An Evolutionary Game Theory-Based Method to Mitigate Block Withholding Attack in Blockchain System
Abstract
1. Introduction
- To the best of our knowledge, this paper is the first to use a dynamic method to study the selection of the profitable optimal strategy for mining pools under a BWH attack.
- Based on the change in the supervision and punishment degree of the blockchain system, this paper implements a model in which mining pools with different probabilities can smoothly be used to select the optimal strategy of obtaining block rewards under different BWH attack scenarios over time using the evolutionary game method.
- We obtain optimal strategies regarding the different degrees of punishment and the tightness of regulation in a blockchain system by analyzing various BWH attack situations on the dynamic replication equation.
- The experimental results show that a dynamic evolutionary game can effectively make the mining pool select the optimal strategy to obtain a block reward under different parameter transformations and BWH attack scenarios of the blockchain system. The experimental results also show that the model and solving method can satisfy the defect that the profit status of static game players cannot change with time.
2. Background
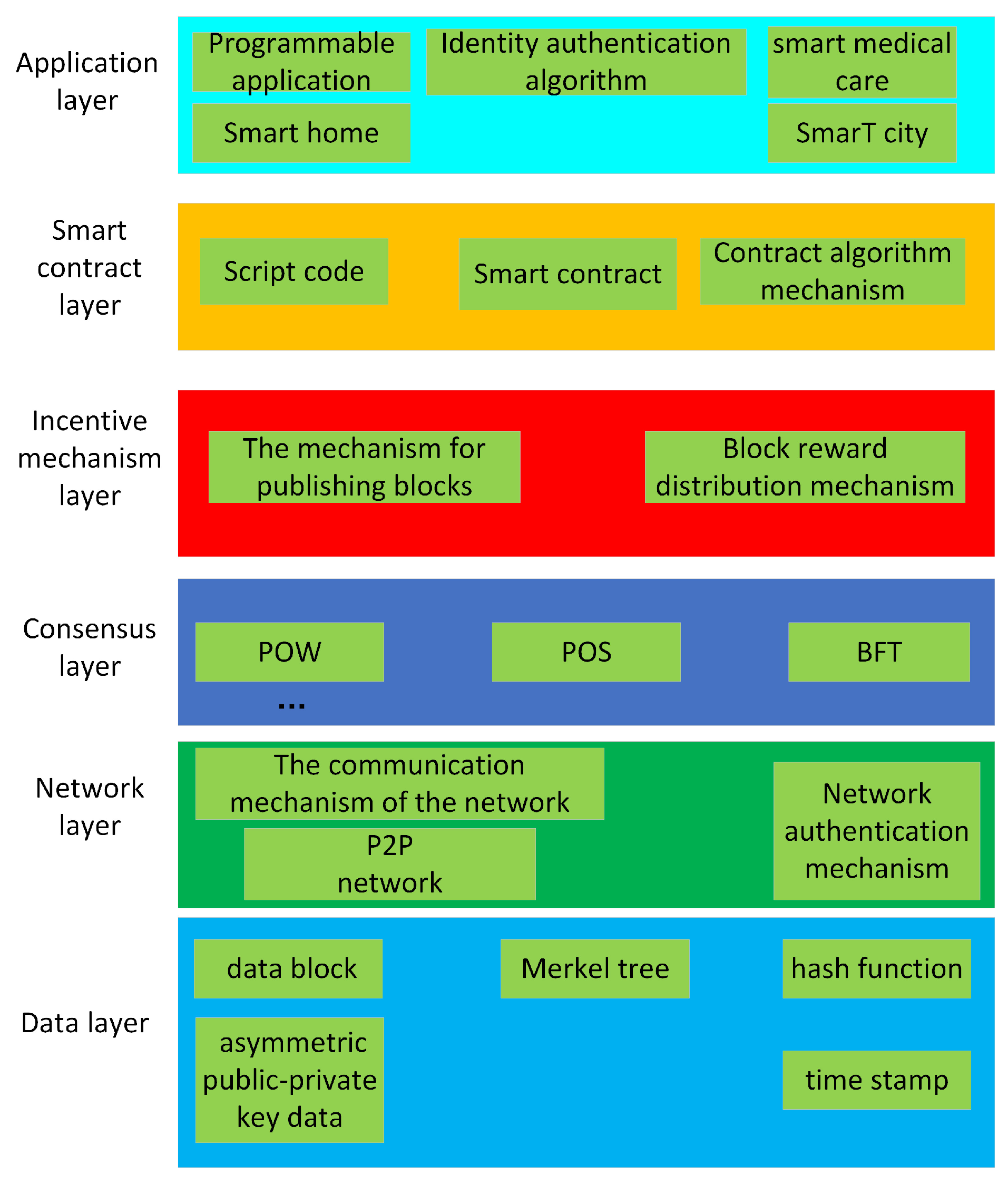
2.1. Blockchain System
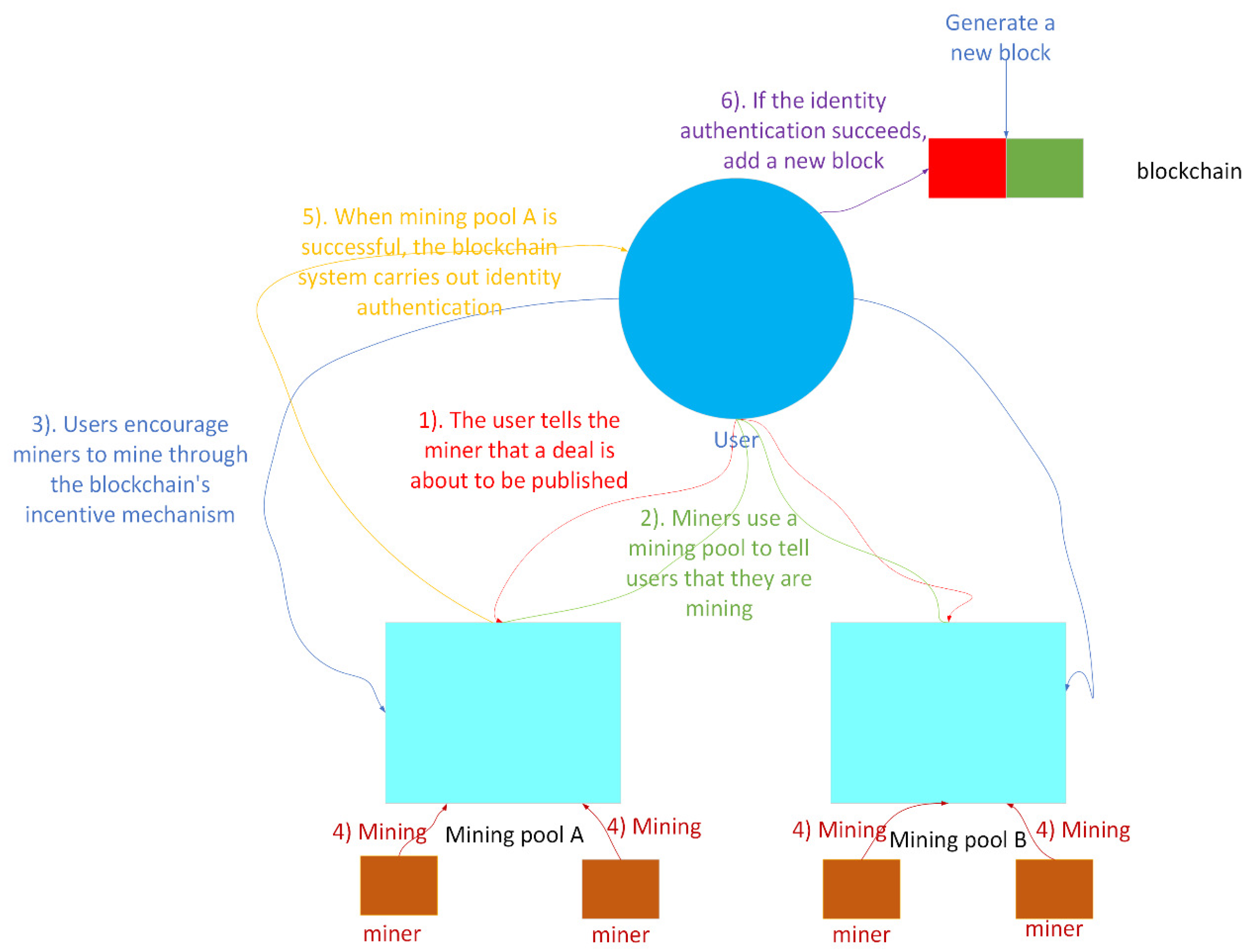
2.2. Pow Consensus Algorithm
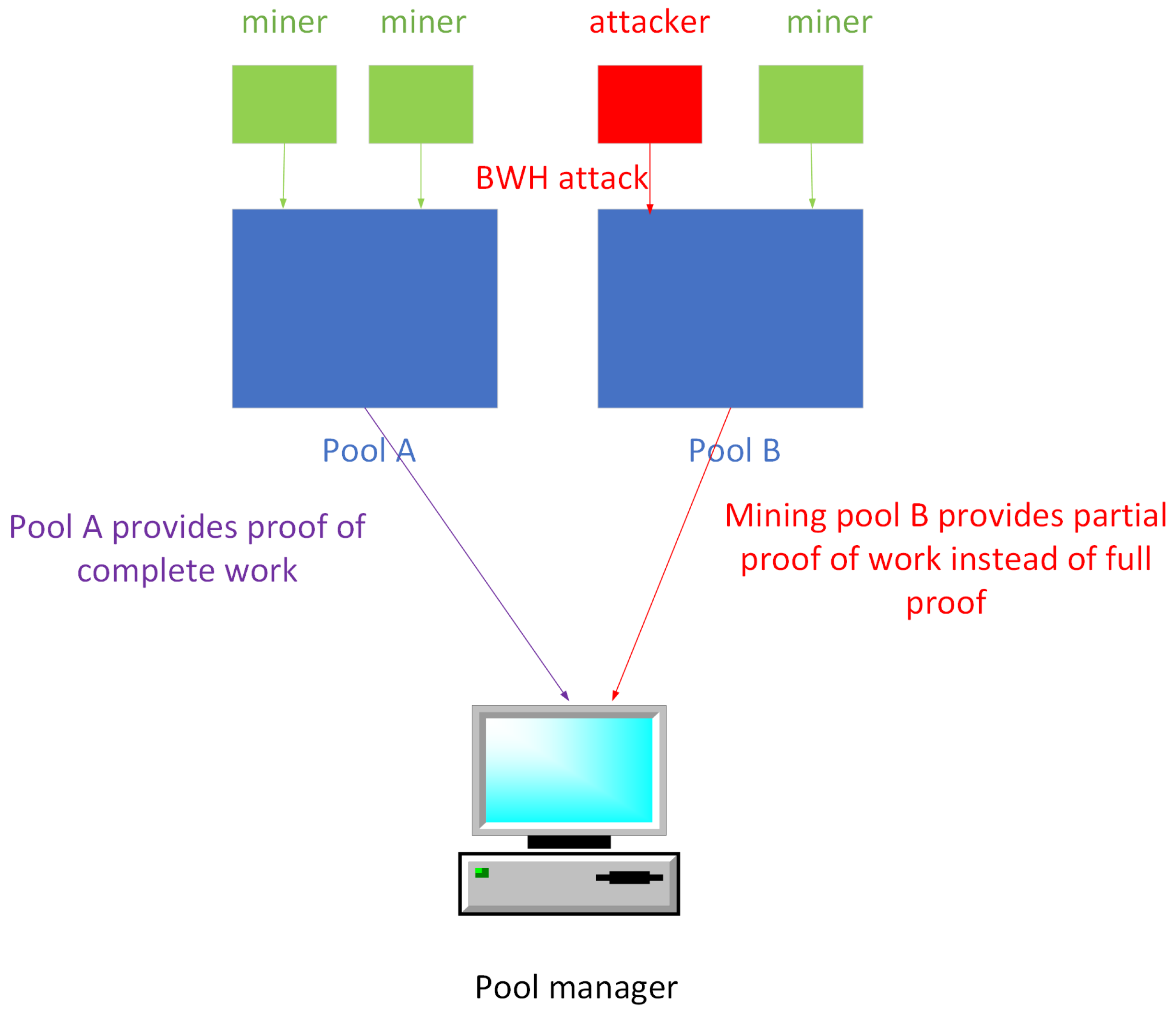
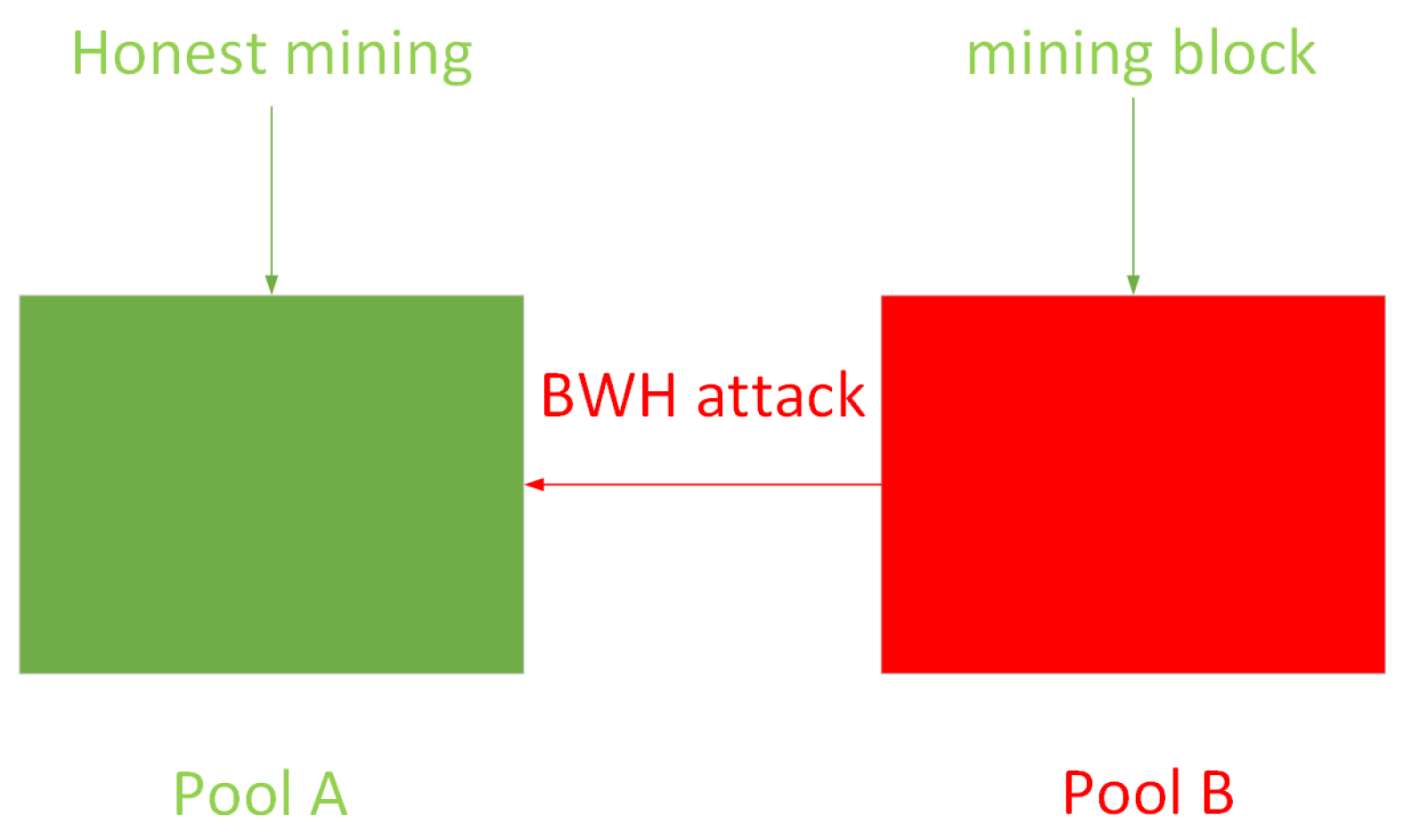
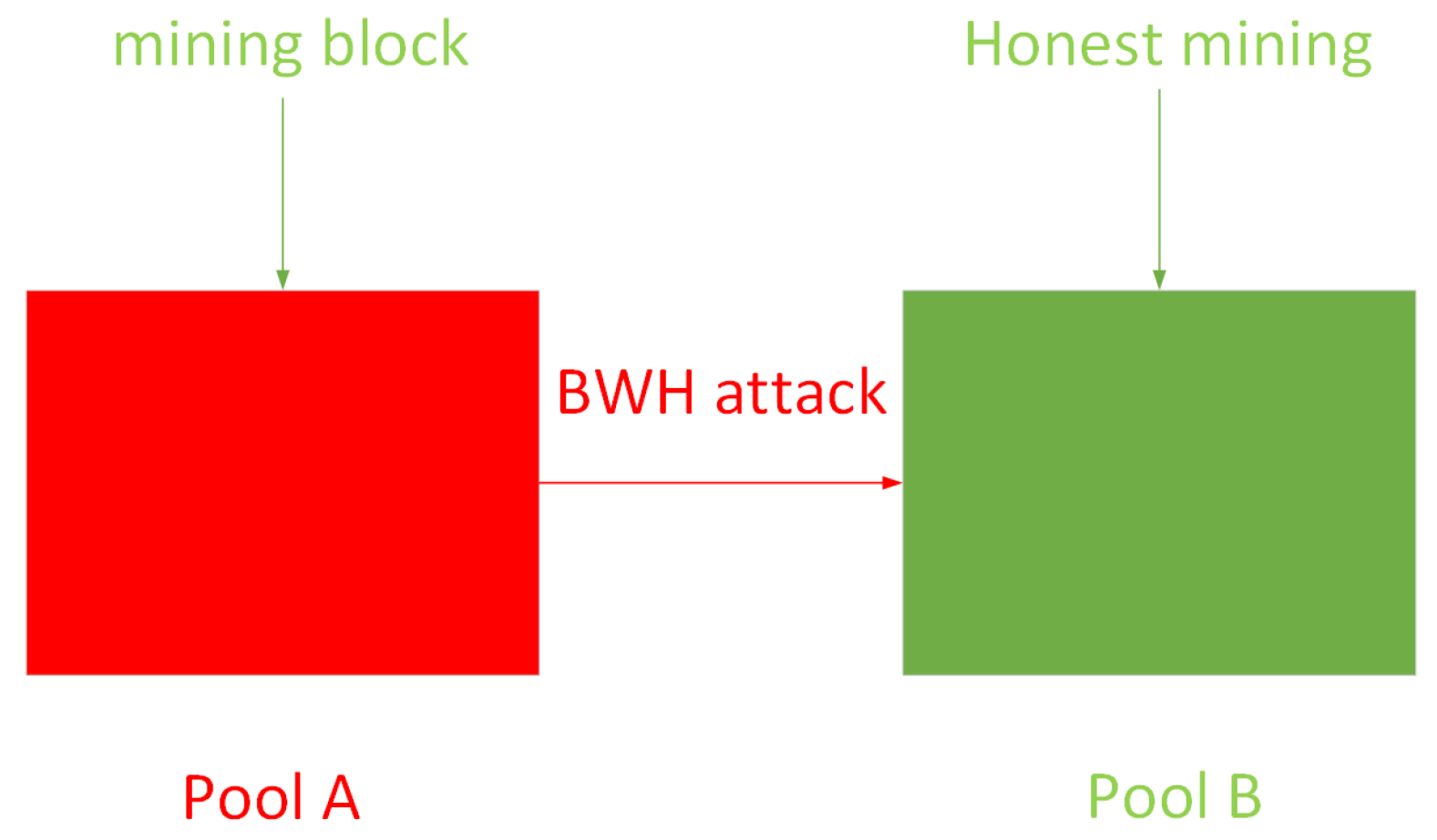
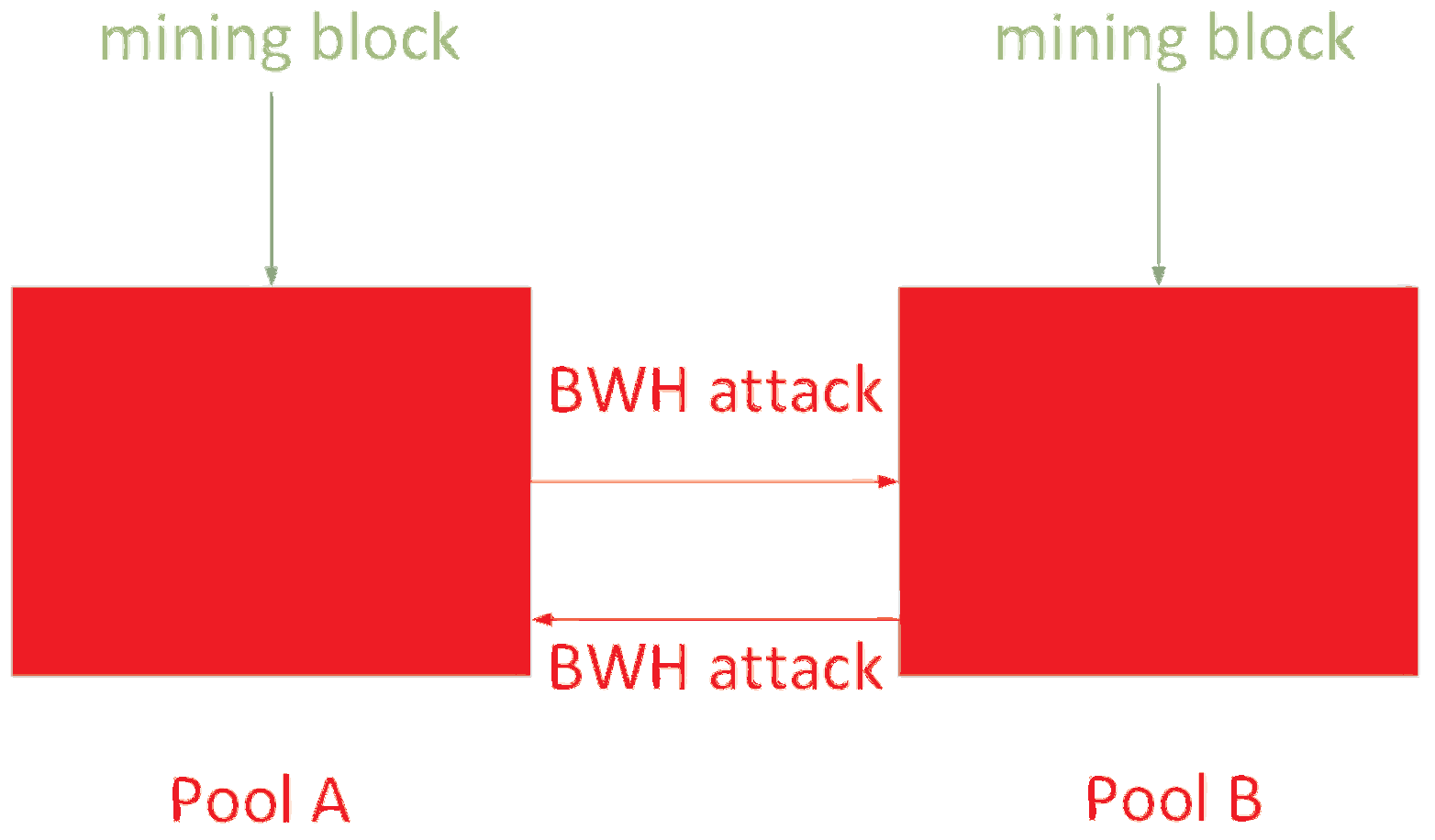
2.3. Block Withholding Attack
2.4. Research Progress and Related Work
3. The Proposed Evolutionary Game Theory Model and Solutions
3.1. Problem Description
