Transforming Cybersecurity into Critical Energy Infrastructure: A Study on the Effectiveness of Artificial Intelligence
Abstract
:1. Introduction
2. Literature Review
3. Materials and Methods
3.1. Definition of the Problem
3.2. Analysis of the Critical Energy Infrastructure Network
- Generation plants are power stations that produce electricity from fossil fuels, hydroelectric, solar, and wind sources.
- Substations are facilities that transform the voltage levels of electricity for distribution and transmission throughout the network.
- Distribution centers are nodes that distribute electrical energy to final consumers, adjusting supply according to demand.
3.3. Description of the AI Technology Implemented
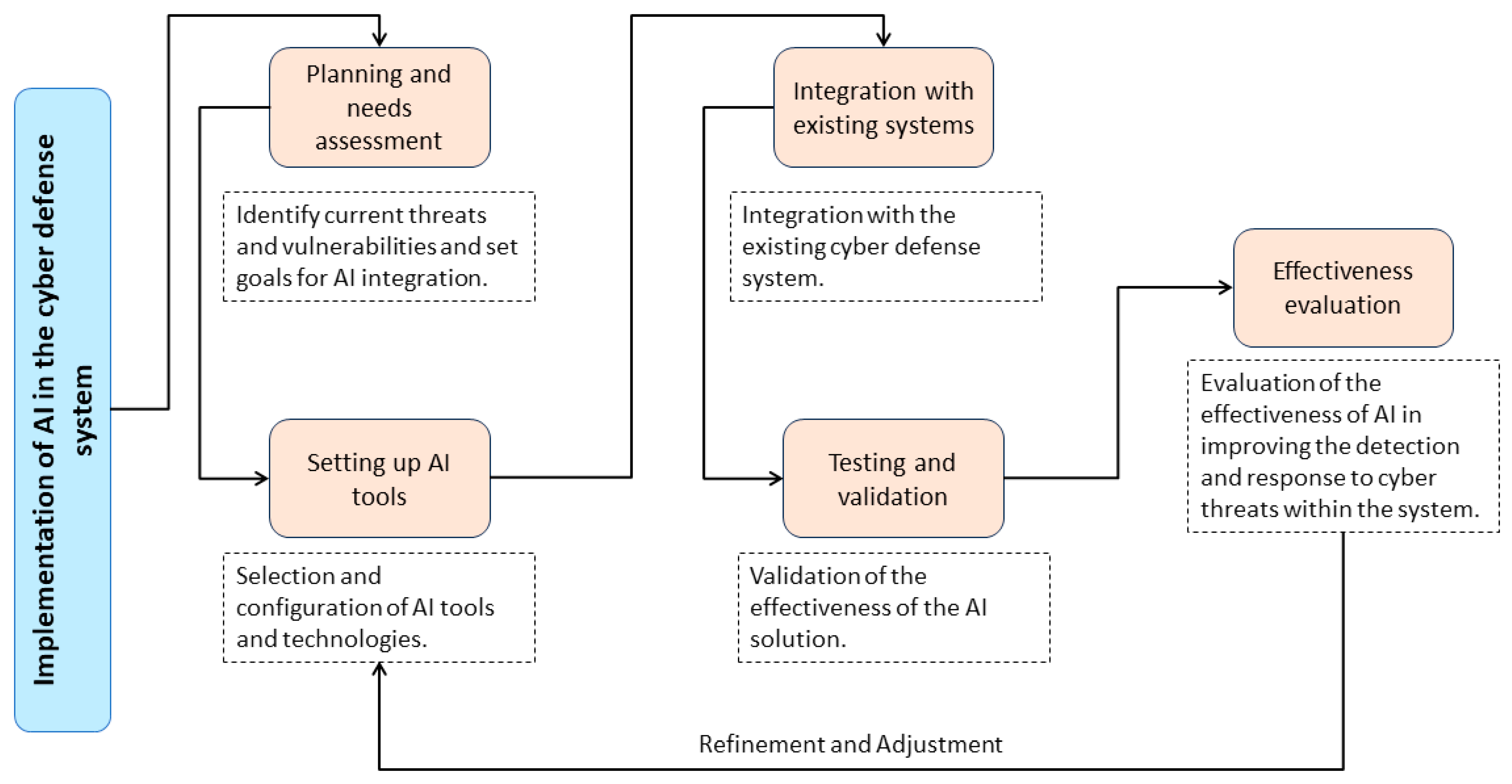
3.4. Implementation Methodology
- The first phase assesses the existing cyber defense infrastructure to identify its strengths and weaknesses, understand the threats to which it is exposed, and clearly define the requirements and objectives for AI integration. This phase allows us to align project expectations with the system’s capabilities and operational needs.
- Subsequently, the AI tools configuration phase involves selecting and customizing AI solutions. Algorithms and platforms are chosen based on their ability to satisfy the identified requirements and are configured to adapt to the specific environment of the cyber defense system. The configuration ranges from adapting machine learning algorithms to integrating NLP systems, ensuring that each AI component is optimized for the context in which it will be deployed.
- Integration with existing systems is the next phase, where the configured AI tools are assembled within the operational framework of the cyber defense system. This integration must be seamless, allowing AI solutions to effectively interact with existing systems, exchange data, and provide real-time analysis and responses. This phase ensures that AI infrastructure coexists and collaborates effectively with already deployed cybersecurity tools.
