Abstract
This paper mainly summarizes three aspects of information security: Internet of Things (IoT) authentication technology, Internet of Vehicles (IoV) trust management, and IoV privacy protection. Firstly, in an industrial IoT environment, when a user wants to securely access data from IoT sensors in real-time, they may face network attacks due to the data being transmitted through an open channel. In order to solve this problem, we innovatively propose a user and device authentication model integrated with cloud computing, introduce an algorithm related to protocol design, and summarize the research direction of developing a more lightweight algorithm when designing security protocols in the future. Secondly, for mobile IoT applications, such as IoV, information collection and distribution is realized by establishing a network between vehicles and infrastructure. IoV will face security threats such as information insecurity and privacy disclosure. We introduce a typical trust management model for the IoV, which solves the problem of information unreliability by storing vehicle trust values. In the future, we are committed to making the process of computing node credibility using a trust model more robust. Finally, aiming at the privacy protection of the IoV, we propose a cross-domain anonymous authentication system model based on blockchain. The user’s auxiliary authentication information is stored in the blockchain, and the auxiliary authentication information of any registered user can be obtained from the blockchain. The privacy protection of cross-domain authentication can be realized through anonymous authentication, which greatly saves the communication cost of cross-domain authentication. In the future, we will try to use deep learning or federated learning to integrate with blockchain for actual deployment.
1. Introduction
With the development of a new generation of communication technologies, the Internet of Things (IoT) is playing an indispensable role in every aspect of people’s work and life, with increasingly widespread applications in intelligent transportation, safe homes, industrial monitoring, personal health, and online intelligence gathering [1]. Specifically, sensors are embedded and equipped in railways, cars, wearables, buildings, and other objects, combining the IoT with the Internet to enable the integration of people, social and physical systems. Although the wide application of IoT technology in various fields has indeed improved the efficiency of social operation, security and privacy protection issues have also aroused people’s attention [2]. IoT authentication technology, Internet of Vehicles (IoV) trust management, and privacy protection are fundamental issues for the security of the IoT. The solution to these issues is closely related to the overall security of IoT systems. At the same time, these three directions are also closely related to key application scenarios of IoT, such as smart cities, intelligent transportation, etc. Therefore, when discussing the information security issues of IoT, these three topics are essential.
First of all, IoT sensor nodes are typically low-power, low-cost, and lightweight devices; therefore, their computing power is relatively limited, leading to their weak ability to resist malicious attacks, which exacerbates the proliferation of malicious attacks on IoT devices. Many existing security mechanisms fail to meet the needs of current high-security features. As a result, devices in various application scenarios are threatened by malicious codes or illegally controlled by rivals. Authentication mechanisms are the first line of security in IoT information security. Secondly, in the transportation IoT, also known as the IoV, the real communication between vehicles is related to social order and life safety. If some malicious vehicle nodes send false information, the consequences will be unimaginable. How to guarantee real communication between vehicles is also a focus of our research. Finally, in the authentication process of the IoT, there is often the demand for cross-domain access of users, and repeated authentication will bring heavy communication costs and expose the privacy of users. Therefore, we also designed a cross-domain anonymous authentication scheme based on blockchain to meet the above requirements. Since there are many widely used technologies in the security mechanisms of the IoT, such as cloud computing and blockchain, the following will introduce the application of these two technologies in the solution.
Since the introduction of IoT technology, application providers have urgently needed updates to and technical progress of IoT technology. The addition of cloud computing meets the needs of the rapid development of the IoT [3,4]. The new model of the IoT needs to realize automatic data processing and exchange operations, which can not only ensure the high efficiency of computing power and storage capacity but also ensure data security and significant cost advantages. Cloud computing technology can meet the above requirements, so the in-depth and effective implementation and application of IoT technology cannot be separated from cloud computing [5].
Cloud computing has advantages over traditional computing models, such as high-speed Internet connections and nearly unlimited storage and computing power [6]. Cloud computing mainly combines multiple computer entities into a powerful computing system through grid computing technology and then distributes the supercomputing power of cloud computing to the end users equally, so that applications can be processed in parallel at a very low cost. In addition to computing power, the advantage of storage capacity is also evident in cloud technology. In recent years, people have become accustomed to transferring the unstructured data they generate or the resources they use to the cloud. In order to protect the privacy of user information, a cloud storage system should have high reliability and automatic fault tolerance.
There are a large number of wireless terminal nodes in the IoT, and mobility nodes may also exist [7]. Without effective management, these nodes are likely to be maliciously invaded, causing errors in device operation analysis and even major accidents [8]. In addition, the nodes in IoT generally consist of sensors with relatively simple functions, which do not have the ability to detect the security of the system [9]. In a peer-to-peer network, when there are too many nodes and excessive network latency, the transaction sequence observed by each node in a certain period of time may not be completely consistent. Based on the above, we need to design a consensus mechanism to ensure that the order of transactions occurs in the same time. The characteristics of blockchain can provide this mechanism for ensuring the secure transmission of data between IoT devices [10,11].
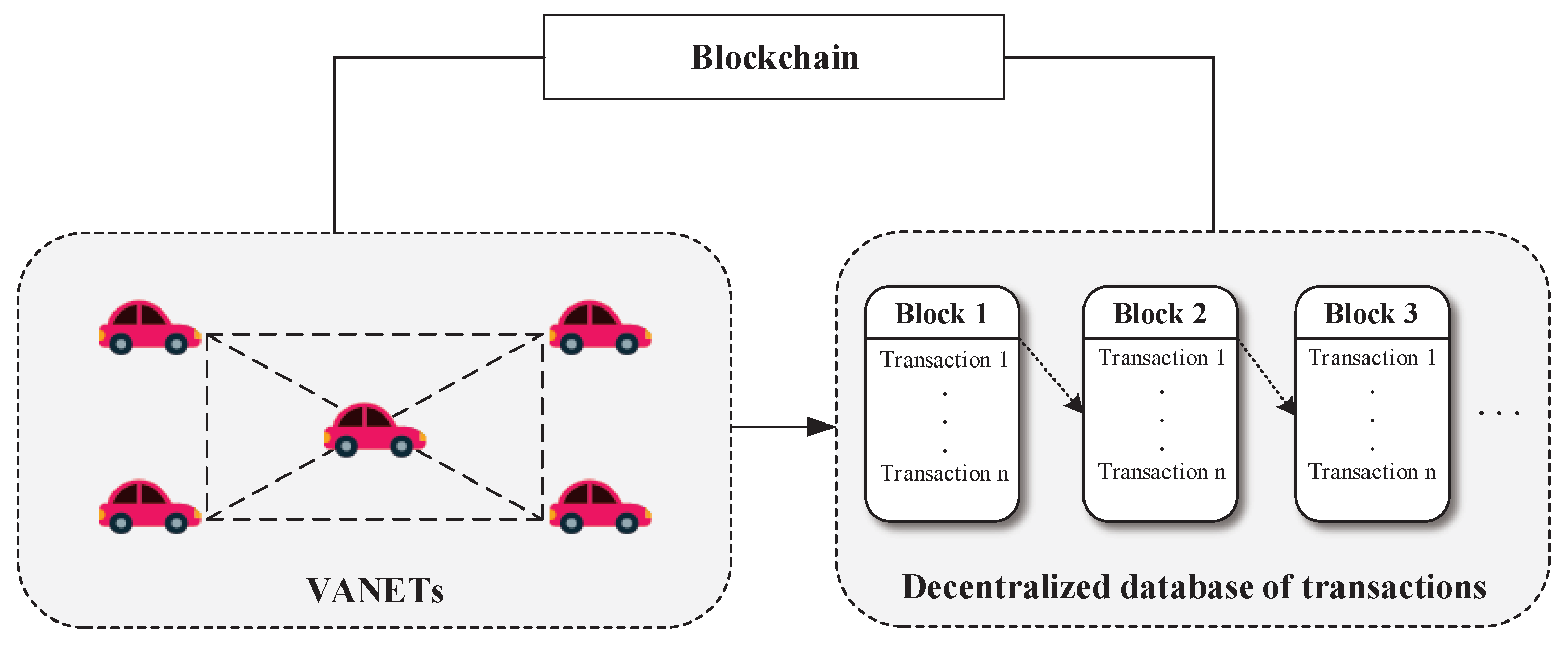
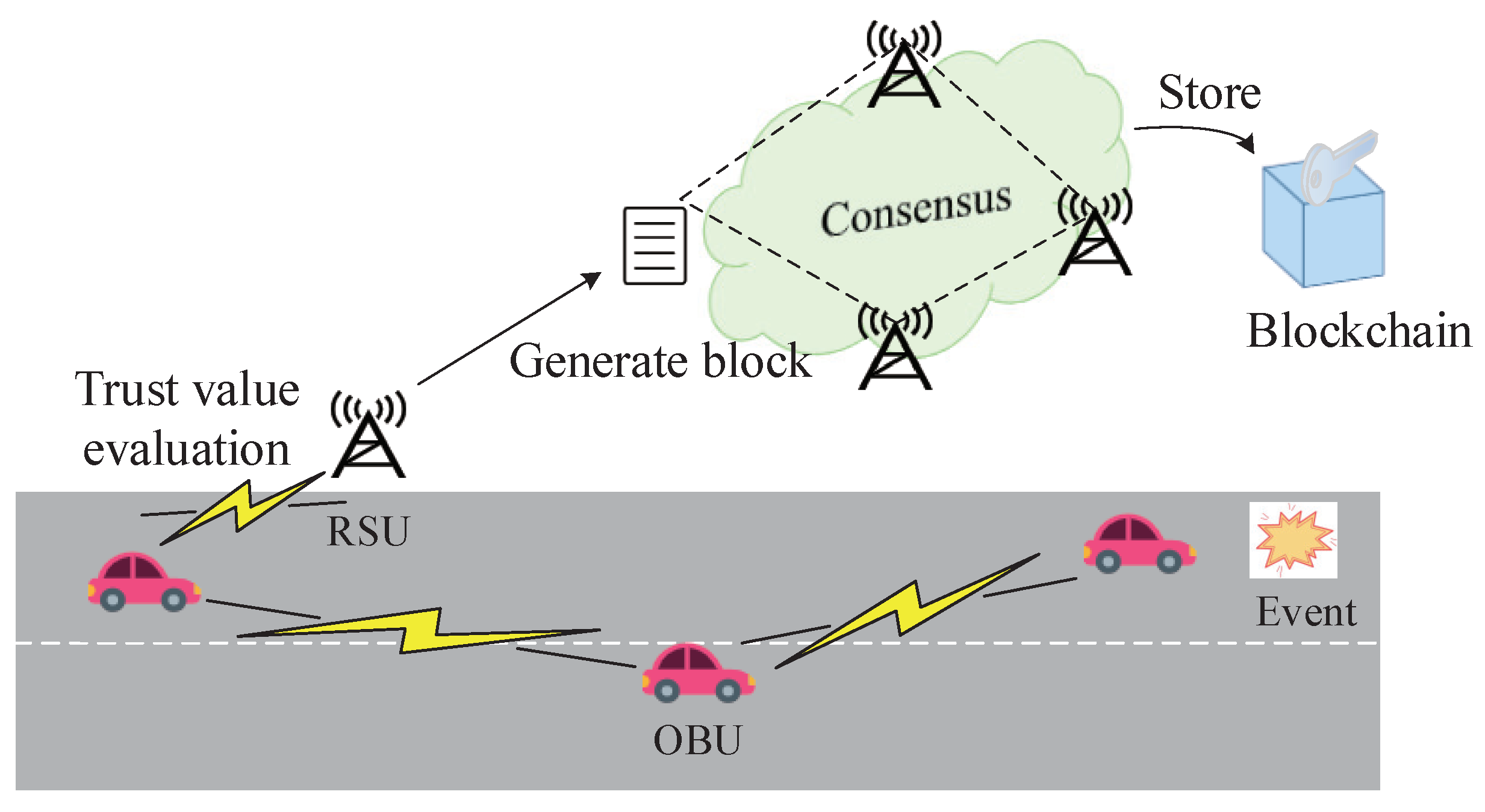
Researchers have provided a series of methods of blockchain deployment in IoV. There are usually two existing entities in IoV: vehicles and roadside units (RSU). The communication styles are divided into vehicle-to-vehicle (V2V) communication and vehicle-to-infrastructure d(V2I) communication. It is common to consider blockchain as a decentralized database. Regarding the process of initial V2I authentication as a transaction, blockchain make use of its chain structure to storage the vehicles’ partial autentication information. Thanks to its chain structure, blockchain can guarantee data consistency, thus making it possible to realize cross-domain authentication. In IoV, RSUs are usually chosen as miners to commit ledgers because they are more stable and secure than vehicles. In the following V2I and V2V authentication phase, RSUs only need to search for the information of vehicles requiring authentication in the blockchain. As a consequence, there is no need for a third-party certification center to always be online. Combing blockchain and IoV enables IoV to further improve its authentication efficiency and scalability [12]. The deployment of blockchain in IoV is shown in Figure 1.
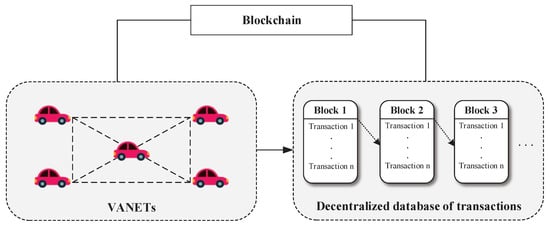
Figure 1.
