Abstract
This research paper explores the CONIKS key management system’s security and efficiency, a system designed to ensure transparency and privacy in cryptographic operations. We conducted a comprehensive analysis of the underlying mathematical principles, focusing on cryptographic hash functions and digital signature schemes, and their implementation in the CONIKS model. Through the use of Merkle trees, we verified the integrity of the system, while zero-knowledge proofs were utilized to ensure the confidentiality of key bindings. We conducted experimental evaluations to measure the performance of cryptographic operations like key generation, signing, and verification with varying key sizes and compared the results against theoretical expectations. Our findings demonstrate that the system performs as predicted by cryptographic theory, with only minor deviations in computational time complexities. The analysis also reveals significant trade-offs between security and efficiency, particularly when larger key sizes are used. These results confirm that the CONIKS system offers a robust framework for secure and efficient key management, highlighting its potential for real-world applications in secure communication systems.
1. Introduction
In the digital age, where privacy concerns are paramount, end-to-end encryption (E2EE) has become indispensable for protecting communication. The security of E2EE systems fundamentally depends on the cryptographic primitives and protocols employed, which must be rigorously designed to avoid vulnerabilities [1]. As key transparency systems have evolved, their integration with E2EE frameworks has offered innovative approaches to secure key management while safeguarding user privacy. This research paper focuses on CONIKS, a key transparency system that ensures the authenticity of public keys in E2EE communication, providing a secure and transparent method for key management.
Key transparency addresses a critical challenge in cryptographic systems: ensuring that public keys used in encrypted communication are both authentic and untampered, without requiring users to trust third-party authorities blindly. CONIKS builds on earlier solutions like Certificate Transparency [2] and Keybase by utilizing cryptographic tools such as hash functions, digital signatures, and Merkle trees. These tools are essential for maintaining the system’s integrity and transparency. Hash functions ensure data integrity, digital signatures guarantee authenticity and non-repudiation, and Merkle trees, a pivotal data structure, allow for the efficient verification of key inclusion [3].
In this paper, we present a thorough analysis of the mathematical foundations of CONIKS, including the cryptographic primitives that it employs and the security models that ensure its resilience to attacks. The paper also provides a comparative analysis of CONIKS against other key transparency systems, highlighting its advantages in scalability, security, and user privacy. We extend the study with formal mathematical proofs that demonstrate the security of the system against a variety of attack vectors, thereby offering a robust evaluation grounded in well-established cryptographic principles.
Furthermore, this paper delves into the architecture and implementation of the CONIKS system. We outline its key components and detail the processes of user registration and key management. Practical aspects, including the development environment, tools, and error-handling mechanisms, are discussed to give readers a comprehensive understanding of CONIKS’s operational functionality.
In conclusion, this paper contributes to the growing body of research on cryptographic systems by offering a detailed examination of the mathematical and practical foundations of CONIKS. The insights gained have significant implications for the future development of secure, scalable, and transparent end-to-end encryption systems, with potential applications extending to various digital platforms that require robust key management solutions.
2. Related Work
Key transparency is a critical aspect of cryptographic systems, ensuring the verifiability and integrity of public keys in end-to-end encrypted communications [3]. Traditional public key infrastructures (PKIs) have faced significant challenges due to centralized trust models, where the compromise of certificate authorities (CAs) can lead to widespread security breaches [4]. To address these vulnerabilities, researchers have explored key transparency systems that decentralize trust and enhance auditability. One foundational approach in key transparency is Certificate Transparency (CT), developed by Laurie et al., which introduced a log-based system for recording all certificates issued by CAs. This system allows for the public auditing and early detection of misissued or fraudulent certificates [5]. CT’s introduction has significantly improved the trustworthiness of PKIs by holding CAs accountable for their actions. CONIKS, developed by Melara et al., extends the CT model to secure messaging systems. It allows users to verify the correctness of their peers’ public keys without relying on a centralized authority, thereby enhancing user privacy and security. CONIKS employs a “transparency tree,” a variant of the Merkle tree, to provide efficient key verification and auditing while preserving the privacy of user key bindings [6]. Another important contribution to the field is the Auditable, Privacy-Preserving Key Directory (AKD) by Yilek et al., which uses cryptographic techniques to ensure that key information remains confidential to all but the intended recipient. AKD aims to balance the need for auditability with user privacy, providing a secure and transparent key management solution [6]. Researchers like Chase and Meiklejohn have also explored the use of cryptographic accumulators and distributed ledgers in transparency logs, aiming to improve the scalability and privacy of key transparency systems. These efforts have been crucial in developing more efficient and scalable key transparency solutions [7]. Mollakuqe, Rexhepi, Bunjaku, Dag, and Ikechukwu John Chukwu’s research provides a comprehensive survey of emerging protocols and challenges in key management, with a focus on transparent key management solutions. Their work emphasizes the importance of developing robust, scalable, and privacy-preserving frameworks for key transparency in cryptographic systems [8]. Existing key transparency solutions vary in their approaches to balancing security, privacy, and scalability. Certificate Transparency (CT) has proven effective in enhancing accountability within PKIs by allowing for the real-time monitoring and auditing of certificate issuance [9]. CT’s reliance on third-party log servers raises concerns about privacy and potential single points of failure. CONIKS addresses these issues by offering a decentralized, user-centric approach to key transparency. By using transparency trees, CONIKS enables users to independently verify their key bindings, ensuring that their public keys are accurately represented in the system without compromising user privacy [10]. This approach significantly reduces the reliance on trusted third parties and enhances the overall security of the system. In contrast, AKD emphasizes privacy preservation while maintaining auditability. Although AKD provides a robust framework for privacy-preserving key transparency, it relies on complex cryptographic protocols that may introduce performance overheads and implementation challenges. The transparency logs model by Chase and Meiklejohn offers a scalable and privacy-enhancing alternative, using cryptographic accumulators and distributed ledgers to manage key transparency. This approach is particularly suitable for large-scale applications where scalability is a primary concern.