3.2. ESS Model Description
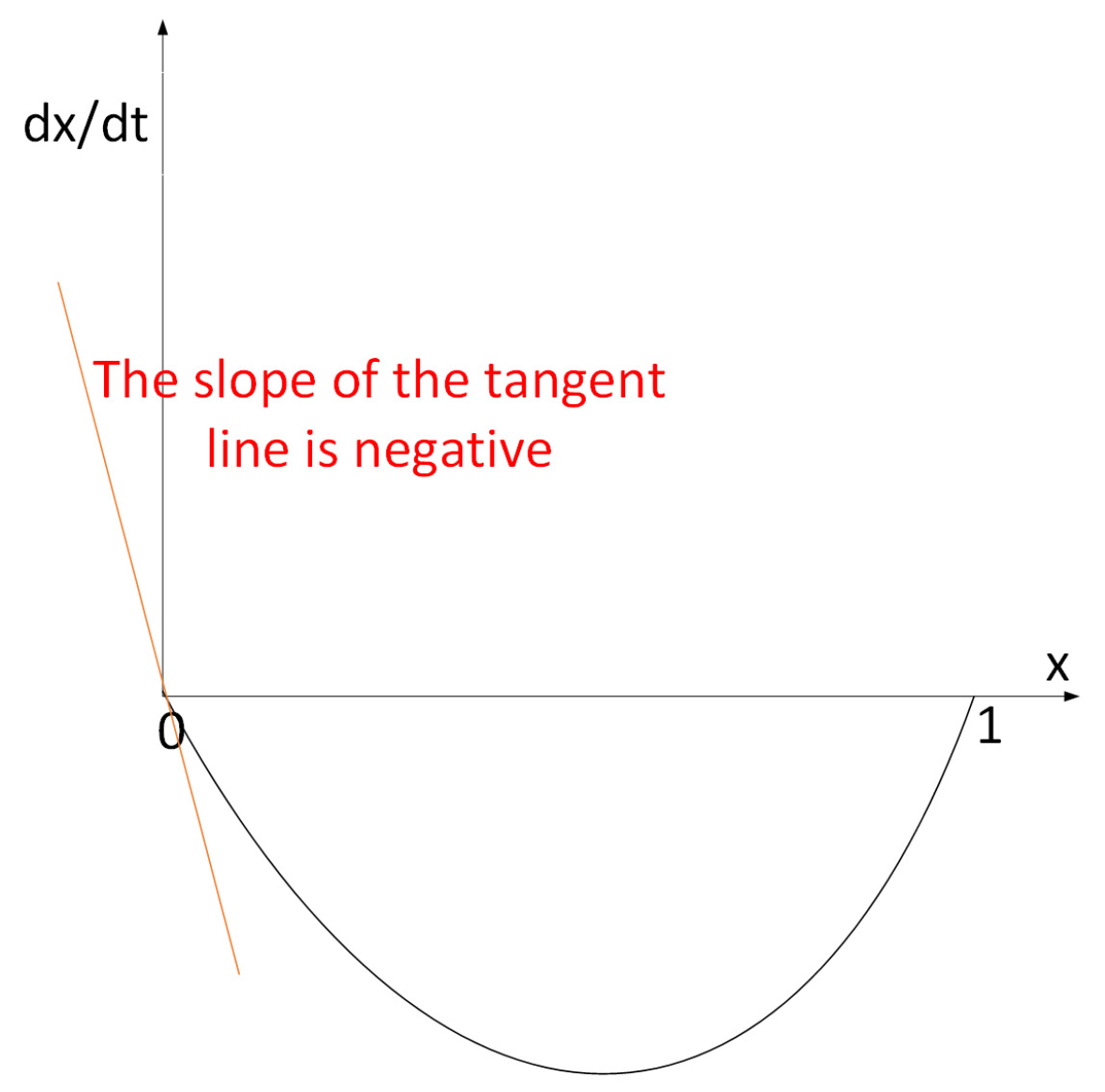
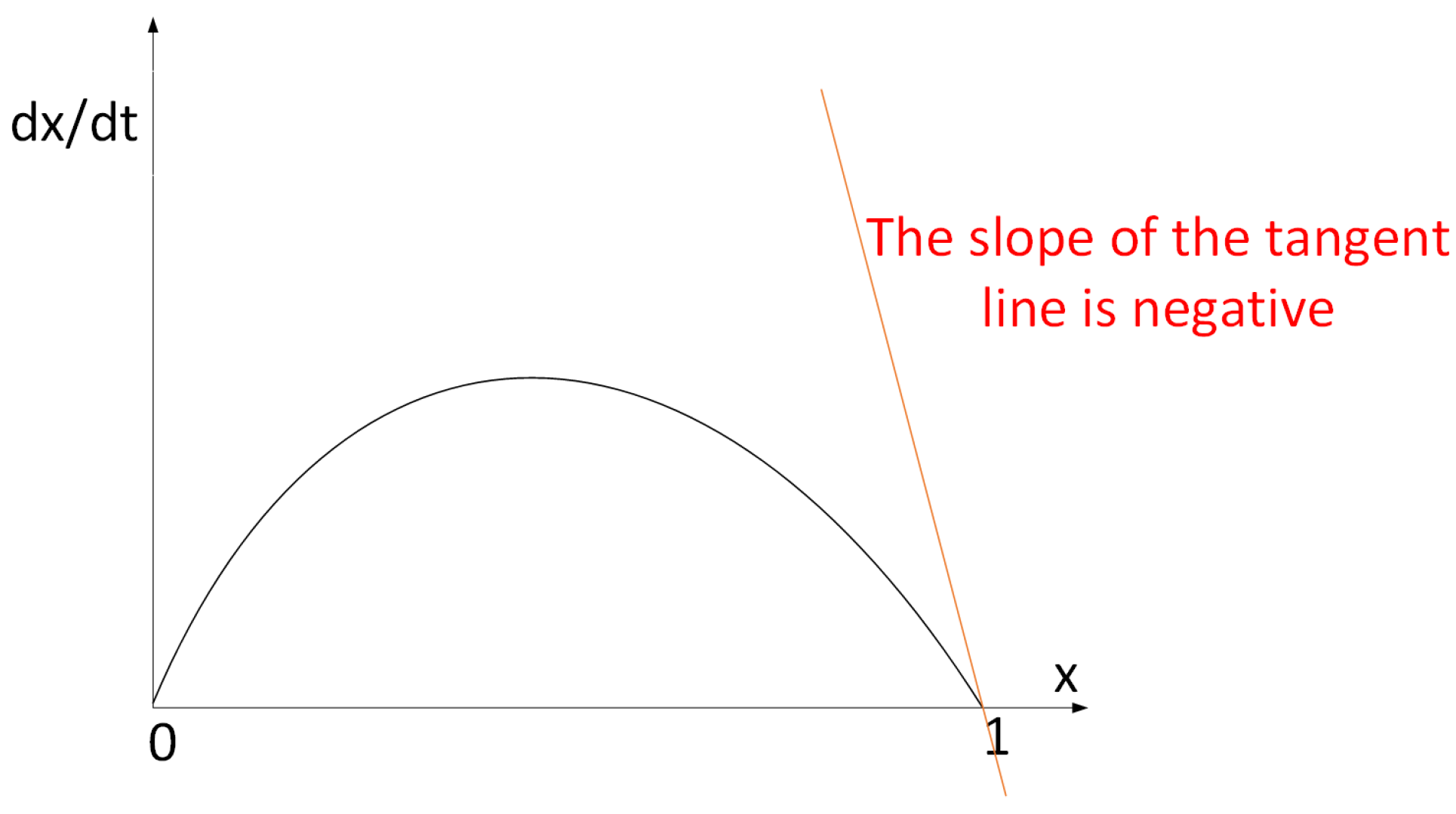
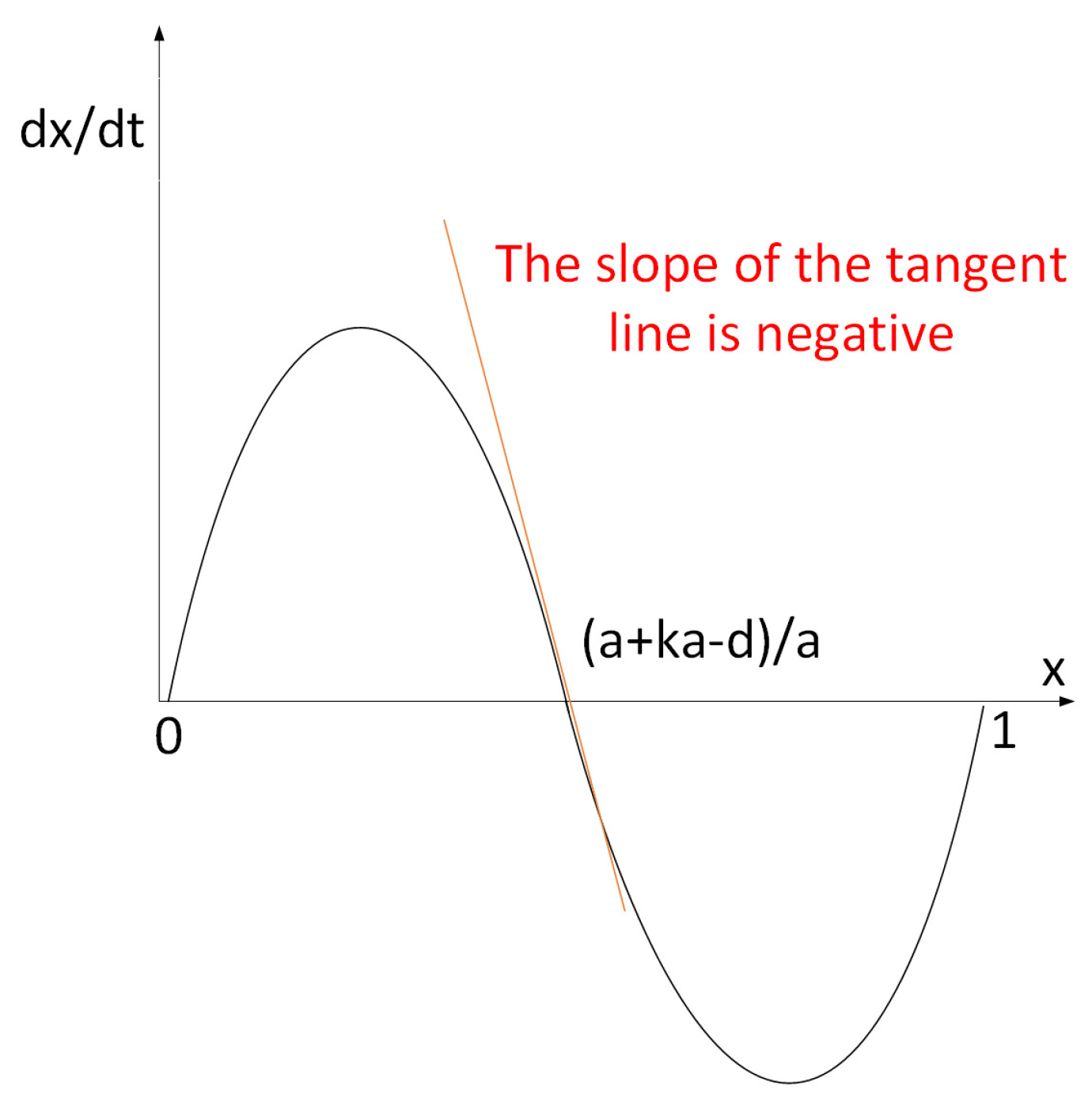
3.3. Steady State Solutions
4. Evaluation Results
4.1. Evolutionary Stability Strategy of Mining Pools
4.2. Experimental Results and Analyses
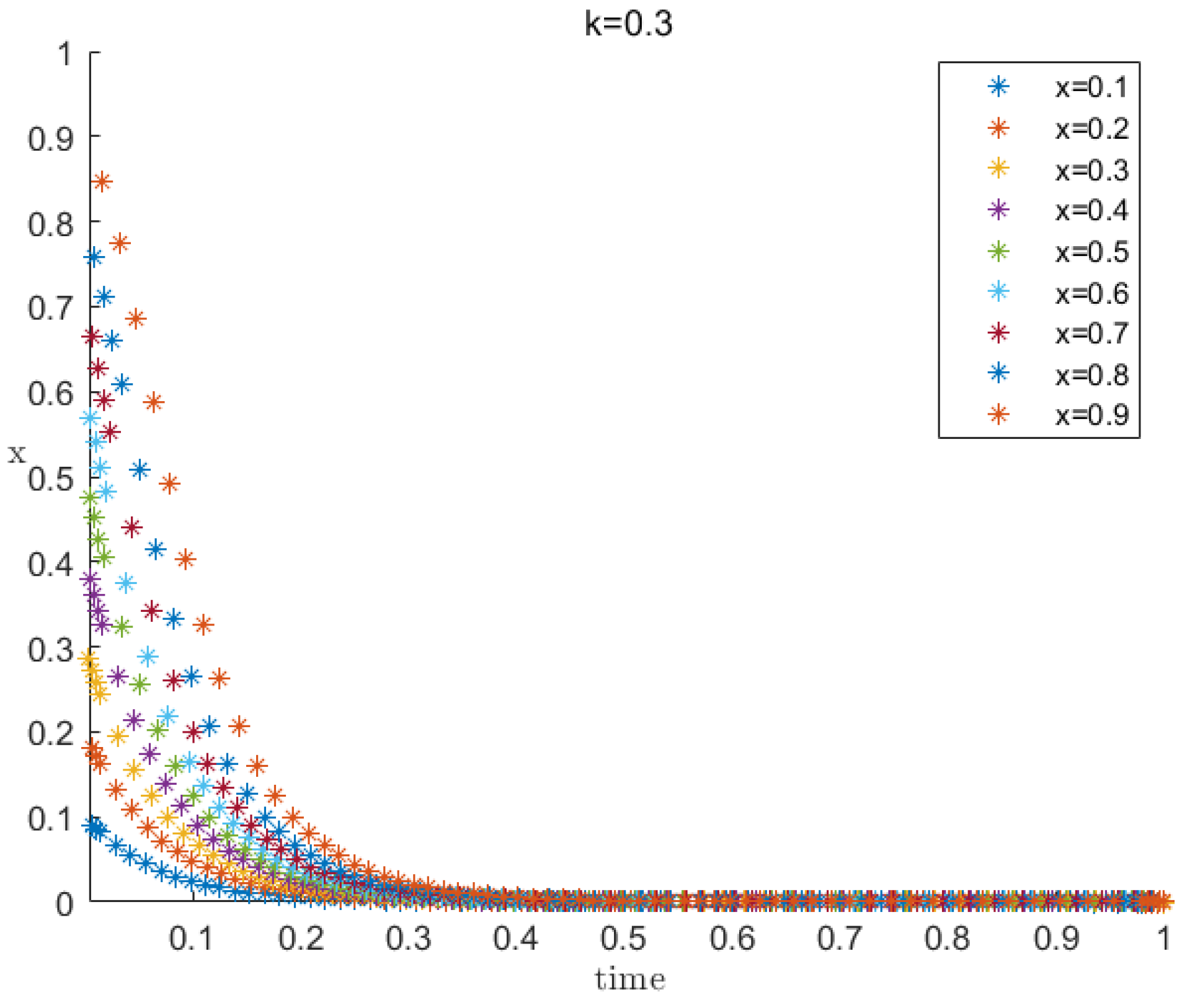
4.2.1. Mining Pool Strategy Selection under Low Penalty and Low Supervision
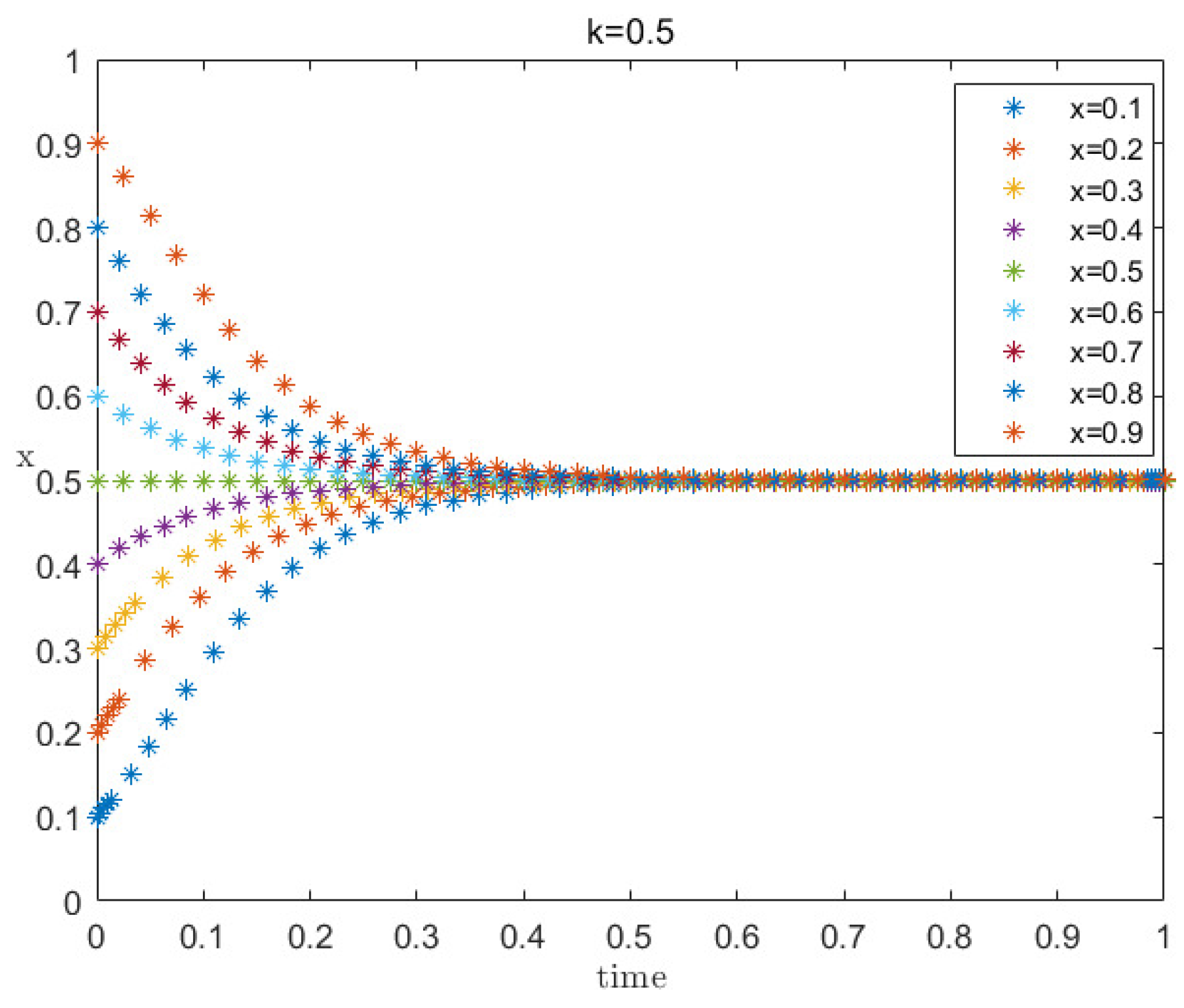
4.2.2. Mining Pool Strategy Selection under Moderate Penalty and Moderate Supervision
4.2.3. Mining Pool Strategy Selection under High Penalty and High Supervision
5. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bao, Q.; Li, B.; Hu, T.; Sun, X. A survey of blockchain consensus safety and security: State-of-the-art, challenges, and future work. J. Syst. Softw. 2023, 196, 111555–111580. [Google Scholar] [CrossRef]
- Bendiab, G.; Hameurlaine, A.; Germanos, G.; Kolokotronis, N.; Shiaeles, S. Autonomous Vehicles Security: Challenges and Solutions Using Blockchain and Artificial Intelligence. IEEE Trans. Intell. Transp. Syst. 2023, 4, 3614–3637. [Google Scholar] [CrossRef]
- Xiao, P.; Salleh, M.I.; Zaidan, B.B.; Xuelan, Y. Research on risk assessment of Blockchain-driven Supply Chain finance: A systematic review. Comput. Ind. Eng. 2023, 176, 108990. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Bit, S.D. A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Lee, T.F.; Lin, K.W.; Hsieh, Y.P.; Lee, K.C. Lightweight Cloud Computing-based RFID Authentication Protocols Using PUF for e-Healthcare Systems. IEEE Sensors J. 2023, 6, 6338–6349. [Google Scholar] [CrossRef]
- binti Malik, M.; Zolkipli, M.F. Blockchain Threats: A Look into the Most Common Forms of Cryptocurrency Attacks. Borneo Int. J. 2023, 1, 20–32. [Google Scholar]