- The testing and validation stage focuses on evaluating the effectiveness of the AI integration. During this phase, rigorous testing is carried out to ensure that the AI solutions perform as expected in the actual operating environment. Testing includes simulating cyber-attacks to verify AI systems’ detection and response capabilities and evaluating precision and efficiency in threat management.
- Effectiveness assessment involves a critical analysis of data and performance metrics collected during testing and actual operation to determine the impact of AI on improving cybersecurity. It evaluates how AI tools have improved threat detection, reduced incident response time, and contributed to the overall cyber defense strategy.
- For our methodology, a refinement and adjustment loop are introduced. This loop is activated if the effectiveness evaluation indicates performance below the desired threshold. The AI technologies are then fine-tuned using performance data and effectiveness metrics collected during testing. The adjustments focus on improving precision, reducing false positives, and adapting AI systems to better respond to emerging threats. This iteration is repeated until the AI systems reach and maintain a level of performance that meets our rigorous criteria for effectiveness and efficiency. At the end of the iterative cycle, AI systems that demonstrate a robust ability to detect and respond to threats in real time and under diverse operating conditions are selected for long-term deployment.
3.5. Data Collection and Analysis
3.5.1. Data Preparation and Preprocessing
3.5.2. Analysis of Data
- Number of Trees (n_estimators): This refers to the number of trees in the forest. A significant number can improve the model’s precision and increase the computational cost. Experiment with 100, 200, or 500 values to balance performance and efficiency.
- Maximum Tree Depth (max_depth): This hyperparameter limits the depth of each tree. A more considerable depth allows the model to capture more detail but can also lead to overfitting. Different depths, such as 10, 20, or None (no limit), are tested to determine the optimal level.
- Minimum Samples to Split (min_samples_split): This parameter indicates the minimum number of samples necessary to split a node. Typical values are 2, 5, or 10. A lower value allows the model to be more detailed but can cause overfitting.
- Minimum Samples per Leaf (min_samples_leaf): The minimum number of samples required to be a tree leaf. Setting this to a more significant value can smooth the model and prevent overfitting.
3.5.3. Evaluation of the Operational Effectiveness of AI in Cybersecurity
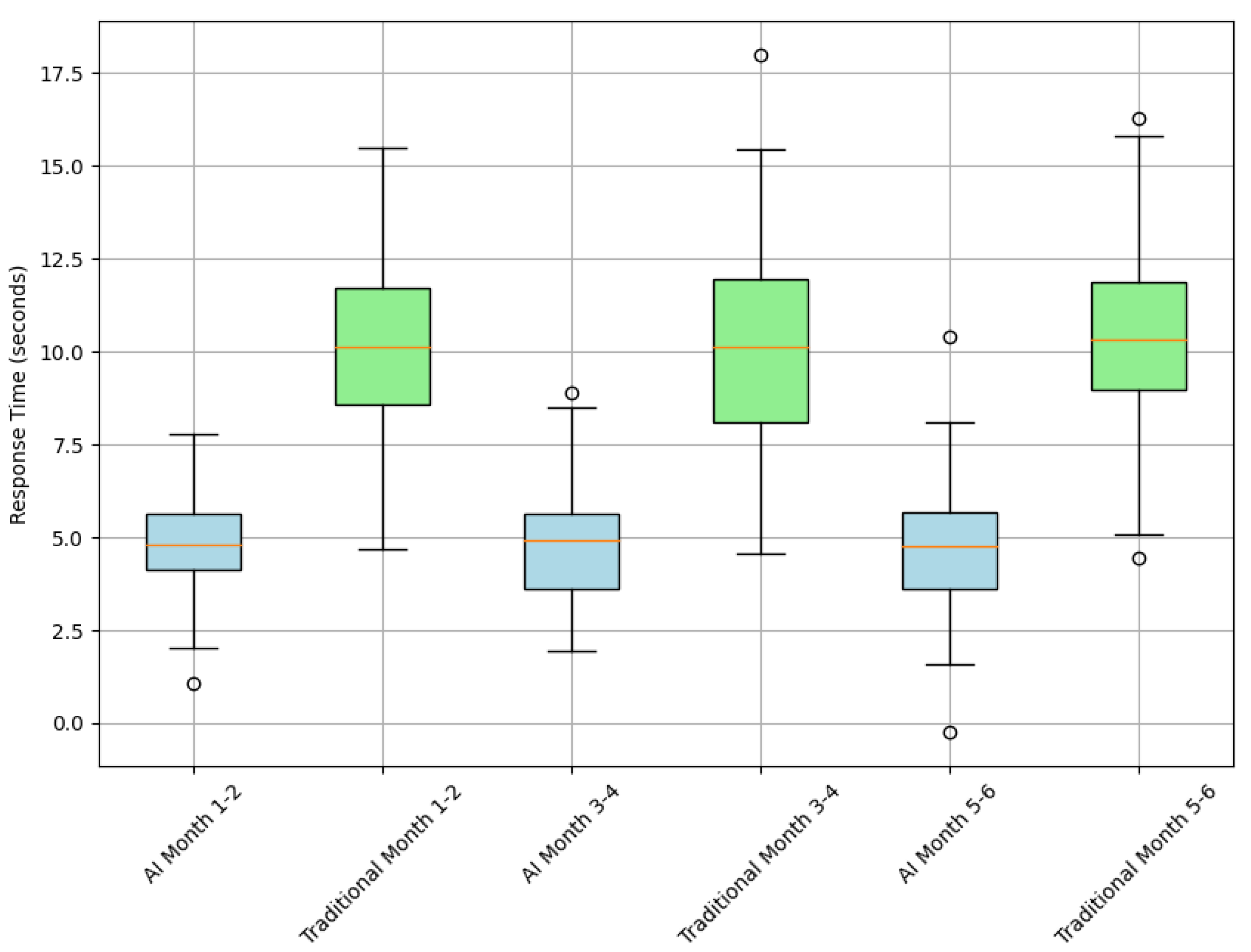
- Practical Application and Response Time: We measured the speed and effectiveness of AI systems responding to detected threats, evaluating the time elapsed from detection to implementing an appropriate response. This metric is vital for mitigating damage and strengthening incident response strategies.
