1. Introduction
Over the past decade, consumers around the world have become increasingly concerned about product safety [
1]. Traceability is considered a promising solution for product safety, as well as to achieve consumer confidence [
2]. Traceability is the ability to access any or all information relating to the product that is under consideration (traceable resource Unit, TRU), throughout its entire life cycle, by means of recorded identifications [
3,
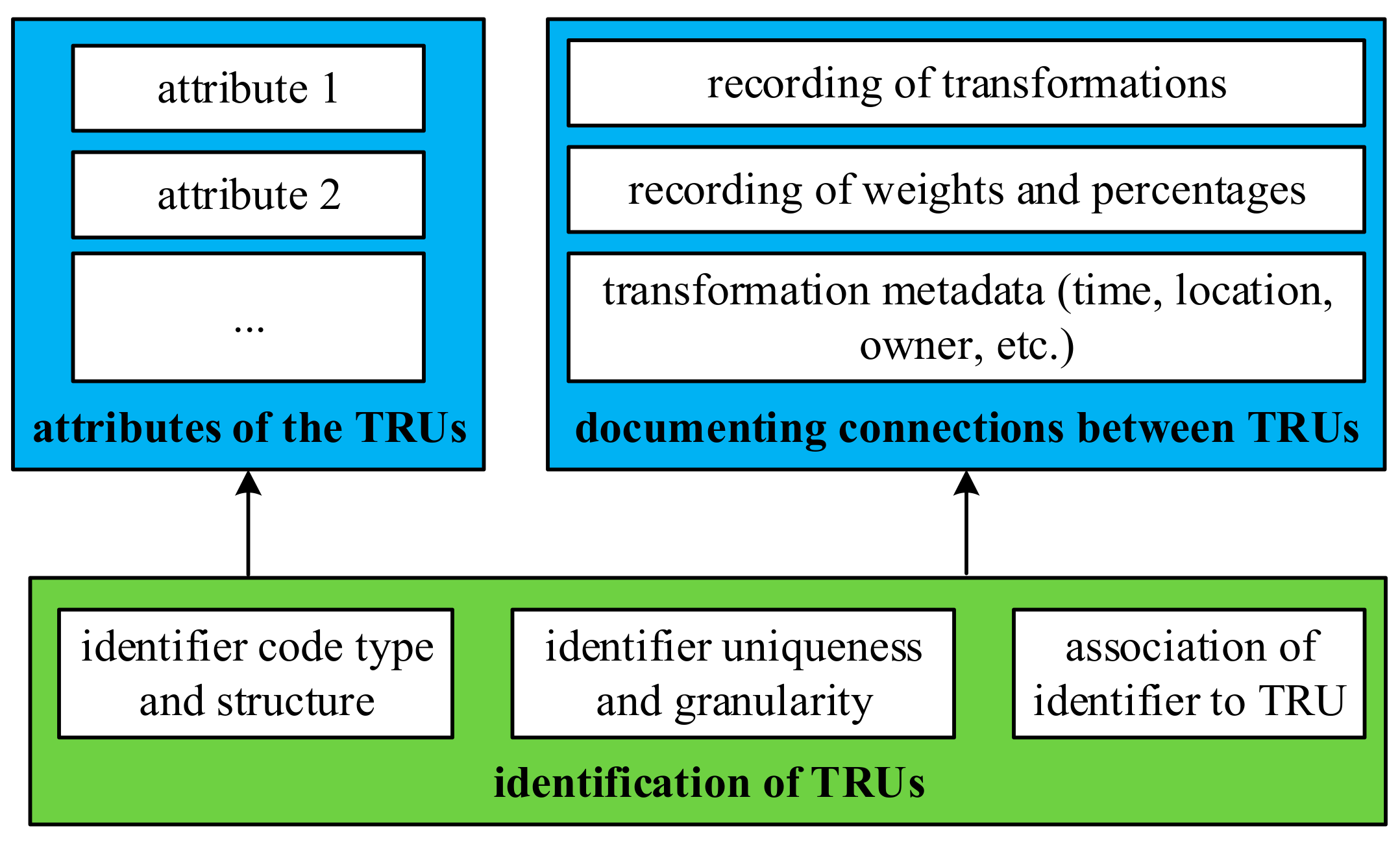
4]. A traceability system consists of three components, that is, identification of TRUs, documenting connections between TRUs, and attributes of the TRUs [
4], as shown in
Figure 1. The first component (identification of TRUs) is the most important component that the other two components build on, whereas the other two components are in principle independent [
4]. Identification of TRUs includes identifier code type and structure, identifier granularity and uniqueness, and association of identifier to TRU [
4].
