Enforcing Behavioral Profiles through Software-Defined Networks in the Industrial Internet of Things
Abstract
:1. Introduction
2. Related Work
3. Specifying Behavioral Profiles in IoT
3.1. Manufacturer Usage Description (MUD)
3.2. MUD Architecture
- Thing or Device, which is responsible for sending an MUD URL,
- Router or Switch to which the device is connected,
- MUD Manager, which is in charge (among other tasks) of requesting an MUD file based on a certain MUD URL,
- MUD File Server, a web server hosting MUD files.
3.3. MUD Model
4. Architecture
- Smart Object: it represents a device intended to join the deployment domain. This entity represents the device itself (a.k.a. Thing in the MUD standard, as described in Section 3). This entity acts as an EAP peer to initiate the EAP exchange, and PANA Client (PaC) to transport the corresponding EAP-PSK interactions as part of PANA messages.
- SDN Switch: this entity acts as the entry point of the network for the smart object. Furthermore, it is responsible for enforcing the corresponding flow rules, which are derived from the rules contained in the MUD file.
- Authentication Agent: it is the intermediate entity in charge of forwarding the EAP-PSK messages between the smart object and the AAA Server. Therefore, it acts as an EAP Authenticator in terminology EAP. For the transport of EAP messages, it acts as a PANA Authentication Agent (PAA) receiving PANA messages from the PaC, and as a RADIUS Client for the communication with the AAA Server through the RADIUS protocol. Furthermore, when the device is authenticated, it gets the MUD URL from the AAA Server and forwards to the MUD Manager.
- MUD Manager: this is the core component of the architecture based on the functionality described in the MUD standard. Based on ANASTACIA architecture [10], this entity plays the following roles:
- -
- SDN Orchestrator: it is in charge of managing the translation of MUD rules into a specific security configuration to be enforced. After receiving the intermediate translation to MSPL, it selects a specific security enabler, which represents a software component in charge of implementing the security function associated with a certain security policy. It also manages the enforcement of that security configuration.