- Nikhalat Jahromi, A.; Saghiri, A.M.; Meybodi, M.R. Nik Defense: An Artificial Intelligence Based Defense Mechanism against Selfish Mining in Bitcoin. arXiv 2023, arXiv:2301.11463. [Google Scholar]
- Al-Jaroodi, J.; Mohamed, N. Blockchain in industries: A survey. IEEE Access 2019, 7, 36500–36515. [Google Scholar] [CrossRef]
- Liu, F.; Li, Z.; Jia, K.; Xiang, P.; Zhou, A.; Qi, J.; Li, Z. Bitcoin Address Clustering Based on Change Address Improvement. IEEE Trans. Comput. Soc. Syst. 2023, 1–12. [Google Scholar] [CrossRef]
- Chen, Z.; Li, B.; Shan, X.; Sun, X.; Zhang, J. Discouraging pool block withholding attacks in Bitcoin. J. Comb. Optim. 2022, 2, 444–459. [Google Scholar] [CrossRef]
- Zhang, Y.; Lv, X.; Chen, Y.; Ren, T.; Yang, C.; Han, M. FAWPA: A FAW Attack Protection Algorithm Based on the Behavior of Blockchain Miners. Sensors 2022, 13, 5032. [Google Scholar] [CrossRef]
- Nikhalat-Jahromi, A.; Saghiri, A.M.; Meybodi, M.R. VDHLA: Variable Depth Hybrid Learning Automaton and Its Application to Defense against the Selfish Mining Attack in Bitcoin. arXiv 2023, arXiv:2302.12096. [Google Scholar]
- Singh, S.; Hosen, A.S.M.S.; Yoon, B. Blockchain Security Attacks, Challenges, and Solutions for the Future Distributed IoT Network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Wenhua, Z.; Qamar, F.; Abdali, T.A.N.; Hassan, R.; Jafri, S.T.A.; Nguyen, Q.N. Blockchain Technology: Security Issues, Healthcare Applications, Challenges and Future Trends. Electronics 2023, 3, 546. [Google Scholar] [CrossRef]
- Chen, Y.; Chen, H.; Zhang, Y.; Han, M.; Siddula, M.; Cai, Z. A survey on blockchain systems: Attacks, defenses, and privacy preservation. High-Confid. Comput. 2022, 2, 1–20. [Google Scholar] [CrossRef]