Blockchain Deployment in IoV.
1.1. Contribution
The contributions of this paper are as follows:
- For the user authentication scenario of the IoT, we analyze the attacks faced by the three-layer structure of the IoT and summarize some methods, algorithms, and previous work of the IoT authentication. Finally, we describe the direction of our future research.
- Aiming at the requirements of vehicle security communication in the IoV, we introduce a trust management model based on blockchain, summarize some common consensus algorithms, and explore the future direction of trust management in the IoV.
- For IoT users’ cross-domain anonymous access requirements, we introduce a cross-domain anonymous authentication system model based on blockchain, summarize the previous work, and conclude and compare the performance parameters of several consensus algorithms.
1.2. Paper Outline
Section 2 introduces the problems in designing authentication protocols for the IoT, including privacy protection and false information spread by malicious nodes in the IoV. Section 3 first introduces the related technologies of security protocol design and the existing related work and schemes and then introduces the application of blockchain technology in the IoV to solve related problems. Section 4 analyzes the development trend of authentication protocol and the next research direction. The last section is the summary.
2. Challenges
2.1. Problems in Designing Security Protocols
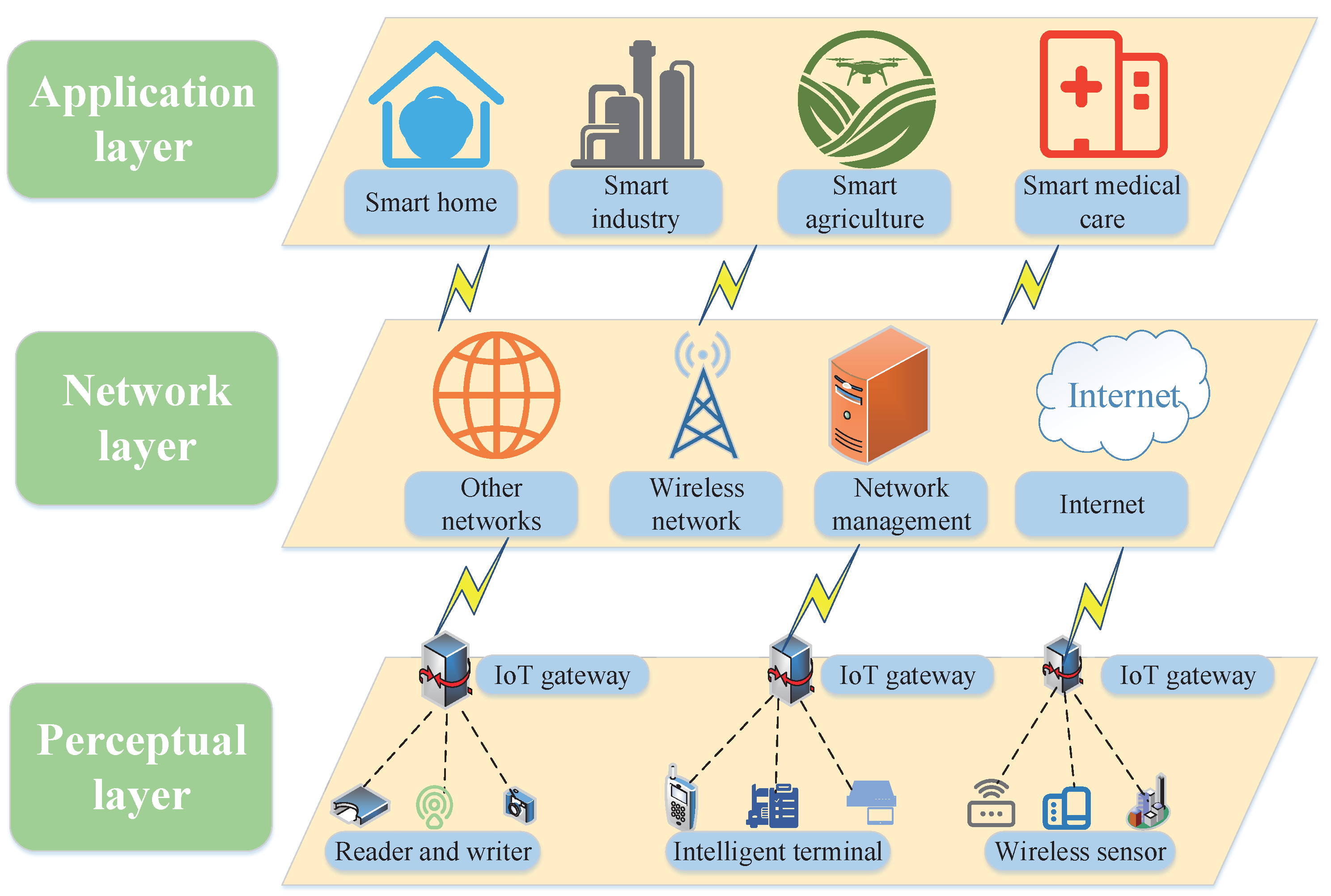
The IoT is mainly composed of a perception layer, network layer, and application layer, as shown in Figure 2 [13]. The perception layer mainly collects and captures the state information of the external environment or items through sensors, which use radio frequency identification(RFID) and communication technologies, and transmits the information to the upper layer. Common attacks in perception layer include side channel attacks, denial of service (DoS) attacks, witch attacks, and so on [14,15]. Based on the existing Internet and mobile communication network, the network layer stores, manages and analyzes data collected by sensors through the cloud computing platform and transmits it to the application layer. Common attacks at the network layer include man-in-the-middle attack, network listening, and routing attack. The application layer provides services to users through the application layer protocols of the IoT. Common attacks include identity forging attacks, injection attacks, and replay attacks. Due to the vulnerability of the IoT network, a secure IoT authentication protocol must meet the requirements of reliability, integrity, privacy, anonymity, forward security, and non-repudiation [16].
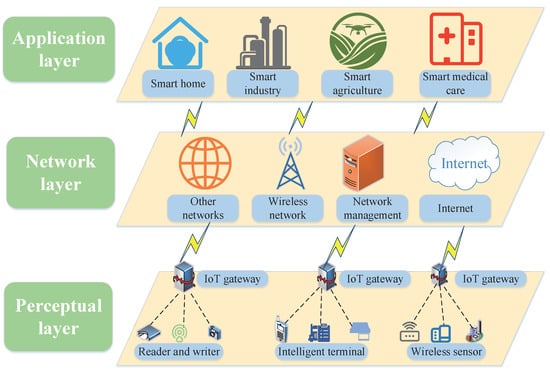
Figure 2.
Three-Layer Structure Diagram of the IoT.
However, the existing authentication protocol generally has the following issues: (1) Most authentication protocols are not as secure as they claim. These protocols have some security problems or functional defects to some extent. For example, some protocols lack an effective mechanism to quickly detect unauthorized logins and cannot resist the user’s fake attacks, offline password guessing attacks, and privileged internal attacks, etc. (2) Some protocols adopt encryption technologies with high complexity, such as the bilinear pairing and elliptic curve cryptography(ECC) algorithm, which will make the designed security protocols consume more computing resources [17,18,19].
2.2. Malicious Vehicles, Nodes Spread False Information
The continuous development of networking has provided great convenience for people’s transportation and information interaction. At the same time, the IoV, as an intelligent network including people, vehicles, base stations, and other elements, the security of the IoV is directly related to the information security of users and life security, and has thus received increasing attention. The relationship between nodes is complicated, which greatly threatens the safety of the IoV. Vehicles share road traffic safety information through communication. However, due to the complicated relationship between cars, the authenticity and reliability of the news are in doubt. On the one hand, vehicles acquire information through sensors, and the information acquired by vehicles may deviate from the real environment due to sensor failures and other reasons. On the other hand, there may be some malicious nodes in the network, which deliberately broadcast false messages and interfere with the normal driving of other vehicles [20].
2.3. Privacy Issues in the IoT
The security of IoT poses a serious threat to users’ privacy protection. A large number of IoT devices record a large amount of user privacy data, which magnifies the security risk coefficient and privacy scope of users. The data not only record people’s travel route, location, voice, and other information, but also include users’ health data and daily travel plans, which can easily be used by platforms and even hackers. In 2021, the discovery that the Tesla company used a camera in the car records and transmitted passenger videos or images has caused a great stir, and various similar events also emerged in in an endless fashion. The security and privacy issues of the IoT have caused problems for and hidden worries in people. Anonymous identity authentication uses cryptography knowledge as the first choice to protect the IoT security and user privacy security. Anonymous identity authentication is usually used to generate pseudonyms, which is divided into two schemes: (1) a trusted third party assigns pseudonyms to users during registration [21,22], and (2) the regular exchange of pseudonyms takes place between users [23,24]. Because both of these schemes rely on a trusted third party entity, the rapid growth of node data overloads the central entity, which may be at risk of a single point of failure. In addition, frequent access to third parties leads to high communication overhead, which is not conducive to cross-domain authentication and fails to meet the requirements of the current IoT for low latency and high reliability.
3. IoT Security Protection: Selected Approaches and Algorithms
This chapter first introduces the user and sensor device authentication scenarios and some existing related work and then introduces the common technologies and mathematical methods in the IoT authentication protocol, including Chebyshev chaotic mapping, biometric identification technology, blockchain, and other encryption technologies. Finally, some solutions to the problem of trust management and anonymous identity authentication are put forward.
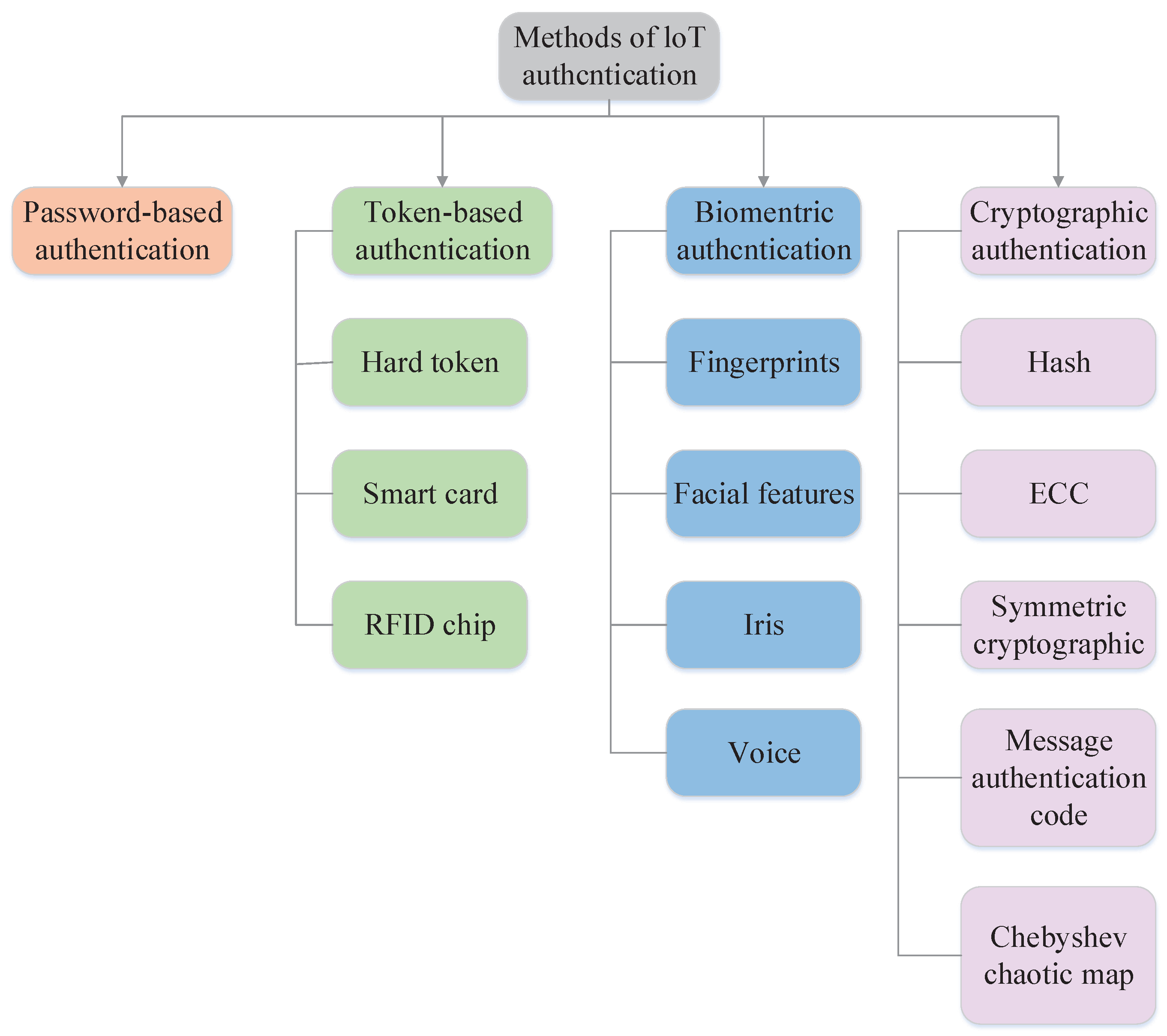
At present, a large amount of literature shows an IoT authentication protocol to protect IoT information security and help users and IoT devices to authenticate each other. Different protocols use different encryption methods and authentication mechanisms. Thus, Figure 3 shows a well-structured taxonomy of technical methods.