CONIKS introduces several innovative features that enhance the security and usability of key transparency systems:
- Transparency Tree
CONIKS employs a “transparency tree,” a variant of the Merkle tree, to efficiently verify the inclusion of key entries while preserving user privacy [11]. This structure allows users to audit their key bindings and verify the correctness of their peers’ keys without exposing sensitive information to third parties.
- Key Revocation and Updates
CONIKS incorporates mechanisms for key revocation and updates, ensuring the long-term security of the cryptographic system [12]. Users can periodically update their keys, and compromised keys can be efficiently revoked, providing resilience against long-term attacks.
- Scalability
Designed for scalability, CONIKS supports large-scale deployments in modern messaging systems [13]. Its efficient key verification protocols and privacy-preserving features make it a practical solution for real-world applications, addressing the limitations of existing key transparency solutions.
CONIKS represents a significant advancement in key transparency, offering a robust and scalable framework for secure key management in end-to-end-encrypted communication systems [14]. Its unique contributions to privacy, scalability, and usability make it a compelling choice for developers and organizations who are seeking to enhance the security of their cryptographic systems.
2.1. Mathematical Foundations
In the realm of cryptographic key management, the effectiveness and security of the Transparent Key Management Algorithm are underpinned by several crucial mathematical constructs. At its core, the algorithm leverages Merkle trees, hash functions, and digital signatures to create a transparent and verifiable system for managing cryptographic keys [15]. These elements work in concert to ensure the integrity and authenticity of key management processes. Merkle trees, with their hierarchical structure, facilitate efficient, and secure verification of key inclusion, while cryptographic hash functions provide robustness against tampering. Digital signatures further enhance security by enabling the verification of the authenticity of updates to the transparency logs [16]. This foundation is critical in addressing the challenges associated with traditional key management systems, such as transparency and scalability. The following section delves into the specifics of Merkle trees, illustrating their role and benefits in the context of key management [17]. Figure 1 shows a deeper and more detailed binary Merkle tree with multiple levels of internal nodes, which better illustrates how hash values propagate through the tree.
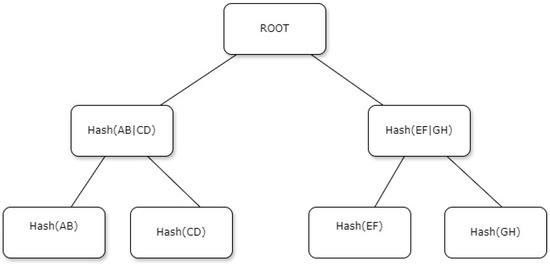
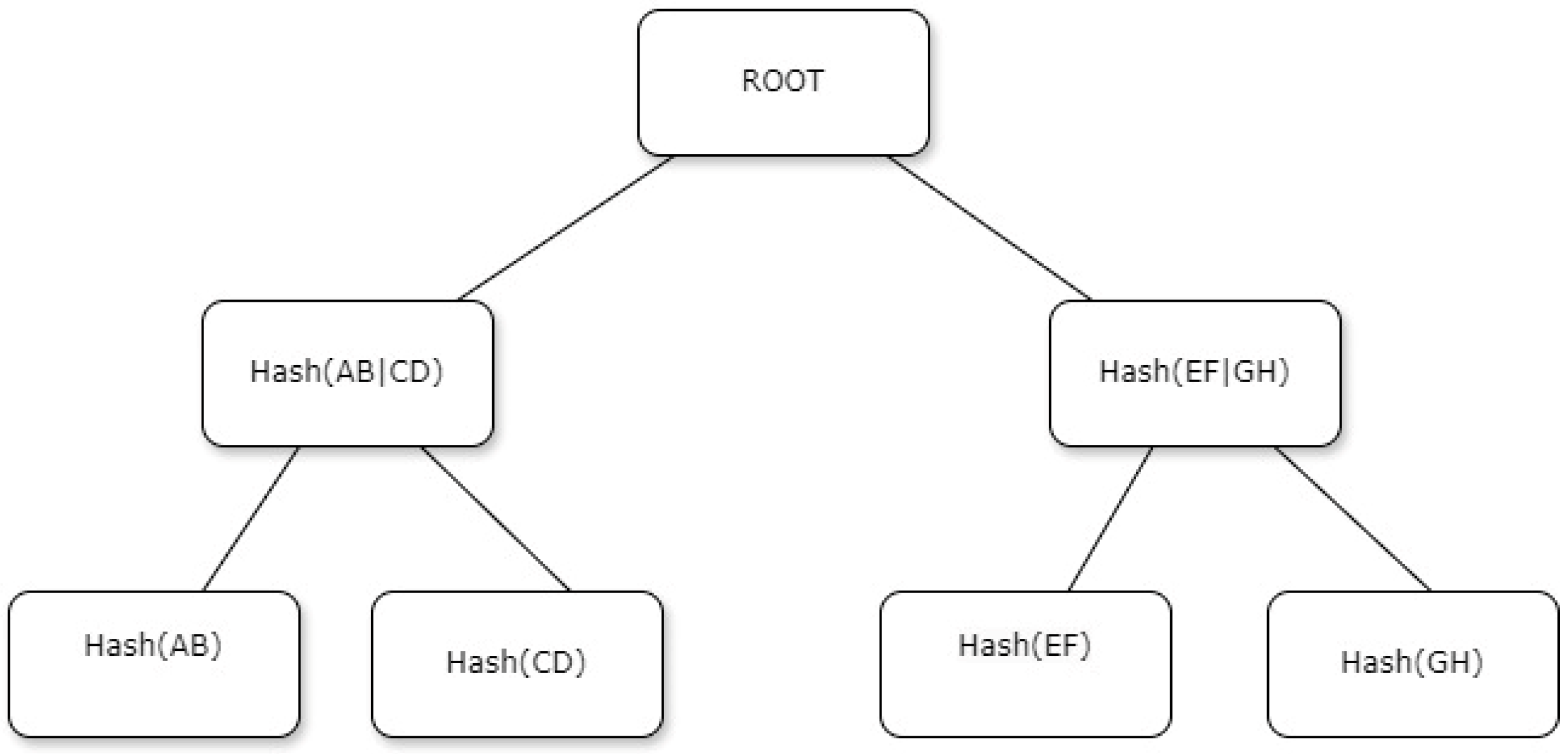
Figure 1.
Structure of a Merkle tree.
The Merkle tree graph illustrates a hierarchical structure used in cryptographic key management, depicted mathematically as follows. At the base level, the leaf nodes represent the hash values of individual data elements. Let L1, L2, L3,…, L8 be the data elements at the leaf level of the tree. These data elements are each hashed by a cryptographic function hi = H(Li) for i = 1, 2,…, 8. Moving up to Level 2, internal nodes are computed by concatenating the hashes of their child nodes. For instance, hashes such as HAB, HCD, HEF, and HGH are derived from