- Guo, H.; Yu, X. A Survey on Blockchain Technology and its security. Blockchain Res. Appl. 2022, 2, 100067. [Google Scholar] [CrossRef]
- Monrat, A.A.; Schelen, O.; Andersson, K. A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- Krichen, M.; Ammi, M.; Mihoub, A.; Almutiq, M. Blockchain for modern applications: A survey. Sensors 2022, 14, 5274. [Google Scholar] [CrossRef]
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Cao, Y. A survey on blockchain technology: Evolution, architecture and security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Xu, J.; Wang, C.; Jia, X. A Survey of Blockchain Consensus Protocols. ACM Comput. Surv. 2023, 111, 1–34. [Google Scholar] [CrossRef]
- Zhang, B.; Kong, L.; Li, Q.; Min, X.; Liu, Y.; Che, Z. EB-BFT: An elastic batched BFT consensus protocol in blockchain. Future Gener. Comput. Syst. 2023, 139, 267–279. [Google Scholar] [CrossRef]
- Wendl, M.; Doan, M.H.; Sassen, R. The environmental impact of cryptocurrencies using proof of work and proof of stake consensus algorithms: A systematic review. J. Environ. Manag. 2023, 326, 116530. [Google Scholar] [CrossRef] [PubMed]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 4, 352–375. [Google Scholar] [CrossRef]
- Moussa, M.; Beltrame, G. On the robustness of consensus-based behaviors for robot swarms. Swarm Intell. 2020, 14, 205–231. [Google Scholar] [CrossRef]
- Bondugula, R.K.; Udgata, S.K.; Bommi, N.S. A Novel Weighted Consensus Machine Learning Model for COVID-19 Infection Classification Using CT Scan Images. Arab J. Sci. Eng. 2021, 2021, 1–12. [Google Scholar] [CrossRef]
