Evaluation and Improvement of Internet Printing Protocol Based on HCPN Model Detection Method
Abstract
:1. Introduction
- It provides the current status of job processing (pages currently being printed) and more detailed information (such as querying completed and canceled jobs);
- The IEEE-ISTO Printer Working Group (PWG) is responsible for standardization. Using the protocol, we can strengthen the control of authentication/authorization, the encryption of transmitted data, access level, and other security-related options;
- With the latest developments of the IPP standard (“IPP Everywhere [2]”), driver-less printing is possible.
2. Preliminary Knowledge
2.1. Internet Printing Protocol
2.2. The Dolev–Yao Adversary Model
- Eavesdropping on all messages in the network;
- Block and intercept all messages in the network;
- Storing intercepted or self-created messages;
- Forge and send messages based on stored messages;
- Participate in the operation of the agreement as a legal agreement entity.
2.3. Petri Nets
2.4. CPN Tools
3. Establishment of HCPN Model for IPP Authentication Process
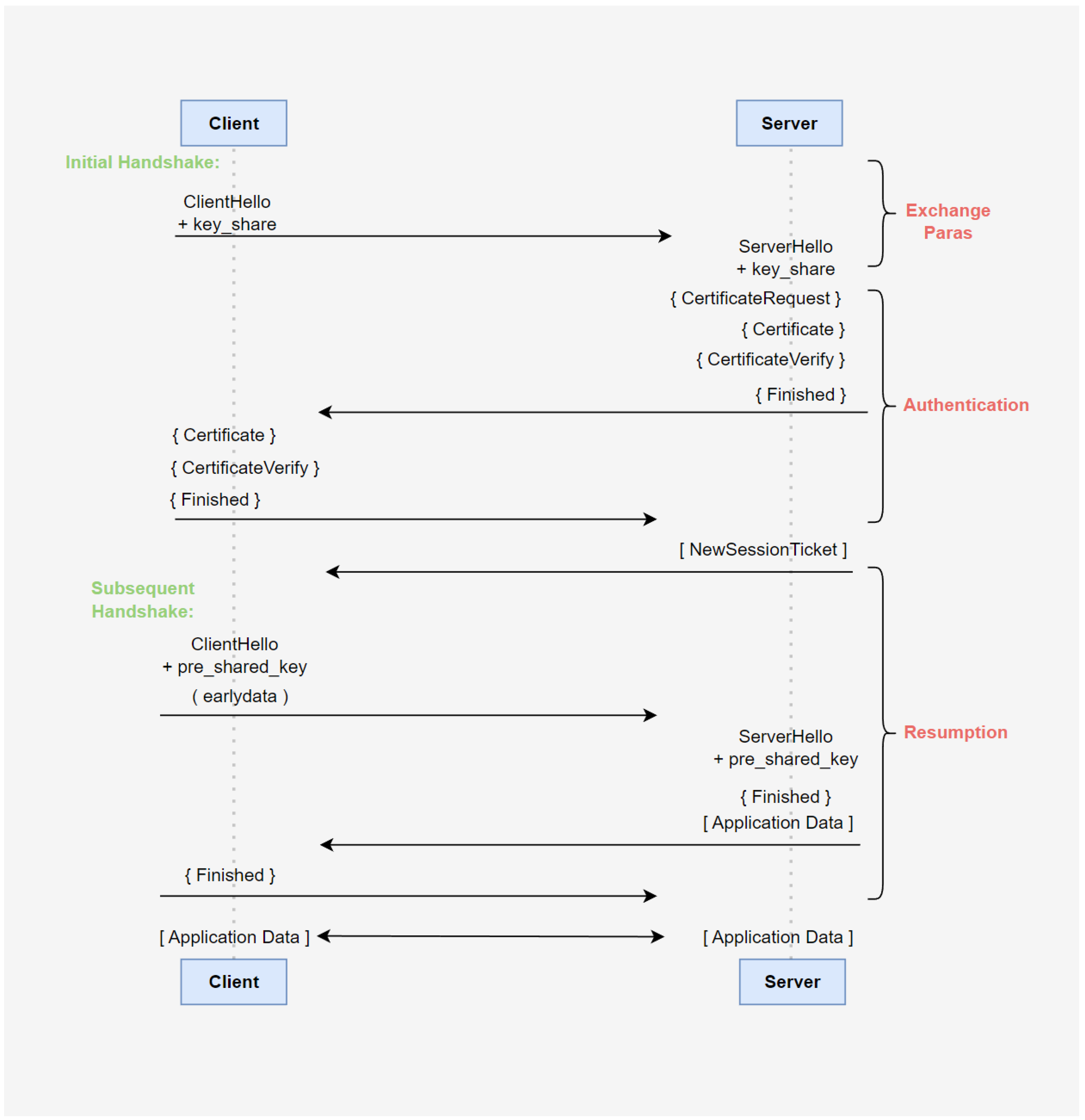
3.1. Authentication Message Flow
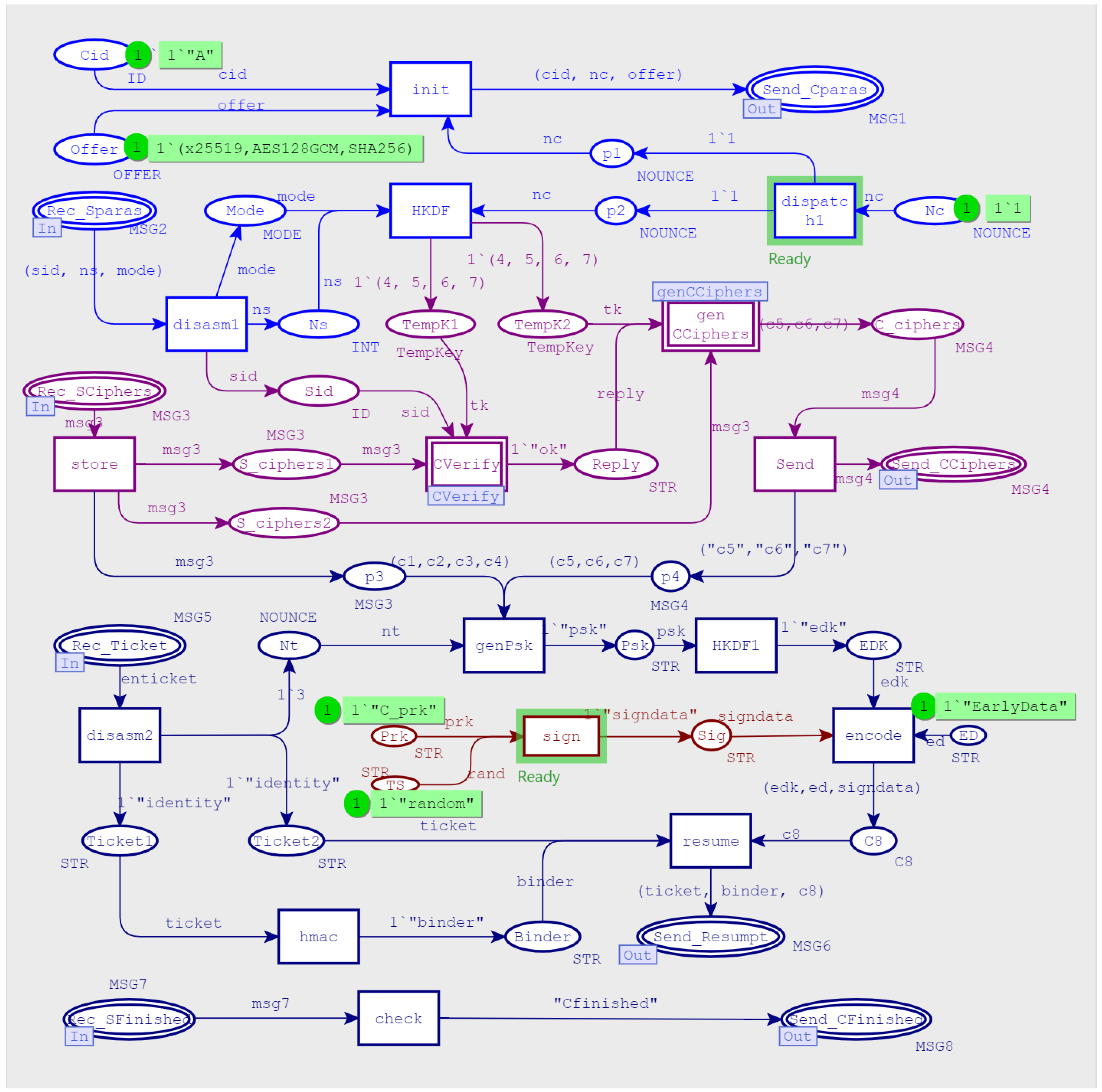
- 1.