Traceability usually improves product safety by providing a means for recall as well as proof of the authenticity of the product [
2]. However, most publications and reports on traceability only focus on the TRU attributes, because those who build the traceability system are mostly interested in the attributes of TRUs for data analysis and connections between TRUs for product tracking and recall [
4]. However, as an essential subsystem of quality management, these traceability systems do not ensure consumers against fraud [
2]. The data in the traceability system is only a claim [
4] rather than a fact. Therefore, the quality and safety of the product cannot be guaranteed since we can neither ensure the authenticity of the data [
5] in the traceability system, nor the authenticity of products in the real world. However, for consumers, their main concern is two problems: the first is whether the information on the system is authentic; the second is whether the information on the system is consistent with the actual product, which is usually call anti-counterfeiting. The two problems are equally important. Failing to solve either of the two problems will lead to a decline in the credibility of the traceability system.
The emergence of blockchain technology has solved the first problem well [
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15], whereas the second problem (anti-counterfeiting) is more difficult to solve. A product is counterfeit if its provenance, specification, quality, and so on are misrepresented [
16]. This applies to the product, its container, or other packaging or labeling information [
17]. Traditional anti-counterfeiting system and traceability system are generally regarded as two independent systems, which not only causes inconvenience to consumers but also makes them more vulnerable to cracking. Combining the two systems into one can effectively solve the above problems. More specifically, integrating anti-counterfeiting techniques into the traceability system can not only solve the anti-counterfeiting problem in the traceability system, but also make it more convenient to consumers.
In recent years, radio-frequency identification (RFID) is used in traceability to perform anti-counterfeiting. Feng Tian [
6] proposed to use RFID to guarantee the quality and safety of the agri-food products in the whole supply chain for the first time. However, this method has two fatal disadvantages. Firstly, the cost of RFlD tags is very high, which means that this method can only be applied to high-value goods. Secondly, investments in corollary equipment and updating the original system are huge [
6], which greatly limits the application of this method. In addition, RFID tag data is usually static and cannot be updated to reflect the latest conditions of products [
16]. Therefore, Kun et al. [
16] develop a novel RFID-based system suitable for counterfeit detection, where different types of on-chip sensors and in-system structures collect the necessary information to detect counterfeits. However, this system is designed for internet of things (IoT) devices and cannot apply to products without a printed circuit board (PCB) and integrated circuits (ICs). In [
18], the RFID tag is made into high-imitation electronic seed and packed in each seed bag to realize the anti-counterfeiting of seeds. In summary, RFID based solutions have disadvantages of high system complexity, high cost for both tags and equipment. Worse, most of the RFID tags on the market today can be easily cloned, which reduces the anti-counterfeiting performance of these solutions.
Non-RFID based solutions for anti-counterfeiting in the traceability system have been explored for a long time. Agrawal et al. [
19,
20] proposed a secured tag, which is a randomly distributed microparticles printed on the textile surface through an uncontrolled screen printing mechanism, for textile products anti-counterfeiting. It is low cost and convenient because only a smartphone with a camera is needed to perform counterfeit detection. However, the secured tag is based on the screen-printing method, so it cannot be applied to products other than textile. In addition, the information in the secured tag is very limited and cannot be manipulated manually. Wang et al. [
21] proposed a textile coding tag, where coded yarns having different optical features are used to represent digits, similar to barcodes. The textile coding tag’s inherent features link the physical product, therefore eliminate the dependency on external tags. However, the textile coding tag is easy to clone when the yarn coding procedure is provided. Chen et al. [
22] proposed to embed codes inside the components made by additive manufacturing (AM) for product authentication and identification of counterfeits but this method can only be applied to AM products and the code can only be captured with a micro-CT scanner. Trenfield et al. proposed to print quick response (QR) codes and data matrices were onto the surface of polymeric-based printlets for scanning using a smartphone device and designed a novel anti-counterfeiting strategy, which involved the deposition of a unique combination of material inks for detection using Raman spectroscopy. The above technologies either have poor performance in anti-counterfeiting, or can only be applied to specific products, or the equipment used to detect counterfeiting is too professional to be operated by ordinary consumers.
A few years ago, copy-detection graphical codes (CDGCs) [
23,
24] were proposed for document authentication. CDGC is a printed machine-readable image that cannot be physically cloned illegally, and its advantages are cheap generation and easy integration [
24], because the equipment an ordinary printer is used to make the CDGC tag, and the equipment used for copy detection of CDGC tag is an ordinary scanner. Two examples of CDGC are copy sensitive pattern (CDP) [
23] and two-level quick response codes (2LQR codes) [
24,
25,
26]. Compared to CDP, 2LQR codes have higher data capacity and are compatible with ordinary quick response code (QR code) readers. Therefore, the 2LQR code is a promising technology to solve the problem of anti-counterfeiting in the traceability system, because a 2LQR code is non-cloneable, easy to check, useable by consumers, etc., which are part of the characteristics of ideal anti-counterfeit technology [
17]. However, at present, there is no public work to integrate the 2LQR code into the existing traceability system. In addition, the difference between an authentic 2LQR code and its cloned version is tiny [
24] during copy detection, which makes the accuracy and robustness of copy detection inferior.
