The Concept regarding Vehicular Communications Based on Visible Light Communication and the IoT
Abstract
1. Introduction
2. Methodology and Design Parameters
2.1. Li-Fi Communication System Proposal
2.2. Proposal for Software Infrastructure and Architectural Components
- (a)
- The header is initialized and a cryptographic key is generated for each ID (i.e., for each device on the network or each device that should connect to it);
- (b)
- The AES algorithm is used to encrypt the data and transmit them via the Li-Fi network;
- (c)
- The unique cryptographic keys are then sent to the connected devices to enable the decryption of the received data. Their form being that of the MD5 hash function, the unique identifier generated for each vehicle in the network can be inserted into their headers;
- (d)
- The keys are used to decrypt the data when they are received by the connected device.
| Algorithm 1: Pseudocode for the encryption process for data at the physical level of the network. |
| from vlc_supp import SEC1_SUPP vlc = SEC1_SUPP(lifi0) vlc.set_network(‘usr’, ‘pass’, Li-Fi1#!2) vlc.enable_network() |
| Algorithm 2: Pseudocode for the import and filtering of access data for the generated address. |
| from ipvlctables import Iptablesvlc ipt = Ipvlctables() ipt.block_all_trafficvlc() ipt.allow_traffic(100.100.1.0/88) |
| Algorithm 3: Pseudocode for final validation and authentication in the created communication process. |
| from passlibvlc.hash import sha256_crypt usr = input(“Enter user: “) pass = input(“Enter pass: “) stored_passvlc = “hashed_pass_from_databasevlc” if shabvlc_crypt.verify(pass, stored_pass): print(“Access granted LiFI.”) else: print(“Access denied to Li-Fi.”) |
3. Implementation and Results
Analysis of the Security Process and the Threats to Which the Network Is Exposed
4. Discussion
5. Conclusions
Funding
Acknowledgments
Conflicts of Interest
References
- Chowdhury, M.Z.; Hossan, M.T.; Islam, A.; Jang, Y.M. A Comparative Survey of Optical Wireless Technologies: Architectures and Applications. IEEE Access 2018, 6, 9819–9840. [Google Scholar] [CrossRef]
- Matheus, L.E.M.; Vieira, A.B.; Vieira, L.F.M.; Vieira, M.A.M.; Gnawali, O. Visible Light Communication: Concepts, Applications and Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3204–3237. [Google Scholar] [CrossRef]
- WHO. Global Status Report on Road Safety 2021 (World Health Organization, 2021), 138. 2021. Available online: https://www.who.int/violence_injury_prevention/road_safety_status/2021/en/ (accessed on 12 January 2023).
- Amani, A.S.; Hesham, A.E.Z.; Sadek, A.A.-S. Secure and intelligent road trafc management system based on rfd technology. In Proceedings of the World Symposium on Computer Applications and Reserch (WSCAR), Cairo, Egypt, 12–14 March 2016; pp. 41–46. [Google Scholar]
- Jungnickel, V.; Uysal, M.; Serafimovski, N.; Baykas, T.; O’Brien, D.; Ciaramella, E.; Ghassemlooy, Z.; Green, R.; Haas, H.; Haigh, P.A.; et al. A European view on the next generation optical wireless communication standard. In Proceedings of the 2015 IEEE Conference on Standards for Communications and Networking (CSCN), Tokyo, Japan, 28–30 October 2015; pp. 106–111. [Google Scholar]
- Ifada, E.; Surajudeen-Bakinde, N.T.; Faruk, N.; Abubakar, A.; Mohammed, O.O.; Otuoze, A.O. Implementation of a data transmission system using Li-Fi technology. In Proceedings of the 2nd International Conference of the IEEE Nigeria Computer Chapter (NigeriaComputConf), Zaria, Nigeria, 14–17 October 2019; pp. 1–7. [Google Scholar]
- IEEE Std 802.15.7-2018 (Revision of IEEE Std 802.15.7-2011); IEEE Standard for Local and Metropolitan Area Networks-Part 15.7: Short-Range Optical Wireless Communications. IEEE: Piscataway, NJ, USA, 2019; pp. 1–407.
