Featured Application
This work is relevant in the context of multi-user LiDAR applications where multiple LiDARs may be active in the same environment simultaneously. Automotive safety, driving assistance, robotic navigation, and automated industrial vehicles are a few examples of scenarios where interference among concurrent LiDARs quickly becomes a critical issue. In those applications, being able to guarantee interference-free LiDAR operation is a necessary step towards the realization of safe and reliable functions.
Abstract
This paper describes an optical interference suppression scheme that allows flash light detection and ranging (LiDAR) imagers to run safely and reliably in uncontrolled environments where multiple LiDARs are expected to operate concurrently. The issue of optical interference is a potential show-stopper for the adoption of flash LiDAR as a technology of choice in multi-user application fields such as automotive sensing and autonomous vehicle navigation. The relatively large emission angle and field of view of flash LiDAR imagers make them especially vulnerable to optical interference. This work illustrates how a time-correlated single-photon counting LiDAR can control the timing of its laser emission to reduce its statistical correlation to other modulated or pulsed light sources. This method is based on a variable random delay applied to the laser pulse generated by LiDAR and to the internal circuitry measuring the time-of-flight. The statistical properties of the pseudorandom sequence of delays determines the effectiveness of LiDAR resilience against unintentional and intentional optical interference. For basic multi-camera operation, a linear feedback shift register (LFSR) was used as a random delay generator, and the performance of the interference suppression was evaluated as a function of sequence length and integration time. Direct interference from an identical LiDAR emitter pointed at the same object was reduced up to 50 dB. Changing integration time between 10 ms and 100 ms showed a marginal impact on the performance of the suppression (less than 3 dB deviation). LiDAR signal integrity was characterized during suppression, obtaining a maximum relative deviation of the measured time-of-flight of 0.1%, and a maximum deviation of measurements spread (full-width half-maximum) of 3%. The LiDAR signal presented an expected worst-case reduction in intensity of 25%.
Keywords:
LiDAR; flash LiDAR; TCSPC; optical interference; interference; multicamera; multiuser; SPAD; TDC; automotive; laser; optics; ADAS 1. Introduction
Light detection and ranging (LiDAR) is rapidly emerging as a key technology in automotive sensing, both for advanced driver assistance systems (ADAS) and as an enabler of fully autonomous driving [1]. The use of LiDAR as a complement to existing technologies, such as radar, ultrasonic range finding, thermal imaging, and image processing, is rapidly changing the landscape of advanced automotive sensor systems. The joint use of heterogeneous sensors, known as sensor fusion, promises to facilitate the safe implementation of level 3 and level 4 autonomy [2,3,4], and to be an enabling factor of fully autonomous driving [5]. Even outside the automotive field, where the reliable and safe navigation of autonomous or semi-autonomous machines is needed (e.g., advanced robotics, automated guided vehicles, factory automation, simultaneous localization and mapping, and drones), LiDAR is proving itself to be a valid complement to existing navigation sensors [6,7].
It is expected that the use of LiDAR in navigation applications will rise steadily in the future [1]. The widespread adoption of LiDAR in uncontrolled, multi-user environments will soon bring the problem of mutual optical interference to the fore. This paper describes an interference suppression scheme specifically designed for flash LiDAR cameras operating in time-correlated single-photon counting (TCSPC) mode, but the same principles are applicable to a wide variety of pulsed LiDAR techniques. The suppression scheme, referred to as FLISS (Flash LiDAR Interference Suppression Scheme) in the remainder of this paper, allows a TCSPC flash LiDAR to operate in an environment shared with other LiDARs without suffering from optical interference. FLISS does not require any form of coordination between cameras and can in principle reject optical interference generated by any type of device.
The paper will first present an overview of existing techniques for LiDAR interference management and relevant literature on the topic. A more formal description of interference in the context of flash LiDAR imagers will then be provided, followed by a presentation of the FLISS method. The paper will conclude with a section on experimental results and future directions.
2. TCSPC LiDAR
A TCSPC LiDAR is a type of direct time-of-flight (d-ToF) sensor. In direct time-of-flight (d-ToF), the distance z to an object is estimated by measuring the round trip time of an electromagnetic pulse (usually infrared light) from a suitable emitter contiguous to the detector to the object, according to the d-ToF relation
where c is the travel speed of the chosen electromagnetic wave in the propagation medium (Figure 1).
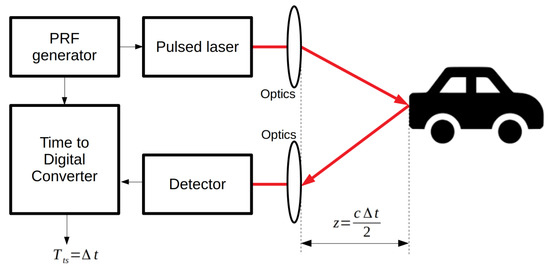
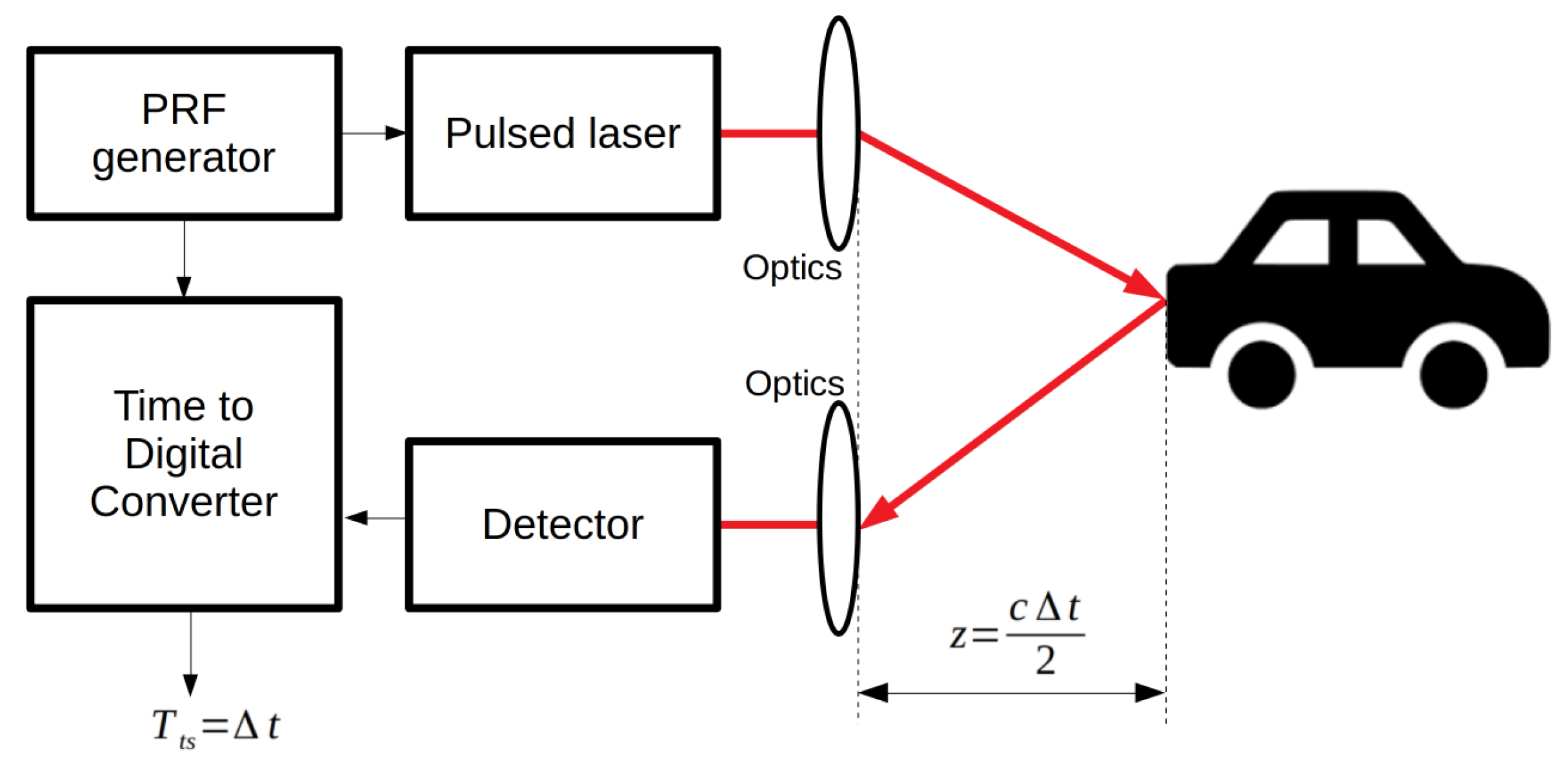
Figure 1.
Schematic representation of a time-correlated single-photon counting (TCSPC) imager. A dedicated digital block generates the control signal for a pulsed laser. The same control signal is used by the time-to-digital converter to start measuring time synchronously to the generation of the laser pulse. The laser pulse travels to the object to be imaged, and it is diffused back to the sensor. On the sensor, it is detected by suitable pixels capable of discriminating the time of arrival of the pulse. The time of arrival event is sent to the time-to-digital converter to produce a digital representation of the duration of the time interval between laser emission and photon detection.
In optical TCSPC imaging (especially 3D range finding) emitters are usually chosen among Q-switched lasers [8] or vertical-cavity surface-emitting laser (VCSEL) arrays [9], due to their fast switching speeds.
Single-photon detectors such as single-photon avalanche diodes (SPADs) are used on the receiver side to detect the time of arrival of individual photons. Photoelectrons generated by the absorption of individual photons are accelerated by the strong electric field in the diode and undergo an avalanche multiplication process that produces a macroscopic, measurable current through the device [10]. Events detected by the SPAD pixels are often timed on-chip using combinations of time-to-analog converters (TACs) and analog-to-digital converters (ADCs) [11,12], or time-to-digital converters (TDCs) [13,14,15], to produce a digital representation of the time of arrival of each detected photon, called a timestamp. Each timestamp is a measure of the time of arrival of a photon detected by the pixel relative to the generation time of the laser pulse , according to the relation
Given it is impossible to discriminate between the possible origins of each individual event produced by a SPAD pixel (thermal noise, ambient light, and active signal being the most prominent sources), TCSPC LiDAR imagers often repeat the same timestamp measurement 10–10,000 times. All measured timestamps undergo simple statistical processing to extract the relevant features of the useful signal. Ambient photon detections and dark counts (including thermally induced events and trap-assisted tunneling) occur at random times and are not correlated to the active signal. Active signal photons, on the other hand, are emitted synchronously to the activation instant of the TDC, and therefore, their time of arrival at the sensor is correlated and dependent on their time-of-flight (ToF). If plotted in a histogram, all detected timestamps will produce a noisy plateau representing uncorrelated events (ambient light and internal detector noise) and a peak constituted by the time of arrival of signal photons. A typical TCSPC histogram is shown in Figure 2.