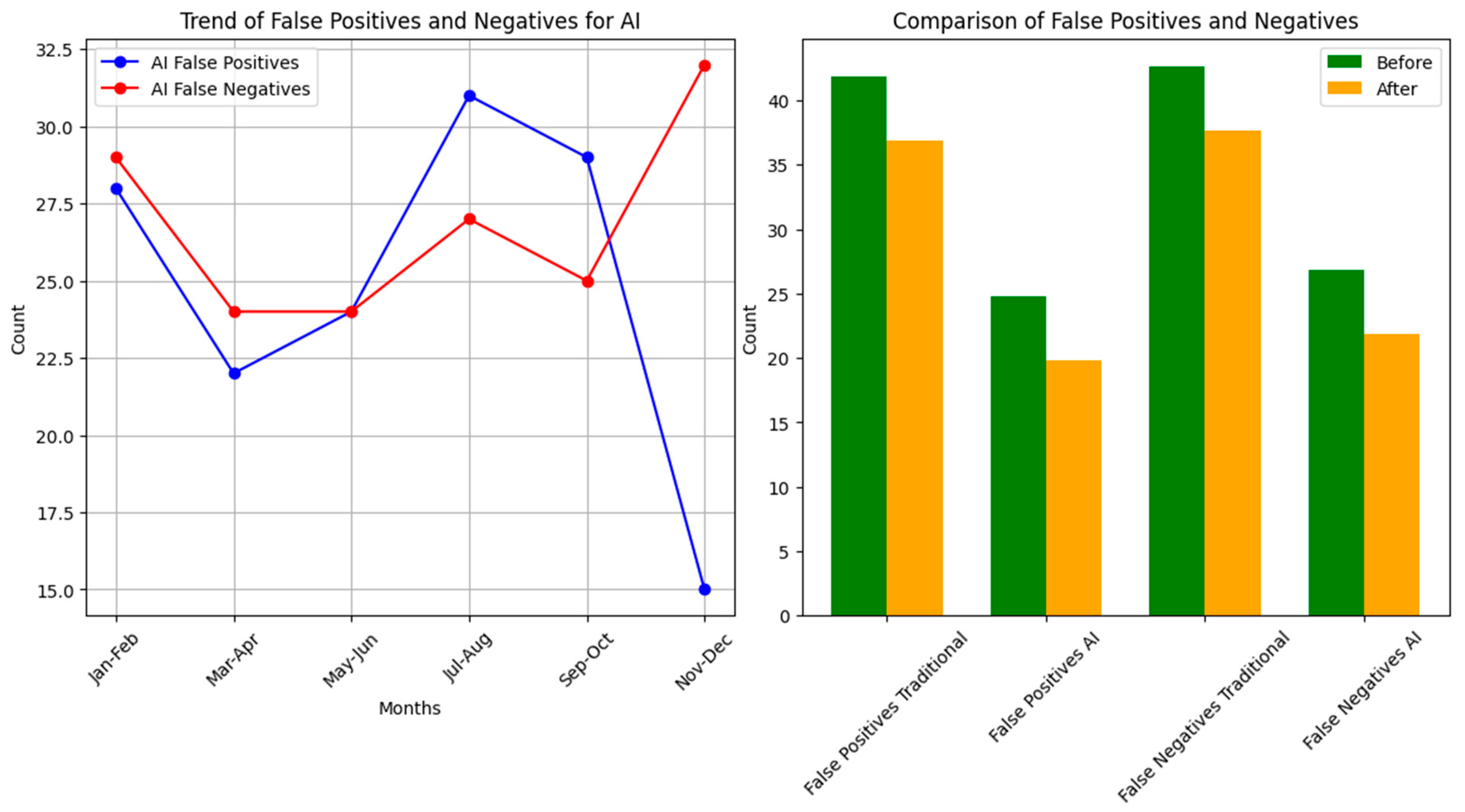
- Managing False Positives in Operational Environments: It is crucial to evaluate how often AI systems incorrectly identify legitimate activities as malicious. A high rate of false positives can create unnecessary operational burdens and divert resources from real threats. We analyzed how these false positives are managed and reduced in the operational context to improve efficiency and minimize disruption.
- Adaptability and Continuous Learning: We implemented periodic testing and adjustments based on updated data analysis to measure AI’s adaptability to new threats and changes in the cyber environment. This dynamic approach allowed us to constantly identifying areas for improvement, optimizing both threat detection precision and response efficiency.