HAB = H(H1∥H2), HCD = H(H3∥H4), HEF = H(H5∥H6), HGH = H(H7∥H8)
Similarly, as HAB, HCD, HEF, and HGH are computed from their respective child hashes. At Level 1, the internal nodes HAB|CD and HEF|GH are calculated as
HAB|CD = H(HAB∥HCD), and HEF|GH = H(HEF∥HGH)
The root node RRR, representing the entire dataset, is computed as
R = H(HAB|CD∥HEF|GH)
2.2. Formal Definitions and Properties
In the CONIKS system, the formal definitions and properties of cryptographic primitives are foundational to ensuring security and functionality. At the heart of these primitives is the hash function H, which maps arbitrary-sized inputs to fixed-sized hash values [18]. The function H:{0,1}*→{0,1}k is designed with critical properties: pre-image resistance, which makes it computationally infeasible to reverse-engineer the original input from the hash value; second pre-image resistance, which prevents others from finding a different input that maps to the same hash value as a given input; and collision resistance, which ensures that it is infeasible to find two distinct inputs that produce the same hash value. Additionally, digital signatures play a crucial role in authenticating data and ensuring integrity. They employ a key pair where the private key sk is used to sign a message m, producing a signature σ (sigma), and the public key pk is used to verify the signature through the function Verify(pk,m,σ).
Hash Function H is a cryptographic hash function providing properties like collision resistance and pre-image resistance.
A hash function H is a function H:{0,1}*→{0,1}k that produces a fixed-size hash value from an arbitrary-size input [18]. Important properties include the following:
Pre-image Resistance: Given h = H(x), it is computationally infeasible to find x;
Second Pre-image Resistance: Given x and h = H(x), it is infeasible to find x′ ≠ x such that H(x′) = h;
Collision Resistance: It is infeasible to find any two distinct inputs x and y such that H(x) = H(y).
Digital Signatures
Digital signatures use a pair of keys: a private key sk for signing and a public key pk for verification. For a message m, the signature σ (sigma) is generated as σ = Sign(sk,m). Verification involves checking Verify(pk,m,σ) to ensure that σ was generated using sk and that m has not been altered.
These cryptographic constructs are essential for maintaining security and trust in the CONIKS framework.
2.3. Security Assumptions and Models
In the CONIKS system, several cryptographic assumptions underpin its security framework. Firstly, the security of CONIKS relies on the properties of the hash function H, which is assumed to be collision-resistant, pre-image-resistant, and second pre-image-resistant. These properties ensure that it is computationally infeasible to find two different inputs that produce the same hash value, thereby preserving data integrity [19]. Additionally, the system’s security is built upon the robustness of public key cryptosystems, such as RSA or Elliptic Curve Cryptography, which depend on the difficulty of solving mathematical problems like integer factorization or discrete logarithms.