- -
- IoT Controller: it makes the request to the corresponding MUD File Server based on the MUD URL, which is obtained from the Authentication Agent.
- -
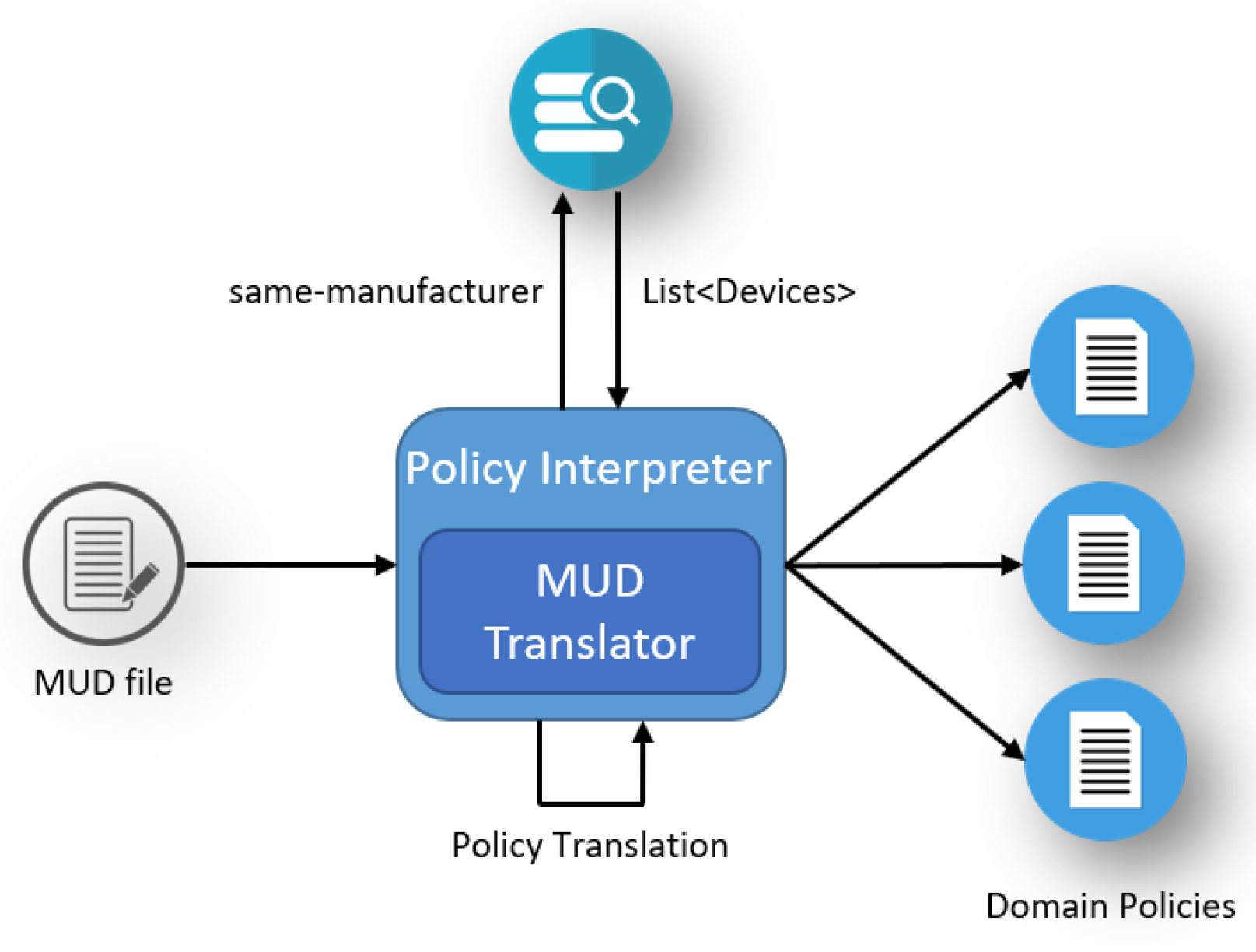
- Policy Interpreter: it is responsible for the translation process itself by converting the MUD rules into intermediate MSPL policies. Then, it translates these policies into specific security configurations based on the security enabler selected by the SDN Orchestrator.
- -
- SDN Controller: it manages the enforcement of the security configurations that are sent by the SDN Orchestrator.
- AAA Server: it acts as a RADIUS Server for the exchange of EAP messages with the Authentication Agent, and as the EAP Server in EAP terminology. This entity is supposed to store the MUD URL associated with a smart object’s MUD file.
- MUD File Server: following the MUD specification [5], it hosts the MUD files associated with the devices of a specific manufacturer.
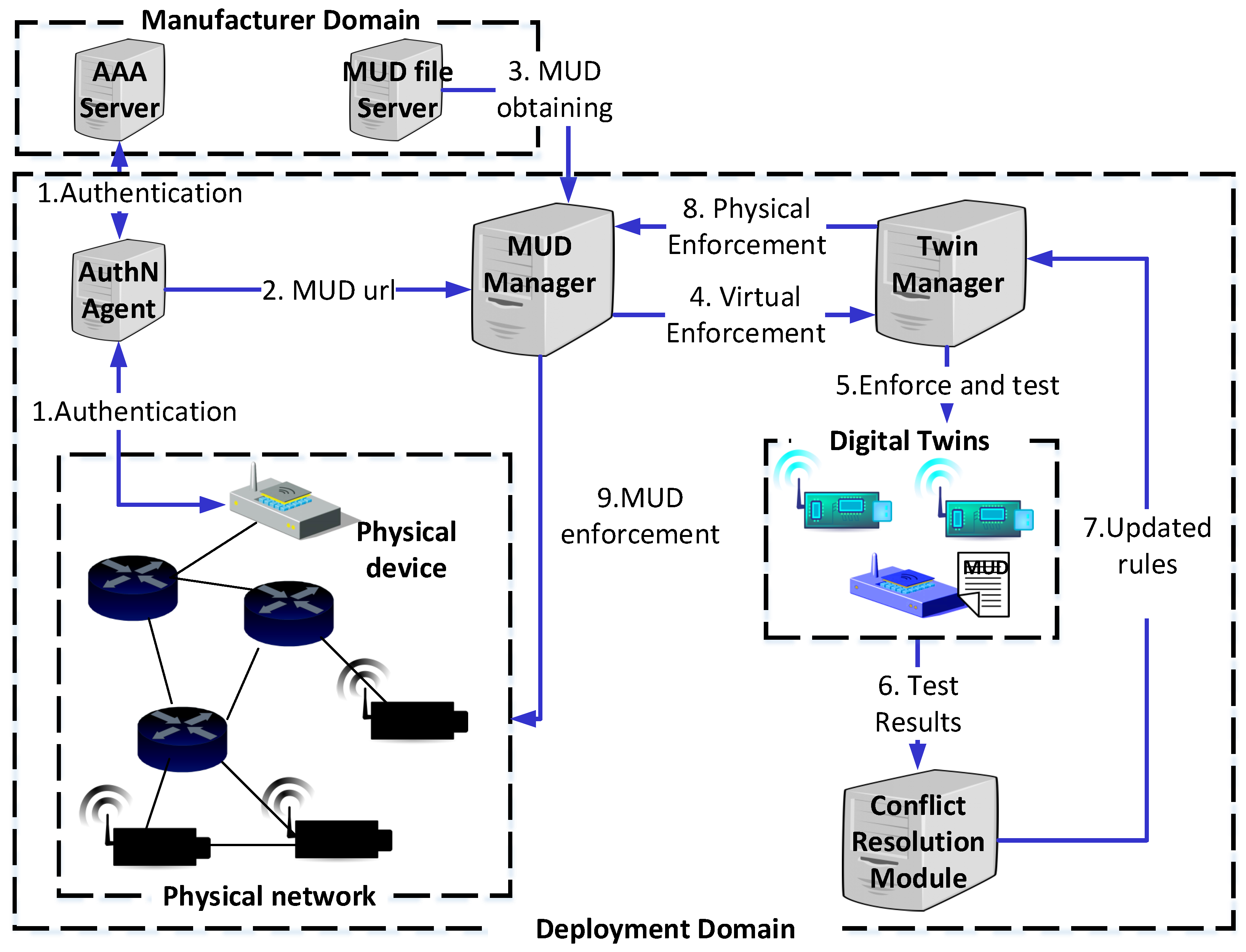
5. MUD-Enhanced Bootstrapping
5.1. Smart Object Authentication
5.2. MUD Obtaining
5.3. MUD Translation
5.4. MUD Enforcement
6. Enhancing Digital Twins with MUD Profiles
| { "ietf-mud:mud": { "mud-version":1, "mud-url":"https://manufacturer1/mote1", "last-update":"2019-01-22T12:49:03" ... "from-device-policy": { "access-lists": { "access-list": [ {"name": "ACL_fromDevice"} ] } }, ... } "ietf-access-control-list:acls": { "acl": [ ... "name": "ACL_fromDevice", "type": "ipv6-acl-type", "aces": { "ace": [{ "name": "ACE_fromDevice_1", "matches": { "ietf-mud:mud": { "same-manufacturer": [manufacturer1] }, "ipv6": {"protocol": 17}, }, "actions": {"forwarding": "accept"} }] } ] } } |
| <ITResourceOrchestration id="omspl_X"> <ITResource id="mspl_X" orchestrationID="omspl_X"> <configuration xsi:type="RuleSetConfiguration"> <capability> <Name>Traffic_Divert</Name> </capability> <configurationRule> <configurationRuleAction xsi:type="TrafficDivertAction"> <TrafficDivertActionType>FORWARD</> <packetDivertAction> <packetFilterCondition> <DestinationAddress>aaaa::2/128</> </packetFilterCondition> </packetDivertAction> </configurationRuleAction> <configurationCondition xsi:type="TrafficDivertConfCondition"> <packetFilterCondition> <SourceAddress>aaaa::1/128</> <Protocoltype>UDP</> </packetFilterCondition> </configurationCondition> <externalData xsi:type="Priority"> <value>60000</value> </externalData> </configurationRule> </configuration> </ITResource> ... </ITResourceOrchestration> |
