Zero-Trust Security Authentication Based on SPA and Endogenous Security Architecture
Abstract
:1. Introduction
- (1)
- For the policy engine construction method under zero-trust authentication architecture, we used heterogeneous components to realize the policy engine construction through operating systems, web servers, databases, etc., which can avoid the hazard of common vulnerabilities of system components.
- (2)
- We proposed a novel authentication system, the MAS, which is based on SPA and endogenous security architecture, to achieve a secure construction of the authentication system. The evaluation results showed that the MAS can effectively avoid DDOS attacks and malicious attacks based on unknown vulnerabilities.
- (3)
- We experimentally verified the feasibility of the MAS, mathematically reasoned about the system security and provable security through attack resistance analysis and demonstrated, through attack resistance testing, that the system can achieve the goal of a security authentication system without taking up too many resources and bandwidth.
2. Related Work
3. MTD Defense Method Compared with MAS
- A lack of awareness of malicious scanning strategies by the hopping mechanism leads to blindness in the selection of hopping defense strategies;
- The poor effectiveness of hopping defense due to limited hopping space and a fixed hopping period;
- The poor availability and scalability of network hopping defense due to a lack of constraints on hopping implementation and high deployment complexity.
4. Threat Models and Attack Scenarios
5. Mimic Authentication Strategy System
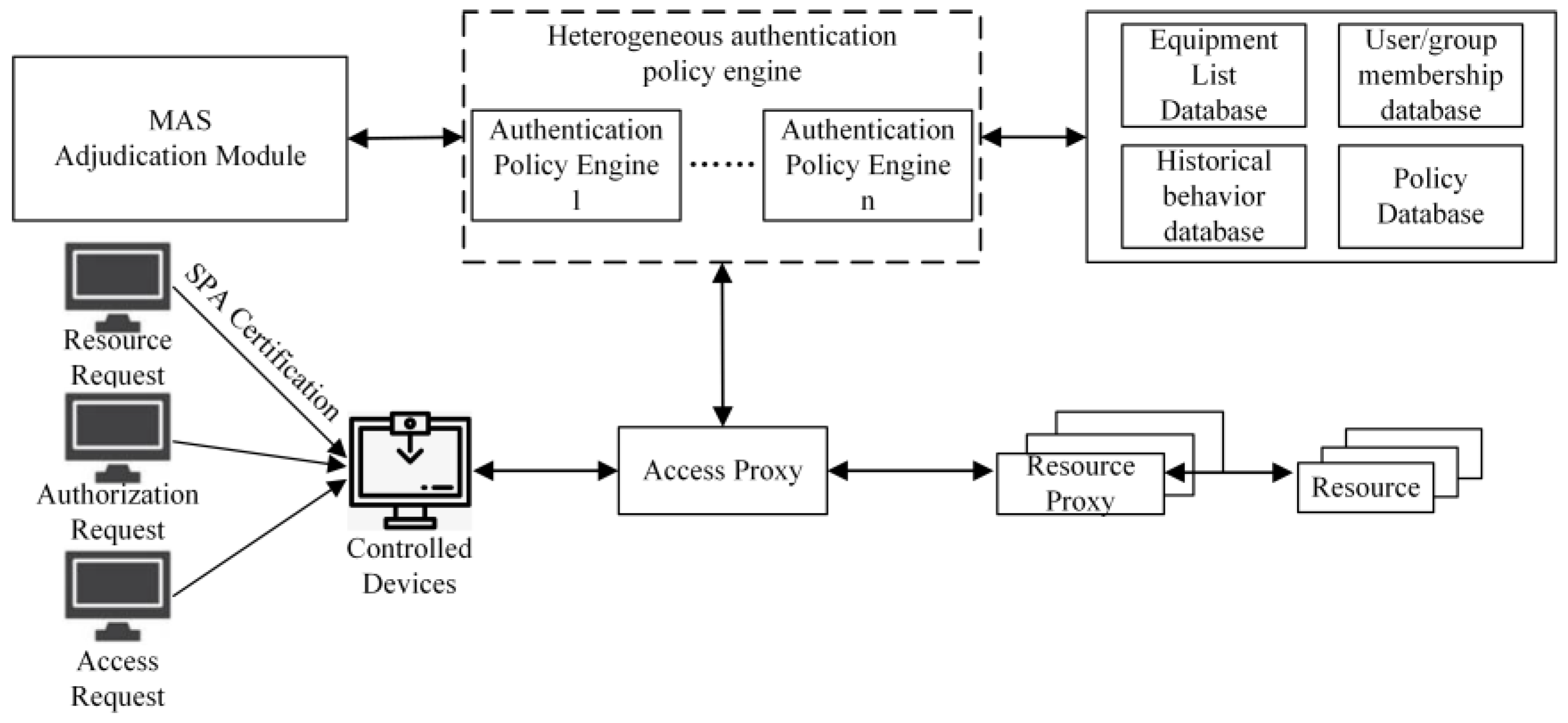
5.1. System Architecture Design
- Different authentication methods;
- A heterogeneous operating environment;
- Different databases;
- Different scoring weights for policy development;
- The difference in the syntax of the establishment policy engine.