- Shi, D.; Zhang, X.; Shi, L.; Vladimirescu, A.; Mazurczyk, W.; Cabaj, K.; Meunier, B.; Ali, K.; Cosmas, J.; Zhang, Y. On Improving 5G Internet of Radio Light Security Based on LED Fingerprint Identification Method. Sensors 2021, 21, 1515. [Google Scholar] [CrossRef]
- Maia, G.; Aquino, A.L.L.; Viana, A.C.; Boukerche, A.; Loureiro, A.A.F. HyDi: A hybrid data dissemination protocol for highway scenariosin vehicular ad hoc networks. In Proceedings of the second ACMinternational Symposium on Design and Analysis of Intelligentvehicular Networks and Applications, Paphos, Cyprus, 21–25 October 2012; pp. 15–122. [Google Scholar]
- Alraih, S.; Shayea, I.; Behjati, M.; Nordin, R.; Abdullah, N.F.; Abu-Samah, A.; Nandi, D. Revolution or Evolution? Technical Requirements and Considerations towards 6G Mobile Communications. Sensors 2022, 22, 762. [Google Scholar] [CrossRef]
- Desai, V. Design and implementation of GSM and GPS based vehicle accident detection system. Int. J. Technol. Sci. 2014, 1, 306–3014. [Google Scholar]
- Abdelhady, A.M.; Amin, O.; Chaaban, A.; Shihada, B.; Alouini, M. Spectral-Efficiency—Illumination Pareto Front for Energy Harvesting Enabled VLC Systems. IEEE Trans. Commun. 2019, 67, 8557–8572. [Google Scholar] [CrossRef]
- Abdillah, M.I.; Darlis, D. Distance measurement implementation for VLC-based V2V communication on motorbike platooning. In Proceedings of the International Conference of Engineering Technology Entrepreneurship, Bandung, India, 13–15 August 2019. [Google Scholar]
- Căilean, A.-M.; Dimian, M.; Popa, V. Noise-Adaptive Visible Light Communications Receiver for Automotive Applications: A Step Toward Self-Awareness. Sensors 2020, 20, 3764. [Google Scholar] [CrossRef]
- Delgado-Rajo, F.; Melian-Segura, A.; Guerra, V.; Perez-Jimenez, R.; Sanchez-Rodriguez, D. Hybrid RF/VLC Network Architecture for the Internet of Things. Sensors 2020, 20, 478. [Google Scholar] [CrossRef]
- Alin-Mihai, C.; Barthélemy, C.; Luc, C.; Suat, T.; Yasser, A.; JeanMarc, B. Visible light communications: Application to cooperation between vehicles and road infrastructures. In Proceedings of the IEEE Intelligent Vehicles International Symposium, Alcalá de Henares, Spain, 3–7 June 2012. [Google Scholar]
- Marabissi, D.; Mucchi, L.; Caputo, S.; Nizzi, F.; Pecorella, T.; Fantacci, R.; Nawaz, T.; Seminara, M.; Catani, J. Experimental Measurements of a Joint 5G-VLC Communication for Future Vehicular Networks. J. Sens. Actuator Netw. 2020, 9, 32. [Google Scholar] [CrossRef]
- de Oliveira, M.A.; Lima, E.S.; Cunha, M.S.P.; Abreu, M.; Arismar Cerqueira, S. RGB-based VLC system using 5G NR standard. Opt. Commun. 2021, 481. [Google Scholar] [CrossRef]
- Hammouda, M.; Akın, S.; Vegni, A.M.; Haas, H.; Peissig, J. Link Selection in Hybrid RF/VLC Systems Under Statistical Queueing Constraints. IEEE Trans. Wirel. Commun. 2018, 17, 2738–2754. [Google Scholar] [CrossRef]
- Khalifeh, A.F.; AlFasfous, N.; Theodory, R.; Giha, S.; Darabkh, K.A. An experimental evaluation and prototyping for visible light communication. Comput. Electr. Eng. 2018, 72, 248–265. [Google Scholar] [CrossRef]