In this paper, we try to solve the safety and quality of the product by integrating an anti-counterfeiting technique (copy detection with 2LQR codes) into the traceability system. Our main contributions are as follows:
An anti-counterfeiting architecture for traceability systems based on 2LQR codes is proposed to solve the anti-counterfeiting problem in the traceability system. The risk of counterfeiting in the supply chain of the product is analyzed, and the corresponding requirements for the tags, packages, and traceability system are given to eliminate these risks. Based on the analysis above, an anti-counterfeiting architecture for traceability systems based on 2LQR codes is proposed, where the problem of counterfeit detection for the product is transformed into the problem of copy detection for the 2LQR code tag.
According to the characteristics of the traceability system, the generation progress of the 2LQR code is modified, and there is a corresponding improved algorithm to estimate the actual location of patterns in the scanned image of the modified 2LQR code tag to improve the performance of copy detection.
A prototype system based on the proposed architecture is implemented, where the consumers can perform traceability information queries by scanning the 2LQR code on the product package with any QR code reader. They can also scan the 2LQR code with a home-scanner or office-scanner, and send the scanned image to the system to perform counterfeit detection.
2. Materials and Methods
A typical product life cycle, as shown in
Figure 2, includes production, packing, warehousing, transportation, and consumption. Participants throughout the product life cycle in the supply chain include producers, distributors, retailers, and customers [
15]. The traceability system collects data throughout the product life cycle in each stage of the supply chain and provides query service to consumers.
Production is the progress to make new products. For industry, it refers to the manufacturing process. For plant agriculture, it refers to the process of planting and harvesting. For animal husbandry, it refers to breeding and slaughtering. The information about the production progress is usually collected with IoT technology [
27].
Packing is the process to make products into separate trading units, which are usually contained in the packages. The trading units are usually called TRUs in the traceability system, where a unique product identifier (product ID) is assigned to each TRU. The product ID is indexed to all data about the product in the system, such as packing time, packing location, etc. The product ID is then stored into a tag that will be attached to the product. The ID tag connects the products in the physical world with the data in the system. The most used tags are two-dimensional barcodes (2D barcodes) and RFIDs.
Transportation is the process where the products are transported from one participant to the next. It is usually performed by a producer, distributor, or retailer. The data about the transportation is collected and stored in the traceability system.
Warehousing is the process of temporary or long-term storage of a product, which is usually done by a distributor. The data about the warehouse is collected and stored in the traceability system.
Retailing is the process that the product reaching consumers, through either online or offline shopping. The data about the retailing is collected and stored in the traceability system.
In the consumption stage, the consumer can scan the ID tag attached to the product to query the traceability information.
2.1. Counterfeiting Analysis and Requirements of the Tags, Packages, and System
In this subsection, we consider the counterfeiting that occurs after the product is sent out by the producer. As shown in
Figure 2, the participants in the yellow box, that is, the distributor, retailer, and even consumer, are potential counterfeiters. The counterfeiter (red dashed box) may get authentic products from the producer, distributor, and retailer, and then send the counterfeit products to the distributor, retailer, and consumer. What’s more, they may have access to a part of the traceability system, such as uploading transportation information, warehousing information, retailing information, and querying traceability information of products. From the point of view of whether products, packages, and tags have been tampered with, counterfeiting can be divided into the following categories:
Recycled package: The packages of authentic products are reused to pack the counterfeit products. In this case, the packages, as well as the ID tags, are authentic.
Recycled ID tag: The ID tags of authentic products are removed from the original packages and reattached to counterfeit packages. In this case, only the ID tags are authentic.
Cloned ID tag: The ID tags are physically cloned and attached to counterfeit packages. In this case, the ID tags, the packages, and the products are counterfeit though the IDs stored in the ID tags are authentic.
Forged ID tag: The Counterfeiter generates IDs and then makes them into forged ID tags. In this case, the ID tags as well as the IDs stored in them, the packages, and the products are counterfeit.
To deceive the traceability system, the counterfeiter need only replace the authentic products with the counterfeit ones for the case of the recycled package, recycled ID tag, and cloned ID tag. For the last case, that is, the forged ID tag, the counterfeiter must have sufficient knowledge about how to generate qualified IDs and have access to upload producing and packing information linked to the forged ID.
Therefore, to prevent the above counterfeiting, the traceability and anti-counterfeiting system architecture must meet the following requirement:
The package must be tamper-evident. Then the consumer can easily tell whether it has been opened.
The ID tag must be reused-prevented. It will be destroyed once you try to remove it from the original package.
The ID tag must be clone-detectable. When it is physically cloned, we can distinguish the cloned one from the original one.
The ID assignment of the system must keep secret from any potential counterfeiter.
For the first requirement, traditional tamper-evident packing technology, such as film wrappers, shrinkable seals, and bands, can be used.