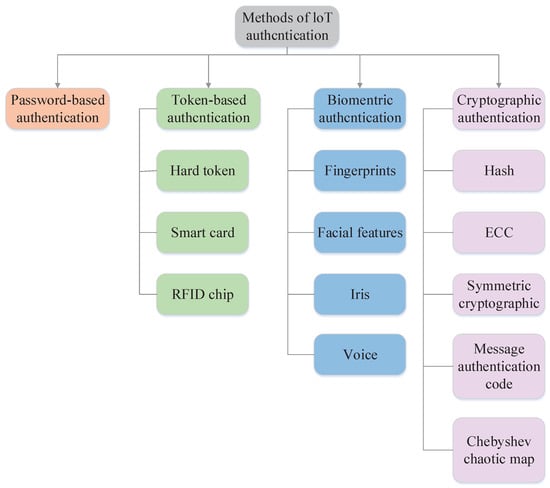
Figure 3.
Methods of loT Authcntication.
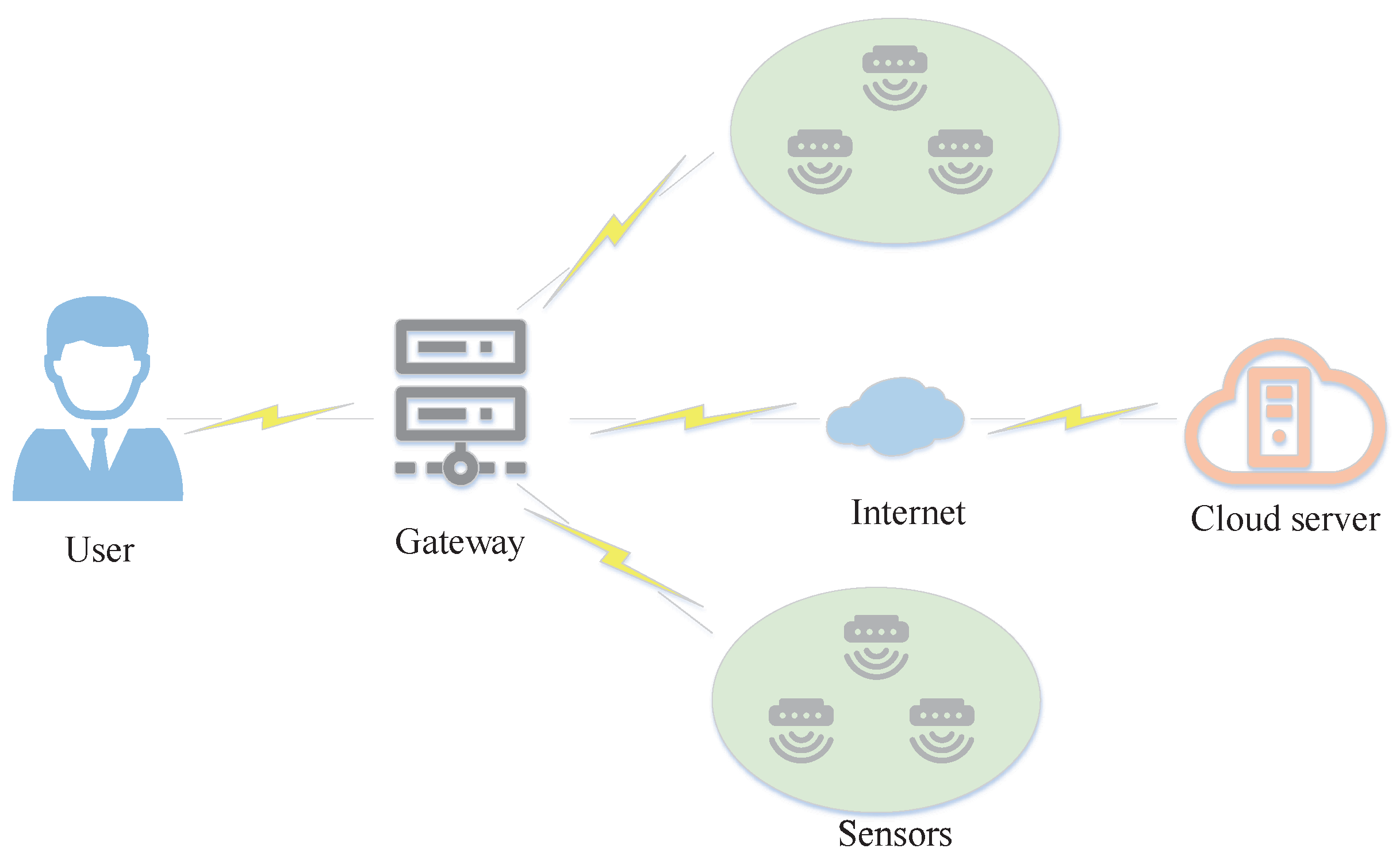
At present, the application scenarios of user and device authentication mainly include users, gateways, wireless sensor networks, and sensors. These scenarios are sometimes accompanied by cloud servers, as shown in Figure 4. In the wireless sensor network, users can access the sensor after being authenticated by the network gateway. The gateway periodically uploads data to the cloud server, and users can access the data after mutual authentication with the cloud server. Previous studies [25,26,27] proposed a two-factor authentication protocol for wireless sensor networks based on ECC to realize mutual authentication among users, sensors and gateways. A two-factor authentication scheme of wireless sensor networks proposed by Vaidya et al. [28] only uses a simple hash function and an exclusive OR(XOR) function for encryption. Hu et al. [29] proposed a three-factor authentication scheme in the industrial IoT environment, and a cloud server can regularly process the data uploaded by the gateway. Other studies [30,31] have proposed the authentication protocol of wireless sensor networks based on smart cards to realize the mutual authentication of users and sensor nodes.
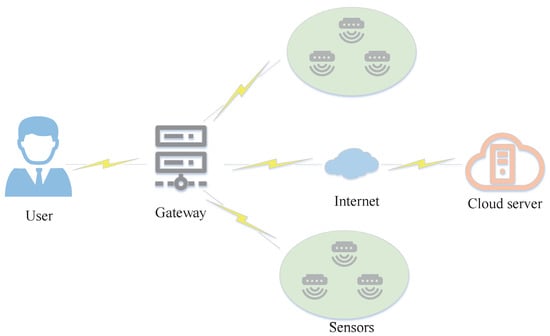
Figure 4.
User and Device Authentication in IoT.
The performance evaluation of authentication schemes is usually considered from three aspects: security, computing overhead, and communication overhead. In terms of security analysis, it mainly evaluates the security of the scheme design, which is generally divided into formal security analysis and informal security analysis. Before security analysis, it is necessary to make assumptions about the attack model of the system. The most common model is the Dolev–Yao model [32]. Informal security analysis is mainly used to analyze the security of the scheme through literal description and inferencing, which is difficult to understand. However, most informal security analyses could only analyze known attacks. Formal security analysis refers to the use of existing security analysis tools to detect possible vulnerabilities in the scheme, including model detection methods, theorem-proving methods, and belief logic methods. The common model detection methods used in papers are Automated Validation of Internet Security-sensitive Protocols and Applications(AVISPA), the tool-theorem-proving methods include ProVerify, and the belief logic methods includ Burrows–Abadi–Needham(BAN) logic. Formal security analysis requires the dedicated study of different rules of distinguished tools. Compared with formal security analysis, the access threshold of informal security analysis is higher. The communication overhead refers to the total amount of data received and sent by each entity in the scheme, usually in bits or bytes. First, the length of the large prime number selected by the system is assumed. Then, the message length after the implementation of the cryptographic algorithm is estimated according to the characteristics of each cryptographic algorithm. The communication overhead of each entity is evaluated mainly by adding the message length of the cryptographic algorithm used. The calculation overhead refers to the total running time of each encryption algorithm implemented by each entity in the scheme, usually in ms [33,34,35].
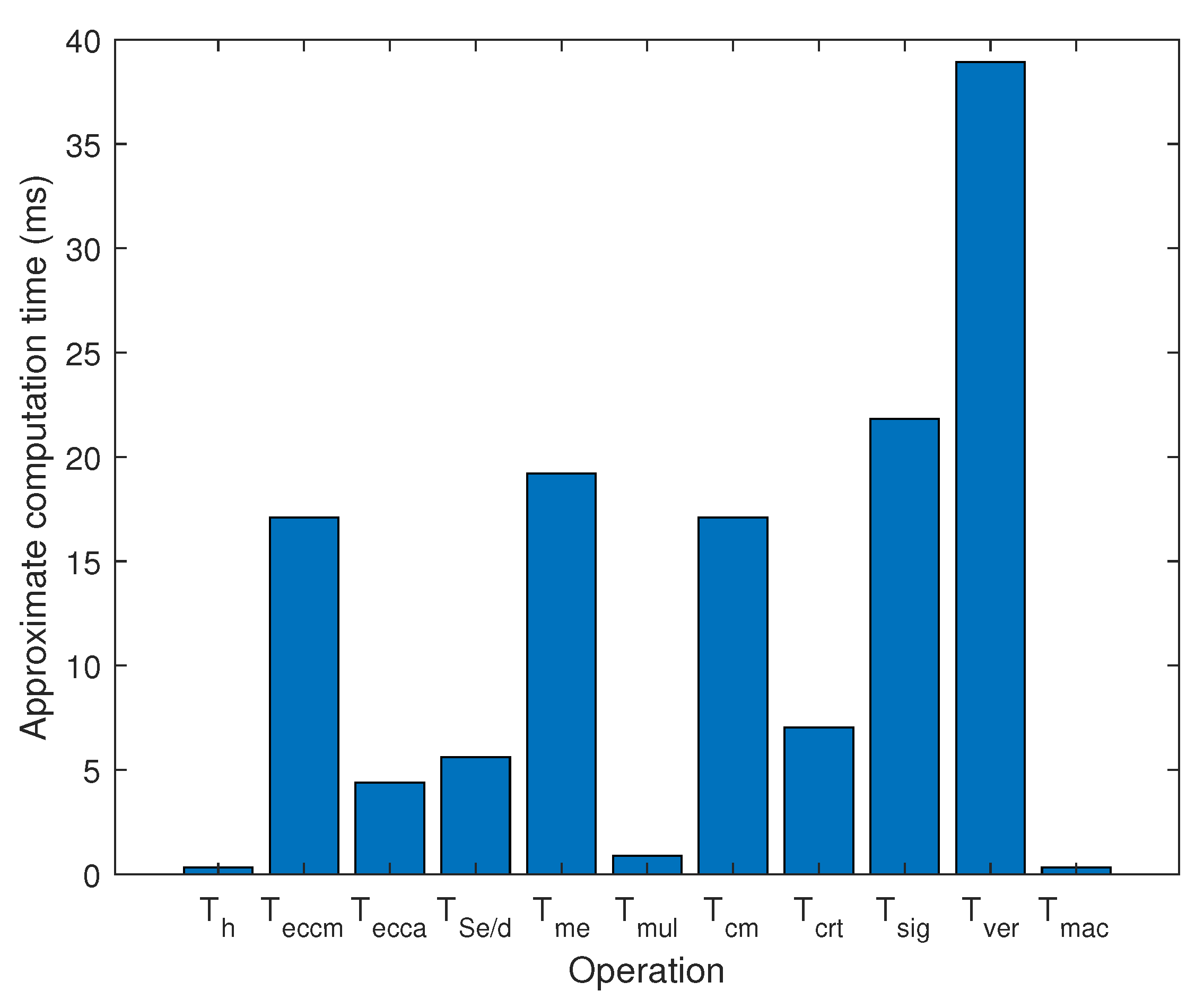
In the design of an authentication protocol, the choice of cryptography related encryption algorithm is also very important for the performance of the whole protocol. Figure 5 shows the computational execution time required for different encryption primitives based on the available experimental results [29,36]. The subsequent Table 1 is the time of various encryption operations.
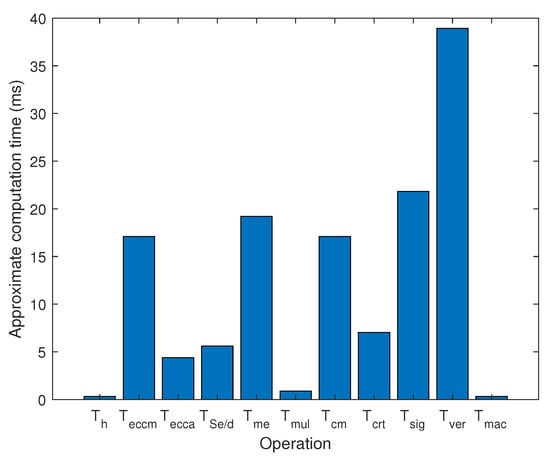
Figure 5.
Approximate Time Required for Various Operations.

Table 1.
Time for Various Cryptographic Operations.
3.1. Chebyshev Chaotic Mapping
At present, most security protocols rely on the ECC algorithm, which can meet the necessary security requirements, but the cost of computation and communication is relatively large. On the basis of meeting the security requirements, the Chebyshev polynomial is used to encrypt messages, but the cost of computation is only one-third of that of the ECC algorithm [37,38,39]. Thus, the following is a brief introduction to the Chebyshev polynomial algorithm.