- Run the initialization algorithm, the client generated DHE handshake parameters and provided various elliptic curve parameters in the key_share extension for the server to choose;
- 2.
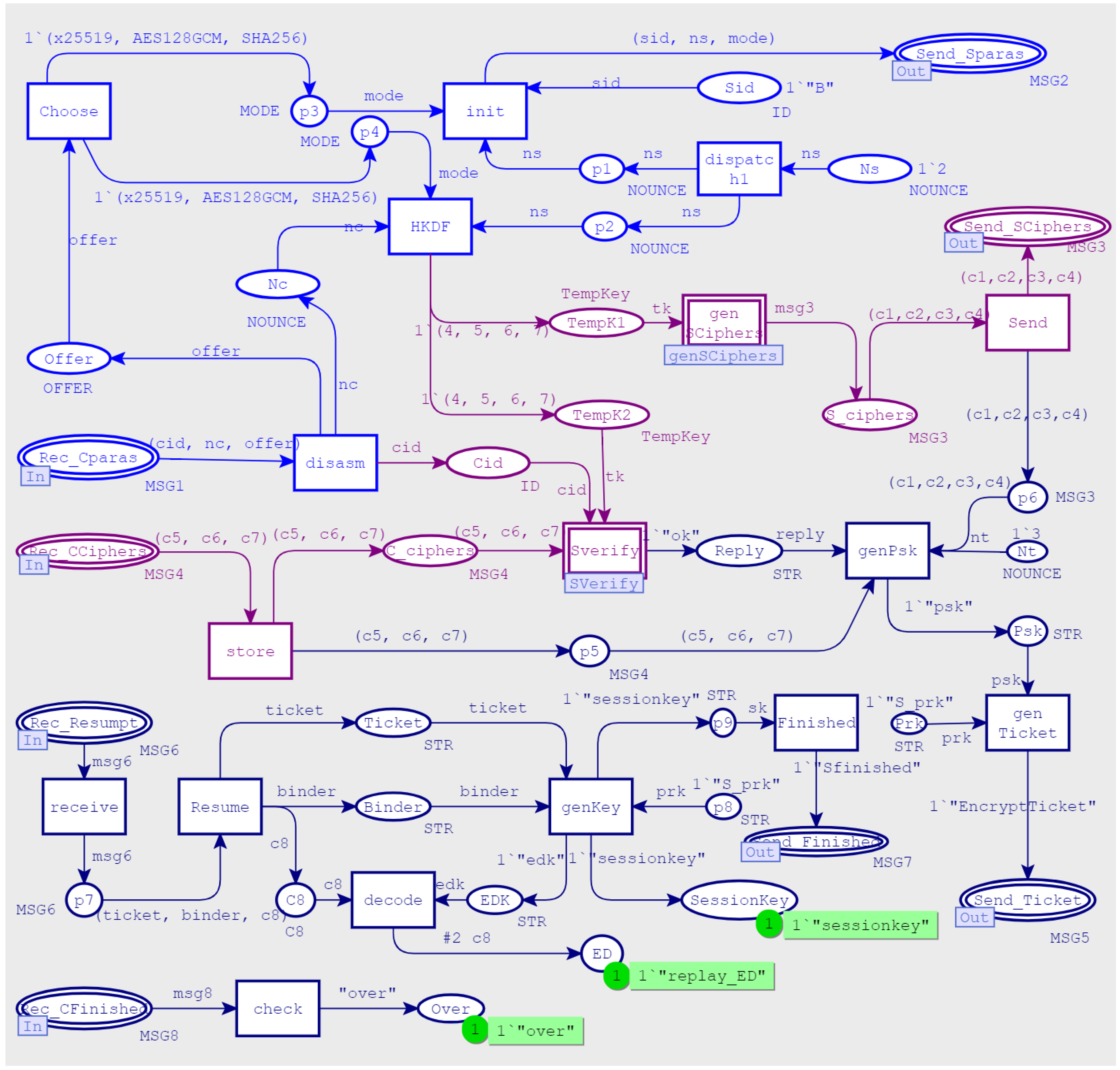
- The server also generated DHE handshake parameters and, at the same time, selected the elliptic curve parameters supported by itself in the key_share extension and passes them to the client to complete the elliptic curve Diffie–Hellman ephemeral (ECDHE) key exchange. Then it generated a set of temporary symmetric keys, TempKey, encrypted subsequent messages (marked with curly braces). Sent a certificate-request message to request that the client should send a certificate for identity verification; sent a certificate message to provide a signature verification key; send a certificate-verify message to provide a signature verification key. Finally, performed integrity protection on the above handshake messages by calculating the message authentication code and obtaining a finished message.
- 3.
- The client sent a certificate message to provide its own signature verification key, sent a certificate-verify message to provide a signature, and finally calculated the message authentication code with all previous handshake messages to obtain a finished message and send it to the client.
- 4.
- After the server had verified the identity of the client, it generated an initial session key based on the TempKey and the handshake messages. The initial handshake phase was nearly complete. However, in order to implement the subsequent short handshake, a session ticket needed to be generated for the client. First, generated a pre-shared key PSK and encrypted it with the server private key S_prk to obtain the tag identity corresponding to the client identity. Then, encrypted with the initial session key (marked with square brackets) to obtain the new-session-ticket message and send it to the client. Thus, the initial handshake phase was complete.
- 5.