- Cevik, T.; Yilmaz, S. An overview of visible light communication systems. arXiv 2015, arXiv:1512.03568. [Google Scholar] [CrossRef]
- Chen, Q.; Wen, H.; He, J.; Deng, R.; Chen, M.; Zhou, Z.; Ma, J.; Zong, T. Performance enhancement of OFDM-VLC system using joint preprocessing scheme. Opt. Commun. 2019, 451, 111–115. [Google Scholar] [CrossRef]
- Chen, C.-W.; Wang, W.-C.; Wu, J.-T.; Chen, H.-Y.; Liang, K.; Wei, L.-Y.; Hsu, Y.; Hsu, C.-W.; Chow, C.-W.; Yeh, C.-H.; et al. Visible light communications for the implementation of internet-of-things. Opt. Eng. 2016, 55, 060501. [Google Scholar] [CrossRef]
- Mohsin, M.J.; Murdas, I.A. Performance analysis of an outdoor Li-Fi system-based AO-OFDM architecture under different FSO turbulence and weather conditions. Optik 2023, 273, 170427. [Google Scholar] [CrossRef]
- Abdallah, W.; Boudriga, N. Enabling 5G wireless access using Li-Fi technology: An OFDM based approach. In Proceedings of the 2016 18th International Conference on Transparent Optical Networks (ICTON), Trento, Italy, 10–14 July 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Durgun, M.; Gokrem, L. VLC4WoT: Visible Light Communication for Web of Things. KSII Trans. Internet Inf. Syst. (TIIS) 2020, 14, 1502–1519. [Google Scholar] [CrossRef]
- Yu, T.-C.; Huang, W.-T.; Lee, W.-B.; Chow, C.-W.; Chang, S.-W.; Kuo, H.-C. Visible Light Communication System Technology Review: Devices, Architectures, and Applications. Crystals 2021, 11, 1098. [Google Scholar] [CrossRef]
- Khan, L.U. Visible light communication: Applications, architecture, standardization and research challenges. Digit. Commun. Netw. 2017, 3, 78–88. [Google Scholar] [CrossRef]
- Hoffmann, M.; Kryszkiewicz, P.; Kliks, A. Frequency Selection for Platoon Communications in Secondary Spectrum Using Radio Environment Maps. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2637–2650. [Google Scholar] [CrossRef]
- Renzler, T.; Stolz, M.; Watzenig, D. Feudalistic Platooning: Subdivide Platoons, Unite Networks, and Conquer Efficiency and Reliability. Sensors 2022, 22, 4484. [Google Scholar] [CrossRef]
- Căilean, A.-M.; Beguni, C.; Avătămăniței, S.-A.; Dimian, M.; Popa, V. Design, Implementation and Experimental Investigation of a Pedestrian Street Crossing Assistance System Based on Visible Light Communications. Sensors 2022, 22, 5481. [Google Scholar] [CrossRef]
- Căilean, A.-M.; Avătămăniţei, S.-A.; Beguni, C.; Popa, V.; Dimian, M. Experimental Demonstration of a 188 meters Infrastructure-to-Vehicle Visible Light Communications Link in Outdoor Conditions. In Proceedings of the 2021 IEEE Sensors Applications Symposium (SAS), Sundsvall, Sweden, 23–25 August 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Beguni, C.; Căilean, A.-M.; Avătămăniței, S.-A.; Zadobrischi, E.; Stoler, R.; Dimian, M.; Popa, V.; Béchadergue, B.; Chassagne, L. In-Vehicle Visible Light Communications Data Transmission System Using Optical Fiber Distributed Light: Implementation and Experimental Evaluation. Sensors 2022, 22, 6738. [Google Scholar] [CrossRef] [PubMed]