Chebyshev’s polynomial is a polynomial of order n in x, ; when , Chebyshev polynomials satisfy the semigroup property. Zhang et al. [40] gave the definition of the extended Chebyshev polynomial on and proved that the extended Chebyshev polynomial also satisfies the semigroup property [41]. The recursive formula of the extended Chebyshev polynomial is as follows:
where p is a large prime number. The semigroup properties of extended Chebyshev polynomials are defined as follows:
Two difficult mathematical problems exist on extended Chebyshev polynomials. According to the chaotic map-based discrete logarithm problem (CMBDLP), given and x, it is infeasible to calculate u in polynomial time.
3.2. Biometric Identification Technology
With the popularity of mobile intelligent devices and the development of biometric identification technology, fingerprint, iris, and other biometric features have become popular identity authentication methods for mobile intelligent devices. The traditional authentication mode has security risks. For example, a user’s password may be leaked, and the secret parameters of smart cards can be extracted using technologies such as energy analysis. Compared with traditional authentication methods, biometric features do not need to be memorized or carried and are difficult to forge. In order to enhance the security of authentication protocols, many schemes begin to introduce biometric features as new authentication factors. Authentication protocols based on biometric features have become a hot topic in the current research of authentication protocols [42,43,44].
Biometric identification refers to using a human’s inherent biological characteristics (such as fingerprints, facial features, iris, voice, etc.) and behavioral characteristics (such as walking posture, gait, etc.) as identification markers, which are not easy to lose and difficult to copy [45,46]. Biometric identification technology makes the authentication system overcome the difficulty of password management and improve the usability of the authentication system. Biometric hashing is a protection technology for the biometric template. The key idea of biometric hashing is to convert the original biometric to a new random space and store the converted template. The conversion function is irreversible [47].
- The original biological features were extracted and the m-bit feature vector y was obtained;
- We generated a pseudo-random matrix of using a user-specific token:, where n is the length of the final value;
- We converted the matrix to an orthonormal matrix ;
- Finally, we made a random projection of y and through the inner product.
3.3. Blockchain Solves the Trust Management Problem
The trust management mechanism is responsible for the generation, distribution and revocation of trust certificates of vehicle nodes [48,49,50,51]. In order to solve the problem of privacy leakage caused by tracking specific trust values, according to the trust values of vehicle nodes obtained by the trust evaluation mechanism, the corresponding trust levels are divided, and the trust certificates of corresponding states are generated [52,53,54,55]. That is, the calculated trust value of vehicle nodes is fuzzified, and the trust state is used instead of the specific trust value [56,57,58,59]. Different trust levels represent different trust states, and the noise contained in them is also different, so users with low trust level cannot query the information of users with high trust levels. It also ensures the privacy of trust value data in the process of trust inquiries and certificate issuance and revocation, avoids the tracking of malicious nodes and the attack of untrusted nodes, and effectively prevents nodes from denying and tampering with trust values [60,61,62]. It can also realize privacy protection in the trust management process and effectively improve the security level of the vehicle networking management model. At the same time, in the blockchain network composed of RSU and its servers, the trust certificates of vehicle nodes are synchronized, and the vehicle nodes can obtain the relevant certificates and verify the authenticity only by querying the RSU without sending a request to a remote server, which greatly reduces the communication delay [63].
Because of the central design, there are some problems, such as a high time delay, a single point of failure, and poor expansibility, which do not meet the demands of the IoV [64]. Blockchain technology applied to the field of trust management of car networking can establish a safe and reliable distributed database and improve the security of car networking. In this mechanism, a blockchain network is constructed by vehicle nodes, RSU, and its servers, and the trust value of vehicle nodes is regarded as a transaction in the IoV, forming a new block in a manner similar to transactions based on Bitcoin. The hash values of each block are chained together in order. Among them, the vehicle nodes only communicate messages and do not participate in data calculation. RSU verifies the authenticity of the event, and its server calculates the corresponding message trust value and then selects one of the nodes for accounting according to the consensus mechanism. All the trust values in the blockchain are accumulated to form a comprehensive trust value of vehicle nodes, which is transmitted, stored, and maintained in the network. There are two kinds of data in blockchain networks: block data and status data. Among them, the block data refers to the record of every transaction in the blockchain, and the state data refers to the information of the current state of the vehicle node. The model diagram is shown in Figure 6.
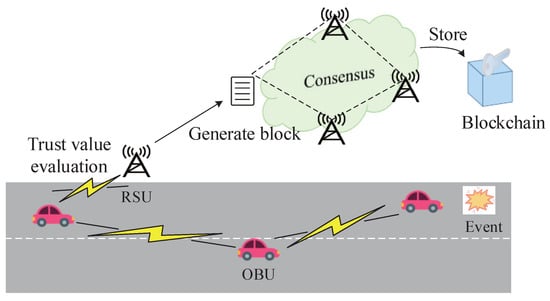
Figure 6.
Trust Evaluation Model of IoV Based on Blockchain.
After calculating the trust value, RSU stores the trust value into the blockchain through a consensus algorithm. As the core technology of blockchain, a consistency algorithm provides mechanism support and a guarantee for realizing the decentralization, openness, autonomy, unchangeable information, anonymous traceability, and other functions of blockchain and allows the efficient realization of strong consistency and final consistency in distributed systems. With the popularity of Bitcoin and the development of blockchain technology, the mainstream model of the blockchain consensus process has been gradually given. Although this model is not a general model and cannot show all consensus processes, it can reflect the core ideas of mainstream consensus algorithms. In the construction of a blockchain system on a P2P network, all nodes can be represented as “miners”, and nodes can be generally divided into those generating data or normal transaction nodes, labeled “P”, and nodes that perform mining operations on normal nodes (including validation, packaging, updates, etc.), labeled “M”. The nodes P and M can intersect. All miners participate in the consensus competition process. In a particular algorithm, miners elect representative nodes to replace their positions in the consensus process and compete for the accounting rights. The set of these representative nodes is labeled “D”. The node that obtains the accounting right is marked as “A”, and in each consensus process, the accounting node of this round is updated. The following will introduce four existing mainstream consensus algorithms [65].
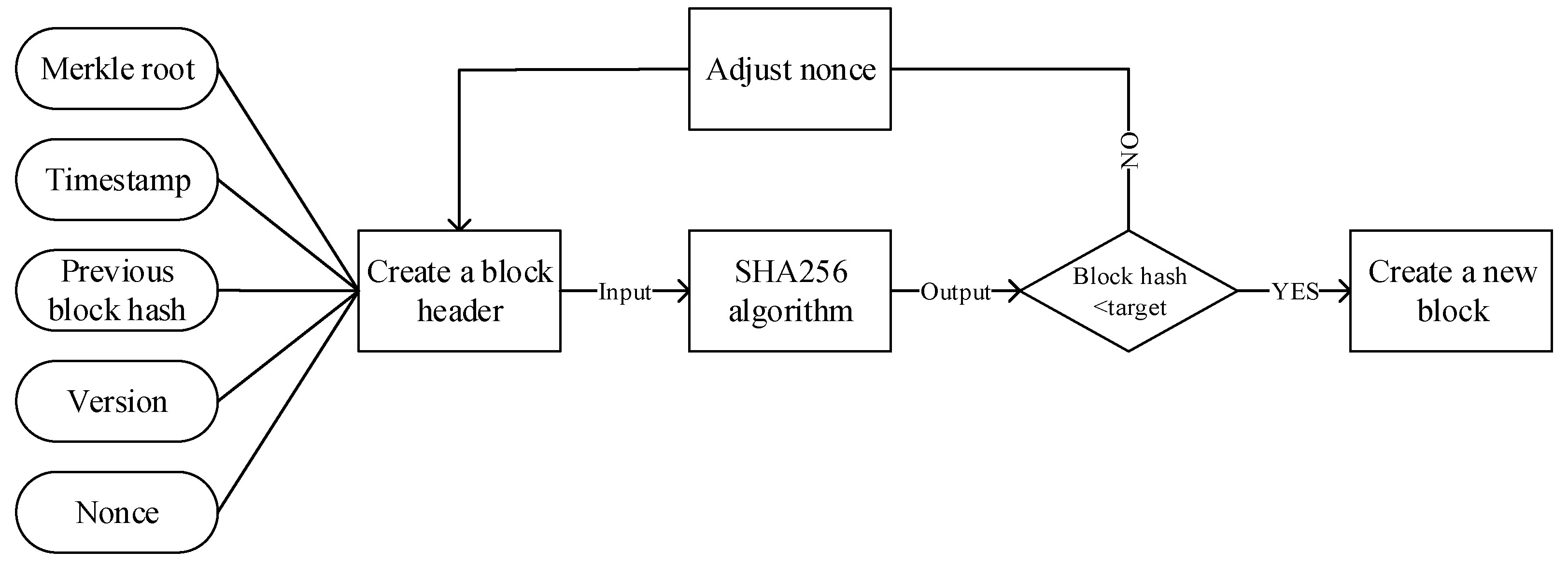
- Proof-of-Work (PoW)A workload certificate can be simply understood as a certificate that confirms that someone have carried out a certain amount of work. The workload proof mechanism is the consensus mechanism adopted by Bitcoin. Miners obtain corresponding block rewards through hard mining.In a digital currency system, workload proof mainly guesses a nonce through calculation, so that the hash value of the content after it pieces together the transaction data meets a prescribed upper limit. As the hash value is obtained by the collision of the group lift method in mathematics, many calculations are needed. As long as the miners who can put forward random numbers that meet the requirements are considered to have been paid a certain amount of work, they can obtain the reward of this block.A hash operation is the most common workload proof mechanism. This mechanism mainly uses the complexity of hash operations through a given initial value, carries out a simple value increment operation, and uses the hash algorithm to solve it until the collision value that meets the conditions is found. The length of the collision value obtained by different hash algorithms is different, and the required workload and security performance are also different. The longer the collision value is, the more work is required. For the same hash algorithm, the number of the first N bits of the hash value can be set to 0 to adjust the operation’s difficulty. Bitcoin adjusts the mining difficulty according to this principle. The recommended miner election principle is:Here, Difficulty represents the hash value of the current block, and the system can adjust Difficulty by controlling the rate at which blocks are generated. The RSU responsible for generating a new block needs to compute the number at the fastest rate while satisfying the above inequality.The specific process is shown in Figure 7. The first node to find the appropriate nonce obtains the bookkeeping right. The node generates a new block and broadcasts it to other nodes, and these other nodes verify the block. If it passes the verification, it will accept the block and complete this round of consensus. Otherwise, it will reject the block and continue to search for the appropriate nonce. Thus far, it has been very difficult to find a nonce that meets the requirements, which requires nodes to consume a lot of computing power. With the continuous accumulation of effective blocks, malicious nodes need to consume a great deal of computing power to overturn the previous blocks.
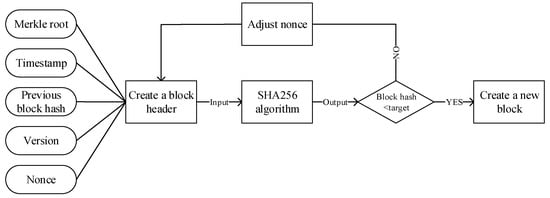 Figure 7. PoW Algorithm Flowchart.
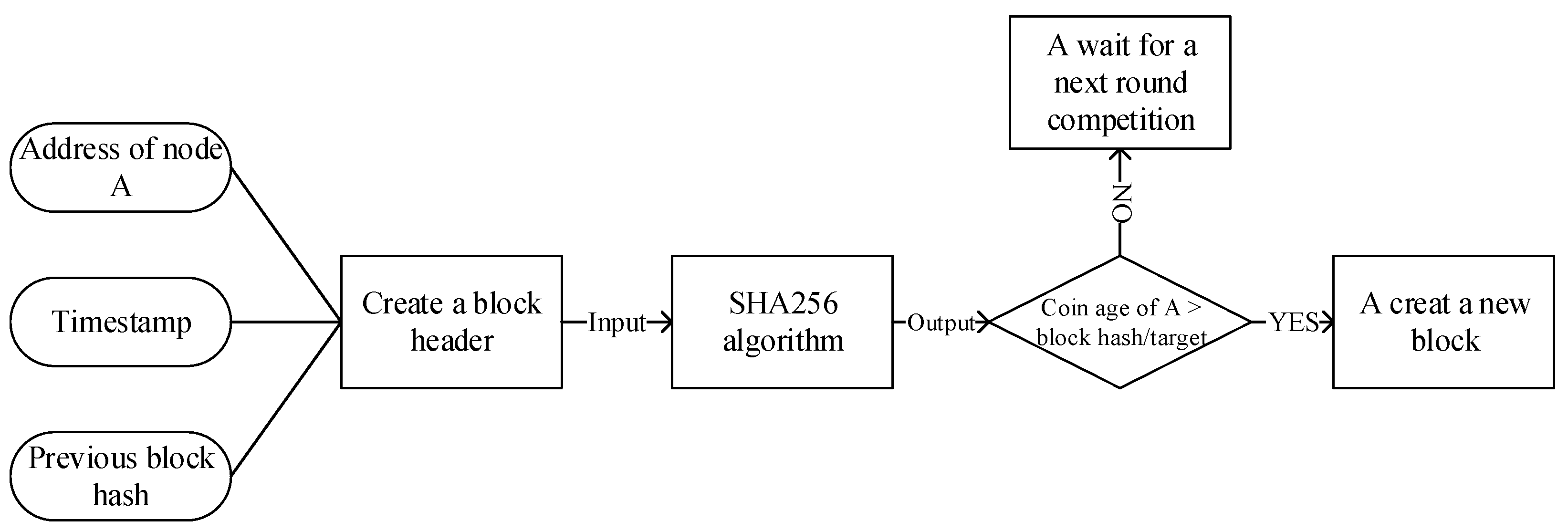
Figure 7. PoW Algorithm Flowchart. - Proof-of-Stake (PoS)With the increasing number of people involved in Bitcoin mining, the disadvantages of PoW have been gradually exposed [66]. For example, due to the increasingly fierce competition for computing power, more energy consumption is needed to obtain tokens, which leads to the gradual concentration of accounting rights in the “mining pool” with a large amount of computing power. Based on this, researchers want to adopt a new mechanism instead of workload authentication. PoS came into being and proposed the concept of “coinage”, which is the accumulation of the product of token holding and holding time. PoS uses coin age competition instead of computing power competition to solve the problems existing in PoW.PoS also needs to calculate the hash value, but unlike PoW, it does not need to find the nonce value through continuous violence calculation. The specific process is shown in Figure 8. Each node only needs to calculate a hash once in each round of consensus. The more rights and interests it has, the greater the chance it has of meeting the hash goal and obtaining bookkeeping rights.