- Feedback and Continuous Improvement Mechanism: We established a feedback mechanism that integrates learnings from real cybersecurity operations, allowing for AI systems to refine and evolve based on practical experiences. This continuous improvement ensures that AI not only stays up to date with the tactics, techniques, and procedures of emerging threats but also aligns with the specific operational needs of the cybersecurity environment.
4. Results
4.1. Evaluation of Data Processing
4.2. Evaluation of AI Performance in Threat Detection
4.2.1. Threat Detection
4.2.2. Precision and Recall Analysis
4.2.3. Comparison of Algorithms
4.3. Effectiveness in Incident Response
4.3.1. Effectiveness in Incident Response
4.3.2. Response Automation
4.4. Reduction in False Positives and Negatives
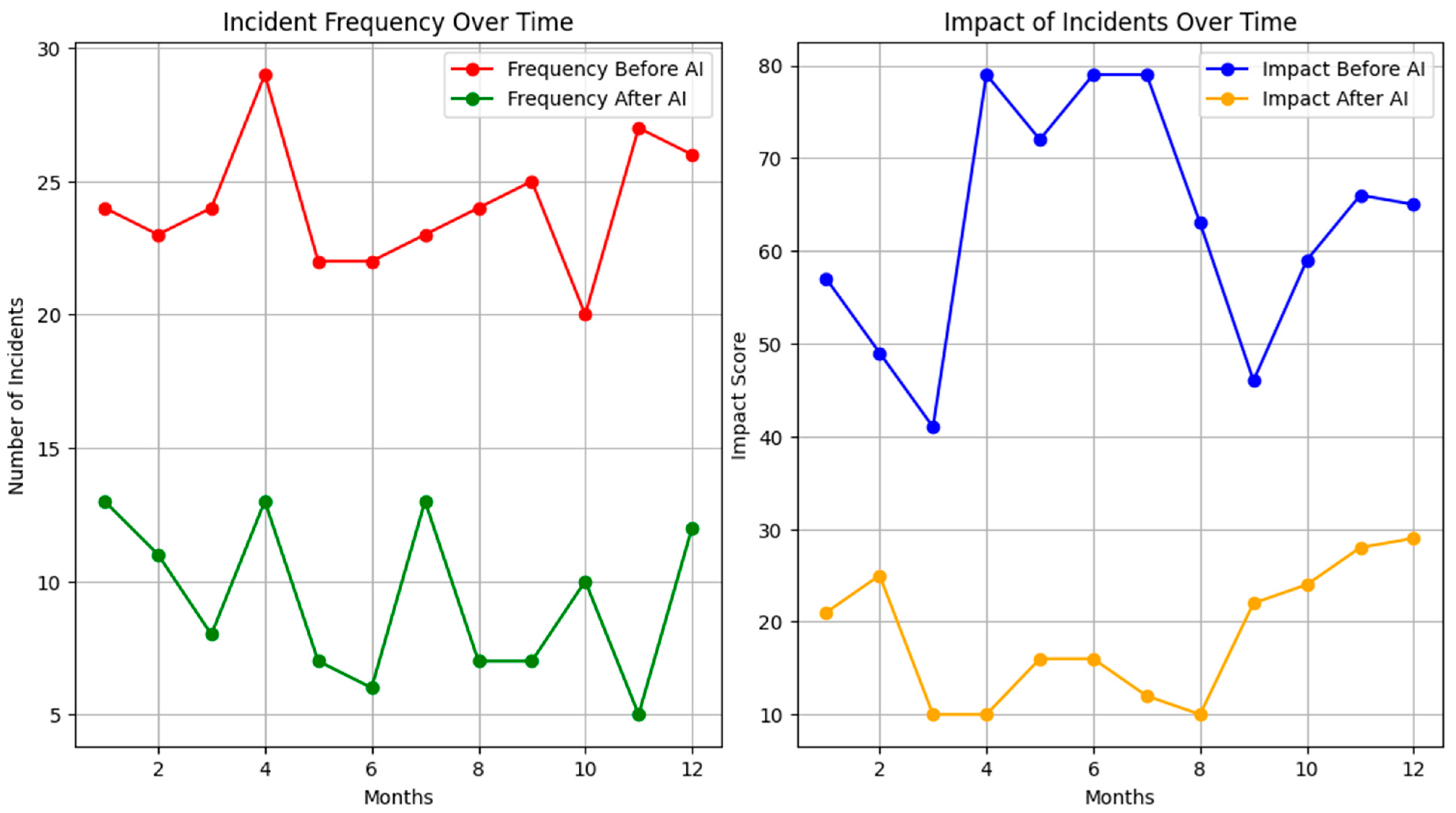
4.5. Impact on Global Cyber Security
4.5.1. General Security Improvements
4.5.2. Comparison with Other Solutions
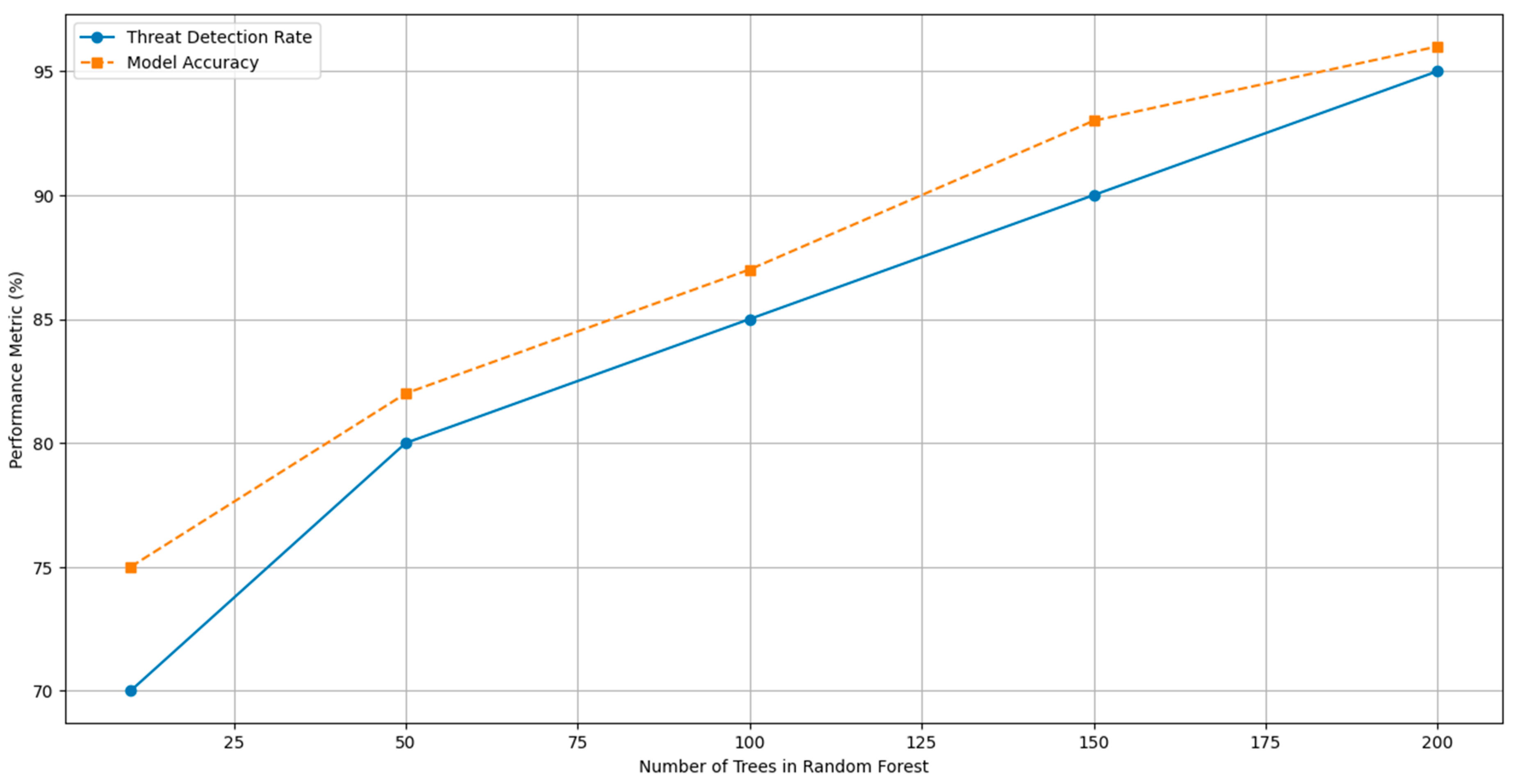
- By increasing the number of trees in the random forests, the threat detection rate improved, going from 85% in rule-based systems to 95% in optimized AI systems. This indicates that a more significant number of trees in the model can increase robustness and the ability to capture complex variations in hazard data.
- Adjusting the maximum depth allowed for a balance between capturing detail in the data and preventing overfitting, improving model precision without sacrificing generalization ability.
- Regular system evaluations demonstrated that AI could adapt to new malicious behavior, as reflected in the progressively decreasing incident response time. Initially, the average response time was 6 s. Then, after regular testing and adjustments, this time was reduced to 3 s, highlighting the agility of the AI system in quickly responding to threats.
- The continuous review of AI performance against simulated threats allowed models to be adjusted to improve detection and response, ensuring that the system reacted efficiently to known threats and could anticipate and neutralize new attack tactics.