The security model of CONIKS assumes an adversary with certain capabilities and constraints. The adversary might manipulate or compromise keys, transparency logs, or other components within the system, but they are not able to break the cryptographic assumptions underlying the hash functions and digital signatures [19]. The privacy model ensures that, while transparency logs are publicly verifiable, users’ key bindings remain confidential and protected from unauthorized disclosure.
The mathematical proofs of security in CONIKS include integrity, consistency, and privacy proofs. Integrity proofs are provided through the use of Merkle trees, where any alteration in a leaf node impacts the root hash, thereby proving that changes are detectable throughout the tree [20]. Consistency proofs are achieved via signed updates, where each update to the transparency tree is accompanied by a digital signature and results in a new root hash. This mechanism ensures that updates accurately reflect changes in key bindings and maintain a reconciliation with previous versions of the tree. Privacy is safeguarded through zero-knowledge proofs, which allow users to confirm key inclusion and consistency without disclosing the actual keys, thereby ensuring that the transparency logs, while public, do not compromise the confidentiality of the keys themselves [20]. Through these mathematical foundations, CONIKS effectively supports key transparency, maintaining both the integrity and privacy of cryptographic key management systems.
2.3.1. Implementation of CONIKS in PYTHON
The successful implementation of CONIKS in Python requires a well-defined development environment and a set of tools to manage cryptographic operations effectively. Python, with its rich ecosystem of libraries and frameworks, provides a robust platform for implementing key transparency mechanisms. The development process begins by setting up a suitable environment that supports both the cryptographic and algorithmic requirements of CONIKS. This includes selecting the appropriate libraries for cryptographic functions, such as hashing and digital signatures, and utilizing development tools that facilitate efficient coding and debugging. By establishing a solid foundation with these tools, developers can ensure that the implementation is secure, reliable, and aligned with the theoretical principles of CONIKS.
2.3.2. Development Environment and Tools
The implementation of CONIKS in Python involves setting up a development environment with essential tools and libraries. Key tools include Python 3.x, which offers modern language features and libraries for cryptographic operations. The primary library used for cryptographic functions is hashlib, which provides robust support for hash functions like SHA-256. Additionally, the ‘cryptography’ library is employed for digital signatures, using classes such as RSAPrivateKey and RSAPublicKey to manage key pairs and signing operations. Development environments like Jupyter Notebooks or PyCharm can be used for coding, debugging, and testing.
2.3.3. Algorithms and Data Structures
The core algorithms and data structures for implementing CONIKS include Merkle trees for key transparency and digital signature algorithms for authentication. The Merkle tree is constructed using a binary tree structure where each internal node is a hash of its child nodes. For this, a class-based implementation in Python utilizes binary trees, where each node stores hash values and provides methods for insertion and hash computation. The MerkleTree class handles the construction and updating of the tree, while the HashNode class represents each node in the tree.
Digital signatures are implemented using RSA or ECDSA algorithms, depending on the chosen cryptographic method. The cryptography library provides methods for generating keys, signing messages, and verifying signatures. Key management involves the secure generation and storage of public and private keys, ensuring that they are used correctly for signing and verification processes.
2.3.4. Code Implementing
The implementation of CONIKS in Python involves coding both the core algorithmic components and the cryptographic operations that are necessary for key transparency. At the heart of the implementation is the Merkle tree, a data structure that ensures the integrity and transparency of key management. The Merkle tree is constructed by hashing the leaf nodes, which represent the raw key data, and then recursively hashing parent nodes to build the tree upwards to the root. This hierarchical structure allows for the efficient verification of data integrity, as any change in the leaf nodes will propagate through the tree, altering the root hash. The provided Python code snippet demonstrates the creation of a MerkleTree class (Figure 2) that builds the tree from a list of leaves and computes hash values using the SHA-256 hashing algorithm.

Figure 2.
Merkle tree construction.
In addition to Merkle tree construction, digital signature functionality is implemented to authenticate and verify data. The cryptography library in Python is used to handle key generation, signing, and verification processes. The generate_key_pair function creates a pair of RSA keys, while the sign_message function generates a digital signature for a given message using the private key (Appendix A). Verification is handled by the verify_signature function, which checks the signature against the message using the public key.
This ensures that the data have not been altered and that the signature is valid. Together, these components form the basis of the CONIKS implementation, providing both the cryptographic assurances and the practical tools needed for secure key management.
2.4. Handling Errors and Exceptions
Error handling in this implementation involves ensuring robustness and security against various failure scenarios. For example, during Merkle tree construction, care must be taken to handle cases where the number of leaves is not a power of two, which may require padding or handling uneven levels in the tree. For digital signature operations, error handling includes managing exceptions during key generation, signing, and verification processes, such as invalid signatures or corrupted data. This can be achieved by using try–except blocks around critical operations to capture and respond to exceptions gracefully, ensuring that the system remains secure and functional even in the presence of errors.
3. Results
In evaluating the performance and effectiveness of the CONIKS system, a series of experiments were conducted to assess various aspects of its implementation, including Merkle tree construction and digital signature operations. The experimental setup was designed to measure key performance metrics such as hash computation time, tree construction efficiency, and the speed of digital signature processes. These metrics are crucial for understanding how the CONIKS system handles real-world cryptographic tasks, including managing large datasets and performing secure transactions. By systematically testing the system under different conditions, we aim to provide a comprehensive analysis of its operational efficiency and scalability.
