohaisen, A. Dine and dash: Static, dynamic, and economic analysis of in-browser cryptojacking. In Proceedings of the APWG Symposium on Electronic Crime Research (eCrime), Pittsburgh, PA, USA, 13–15 November 2019; pp. 1–12. [Google Scholar]
- Pastrana, S.; Suarez-Tangil, G. A first look at the crypto-mining malware ecosystem: A decade of unrestricted wealth. In Proceedings of the Internet Measurement Conference, Amsterdam, The Netherlands, 21–23 October 2019; pp. 73–86. [Google Scholar]
- Jayasinghe, K.; Poravi, G. A survey of attack instances of cryptojacking targeting cloud infrastructure. In Proceedings of the 2nd Asia Pacific Information Technology Conference, Bali Island, Indonesia, 17–19 January 2020; pp. 100–107. [Google Scholar]
- Darabian, H.; Homayounoot, S.; Dehghantanha, A.; Hashemi, S.; Karimipour, H.; Parizi, R.M.; Choo, K.K.R. Detecting cryptomining malware: A deep learning approach for static and dynamic analysis. J. Grid Comput. 2020, 18, 293–303. [Google Scholar] [CrossRef]
- Yulianto, A.D.; Sukarno, P.; Warrdana, A.A.; Makky, M.A. Mitigation of Cryptojacking Attacks Using Taint Analysis. In Proceedings of the 4th International Conference on Information Technology, Information Systems and Electrical Engineering (ICITISEE), Yogyakarta, Indonesia, 20–21 November 2019; pp. 234–238. [Google Scholar] [CrossRef]
- Razali, M.A.; Mohd Shariff, S. CMBlock: In-Browser Detection and Prevention Cryptojacking Tool Using Blacklist and Behavior-Based Detection Method. In Proceedings of the Advances in Visual Informatics, Bangi, Malaysia, 19–21 November 2019; Badioze Zaman, H., Smeaton, A.F., Shih, T.K., Velastin, S., Terutoshi, T., Mohamad Ali, N., Ahmad, M.N., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 404–414. [Google Scholar]
- Bian, W.; Meng, W.; Zhang, M. MineThrottle: Defending against Wasm In-Browser Cryptojacking. In Proceedings of the Web Conference, WWW ’20, Taipei, Taiwan, 20–24 April 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 3112–3118. [Google Scholar] [CrossRef]
- WebAssembly-Language. Available online: https://webassembly.org/ (accessed on 31 May 2022).
- Tekiner, E.; Acar, A.; Uluagac, A.S.; Kirda, E.; Selcuk, A.A. SoK: Cryptojacking Malware, 2021. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy (EuroS&P), Vienna, Austria, 6–20 September 2021. [Google Scholar]
- Rodriguez, J.D.P.; Posegga, J. RAPID: Resource and API-Based Detection Against In-Browser Miners. In Proceedings of the 34th Annual Computer Security Applications Conference, ACSAC ’18, San Juan, PR, USA, 3–7 December 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 313–326. [Google Scholar] [CrossRef]
- Rüth, J.; Zimmermann, T.; Wolsing, K.; Hohlfeld, O. Digging into Browser-Based Crypto Mining. In Proceedings of the Internet Measurement Conference, IMC ’18, Boston, MA, USA, 31 October–2 November 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 70–76. [Google Scholar] [CrossRef]
- Monero. Available online: https://www.getmonero.org/ (accessed on 31 May 2022).