7. Performance Evaluation
7.1. Smart Object Authentication and MUD Obtaining
7.2. Translating and Enforcing MUD Rules
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| 6LoWPAN | IPv6 over Low power Wireless Personal Area Networks |
| ACL | Access Control List |
| API | Application Programming Interface |
| CoAP | Constrained Application Protocol |
| DHCP | Dynamic Host Configuration Protocol |
| DNS | Domain Name System |
| DoS | Denial Of Service |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| ETSI | European Telecommunications Standards Institute |
| IETF | Internet Engineering Task Force |
| IPv6 | Internet Protocol version 6 |
| IoT | Internet of Things |
| JSON | JavaScript Object Notation |
| LLDP | Link Layer Discovery Protocol |
| MUD | Manufacturer Usage Description |
| NIST | National Institute of Standard and Technology |
| NTBD | National Thing Behavior Database |
| PSK | Pre-Shared Key |
| REST | Representational State Transfer |
| SDN | Software Defined Network |
| UDP | User Datagram Protocol |
| URI | Uniform Resource Identifier |
| URL | Uniform Resource Locator |
| YANG | Yet Another Next Generation |
References
- Gilchrist, A. Industry 4.0—The Industrial Internet of Things, 1st ed.; Apress: New York, NY, USA, 2016. [Google Scholar]
- European Commission. Digitising European Industry. In Digital Single Market; European Commission: Brussels, Belgium, 2015; Available online: https://ec.europa.eu/digital-single-market/en/policies/digitising-european-industry (accessed on 13 April 2015).
- Sadeghi, A.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial Internet of Things. In Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference, San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Lear, E.; Romascanu, D.; Droms, R. Manufacturer Usage Description Specification (RFC 8520), Internet Engineering Task Force, 2019. Available online: https://tools.ietf.org/html/rfc8520 (accessed on 24 October 2019).