- Kadam, K.; Dhage, M.R. Visible Light Communication for IoT. In Proceedings of the 2016 2nd International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT), Bangalore, India, 21–23 July 2016; pp. 275–278. [Google Scholar] [CrossRef]
- Ismail, S.N.; Salih, M.H. A review of visible light communication (VLC) technology. In AIP Conference Proceedings; AIP Publishing LLC: Melville, NY, USA, 2020; p. 020289. [Google Scholar]
- Katz, M.; O’Brien, D. Exploiting novel concepts for visible light communications: From light-based IoT to living surfaces. Optik 2019, 195, 163176. [Google Scholar] [CrossRef]
- Teli, S.R.; Zvanovec, S.; Ghassemlooy, Z. Optical internet of things within 5G: Applications and challenges. In Proceedings of the 2018 IEEE International Conference on Internet of Things and Intelligence System (IOTAIS), Bali, Indonesia, 1–3 November 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 40–45. [Google Scholar]
- Almadani, Y.; Plets, D.; Bastiaens, S.; Joseph, W.; Ijaz, M.; Ghassemlooy, Z.; Rajbhandari, S. Visible Light Communications for Industrial Applications—Challenges and Potentials. Electronics 2020, 9, 2157. [Google Scholar] [CrossRef]
- Beguni, C.; Zadobrischi, E.; Avătămăniţei, S.-A.; Căilean, A.-M. Experimental Demonstration of a Visible Light Communications Crosswalk Assistance System. In Proceedings of the 2022 International Symposium on Electronics and Telecommunications (ISETC), Timisoara, Romania, 10–11 November 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Yang, H.; Zhong, W.-D.; Chen, C.; Alphones, A. Integration of Visible Light Communication and Positioning within 5G Networks for Internet of Things. IEEE Netw. 2020, 34, 134–140. [Google Scholar] [CrossRef]
- Katz, M.; Ahmed, I. Opportunities and challenges for visible light communications in 6G. In Proceedings of the 2020 2nd 6G wireless summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar]
- Lee, Y.U. Secure Visible Light Communication Technique Based on Asymmetric Data Encryption for 6G Communication Service. Electronics 2020, 9, 1847. [Google Scholar] [CrossRef]
- Webber, J.; Mehbodniya, A.; Teng, R.; Arafa, A.; Alwakeel, A. Finger-Gesture Recognition for Visible Light Communication Systems Using Machine Learning. Appl. Sci. 2021, 11, 11582. [Google Scholar] [CrossRef]
- Rehman, S.U.; Ullah, S.; Chong, P.H.J.; Yongchareon, S.; Komosny, D. Visible Light Communication: A System Perspective-Overview and Challenges. Sensors 2019, 19, 1153. [Google Scholar] [CrossRef]
- Sharma, P.K.; Ryu, J.H.; Park, K.Y.; Park, J.H.; Park, J.H. Li-Fi based on security cloud framework for future IT environment. Hum. Cent. Comput. Inf. Sci. 2018, 8, 23. [Google Scholar] [CrossRef]
- Perwej, Y. The Next Generation of Wireless Communication Using Li-Fi (Light Fidelity) Technology. J. Comput. Netw. (JCN) 2017, 4, 20–29. [Google Scholar] [CrossRef]