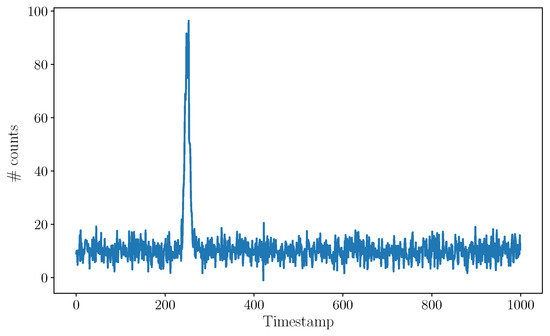
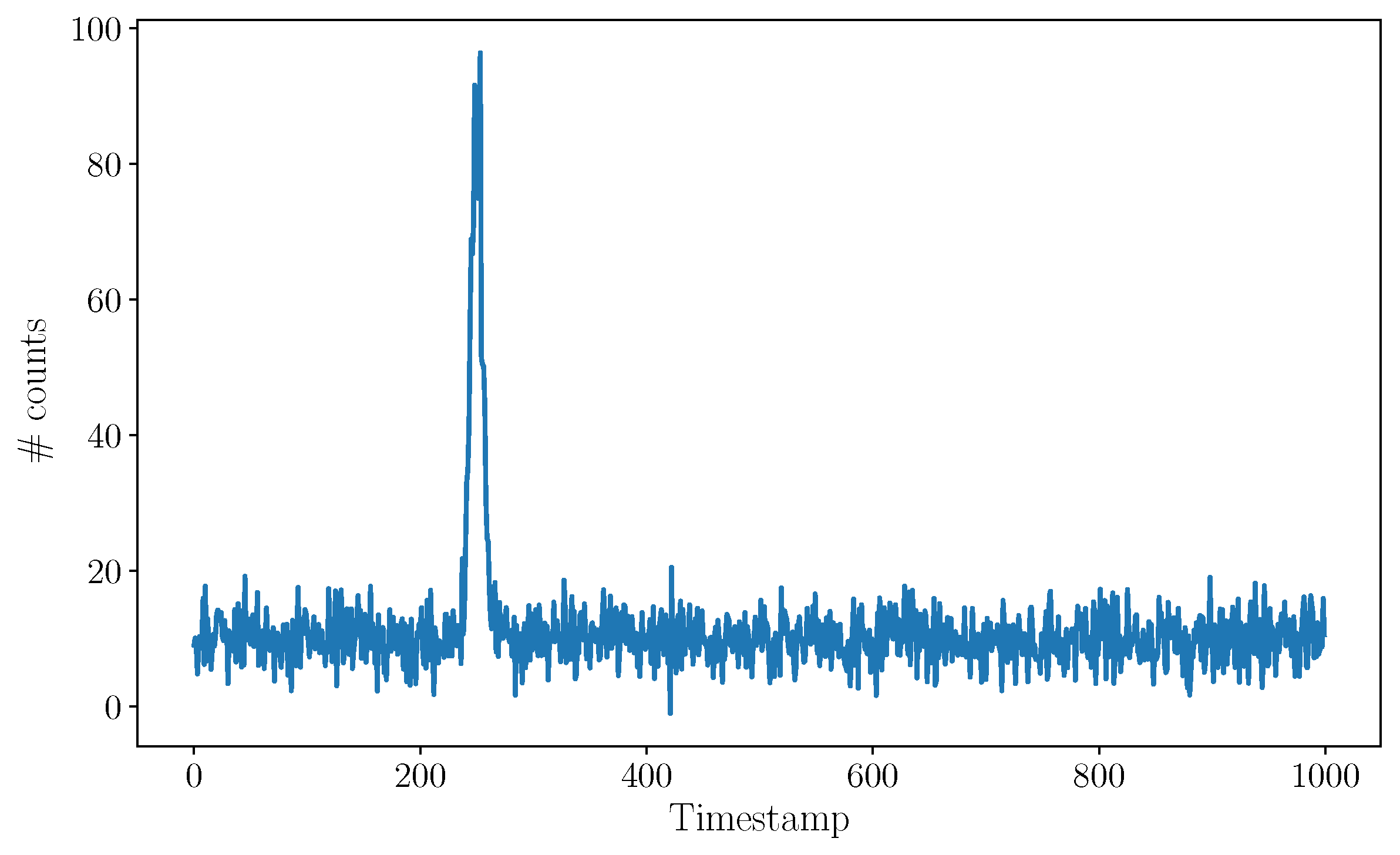
Figure 2.
Illustrative example of a TCSPC histogram. The position of the peak correlates to the distance of the imaged object. The level of the background gives a measure of the intensity of ambient light and of internal noise in the detector.
3. Related Work
Several contributions have been published on topics that are closely related to LiDAR optical interference suppression. It is challenging, however, to pinpoint one main line of research on the topic, due to the variety of technologies and techniques available for 3D imaging and range finding.
Signal-to-noise ratio (SNR) improvement is often seen as a necessary step towards proper rejection of extraneous interference. Matched filter approaches [16] and customized digital post-processors [17] have been proposed to achieve high SNR of the LiDAR signal in avalanche photo-diode (APD)-based sensors.
One special case of LiDAR interference that has been studied extensively is the multi-path interference (MPI) [18,19,20,21], which is a LiDAR system interfering with itself through a plurality of optical paths, either as a consequence of the complex geometry of the imaged scene or the presence of semi-transparent or specular objects. Published approaches to MPI suppression include the use of multiple modulation frequencies in indirect time-of-flight (i-ToF) [22], sometimes in conjunction with compressive sensing to reconstruct multi-path reflections [23].
Proper multi-camera interference occurs when multiple LiDAR sensors operate in the same environment. Several techniques borrowed from telecommunications technology and signal processing theory are known to minimize the interference between multiple LiDAR cameras sharing the same communication channel: space-division multiple access (SDMA), frequency-division multiple access (FDMA), wavelength-division multiple access (WDMA), time-division multiple access (TDMA), and code-division multiple access (CDMA).
The SDMA method requires spatial separation of the LiDAR cameras so that their fields of view do not overlap. Each camera monitors a well-defined portion of space, and its emission never overlaps with the field of view of any other camera in the same environment. SDMA is scalable to an arbitrary number of cameras but is unsuitable for use in uncontrolled environments without considerable coordination between all the cameras.
In FDMA, each LiDAR camera must be assigned a unique operating frequency, which is represented by the pulse repetition frequency (PRF) in d-ToF. When operating at different PRFs, two LiDAR systems will not interfere with one another and will appear to each other as uncorrelated noise. The LiDAR PRFs must be separated enough to guarantee the minimization of systematic errors at short integration times, thereby limiting the maximum number of parallel channels. It should be noted that LiDAR imagers based on FDMA require coordination in uncontrolled environments in order to reassign the PRFs in the case of collision.
A popular option for optical devices such as LiDAR imagers is WDMA. WDMA mandates the use of multiple, non-overlapping optical channels centered on different wavelengths, separated on the receiver side by means of appropriate narrow-band optical filters. Such systems must handle the relatively low number of available channels in the operating band, which is limited by eye safety limits in the visible range, the bandwidth of the optical filter, the spectral purity of the emitter, and by the spectral sensitivity of the detector.
In TDMA, concurrent imagers are assigned unique, non-overlapping time intervals in which they are allowed to emit. TDMA side-steps the issue of interference by guaranteeing that at most one camera is active at any given time. The trade-off is of course the need to centrally coordinate all cameras (although peer-to-peer approaches are also possible).
The CDMA technique achieves interference suppression by borrowing alternative modulation schemes from spread-spectrum telecommunication systems. The basic idea of CDMA for LiDAR is that the light signal produced by each camera is shaped according to a specific digital or analog modulation scheme that allows the emitter to recognize its own signal over noise and interference. Detection and recognition are often performed by correlating the measured (noisy) signal with a specific correlation target function. The use of pseudorandom noise in i-ToF [24] falls into this broad category, as do phase-shift keying (PSK) modulation in TCSPC LiDARs [25] and the use of optical orthogonal codes [26,27].
Related research has been published on the topic of the identification and authentication of a LiDAR signal as one’s own by means of side-channel fingerprinting and advanced encryption standard (AES) encryption [28]. While unsuitable for solving the multi-camera interference problem per se, these techniques are important steps towards comprehensive security of the LiDAR channel.
4. LiDAR Optical Interference
This section provides some required definitions and a description of optical interference in the case of TCSPC LiDAR imagers.
In the context of this paper, a victim is a TCSPC LiDAR system potentially subject to optical interference. We define optical interference as any optical signal possessing the following properties.
- The signal is modulated or pulsed, so as to appear distinctly different in its temporal evolution from ambient light or detector noise in the victim.
- The signal is actively generated by a third party, potentially a TCSPC LiDAR of the same nature as the victim.
- The signal is detected by the victim.
The saturation of the detector is not considered as optical interference. Issues related to pile-up distortion and saturation, including strong sunlight and the intentional blinding of the victim, remain open and should be addressed by different methods.
A third-party device able to generate optical interference is defined as an aggressor, regardless of the intent of the interference action. Figure 3 illustrates the concept of optical interference between two cameras imaging the same object.