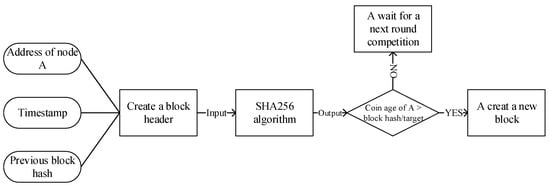 Figure 8. PoS Algorithm Flowchart.
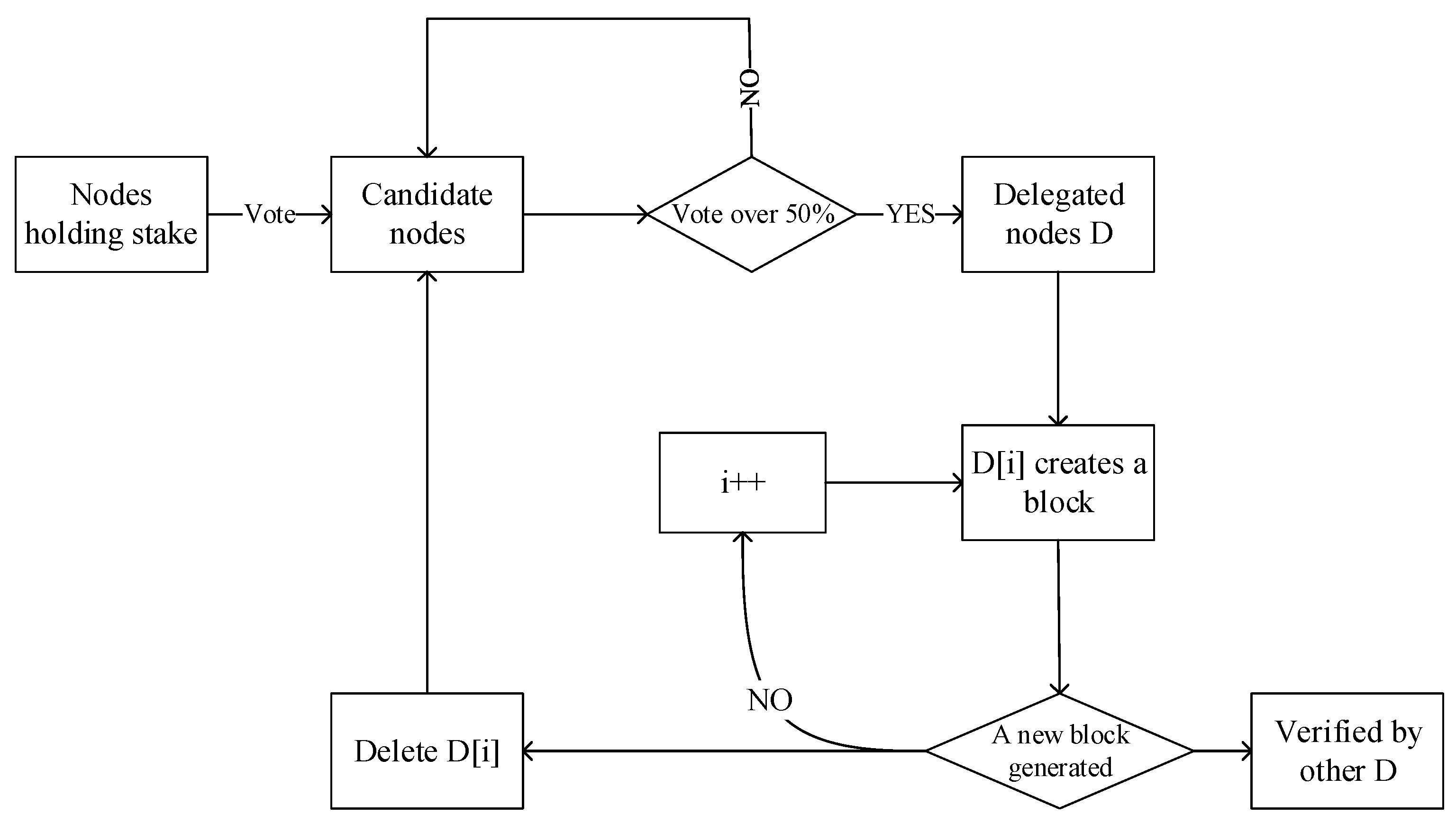
Figure 8. PoS Algorithm Flowchart. - Delegated-Proof-of-Stake (DPoS)The entrusted equity proof blockchain has a voting system, and stakeholders deliver their work to a third party. In other words, they can vote for several representatives to protect the network instead of themselves. Delegates are also called witnesses, and they need to reach a consensus in the process of generating and verifying new blocks. The voting right is proportional to the number of coins held by each user. The voting system varies from project to project, but generally, each delegate gives his or her own opinion when voting. Delegates collect awards and distribute them proportionally among their respective constituents.The specific process is shown in Figure 9. Token holders obtain votes through pledge tokens and select a number of nodes as block producers by voting to perform the obligation of generating blocks on behalf of token holders. DPoS is similar to the system of the company’s board of directors, which allows users with coins to entrust the work of production blocks to more competent professionals, and at the same time, they can enjoy the rewards of participating in the block. The nodes with the most votes from users become out-of-block nodes, with 21 nodes represented by the enterprise operation system (EoS). In each round of consensus, one outbound node is selected in turn to generate blocks and broadcast to other outbound nodes for verification. If the node fails to complete the block out within the specified time or generates invalid blocks, it will be disqualified and replaced by voting again to select a new block-out node.
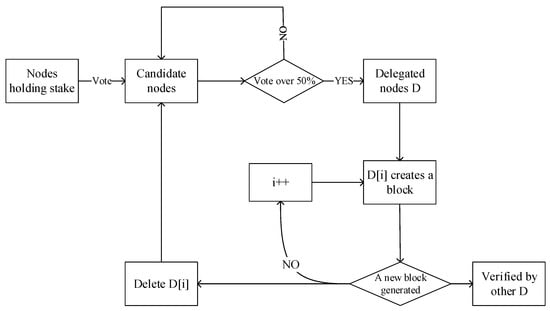 Figure 9. DPoS Algorithm Flowchart.
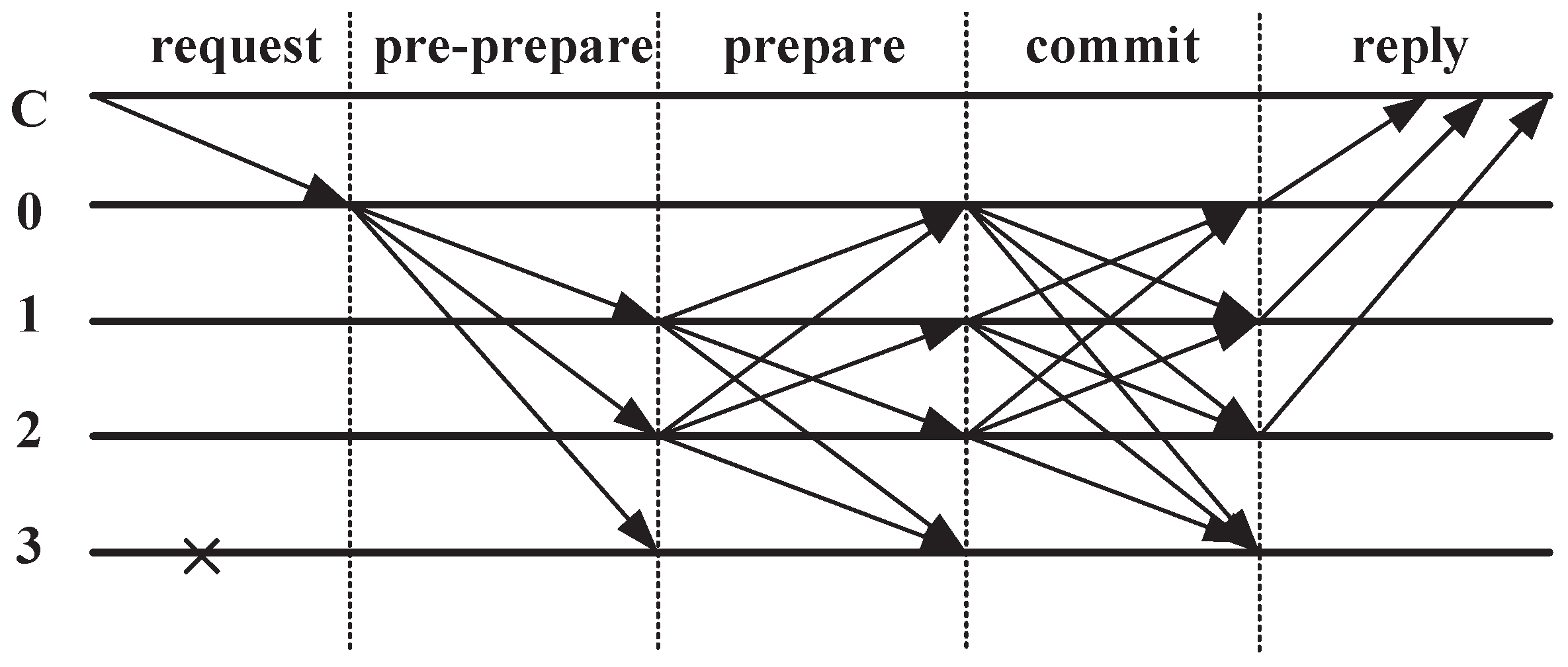
Figure 9. DPoS Algorithm Flowchart. - Practical Byzantine Fault Tolerance (PBFT)The Byzantine problem is a classic problem in distributed computing. The problem is described as follows. Suppose several Byzantine generals lead troops to surround a city. They must unanimously decide whether to launch a siege. If some generals decide to launch a siege without the participation of other generals, then their actions will end in failure. Generals are separated from each other by a certain distance, and they must rely on information transmission to communicate. Some cryptocurrency protocols use specific versions of BFT when reaching consensus, and each version has its own advantages and disadvantages.PBFT: The first proposed solution to this problem is called “practical Byzantine fault tolerance”, which has been adopted by Hyperledger Fabric. PBFT uses fewer pre-selected generals, so it runs very efficiently. Its advantage is high transaction flux and throughput, but its disadvantage is that it is centralized and used for licensing networks.Federated Byzantine agreement (FBA): The solution to another Byzantine general problem is FBA, which has been used by tokens such as Stellar and Ripple. The general idea of FBA is that every Byzantine general is responsible for his own chain, and once the news arrives, the chain establishes the facts through sorting. In Ripple, generals (verifiers) are pre-selected by Ripple Foundation. In Stellar, anyone can be a verifier, and users need to choose which verifier to trust. FBA can provide incredible throughput, low transaction overhead, and network scalability.PBFT is based on the Byzantine general problem, and the guarantee of consistency can be divided into three stages: pre-prepare, prepare, and commit, as shown in Figure 10.
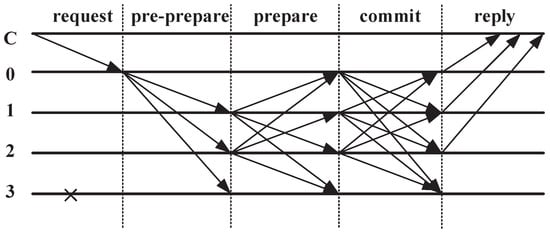 Figure 10. Byzantine Diagram.
Figure 10. Byzantine Diagram.
C is the client, 0, 1, 2 is the server, and 3 is the closed server. The specific steps of consensus algorithm are as follows:
- First, client C sends the request as the leader node.
- After receiving the request, the master node 0 assigns a sequence number to the request and broadcasts the sequence number to assign the message and the client request to all other slave nodes.
- After receiving the message from the master node, the slave node broadcasts the preparation message to other nodes.
- After each node verifies the received preparation message, they must broadcast the confirmation message, execute the request of the leader node, and then respond to the leader node.
- As long as the leader node receives an f+1 identical response, where f is the number of malicious nodes, it will consider that its request has been realized, and the PBFT consensus process is over.