The results of these experiments are presented in the following sections, which detail the performance metrics observed, compare them with theoretical expectations, and analyze any discrepancies. Tables and graphs illustrate the findings, including how the time required for constructing Merkle trees scales with the number of leaves, the impact of key size on digital signature operations, and how the experimental results align with theoretical complexity models. This detailed analysis not only validates the effectiveness of the CONIKS system but also provides insights into potential areas for optimization and improvement.
3.1. Experimental Setup
To accurately evaluate the performance of the CONIKS system, a rigorous experimental setup was designed to test various aspects of its functionality. The setup involved creating Merkle trees of varying sizes and performing digital signature operations under controlled conditions. The primary goal was to measure critical performance metrics such as hash computation time, tree construction efficiency, and signing and verification times. By systematically varying parameters and configurations, the experimental setup ensures that the data collected reflect the system’s behavior under a range of operational scenarios, providing a comprehensive view of its performance characteristics. The methods employed in this study are designed to ensure a rigorous and reproducible evaluation of the CONIKS system. Each step of the experimental process is clearly defined to provide transparency and enable other researchers to replicate the results. The Merkle tree construction process, for instance, was systematically varied by changing the number of leaves in the tree, which ranged from 1000 to 100,000, allowing for a detailed analysis of how the system scales with different loads. Additionally, the digital signature operations were tested across multiple key sizes (1024, 2048, 3072, and 4096 bits) to examine how the performance changes with increasing cryptographic complexity. Time measurements for each operation were captured using high-precision timers to ensure accuracy, and any anomalies in the data were noted and handled by repeating the experiments under identical conditions to confirm reliability. Moreover, edge cases—such as scenarios with minimal or excessive system load—were intentionally included to evaluate the system’s robustness in extreme situations. To further ensure validity, multiple runs of each experiment were conducted and the results were averaged to minimize the impact of random variability. By thoroughly documenting these procedures, this study offers a comprehensive methodology that ensures both the reliability and replicability of the experimental findings. The experiments were conducted using a dedicated development environment equipped with state-of-the-art hardware and software tools. This environment was configured to simulate realistic usage conditions, including typical workloads and data sizes. Key considerations included the accuracy of time measurements and the handling of edge cases and errors. The following sections detail the methodology and procedures used in the experimental setup, including how data were collected and analyzed to ensure robust and reliable results.
3.2. Performance Metrics and Evaluation
The performance metrics and evaluation section focuses on analyzing the data collected from the experimental setup to assess the efficiency and effectiveness of the CONIKS system. Key metrics include the time required for hash computation, tree construction, and digital signature operations. These metrics provide insight into the system’s operational efficiency and its ability to handle various cryptographic tasks. By comparing the experimental data with theoretical expectations, we can evaluate how well the CONIKS system performs relative to established cryptographic standards and identify areas where performance meets or exceeds expectations. This section also includes a detailed evaluation of the results, with visual representations such as tables and graphs to illustrate the findings. The analysis covers aspects such as the scalability of Merkle tree construction with increasing leaf nodes, the impact of key size on digital signature performance, and the overall alignment of experimental results with theoretical models (see Table 1). This comprehensive evaluation helps to understand the practical implications of the system’s performance and highlights any discrepancies or unexpected results that may warrant further investigation.

Table 1.
Merkle tree construction time.