- Different scoring weighting mechanisms for the same type of request authorization behavior;
- Different scoring weighting mechanisms for different types of request authorization behaviors;
- Different syntax for building policy engines.
5.2. Certification Process Analysis
6. Experiment Analysis
6.1. Attacker–Defender Game Analysis
6.2. Safety Gain Analysis
6.3. Experiment Environment
- FWKNOP, as an open-source and mature tool for single-packet authorization and port probe, is used to hide system services. By encrypting a single data packet, replay attacks are avoided and the authentication credentials are hash encoded (MD5, SHA-256, SHA-512, etc.), so to authenticate via HMAC, the workload needs to do less than a single-decrypt SPA packet. At the same time, the server side of FWKNOP acts as a front-end proxy under the whole system, blocking all service traffic that has not been authorized by a single package, preventing the system from being damaged by DDOS attacks;
- As a free, open-source, high-performance HTTP server and reverse proxy server, Nginx can realize the function of service request forwarding and the load balancing effect by setting the Nginx configuration file. Compared with the forward proxy, the deployment location of the reverse proxy server is closer to the source server, which makes it easier to control and centralize permissions;
- Docker, as an open-source application container engine, adopts the sandbox mechanism, and each container is independent of each other without any interface. The performance overhead of containers is extremely low and it is simple and easy to use compared to VMware or VirtualBox. The image shared by the Docker community is very easy to use to deploy containers, and it can be built locally, deployed to the cloud at any time and can be run anywhere. At the same time, it is very convenient to manage Docker containers using container cluster management tools such as Kubernetes, Docker Swarm and OpenShift.
6.4. Experiment Procedure
6.4.1. System Information
6.4.2. SPA (Single Package Authorization)
6.4.3. Request Processing and Distribution
6.4.4. Information Judgment
| Algorithm 1. Consensus voting. |
| Consensus—Voting |
| Input: client request parameters ClientRequest and authentication key ClientSecret |
| begin |
| If get client requests |
| // First authenticate the user’s identity and perform security checks |
| Processed_Auth=Id_Authentication(ClientSecret) |
| // Determining user identity |
| If(Processed_Auth) |
| // Handling user request parameters |
| Processed_Request=Request_exec(ClientRequest) |
| // Send processed user requests to heterogeneous policy engines PE1, PE2, PE3 |
| Response1=Send_to_PE1(Processed_Request) |
| Response2=Send_to_PE2(Processed_Request) |
| Response3=Send_to_PE3(Processed_Request) |
| // Voting on messages using a consistent voting machine |
| Response_to_Client=Consensus-Voting(Response1,Response2,Response3) |
| // Return the processing results to the controlled device |
| Send_to_CD(Response_to_Client) |
| end if |
| end if |
| end |
6.5. Experiment Analysis
- (1)
- System failure rate
- (2)
- Vulnerability Utilization
- (3)
- Attack–defense time cost
- (4)
- Effect of the number of isomers
- By introducing the SPA single-packet authorization mechanism, it ensures that the system can operate safely under DDOS attacks and the system resources are utilized stably.
- Compared with the single authentication center (policy engine) authentication system, the multipolicy engine construction method can ensure stable operation and a lower system failure rate after the attacker increases the intensity of the attack on the system.