3.4. Blockchain Solves the Problem of Anonymous Identity Authentication
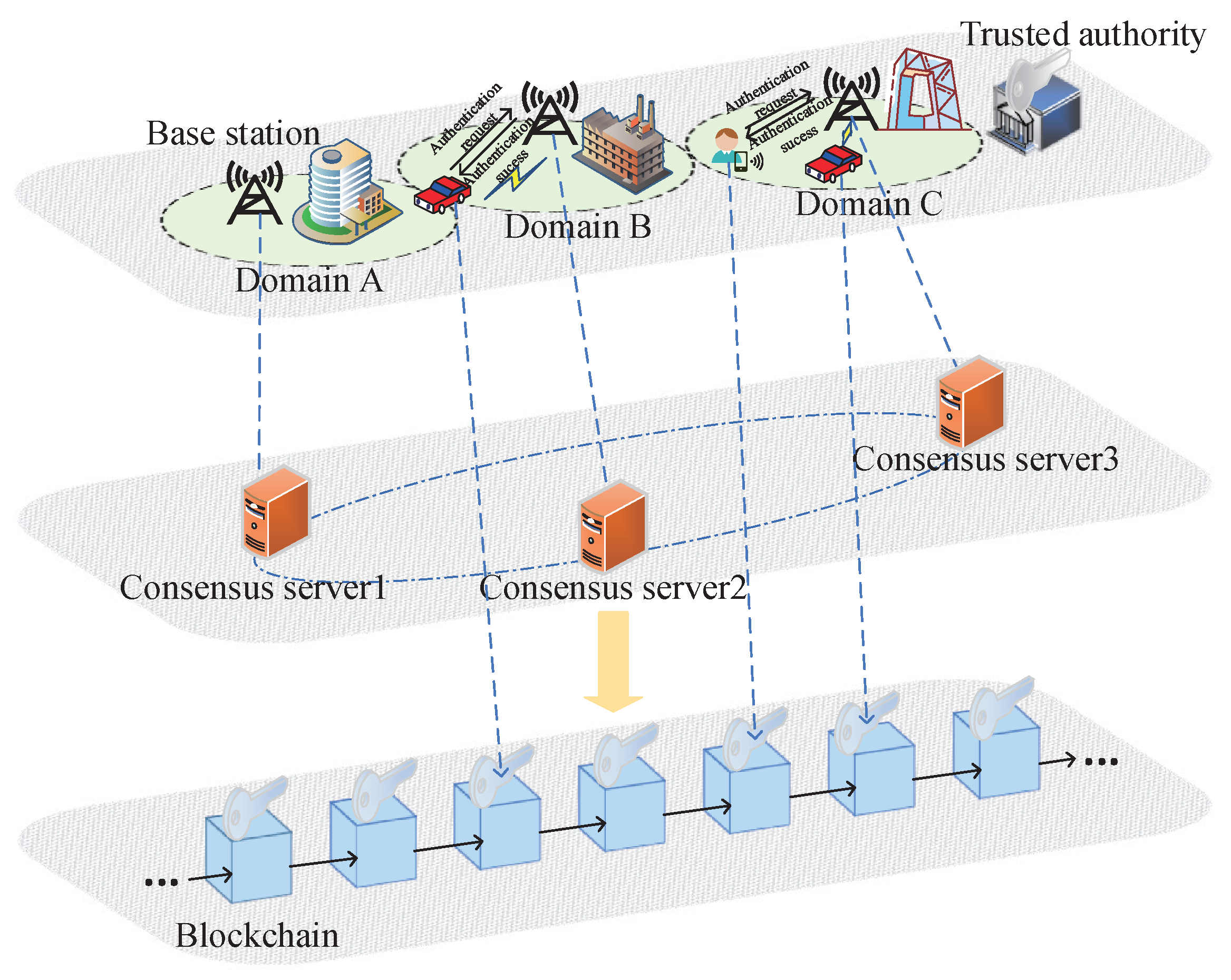
As shown in Figure 11, blockchain technology is applied to cross-domain anonymous authentication. The system divides the large area into several small areas, namely domain A, domain B, and domain C. Each area is managed by a base station, which is responsible for building a consistent blockchain network and storing part of the user’s authentication information. When users arrive at a new area, they need to change their pseudonyms for authentication with the base station [67,68], which uses the information stored in the blockchain and the information provided by the user to authenticate their identity. Chao et al. [69] proposed a blockchain-based security mutual authentication system, namely BSeIn. The system has integrated attribute signatures, multi-receiver encryption, and message authentication code, aiming to provide privacy and security guarantees. However, in attribute-based signature verification, some attributes can be obtained, which may affect the unlinkability. Liu et al. [70] recommended an anonymous identity authentication protocol based on blockchain using homomorphic encryption, but the unlinkability of this scheme cannot resist collusion. Only the service manager can decrypt the pseudonym due to the fact that the vehicle selects an unknown random number when generating the pseudonym. However, the scheme cannot achieve traceability and non-repudiation. Li et al. [71] presented a protocol for anonymous identity authentication between vehicles, realizing traceability and non-repudiation on the basis of [70]. Yao et al. [72] first proposed a non-interactive anonymous cross-data-center authentication mechanism in their vehicular ad-hoc network(VANET), realizing conditional privacy protection while the communication delay was significantly reduced.
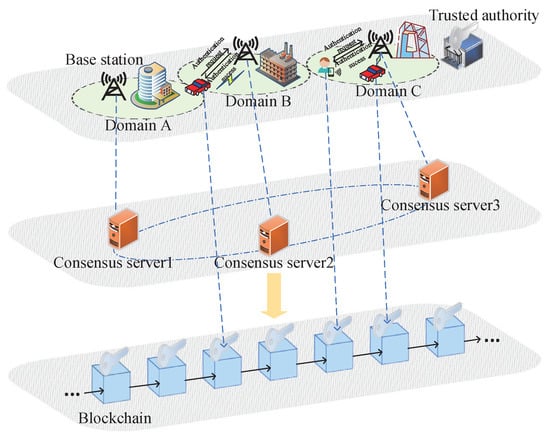
Figure 11.
Cross-Domain Anonymous Authentication System Model.
Feng et al. [73] adopted a novel blockchain-assisted privacy-preserving authentication system in VANET by combining blockchain features and access control encryption primitives. Blockchain is considered a mature database; thus, the registration center need not always be online. In [74], a permissioned consortium blockchain system with a smart contract was implemented in a vehicular network. The system ensures secure and conditional privacy-preserving vehicular pseudonym issuance. Smart contracts, an automatic computer protocol [75], are used in several stages, such as pseudonym revocation checks, pseudonym issuances, pseudonym revocations, and expired pseudonym deletions. Tomar et al. [76] introduced a blockchain-based certificateless authentication scheme. By adopting the PBFT consensus algorithm, the ledger keeps the partial private and public keys of vehicles in order to achieve cross-domain certification. They also designed a batch verification algorithm, which can significantly reduce the time and computation cost of multiple message signature verifications. Xue et al. [77] bestowed a scheme about roaming authentication by leveraging smart contracts. To further guarantee the unforgettable and undeniable nature of billing, they employed hash chain technology to prevent users from evading payment. Singh et al. [78] proposed a blockchain-based secure storage architecture for an intelligent IoV, namely BIIoVT. By applying blockchian and decentralized storage in the cloud, the security and privacy of vehicular networks can be guaranteed. Son et al. [79] provided a blockchain-based handover authentication protocol for VANETs. By adopting lightweight hash and XOR functions in the handover authentication phase, the protocol significantly improved efficiency and security. Pariyarath et al. [80] designed a blockchain-based privacy-preserving authentication protocol for secure communication in VANETs, which meets the requirements of higher scalability and lower fees. Subramani et al. [81] adopted fog computing architecture to design a blockchain-based anonymous authentication scheme, considering fog nodes as miners to authenticate vehicles’ identities. In the meanwhile, they also used a Merkle hash tree to ensure the real-time update of authentication data.
Compared with traditional cross-domain authentication schemes, blockchain-assisted cross-domain authentication can improve certification efficiency and resist distributed denial of service attacks. When one node fails, it may affect the entire network, resulting in the paralysis of the entire network. By applying blockchain techniques, the system can reach higher levels of stability and scalability. Typically, blockchain-assisted cross-domain authentication stores auxiliary authentication in the block by using consensus algorithms. There are a number of consensus algorithms, such as PoW, PoS, DPoS, Casper, PBFT, proof of elapsed time (PoET), and Raft [82]. Blockchain-assisted cross-domain authentication schemes utilize PBFT at most.
A comparison of consensus algorithms is shown in Table 2. “Capability” is a symbol of the ability of consensus algorithms to reach consensus. The “decentralization” is the degree of the decentralization of consensus algorithms. The “maximum evil nodes allowed” means the maximum rate of evil nodes that the consensus algorithms can tolerate, which is equal to dividing the maximum number of evil nodes by the total number of nodes in the blockchain. Here, “tokens” means that consensus algorithms have to use dedicated currency, such as Bitcoin. The “scenario” shows the consensus algorithms applied to different blockchains, including public blockchains, private blockchains and consortium blockchains. The “technical maturity” demonstrates the maturity of the consensus algorithm application. “Special hardware” suggests whether the consensus algorithm requires special hardware to run, which may affect the widespread use of the consensus algorithm.

Table 2.
Comparison of Consensus Algorithm.
In the practical application of IoT, the capability of the blockchain system is particularly important to the researchers, which is usually measured by transactions per second (TPS). In order to improve the capability of the blockchain system, consensus algorithms with high capability are usually adopted. PBFT consensus mechanisms meet this requirement. Decentralization is an important indicator of blockchain technology, representing the openness of blockchain and the difficulty of not being manipulated by people. The PoS, DPoS, and Casper consensus algorithms are completely decentralized, while the PBFT, PoET and Raft consensus algorithms are semi-decentralized. According to the different open levels of blockchain, blockchain can be roughly divided into three types: public blockchain, consortium blockchain, and private blockchain [83]. Public blockchains are fully open, and anyone can participate in it with no need to obtain permission from a central authority [84]. Consortium blockchains are semi-open and have certain access requirements. They are mainly introduced between specific organizations, and only member nodes can be involved in them. Private blockchains are closed, and only individuals or companies can join in. The consensus algorithms PoS, DPoS, and Casper are mainly aimed at public blockchains, while the consensus algorithms PBFT, PoET, and Raft are applied in consortium blockchains. In the distributed algorithm, the misbehavior of nodes always exist. Consensus is achieved when all distributed nodes update their ledgers and a consistent statement is made in a copy of the ledger [85]. The consensus algorithm needs to tolerate these errors and ensure the data consistency of blocks. The maximum number of malicious nodes that the PoS, DPoS, Casper, PoET, and Raft consensus algorithms can tolerate is 51% of the total number of nodes, yet the PBFT is 33% [86]. The token refers to the currency used for circulation in the blockchain ecosystem. PoS, DPoS and Casper rely on tokens, while others do not. At present, the PoS, DPoS, PBFT, and Raft consensus algorithms have become increasingly mature and widely used. However, the rest of the consensus algorithms are still in the process of development. In particular, the PoET consensus algorithm must use specific hardware despite its low cost. Therefore, it is extremely difficult to adopt it on a large scale.
In blockchain-assisted cross-domain authentication, the block generation time of PoS is usually around 10 min, which does not meet the low-delay requirement of the IoV. As a semi-decentralized consensus algorithm, PBFT has the ability to control node access in order to guarantee a more stable network. Moreover, PBFT does not need to deploy special hardware or use tokens in the authentication phase, which means it is easier to implement.
4. Research Prospects
Currently, there are some limiting factors in the fields of IoT authentication technology, trust management in VANETs, and privacy protection in VANETs. For example, in IoT authentication technology, there are various limitations in existing IoT authentication mechanisms, such as inefficiency, low security, and vulnerability to attacks. In the aspect of trust management in VANETs, there are various limitations in existing VANETs’ trust management mechanisms, such as low scalability, low robustness, and vulnerability to Sybil attacks and node compromise attacks. Additionally, the dynamic nature of VANETs makes it challenging to establish and maintain trust relationships [87,88,89]. In the aspect of privacy protection in VANETs, there are various limitations in existing VANETs’ privacy protection mechanisms, such as high computational complexity, low accuracy, and limited scalability. Moreover, many of these mechanisms are susceptible to attacks, such as side-channel attacks and data inference attacks. To address these limitations, we have read some interesting recent works and combined these directions with information security. We also focus on studying the combination of artificial intelligence technology and information security to seek new solutions [90,91,92,93].
Both Gupta and Mawla [94,95] proposed activity-based access control models aimed at providing more flexible and secure authorization and access control for collaborative information systems and IoT applications. We consider using an activity-centric access control model to authenticate IoT devices, ensuring that only authorized devices can access the system and data, or to provide fine-grained access control for IoT devices, allowing only specific devices to access specific resources or perform specific operations. At the same time, adversarial attacks, as a new type of threat [96,97], target malicious code detection methods, allowing malicious code to deceive detectors. Therefore, researching how to improve the robustness of malicious code detectors and defend against adversarial attacks is an important research direction in the field of information security. We note that IoT devices are vulnerable to various network attacks due to limited resources. Therefore, we consider using digital twin technology to simulate the behavior and communication of IoT devices and predict possible security risks [98,99]. Simulating and evaluating IoT devices can help design more secure IoT systems.