- Kelton, C.; Balasubramanian, A.; Raghavendra, R.; Srivatsa, M. Browser-Based Deep Behavioral Detection of Web Cryptomining with CoinSpy. In Proceedings of the 27th Annual Network and Distributed System Security Symposium, NDSS, San Diego, CA, USA, 23–26 February 2020; pp. 23–26. [Google Scholar]
- Naseem, F.; Aris, A.; Babun, L.; Tekiner, E.; Uluagac, S. MINOS: A lightweight real-time cryptojacking detection system. In Proceedings of the 28th Annual Network and Distributed System Security Symposium, NDSS, Virtual, 21–25 February 2021. [Google Scholar]
- Rauchberger, J.; Schrittwieser, S.; Dam, T.; Luh, R.; Buhov, D.; Pötzelsberger, G.; Kim, H. The Other Side of the Coin: A Framework for Detecting and Analyzing Web-Based Cryptocurrency Mining Campaigns. In Proceedings of the 13th International Conference on Availability, Reliability and Security, ARES, Hamburg, Germany, 27–30 August 2018; Association for Computing Machinery: New York, NY, USA, 2018. [Google Scholar] [CrossRef]
- i Muñoz, J.Z.; Suárez-Varela, J.; Barlet-Ros, P. Detecting cryptocurrency miners with NetFlow/IPFIX network measurements. In Proceedings of the IEEE International Symposium on Measurements & Networking (M&N), Catania, Italy, 8–10 July 2019; pp. 1–6. [Google Scholar]
- Musch, M.; Wressnegger, C.; Johns, M.; Rieck, K. Thieves in the Browser: Web-Based Cryptojacking in the Wild. In Proceedings of the 14th International Conference on Availability, Reliability and Security, ARES ’19, Canterbury, UK, 26–29 August 2019; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Liu, J.; Zhao, Z.; Cui, X.; Wang, Z.; Liu, Q. A Novel Approach for Detecting Browser-Based Silent Miner. In Proceedings of the IEEE Third International Conference on Data Science in Cyberspace (DSC), Guangzhou, China, 18–21 June 2018; pp. 490–497. [Google Scholar]
- Caprolu, M.; Raponi, S.; Oligeri, G.; Pietro, R.D. Crypto Mining Makes Noise. arXiv 2019, arXiv:1910.09272. [Google Scholar]
- Gangwal, A.; Piazzetta, S.G.; Lain, G.; Conti, M. Detecting Covert Cryptomining using HPC. In Proceedings of the Cryptology and Network Security: 19th International Conference, CANS 2020, Vienna, Austria, 14–16 December 2020; pp. 344–364. [Google Scholar]
- Tahir, R.; Durrani, S.; Ahmed, F.; Saeed, H.; Zaffar, F.; Ilyas, S. The Browsers Strike Back: Countering Cryptojacking and Parasitic Miners on the Web. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 703–711. [Google Scholar] [CrossRef]
- Konoth, R.K.; Vineti, E.; Moonsamy, V.; Lindorfer, M.; Kruegel, C.; Bos, H.; Vigna, G. MineSweeper: An In-Depth Look into Drive-by Cryptocurrency Mining and Its Defense. In Proceedings of the CCS ‘18: 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1714–1730. [Google Scholar] [CrossRef]
- Kharraz, A.; Ma, Z.; Murley, P.; Lever, C.; Mason, J.; Miller, A.; Borisov, N.; Antonakakis, M.; Bailey, M. Outguard: Detecting In-Browser Covert Cryptocurrency Mining in the Wild. In Proceedings of the The World Wide Web Conference, WWW ’19, San Francisco, CA, USA, 13–17 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 840–852. [Google Scholar] [CrossRef]
- Hong, G.; Yang, Z.; Yang, S.; Zhang, L.; Nan, Y.; Zhang, Z.; Yang, M.; Zhang, Y.; Qian, Z.; Duan, H. How You Get Shot in the Back: A Systematical Study about Cryptojacking in the Real World. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, CCS ’18, Toronto, ON, Canada, 15–19 October 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1701–1713. [Google Scholar] [CrossRef]
- Wang, W.; Ferrell, B.; Xu, X.; Hamlen, K.W.; Hao, S. SEISMIC: SEcure In-lined Script Monitors for Interrupting Cryptojacks. In Proceedings of the Computer Security, Barcelona, Spain, 3–7 September 2018; Lopez, J., Zhou, J., Soriano, M., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 122–142. [Google Scholar]
- Sivaraju, S. An Insight into Deep Learning based Cryptojacking Detection Model. J. Trends Comput. Sci. Smart Technol. 2022, 4, 175–184. [Google Scholar] [CrossRef]
- Ying, Q.; Yu, Y.; Tian, D.; Jia, X.; Ma, R.; Hu, C. CJSpector: A Novel Cryptojacking Detection Method Using Hardware Trace and Deep Learning. J. Grid Comput. 2022, 20, 31. [Google Scholar] [CrossRef]
- Hernandez-Suarez, A.; Sanchez-Perez, G.; Toscano-Medina, L.K.; Olivares-Mercado, J.; Portillo-Portilo, J.; Avalos, J.G.; García Villalba, L.J. Detecting Cryptojacking Web Threats: An Approach with Autoencoders and Deep Dense Neural Networks. Appl. Sci. 2022, 12, 3234. [Google Scholar] [CrossRef]
- Mani, G.; Pasumarti, V.; Bhargava, B.; Vora, F.; MacDonald, J.; King, J.; Kobes, J. DeCrypto Pro: Deep Learning Based Cryptomining Malware Detection Using Performance Counters. In Proceedings of the IEEE International Conference on Autonomic Computing and Self-Organizing Systems (ACSOS), Washington, DC, USA, 17–21 August 2020; IEEE Computer Society: Los Alamitos, CA, USA, 2020; pp. 109–118. [Google Scholar] [CrossRef]
- Long Short-Term Memory. Available online: https://en.wikipedia.org/wiki/Long_short-term_memory (accessed on 31 May 2022).
- Coinhive. Available online: https://krebsonsecurity.com/2018/03/who-and-what-is-coinhive/ (accessed on 31 May 2022).
- Metrics. Available online: https://onlineconfusionmatrix.com/ (accessed on 31 May 2022).
- Alexa. Available online: https://www.alexa.com/ (accessed on 31 May 2022).