- National Institute of Standards and Technology. Securing Small-Business and Home Internet of Things Devices, NIST Special Publication 1800-15, 2019. Available online: https://www.nccoe.nist.gov/publication/1800-15/ (accessed on 24 June 2019).
- Li, W.; Le Gall, F.; Spaseski, N. A Survey on Model-Based Testing Tools for Test Case Generation. In Tools and Methods of Program Analysis; Itsykson, V., Scedrov, A., Zakharov, V., Eds.; Springer International Publishing: Cham, Switzerland, 2018; Volume 779, pp. 77–89. [Google Scholar] [CrossRef]
- Ohba, Y.; Patil, B.; Forsberg, D.; Tschofenig, H.; Yegin, A.E. Protocol for Carrying Authentication for Network Access (RFC 5191), Internet Engineering Task Force, 2008. Available online: hhttps://tools.ietf.org/html/rfc5191 (accessed on 24 October 2019).
- Vollbrecht, J.R.; Aboba, B.; Blunk, L.J.; Levkowetz, H.; Carlson, J. Extensible Authentication Protocol (RFC 3748), Internet Engineering Task Force, 2004. Available online: https://tools.ietf.org/html/rfc3748 (accessed on 24 October 2019).
- Zarca, A.M.; Bernabe, J.B.; Trapero, R.; Rivera, D.; Villalobos, J.; Skarmeta, A.; Bianchi, S.; Zafeiropoulos, A.; Gouvas, P. Security Management Architecture for NFV/SDN-aware IoT Systems. IEEE Internet Things J. 2019, 6, 8005–8020. [Google Scholar] [CrossRef]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow - enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69. [Google Scholar] [CrossRef]
- Rosen, R.; von Wichert, G.; Lo, G.; Bettenhausen, K.D. About The Importance of Autonomy and Digital Twins for the Future of Manufacturing. IFAC 2015, 48, 567–572. [Google Scholar] [CrossRef]
- Sivanathan, A.; Sherratt, D.; Gharakheili, H.H.; Radford, A.; Wijenayake, C.; Vishwanath, A.; Sivaraman, V. Characterizing and classifying IoT traffic in smart cities and campuses. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017. [Google Scholar] [CrossRef]
- Polk, T.; Souppaya, M.; Barker, W.C. Mitigating IoT-Based Automated Distributed Threats, National Institute of Standards and Technology and National Cybersecurity Center of Excellence, 2017. Available online: https://www.nccoe.nist.gov/sites/default/files/library/project-descriptions/iot-ddos-project-description-draft.pdf (accessed on 24 October 2019).