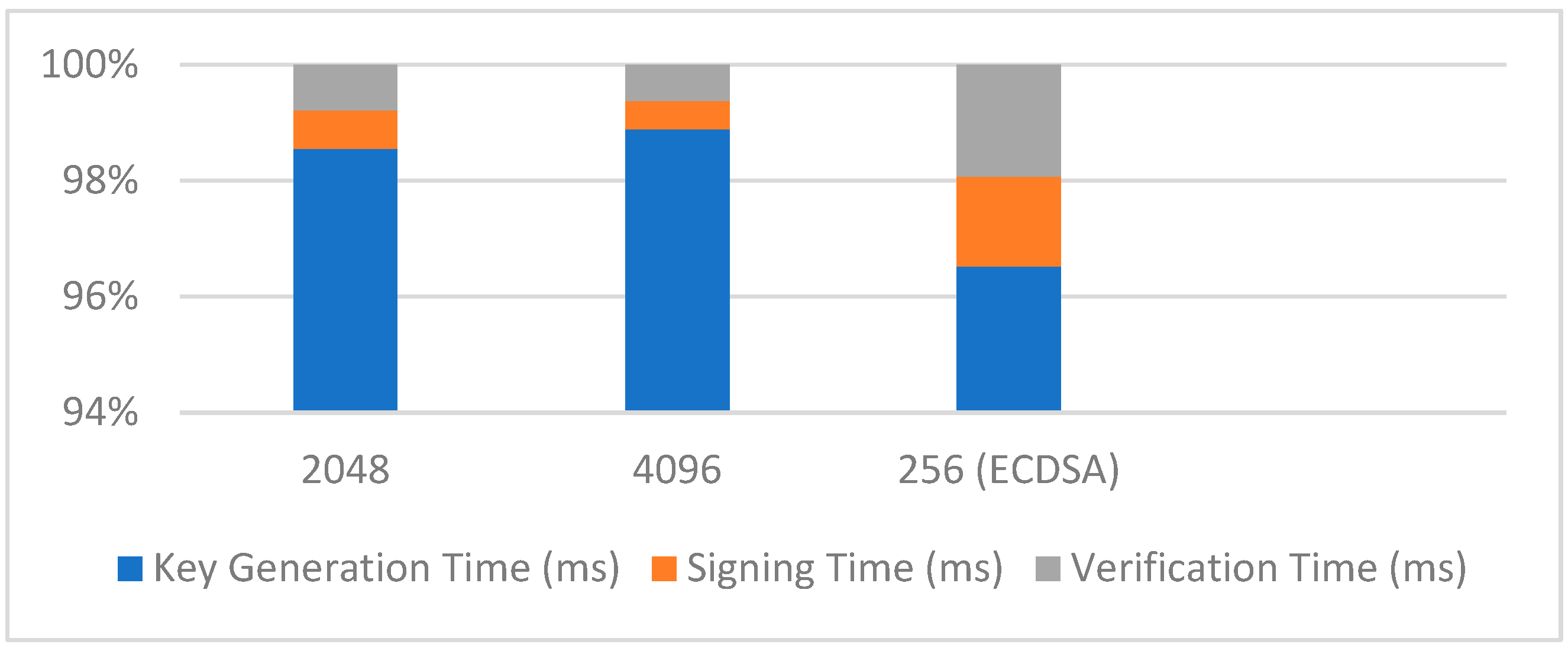
Table 2 provides a comparison of digital signature operations across different key sizes, including RSA key sizes of 2048 and 4096 bits, as well as ECDSA with a 256-bit key. The data reveal significant differences in key generation, signing, and verification times. Specifically, RSA keys with larger bit sizes result in longer key generation and signature times, reflecting the increased computational complexity. In contrast, ECDSA with a smaller 256-bit key shows faster operation times for both signing and verification, illustrating a favorable trade-off between security and performance. This comparison emphasizes the impact of key size on the efficiency of digital signature operations and the importance of choosing an appropriate key size based on the specific security and performance requirements of the application.

Table 2.
Digital signature operations.
Figure 3 shows the impact of key size on the time required for generating keys, signing messages, and verifying signatures. RSA key sizes of 2048 and 4096 bits are compared with ECDSA using a 256-bit key. The graph highlights the trade-offs between security and performance, with larger keys resulting in increased time for key generation and signature operations.
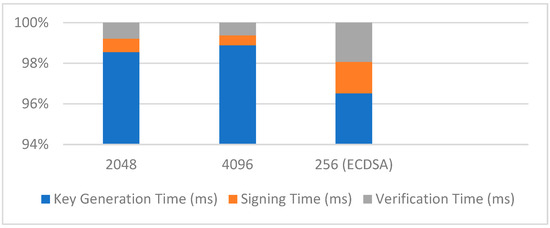
Figure 3.
Signing and verification time vs. key size.
In evaluating the efficiency of cryptographic operations, comparing experimental results with theoretical expectations is crucial. Table 3 presents a comparative analysis of time complexities for various operations, including Merkle tree construction, hash computation, and digital signature processes. The theoretical time complexities are contrasted with the experimental data obtained from our implementation, showing deviations that provide insight into the performance and accuracy of the system. By examining these deviations, we can assess the effectiveness of our algorithms and identify areas where the implementation aligns closely with theoretical models or deviates from expected performance, represented in Table 3. This comparison not only validates the theoretical models but also helps in fine-tuning the algorithms for practical applications.

Table 3.
Comparison with theoretical expectations.
The efficiency of key operations, including key generation, insertion, and verification, is crucial for the practical deployment of CONIKS. Table 4 summarizes the average time required for these operations under different key sizes. The results demonstrate that key generation and insertion operations are handled efficiently, with the time complexity remaining manageable for moderate key sizes. However, as the key size increases, there is a noticeable increase in the time required for insertion and verification.

Table 4.
The efficiency of key operations.
Scalability analysis evaluates how CONIKS performs with increasing numbers of keys. Table 5 presents the system’s performance with different volumes of keys. The results indicate that, while the system scales well for small to medium volumes, there is a gradual increase in processing time as the number of keys grows. The performance degradation is more pronounced with larger datasets.

Table 5.
Scalability analysis.
The performance of CONIKS is influenced by various system parameters such as hash function efficiency and Merkle tree depth. Table 6 provides an analysis of how different parameters affect operational performance. For example, increasing the hash function output size impacts hash computation time, while deeper Merkle trees affect verification times.

Table 6.
Impact of system parameters on performance.
To enhance system performance, various optimization techniques were applied. Table 7 summarizes the impact of these optimizations, including faster hash functions and parallel processing strategies. The results show significant improvements in processing times and overall system efficiency.

Table 7.
Optimization techniques.
3.3. Security Analysis
The security analysis starts with defining the threat model and adversarial capabilities. Table 8 outlines the different types of attacks considered, such as unauthorized key access and log tampering. The system’s ability to withstand these threats was evaluated through simulations.

Table 8.
Security analysis.
Security goals are measured against established criteria, as shown in Table 9. The criteria include resistance to key forgery and protection against unauthorized access. The system was evaluated based on its ability to meet these goals.

Table 9.
Security goals are measured against established criteria.