The second and third requirements are the difficulties and emphases of the system. The commonly used 2D barcodes are easy to be cloned. Although there are techniques, such as material ink [
28] and secured tag [
20], can prevent the code to be cloned, they can only be applied to specific products. It is complicated to prevent the reused of RFID tags. Furthermore, most RFID tags in use can be cloned because they do not have the physical unclonable function [
16] (PUF) embedded. The 2LQR code [
25], which is designed to increase the capacity and security of the QR code and can be used for document authentication [
26], is a promising solution. If it is printed on a void sticker [
29] or fragile label, the 2LQR code tag can be both clone-detectable and reused-prevented. However, as a new emerging technology, the performance of 2LQR code in copy detection needs to be improved. The improvement of the 2LQR code will be discussed later in this paper.
The last requirement is easy to meet by restricting access to the ID assignment to those who are trusted.
2.2. Architecture of the System
The anti-counterfeiting architecture for traceability systems based on 2LQR codes is shown in
Figure 3, which is divided into four layers: database, back end, front end, and device. On the database and back end layers, the white solid boxes are submodules of a basic traceability system, and the blue dashed boxes are submodules for anti-counterfeiting.
Database layer: The traceability database stores traceability information of products throughout all their life cycle, and the anti-counterfeiting database stores information for counterfeit detection, such as product status, parameters of the clone-detectable ID tags, etc. The implementation of the databases can be traditional central database, or distributed ledger technologies (DLT) such as blockchain [
30].
Back end layer: There are three modules, ID assignment, data collection, and information query. The ID assignment module generates the product ID as well as the corresponding 2LQR tag for every new product in the packing stage. The ID and the information about the corresponding product are then stored in the traceability database. The parameters for the 2LQR tag are stored in the anti-counterfeiting database. As mentioned in the previous subsection, the ID assignment module can only be accessed by the producer. The data collection module collect data in the stages of production, packing, warehousing, transportation, retailing, and stores the data in the traceability database. Besides, the status about which stage the product is undertaken is stored in the anti-counterfeiting database. The information query module provides query services for consumers, including traceability information and counterfeit detection.
Front end layer: Provides an operation interface for back end modules. For the ID assignment module and data collection module, a web page and client software for personal computers (PCs) are provided. For the information query module, web page as well as mobile application software (APP), such as iOS APP, Android APP, can be provided.
Device layer: In the production and packing stage, the producer uses a web page or client software on PC to assign IDs to each product, print the corresponding 2LQR tag with a printer, and attaches it to the product. Besides this, the production and packing information is uploaded to the traceability database. In the warehousing, transportation, and retailing stage, the distributor or retailer can use any QR code scanner or reader to get the product ID and update the corresponding information to the traceability database. In the consumption stage, the consumer can use a mobile phone with a camera to scan the 2LQR tag for traceability information queries. The consumer can also use a home or office scanner to scan the 2LQR tag with specific parameters and send the scanned image to the counterfeit detection submodule for counterfeit detection.
At present, the packaging of most products on the market is sealed. Therefore, is reasonable to assume that the package for each TRU is sealed with tamper-evident packing technology and the tag cannot be removed from the package without damaging it. As a result, the TRU, the package, and the tag are one-to-one and cannot be separated without being discovered. Therefore, the counterfeit detection of the product is simply the copy detection of the 2LQR code tag on its package.
As the two most important modules of the system, the 2LQR code generation, and counterfeit detection module are described in detail in the following subsections.
2.3. Implementation of the 2LQR Tag Generation Submodule
In this subsection, the 2LQR code and physical cloning process are introduced. Then the modification of the 2LQR code is made according to the requirement of the traceability system for better performance in copy detection.
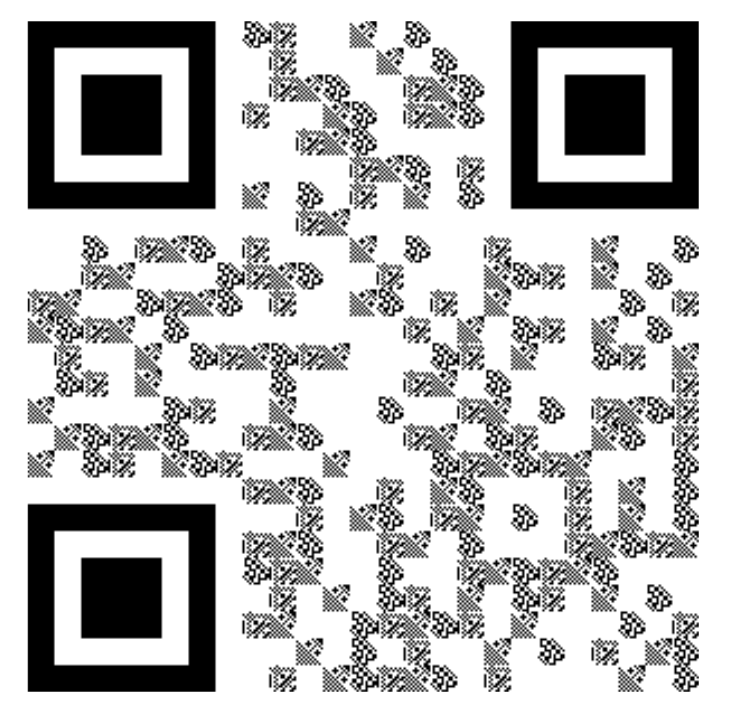
2.3.1. The 2LQR Codes and Physically Clone Process
2LQR codes are QR codes where dark modules are replaced with specific textured patterns that are sensitive to the P&S process [
25]. 2LQR codes are originally designed to improve the storage capacity of QR codes [
25] and perform document authentication [
26]. Document authentication is to detect whether the document is physically cloned or not. Therefore, document authentication is also called copy detection. Suppose that there are
original patterns
, and the corresponding P&S degraded versions are
, the correlation between the original and degraded patterns
satisfies [
26]
Suppose that
and
are
matrices, i.e.,
, the correlation between them is
where
and
are the mean value of
and
, respectively.