- Kenyeres, M.; Kenyeres, J. Distributed Mechanism for Detecting Average Consensus with Maximum-Degree Weights in Bipartite Regular Graphs. Mathematics 2021, 9, 3020. [Google Scholar] [CrossRef]
- Meneghetti, A.; Sala, M.; Taufer, D. A survey on pow-based consensus. Ann. Emerg. Technol. Comput. (AETiC) 2020, 1, 8–18. [Google Scholar] [CrossRef]
- Li, C.; Spychiger, F.; Tessone, C.J. The Miner’s Dilemma with Migration: The Control Effect of Solo-Mining. IEEE Trans. Netw. Serv. Manag. 2022. [Google Scholar] [CrossRef]
- Praveen, G.; Singh, S.P.; Chamola, V.; Guizani, M. Novel Consensus Algorithm for Blockchain Using Proof-of-Majority (PoM). IEEE Netw. Lett. 2022, 4, 208–211. [Google Scholar] [CrossRef]
- Ding, X.; Guo, J.; Li, D.; Wu, W. An incentive mechanism for building a secure blockchain-based internet of things. IEEE Trans. Netw. Sci. Eng. 2020, 1, 477–487. [Google Scholar] [CrossRef]
- Sun, S.; Wang, W.; Xu, W.; Guo, J. Against Colluding Mining with Reward Sharing in MEC Empowered Mobile Blockchain System. In Proceedings of the 2022-IEEE International Conference on Communications (ICC), Seoul, Republic of Korea, 16–20 May 2022; pp. 4223–4228. [Google Scholar] [CrossRef]
- Islam, M.D.; Shen, H.; Badsha, S. Integrating blockchain into supply chain safeguarded by PUF-enabled RFID. Internet Things 2022, 18, 100505. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, Q. A PUF-based unified identity verification framework for secure IoT hardware via device authentication. World Wide Web 2020, 2, 1057–1088. [Google Scholar] [CrossRef]
- Lee, S.; Kim, S. Countering block withholding attack efficiently. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April 2019; pp. 330–335. [Google Scholar] [CrossRef]