4.6. Study Cases
4.6.1. Quantitative Analysis
4.6.2. Detailed Qualitative Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Li, G.; Shen, Y.; Zhao, P.; Lu, X.; Liu, J.; Liu, Y.; Hoi, S.C.H. Detecting Cyberattacks in Industrial Control Systems Using Online Learning Algorithms. Neurocomputing 2019, 364, 338–348. [Google Scholar] [CrossRef]
- Noorizadeh, M.; Shakerpour, M.; Meskin, N.; Unal, D.; Khorasani, K. A Cyber-Security Methodology for a Cyber-Physical Industrial Control System Testbed. IEEE Access 2021, 9, 16239–16253. [Google Scholar] [CrossRef]
- Etxezarreta, X.; Garitano, I.; Iturbe, M.; Zurutuza, U. Low Delay Network Attributes Randomization to Proactively Mitigate Reconnaissance Attacks in Industrial Control Systems. Wirel. Netw. 2023, 30, 1572–1587. [Google Scholar] [CrossRef]
- Rencelj Ling, E.; Ekstedt, M. Estimating Time-To-Compromise for Industrial Control System Attack Techniques Through Vulnerability Data. SN Comput. Sci. 2023, 4, 318. [Google Scholar] [CrossRef]
- Alzahrani, A.; Aldhyani, T.H.H. Design of Efficient Based Artificial Intelligence Approaches for Sustainable of Cyber Security in Smart Industrial Control System. Sustainability 2023, 15, 8076. [Google Scholar] [CrossRef]
- Etxezarreta, X.; Garitano, I.; Iturbe, M.; Zurutuza, U. Software-Defined Networking Approaches for Intrusion Response in Industrial Control Systems: A Survey. Int. J. Crit. Infrastruct. Prot. 2023, 42, 100615. [Google Scholar] [CrossRef]
- Kulkov, I.; Kulkova, J.; Rohrbeck, R.; Menvielle, L.; Kaartemo, V.; Makkonen, H. Artificial Intelligence—Driven Sustainable Development: Examining Organizational, Technical, and Processing Approaches to Achieving Global Goals. Sustain. Dev. 2023. [Google Scholar] [CrossRef]
- Paice, A.; McKeown, S. Practical Cyber Threat Intelligence in the UK Energy Sector; Springer: Berlin/Heidelberg, Germany, 2023. [Google Scholar]
- Ameri, K.; Hempel, M.; Sharif, H.; Lopez, J.; Perumalla, K. Design of a Novel Information System for Semi-Automated Management of Cybersecurity in Industrial Control Systems. ACM Trans. Manag. Inf. Syst. 2023, 14, 1–35. [Google Scholar] [CrossRef]
- Govindaraji, M.; Periyasamy, R. Vidyaathulasiraman Deep Learning-Based Detection of IoT Botnet Attacks: An Exploration of Residual Networks. Int. J. Saf. Secur. Eng. 2023, 13, 715–722. [Google Scholar] [CrossRef]
- Kumar, A.; Sharma, K.; Jain, S.; Sharma, D.K.; Aggarwal, A. Trends in Existing and Emerging Cyber Threat Intelligence Platforms. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 3194–3201. [Google Scholar] [CrossRef]
- Siva Kumar, C.; Kolla, H.; Sravya, B.; Sri, D.L.; Nikitha, G. Obtrusion Unmasking of Machine Learning-Based Analysis of Imbalanced Network Traffic. In Proceedings of the 2023 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 23–25 January 2023. [Google Scholar]
- Yigitcanlar, T.; Desouza, K.C.; Butler, L.; Roozkhosh, F. Contributions and Risks of Artificial Intelligence (AI) in Building Smarter Cities: Insights from a Systematic Review of the Literature. Energies 2020, 13, 1473. [Google Scholar] [CrossRef]
- Rizvi, M. Enhancing Cybersecurity: The Power of Artificial Intelligence in Threat Detection and Prevention. Int. J. Adv. Eng. Res. Sci. 2023, 10, 55–60. [Google Scholar] [CrossRef]
- Firouzi, F.; Farahani, B.; Marinšek, A. The Convergence and Interplay of Edge, Fog, and Cloud in the AI-Driven Internet of Things (IoT). Inf. Syst. 2022, 107, 101840. [Google Scholar] [CrossRef]
- Malik, M.Z.; Khan, S.; Khan, H.U. Transforming the Competencies of Artificial Intelligence to Ensure the Cyber Threats: A Systemic Literture Review of Busniess Sectors. In Proceedings of the 2022 1st International Conference on AI in Cybersecurity (ICAIC), Victoria, TX, USA, 24–26 May 2022. [Google Scholar]
- D’Amore, G.; Di Vaio, A.; Balsalobre-Lorente, D.; Boccia, F. Artificial Intelligence in the Water–Energy–Food Model: A Holistic Approach towards Sustainable Development Goals. Sustainability 2022, 14, 867. [Google Scholar] [CrossRef]
- Wenninger, S.; Karnebogen, P.; Lehmann, S.; Menzinger, T.; Reckstadt, M. Evidence for Residential Building Retrofitting Practices Using Explainable AI and Socio-Demographic Data. Energy Rep. 2022, 8, 13514–13528. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.; Page, K.; Nurse, J.R.C.; Mantilla Montalvo, R.; Santos, O.; Maddox, L.T.; Burnap, P. Cyber Risk at the Edge: Current and Future Trends on Cyber Risk Analytics and Artificial Intelligence in the Industrial Internet of Things and Industry 4.0 Supply Chains. Cybersecurity 2020, 3, 1–21. [Google Scholar] [CrossRef]
- Bécue, A.; Praça, I.; Gama, J. Artificial Intelligence, Cyber-Threats and Industry 4.0: Challenges and Opportunities. Artif. Intell. Rev. 2021, 54, 3849–3886. [Google Scholar] [CrossRef]