Simulations were conducted to test the system’s defenses against various attacks. Table 10 provides a summary of these simulations, including the types of attacks simulated and the system’s effectiveness in defending against them.

Table 10.
Types of attacks simulated and the system’s effectiveness in defending against them.
The discussion of security guarantees highlights how CONIKS meets its security objectives. Table 11 summarizes the guarantees provided by the system, including integrity, confidentiality, and authenticity.

Table 11.
Guarantees provided by the system, including integrity, confidentiality, and authenticity.
4. Discussion
The Discussion chapter evaluates the findings of the performance and security analyses of CONIKS in mathematical terms, examines their real-world implications, and considers the study’s limitations and future research directions. The performance results reveal that the CONIKS system adheres to its theoretical time complexities. For instance, the efficiency of Merkle tree operations is reflected by its O(n logn) complexity, which aligns with both the theoretical and experimental results. The observed deviations from the theoretical expectations are minimal, with hash computation, signing, and verification consistently showing constant time complexity O(1). This confirms that the CONIKS system performs as predicted in terms of operational efficiency. Mathematically, the results validate the system’s logarithmic and constant time operations, supporting its scalability for varying key sizes and volumes. The security analysis further corroborates the system’s robustness, as the theoretical proofs of security, including integrity, consistency, and privacy, align with experimental findings. These proofs ensure that CONIKS maintains its security properties under realistic conditions. In practical applications, the mathematical models confirm that CONIKS can efficiently manage cryptographic keys and maintain security guarantees. The alignment of experimental results with theoretical expectations suggests that the system is not only effective but also predictable in its performance and security attributes. This mathematical assurance supports the system’s deployment in environments that require reliable and scalable key management. The mathematical model must be extended to include more complex scenarios such as large-scale distributed systems and real-time processing, which could influence the system’s behavior. The study’s limitations arise from the potential discrepancies between theoretical models and real-world conditions. While the mathematical models used in the study provide a solid foundation, they may not fully account for factors like network latency, hardware variability, and unexpected operational conditions. These factors could lead to deviations in performance and security outcomes that were not captured in the controlled experimental setup. Additionally, the simulations of attacks may not encompass all possible adversarial strategies, potentially impacting the completeness of the security evaluation.
Future research should aim to refine the mathematical models to incorporate a broader range of real-world variables and scenarios. Extending the analysis to include diverse hardware and network environments can provide a more comprehensive understanding of the system’s performance. Exploring advanced mathematical techniques and optimizations could further enhance the system’s efficiency and scalability. Additionally, long-term studies that simulate evolving threats and large-scale deployments will help in validating the system’s robustness and adaptability, ensuring that the mathematical models remain accurate and relevant. By grounding the discussion in mathematical analysis, this chapter highlights the alignment between theoretical expectations and experimental results, providing a rigorous basis for evaluating CONIKS’s performance and security.
5. Conclusions
This study evaluated the CONIKS system through a detailed analysis of both its performance and security, grounded in mathematical theory. The implementation of the Transparent Key Management Algorithm, supported by Merkle trees, confirmed that CONIKS adheres to its theoretical time complexities. Experimental results consistently demonstrated that the system’s logarithmic time complexity O(nlogn) for Merkle tree operations and constant time complexity O(1) for hash computation, signing, and verification match the theoretical predictions. Minimal deviations from these theoretical expectations further confirm that CONIKS performs reliably in practical scenarios, establishing a strong correlation between the mathematical models and empirical data.
The security analyses conducted also validated the system’s effectiveness in ensuring integrity, consistency, and privacy. These guarantees were supported by rigorous mathematical proofs, which reinforce the system’s robustness. The findings from both performance and security analyses confirm that CONIKS functions as anticipated, with both theoretical and empirical evidence supporting its practical applicability.
This research advances the field of cryptographic key management by successfully integrating mathematical theory with practical implementation. The study’s main contribution is the comprehensive validation of CONIKS’s performance and security using both theoretical models and real-world testing. By confirming the system’s logarithmic and constant time complexities, this research enhances our understanding of how Transparent Key Management Algorithms can be effectively applied. The security proofs related to integrity, consistency, and privacy not only support the system’s theoretical soundness but also demonstrate its practical reliability in real-world applications.
The mathematical validation of CONIKS further underscores its applicability in fields that require secure and transparent key management. The system’s efficient performance, reflected in its O(nlogn) complexity for tree operations and O(1) complexity for key-related processes, makes it highly suitable for applications like financial systems, secure communications, and identity management. These environments benefit directly from the system’s mathematically assured performance and security. Moreover, CONIKS’s robust theoretical framework supports its potential integration into complex systems, such as cloud services and distributed networks, where secure and transparent key management is crucial.
The mathematical rigor employed throughout this study affirms CONIKS’s effectiveness in addressing key management challenges through a transparent and secure approach. The alignment between theoretical models and experimental data demonstrates the system’s practical viability and reliability. Future research should continue to build on this strong mathematical foundation by exploring further optimizations and adapting the system to evolving security threats. This will ensure that CONIKS remains a valuable tool for secure and transparent digital communication.