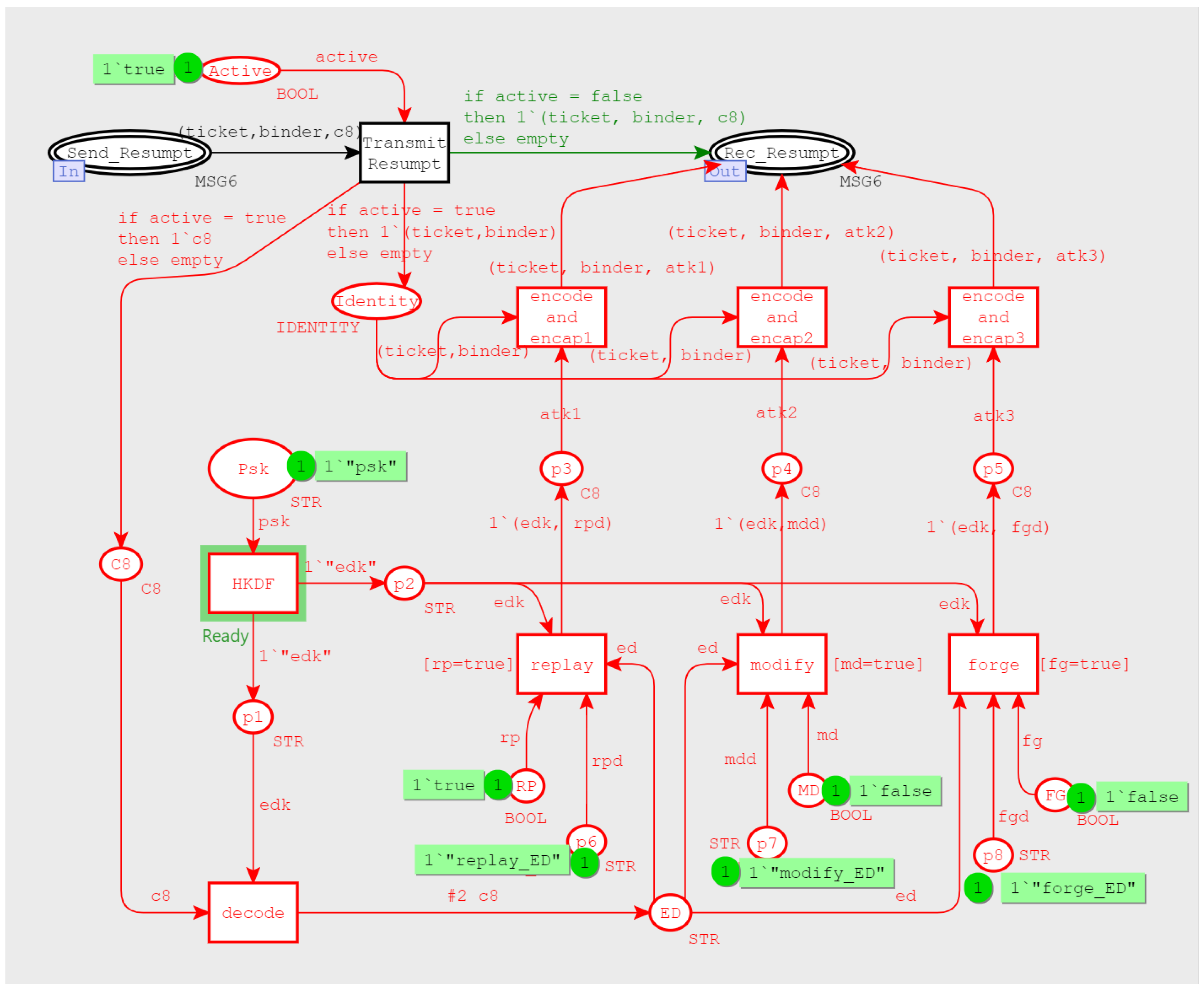
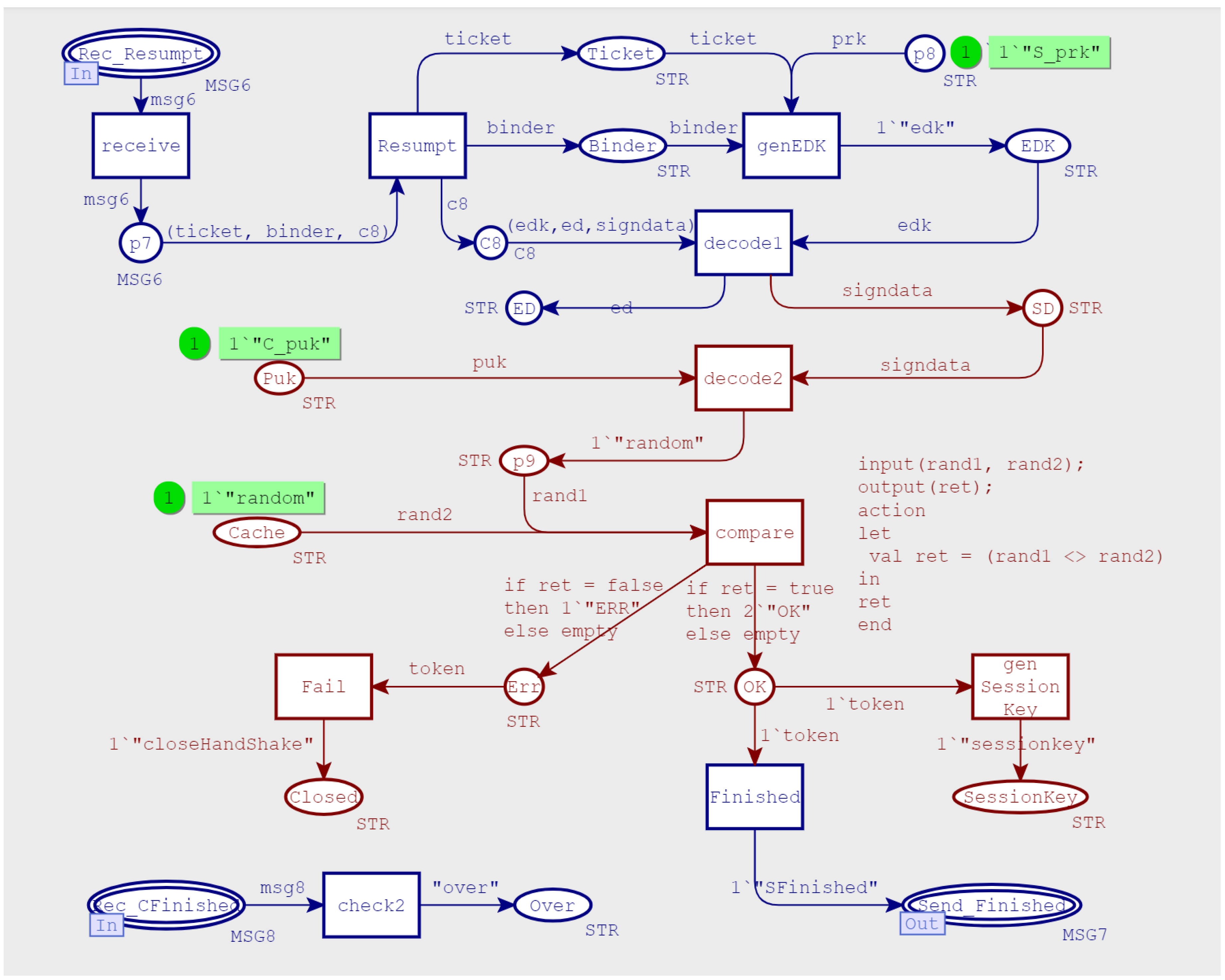
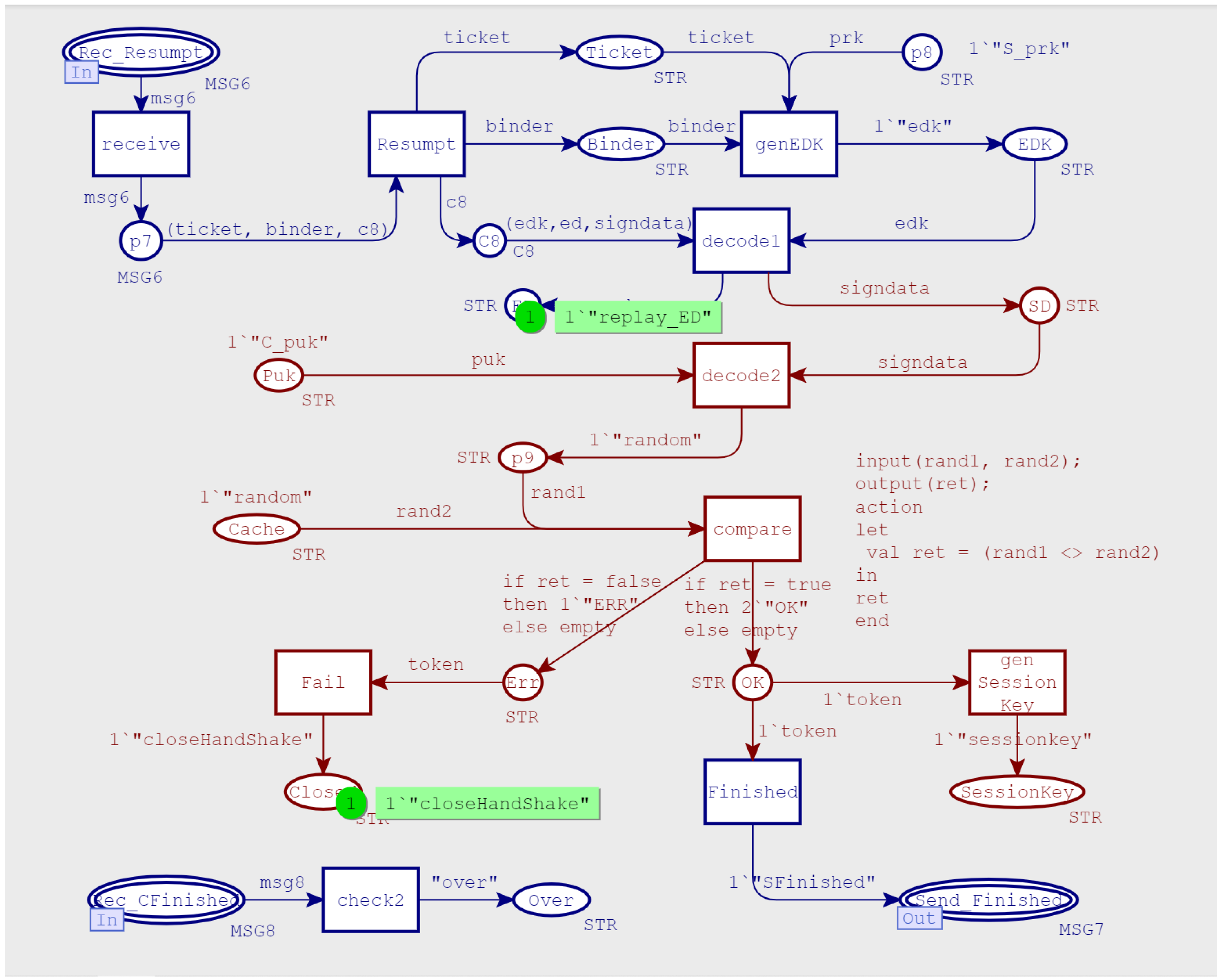
- Entered the subsequent short handshake process, and the main purpose of this stage was for session resumption. The client calculated the session-binding value (binder) according to a label (identity) in the ticket information, and encapsulated it into the pre_shared_key extension of the client-hello message. At the same time, it used pre-shared-key to derive early data key (EDK) and encrypted (marked with parentheses) early data. This was the so-called 0-RTT mode, that is, the application data were sent during the first handshake. It should be noted that the pre_shared_key extension did not contain the real PSK value. In other words, the PSK value would not be transmitted in the network channel.
- 6.