An example of a 2LQR code for copy detection is shown in
Figure 4. Except for modules in the three finder patterns, all black modules are replaced with textured patterns. The textured patterns used in
Figure 4 are shown in
Figure 5. The size of the textured patterns, which are the same as that of modules in the QR code image, is
pixels, and each pixel is black or white.
The copy detection of 2LQR makes use of the fact that the counterfeiter does not have access to the original patterns
[
26] and it is impossible to recover the original patterns
from its P&S degraded version
because the P&S process can be considered as a PUF [
31].
The physical cloning (or copy) process of a 2LQR code and a textured pattern is shown in
Figure 6. The original image of the 2LQR code
is a digital image generated with a program. The textured patterns
in
is an ideal binary image. Then the original image is printed to make a tag, expressed by
, which is an analog image in the physical world. The textured patterns
in
is blurred because of the degradation caused by the printer. We call
an authentic tag because it is the printed version of the original image. Then
is scanned with a scanner to get a digital image
, which is called the P&S version of
. The textured patterns
in
correspond with the P&S versions of
. The process to get
from
is a P&S process in which the input and output are both digital images. The counterfeiters, who have only access to
and
, want to make a counterfeit of the authentic tag
. They print
to get a counterfeit tag
. The process to make a counterfeit tag
from the authentic tag
is physical cloning (or copy). The pattern in
is further degraded. The counterfeit tag
is scanned with scanner to get a digital image
, which is the P&S version of
.
Copy detection is to distinguish between the authentic tag
and the counterfeit tag
. However, the program can only process digital images. Therefore, the copy detection program is actually to distinguish their scanned versions, that is,
and
. Copy detection of 2LQR codes is based on the information loss principle, that is, every time an image is printed or scanned, some information is lost about the original digital image [
24]. The correlation coefficient (or correlation) is an indicator to describe the information loss. The following proposition has been proved in [
32]:
The correlation between textured patterns in and is greater than the correlation between textured patterns in in and , i.e., . More generally, suppose that the k-th P&S version of is , this proposition is generalized as .
The proposition describes the loss of information in the P&S process. The original pattern is used as a reference to measure information loss, as the copy detection program of 2LQR codes does. However, the textured patterns should not be accessible to potential counterfeiters. Therefore, the copy detection program of 2LQR codes should be run in a relatively safe environment, such as the servers where the traceability system is deployed. That is to say, the customer scans the 2LQR image and sends it to the traceability system. Then the system carries out the copy detection and returns the result back to the customer.
2.3.2. Modification of 2LQR Code Generation Process
The 2LQR code generation includes three steps: public message encoding, private message encoding, and replacing black modules in the QR code with textured patterns [
25]. The public message is encoded into the QR code directly and can be retrieved with any QR code reader, whereas the private message is scrambled with a key after it is encoded with an error correction code and must be captured with a scanner instead of a camera. However, in the traceability system, the ID tag only needs to store the product ID and the private message is not needed. Therefore, we record the locations of textured patterns instead of the private message encoding step.
The generation of the modified 2LQR code tags is shown in
Figure 7. Firstly, the identifier
for a TRU are generated by the traceability system. Then the producer generates a QR code that stores the
. The black modules in the QR code are replaced with textured patterns
to get a 2LQR code. Usually, the patterns
are predetermined with a corresponding threshold
used for copy detection. More details about the threshold can be found in [
25]. The replace scheme is about replacing the black modules with
. Since we do not need to store information in the private storage level of 2LQR code as in [
24,
25,
26], we can replace the black modules randomly with textured patterns, or just simply replace all the black modules with
in order of
. The patterns, the threshold, and the replace scheme are then stored to the traceability system. The generated 2LQR code is an image that is called an original image. At last, the 2LQR code is printed on paper or other material to make a tag. The tag, also called the authentic tag, is the printed version of the original image. The parameters of tag printing, such as printing resolution, are also stored in the system.