- Voas, J.; Kuhn, R.; Laplante, P.; Applebaum, S. NISTIR 8222: Internet of Things (IoT) Trust Concerns, National Institute of Standards and Technology, 2018. Available online: https://csrc.nist.gov/publications/detail/nistir/8222/draft (accessed on 24 October 2019).
- Caspar Schutijser. Towards Automated DDoS Abuse Protection Using MUD Device Profiles. Ph.D. Thesis, University of Twente, Enschede, The Netherlands, 2018. [Google Scholar]
- Hamza, A.; Ranathunga, D.; Gharakheili, H.H.; Roughan, M.; Sivaraman, V. Clear as MUD: Generating, Validating and Applying IoT Behaviorial Profiles (Technical Report). arXiv 2018, arXiv:1804.04358. [Google Scholar]
- Hamza, A.; Ranathunga, D.; Gharakheili, H.H.; Benson, T.A.; Roughan, M.; Sivaraman, V. Verifying and Monitoring IoTs Network Behavior using MUD Profiles. arXiv 2019, arXiv:1902.02484. [Google Scholar]
- Droms, R. Dynamic Host Configuration Protocol (RFC 2131), Internet Engineering Task Force, 1997. Available online: https://tools.ietf.org/html/rfc2131 (accessed on 24 October 2019).
- Institute of Electrical and Electronics Engineers. IEEE Standard for Local and metropolitan area networks—Station and Media Access Control Connectivity Discovery. In IEEE Std 802.1AB-2016; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2016; pp. 1–146. [Google Scholar] [CrossRef]
- Institute of Electrical and Electronics Engineers. IEEE Standard for local and metropolitan area networks—Secure Device Identity, 802.1AR, 2018. Available online: https://1.ieee802.org/security/802-1ar/ (accessed on 24 October 2019).
- Garcia-Morchon, O.; Kumar, S.S.; Sethi, M. Internet of Things Security: State of the Art and Challenges (RFC 8576), 2019. Internet Engineering Task Force, 2019. Available online: https://tools.ietf.org/html/rfc8576 (accessed on 24 October 2019).
- Hamza, A.; Gharakheili, H.H.; Sivaraman, V. Combining MUD Policies with SDN for IoT Intrusion Detection. In Proceedings of the 2018 Workshop on IoT Security and Privacy, Budapest, Hungary, 20 August 2018; ACM: New York, NY, USA, 2018; pp. 1–7. [Google Scholar]
- Hamza, A.; Gharakheili, H.H.; Benson, T.A.; Sivaraman, V. Detecting Volumetric Attacks on IoT Devices via SDN-Based Monitoring of MUD Activity. In Proceedings of the 2019 ACM Symposium on SDN Research, San Jose, CA, USA, 3–4 April 2019; pp. 36–48. [Google Scholar]
- Al-Shaboti, M.; Welch, I.; Chen, A.; Mahmood, M.A. Towards Secure Smart Home IoT - Manufacturer and User Network Access Control Framework. In Proceedings of the IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 892–899. [Google Scholar]
- Ranganathan, M. Soft MUD: Implementing Manufacturer Usage Descriptions on OpenFlow SDN Switches. In Proceedings of the International Conference on Networks (ICN), Valencia, Spain, 24–28 March 2019. [Google Scholar]
- Jethanandani, M.; Blair, D.; Huang, L.; Agarwal, S. YANG Data Model for Network Access Control Lists (RFC8519). Internet Engineering Task Force, 2019. Available online: https://tools.ietf.org/html/rfc8519 (accessed on 24 October 2019).