- After verifying the ticket, the server carried the pre_shared_key extension in the server-hello message to indicate that it agreed with the client to complete the handshake authentication in PSK mode. Then, it calculated the handshake message authentication code to ensure message integrity. Finally, it calculated the subsequent session key and encrypt the application data.
- 7.
- The client replied with a finished message. Here, the finished message had the same function as the server-side finished message. It was the last message in the authentication process, marking the completion of the authentication process, and the session was completely restored.
- 8.
- The client and the server encrypted (marked with square brackets) the application data through the subsequent session key for subsequent communication.
3.2. 0-RTT Authentication Model
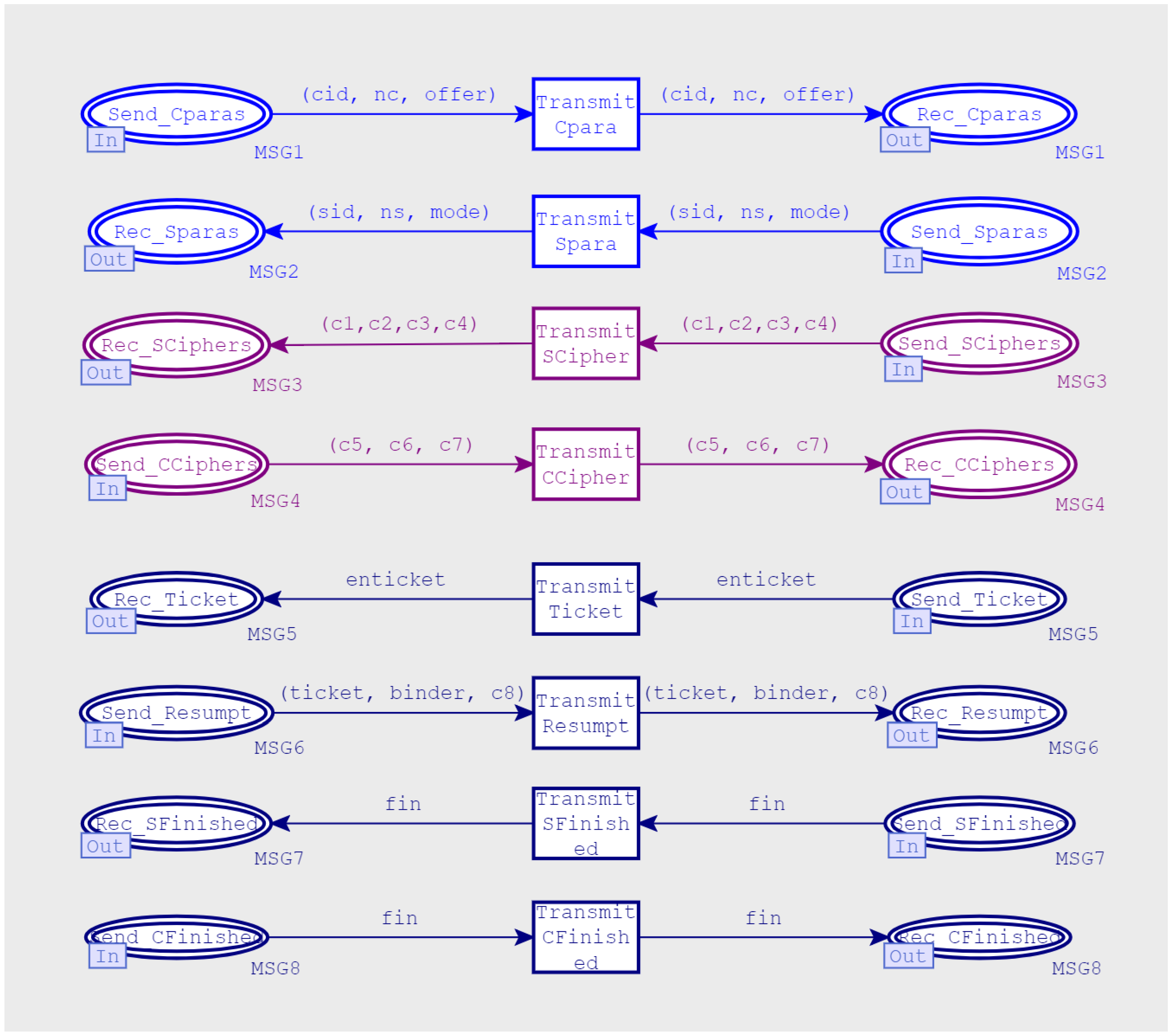
3.2.1. Top-Level Model
3.2.2. Color Set Definition