- PublicWWW. Available online: https://publicwww.com/ (accessed on 31 May 2022).



| S. No | URL | Service Provider | Keyword |
|---|---|---|---|
| 0 | rugbysearch.co.za | jsecoin | load.jsecoin.com |
| 1 | czh72.com | nerohut | nerohut.com/srv |
| 2 | raffey-cassidy.com | jsecoin | load.jsecoin.com |
| 3 | school-shop.su | coinhive | coinhive.min.js |
| 4 | 247iphone.co.uk | authedmine | authedmine.min.js |
| 5 | myweedmarket.com | coinhive | coinhive.min.js |
| 6 | viralrugby.com | coinimp | client.start |
| 7 | mistressalanaaradia.com | coinhive | coinhive.min.js |
| 8 | greenheartoc.com | coinhive | coinhive.min.js |
| 9 | intellegration.com | coinimp | client.start |
| 10 | my-shopping-list.de | authedmine | authedmine.min.js |
| 11 | arcadianlandscape.com | coinimp | client.start |
| 12 | ifixxxx.com | coinhive | coinhive.min.js |
| 13 | sto-avtomix.ru | monerise | monerisepaymentaddress |
| 14 | dnd5spells.rpgist.net | coinimp | client.start |
| 15 | tabforcancer.com | coinhive | coinhive.min.js |
| 16 | onkoliki.com | coinhive | coinhive.min.js |
| 17 | tildrakizumab.de | coinhive | coinhive.min.js |
| 18 | 9-journal.com | coinhive | coinhive.min.js |
| 19 | niftybuzz.com | jsecoin | load.jsecoin.com |
| 20 | fhkwindowsanddoor.com | browsermine | bmst.pw |
| S. No | Service Providers | Keywords |
|---|---|---|
| 1 | coinimp | client.start |
| 2 | coinhive | coinhive.min.js |
| 3 | jsecoin | load.jsecoin.com |
| 4 | cryptoloot | CRLT.Anonymous( |
| 5 | webminepool | WMP.Anonymous( |
| 6 | browsermine | bmst.pw |
| 7 | wpmonerominer | wp-monero-miner |
| 8 | nerohut | nerohut.com/srv |
| 9 | webminerpool | webmr.js |
| 10 | coinhave | cdn.minescripts.info |
| 11 | deepminer | deepMiner.Anonymous |
| 12 | monerise | monerisepaymentaddress |
| 13 | webmine | webmine.cz |
| 14 | coinnebula | CoinNebula |
| S. No | Metrics | Values |
|---|---|---|
| 1 | Accuracy | 99.6% |
| 2 | False Positive Rate | 0% |
| 3 | False Negative Rate | 13.3% |
| S. No | Website | WASM/Non-WASM | Blacklisting Technique | Signature-Based Technique | Total Static Analysis | Dynamic Analysis | Percentage Increase |
|---|---|---|---|---|---|---|---|
| 1 | http://beerthievery.com | Non-WASM | 0.0023 | 0.04626 | 0.04884 | 1.042 | 4.68% |
| 2 | http://www.rotoglow.com/ | Non-WASM | 0.00161 | 0.10990 | 0.11167 | 1.034 | 10.7% |
| 3 | https://www.dailypaws.com/cats-kittens/cat-names/most-popular-cat-names-2021 | Non-WASM | 0.001683 | 0.06111 | 0.06384 | 2.714 | 2.35% |
| 4 | https://wasm4.org/play/lingword/ | WASM | 0.001579 | 0.08252 | 0.08528 | 1.176 | 7.25% |
| 5 | https://secure.imvu.com/ | WASM | 0.001496 | 0.13784 | 0.13984 | 1.379 | 10.1% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan Abbasi, M.H.; Ullah, S.; Ahmad, T.; Buriro, A. A Real-Time Hybrid Approach to Combat In-Browser Cryptojacking Malware. Appl. Sci. 2023, 13, 2039. https://doi.org/10.3390/app13042039
Khan Abbasi MH, Ullah S, Ahmad T, Buriro A. A Real-Time Hybrid Approach to Combat In-Browser Cryptojacking Malware. Applied Sciences. 2023; 13(4):2039. https://doi.org/10.3390/app13042039
Chicago/Turabian StyleKhan Abbasi, Muhammad Haris, Subhan Ullah, Tahir Ahmad, and Attaullah Buriro. 2023. "A Real-Time Hybrid Approach to Combat In-Browser Cryptojacking Malware" Applied Sciences 13, no. 4: 2039. https://doi.org/10.3390/app13042039
APA StyleKhan Abbasi, M. H., Ullah, S., Ahmad, T., & Buriro, A. (2023). A Real-Time Hybrid Approach to Combat In-Browser Cryptojacking Malware. Applied Sciences, 13(4), 2039. https://doi.org/10.3390/app13042039