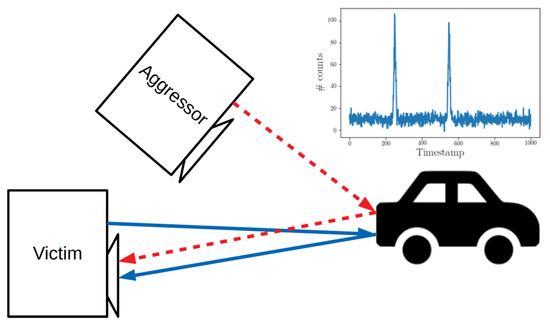
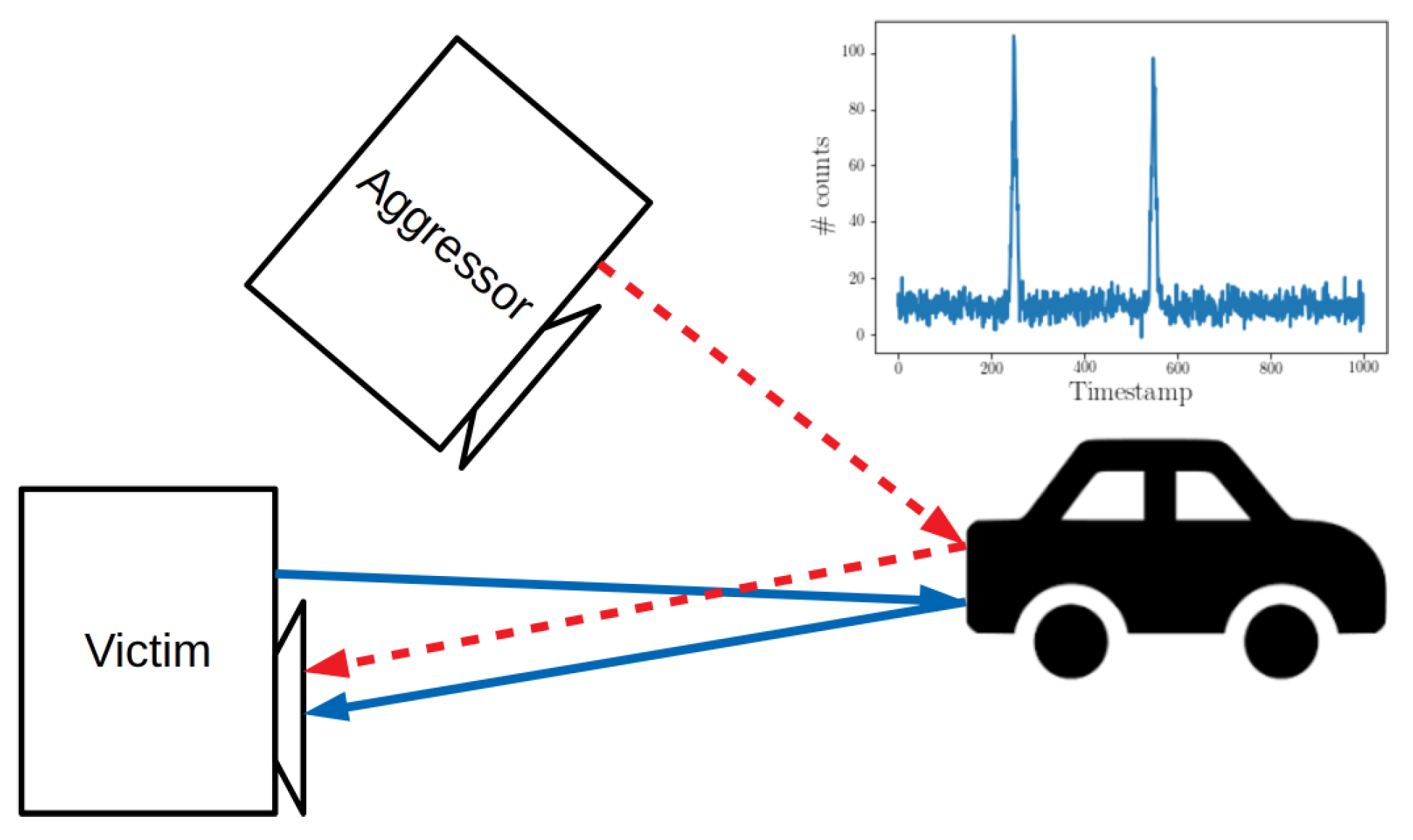
Figure 3.
Illustrative example of optical interference. The victim imager emits and detects reflected laser pulses along the blue arrows. The emission of a second camera active in the same environment (the aggressor) is also detected by the victim. If the two trains of pulses are sufficiently similar in timing, duration, and repetition frequency, then the victim would have no way of distinguishing the origin of each individual pulse, the time-of-flight (ToF) to the target object being unknown. In this case, the victim will construct a histogram containing two peaks, which is a source of potential ambiguity.
The worst possible case for a TCSPC LiDAR victim is to operate in an environment with an aggressor that uses the same functional parameters (emission wavelength, pulse repetition frequency, and pulse duration). In this case, the photons of the aggressor will appear as correlated to the victim. The corresponding pixel events will build up in a second histogram peak with an unknown delay that is dependent on the phase shift between the PRFs of the two devices and the difference in length between the victim–target–victim and aggressor–target–victim optical paths.
Once in the histogram, the aggressor peak is indistinguishable from the victim’s peak. This uncertainty in the interpretation of the LiDAR data is a source of risk as it is impossible to differentiate between a real object and an artifact of interference.
5. Interference Suppression
The FLISS technique allows a TCSPC LiDAR to operate safely and free from optical interference in the presence of an arbitrary number of aggressors without requiring any central coordination or communication between devices.
Optical interference suppression is achieved by the addition of discrete random delays to the generation of the laser pulse of the victim. The interval between two laser pulses of the victim then becomes
where is the interval between two consecutive laser pulses of the victim, is the nominal pulse repetition frequency of the victim, is the period of laser repetition at the nominal , and is a discrete random variable describing a positive delay with a different value for every generated laser pulse. Under this definition, the victim implementing FLISS will operate at an effective average PRF that is lower than the nominal PRF and is defined as
where represents the expected value of the random variable .
The next laser pulse is therefore fired at , where is the time at which the laser would normally have fired according to its nominal PRF. Due to the delay in the firing of the laser, all signal-related pixel activity will also be delayed by an equal amount (). The statistics of events induced by ambient light and noise won’t change as a consequence of the introduction of . The final timestamp is calculated as the difference of the previous quantities, therefore
It is shown that the victim is in principle not affected by , regardless of its value and temporal evolution. The delay is chosen randomly in a bounded interval , where is finite.
The absolute timing of the laser pulses generated by the aggressor is not influenced by the random delay , therefore the timestamps generated by the victim from aggressor activity can be defined as
where is the ToF from the aggressor to the victim, passing by the target object. It is shown that each aggressor timestamp is shifted in the victim’s reference frame by an amount equal to the variable quantity , which is not canceled out for the aggressor.
Thanks to the variable nature of , aggressor timestamps can be distributed across the entire measurement range of the victim, effectively decorrelating the aggressor signal. The quality and performance of the decorrelation depend on the statistical properties of the temporal evolution of .
The random delay can be generated in a variety of ways. For simplicity of implementation and explanation, we chose to generate the pseudorandom delays using a well-known linear feedback shift register (LFSR) structure [29,30], exemplified in the high-level diagram of Figure 4. The statistical properties of the pseudorandom sequence generated by an LFSR depend on the register’s length L and on the position of the register feedback taps, defined by the feedback polynomial
where are the feedback coefficients of the LFSR. In particular, we restricted ourselves to the use of LFSRs whose characteristic polynomial, defined as
is primitive. LFSRs with primitive characteristic polynomials generate maximum-length sequences (m-sequences) that guarantee that all possible register combinations will be reached before the sequence repeats.
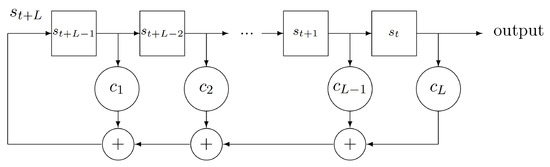
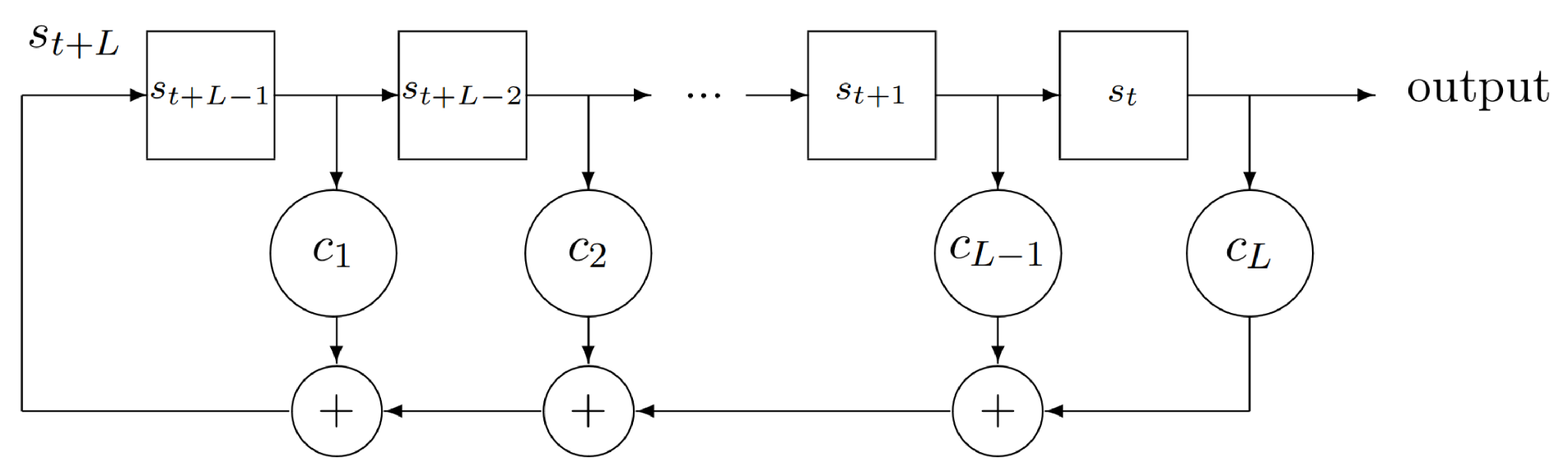
Figure 4.
High-level block diagram of a generic linear feedback shift register of length L. At each clock cycle, the most significant bit (MSB) of the register is set to a linear combination of the outputs of all the L register stages. The coefficients determine which bits are connected to the feedback summing nodes and which ones are not. For a given register length L, the feedback coefficients determine all the properties of the structure, including the length of the pattern being generated by the register.
In our implementation, can be chosen from a finite list of candidate delays steps D defined as
where is the set of all possible states of the LFSR of length L, and is the period of the system clock.
6. Experimental Results
The experimental setup is based on a custom-designed field-programmable gate array (FPGA) board (Figure 5) equipped with a custom SPAD sensor with on-chip TDCs (center) and four independent pulsed VCSEL array illuminators, two of which (lower left and lower right) were used in this work. A conventional webcam has been added to the setup to simplify the optical alignment.