3.2.3. Middle-Level Model
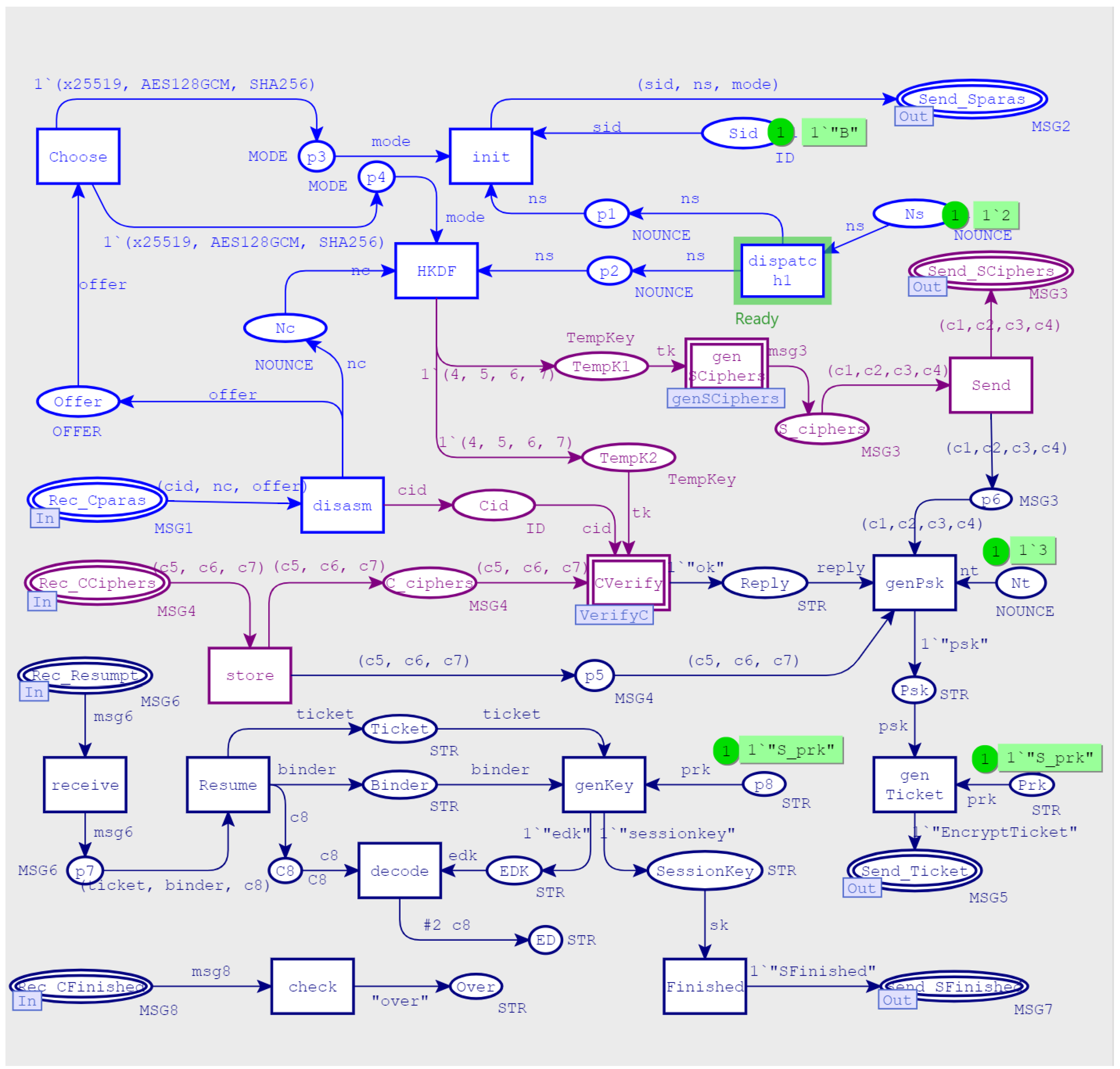
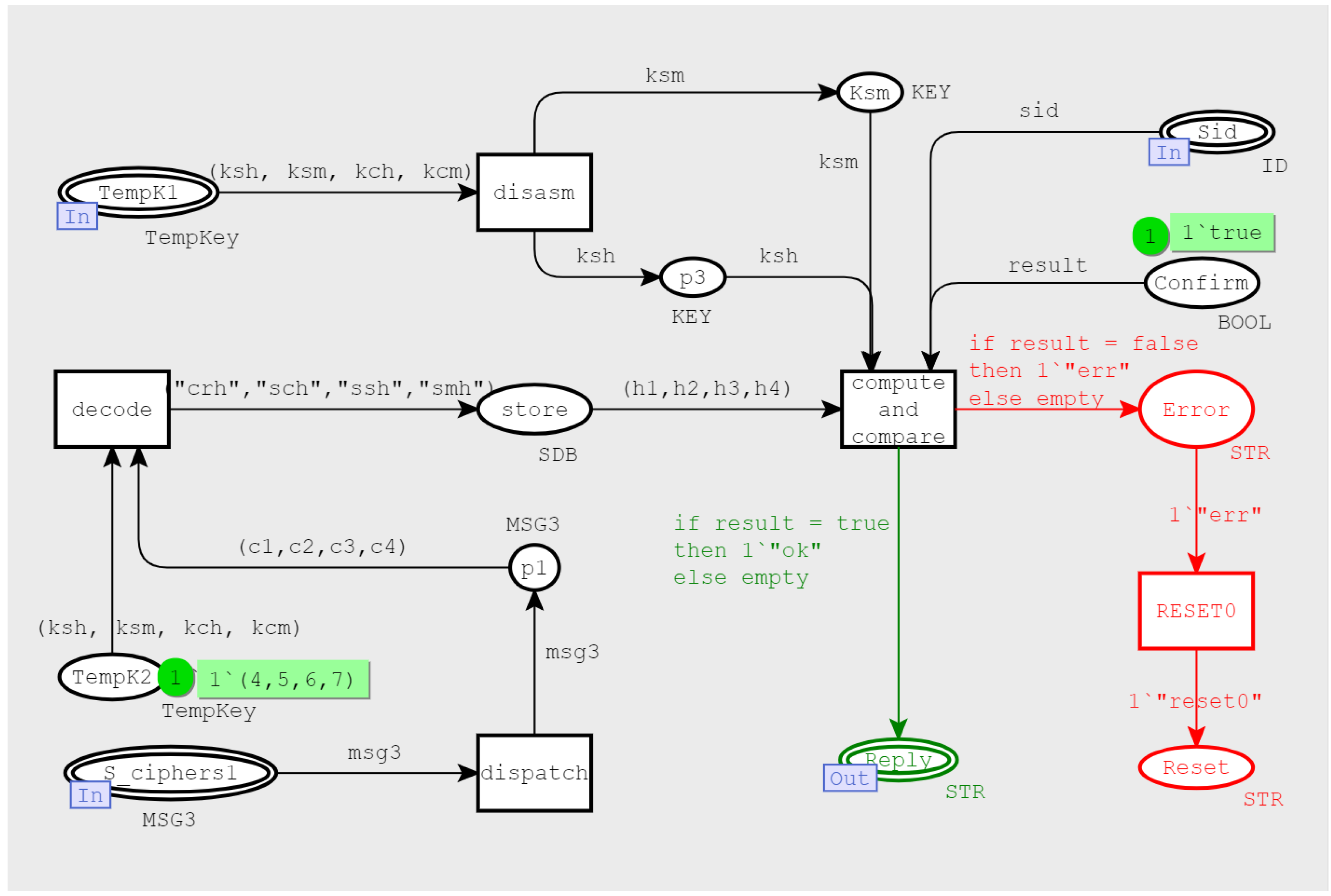
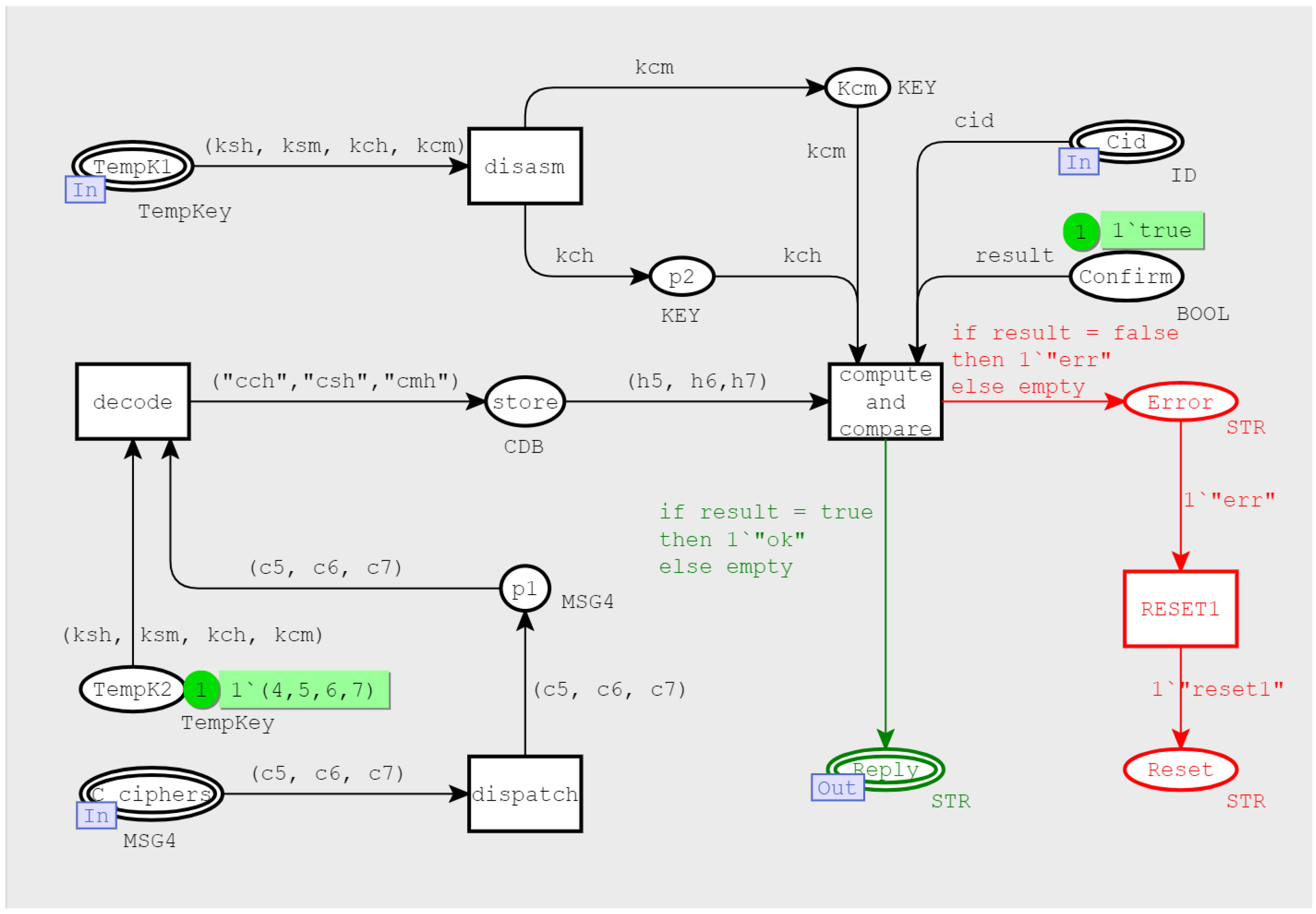
3.2.4. Bottom-Level Model
3.3. Consistency Verification
3.3.1. Expected Results
3.3.2. Experiment Results
4. Security Assessment of Original Scheme
4.1. Security Assessment Model
- MSG1 (CID, nc, offer) and MSG2 (SID, ns, mode) were transmitted over the network in plain text in order to complete the parameter exchange, so the security authentication function was provided by the follow-up mechanisms.
- MSG3 (c1, c2, c3, c4), MSG4 (c5, c6, c7) assisted the client and the server in verifying each other’s identity encrypted with TempKey. The key was obtained by ECDHE key exchange, and the generation process involved the participation of the private keys( in Definitions (1) and (2)), of both communication parties. The improved Dolev–Yao attacker model did not have the ability to corrupt the client and server, obtain their private keys, nor decipher the two messages.
- In MSG5(ticket), the ticket was obtained by encrypting PSK with the server’s private key, which was used as a credential for subsequent session resumption and encrypted by the initial session key. The initial session key was derived from the temporary symmetric key TempKey, with a previous handshake messages. As long as the TempKey was not leaked, the security of the message could be guaranteed.
- MSG7 (SFinished) and MSG8 (CFinished) were encrypted and transmitted by the subsequent handshake key. At this time, in order to ensure forward security, another round of ECDHE key exchange was performed during the subsequent handshake-key-generation process. This process involved the private keys of both parties and could be cracked.
