Abstract
A large amount of high-value data are stored in smart grid data centers, but since the resource diversity of a single data center is limited, data sharing becomes especially important in conducting an effective data mining process. However, traditional data-sharing models often use centralized schemes without authentication of the shared objects, making it difficult to establish trust relationships and ensure data privacy. This makes it difficult to break through the problem of data islands. To solve the above problems, this paper proposes a blockchain-based data-sharing incentive model for edge smart grid scenarios. First, the model uses blockchain and proxy re-encryption technology to achieve the security and traceability of the smart grid data-sharing process. Secondly, the data-sharing incentive algorithm is designed using game theory to maximize the willingness of data owners to share data. Finally, the model in this paper is compared and analyzed with other existing data-sharing models, and the designed performance test shows that the scheme in this paper has significant advantages over the other literature schemes in terms of functionality and computational overhead, and the increase in costs is not significant, and the model can meet the requirements for large-scale data sharing in edge smart grid scenarios.
1. Introduction
At present, smart grid, new power equipment, and electric power information systems are in a rapid development stage, but there are still great deficiencies in the security management of smart grid data. First, the source of smart grid data are complex, and the data structure is quite different [1]. For example, the smart grid includes a data acquisition and monitoring control system (SCADA), power production system (PPS), power dispatching system (PMS), and other independent smart grid data management systems that cover a series of processes of power transmission, transformation, distribution and sales of power grid enterprises [2,3,4]. In the face of these heterogeneous data from a wide range of sources, differentiated management is required. Secondly, the rapid development of big data applications has created increasingly high requirements for data sharing and transmission and poses more challenges to data security [5]. The above smart grid data management systems are used to collect and process various kinds of power data, which has high research value. However, these systems are developed and applied at different times, and they are in a relatively independent state in the operation. How to share data and information safely and traceably while protecting data privacy has become a current research hotspot. Finally, traditional data-sharing solutions focus on third-party organizations and face problems such as the untraceable authenticity of data sources, the opaque flow of data sharing, and easy disclosure or tampering of data. The above problems lead to extremely difficult data sharing within the power grid enterprises, forming the “information island” phenomenon of power data, which is not conducive to optimizing the power grid operation state and mining the potential value of data [6]. How to address these problems is the key challenge in designing the data-sharing system.
The emergence of blockchain technology provides a new solution for the safe sharing of smart grid data [7]. In essence, blockchain is a distributed database. First of all, the tamper-proof feature of the data on the blockchain ensures the transparency of the data-sharing process so that users can clearly know the sharing and transmission process of all data, which eliminates the possibility of illegal use of data [8]. Secondly, the combination of blockchain and proxy re-encryption (PRE) technology can achieve secure data sharing [9]. Finally, the incentive mechanism for data sharing is written into the blockchain smart contract, which can use the nature of automatic execution of the smart contract to standardize the entire process of data sharing and incentive [10]. Through the above description, building a smart grid data-sharing incentive platform based on the blockchain can effectively expand the scale of data management and standardize the process of data management.
In the traditional proxy re-encryption scheme, the proxy server has strong authority to convert ciphertext [11]. As long as the data holder generates the corresponding conversion key, the proxy server can convert all ciphertext uploaded by the data owner or even conspire to share data with other users. At the same time, the traditional proxy re-encryption scheme does not support the sharing of ciphertext data fineness [12], which is difficult to adapt to the needs of specific users. Therefore, the literature proposed a conditional proxy re-encryption to solve the above problem [13]. Specifically, a conditional parameter is embedded in the ciphertext and re-encrypted key to limit the proxy server’s ability to convert ciphertext. For the data holder, it can effectively resist the collusion attacks launched by the proxy server and other users, and the data sharing parties can embed different conditional parameters in the conversion key to achieve the designated sharing of ciphertext.
Therefore, we propose an identity-based proxy re-encryption-based smart grid data sharing scheme to overcome the security and privacy protection challenges in traditional smart grid data sharing schemes. By using identity information as a public key, generating private keys for users using a private key generator, and embedding conditional parameters in the ciphertext and re-encryption keys, this scheme enables fine-grained control over the data-sharing process, thereby enhancing the security and traceability of data-sharing. In addition, this scheme can effectively reduce the cost and improve the efficiency of data sharing, which is of great significance for the sharing and processing of large amounts of data in smart grids. Specifically, the contribution of the article is described below:
- (1)
- An innovative identity-based conditional proxy re-encryption scheme is adopted to simplify certificate management in PRE. This scheme treats identity information as a public key, eliminating the need for additional public key infrastructure.