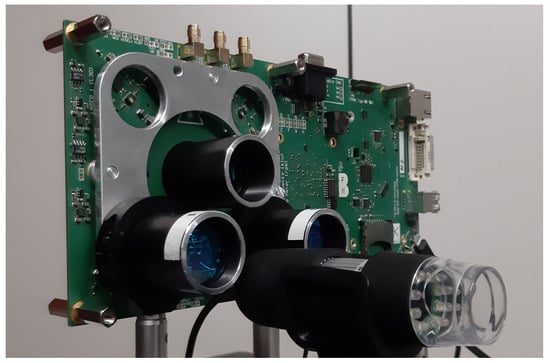
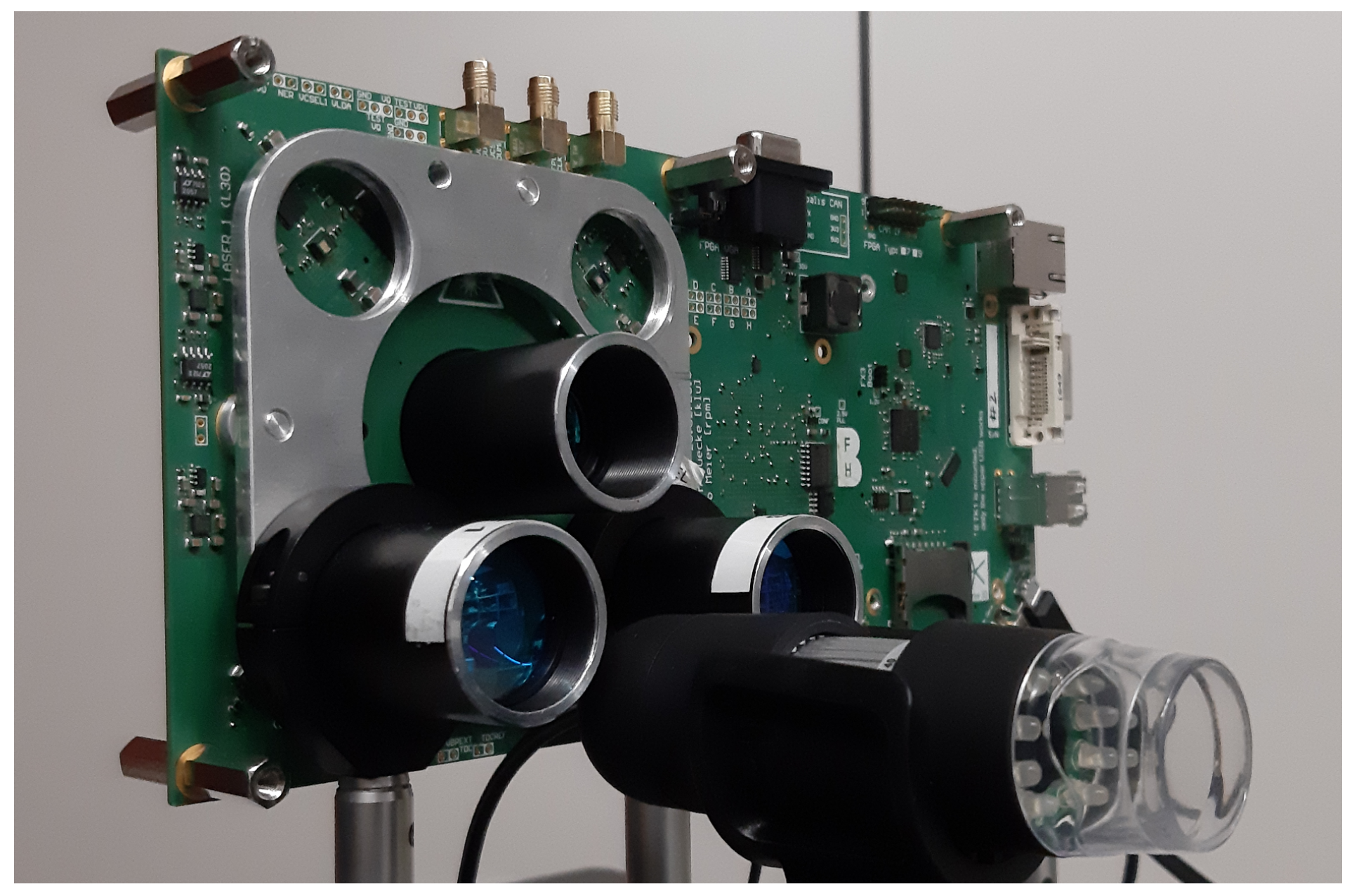
Figure 5.
Picture of the experimental setup. The field-programmable gate array (FPGA) board depicted here hosts a custom single-photon avalanche diode (SPAD) sensor integrated circuit (IC) with integrated time-to-digital converters (TDCs) that was used as the sensor front-end of the victim. Timestamps are transferred to the controlling PC (not shown) without further additional processing. The board is equipped with four identical independent pulsed laser illuminators based on vertical-cavity surface-emitting laser (VCSEL) arrays installed around the detector optics. The two illuminators on the bottom were used for the experiments, one being the illuminator of the victim and the other acting as the aggressor. Both illuminators were controlled by custom firmware running on the FPGA. A conventional USB webcam was also part of the setup and was used to align the setup to the wall we used as the target.
Table 1 summarizes the key specifications of the system, and Figure 6 shows an overview of the high-level architecture of the detector chip.

Table 1.
Summary of the specifications of the system.
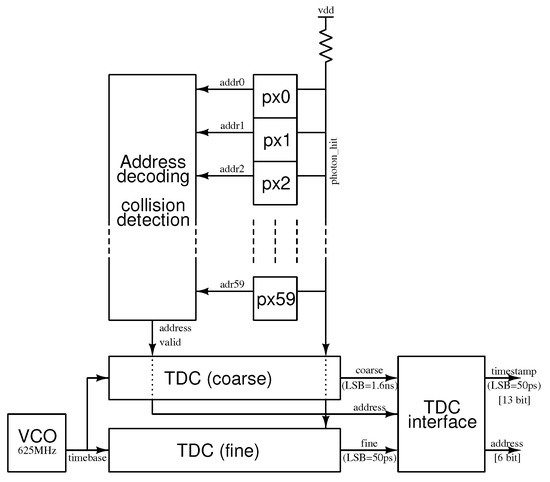
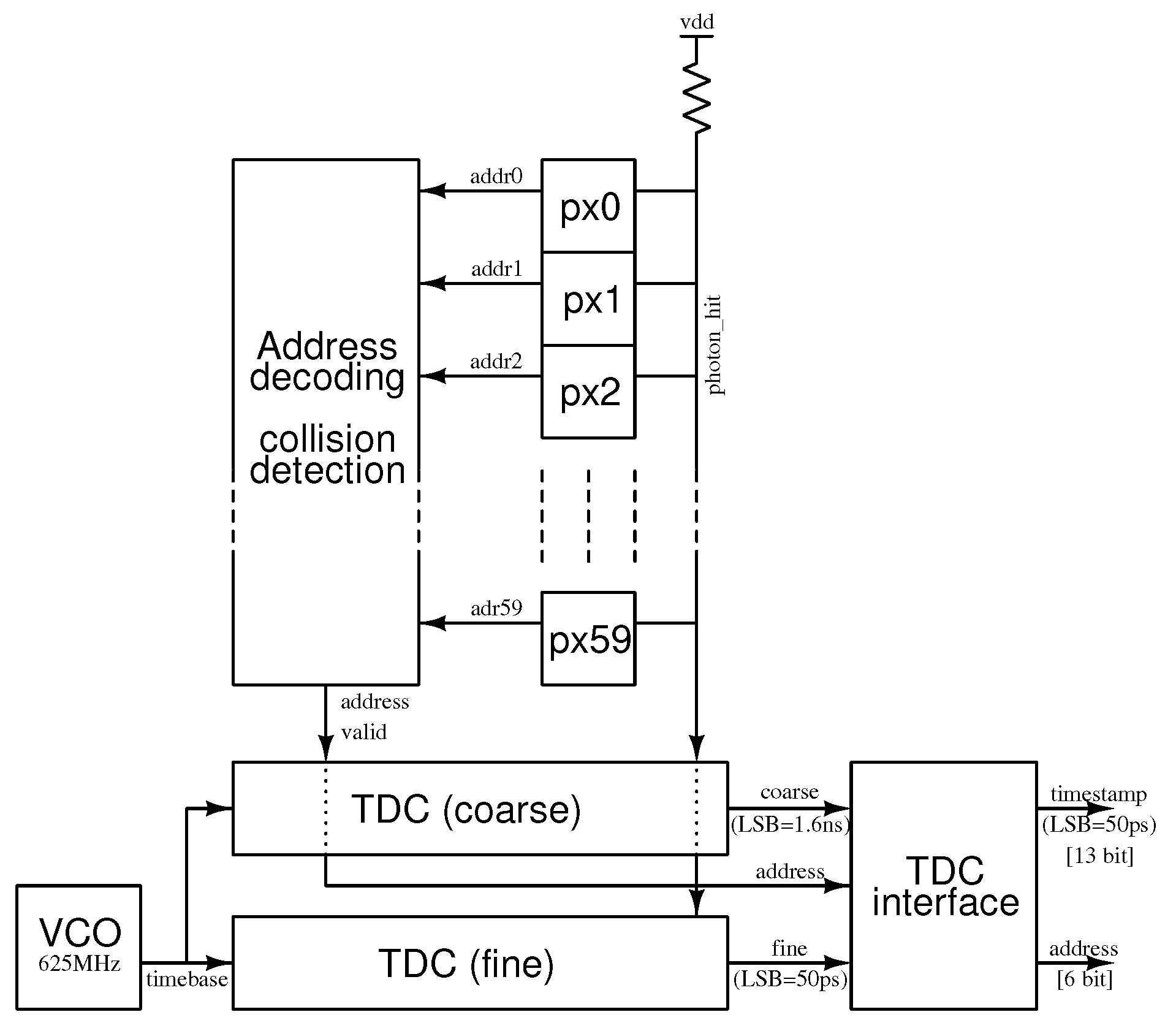
Figure 6.
High-level block diagram of the detector chip. A single active column of 60 pixels shares one output line carrying the photon time of arrival information to a TDC bank underneath. An address decoding and collision detection block allows the TDC bank to identify the pixel that fired last and to determine if two or more pixels tried to access the photon_hit bus at the same time. The TDC uses a 625 MHz frequency generated by an integrated voltage-controlled oscillator (VCO) as a time base. The TDC implements a coarse measurement block that counts the periods of the time base signal (giving a least significant bit (LSB) resolution of 1.6 ns) and a fine measurement block realized as a 32-stage phase interpolator that brings the LSB resolution down to the target 50 ps. A small digital interface block merges the coarse and fine measurements to produce a 13-bit, binary coded timestamp representing the time of arrival of the last detected photon and a 6-bit address identifying the pixel that fired last.
The victim and the aggressor were installed in front of the same target (a white wall) and operated indoors. When active, the aggressor was assigned a fixed time offset to emulate a relative distance to the victim. The aggressor was configured to operate at the effective PRF of the victim to actively try to inject an artifact into the victim’s histogram. All measurements were taken from a single pixel and a single TDC of the sensor. For each experiment, 300 identical acquisitions were recorded to capture statistical fluctuations in the data. Unless otherwise noted, all acquisitions were repeated for three values of integration time .