With the development of artificial intelligence(AI), we are also considering combining AI technology with information security. For IoT authentication technology, AI can be used to improve the security and efficiency of IoT authentication protocols. For example, deep learning technology can be used to identify the behavior patterns of IoT devices and automatically trigger alarms or take other security measures when abnormal situations are detected. In addition, AI-based algorithms can be used to evaluate the credibility and trustworthiness of IoT devices, making the authentication protocol more intelligent and adaptive. In terms of trust management in a connected car network, AI-based anomaly detection technology can monitor the behavior of vehicles in the network and detect potential attacks. When any unusual behavior is detected, appropriate measures such as disconnection or triggering an alarm can be taken. In terms of privacy protection in the connected car network, vehicle identification information and personal information can be shielded or replaced using data obfuscation techniques to protect the identity information of car owners and drivers. Additionally, differential privacy models can be used to protect data privacy, where adding noise makes it impossible to infer personal privacy information from the processed data, even if it is obtained by attackers.
In summary, the development and application of IoT identity authentication technology, VANET trust management, and privacy protection face various limitations and challenges. The integration of artificial intelligence technologies and information security can provide new solutions to enhance the security, efficiency, and trustworthiness of these mechanisms. However, the progress of AI technology also brings about new changes and challenges to the information security field. Therefore, there is still a long way to go in information security research and innovation, and it is crucial to continue to pay attention to new developments and explore novel solutions and approaches.
5. Conclusions
With the expansion of the application scope of IoT devices, authentication protocols have become one of the important research directions of IoT security. First of all, this paper summarizes the typical authentication system model, common technologies, challenges, and related technical requirements when designing a security authentication protocol. Secondly, this paper also proposes the security problems and total solutions of the IoT from the perspective of privacy protection. With the help of blockchain technology, this paper provides a security management model for the IoV, a dynamic trust assessment mechanism, and a trust management mechanism that meets the privacy protection requirements for vehicle nodes. The proposed solution in this paper can also quickly and effectively implement the nodes’ dynamic trust evaluation, screen out untrusted nodes, and solve the problem of behavior-trusted nodes’ untrusted messages. Finally, the proposed solution solves the privacy security problems in the process of trust evaluation and certificate management of vehicle nodes, and thereby, it improves the security level of the IoV management model.
Existing mechanisms for IoT identity authentication, VANET trust management, and privacy protection have various limitations and deficiencies, such as low efficiency, poor security, susceptibility to attacks, and forgery. In future research, we will consider combining artificial intelligence technology with the field of information security to seek new solutions. Specifically, deep learning techniques can be used to improve the security and efficiency of IoT identity authentication protocols, AI-based algorithms can be utilized to evaluate the trustworthiness and trust level of VANET trust relationships, and data obfuscation techniques and differential privacy models can be employed to protect the privacy of the VANET. However, the development of artificial intelligence technology will also bring about more challenges to the field of information security. Therefore, we need to continuously monitor the new trends in the field of information security to explore new solutions.
Author Contributions
Conceptualization, J.Z. and H.H.; methodology, H.H., F.H. and Y.G.; validation, J.Z., H.H. and Y.G.; formal analysis, J.Z., H.H. and F.H.; investigation, J.Z.; resources, J.Z. and L.L.; data curation, H.H. and F.H.; writing—original draft preparation, H.H., F.H. and Y.G.; writing—review and editing, J.Z. and L.L.; visualization, H.H., F.H. and Y.G.; supervision, J.Z.; project administration, J.Z.; funding acquisition, J.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundation of China (U2001213 and 61971191), in part by the Beijing Natural Science Foundation under Grant L201011, in part by the National Key Research and Development Project (2020YFB1807204), in part by the Key project of Natural Science Foundation of Jiangxi Province (20202ACBL202006), in part by the Jiangxi Key Laboratory of Artificial Intelligence Transportation Information Transmission and Processing (20202BCD42010), and in part by the Jiangxi Provincial Natural Science Foundation (20212BAB212001).
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zhao, J.; Liu, J.; Yang, L.; Ai, B.; Shanjin, N. Future 5G-oriented system for urban rail transit: Opportunities and challenges. China Commun. 2021, 18, 1–12. [Google Scholar] [CrossRef]
- Zhao, J.; Sun, X.; Ma, X.; Zhang, H.; Yu, F.R.; Hu, Y. Online Distributed Optimization for Energy-Efficient Computation Offloading in Air-Ground Integrated Networks. IEEE Trans. Veh. Technol. 2022, 1–14. [Google Scholar] [CrossRef]
- Guerbouj, S.S.E.; Gharsellaoui, H.; Bouamama, S. A comprehensive survey on privacy and security issues in cloud computing, internet of things and cloud of things. Int. J. Serv. Sci. Manag. Eng. Technol. (IJSSMET) 2019, 10, 32–44. [Google Scholar]
- Sahmim, S.; Gharsellaoui, H. Privacy and security in internet-based computing: Cloud computing, internet of things, cloud of things: A review. Procedia Comput. Sci. 2017, 112, 1516–1522. [Google Scholar] [CrossRef]
- Naveen, S.; Kounte, M.R. Key Technologies and challenges in IoT Edge Computing. In Proceedings of the 2019 Third International conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 12–14 December 2019; pp. 61–65. [Google Scholar]
- Othman, M.M.; El-Mousa, A. Internet of things & cloud computing internet of things as a service approach. In Proceedings of the 2020 11th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 7–9 April 2020; pp. 318–323. [Google Scholar]
- Khapre, S.P.; Satpathy, S.P.; Chandramohan, D. Optimization of Consensus Mechanism for IoT Blockchain: A Survey. In Research Anthology on Convergence of Blockchain, Internet of Things, and Security; IGI Global: Hershey, PA, USA, 2023; pp. 931–959. [Google Scholar]
- Zhang, H.; Liu, J.; Zhao, H.; Wang, P.; Kato, N. Blockchain-based trust management for internet of vehicles. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1397–1409. [Google Scholar]
- Zhao, J.; Ni, S.; Yang, L.; Zhang, Z.; Gong, Y.; You, X. Multiband Cooperation for 5G HetNets: A Promising Network Paradigm. IEEE Veh. Technol. Mag. 2019, 14, 85–93. [Google Scholar] [CrossRef]
- Pu, C. A novel blockchain-based trust management scheme for vehicular networks. In Proceedings of the 2021 Wireless Telecommunications Symposium (WTS), Virtual, CA, USA, 21–23 April 2021; pp. 1–6. [Google Scholar]
- Zhao, J.; Wu, Y.; Zhang, Q.; Liao, J. Two-Stage Channel Estimation for mmWave Massive MIMO Systems Based on ResNet-UNet. IEEE Syst. J. 2023, 1–10. [Google Scholar] [CrossRef]
- Gong-Guo, Z.; Wan, Z. Blockchain-based IoT security authentication system. In Proceedings of the 2021 International Conference on Computer, Blockchain and Financial Development (CBFD), Nanjing, China, 23–25 April 2021; pp. 415–418. [Google Scholar]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Deogirikar, J.; Vidhate, A. Security attacks in IoT: A survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)(I-SMAC), Palladam, India, 10–11 February 2017; pp. 32–37. [Google Scholar]
- Black, S.; Kim, Y. An Overview on Detection and Prevention of Application Layer DDoS Attacks. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022; pp. 791–800. [Google Scholar]
- Cao, J.; Yan, Z.; Ma, R.; Zhang, Y.; Fu, Y.; Li, H. LSAA: A Lightweight and Secure Access Authentication Scheme for Both UE and mMTC Devices in 5G Networks. IEEE Internet Things J. 2020, 7, 5329–5344. [Google Scholar] [CrossRef]
- Miloslavskaya, N.; Tolstoy, A. Internet of Things: Information security challenges and solutions. Clust. Comput. 2019, 22, 103–119. [Google Scholar] [CrossRef]
- Djenna, A.; Harous, S.; Saidouni, D.E. Internet of things meet internet of threats: New concern cyber security issues of critical cyber infrastructure. Appl. Sci. 2021, 11, 4580. [Google Scholar] [CrossRef]
- Alrubaiei, M.H.; Al-Saadi, M.H.; Shaker, H.; Sharef, B.; Khan, S. Internet of Things in Cyber Security Scope. In Blockchain Technology and Computational Excellence for Society 5.0; IGI Global: Hershey, PA, USA, 2022; pp. 146–187. [Google Scholar]
- Li, B.; Liang, R.; Zhu, D.; Chen, W.; Lin, Q. Blockchain-Based Trust Management Model for Location Privacy Preserving in VANET. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3765–3775. [Google Scholar] [CrossRef]
- Boualouache, A.; Senouci, S.M.; Moussaoui, S. A Survey on Pseudonym Changing Strategies for Vehicular Ad-Hoc Networks. IEEE Commun. Surv. Tutor. 2018, 20, 770–790. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J.P.; Ning, P.; Du, W. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Artail, H.; Abbani, N. A Pseudonym Management System to Achieve Anonymity in Vehicular Ad Hoc Networks. IEEE Trans. Dependable Secur. Comput. 2016, 13, 106–119. [Google Scholar] [CrossRef]
- Boualouache, A.; Moussaoui, S. S2si: A practical pseudonym changing strategy for location privacy in vanets. In Proceedings of the 2014 International Conference on Advanced Networking Distributed Systems and Applications, Bejaia, Algeria, 17–19 June 2014; pp. 70–75. [Google Scholar]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A privacy-preserving and provable user authentication scheme for wireless sensor networks based on Internet of Things security. J. Ambient Intell. Humaniz. Comput. 2017, 8, 101–116. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Wei, F.; Tian, Y.; Shen, J.; Yang, Y. An untraceable temporal-credential-based two-factor authentication scheme using ECC for wireless sensor networks. J. Netw. Comput. Appl. 2016, 76, 37–48. [Google Scholar] [CrossRef]
- Arafin, M.T. Hardware-Based Authentication for the Internet of Things. Ph.D. Thesis, University of Maryland, College Park, MD, USA, 2018. [Google Scholar]
- Vaidya, B.; Makrakis, D.; Mouftah, H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2016, 9, 171–183. [Google Scholar] [CrossRef]
- Hu, H.; Liao, L.; Zhao, J. Secure Authentication and Key Agreement Protocol for Cloud-Assisted Industrial Internet of Things. Electronics 2022, 11, 1652. [Google Scholar] [CrossRef]
- Mishra, D.; Vijayakumar, P.; Sureshkumar, V.; Amin, R.; Islam, S.H.; Gope, P. Efficient authentication protocol for secure multimedia communications in IoT-enabled wireless sensor networks. Multimed. Tools Appl. 2018, 77, 18295–18325. [Google Scholar] [CrossRef]
- Chang, I.P.; Lee, T.F.; Lin, T.H.; Liu, C.M. Enhanced two-factor authentication and key agreement using dynamic identities in wireless sensor networks. Sensors 2015, 15, 29841–29854. [Google Scholar] [CrossRef] [PubMed]
- Dolev, D.; Yao, A.C. On the security of public key protocols. Inf. Theory IEEE Trans. 1981, 29, 198–208. [Google Scholar] [CrossRef]
- Xue, K.; Meng, W.; Li, S.; Wei, D.S.; Zhou, H.; Yu, N. A secure and efficient access and handover authentication protocol for Internet of Things in space information networks. IEEE Internet Things J. 2019, 6, 5485–5499. [Google Scholar] [CrossRef]
- El-Meniawy, N.; Rizk, M.R.; Ahmed, M.A.; Saleh, M. An Authentication Protocol for the Medical Internet of Things. Symmetry 2022, 14, 1483. [Google Scholar] [CrossRef]
- Tewari, A.; Gupta, B.B. A novel ECC-based lightweight authentication protocol for internet of things devices. Int. J. High Perform. Comput. Netw. 2019, 15, 106–120. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J. Cloud centric authentication for wearable healthcare monitoring system. IEEE Trans. Dependable Secur. Comput. 2018, 17, 942–956. [Google Scholar] [CrossRef]
- Gupta, M.; Gupta, K.K.; Shukla, P.K. Session key based novel lightweight image encryption algorithm using a hybrid of Chebyshev chaotic map and crossover. Multimed. Tools Appl. 2021, 80, 33843–33863. [Google Scholar] [CrossRef]
- Liu, L.; Jiang, D.; Wang, X.; Rong, X.; Zhang, R. 2D Logistic-Adjusted-Chebyshev map for visual color image encryption. J. Inf. Secur. Appl. 2021, 60, 102854. [Google Scholar] [CrossRef]