- Jadidi, Z.; Pal, S.; Hussain, M.; Nguyen Thanh, K. Correlation-Based Anomaly Detection in Industrial Control Systems. Sensors 2023, 23, 1561. [Google Scholar] [CrossRef] [PubMed]
- Azzam, M.; Pasquale, L.; Provan, G.; Nuseibeh, B. Forensic Readiness of Industrial Control Systems under Stealthy Attacks. Comput. Secur. 2023, 125, 103010. [Google Scholar] [CrossRef]
- Kobara, K. Cyber Physical Security for Industrial Control Systems and IoT. IEICE Trans. Inf. Syst. 2016, E99D, 787–795. [Google Scholar] [CrossRef]
- Koay, A.M.Y.; Ko, R.K.L.; Hettema, H.; Radke, K. Machine Learning in Industrial Control System (ICS) Security: Current Landscape, Opportunities and Challenges. J. Intell. Inf. Syst. 2023, 60, 377–405. [Google Scholar] [CrossRef]
- Gu, H.; Lai, Y.; Wang, Y.; Liu, J.; Sun, M.; Mao, B. DEIDS: A Novel Intrusion Detection System for Industrial Control Systems. Neural Comput. Appl. 2022, 34, 9793–9811. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Burnap, P.; Jones, K. A Three-Tiered Intrusion Detection System for Industrial Control Systems. J. Cybersecur. 2021, 7, tyab006. [Google Scholar] [CrossRef]
- Yang, T.; Zhang, J.; Huang, Z.; Chen, Y.; Huang, C.; Zhou, W.; Liu, P.; Feng, T.; Zhang, Y. Survey of Industrial Control Systems Security. Jisuanji Yanjiu Yu Fazhan/Comput. Res. Dev. 2022, 59, 1035–1053. [Google Scholar]
- Anthi, E.; Williams, L.; Rhode, M.; Burnap, P.; Wedgbury, A. Adversarial Attacks on Machine Learning Cybersecurity Defences in Industrial Control Systems. J. Inf. Secur. Appl. 2021, 58, 102717. [Google Scholar] [CrossRef]
- Knowles, W.; Prince, D.; Hutchison, D.; Disso, J.F.P.; Jones, K. A Survey of Cyber Security Management in Industrial Control Systems. Int. J. Crit. Infrastruct. Prot. 2015, 9, 52–80. [Google Scholar] [CrossRef]
- Booth, H.; Rike, D.; Witte, G. The National Vulnerability Database (Nvd): Overview; ITL Bulletin, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2013.
- McRee Möller, K. Setting up a Grid-CERT: Experiences of an Academic CSIRT. Campus-Wide Inf. Syst. 2007, 24, 260–270. [Google Scholar] [CrossRef]
- Gordillo, R.; García, A. CrowdStrike, Plataforma Nativa Desde La Nube Para La Protección de Endpoints. Rev. SIC Cibersegur. Segur. Inf. Privacidad 2019, 28, 124–126. [Google Scholar]
- FireEye. Available online: https://fireeye.market/apps/219385 (accessed on 23 April 2024).
- Beguería, S.; Vicente-Serrano, S.M.; Reig, F.; Latorre, B. Standardized Precipitation Evapotranspiration Index (SPEI) Revisited: Parameter Fitting, Evapotranspiration Models, Tools, Datasets and Drought Monitoring. Int. J. Climatol. 2014, 34, 3001–3023. [Google Scholar] [CrossRef]
- Taleb, I.; Serhani, M.A. Big Data Pre-Processing: Closing the Data Quality Enforcement Loop. In Proceedings of the IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 498–501. [Google Scholar]
- Bernhardt, M.; Castro, D.C.; Tanno, R.; Schwaighofer, A.; Tezcan, K.C.; Monteiro, M.; Bannur, S.; Lungren, M.P.; Nori, A.; Glocker, B.; et al. Active Label Cleaning for Improved Dataset Quality under Resource Constraints. Nat. Commun. 2022, 13, 1161. [Google Scholar] [CrossRef]
- Lakshmanaprabu, S.K.; Shankar, K.; Sheeba Rani, S.; Abdulhay, E.; Arunkumar, N.; Ramirez, G.; Uthayakumar, J. An Effect of Big Data Technology with Ant Colony Optimization Based Routing in Vehicular Ad Hoc Networks: Towards Smart Cities. J. Clean. Prod. 2019, 217, 584–593. [Google Scholar] [CrossRef]
- Morales, A.; Cuevas, R.; Martínez, J.M. Analytical Processing with Data Mining. RECI Rev. Iberoam. Cienc. Comput. Inform. 2016, 5, 22–43. [Google Scholar]
- Ortiz-Aguilar, L.D.M.; Carpio, M.; Soria-Alcaraz, J.A.; Puga, H.; Díaz, C.; Lino, C.; Tapia, V. Training OFF-Line Hyperheuristics For Course Timetabling Using K-Folds Cross Validation. Rev. Program. Mat. Softw. 2016, 8, 1–8. [Google Scholar]
- Shadiev, R.; Wu, T.T.; Huang, Y.M. Using Image-to-Text Recognition Technology to Facilitate Vocabulary Acquisition in Authentic Contexts. ReCALL 2020, 32, 195–212. [Google Scholar] [CrossRef]
- Arimatsu, T.; Yano, Y.; Takahashi, Y. Security Operations Center (SOC) and Security Monitoring Services to Fight Complexity and Spread of Cyber Threats. NEC Tech. J. 2018, 12, 34–37. [Google Scholar]
- Eryanto, H. Cyber Security Strategy: Factors Affecting Performance at Security Operation Center (SOC) In Indonesia. Soc. Sci. J. 2023, 13, 3110–3127. [Google Scholar]
- Krishnan, P.; Duttagupta, S.; Achuthan, K. VARMAN: Multi-Plane Security Framework for Software Defined Networks. Comput. Commun. 2019, 148, 215–239. [Google Scholar] [CrossRef]
- Infrastructure Security Agency (CISA). Known Exploited Vulnerabilities Catalog; CISA: Denver, CO, USA, 2021.