- With the introduction of the multipolicy engine approach in the system, the defense capability of the system and the attacker’s attack overhead tend to grow nonlinearly as the number of heterogeneous bodies increases, which can improve the security defense capability of the system.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Gilman, E. Zero Trust Networks: Building Systems in Untrusted Networks. In USENIX Security; O’Reilly Media: Newton, MA, USA, 2016. [Google Scholar]
- Norquist, D.L. DoD Digital Modernization Strategy: DoD Information Resources Management Strategic Plan FY19-23. 12 July 2019. Available online: https://apps.dtic.mil/sti/pdfs/AD1077734.pdf (accessed on 2 January 2023).
- Rose, S.; Borchert, O.; Mitchell, S. NIST Special Publication 800–207 Zero Trust Architecture; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020.
- Gartner. Building Trust with Zero Trust—Reinventing the New Boundary of Security. 2021. Available online: https://www.tisi.org/18597 (accessed on 2 January 2023).
- Peng, W.; Li, F.; Huang, C.T. A moving-target defense strategy for cloud-based services with heterogeneous and dynamic attack surfaces. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014. [Google Scholar]
- Hu, H.; Wu, J.; Wang, Z. Mimic defense: A designed-in cybersecurity defense framework. IET Inf. Secur. 2018, 12, 226–237. [Google Scholar] [CrossRef]
- De Capitani di Vimercati, S.; Paraboschi, S.; Samarati, P. Access control: Principles and solutions. Softw. Pract. Exp. 2003, 33, 397–421. [Google Scholar] [CrossRef]
- Braghin, C.; Cortesi, A.; Focardi, R. Security boundaries in mobile ambients. Comput. Lang. Syst. Struct. 2002, 28, 101–127. [Google Scholar] [CrossRef]
- Farrell, S. Security boundaries. IEEE Internet Comput. 2008, 12, 93–96. [Google Scholar] [CrossRef]
- Ahmed, I.; Nahar, T.; Urmi, S.S. Protection of sensitive data in zero trust model. In Proceedings of the ICCA 2020: International Conference on Computing Advancements, Dhaka, Bangladesh, 10–12 January 2020. [Google Scholar]
- Papakonstantinou, N.; Van Bossuyt, D.L.; Linnosmaa, J. A Zero Trust Hybrid Security and Safety Risk Analysis Method. J. Comput. Inf. Sci. Eng. 2021, 21, 050907. [Google Scholar] [CrossRef]
- DeCusatis, C.; Liengtiraphan, P.; Sager, A. Implementing zero trust cloud networks with transport access control and first packet authentication. In Proceedings of the 2016 IEEE International Conference on Smart Cloud (SmartCloud), New York, NY, USA, 18–20 November 2016. [Google Scholar]
- Sateesh, H.; Zavarsky, P. State-of-the-Art VANET trust models: Challenges and recommendations. In Proceedings of the 2020 11th IEEE Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 4–7 November 2020. [Google Scholar]
- Samaniego, M.; Deters, R. Zero-trust hierarchical management in IoT. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018. [Google Scholar]
- Dhar, S.; Bose, I. Securing IoT devices using zero trust and blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Zhang, X.J. Power IoT security protection architecture based on zero trust framework. In Proceedings of the 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP), Zhuhai, China, 8–10 January 2021. [Google Scholar]
- Puthal, D.; Yang, L.T.; Dustdar, S. A user-centric security solution for Internet of Things and edge convergence. ACM Trans. Cyber-Phys. Syst. 2020, 4, 32. [Google Scholar] [CrossRef]
- Sultana, M.; Hossain, A.; Laila, F. Towards developing a secure medical image sharing system based on zero trust principles and blockchain technology. BMC Med. Inform. Decis. Mak. 2020, 20, 256. [Google Scholar] [CrossRef] [PubMed]