- Bag, S.; Ruj, S.; Sakurai, K. Bitcoin block withholding attack: Analysis and mitigation. IEEE Trans. Inf. Forensics Secur. 2016, 8, 1967–1978. [Google Scholar] [CrossRef]
- Courtois, N.T.; Bahack, L. On subversive miner strategies and block withholding attack in bitcoin digital currency. arXiv 2014, arXiv:1402.1718. [Google Scholar]
- Fujita, K.; Zhang, Y.; Sasabe, M.; Kasahara, S. Mining pool selection under block withholding attack. Appl. Sci. 2021, 4, 1617. [Google Scholar] [CrossRef]
- Fujita, K.; Zhang, Y.; Sasabe, M.; Kasahara, S. Intelligent Mining Pool Selection in the Case of Unobservable Block Withholding Attack. In Proceedings of the 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Virtual Conference, 3–6 May 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Chen, H.; Chen, Y.; Xiong, Z.; Han, M.; He, Z.; Liu, B.; Wang, Z.; Ma, Z. Prevention method of block withholding attack based on miners’ mining behavior in blockchain. Appl. Intell. 2023, 53, 9878–9896. [Google Scholar] [CrossRef]
- Kim, S.; Hahn, S.G. Mining pool manipulation in blockchain network over evolutionary block withholding attack. IEEE Access 2019, 7, 144230–144244. [Google Scholar] [CrossRef]
- Can, B.; Hougaard, J.L.; Pourpouneh, M. On reward sharing in blockchain mining pools. Games Econ. Behav. 2022, 136, 274–298. [Google Scholar] [CrossRef]
- Tuo, J.; Qin, G.; Shang, K.; Wang, Y. The Mining Selection in Multi-pools Under Block WithHolding Attack. In Proceedings of the 2022 41st Chinese Control Conference (CCC), Hefei, China, 25–27 July 2022; pp. 7454–7459. [Google Scholar] [CrossRef]
- Wang, C.; Chu, X.; Qin, Y. Dissecting Mining Pools of Bitcoin Network: Measurement, Analysis and Modeling. IEEE Trans. Netw. Sci. Eng. 2022, 10, 398–412. [Google Scholar] [CrossRef]