- Cailean, A.M.; Dimian, M. Impact of IEEE 802.15.7 Standard on Visible Light Communications Usage in Automotive Applications. IEEE Commun. Mag. 2017, 55, 169–175. [Google Scholar] [CrossRef]
- Sejan, M.A.S.; Rahman, M.H.; Aziz, M.A.; Kim, D.-S.; You, Y.-H.; Song, H.-K. A Comprehensive Survey on MIMO Visible Light Communication: Current Research, Machine Learning and Future Trends. Sensors 2023, 23, 739. [Google Scholar] [CrossRef]
- Shi, J.; Niu, W.; Ha, Y.; Xu, Z.; Li, Z.; Yu, S.; Chi, N. AI-Enabled Intelligent Visible Light Communications: Challenges, Progress, and Future. Photonics 2022, 9, 529. [Google Scholar] [CrossRef]
- Aydin, B.; Duman, Ç. Comparison of OOK-RZ and 4-PPM performances in Li-Fi systems using LED arrays. Opt. Laser Technol. 2022, 153, 108247. [Google Scholar] [CrossRef]
- Stoicuta, O.; Riurean, S.; Burian, S.; Leba, M.; Ionica, A. Application of Optical Communication for an Enhanced Health and Safety System in Underground Mine. Sensors 2023, 23, 692. [Google Scholar] [CrossRef]
- Gao, D.; Zhang, J.; Wang, F.; Liang, J.; Wang, W. Design and simulation of ultra-thin and high-efficiency silicon-based trichromatic PIN photodiode arrays for visible light communication. Opt. Commun. 2020, 475, 126296. [Google Scholar] [CrossRef]
- Li, J.; Zou, P.; Ji, X.; Guo, X.; Chi, N. High-speed visible light communication utilizing monolithic integrated PIN array receiver. Opt. Commun. 2021, 494, 127027. [Google Scholar] [CrossRef]
- Qiu, J.; Zhang, L.; Li, D.; Liu, X. High security chaotic multiple access scheme for visible light communication systems with advanced encryption standard interleaving. Opt. Eng. 2016, 55, 066121. [Google Scholar] [CrossRef]
- Zia-Ul-Mustafa, R.; Boroujeni, S.S.; Guerra-Yanez, C.; Ghassemlooy, Z.; Minh, H.L.; Zvanovec, S. Quantum Key Distribution for Visible Light Communications: A Review. In Proceedings of the 2022 13th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20–22 July 2022; pp. 589–594. [Google Scholar] [CrossRef]
- Osama, E.; Mohsen, R. Wireless Quantum Key Distribution in Indoor Environments. J. Opt. Soc. Am. B 2018, 35, 197–207. [Google Scholar] [CrossRef]
- Lu, Q.; Wang, F.; Huang, K.; Wu, X.; Wang, S.; He, D.; Yin, Z.; Guo, G.; Chen, W.; Han, Z. Quantum key distribution over scattering channel. arXiv 2021, arXiv:2109.12282. [Google Scholar] [CrossRef]
- Muhammad, T.; Marcos, K. Performance evaluation of IEEE 802.11p, LTE and 5G in connected vehicles for cooperative awareness. Eng. Rep. 2022, 4, e12467. [Google Scholar] [CrossRef]
- Plascencia, E.; Guan, H.; Chassagne, L.; Barrois, O.; Shagdar, O.; Căilean, A.-M. A Comprehensive Investigation on Multi-User Interference Effects in Vehicular Visible Light Communications. Sensors 2023, 23, 2553. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Chen, H.; Jiang, W.; Li, X.; Chen, X.; Meng, X.; Tian, P.; Sun, B. Optical encryption for visible light communication based on temporal ghost imaging with a micro-LED. Opt. Lasers Eng. 2020, 134, 106290. [Google Scholar] [CrossRef]