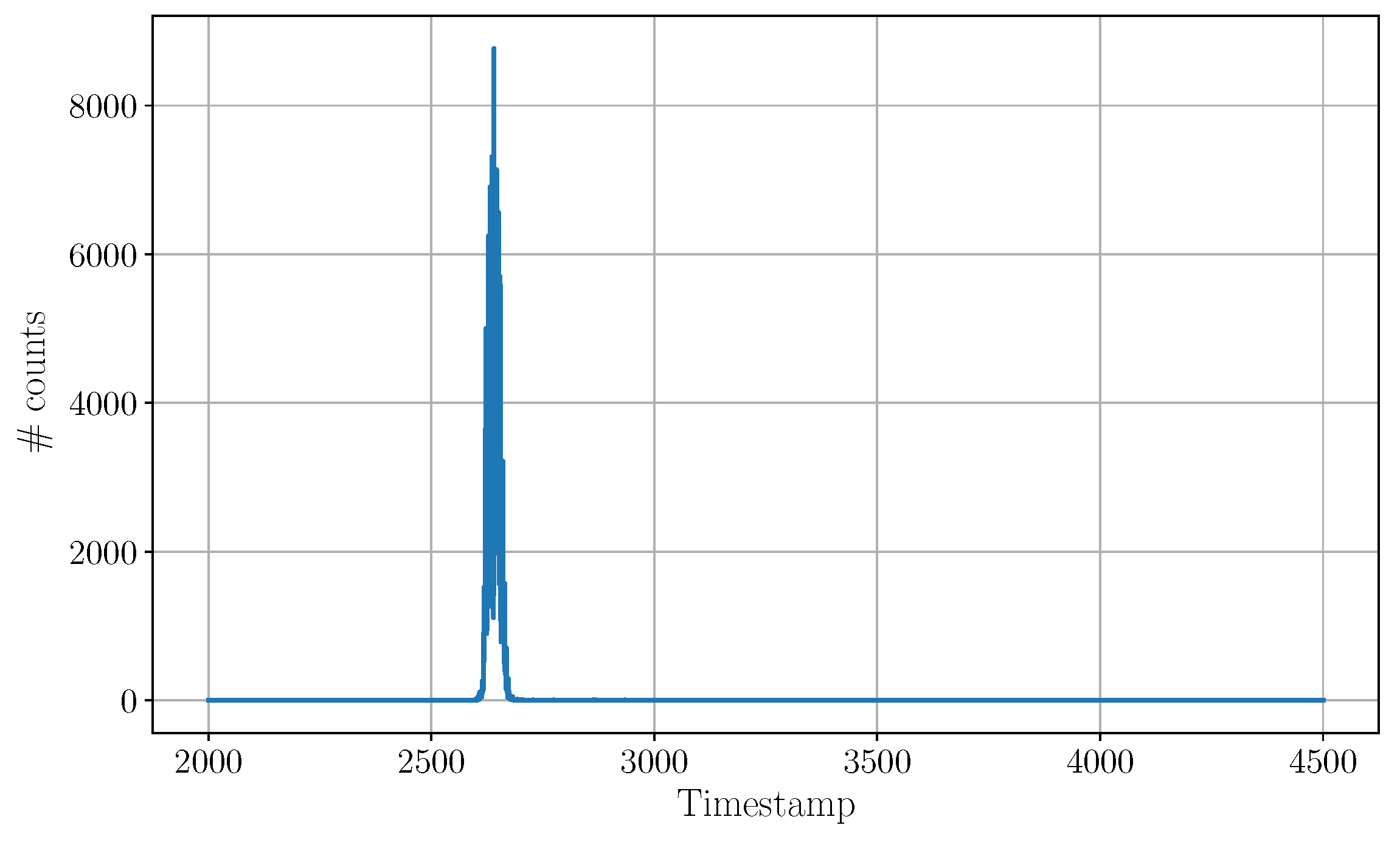
Figure 7 shows the histogram of the victim in absence of any aggressor activity. Under the measurement conditions indicated in Table 1 and with an integration time of , the victim expresses a single histogram peak with located at .
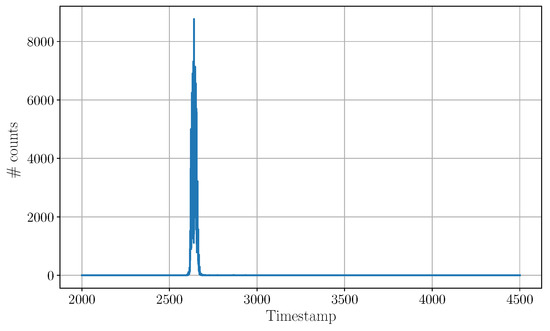
Figure 7.
Output of the victim before activating the aggressor. Measurements have been taken indoors to limit the effect of ambient light and focus on the behavior of the TCSPC peaks. The victim measures a consistent time-of-flight of (not calibrated, therefore affected by a constant offset that is immaterial to this work) with a peak width of . The measurement plot has been zoomed in to the timestamp range from the original to better appreciate the shape of the pulse.
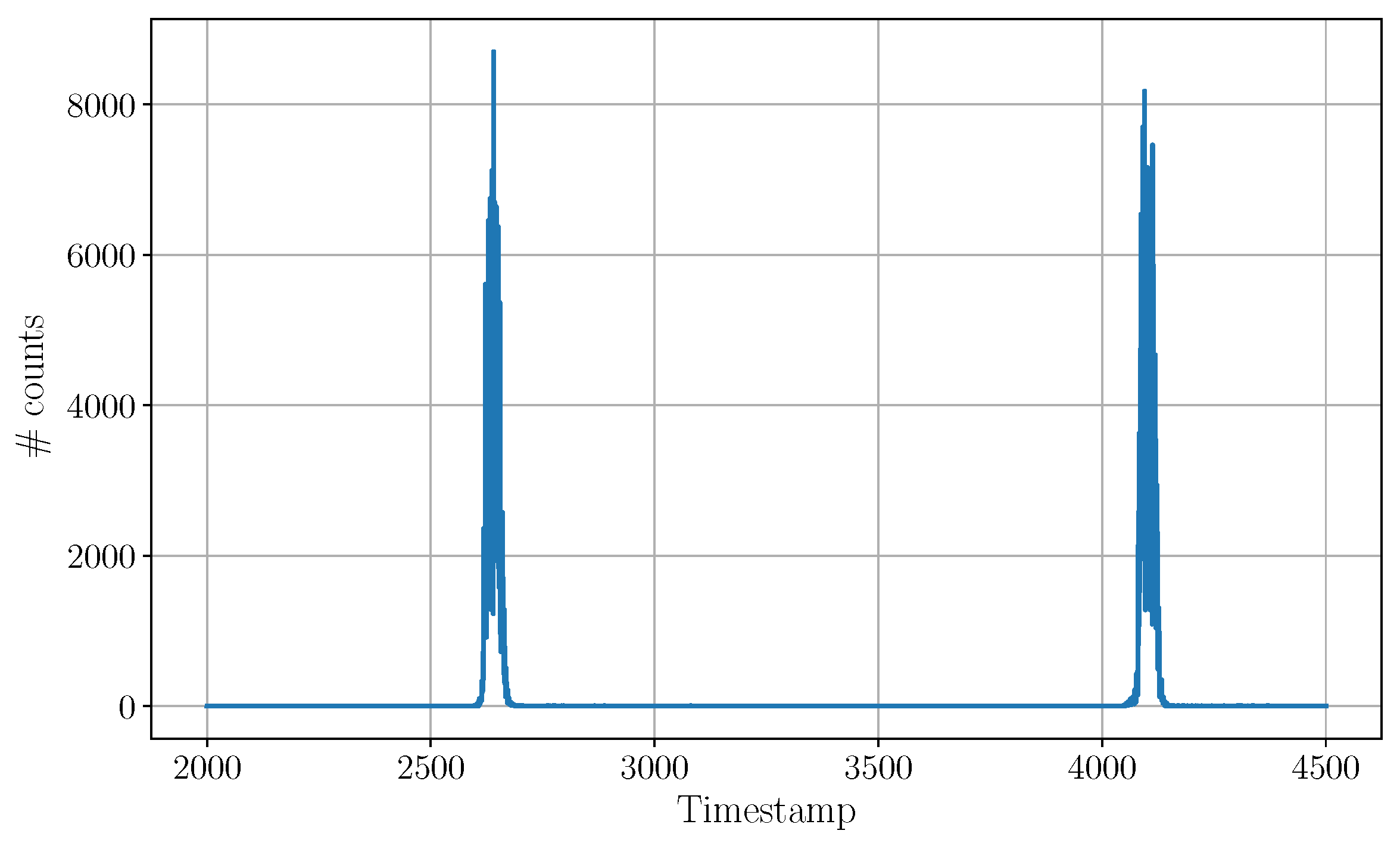
The aggressor was then activated and configured to run at the same PRF as the victim. The plot in Figure 8 shows the histogram measured by the victim in this case. A second peak at appears due to the aggressor interfering with the victim.
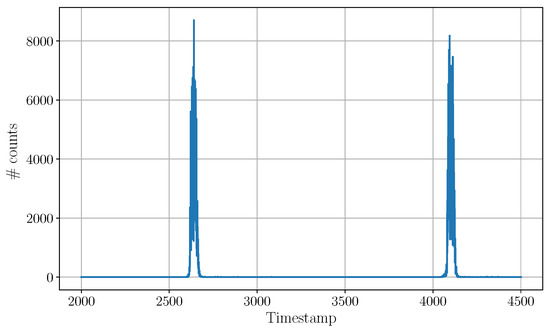
Figure 8.
Once the aggressor is activated and running at the same PRF as the victim, the victim will build a histogram with multiple peaks. Without external information, it is not possible to identify the source of each signal. During this measurement, the position and width of the victim peak was measured to be very stable (less than fluctuation over the entire experiment) and identical to the previous measurement. The aggressor peak appears later in the histogram (not a condition) at with a width of . Both emitters operate at the nominal PRF of 1 MHz.
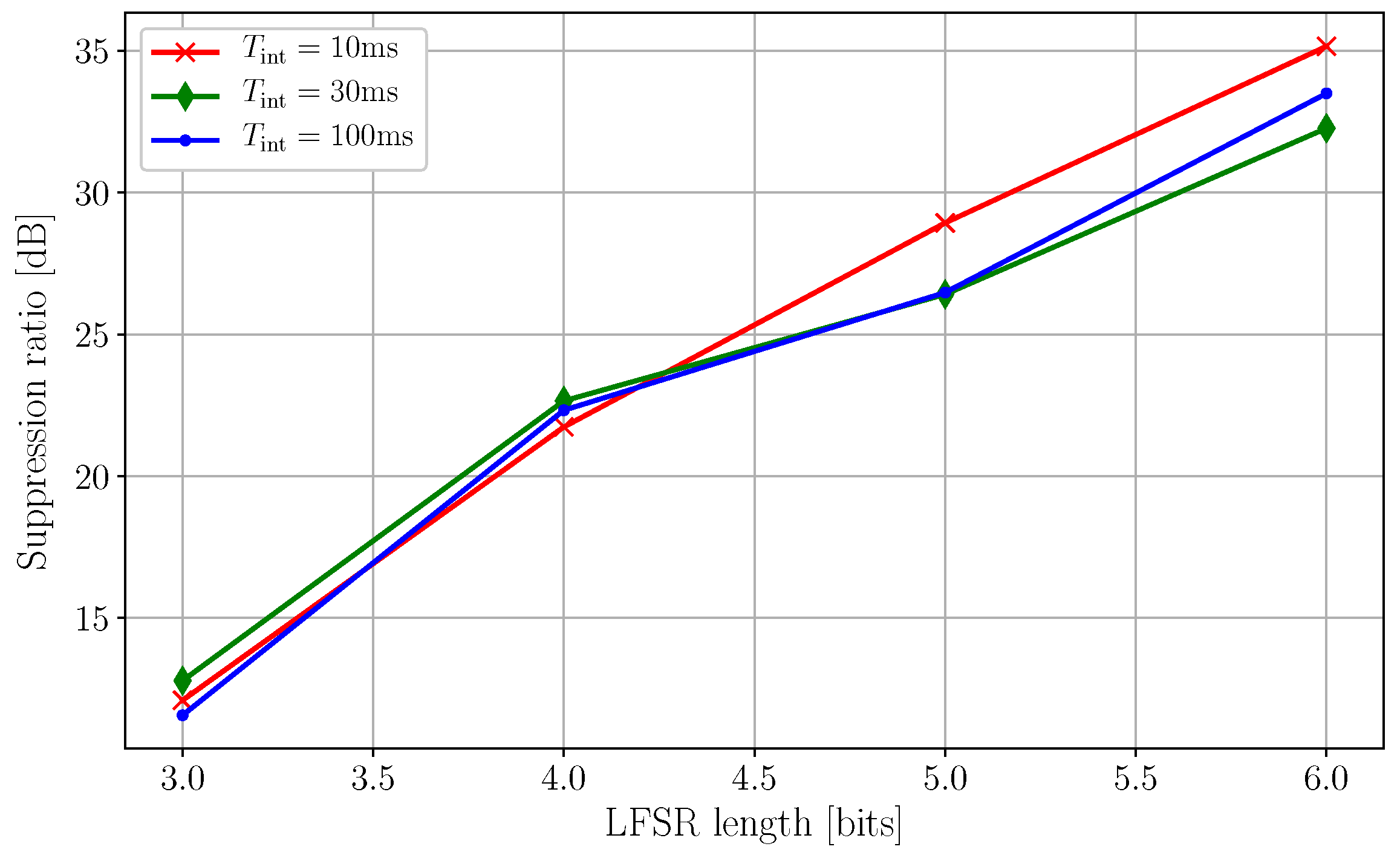
In the following measurement, the optical interference suppression characteristics of the FLISS method were investigated. In all previous measurements, the time interval between two consecutive laser pulses was always and unconditionally equal to . Now, each laser pulse of the victim is delayed by a random number of system clock cycles compared to its scheduled time. An LFSR with a primitive polynomial is used to generate a maximum-length pseudorandom sequence of delays. Four LFSRs were used, with length bits, and the suppression ratio was measured for three different values of integration time (Figure 9). The suppression ratio is defined as
where is the histogram peak value of the victim, is that of the aggressor, and S is the suppression ratio expressed in dB. Figure 10 illustrates the effect of the suppression on the histogram of the victim.