- Ren, M.; Guo, H.; Wang, Z. Mitigation of block withholding attack based on zero-determinant strategy. PeerJ Comput. Sci. 2022, 8, e997. [Google Scholar] [CrossRef]
- Li, W.; Cao, M.; Wang, Y.; Tang, C.; Lin, F. Mining pool game model and nash equilibrium analysis for pow-based blockchain networks. IEEE Access 2020, 8, 101049–101060. [Google Scholar] [CrossRef]
- Sigmund, K.; Nowak, M.A. Evolutionary game theory. Curr. Biol. 1999, 9, 503–505. [Google Scholar] [CrossRef] [PubMed]
- Harper, M. Information Geometry and Evolutionary Game Theory. arXiv 2009, arXiv:0911.1383. [Google Scholar]


| Parameters | Description and Function of Parameters |
|---|---|
| R | Mining pool revenue from honest mining. |
| d | The illegal revenue gained by the attacker or the revenue lost by the attacked mining pool. |
| a | The blockchain system gives rewards to honest mining pools and punishments to attacking mining pools. |
| k | The supervision coefficient of blockchain system on launching BWH attack mining pool. |
| The average return of honest mining by a mining pool. | |
| Average return of a mining pool launching a BWH attack. | |
| Average return of a mining pool. | |
| The dynamic equation of replication for x and time t. | |
| The first derivative of with respect to the probability x of honest mining. | |
| x | The probability that the pool mines honestly. |
| The different steady states computed by the replicated dynamic equation. | |
| Deterministic mining strategies under different degrees of punishment and supervision. |
| Pool B | H | BW | |
|---|---|---|---|
| Pool A | |||
| H | (R, R) | (R − d + a, R + d − ka) | |
| BW | (R + d − ka, R − d + a) | (R − ka, R − ka) | |