- Bray, T. The JavaScript Object Notation (JSON) Data Interchange Format (RFC8259). Internet Engineering Task Force, 2017. Available online: https://tools.ietf.org/html/rfc8259 (accessed on 24 October 2019).
- Vollbrecht, J.; Holdrege, M.; Laat, C.; Calhoun, P.; Gommans, L.; Farrell, S.; Bruijn, B.d.; Gross, G.; Spence, D. AAA Authorization Framework (RFC 2904). Internet Engineering Task Force, 2000. Available online: https://tools.ietf.org/html/rfc2904 (accessed on 24 October 2019).
- Hurst, R.; Aboba, B.; Simon, D. The EAP-TLS Authentication Protocol (RFC 5216). Internet Engineering Task Force, 2008. Available online: https://tools.ietf.org/html/rfc5216 (accessed on 24 October 2019).
- Bersani, F.; Tschofenig, H. The EAP-PSK Protocol: A Pre-Shared Key Extensible Authentication Protocol Method (RFC 4764). Internet Engineering Task Force, 2007. Available online: https://tools.ietf.org/html/rfc4764 (accessed on 24 October 2019).
- Garcia-Carrillo, D.; Marin-Lopez, R. Lightweight CoAP-Based Bootstrapping Service for the Internet of Things. Sensors 2016, 16, 358. [Google Scholar] [CrossRef] [PubMed]
- Perez, S.; Garcia-Carrillo, D.; Marin-Lopez, R.; Hernandez-Ramos, J.L.; Marin-Perez, R.; Skarmeta, A.F. Architecture of security association establishment based on bootstrapping technologies for enabling secure IoT infrastructures. Future Gener. Comput. Syst. 2019, 95, 570–585. [Google Scholar] [CrossRef]
- Aboba, B.; Simon, D.; Eronen, P. Extensible Authentication Protocol (EAP) Key Management Framework (RFC 5247). Internet Engineering Task Force, 2008. Available online: https://tools.ietf.org/html/rfc5247 (accessed on 24 October 2019).
- Sarikaya, B.; Sethi, M.; Garcia-Carillo, D. Secure IoT Bootstrapping: A Survey. Internet Engineering Task Force, 2018. Available online: https://tools.ietf.org/id/draft-sarikaya-t2trg-sbootstrapping-05.html (accessed on 24 October 2019).
- Alliance, Z. ZigBee IP Specification. ZigBee Alliance, 2013. Available online: http://www.sandelman.ca/tmp/6tisch/13002r01ZB_Marketing-ZigBee_IP_Specification_Public_Download.pdf (accessed on 24 October 2019).
- European Telecommunications Standards Institute. Machine-To-Machine Communications (M2M); Functional Architecture. ETSI TS 102 690, Sophia Antipolis, France, 2013. Available online: https://www.etsi.org/deliver/etsi_ts/102600_102699/102690/02.01.01_60/ts_102690v020101p.pdf (accessed on 24 October 2019).
- Kanda, M.; Chasko, S. PANA applicability in constrained environments. In Proceedings of the Workshop on Smart Object Security, Paris, France, 23 March 2012; Available online: http://www.lix.polytechnique.fr/hipercom/SmartObjectSecurity/papers/MitsuruKanda.pdf (accessed on 24 October 2019).
- Eronen, P.; Kaufman, C.; Nir, Y.; Hoffman, P. Internet Key Exchange Protocol Version 2 (RFC 5996). Internet Engineering Task Force, 2010. Available online: https://tools.ietf.org/html/rfc5996 (accessed on 24 October 2019).
- Aboba, B.; Calhoun, P.R. RADIUS (Remote Authentication Dial In User Service) Support For Extensible Authentication Protocol (EAP) (RFC 3579). Internet Engineering Task Force, 2003. Available online: https://tools.ietf.org/html/rfc3579 (accessed on 24 October 2019).