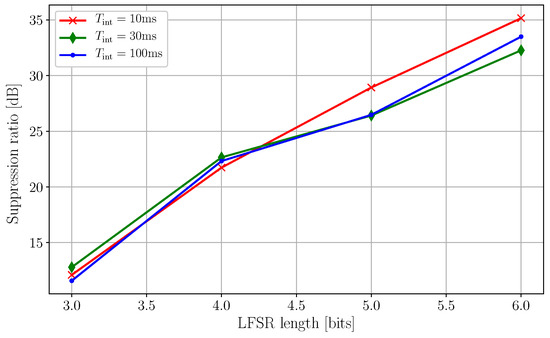
Figure 9.
Characterization of the interference suppression performance. The three lines show the suppression ratio (in dB) as a function of the length of the linear feedback shift register (LFSR) for three different integration times. With a maximum LFSR length of 6 bits and using only complete sequences, we were able to suppress the aggressor peak by 35 dB. The plot shows clearly a direct correlation between the length of the LFSR and the suppression ratio. This is expected, as shorter LFSRs produce shorter sequences containing fewer possible values; therefore, the aggressor cannot be efficiently diluted across the entire time base of the victim. Another notable point is that changing the integration time seems to have marginal effects on the suppression.
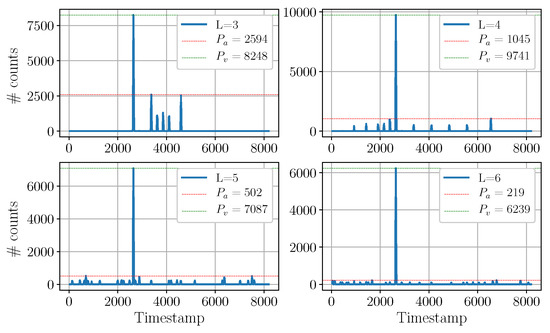
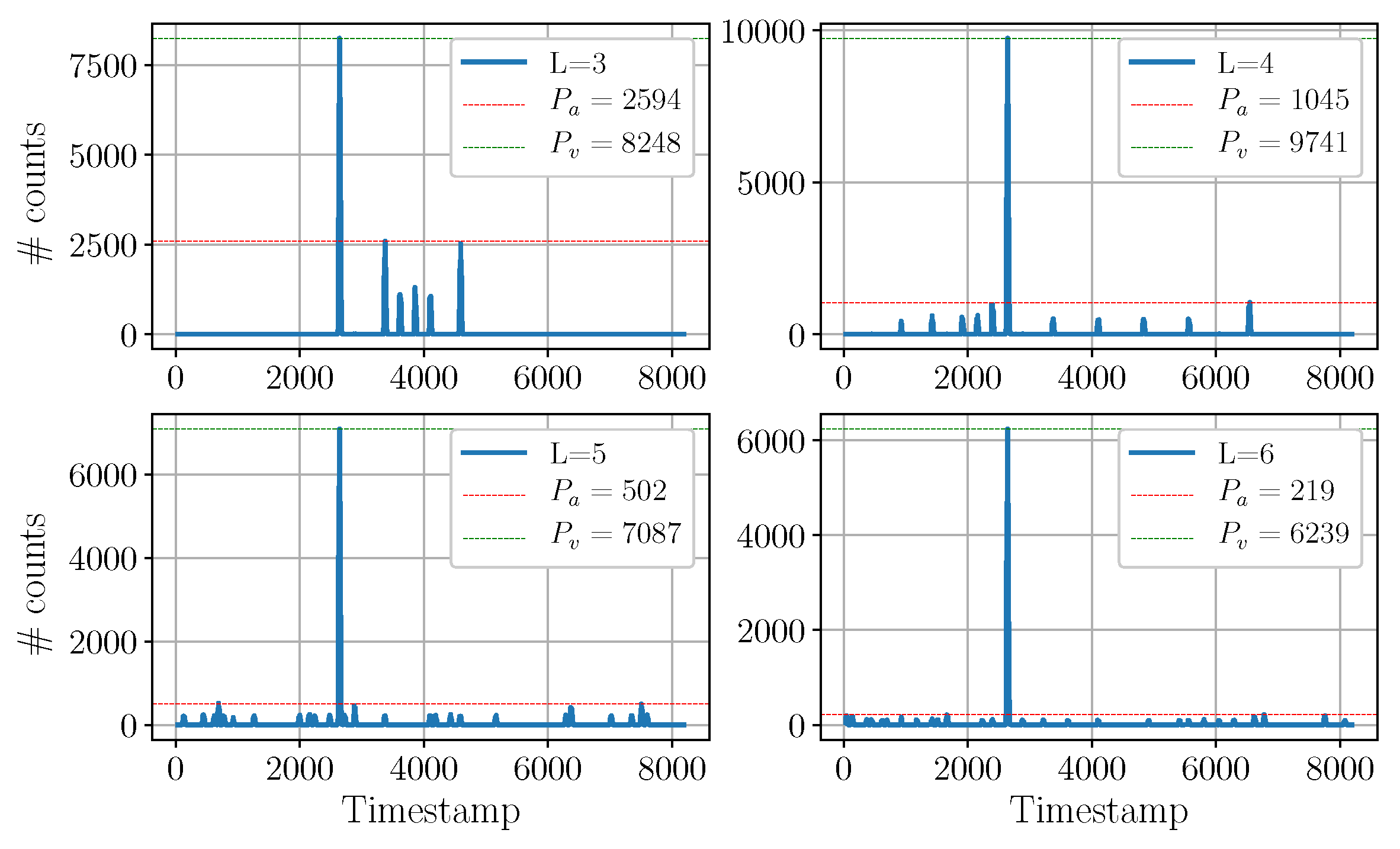
Figure 10.
This plot illustrates the histogram acquired by the victim when the suppression was active, for 4 different lengths of the LFSR. All the measurements were acquired at integration time. In all four subplots, the major peak is the victim’s peak. The minor peaks represent the aggressor signal. In each subplot, the red line indicates the highest aggressor peak, while the green line highlights the victim’s peak. It is shown that aggressor peaks get progressively more numerous and smaller as the victim’s LFSR gets longer.
It is shown that the suppression ratio improves with the increasing length of the LFSR, reaching a maximum measured suppression of using complete sequences. This is expected, as longer LFSRs produce longer sequences with a larger set of delay steps. The suppression appears to be worst for short LFSRs and long integration times. This occurs when , where is the length of the m-sequence generated by the LFSR of length L, is the system clock frequency, and is the integration time. In this case, the repetition of the same pseudorandom sequence of delays during the same acquisition introduces deterministic systematic patterns in the scrambling of the aggressor.
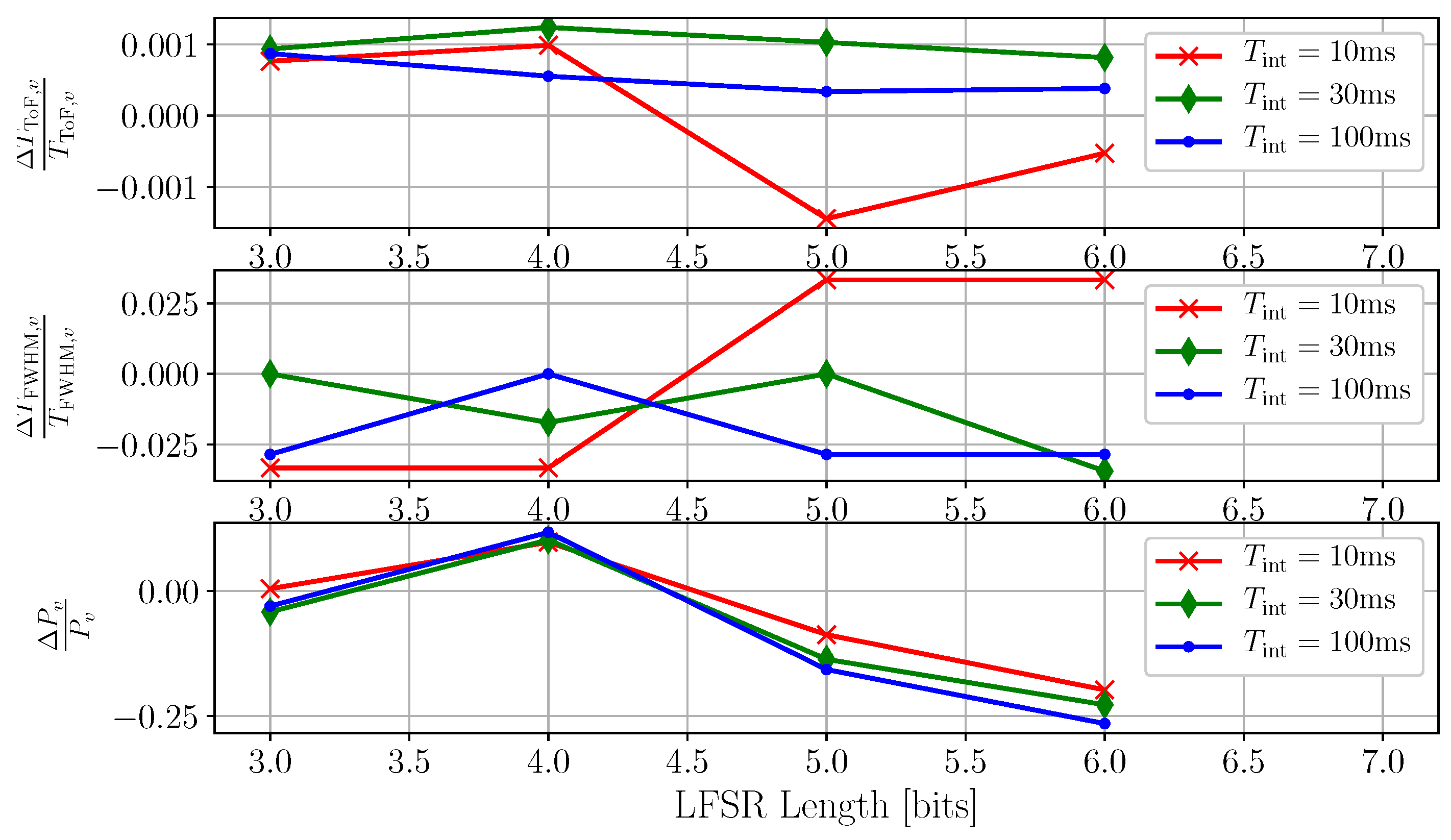
The use of the FLISS technique is shown to have minimal impact on the characteristics of the victim’s output. Figure 11 illustrates the variation of three key quantities (the intensity of the TCSPC peak , the measured time-of-flight , and the width of the peak ) relative to a reference acquisition taken in absence of interference. The experiment shows that applying FLISS does not substantially impact the measurement of the time-of-flight. Similarly, the full-width at half-maximum (FWHM) of the peak shows a maximum deviation of 3%, which is very tolerable from the point of view of signal integrity. The relative variation of the TCSPC peak intensity stays small and close to 0 for . For larger values of L, a consistent and expected decline has been observed. The reason is to be found in the probability of accidentally shifting aggressor activity right before the time of arrival of the signal peak. Given the parameters of the system, including the distance between victim and aggressor and the mutual phase shift of their PRFs, there will be a value of L after which the activity of the aggressor will start to be shifted in the vicinity of the time of arrival of the signal. When that happens, the shifted aggressor events will likely occupy the sensor and compete with signal photons. It is exactly the same effect we observe when the LiDAR imager interacts with uncorrelated signals such as sunlight. Figure 10 provides a good example to visualize this concept. This is another evidence that for , the aggressor will lose its correlation to the victim and will start behaving like ambient light for all intents and purposes.