4.2. Original Protocol Evaluation Results
5. Improved Scheme and Results
5.1. Improved Scheme
5.1.1. Client Side
5.1.2. Server Side
5.2. Improved Result
6. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AEAD | Authenticated Encryption with Associated Data |
| CUPS | Common UNIX Printing System |
| ECDHE | Elliptic Curve Diffie–Hellman Ephemeral |
| ED | Early Data |
| EDK | Early Data Key |
| GSSAPI | Generic Security Service Application Program Interface |
| HCPN | Hierarchical Colored Petri Nets |
| HKDF | HMAC-Based Key Derivation Function |
| IPP | Internet Printing Protocol |
| ISTO | Industry Standards and Technology Organization |
| LDP | Line Printer Daemon protocol |
| MAC | Message Authentication Code |
| PSK | Pre-Shared key |
| PWG | Printer Working Group |
| RTT | Round Trip Time |
Appendix A. System Configuration
| OS: | Windows 10 version 21H2(OS build 19044.2486), 64-bit operating system |
| Processor: | Intel(R) Core (TM) i7-10750H CPU @ 2.60GHz 2.59 GHz |
| Software: | CPN Tools version 4.0.1 |
References
- Print-Security-Market-Trends-2022. Available online: https://quocirca.com/content/quocirca-print-security-landscape-2022-press-release/ (accessed on 4 March 2023).
- IPP Everywhere. Available online: https://pwg.org/ipp/everywhere.html (accessed on 4 March 2023).
- Michael, S. CUPS Plenary, Joint PWG/Open Printing Meeting, Sunnyvale, California. Available online: https://ftp.pwg.org/pub/pwg/liaison/openprinting/presentations/cups-plenary-may-18.pdf (accessed on 4 March 2023).
- Murata, T. Petri nets: Properties, analysis and applications. Proc. IEEE 1989, 77, 541–580. [Google Scholar] [CrossRef]
- Jensen, K. Coloured petri nets. In Petri Nets: Central Models and Their Properties; Springer: Berlin/Heidelberg, Germany, 1987; pp. 248–299. [Google Scholar]
- Jensen, K.; Kristensen, L.M. Colored Petri nets: A graphical language for formal modeling and validation of concurrent systems. Commun. ACM 2015, 58, 61–70. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Cervesato, I. The Dolev–Yao intruder is the most powerful attacker. In Proceedings of the 16th Annual Symposium on Logic in Computer Science—LICS, Boston, MA, USA, 16–19 June 2001; Volume 1, pp. 1–2. [Google Scholar]
- Jensen, K.; Kristensen, L.M.; Wells, L. Coloured Petri Nets and CPN Tools for modelling and validation of concurrent systems. Int. J. Softw. Tools Technol. Transf. 2007, 9, 213–254. [Google Scholar] [CrossRef]
- Sweet, M.; McDonald, I. Internet Printing Protocol/1.1: Encoding and Transport. RFC 8010, 2017. Available online: https://www.rfc-editor.org/rfc/rfc8010.html (accessed on 4 March 2023).
- Sweet, M.; McDonald, I. Internet Printing Protocol/1.1: Model and Semantics. RFC 8011, 2017. Available online: https://www.rfc-editor.org/rfc/rfc8011.html (accessed on 4 March 2023).
- Wright, D. Design Goals for an Internet Printing Protocol. RFC 2567, 1999. Available online: https://www.rfc-editor.org/rfc/rfc2567.html (accessed on 4 March 2023).
- Zilles, S.N. Rationale for the Structure of the Model and Protocol for the Internet Printing Protocol. RFC 2568, 1999. Available online: https://www.rfc-editor.org/rfc/rfc2568.html (accessed on 4 March 2023).
- Khare, R.; Lawrence, S. Upgrading to TLS within HTTP/1.1. RFC 2817, 2000. Available online: https://www.rfc-editor.org/rfc/rfc2817 (accessed on 4 March 2023).
- Herriot, R.; McDonald, I. Internet Printing Protocol/1.1: IPP URL Scheme. RFC 3510, 2003. Available online: https://www.rfc-editor.org/rfc/rfc3510.html (accessed on 4 March 2023).
- McDonald, I.; Sweet, M. Internet Printing Protocol (IPP) over HTTPS Transport Binding and the ’IPPS’ URI Scheme. RFC 7472, 2015. Available online: https://www.rfc-editor.org/rfc/rfc7472.html (accessed on 4 March 2023).
- Rizk-Allah, R.M.; Abdulkader, H.; Elatif, S.S.A.; Elkilani, W.S.; Al Maghayreh, E.; Dhahri, H.; Mahmood, A. A Novel Binary Hybrid PSO-EO Algorithm for Cryptanalysis of Internal State of RC4 Cipher. Sensors 2022, 22, 3844. [Google Scholar] [CrossRef] [PubMed]
- Amodei, A.; Capriglione, D.; Ferrigno, L.; Miele, G.; Tomasso, G.; Cerro, G. A rule-based approach for detecting heartbleed cyber attacks. In Proceedings of the 2022 IEEE International Symposium on Measurements & Networking (M&N), Padua, Italy, 18–20 July 2022; pp. 1–6. [Google Scholar]
- Al Fardan, N.J.; Paterson, K.G. Lucky thirteen: Breaking the TLS and DTLS record protocols. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 526–540. [Google Scholar]
- Adrian, D.; Bhargavan, K.; Durumeric, Z.; Gaudry, P.; Green, M.; Halderman, J.A.; Heninger, N.; Springall, D.; Thomé, E.; Valenta, L.; et al. Imperfect forward secrecy: How Diffie-Hellman fails in practice. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 5–17. [Google Scholar]
- Adrian, A.; Cendana, M.; Permana, S.D.H. Diffie-Hellman key exchange modification using blowfish algorithm to prevent logjam attack. J. Telecommun. Electron. Comput. Eng. (JTEC) 2018, 10, 1–7. [Google Scholar]
- Kumari, N.; Mohapatra, A. A comprehensive and critical analysis of TLS 1.3. J. Inf. Optim. Sci. 2022, 43, 689–703. [Google Scholar] [CrossRef]
- Langley, A.; Riddoch, A.; Wilk, A.; Vicente, A.; Krasic, C.; Zhang, D.; Yang, F.; Kouranov, F.; Swett, I.; Iyengar, J.; et al. The quic transport protocol: Design and internet-scale deployment. In Proceedings of the Conference of the ACM Special Interest Group on Data Communication, Los Angeles, CA, USA, 21–25 August 2017; pp. 183–196. [Google Scholar]
- Chen, S.; Jero, S.; Jagielski, M.; Boldyreva, A.; Nita-Rotaru, C. Secure communication channel establishment: TLS 1.3 (over TCP fast open) versus QUIC. J. Cryptol. 2021, 34, 26. [Google Scholar] [CrossRef]
- Aviram, N.; Gellert, K.; Jager, T. Session resumption protocols and efficient forward security for TLS 1.3 0-RTT. J. Cryptol. 2021, 34, 20. [Google Scholar] [CrossRef]
- Aziz, B.; Aziz, B. Formal Analysis by Abstract Interpretation; Springer: Berlin/Heidelberg, Germany, 2022. [Google Scholar]
- Zhong, X.; Xiao, M.; Zhang, T.; Yang, K.; Luo, Y. Proving mutual authentication property of rcia protocol in rfid based on logic of events. Chin. J. Electron. 2022, 31, 79–88. [Google Scholar]
- Lu, S.; Zhou, S.; Mao, Y. Formal Analysis and Optimization of TLS1. 3 Protocol in Strong Security Model. J. Softw. 2021, 32, 2849–2866. [Google Scholar]
- Ram, S.B.; Odelu, V. Security Analysis of a Key Exchange Protocol under Dolev–Yao Threat Model Using Tamarin Prover. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022; pp. 0667–0672. [Google Scholar]
- Du, J.; Gao, C.; Feng, T. Formal Safety Assessment and Improvement of DDS Protocol for Industrial Data Distribution Service. Future Internet 2022, 15, 24. [Google Scholar] [CrossRef]
- Petri, C.A. Kommunikation mit Automaten. Ph.D. Thesis, University of Hamburg, Hamburg, Germany, 1962. [Google Scholar]
- Sheng, J.; Prescott, D. Using a novel hierarchical coloured Petri net to model and optimise fleet spare inventory, cannibalisation and preventive maintenance. Reliab. Eng. Syst. Saf. 2019, 191, 106579. [Google Scholar] [CrossRef]
- Grobelna, I.; Szcześniak, P. Interpreted petri nets applied to autonomous components within electric power systems. Appl. Sci. 2022, 12, 4772. [Google Scholar] [CrossRef]
- Farooq, M.S.; Idrees, M.; Rehman, A.U.; Khan, M.Z.; Abunadi, I.; Assam, M.; Althobaiti, M.M.; Al-Wesabi, F.N. Formal Modeling and Improvement in the Random Path Routing Network Scheme Using Colored Petri Nets. Appl. Sci. 2022, 12, 1426. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Wisniewski, R.; Nidumolu, V. Holistic Research on Blockchain’s Consensus Protocol Mechanisms with Security and Concurrency Analysis Aspects of CPS. Electronics 2022, 11, 2760. [Google Scholar] [CrossRef]
- A Tool for Editing, Simulating, and Analyzing Colored Petri Nets. Available online: http://cpntools.org/ (accessed on 4 March 2023).