- Liao, T.-L.; Chen, C.-Y.; Chen, H.-C.; Chen, Y.-Y.; Hou, Y.-Y. Realization of a Secure Visible Light Communication System via Chaos Synchronization. Math. Probl. Eng. 2021, 2021, 6661550. [Google Scholar] [CrossRef]
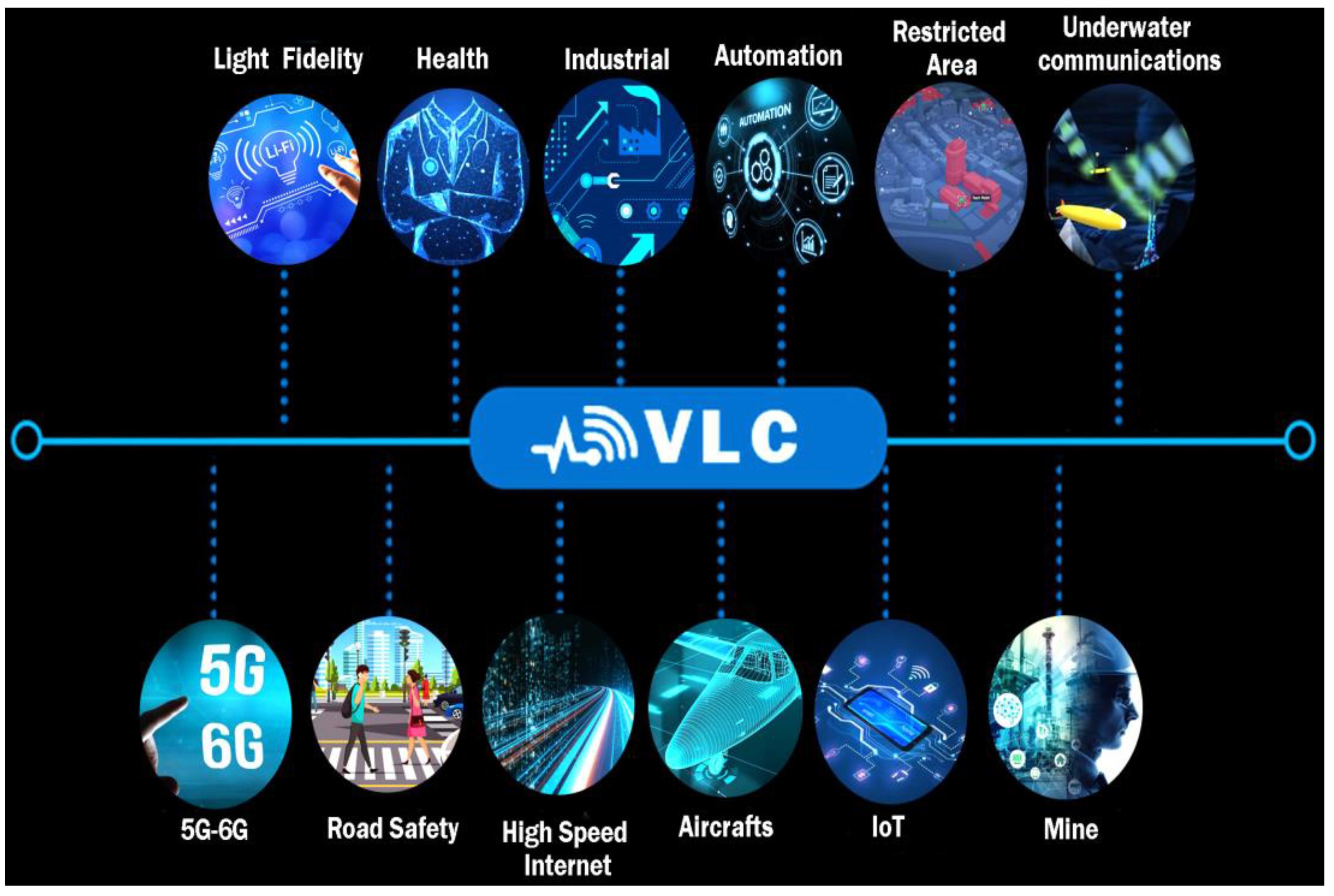







| Traffic Networks | RF Systems | Network Approaches |
|---|---|---|
| Low-density and sparse network | Radio cognitive network Short-range radio | Low |
| Vehicular network-type for densities | Short-range radio millimeter waves | High |
| Use of high-density network millimeter waves | Network based on VLC radio | High |
| Use of higher frequency bands (THZ) | Network based on 5G | High |
| VLC Applicability | VLC/Li-Fi Design and Architecture | VLC Approaches and Proposals | VLC IoT Challenges | Solution Presented | Future Perspectives |
|---|---|---|---|---|---|
| VLC systems [31] | ✓ | ✓ | ✓ | ✓ | ✓ |
| Vehicular systems [32] | ✓ | ✓ | ✓ | ✓ | ✓ |
| IoT [33] | ✓ | ✓ | ✓ | ✓ | ✓ |
| Safety systems [34] | ✓ | ✓ | ✓ | ✓ | ✓ |
| V2V and Li-Fi [35] | ✓ | ✓ | ✓ | ✓ | ✓ |
| IoT [36] | ✓ | ✓ | X | ✓ | ✓ |
| OIoT [37] | ✓ | X | ✓ | X | X |
| Industrial applications [38] | ✓ | ✓ | ✓ | ✓ | ✓ |
| IoT [39] | ✓ | X | ✓ | ✓ | ✓ |
| 5G and IoT [40] | ✓ | ✓ | ✓ | X | ✓ |
| 6G [41] | ✓ | ✓ | ✓ | X | ✓ |
| Source | Next Node | Destination Node | Mask Address | Interface Connection |
|---|---|---|---|---|
| 100.100.1.0 | 100.100.1.1 | 100.100.1.0 | 255.255.255.0 | ethvlc0 |
| 100.100.2.0 | 100.100.2.2 | 100.100.2.0 | 255.255.255.0 | ethvlc0 |
| 100.100.3.0 | 100.100.3.3 | 100.100.3.0 | 255.255.255.0 | ethvlc0 |
| 100.100.4.0 | 100.100.4.4 | 100.100.4.0 | 255.255.255.0 | ethvlc0 |
| 100.100.5.0 | 100.100.5.5 | 100.100.5.0 | 255.255.255.0 | ethvlc0 |
| 100.100.6.0 | 100.100.6.6 | 100.100.6.0 | 255.255.255.0 | ethvlc0 |
| 100.100.7.0 | 100.100.7.7 | 100.100.7.0 | 255.255.255.0 | ethvlc0 |
| 100.100.8.0 | 100.100.8.8 | 100.100.8.0 | 255.255.255.0 | ethvlc0 |
| 100.100.9.0 | 100.100.9.9 | 100.100.9.0 | 255.255.255.0 | ethvlc0 |
| 100.100.10.0 | 100.100.10.10 | 100.100.10.0 | 255.255.255.0 | ethvlc0 |
| 100.100.11.0 | 100.100.11.11 | 100.100.11.0 | 255.255.255.0 | ethvlc0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zadobrischi, E. The Concept regarding Vehicular Communications Based on Visible Light Communication and the IoT. Electronics 2023, 12, 1359. https://doi.org/10.3390/electronics12061359
Zadobrischi E. The Concept regarding Vehicular Communications Based on Visible Light Communication and the IoT. Electronics. 2023; 12(6):1359. https://doi.org/10.3390/electronics12061359
Chicago/Turabian StyleZadobrischi, Eduard. 2023. "The Concept regarding Vehicular Communications Based on Visible Light Communication and the IoT" Electronics 12, no. 6: 1359. https://doi.org/10.3390/electronics12061359
APA StyleZadobrischi, E. (2023). The Concept regarding Vehicular Communications Based on Visible Light Communication and the IoT. Electronics, 12(6), 1359. https://doi.org/10.3390/electronics12061359