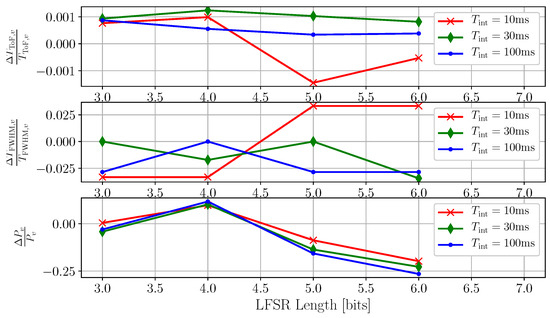
Figure 11.
Variation of key signal parameters during the application of the interference suppression technique, relative to a reference acquisition performed in the absence of interference. The relative variation of the measured time-of-flight is negligible (<0.15%) and practically constant, and it does not seem to depend on the integration time or on the LFSR length L. The relative variation of the peak width is mostly small and marginally dependent on the length of the LFSR, with all the curves being contained within 3% of the reference measurement. The relative variation of the TCSPC peak height provides an indirect indication of the changing statistical properties of the suppressed aggressor. The longer the LFSR, the more likely it is for aggressor events to be shifted right before the time of arrival of the signal. What follows is a reduction of the number of detectable signal photons due to competition between the regular signal photons and the shifted aggressor.
It is important to note that increasing the length L of the LFSR has the undesirable consequence of reducing the effective PRF of the system. Table 2 shows the effective PRF of a system running at a nominal PRF of and system clock of , for various lengths of the LFSR.

Table 2.
This table provides a correspondence between the length of the LFSR and the effective PRF of the system running at and using complete m-sequences.
It is therefore impractical to use long LFSRs in real-time applications.
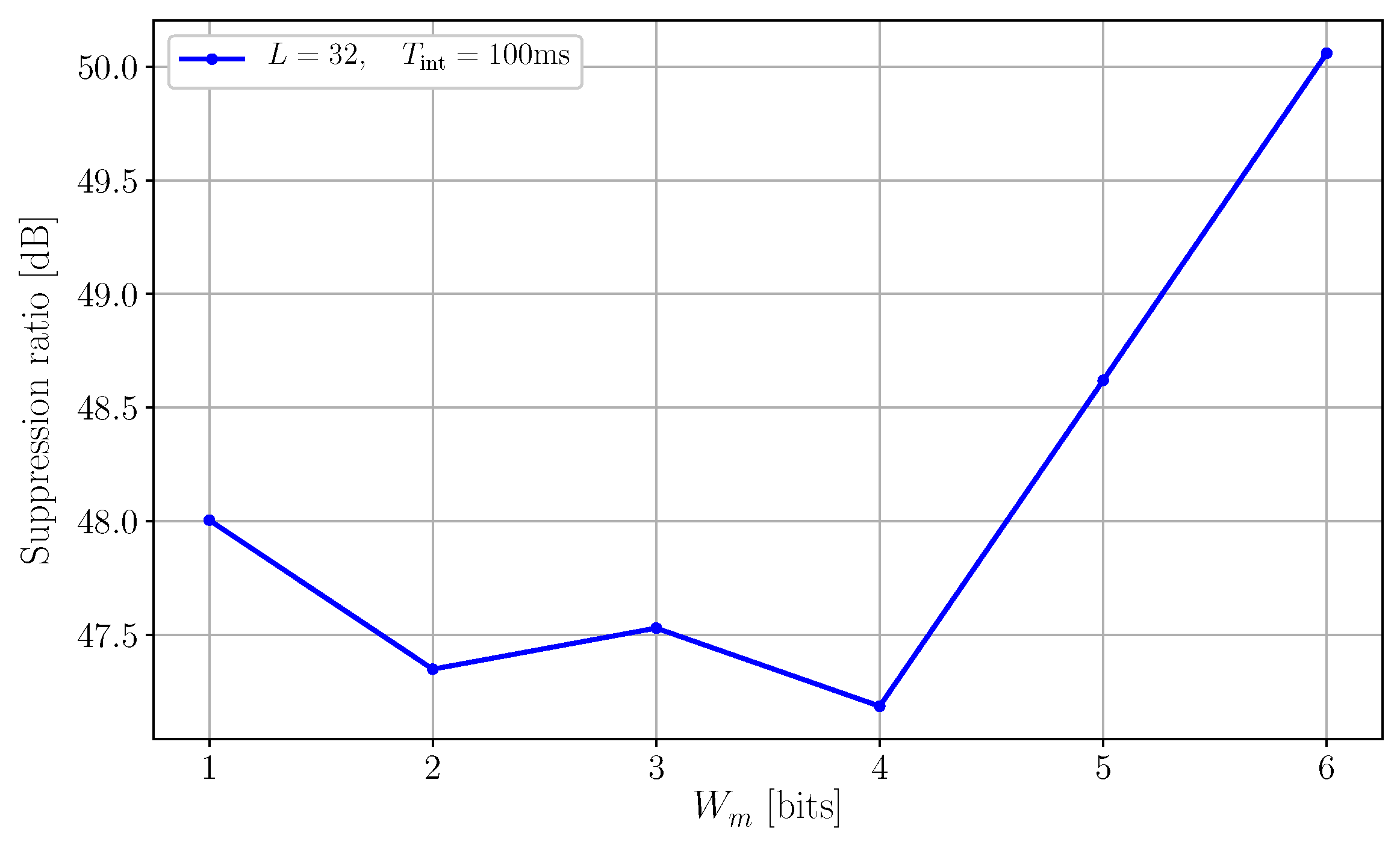
One way to overcome such a limitation is to use a different random number generator (RNG) architecture that can generate long, non-repeating sequences of small values. In our experiment, this was achieved by applying a modulo operator to the state of a 32-bit LFSR. The modulo was implemented as a bit-mask on the last LSBs of the LFSR, and the width of the bit-mask was selectable in . The periodicity of the resulting sequence is determined by the length L of the LFSR, while the maximum applicable delay is defined by the bit-mask width and the system clock frequency according to the relation . Figure 12 reports the suppression ratio for a victim using a long LFSR () as a function of the bit-mask width .
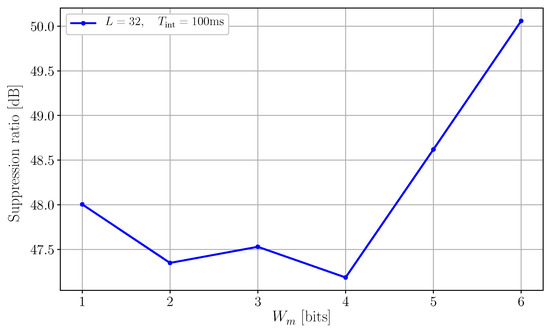
Figure 12.
This plot illustrates the interference suppression ratio as a function of the width of the bit-mask used to define the modulo operator. The experiment was run at integration time. By applying a modulo operator to the state of a 32-bit LFSR, we can guarantee a long, non-repeating sequence (property of long registers) and a minimal impact on (property of short registers). The increased randomness of the sequence translates directly into a better and more uniform dispersion of the aggressor. The result is a net improvement of the suppression ratio that reaches 50 dB for .
7. Conclusions and Future Work
This work presents the successful implementation of an optical interference suppression scheme for TCSPC flash LiDAR imagers. By applying the method described in this paper, a TCSPC flash LiDAR can effectively operate in environments shared with devices emitting modulated optical signals of arbitrary shape. This is a critical requirement for LiDAR imagers intended to operate in uncontrolled environments where other LiDAR cameras with various architectures and characteristics are expected to be present and active. The robustness of this method against intentional attacks depends on the ability of the aggressor to predict the emission time of each laser pulse of the victim. The method presented in this paper is independent of the specific RNG used. In this paper, we chose to implement a fixed m-sequence generated by a LFSR as an example of an RNG. Hardening the method against intentional interference implies choosing a high-entropy RNG producing long sequences of non-repeating values.
Typical applications in which this work will prove to be useful are automotive sensing for ADAS and autonomous driving, automated guided vehicle (AGV) navigation, and simultaneous localization and mapping (SLAM).
This work is especially significant for flash LiDAR imagers as they are more susceptible to optical interference than scanning LiDARs.
Several directions could be taken to improve and further develop the technique presented in this paper. One interesting possibility to be examined is the extension of this work to include the rejection of MPI self-interference. The authors intend to investigate the properties of alternative pseudorandom number generators (PRNGs) with different statistical distributions and the possibility of using quasi-continuous delay steps, as a necessary measure to enhance the victim’s resilience against intentional attacks.
Author Contributions
L.C. conceived the method and performed the theoretical analysis. A.F. contributed to the refinement of the concept and the implementation of the necessary firmware. A.F. and L.C. designed the experiments. A.F. executed the experiments, collected raw data, and validated it. L.C. performed the final data treatment and extracted the figures of merit.