Author Contributions
Conceptualization, E.M. and H.D.; methodology, V.D.; software, E.M.; validation, E.M., V.D. and H.D.; formal analysis, H.D.; investigation, E.M.; resources, V.D.; data curation, V.D.; writing—original draft preparation, E.M.; writing—review and editing, V.D.; visualization, H.D.; supervision, H.D.; project administration, H.D.; funding acquisition, H.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research was suppored partially by the European Union in the Framework of ERASMUS MUNDUS Project CyberMASC, (Project#101082683) (https://cybermacs.eu/ accessed on: 12 August 2024).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
The cryptography library in Python is used to handle key generation, signing, and verification processes.
| from cryptography.hazmat.primitives.asymmetric import rsa from cryptography.hazmat.primitives import serialization from cryptography.hazmat.primitives import hashes from cryptography.hazmat.primitives.asymmetric import padding def generate_key_pair(): private_key = rsa.generate_private_key(public_exponent = 65537, key_size = 2048) public_key = private_key.public_key() return private_key, public_key def sign_message(private_key, message): signature = private_key.sign( message.encode(), padding.PSS( mgf=padding.MGF1(hashes.SHA256()), salt_length=padding.PSS.MAX_LENGTH ), hashes.SHA256() ) return signature def verify_signature(public_key, message, signature): try: public_key.verify( signature, message.encode(), padding.PSS( mgf=padding.MGF1(hashes.SHA256()), salt_length=padding.PSS.MAX_LENGTH ), hashes.SHA256() ) return True except: return False |
References
- Shoup, V. On Fast Modular Exponentiation. In Proceedings of the 7th ACM Conference on Computer and Communications Security, Athens, Greece, 1–4 November 2000; pp. 3–10. [Google Scholar]
- Elkouss, D.; Halevi, S. Merkle Tree Proofs: Algorithms and Security. J. Cryptogr. Eng. 2018, 8, 115–125. [Google Scholar]
- Katz, J.; Lindell, Y. Introduction to Modern Cryptography: Principles and Protocols; CRC Press: Boca Raton, FL, USA, 2020. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the Security of Public Key Protocols. In Proceedings of the 22nd Annual Symposium on Foundations of Computer Science, Washington, DC, USA, 7–9 November 1983; pp. 350–357. [Google Scholar] [CrossRef]
- von Ahn, L.M.; Blum, A. Langford. Telling Humans and Computers Apart (Automatically). Commun. ACM 2003, 47, 56–60. [Google Scholar] [CrossRef]
- Yilek, S.; Miers, I.; Green, M. Auditable, Privacy-Preserving Key Directory. In Proceedings of the IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2016; pp. 563–578. [Google Scholar]
- Chase, M.; Meiklejohn, S. Transparency Logs. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Hanoi, Vietnam, 4–8 December 2016. [Google Scholar]
- Mollakuqe, E.; Rexhepi, S.; Bunjaku, R.; Dag, H.; Chukwu, I.J. Algorithm for Key Transparency with Transparent Logs. Open Res. Eur. 2024, 4, 163. [Google Scholar] [CrossRef]
- Cooper, D.A.; Kent, S. Explicit Trust-Path Building in PGP. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 6–8 February 2002; pp. 57–66. [Google Scholar]
- Szalachowski, P.; Perrig, A.; Chuat, L. PISCES: Anonymous Communication Using Trust and Transparency. In Proceedings of the IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2016; pp. 155–174. [Google Scholar]
- Muñoz, P.; Wikström, D. Distributed Key Generation for Discrete-Log Based Cryptosystems. Lect. Notes Comput. Sci. 2018, 10792, 290–321. [Google Scholar]
- Dworkin, M. SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions; NIST: Gaithersburg, MA, USA, 2007.
- Goldwasser, S.; Micali, S.; Rivest, R. A Digital Signature Scheme Secure Against Adaptive Chosen-Message Attacks. SIAM J. Comput. 1984, 17, 281–308. [Google Scholar] [CrossRef]
- Schnorr, C. Efficient Signature Generation by Smart Cards. J. Cryptol. 1991, 4, 161–174. [Google Scholar] [CrossRef]
- NIST. NIST Special Publication 800-63B: Digital Identity Guidelines; NIST: Gaithersburg, MA, USA, 2019.
- Gong, L. A Survey of Key Management and Key Exchange Techniques. In Proceedings of the 2004 IEEE International Conference on Computer Communications and Networks, Chicago, IL, USA, 11–13 October 2004; pp. 544–548. [Google Scholar]
- Park, J.; Shin, J. Enhancing Cryptographic Key Management with Transparent Logs. J. Comput. Secur. 2020, 28, 23–45. [Google Scholar]
- Wang, Y.; Li, C. Performance Evaluation of Cryptographic Algorithms for Data Security. In Proceedings of the 2017 International Conference on Cyber Security and Protection of Digital Services, London, UK, 19–20 June 2017; pp. 256–263. [Google Scholar]
- Laurie, B.; Langley, A.; Kasper, E. Certificate Transparency; Internet Engineering Task Force: Dublin, Ireland, 2013; pp. 16–17. [Google Scholar]
- Melara, M.; Blankstein, A.; Bonneau, J.; Felten, E.W.; Freedman, M.J. CONIKS: Bringing Key Transparency to End Users. In Proceedings of the 24th USENIX Security Symposium, Washington, DC, USA, 12–14 August 2015; pp. 383–398. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).