- Willens, S.; Rubens, A.C.; Rigney, C.; Simpson, W.A. Remote Authentication Dial In User Service (RFC 2865). Internet Engineering Task Force, 2000. Available online: https://tools.ietf.org/html/rfc2865 (accessed on 24 October 2019).
- Burbank, J.; Mills, D.; Kasch, W. Network Time Protocol Version 4: Protocol and Algorithms Specification (RFC 5905). Internet Engineering Task Force, 2010. Available online: https://tools.ietf.org/html/rfc5905 (accessed on 24 October 2019).
- Rescorla, E.; Modadugu, N. Datagram Transport Layer Security Version 1.2 (RFC 6347). Internet Engineering Task Force, 2012. Available online: https://tools.ietf.org/html/rfc6347 (accessed on 24 October 2019).
- Enns, R.; Bjorklund, M.; Schoenwaelder, J. Network Configuration Protocol (RFC 6241). Internet Engineering Task Force, 2011. Available online: https://tools.ietf.org/html/rfc6241 (accessed on 24 October 2019).
- Berde, P.; Gerola, M.; Hart, J.; Higuchi, Y.; Kobayashi, M.; Koide, T.; Lantz, B.; O’Connor, B.; Radoslavov, P.; Snow, W.; et al. ONOS—Towards an Open, Distributed SDN OS. In Proceedings of the Third Workshop on Hot Topics in Software Defined Networking, Chicago, IL, USA, 17–22 August 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Panetta, K. Gartner Top 10 Strategic Technology Trends for 2019. Gartner, 2018. Available online: https://www.gartner.com/smarterwithgartner/gartner-top-10-strategic-technology-trends-for-2019/ (accessed on 24 October 2019).
- Shao, G.; Kibira, D. Digital manufacturing: requirements and challenges for implementing digital surrogates. In Proceedings of the 2018 Winter Simulation Conference, Gothenburg, Sweden, 9–12 December 2018. [Google Scholar] [CrossRef]
- Dunkels, A.; Gronvall, B.; Voigt, T. Contiki, a lightweight and flexible operating system for tiny networked sensors. In Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks, Tampa, FL, USA, 16–18 November 2004; pp. 455–462. [Google Scholar] [CrossRef]





| Reference | General Description | Gaps Addressed in Our Proposal |
|---|---|---|
| [16] | MUD files are generated from pcap files to protect IoT devices against DDoS attacks. | The process required to obtain the generated MUD file is not considered. |
| [17] | MUD files are generated from pcap files to create public profiles. | MUD files are generated after the device is installed in the network. The process required to obtain the generated MUD file is not considered. |
| [18] | Usage of the MUD to monitor suspicious behaviors. | The obtaining and enforcement phases of the MUD files are not addressed. |
| [23] | SDN-based architecture to translate MUD policies into flow rules to be enforced. | Details of the process to translate MUD files are not provided. Furthermore, the obtaining of the MUD files is not considered. |
| [24] | SDN-based approach to monitor the compliance of a device’s behavior with the corresponding MUD profile. | The process required to obtain the generated MUD file is not considered. |
| [25] | SDN-based framework for enforcing network access control and mitigating ARP spoofing attacks validated with MUD files. | Details of the process to translate MUD files are not provided. Furthermore, the obtaining of the MUD files is not considered. |
| [26] | SDN-based enforcement approach of MUD profiles. | Details of the process to translate MUD files are not provided. Furthermore, the obtaining of the MUD files is not considered. |