- Zaheer, Z.; Chang, H.; Mukherjee, S. eztrust: Network-independent zero-trust perimeterization for microservices. In Proceedings of the SOSR ‘19: Symposium on SDN Research, San Jose, CA, USA, 3–4 April 2019. [Google Scholar]
- Chen, X.; Feng, W.; Ge, N. Zero Trust Architecture for 6G Security. arXiv 2022, arXiv:2203.07716. [Google Scholar]
- Han, C.; Kim, G.J.; Alfarraj, O. ZT-BDS: A Secure Blockchain-based Zero-trust Data Storage Scheme in 6G Edge IoT. J. Internet Technol. 2022, 23, 289–295. [Google Scholar]
- Almaiah, M.A.; Al-Zahrani, A.; Almomani, O.; Alhwaitat, A.K. Classification of cyber security threats on mobile devices and applications. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer International Publishing: Cham, Switzerland, 2021; pp. 107–123. [Google Scholar]
- Al Hwaitat, A.K.; Almaiah, M.A.; Almomani, O.; Al-Zahrani, M.; Al-Sayed, R.M.; Asaifi, R.M.; Adhim, K.K.; Althunibat, A.; Alsaaidah, A. Improved security particle swarm optimization (PSO) algorithm to detect radio jamming attacks in mobile networks. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 614–625. [Google Scholar] [CrossRef]
- Almaiah, M.A. Almaiah, M.A. A new scheme for detecting malicious attacks in wireless sensor networks based on blockchain technology. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer International Publishing: Cham, Switzerland, 2021; pp. 217–234. [Google Scholar]
- Almaiah, M.A.; Dawahdeh, Z.; Almomani, O.; Alsaaidah, A.; Al-Khasawneh, A.; Khawatreh, S. A new hybrid text encryption approach over mobile ad hoc network. Int. J. Electr. Comput. Eng. (IJECE) 2020, 10, 6461–6471. [Google Scholar] [CrossRef]
- Al Nafea, R.; Almaiah, M.A. Cyber security threats in cloud: Literature review. In Proceedings of the 2021 International Conference on Information Technology (ICIT), IEEE, Amman, Jordan, 14–15 July 2021; pp. 779–786. [Google Scholar]
- Alamer, M.; Almaiah, M.A. Cybersecurity in Smart City: A systematic mapping study. In Proceedings of the 2021 International Conference on Information Technology (ICIT), IEEE, Amman, Jordan, 14–15 July 2021; pp. 719–724. [Google Scholar]
- Moubayed, A.; Refaey, A.; Shami, A. Software-defined perimeter (sdp): State of the art secure solution for modern networks. IEEE Netw. 2019, 33, 226–233. [Google Scholar] [CrossRef]
- Sallam, A.; Refaey, A.; Shami, A. On the security of SDN: A completed secure and scalable framework using the software-defined perimeter. IEEE Access 2019, 7, 146577–146587. [Google Scholar] [CrossRef]
- Omar, R.R.; Abdelaziz, T.M. A comparative study of network access control and software-defined perimeter. In Proceedings of the ICEMIS’20: The 6th International Conference on Engineering & MIS 2020, Almaty, Kazakhstan, 14–16 September 2020. [Google Scholar]
- Singh, J.; Refaey, A.; Koilpillai, J. Adoption of the software-defined perimeter (sdp) architecture for infrastructure as a service. Can. J. Electr. Comput. Eng. 2020, 43, 357–363. [Google Scholar] [CrossRef]
- Bello, Y.; Hussein, A.R.; Ulema, M.; Koilpillai, J. On Sustained Zero Trust Conceptualization Security for Mobile Core Networks in 5G and Beyond. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1876–1889. [Google Scholar] [CrossRef]
- Albuali, A.; Mengistu, T.; Che, D. ZTIMM: A zero-trust-based identity management model for volunteer cloud computing. In Proceedings of the CLOUD 2020, Honolulu, HI, USA, 18–20 September 2020. [Google Scholar]
- Yao, Q.; Wang, Q.; Zhang, X. Dynamic access control and authorization system based on zero-trust architecture. In Proceedings of the CCRIS ‘20: Proceedings of the 2020 1st International Conference on Control, Robotics and Intelligent System, Xiamen China, 27–29 October 2020. [Google Scholar]