2.4. Implementation of Counterfeit Detection Submodule
As mentioned above, the counterfeit detection of a product is the copy detection of the 2LQR code tag in this system. Therefore, a copy detection process of the modified 2LQR code tag is introduced here. Making use of the fact that the locations of textured patterns are recorded, an improved algorithm to estimate the actual location of patterns in the scanned image is proposed.
2.4.1. Copy Detection Process of the Modified 2LQR Code Tag
The copy detection process for the modified 2LQR code tag is shown in
Figure 8. Firstly, the identifier
is extracted using a QR code reader. Then the printing parameters (such as printing resolution) are queried from the system with
. The 2LQR code tag is then scanned using a scanner with the same resolution as the printing. The test 2LQR code image
is extracted from the scanned image. The authentic indicator
of
is calculated after the textured patterns
with corresponding threshold
, the replace scheme are queried from the system. The indicator
is the mean value of all correlations between patterns in
and the corresponding patterns in the same location of
[
26]. The correlations between patterns are calculated with Equation (2). If the indicator is not less than
, the tag is considered to be authentic. Otherwise, the tag is considered to be an illegal copy.
2.4.2. An Improved Algorithm to Estimate the Actual Location of Patterns
The accuracy of locations of patterns in the scanned image
is very important to calculate
. In [
26] the locations of patterns are determined using the reference decode algorithm for QR code [
33], and the detected patterns are classified into
classes
using pattern recognition algorithm. There are two problems with the method above. Firstly, local distortion of the 2LQR image, which is very common and can affect the accuracy of pattern location, is not handled by the reference decode algorithm. Secondly, the accuracy of the pattern recognition algorithm in [
26] is not 100%, resulting in the wrong correspondence between some detected patterns and their original patterns. The two problems make the indicator
for authentic tag decrease and reduce the accuracy of copy detection. Therefore, we proposed an improved algorithm to estimate the actual location of patterns.
Instead of recognizing each pattern in the test 2LQR image
, we store the ideal locations of each class of patterns
in the system. For example, the ideal locations (coordinates of the upper left of the patterns) of the first class of patterns
in the 2LQR code in
Figure 4 are
, where the origin
is on the upper left corner of the 2LQR code, and the positive direction of the
axis is downward.
Assume that there are
patterns in
, expressed by
, their corresponding original patterns are
, respectively, and their ideal coordinates of the upper left are
, respectively. Set the width and height of the original patterns are
and
, respectively. The key schematic of the process of estimating the actual locations of the patterns is shown in
Figure 9, where the same 2LQR code as in
Figure 4 is used, that is,
.
Firstly, the 2LQR code tag is scanned and an image containing the 2LQR is obtained, as shown in
Figure 9a.
Secondly, the reference decode algorithm for QR code [
33] is used to process the scanned image. In this step, the geometric deformation is corrected and the 2LQR code is rotated to a specific direction, that is, the three finder patterns are in the lower left, upper left, and upper right, respectively. Besides, the 2LQR code is resized to the same size as its original image, resulting in the test image
, as shown in
Figure 9b.
The ideal locations of all patterns that were queried from the traceability system are shown in
Figure 9c, where the original patterns of detected patterns
in red, green, blue boxes are
,
,
, respectively.
For each detected pattern
, the estimated location of it is searched within the neighborhood of its ideal location, as shown in
Figure 9d. The solid red box is the neighborhood of the ideal location of the last detected pattern
, where
in the case in
Figure 9d. Set the distance between the edges of the dotted red box and solid red box in horizontal and vertical are
and
, respectively. The coordinate of upper left of the neighborhood of each detected pattern
is
. The width and height of them is
and
, respectively. The estimated location of
is
where
is the detected pattern
when its location is
.
Obviously, the correlation between the original pattern
and the detected pattern in the estimated location
is not less than the correlation between the original pattern
and the detected pattern in the ideal location
, i.e.,
Because all patterns satisfy Equation (1), the algorithm above can find the exact location of the patterns in large probability and improve the accuracy of , which will increase the accuracy of copy detection for the 2LQR code tag.
Now we discuss the complexity of the proposed algorithm. For each pattern, there are correlations to be calculated and compared, as shown in Equation (3). According to Equation (2), loops are needed to calculate a correlation between two patterns. Therefore, the overall complexity for the proposed location estimation algorithm is , where is the number of patterns in a 2LQR code tag.
2.4.3. Calculation of Threshold for Copy Detection
Ideally, the threshold is calculated with all the scanned images of the authentic and counterfeited 2LQR code tags. However, it is impossible to get all counterfeited 2LQR code tags. What is more, in practical application, the number of authentic 2LQR code tags is usually large and it is not practical to scan all the authentic 2LQR code tags by the producer. Therefore, a compromise is to use a small part of the authentic and counterfeited 2LQR code tags to calculate the threshold .