- Kim, H.S.; Lim, C.G.; Lee, S.J.; Kim, Y.M. GRU-Based Buzzer Ensemble for Abnormal Detection in Industrial Control Systems. Comput. Mater. Contin. 2023, 74, 1749–1763. [Google Scholar] [CrossRef]
- Djenouri, Y.; Michalak, T.P.; Lin, J.C.W. Federated Deep Learning for Smart City Edge-Based Applications. Future Gener. Comput. Syst. 2023, 147, 350–359. [Google Scholar] [CrossRef]
- Kumari, A.; Gupta, R.; Tanwar, S.; Kumar, N. Blockchain and AI Amalgamation for Energy Cloud Management: Challenges, Solutions, and Future Directions. J. Parallel Distrib. Comput. 2020, 143, 148–166. [Google Scholar] [CrossRef]
- Al-Muntaser, B.; Mohamed, M.A.; Tuama, A.Y. Real-Time Intrusion Detection of Insider Threats in Industrial Control System Workstations through File Integrity Monitoring. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 326–333. [Google Scholar] [CrossRef]
| AI Technology | Detection Efficiency | Integration with Existing Systems | Scalability | Resource Management | Cost |
|---|---|---|---|---|---|
| Neural Networks | High | Moderate | High | Intensive | High |
| CNN | High | Moderate | High | Intensive | High |
| LSTM | High | Moderate | High | Intensive | High |
| GNN (Graph Neural Network) | High | Moderate | High | Intensive | High |
| Decision Trees | Medium | High | Medium | Moderate | Medium |
| C4.5 | Medium | High | Medium | Moderate | Medium |
| ID3 | Medium | High | Medium | Moderate | Medium |
| Support Vector Machines (SVMs) | Medium | High | Medium | Moderate | Medium |
| Natural Language Processing (NLP) | Medium | Moderate | High | Intensive | High |
| GPT (Generative Pretrained Transformer) | High | Moderate | High | Intensive | High |
| BERT (Bidirectional Encoder Representations from Transformers) | High | Moderate | High | Intensive | High |
| Evaluated Aspect | Result Before Treatment | Result After Treatment |
|---|---|---|
| Amount of Data (records) | 1,200,000 | 1,150,000 |
| Identified Duplicates | 30,000 | 0 |
| Missing Values | 100,000 | 0 |
| Anomalies/Outliers Detected | 20,000 | 0 |
| Format Consistency | Low | high |
| Numeric Value Range | Varied (unnormalized) | 0–1 (normalized) |
| Criterion | AI Model | Traditional System |
|---|---|---|
| Threat Detection Rate (%) | 94.7 | 74.9 |
| Total Number of Threats Detected | 947 | 749 |
| Total Number of Threats Present | 1000 | 1000 |
| False Positives | 53 | 104 |
| False Negatives | 53 | 251 |
| AI Algorithm | Precision (%) | Recall (%) | F1 Score (%) |
|---|---|---|---|
| Random Forest | 92 | 88 | 90 |
| SVM | 89 | 85 | 87 |
| Deep Neural Network | 93 | 90 | 91.5 |
| CNN | 91 | 87 | 89 |
| Decision Trees | 88 | 84 | 86 |
| Traditional System | 75 | 70 | 72 |
| Automated Response Type | Description | Activation Frequency |
|---|---|---|
| System Isolation | Disconnecting infected devices from the network to contain the spread of a threat | 120 times |
| Account Deactivation | Temporary suspension of user accounts with abnormal behavior | 75 times |
| Blocking Network Traffic | Immediate interruption of traffic flows identified as malicious | 200 times |
| Automatic Patching | Applying security patches to vulnerable software without human intervention | 150 times |
| Security Alerts | Automatic notifications to security teams for situations that require human review | 300 times |
| Parameter | Our AI Solution | Rules Based System | Hybrid System (Rules and Essential ML) |
|---|---|---|---|
| Threat Detection Rate (%) | 95 | 85 | 90 |
| Average Response Time (sec) | 3 | 9 | 6 |
| False Positive Rate (%) | 4 | 12 | 9 |
| False Negative Rate (%) | 5 | 15 | 10 |
| Estimated Operating Cost (USD) | 50,000 | 40,000 | 30,000 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Govea, J.; Gaibor-Naranjo, W.; Villegas-Ch, W. Transforming Cybersecurity into Critical Energy Infrastructure: A Study on the Effectiveness of Artificial Intelligence. Systems 2024, 12, 165. https://doi.org/10.3390/systems12050165
Govea J, Gaibor-Naranjo W, Villegas-Ch W. Transforming Cybersecurity into Critical Energy Infrastructure: A Study on the Effectiveness of Artificial Intelligence. Systems. 2024; 12(5):165. https://doi.org/10.3390/systems12050165
Chicago/Turabian StyleGovea, Jaime, Walter Gaibor-Naranjo, and William Villegas-Ch. 2024. "Transforming Cybersecurity into Critical Energy Infrastructure: A Study on the Effectiveness of Artificial Intelligence" Systems 12, no. 5: 165. https://doi.org/10.3390/systems12050165
APA StyleGovea, J., Gaibor-Naranjo, W., & Villegas-Ch, W. (2024). Transforming Cybersecurity into Critical Energy Infrastructure: A Study on the Effectiveness of Artificial Intelligence. Systems, 12(5), 165. https://doi.org/10.3390/systems12050165