- Ratzer, A.V.; Wells, L.; Lassen, H.M.; Laursen, M.; Qvortrup, J.F.; Stissing, M.S.; Westergaard, M.; Christensen, S.; Jensen, K. CPN tools for editing, simulating, and analysing coloured Petri nets. In Proceedings of the Applications and Theory of Petri Nets 2003: 24th International Conference, ICATPN 2003, Eindhoven, The Netherlands, 23–27 June 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 450–462. [Google Scholar]
- Verbeek, E.; Fahland, D. CPN IDE: An Extensible Replacement for CPN Tools That Uses Access/CPN. In Proceedings of the 3rd International Conference on Process Mining Doctoral Consortium and Demo Track, ICPM-D 2021, Eindhoven, The Netherlands, 31 October–4 November 2021; pp. 29–30. [Google Scholar]





| Stage | Type | Colset Def. |
|---|---|---|
| ID | colset ID = string with “A”, ..., “D”; | |
| ParasExchange | NONCE | colset NONCE = int with 1, …, 3; |
| Group List | colset GroupList = with secp256r1|x25519; | |
| EncryptionList | colset EncryptionList = with AES128GCM|AES256GCM|CHACHA20POLY1305|AES128CCM; | |
| HashList | colset HashList = with SHA256|SHA384; | |
| OFFER | colset OFFER = product GroupList*EncryptionList*HashList; | |
| MODE | colset MODE = product GroupList*EncryptionList*HashList; | |
| MSG1 | colset MSG1 = product ID*NONCE*OFFER | |
| MSG2 | colset MSG2 = product ID*NONCE*MODE | |
| KEY | colset KEY = int with 4, …, 8; | |
| Authentication | TempKey | colset TempKey = product KEY*KEY*KEY*KEY; |
| CR | colset CR = string; | |
| Cert | colset Cert = string; | |
| Sign | colset Sign = string; | |
| MAC | colset MAC = string; | |
| MSG3 | colset MSG3 = product C1*C2*C3*C4; | |
| MSG4 | colset MSG4 = product C5*C6*C7; | |
| SHASH | colset SHASH = product STR*STR*STR*STR; | |
| CHASH | colset CHASH = product STR*STR*STR; | |
| RESULT | colset RESULT = bool; | |
| MSG5 | colset MSG5 = STR; | |
| Resumption | EarlyData | colset EarlyData = STR; |
| MSG6 | colset MSG6 = product STR*STR*STR; | |
| MSG7 | colset MSG7 = SFinished; | |
| MSG8 | colset MSG8 = CFinished; |
| Category | Dead Transition | Live Transition | Status | Home Marking | Dead Marking |
|---|---|---|---|---|---|
| Count | 2 | 0 | Null | 1 | 1 |
| Name | RESET0, RESET1 | Null | Full | End-node number | End-node number |
| Category | Statistics | Name |
|---|---|---|
| Nodes | 443 | 1, …, 443 |
| Arcs | 1090 | 1, …, 1090 |
| Status | Full | Null |
| Nodes(SCC) | 443 | 1, …, 443 |
| Arcs(SCC) | 1090 | 1, …, 1090 |
| Home Markings | 1 | 443 * |
| Live Transitions | 0 | 0 |
| Dead Transitions | 1 | 443 * |
| Dead Transitions | 2 | RESET0, RESET1 |
| Category | Statistics | Name |
|---|---|---|
| Nodes | 875 | 1, …, 875 |
| Arcs | 2593 | 1, …, 2593 |
| Status | Full | Null |
| Nodes(SCC) | 875 | 1, …, 875 |
| Arcs(SCC) | 2593 | 1, …, 875 |
| Home Markings | 1 | 875 * |
| Live Transitions | 0 | 0 |
| Dead Transitions | 1 | 875 * |
| Category | Statistics | Name |
|---|---|---|
| Nodes | 1718 | 1, …, 1718 |
| Arcs | 5988 | 1, …, 5988 |
| Status | Full | Null |
| Nodes(SCC) | 1718 | 1, …, 1718 |
| Arcs(SCC) | 5988 | 1, …, 5988 |
| Home Markings | 1 | 1718 * |
| Live Transitions | 0 | 0 |
| Dead Transitions | 1 | 1718 * |
| Category | Before | After |
|---|---|---|
| Nodes | 875 | 1718 |
| Arcs | 2593 | 5988 |
| Status | Full | Full |
| Nodes(SCC) | 875 | 1718 |
| Arcs(SCC) | 2593 | 5988 |
| Home Markings | 875 * | 1718 * |
| Live Transitions | 0 | 0 |
| Dead Transitions | 875 * | 1718 * |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, T.; Bei, H.-R. Evaluation and Improvement of Internet Printing Protocol Based on HCPN Model Detection Method. Appl. Sci. 2023, 13, 3467. https://doi.org/10.3390/app13063467
Feng T, Bei H-R. Evaluation and Improvement of Internet Printing Protocol Based on HCPN Model Detection Method. Applied Sciences. 2023; 13(6):3467. https://doi.org/10.3390/app13063467
Chicago/Turabian StyleFeng, Tao, and Hong-Ru Bei. 2023. "Evaluation and Improvement of Internet Printing Protocol Based on HCPN Model Detection Method" Applied Sciences 13, no. 6: 3467. https://doi.org/10.3390/app13063467