Suppose that the scanned image of the authentic and counterfeited 2LQR code tags are
and
, respectively, where
and
are the number of authentic and counterfeited 2LQR code tags. The threshold
is
3. Results
In this section, two experiments are performed to measure the performance of the modified 2LQR code and the corresponding improved algorithm in copy detection. Then a prototype system for the proposed architecture is implemented to verify how the architecture works to fight against counterfeiting. At last, a comparison of the proposed architecture and other solutions, such as RFID based solutions, is made, which shows that counterfeit detection using 2LQR code has the advantages of low cost, high reliability, and high usability.
3.1. Performance of the Modified 2LQR Code and the Corresponding Improved Algorithm
To measure the performance of the modified 2LQR code in copy detection and the improved algorithm to estimate the actual location of patterns, 120 2LQR codes with random content were generated with the algorithm described in
Figure 7 and printed to make 120 authentic tags with printer HP LaserJet Pro M126 MFP. Then the tags were copied to make 120 counterfeit tags with HP Color LaserJet Pro MFP M377. The print and copy processes were both performed with a 600-dpi resolution. There were 240 2LQR code tags in total to be tested. The paper used to make the tags in the above process was A4 printer paper. The algorithm was implemented using MATLAB R2019a and ran on HP Z230 Tower Workstation with an Intel Xeon E3-1246 v3 processor and 8 GB memory.
In the first experiment, we scanned the tags using the same machine as the printing machine, that is, HP LaserJet Pro M126 MFP. Then the copy detection process described in
Figure 8 is performed. This experiment is similar to that in [
26], as shown in
Figure 10.
Without the improved algorithm to estimate the actual location of patterns, the authenticity indicators for authentic and counterfeit 2LQR code tag images overlap seriously in some areas, such as data points around 20, 50, etc. When the improved algorithm is applied, the authenticity indicators increase for both authentic and counterfeit 2LQR code tag images. However, the standard deviation of indicators for authentic and counterfeit 2LQR code tag images decreases by 57.53% and 81.72%, respectively, which means that the improved algorithm improves the robustness of copy detection. Therefore, it is easy to distinguish between them according to the authenticity indicators.
The average runtimes to calculate authenticity indicators for a single 2LQR code tag with and without the improved algorithm are 0.0754 s and 1.8203 s, respectively. The runtime overhead is significant. However, compared to other steps, such as scanning the tag, which usually needs tens of seconds, a few seconds runtime overhead is acceptable.
To perform copy detection, we select three sets of scanned images to calculate the threshold with Equation (5). The first set includes all the 240 authentic and counterfeited 2LQR code tags. The second set includes 10 tags randomly selected from the 120 authentic tags and 10 tags randomly selected from the 120 counterfeited tags. The three sets include the first 10 tags of the 120 authentic tags and the first 10 tags of the 120 counterfeited tags. The thresholds calculated with the three sets of data before the improved algorithm applied are , , , respectively. After the improved algorithm applied, the thresholds are , , , respectively. It is clear that the difference of thresholds calculated with the different sets of images is very small.
Without the improved algorithm, the accuracies of copy detection are 84.61%, 81.25%, 98.89%, respectively, when , , , respectively. After the improved algorithm applied, the threshold, the accuracies of copy detection are 100%, 100%, 100%, respectively, when , , , respectively. Obviously, a small error of threshold will affect the accuracy of copy detection significantly, whereas when the improved algorithm is applied, the accuracy is unchanged when the threshold varies. This means that the proposed algorithm improves both the accuracy and robustness of copy detection.
In the second experiment, we scanned the tags using the same machine as the copy machine, that is, HP Color LaserJet Pro MFP M377. The results are shown in
Figure 11. The standard deviation of indicators for authentic and counterfeit 2LQR code tag images decrease by 64.46% and 80.65%, respectively, which is similar to the results in the first experiment.
Using the same thresholds calculated in the first experiment to perform copy detection, the accuracies before and after the improved algorithm is applied are 96.84%, 93.94%, 98.85% and 100%, 100%, 100%, respectively, which is very similar to that in the first experiment.
The average runtimes to calculate authenticity indicators for a single 2LQR code tag with and without the improved algorithm are 0.0754 s and 1.8163 s, respectively, which is very similar to that in the first experiment.
The two experiments have shown that:
The improved algorithm can increase the accuracy of copy detection for 2LQR code to 100% with lesser standard deviation of indicators, meaning that the improved algorithm improves the robustness of copy detection.
The scanner used for copy detection has little effect on the accuracy of copy detection for 2LQR code.
3.2. Comparison of 2LQR Code with Other Barcodes
Originally, barcodes do not have the feature of copy detection. However, there are researches on the copy detection of 2D barcodes in recent years. To compare the performance of copy detection for different barcodes, the normalized accuracy (NACC) [
34] is used:
where
FAR is the percentage of counterfeited samples that have been falsely accepted as genuine,
FRR is the percentage of genuine samples that have been falsely accepted as counterfeit.