- Sun, J.; Zhao, G.; Li, X. An improved public key encryption algorithm based on Chebyshev polynomials. Indones. J. Electr. Eng. Comput. Sci. 2013, 11, 864–870. [Google Scholar] [CrossRef]
- Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 2008, 37, 669–674. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N. Anonymous lightweight chaotic map-based authenticated key agreement protocol for industrial Internet of Things. IEEE Trans. Dependable Secur. Comput. 2018, 17, 1133–1146. [Google Scholar] [CrossRef]
- Sarkar, A.; Singh, B.K. A review on performance, security and various biometric template protection schemes for biometric authentication systems. Multimed. Tools Appl. 2020, 79, 27721–27776. [Google Scholar] [CrossRef]
- Rui, Z.; Yan, Z. A survey on biometric authentication: Toward secure and privacy-preserving identification. IEEE Access 2018, 7, 5994–6009. [Google Scholar] [CrossRef]
- Griffin, P.H. Secure authentication on the Internet of Things. In Proceedings of the SoutheastCon 2017, Concord, NC, USA, 30 March–2 April 2017; pp. 1–5. [Google Scholar]
- Mayron, L.M. Biometric authentication on mobile devices. IEEE Secur. Priv. 2015, 13, 70–73. [Google Scholar] [CrossRef]
- Neal, T.J.; Woodard, D.L. Surveying biometric authentication for mobile device security. J. Pattern Recognit. Res. 2016, 11, 74–110. [Google Scholar] [CrossRef]
- Bureva, V.; Sotirova, E.; Bozov, H. Generalized Net Model of Biometric Identification Process. In Proceedings of the 2018 20th International Symposium on Electrical Apparatus and Technologies (SIELA), Bourgas, Bulgaria, 3–6 June 2018; pp. 1–4. [Google Scholar]
- Dharma Putra, G.; Kang, C.; Kanhere, S.S.; Won-Ki Hong, J. DeTRM: Decentralised Trust and Reputation Management for Blockchain-based Supply Chains. In Proceedings of the 2022 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Shanghai, China, 2–5 May 2022; pp. 1–5. [Google Scholar]
- Song, Y.; Sun, C.; Peng, Y.; Zeng, Y.; Sun, B. Research on Multidimensional Trust Evaluation Mechanism of FinTech Based on Blockchain. IEEE Access 2022, 10, 57025–57036. [Google Scholar] [CrossRef]
- Jeribi, F.; Amin, R.; Alhameed, M.; Tahir, A. An Efficient Trust Management Technique Using ID3 Algorithm With Blockchain in Smart Buildings IoT. IEEE Access 2023, 11, 8136–8149. [Google Scholar] [CrossRef]
- Sun, R.; Zhang, G.; Tang, H. Trust Based lot Access Control Using Blockchain. In Proceedings of the 2022 IEEE International Conference on Sensing, Diagnostics, Prognostics, and Control (SDPC), Chongqing, China, 5–7 August 2022; pp. 240–245. [Google Scholar]
- Pal, S.; Hill, A.; Rabehaja, T.; Hitchens, M. VeriBlock: A Blockchain-Based Verifiable Trust Management Architecture with Provable Interactions. In Proceedings of the 2022 International Conference on Computer Communications and Networks (ICCCN), Virtual, 25–27 July 2022; pp. 1–7. [Google Scholar]
- Goh, Y.; Yun, J.; Jung, D.; Chung, J.M. Secure Trust Based Delegated Consensus for Blockchain Frameworks Using Deep Reinforcement Learning. IEEE Access 2022, 10, 118498–118511. [Google Scholar] [CrossRef]
- Wang, X.; Garg, S.; Lin, H.; Kaddoum, G.; Hu, J.; Hassan, M.M. Heterogeneous Blockchain and AI-Driven Hierarchical Trust Evaluation for 5G-Enabled Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2074–2083. [Google Scholar] [CrossRef]
- Ye, J.; Kang, X.; Liang, Y.C.; Sun, S. A Trust-Centric Privacy-Preserving Blockchain for Dynamic Spectrum Management in IoT Networks. IEEE Internet Things J. 2022, 9, 13263–13278. [Google Scholar] [CrossRef]
- Tangade, S.S.; Manvi, S.S. A survey on attacks, security and trust management solutions in VANETs. In Proceedings of the 2013 Fourth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Tiruchengode, India, 4–6 July 2013; pp. 1–6. [Google Scholar]
- Rivera, J.J.D.; Khan, T.A.; Akbar, W.; Muhammad, A.; Song, W.C. ZT&T: Secure blockchain-based tokens for service session management in Zero Trust Networks. In Proceedings of the 2022 6th Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 24–26 October 2022; pp. 1–7. [Google Scholar]
- El-Sayed, H.; Alexander, H.; Kulkarni, P.; Khan, M.A.; Noor, R.M.; Trabelsi, Z. A Novel Multifaceted Trust Management Framework for Vehicular Networks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 20084–20097. [Google Scholar] [CrossRef]
- Jiao, Y.; Wang, C. A Blockchain-Based Trusted Upload Scheme for the Internet of Things Nodes. Int. J. Crowd Sci. 2022, 6, 92–97. [Google Scholar] [CrossRef]
- Liu, X.; Huang, H.; Xiao, F.; Ma, Z. A Blockchain-Based Trust Management With Conditional Privacy-Preserving Announcement Scheme for VANETs. IEEE Internet Things J. 2020, 7, 4101–4112. [Google Scholar] [CrossRef]
- Elmadani, S.; Hariri, S.; Shao, S. Blockchain Based Methodology for Zero Trust Modeling and Quantification for 5G Networks. In Proceedings of the 2022 IEEE/ACS 19th International Conference on Computer Systems and Applications (AICCSA), Abu Dhabi, United Arab Emirates, 5–8 December 2022; pp. 1–9. [Google Scholar]
- Chen, X.; Ding, J.; Lu, Z. A Decentralized Trust Management System for Intelligent Transportation Environments. IEEE Trans. Intell. Transp. Syst. 2022, 23, 558–571. [Google Scholar] [CrossRef]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- Zhao, J.; Sun, X.; Li, Q.; Ma, X. Edge Caching and Computation Management for Real-Time Internet of Vehicles: An Online and Distributed Approach. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2183–2197. [Google Scholar] [CrossRef]
- Zhao, W. Consensus Algorithms for Blockchain. In From Traditional Fault Tolerance to Blockchain; Wiley: Hoboken, NJ, USA, 2021. [Google Scholar]
- Hang, L.; Chen, C.; Zhang, L.; Yang, J. Blockchain for applications of clinical trials: Taxonomy, challenges, and future directions. IET Commun. 2022, 16, 2371–2393. [Google Scholar] [CrossRef]
- Zhao, J.; Yang, L.; Xia, M.; Motani, M. Unified Analysis of Coordinated Multipoint Transmissions in mmWave Cellular Networks. IEEE Internet Things J. 2022, 9, 12166–12180. [Google Scholar] [CrossRef]
- Ding, X.; Wang, X.; Xie, Y.; Li, F. A Lightweight Anonymous Authentication Protocol for Resource-Constrained Devices in Internet of Things. IEEE Internet Things J. 2022, 9, 1818–1829. [Google Scholar] [CrossRef]
- Chao, L.; He, D.; Huang, X.; Choo, K.; Vasilakos, A.V. BSeIn: A blockchain-based secure mutual authentication with fine-grained access control system for industry 4.0. J. Netw. Comput. Appl. 2018, 116, 42–52. [Google Scholar]
- Liu, J.; Li, X.; Jiang, Q.; Obaidat, M.S.; Vijayakumar, P. BUA: A blockchain-based unlinkable authentication in vanets. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Li, X.; Liu, J.; Obaidat, M.S.; Vijayakumar, P.; Jiang, Q.; Amin, R. An unlinkable authenticated key agreement with collusion resistant for VANETs. IEEE Trans. Veh. Technol. 2021, 70, 7992–8006. [Google Scholar] [CrossRef]
- Yao, Y.; Chang, X.; Mišić, J.; Mišić, V.B.; Li, L. BLA: Blockchain-Assisted Lightweight Anonymous Authentication for Distributed Vehicular Fog Services. IEEE Internet Things J. 2019, 6, 3775–3784. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Liang, K. BPAS: Blockchain-assisted privacy-preserving authentication system for vehicular ad hoc networks. IEEE Trans. Ind. Inform. 2019, 16, 4146–4155. [Google Scholar] [CrossRef]
- Chulerttiyawong, D.; Jamalipour, A. A blockchain assisted vehicular pseudonym issuance and management system for conditional privacy enhancement. IEEE Access 2021, 9, 127305–127319. [Google Scholar] [CrossRef]
- Ma, Z.; Zhang, J.; Guo, Y.; Liu, Y.; Liu, X.; He, W. An efficient decentralized key management mechanism for VANET with blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5836–5849. [Google Scholar] [CrossRef]
- Tomar, A.; Tripathi, S. BCAV: Blockchain-based certificateless authentication system for vehicular network. Peer- Netw. Appl. 2022, 15, 1733–1756. [Google Scholar] [CrossRef]
- Xue, K.; Luo, X.; Ma, Y.; Li, J.; Liu, J.; Wei, D.S. A distributed authentication scheme based on smart contract for roaming service in mobile vehicular networks. IEEE Trans. Veh. Technol. 2022, 71, 5284–5297. [Google Scholar] [CrossRef]
- Singh, S.K.; Park, J.H.; Sharma, P.K.; Pan, Y. BIIoVT: Blockchain-based secure storage architecture for intelligent internet of vehicular things. IEEE Consum. Electron. Mag. 2021, 11, 75–82. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Pariyarath, A.; Tomar, S.; Tripathi, M. Efficient Privacy-Preserving Authentication using Blockchain for VANET. In Proceedings of the 2023 15th International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 3–8 January 2023; pp. 423–426. [Google Scholar]
- Subramani, J.; Maria, A.; Rajasekaran, A.S.; Al-Turjman, F.; Gopal, M. Blockchain-based Physically Secure and Privacy-Aware Anonymous Authentication Scheme for Fog-based VANETs. IEEE Access 2023, 11, 17138–17150. [Google Scholar] [CrossRef]
- Chen, Z.; Chen, S.; Xu, H.; Hu, B. A Security Authentication Scheme of 5G Ultra-Dense Network Based on Block Chain. IEEE Access 2018, 6, 55372–55379. [Google Scholar] [CrossRef]
- Tandon, R.; Verma, A.; Gupta, P. Blockchain enabled vehicular networks: A review. In Proceedings of the 2022 5th International Conference on Multimedia, Signal Processing and Communication Technologies (IMPACT), Aligarh, India, 26–27 November 2022; pp. 1–6. [Google Scholar]
- Shrestha, R.; Bajracharya, R.; Shrestha, A.P.; Nam, S.Y. A new type of blockchain for secure message exchange in VANET. Digit. Commun. Netw. 2020, 6, 177–186. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, X. Data security sharing and storage based on a consortium blockchain in a vehicular ad-hoc network. IEEE Access 2019, 7, 58241–58254. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, N.; Lou, W.; Hou, Y.T. A survey of distributed consensus protocols for blockchain networks. IEEE Commun. Surv. Tutor. 2020, 22, 1432–1465. [Google Scholar] [CrossRef]
- Singh, S.K.; Park, J.H. TaLWaR: Blockchain-Based Trust Management Scheme for Smart Enterprises With Augmented Intelligence. IEEE Trans. Ind. Inform. 2023, 19, 626–634. [Google Scholar] [CrossRef]
- Lai, R.; Zhao, G. ValidatorRep: Blockchain-based Trust Management for Ensuring Accountability in Crowdsourcing. In Proceedings of the 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 27 June–1 July 2022; pp. 716–725. [Google Scholar]
- Yu, J.; Zhang, G.; Lu, D.; Liu, H. Blockchain-based Crowd-sensing Trust Management Mechanism for Crowd Evacuation. In Proceedings of the 2022 IEEE 25th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Hangzhou, China, 4–6 May 2022; pp. 1179–1184. [Google Scholar]
- Yang, T.; Zhang, G.; Liu, L.; Yang, Y.; Zhao, S.; Sun, H.; Wang, W. New Features of Authentication Scheme for the IoT: A Survey. In Proceedings of the 2nd International ACM Workshop on Security and Privacy for the Internet-Of-Things (IOT S&P’19), London, UK, 15 November 2019; pp. 44–49. [Google Scholar]
- Azrour, M.; Mabrouki, J.; Guezzaz, A.; Farhaoui, Y. New enhanced authentication protocol for internet of things. Big Data Min. Anal. 2021, 4, 1–9. [Google Scholar] [CrossRef]
- Wei, F.; Vijayakumar, P.; Kumar, N.; Zhang, R.; Cheng, Q. Privacy-preserving implicit authentication protocol using cosine similarity for Internet of Things. IEEE Internet Things J. 2020, 8, 5599–5606. [Google Scholar] [CrossRef]
- Chikouche, N.; Cayrel, P.L.; Mboup, E.H.M.; Boidje, B.O. A privacy-preserving code-based authentication protocol for Internet of Things. J. Supercomput. 2019, 75, 8231–8261. [Google Scholar] [CrossRef]
- Gupta, M.; Sandhu, R. Towards activity-centric access control for smart collaborative ecosystems. In Proceedings of the 26th ACM Symposium on Access Control Models and Technologies, Virtual Event, Spain, 16–18 June 2021; pp. 155–164. [Google Scholar]
- Mawla, T.; Gupta, M.; Sandhu, R. BlueSky: Activity Control: A Vision for “Active” Security Models for Smart Collaborative Systems. In Proceedings of the 27th ACM on Symposium on Access Control Models and Technologies, New York, NY, USA, 8–10 June 2022; pp. 207–216. [Google Scholar]
- Grosse, K.; Papernot, N.; Manoharan, P.; Backes, M.; McDaniel, P. Adversarial examples for malware detection. In Proceedings of the Computer Security–ESORICS 2017: 22nd European Symposium on Research in Computer Security, Oslo, Norway, 11–15 September 2017; pp. 62–79. [Google Scholar]
- Aryal, K.; Gupta, M.; Abdelsalam, M. A survey on adversarial attacks for malware analysis. arXiv 2021, arXiv:2111.08223. [Google Scholar]
- Cathey, G.; Benson, J.; Gupta, M.; Sandhu, R. Edge centric secure data sharing with digital twins in smart ecosystems. In Proceedings of the 2021 Third IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 13–15 December 2021; pp. 70–79. [Google Scholar]
- Zhao, J.; Nie, Y.; Zhang, H.; Yu, F.R. A UAV-aided vehicular integrated platooning network for heterogeneous resource management. IEEE Trans. Green Commun. Netw. 2023, 7, 512–521. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).