- Laplante, P.; Voas, J. Zero-Trust Artificial Intelligence? Computer 2022, 55, 10–12. [Google Scholar] [CrossRef]
- Ferretti, L.; Magnanini, F.; Andreolini, M. Survivable zero trust for cloud computing environments. Comput. Secur. 2021, 110, 102419. [Google Scholar] [CrossRef]
- Guo, J.; Xu, M. ZTESA—A Zero-Trust Endogenous Safety Architecture: Gain the endogenous safety benefit, avoid insider threats. In Proceedings of the International Symposium on Computer Applications and Information Systems (ISCAIS 2022), SPIE, Shenzhen, China, 25–27 February 2022; Volume 12250, pp. 192–202. [Google Scholar]
- Rash, M. Single packet authorization with fwknop. USENIX Mag. 2006, 31, 63–69. [Google Scholar]

















| Factor | Behavioral Elements | Score | Security Level |
|---|---|---|---|
| Policy | Login and query times | 60 | Medium |
| Access to sensitive servers | 85 | High | |
| Number of guesses for username/password | 80 | Medium high | |
| Modify file permissions | 85 | High | |
| Number of port scans | 80 | Medium high | |
| Number of leapfrog operations | 95 | Very high | |
| Number of threads created | 60 | Medium | |
| Change system settings | 90 | Very high | |
| Continuous authentication failures | 85 | High | |
| Language | Writing Language | Compiler | Efficiency Score |
| C/C++ | GCC | 85 | |
| Java | Eclipse | 80 | |
| Python | PyCharm | 75 |
| No. | Server Name | IP | Software Stack Composition | Image/Container |
|---|---|---|---|---|
| 1 | Controlled Device | 192.168.73.134 | Centos 7 + Apache + Redis + PHP | CD_Centos |
| 2 | Access Proxy | 192.168.73.7 | Ubuntu + Nginx + MySQL + C++ | AP_Ubuntu |
| 3 | Policy Engine 1 | 192.168.73.25 | Debian + Apache + Oracle + JAVA | PE_Debian_Docker1 |
| 4 | Policy Engine 2 | 192.168.73.26 | Fedora + Lighttpd + MariaCB + Python | PE_Fedora_Docker2 |
| 5 | Policy Engine 3 | 192.168.73.27 | RedHat + Tomcat + Sqlite + C++ | PE_RedHat_Docker3 |
| 6 | Adjudicator | 192.168.73.202 | Windows + IIS + SQL server + NET | Adjudicator_Windows |
| Message Name | Parameter Value |
|---|---|
| Local Username | chris |
| Local Timestamp | 202204121724 |
| Client IP | 192.168.73.135 |
| Verify Password | ZzuP@ss_Word |
| Hash-Encoded Value (MD5) | (“chris: 202204121724:192.168.73.135:ZzuP@ss_Word”) = e30316234dd806f64026fa52dc67d627 |
| Upstream Server | IP | PORT |
|---|---|---|
| PE_Debian_Docker1 | 192.168.73.25 | 8080 |
| PE_Fedora_Docker2 | 192.168.73.26 | 8080 |
| PE_RedHat_Docker3 | 192.168.73.27 | 8080 |
| No. | Server Name | IP | Port | Result |
|---|---|---|---|---|
| 1 | PE_Debian_Docker1 | 192.168.73.25 | 8080 | Authorization verification passed |
| 2 | PE_Fedora_Docker2 | 192.168.73.26 | 8080 | Authorization verification passed |
| 3 | PE_RedHat_Docker3 | 192.168.73.27 | 8080 | Authorization verification passed |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, M.; Guo, J.; Yuan, H.; Yang, X. Zero-Trust Security Authentication Based on SPA and Endogenous Security Architecture. Electronics 2023, 12, 782. https://doi.org/10.3390/electronics12040782
Xu M, Guo J, Yuan H, Yang X. Zero-Trust Security Authentication Based on SPA and Endogenous Security Architecture. Electronics. 2023; 12(4):782. https://doi.org/10.3390/electronics12040782
Chicago/Turabian StyleXu, Mingyang, Junli Guo, Haoyu Yuan, and Xinyu Yang. 2023. "Zero-Trust Security Authentication Based on SPA and Endogenous Security Architecture" Electronics 12, no. 4: 782. https://doi.org/10.3390/electronics12040782