| Degree of Punishment a | Blockchain System Supervision Coefficient k | Evolutionary Steady-State Strategy | Analysis |
|---|---|---|---|
| Low degree of punishment and frequency of supervision | |||
| High degree of punishment and frequency of supervision | |||
| Moderate degree of punishment and frequency of supervision |
| Mining Pool Honest Mining Profit R | Illegal Profits of Mining Pools Launching BWH Attacks d | Degree of Punishment a | Supervision Coefficient k | Evolutionary Steady-State Strategy | Analysis |
|---|---|---|---|---|---|
| The solution obtained in experiment a corresponds to case A in Section 3.3 | |||||
| The solution obtained in experiment b corresponds to case E in Section 3.3 | |||||
| The solution obtained in experiment c corresponds to case C in Section 3.3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, X.; Huang, Z.; Wang, Q.; Wan, B. An Evolutionary Game Theory-Based Method to Mitigate Block Withholding Attack in Blockchain System. Electronics 2023, 12, 2808. https://doi.org/10.3390/electronics12132808
Liu X, Huang Z, Wang Q, Wan B. An Evolutionary Game Theory-Based Method to Mitigate Block Withholding Attack in Blockchain System. Electronics. 2023; 12(13):2808. https://doi.org/10.3390/electronics12132808
Chicago/Turabian StyleLiu, Xiao, Zhao Huang, Quan Wang, and Bo Wan. 2023. "An Evolutionary Game Theory-Based Method to Mitigate Block Withholding Attack in Blockchain System" Electronics 12, no. 13: 2808. https://doi.org/10.3390/electronics12132808
APA StyleLiu, X., Huang, Z., Wang, Q., & Wan, B. (2023). An Evolutionary Game Theory-Based Method to Mitigate Block Withholding Attack in Blockchain System. Electronics, 12(13), 2808. https://doi.org/10.3390/electronics12132808