- (2)
- Introduced a private key generator for identity verification, generating private keys for users and ensuring key security, avoiding reliance on traditional public key infrastructure.
- (3)
- Embedding a conditional parameter in the ciphertext and re-encryption key limits the proxy server’s ability to convert ciphertexts. Data-sharing parties can embed different conditional parameters in the conversion key to achieve specified shared ciphertexts, thereby supporting data granularity sharing.
- (4)
- Transfer part of the decryption cost to the user while proposing methods to reduce security risks and improve checkability. This scheme significantly reduces the cost of message initiators in the case of group member changes (i.e., condition value changes).
2. Related Works
2.1. Blockchain Technology in Secure Data Sharing
The decentralization, immutability, and transparency of blockchain technology ensure the security, reliability, and trustworthiness of data. Its application has gradually gained attention in the field of data security sharing, providing new ideas and methods for solving security and privacy issues in data sharing. Wang et al. [14] proposed a data security sharing network system using blockchain technology, but it adopts a centralized storage method with low storage efficiency. Li et al. [15] proposed a blockchain-based education record security storage and sharing scheme, which adopts a strict access mechanism for nodes, and smart contracts are used to regulate the data-sharing process between nodes. However, its off-chain storage still relies on centralized databases. The centralized data-sharing model often consumes a lot of communication overhead and computational cost, and its security basically depends on whether the central database complies with the agreement. Therefore, centralized data sharing is not suitable for a smart grid, and distributed data sharing based on blockchain is obviously a better choice.
Sun et al. [16] proposed a distributed data-sharing system for IoT based on blockchain, using distributed machine learning methods to classify and process different types of data, which reduces network complexity and improves system scalability. Wu et al. [17] proposed a secure storage and sharing system for smart grid data based on the federated chain, which realized the effective and secure storage of smart grid data, but there were efficiency problems caused by block “bloat” and data redundancy.
In the above scheme, repeated encryption of data are required whenever the access rights of blockchain transaction data change, which may increase the overhead and complexity of the system. Therefore, there is a need to explore and investigate further how to combine blockchain technology with more efficient encryption techniques to optimize the performance and security of data-sharing systems.
2.2. Proxy Re-Encryption Techniques in Data Sharing
In traditional encryption schemes [17], if the data owner wants to share encrypted data with other users, they need to inform the receiver of the decryption key. However, this approach poses security risks, as the receiver may abuse the decryption key or leak it to unauthorized users. Proxy re-encryption is a technique that allows a trusted third party (proxy) to re-encrypt encrypted data without decrypting the original data. This technique can be used to implement more fine-grained data access control and stronger data protection.
2.2.1. Proxy Re-Encryption
Proxy re-encryption (PRE) [18] is a public key encryption scheme. Data holder A entrusts data decryption capability to data requester B and re-encrypts the ciphertext according to the public key of data holder A in a semi-trusted proxy environment. Data requester B can use its private key to decrypt the re-encrypted ciphertext.
Proxy re-encryption has been favored by many scholars since it was proposed, and many improved schemes have been applied to data sharing. Lin et al. [18] proposed an outsourcing-oriented proxy re-encryption scheme for IoT cloud data security, which supports a bi-directional multi-hop function, the ciphertext length is independent of the number of IoT nodes, and the re-encryption process only requires one exponential calculation, which greatly saves the computational overhead. Gao et al. [19] proposed a blockchain-based IIoT data security sharing scheme in a pervasive edge computing environment, combined with an identity-based agent re-encryption scheme and designed a series of smart contracts to achieve secure data sharing among devices in an edge computing environment, and used blockchain to solve the problem of centralized SDN networks and suffering from a single point of attack.
2.2.2. Identity-Based Proxy Re-Encryption
Identity-based proxy re-encryption (IBPRE) [20] is an improvement on the PRE scheme. Data holder A takes the identity information as the public key, and no additional public key infrastructure is required. In this process, data holder A only needs to encrypt the data once to obtain the ciphertext. Later, whenever someone requests A’s data, A only needs to send the ciphertext and re-encryption key to the proxy server to perform the re-encryption step. Data holder A no longer needs to download and decrypt the ciphertext, which simplifies the data-sharing process.