Funding
This project has received funding from the European Union’s Horizon 2020 research and innovation program under grant agreement No 783119 (project SECREDAS, covering security for automated systems).
Acknowledgments
The authors gratefully acknowledge the contribution of the following individuals and institutions: Theo Kluter and his team at HuCE microLab for designing and building the FPGA-based development kit used in this work; Stefan T. Keller for executing preliminary simulations and contributing to technical documentation; and the R&D team at Fastree3D for the useful exchanges during the execution of the experiments and the redaction of the paper.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| ADAS | Advanced driver assistance systems |
| ADC | Analog-to-digital converter |
| AES | Advanced encryption standard |
| AGV | Automated guided vehicle |
| APD | Avalanche photo-diode |
| CDMA | Code-division multiple access |
| CIS | CMOS image sensor process |
| CMOS | Complementary metal-oxide-semiconductor |
| d-ToF | Direct time-of-flight |
| FDMA | frequency-division multiple access |
| FLISS | Flash LiDAR interference suppression scheme |
| i-ToF | Indirect time-of-flight |
| IC | Integrated circuit |
| LiDAR | Light detection and ranging |
| LFSR | Linear feedback shift register |
| LSB | Least significant bit |
| MPI | Multi-path interference |
| MSB | Most significant bit |
| NIR | Near infra-red |
| PRF | Pulse repetition frequency |
| PRNG | Pseudorandom number generator |
| RNG | Random number generator |
| SDMA | Space-division multiple access |
| SLAM | Simultaneous localization and mapping |
| SNR | Signal-to-noise ratio |
| SPAD | Single-photon avalanche diode |
| TAC | Time-to-analog converter |
| TCSPC | Time-correlated single-photon counting |
| TDC | Time-to-digital converter |
| TDMA | Time-division multiple access |
| VCSEL | Vertical-cavity surface emitting laser |
| WDMA | Wavelength-division multiple access |
References
- LiDARs For Automotive And Industrial Applications 2018; Yole Développement: Lyon, France, May 2018.
- Wu, T.; Tsai, C.; Guo, J. LiDAR/camera sensor fusion technology for pedestrian detection. In Proceedings of the APSIPA Annual Summit and Conference, Kuala Lumpur, Malaysia, 12–15 December 2017. [Google Scholar]
- Lindner, P.; Wanielik, G. Multi level fusion for an automotive pre-crash safety system. In Proceedings of the IEEE International Conference on Multisensor Fusion and Integration for Intelligent Systems, Seoul, Korea, 20–22 August 2008. [Google Scholar]
- Kwon, S.K.; Hyun, E.; Lee, J.H.; Lee, J.; Son, S.H. A low-complexity scheme for partially occluded pedestrian detection using LiDAR-radar sensor fusion. In Proceedings of the IEEE 22nd International Conference on Embedded and Real-Time Computing Systems and Applications, Daegu, Korea, 17–19 August 2016. [Google Scholar]
- Kocić, J.; Jovičić, N.; Drndarević, V. Sensors and sensor fusion in autonomous vehicles. In Proceedings of the 26th Telecommunications forum TELFOR, Belgrade, Serbia, 20–21 November 2018. [Google Scholar]
- Kohlbrecher, S.; Von Stryk, O.; Meyer, J.; Klingauf, U. A flexible and scalable SLAM system with full 3D motion estimation. In Proceedings of the IEEE International Symposium on Safety, Security, and Rescue Robotics, Kyoto, Japan, 1–5 November 2011. [Google Scholar]
- Deng, Y.; Shan, Y.; Gong, Z.; Chen, L. Large-Scale Navigation Method for Autonomous Mobile Robot Based on Fusion of GPS and Lidar SLAM. In Proceedings of the Chinese Automation Congress (CAC), Xi’an, China, 30 Novemner–2 December 2018. [Google Scholar]
- Polyakov, V.M.; Vitkin, V.V.; Lychagin, D.I.; Krylov, A.A.; Buchenkov, V.A.; Kashcheev, S.V. Compact Q-switched high repetition rate Nd:YLF laser with 100mJ pulse energy for airborne lidars. In Proceedings of the International Conference on Laser Optics, St. Petersburg, Russia, 30 June–4 July 2014. [Google Scholar]
- Iga, K. Surface-emitting laser—Its birth and generation of new optoelectronics field. IEEE J. Sel. Top. Quantum Electron. 2000, 6, 1201–1215. [Google Scholar] [CrossRef]
- Niclass, C.; Rochas, A.; Besse, P.A.; Popovic, R.S.; Charbon, E. CMOS imager based on Single-Photon Avalanche Diodes. In Proceedings of the 13th International Conference on Solid-state Sensors, Actuators and Microsystems, Seoul, Korea, 5–9 June 2005. [Google Scholar]
- Parmesan, L.; Dutton, N.A.; Calder, N.J.; Holmes, A.J.; Grant, L.A.; Henderson, R.K. A 9.8 μm sample and hold time to amplitude converter CMOS SPAD pixel. In Proceedings of the 44th European Solid State Device Research Conference (ESSDERC), Venice, Italy, 22–26 September 2014. [Google Scholar]
- Morrison, D.; Kennedy, S.; Delic, D.; Yuce, M.; Redouté, J.M. A Triple Integration Timing Scheme for SPAD Time of Flight Imaging Sensors in 130 nm CMOS. In Proceedings of the 25th IEEE International Conference on Electronics, Circuits and Systems (ICECS), Bordeaux, France, 9–12 December 2018. [Google Scholar]
- Sesta, V.; Villa, F.; Conca, E.; Tosi, A. A novel sub-10 ps resolution TDC for CMOS SPAD array. In Proceedings of the 25th IEEE International Conference on Electronics, Circuits and Systems (ICECS), Bordeaux, France, 9–12 December 2018. [Google Scholar]
- Villa, F.; Lussana, R.; Tamborini, D.; Tosi, A.; Zappa, F. High-Fill-Factor 60x1 SPAD Array With 60 Subnanosecond Integrated TDCs. IEEE Photonics Technol. Lett. 2015, 27, 1261–1264. [Google Scholar] [CrossRef]
- Lindner, S.; Zhang, C.; Antolovic, I.M.; Wolf, M.; Charbon, E. A 252 x 144 SPAD Pixel Flash Lidar with 1728 Dual-Clock 48.8 PS TDCs, Integrated Histogramming and 14.9-to-1 Compression in 180NM CMOS Technology. In Proceedings of the IEEE Symposium on VLSI Circuits, Honolulu, HI, USA, 18–22 June 2018. [Google Scholar]
- Fersch, T.; Weigel, R.; Koelpin, A. Increasing the Signal-to-Noise ratio in APD-based scanning LiDAR sensors on the transmission side. In Proceedings of the IEEE Conference on Recent Advances in Lightwave Technology (CRALT), Bangalore, India, 21–23 September 2016. [Google Scholar]
- Li, J.; Zhao, B.; Tang, L.; Zhao, X. The research and implementation of digital signal processing algorithms on pulse LiDAR. In Proceedings of the IET International Radar Conference, Guilin, China, 20–22 April 2009. [Google Scholar]
- Kirmani, A.; Benedetti, A.; Chou, P. SPUMIC, simultaneous phase unwrapping and multipath interference cancellation in Time-of-Flight cameras using spectral methods. In Proceedings of the IEEE International Conference on Multimedia and Expo (ICME), San Jose, CA, USA, 15–19 July 2013. [Google Scholar]
- Naik, N.; Kadambi, A.; Rhemann, C.; Izadi, S.; Raskar, R.; Bing Kang, S. A light transport model for mitigating multipath interference in Time-of-Flight sensors. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Boston, MA, USA, 7–12 June 2015. [Google Scholar]
- Nobuhara, S.; Kashino, T.; Matsuyama, T.; Takeuchi, K.; Fujii, K. A single-shot multi-path interference resolution for mirror-based full 3D shape measurement with a correlation-based ToF camera. In Proceedings of the Fourth International Conference on 3D Vision (3DV), Stanford, CA, USA, 25–28 October 2016. [Google Scholar]
- Islam, A.; Hossain, M.A.; Jang, Y.M. Interference mitigation technique for Time-of-Flight (ToF) camera. In Proceedings of the Eighth International Conference on Ubiquitous and Future Networks (ICUFN), Vienna, Austria, 5–8 July 2016. [Google Scholar]
- Bhandari, A.; Feigin, M.; Izadi, S.; Rhemann, C.; Schmidt, M.; Raskar, R. Resolving multipath interference in Kinect: An inverse problem approach. In Proceedings of the IEEE Sensors, Valencia, Spain, 2–5 November 2014. [Google Scholar]
- Xuan, V.N.; Hartmann, K.; Loffeld, O. Multi-target super-resolution using compressive sensing arguments for multipath interference recovery. In Proceedings of the 4th International Workshop on Compressed Sensing Theory and its Applications to Radar, Sonar and Remote Sensing (CoSeRa), Aachen, Germany, 19–22 September 2016. [Google Scholar]
- Buttgen, B.; Lustenberger, F.; Seitz, P. Pseudonoise optical modulation for real-time 3D imaging with minimum interference. IEEE Trans. Circ. Syst. I Regular Papers 2007, 54, 2109–2119. [Google Scholar] [CrossRef]
- Ximenes, A.R.; Padmanabhan, P.; Lee, M.J.; Yamashita, Y.; Yaung, D.N.; Charbon, E. A 256×256 45/65nm 3D-stacked SPAD-based direct TOF image sensor for LiDAR applications with optical polar modulation for up to 18.6dB interference suppression. In Proceedings of the IEEE International Solid-State Circuits Conference—(ISSCC), San Francisco, CA, USA, 11–15 February 2018; pp. 96–98. [Google Scholar]
- Fersch, T.; Weigel, R.; Koelpin, A. A CDMA modulation technique for automotive Time-of-Flight LiDAR systems. IEEE Sens. J. 2017, 17, 3507–3516. [Google Scholar] [CrossRef]
- Niclass, C.L.; Shpunt, A.; Agranov, G.A.; Oggier, T. LiDAR with Irregular Pulse Sequence. US Patent US20180081041A1, 2017. Available online: https://patents.google.com/patent/US20180081041A1/en (accessed on 10 May 2019).
- Matsumura, R.; Sugawara, T.; Sakiyama, K. A secure LiDAR with AES-based side-channel fingerprinting. In Proceedings of the Sixth International Symposium on Computing and Networking Workshops, Takayama, Japan, 27–30 November 2018. [Google Scholar]
- Dutta, D.; Datta, B.; Dutta, H. Design and implementation of multibit LFSR on FPGA to generate pseudorandom sequence number. In Proceedings of the Devices for Integrated Circuit (DevIC), Kalyani, India, 23–24 March 2017. [Google Scholar]
- Colavito, L.; Silage, D. Efficient PGA LFSR Implementation Whitens Pseudorandom Numbers. In Proceedings of the International Conference on Reconfigurable Computing and FPGAs, Quintana Roo, Mexico, 9–11 December 2009. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).