| Component | Hardware | Role | Software |
|---|---|---|---|
| Smart Object | Zolertia Z1 with 92 kB of nominal ROM and 8 kB of RAM | EAP peer PANA Client | Cooja (Contiki OS 2.7) OpenPana |
| Authentication Agent | Linux Ubuntu VM with 2 GB of RAM, 30 GB HDD and a processor Intel(R) Core(TM) i7-8550U at 1.9 GHz, using 1 core | EAP Authenticator PAA | FreeRadius 2.0.2. OpenPana |
| PAA | OpenPana | ||
| AAA Server | Linux Ubuntu VM with 2 GB of RAM, 30 GB HDD and a processor Intel(R) Core(TM) i7-8550U at 1.9 GHz, using 1 core | AAA Server | FreeRadius 2.0.2. |
| EAP Server | C application | ||
| MUD Manager | Intel Core Processor (Haswell) at 1.5 GHz using 2vCores, 2 GB of RAM and 15 GB of HDD Intel(R) Core(TM) i7-2600 CPU at 3.4 GHz, using 3 vCores, 3.5 GB of RAM and 30 GB of HDD | IoT Controller SDN Orchestrator | Python application Django 2.2.2 and Falcon 2.0 |
| SDN Controller Policy Interpreter | ONOS Django 2.2.2 and Falcon 2.0 | ||
| MUD Server | Linux Ubuntu VM with 2 GB of RAM, 30 GB HDD and a processor Intel(R) Core(TM) i7-8550U at 1.9 GHz, using 1 core | MUD Server | Apache 2.4.39 |
| Border router | Zolertia Z1 with 92 kB of nominal ROM and 8 kB of RAM | Border router | Contiki OS 2.7 |
| Message Number | Mean Time | Standard Deviation | Message Number | Mean Time | Standard Deviation | Message Number | Mean Time | Standard Deviation |
|---|---|---|---|---|---|---|---|---|
| 1 | 0.297 | 0.094 | 8 | 462.842 | ±53.522 | 15 | 0.105 | ±0.028 |
| 2 | 642.532 | ±62.484 | 9 | 0.098 | ±0.020 | 16 | 588.944 | ± 67.125 |
| 3 | 0.104 | ±0.045 | 10 | 0.637 | ±0.083 | 17 | 0.094 | ±0.021 |
| 4 | 496.934 | ±92.464 | 11 | 0.156 | ±0.154 | 18 | 0.194 | ±0.036 |
| 5 | 0.093 | ±0.009 | 12 | 593.152 | ± 0.828 | 19 | 0.195 | ±0.154 |
| 6 | 0.165 | ±0.018 | 13 | 0.100 | ±0.020 | 36 | 1013.92 | ±97.167 |
| 7 | 0.140 | ±0.123 | 14 | 0.197 | ±0.053 | 37 | 631.034 | ±50.481 |
| Phase | Mean Time (ms) | Standard Deviation |
|---|---|---|
| Manufacturer Usage Description obtaining | 37.133 | 6.791 |
| Manufacturer Usage Description signature obtaining | 34.833 | 3.905 |
| Manufacturer Usage Description signature verification | 7.733 | 1.964 |
| Total | 79.700 | 8.243 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
García, S.N.M.; Molina Zarca, A.; Hernández-Ramos, J.L.; Bernabé, J.B.; Gómez, A.S. Enforcing Behavioral Profiles through Software-Defined Networks in the Industrial Internet of Things. Appl. Sci. 2019, 9, 4576. https://doi.org/10.3390/app9214576
García SNM, Molina Zarca A, Hernández-Ramos JL, Bernabé JB, Gómez AS. Enforcing Behavioral Profiles through Software-Defined Networks in the Industrial Internet of Things. Applied Sciences. 2019; 9(21):4576. https://doi.org/10.3390/app9214576
Chicago/Turabian StyleGarcía, Sara Nieves Matheu, Alejandro Molina Zarca, José Luis Hernández-Ramos, Jorge Bernal Bernabé, and Antonio Skarmeta Gómez. 2019. "Enforcing Behavioral Profiles through Software-Defined Networks in the Industrial Internet of Things" Applied Sciences 9, no. 21: 4576. https://doi.org/10.3390/app9214576
APA StyleGarcía, S. N. M., Molina Zarca, A., Hernández-Ramos, J. L., Bernabé, J. B., & Gómez, A. S. (2019). Enforcing Behavioral Profiles through Software-Defined Networks in the Industrial Internet of Things. Applied Sciences, 9(21), 4576. https://doi.org/10.3390/app9214576