We used the data samples of the first experiment in
Section 3.1 to calculate
FAR,
FRR, and NACC of 2LQR codes and modified 2LQR codes (the improved algorithm is applied) with different thresholds, as shown in
Table 1, where the performance of DFT-based, LBP-based, and DFT+LBP-based barcodes proposed in [
34] are also listed.
Table 1 shows that the performance of DFT-based, LBP-based, and DFT+LBP-based barcodes is better than the 2LQR code because they have lower FRR. However, the performance of the modified 2LQR code is the best no matter which threshold is used.
3.3. The Prototype System for the Proposed Architecture and Comparison with other Solutions
To verify the anti-counterfeiting capability of the proposed architecture, a prototype system based on the architecture is implemented, as shown in
Figure 12. The software platform of the prototype system is Windows 10. In the database layer, the databases are implemented with MariaDB. In the back end, the submodules for anti-counterfeiting are implemented with MATLAB and encapsulated with a windows batch file, which is called by the information query module written in PHP. The system is running on HP Z230 Tower Workstation with Intel Xeon E3-1246 v3 processor and 8 GB memory. The mobile phone used for traceability information query is iPhone XR with iOS 14.2, and the Camera application is used to scan the 2LQR code.
The tags generated in the previous subsection are used to test the prototype system. An example of the tags is shown in
Figure 13, where the original image, the scanned images of the authentic and counterfeit tag are shown in (a), (b), and (c), respectively. In order to simulate the case of forged tag, we intentionally delete the data of a tag from the traceability database and anti-counterfeiting database, as shown in
Figure 13d.
3.3.1. Traceability Information Query Test
Firstly, the traceability information query of the prototype system is tested. Reading the tag with any QR code reader, such as the iPhone camera program, a web page showing the traceability information of the product is opened, as shown in
Figure 14. Note that the product ID stored in the counterfeit tag is the same as that in the authentic tag. Therefore, the traceability information for the two tags is the same. Obviously, no data is shown for the forged tag because there no data in the databases that links to the forged ID.
3.3.2. Anti-Counterfeiting Test
Click the
check button in the traceability information query web page to open the anti-counterfeiting page, as shown in
Figure 15. All tags are correctly classified by the prototype system and detailed instructions are given to consumers. After anti-counterfeiting checking of the tags, all checking records are stored in the database and will be shown in the traceability information query web page, as shown in
Figure 16.
The response time of the counterfeit detection is an important index to show the efficiency of the anti-counterfeiting method. The response time mainly includes two parts: time to scan the 2LQR tag (
) and time to upload the scanned image to get counterfeit detection result (
). To get the response time, we scanned 10 2LQR tags and calculated the average time as the
, and calculate the average time of uploading the 10 scanned images to get counterfeit detection results as the
. The response times for different scanners are shown in
Table 2. The response time is less than 1 minute, showing the high efficiency of the proposed method in counterfeit detection.
3.3.3. Comparison with Other Works
The comparison of the proposed architecture with other anti-counterfeiting solutions is shown in
Table 3. We compare them in three areas, that is, application scope, cost (tag cost, reading device cost, and anti-counterfeiting device cost), and anti-counterfeiting performance (recycled package detection, recycled ID tag detection, cloned ID tag detection, and forged ID tag detection). Compared with CDTA [
16] and Textile Coding Tag [
21], the proposed architecture is more general and low cost. Compared with Frequent pattern mining [
35] and Textile Coding Tag [
21], the proposed architecture has better performance in anti-counterfeiting. Therefore, the proposed architecture is a promising solution for product anti-counterfeiting with the advantages of low cost, generality, and good performance.
4. Discussion and Conclusions
In this paper, the problem of product counterfeiting in its life cycle is discussed and an anti-counterfeiting system architecture for traceability based on modified 2LQR codes is proposed to solve this problem, where the problem of counterfeit detection for the product is transformed into the problem of copy detection of the 2LQR code tag. To effectively perform copy detection of 2LQR code tags, an improved algorithm is proposed to estimate the accurate location of patterns in the scanned 2LQR code image. Experiments show that the accuracy and robustness of copy detection for 2LQR codes improve when the improved algorithm is applied. Besides this, the experiments also show that the scanner used for copy detection has little effect on the accuracy of copy detection for the 2LQR code tag. Therefore, customers can use any qualified scanner to scan the 2LQR tag for copy detection. In summary, using 2LQR codes is a low-cost, reliable, and convenient solution for product counterfeit detection in traceability systems.
The prototype system of the proposed architecture proves the feasibility of the proposed architecture. Compared with other anti-counterfeiting solutions, the proposed architecture has advantages of low cost, generality, and good performance. Therefore, it is a promising solution to replace the existing anti-counterfeiting system.
However, the data samples for 2LQR codes are limited in the experiments, and more experiments to test different printers and scanners should be done in the future. Moreover, copy detecting of 2LQR codes by taking photos instead of scanning with a scanner is also an attractive research direction.