Green et al. [20] introduced identity-based encryption (IBE) into proxy re-encryption and designed the first identity-based proxy re-encryption scheme, in which users en-crypt data using identity information, and the proxy transforms the ciphertext encrypted by the data holder’s identity information into the ciphertext encrypted by the data user’s identity information, which greatly simplifies the system structure. Shao et al. [21] proposed a conditional proxy re-encryption scheme that embeds a conditional parameter in the ciphertext and re-encryption key to limit the ciphertext conversion capability of the proxy server, which is effective for the data holder to resist collusion attacks launched by the proxy server and other users, and the data sharing parties can embed different conditional parameters in the conversion key to achieve specified sharing of ciphertexts. Paul et al. [22] proposed a provably secure bilinear pair-free conditional agent re-encryption scheme with fine-grained delegation control on the data, which greatly reduces the computational overhead and achieves modularity. Xiong et al. [23] proposed a one-way multi-hop conditional proxy re-encryption scheme with strong unforgeable signatures to achieve CCA security under the standard model while keeping the ciphertext length fixed. Yao et al. [24] proposed an identity-based conditional proxy re-encryption scheme for cloud data secure sharing scheme by adding a ciphertext evolution function to support updating the ciphertext after changing the identity key as well as implementing an authorization revocation function, and its efficiency and security do not become significantly lower, so the scheme is also applicable to other key update scenarios. Weiwei Ye et al. [25] proposed an identity-based conditional agent re-encryption scheme, which implements agent authority control at the delicate level, and the scheme is more efficient and secure. Li et al. [26] proposed a gated conditional anonymous agent re-encryption scheme, which verifies the conditions of ciphertext and re-encryption key simultaneously anonymizes sensitive information, and distributes the re-encryption to multiple agent nodes for completion using gating, which effectively resists collusion attacks, and in addition, this scheme also solves the problem of ignoring the re-encryption key validity in the scheme of Paul et al.
2.3. Summary and Analysis
Although blockchain technology and proxy re-encryption schemes have been widely applied in the field of data sharing, there is still a lack of effective solutions to combine the two in smart grid application scenarios to address data security and privacy issues in the process of data sharing. Therefore, this article adopts a distributed storage and verification mechanism based on blockchain technology to ensure the authenticity and integrity of data and introduces an identity-based proxy re-encryption scheme to achieve finer-grained data access control.
This paper uses the IBPRE algorithm for three reasons. First, the IBPRE scheme effectively guarantees the security and privacy of data sharing between two physical devices in heterogeneous and untrusted networks [24]. Secondly, the device encrypts its data through IBPRE and stores it in the ECS. When sharing with other devices, it does not need to download encrypted data, simplifying the data-sharing process [25]. Third, IBPRE is an improvement on PRE. It gets rid of PKI and simplifies certificate management in PRE [24]. However, IBPRE requires a private key generator (PKG) to authenticate users, generate private keys for users, and maintain keys [15].
If curious or malicious members control the PKG, they will be able to access the user’s data. In order to solve this problem, the identity center of the certificateless cryptosystem is used to provide identity certificates for various nodes in the system. With this identity certificate, various nodes involved in smart grid data sharing can authenticate the role in the request and reply. At the same time, the certificateless cryptosystem provides partial key pairs for various nodes in smart grid data sharing, synthesizes complete key pairs at the nodes, and publishes them in the blockchain. It is used for encrypting and decrypting information. The blockchain is used to manage the encryption key of the device data and record the access to the key to achieve accountability and enhance data security. The proxy re-encryption steps are as follows:
(1) A uses the public key as its identity to encrypt its data M, and obtains the ciphertext CA.
(2) When A wants to share data M with B, a heavily encrypted key can be generated through its private key and B’s public key .
(3) A sends CA and to proxy server, which can be an edge server.
(4) The proxy server is re-encrypted CA to obtain CB, and will be CB sent to B.
(5) B decrypts with its private key and finally obtains the data M.
3. Re-Encryption Data Sharing Scheme Based on Blockchain and Identity Condition Agent
3.1. System Model
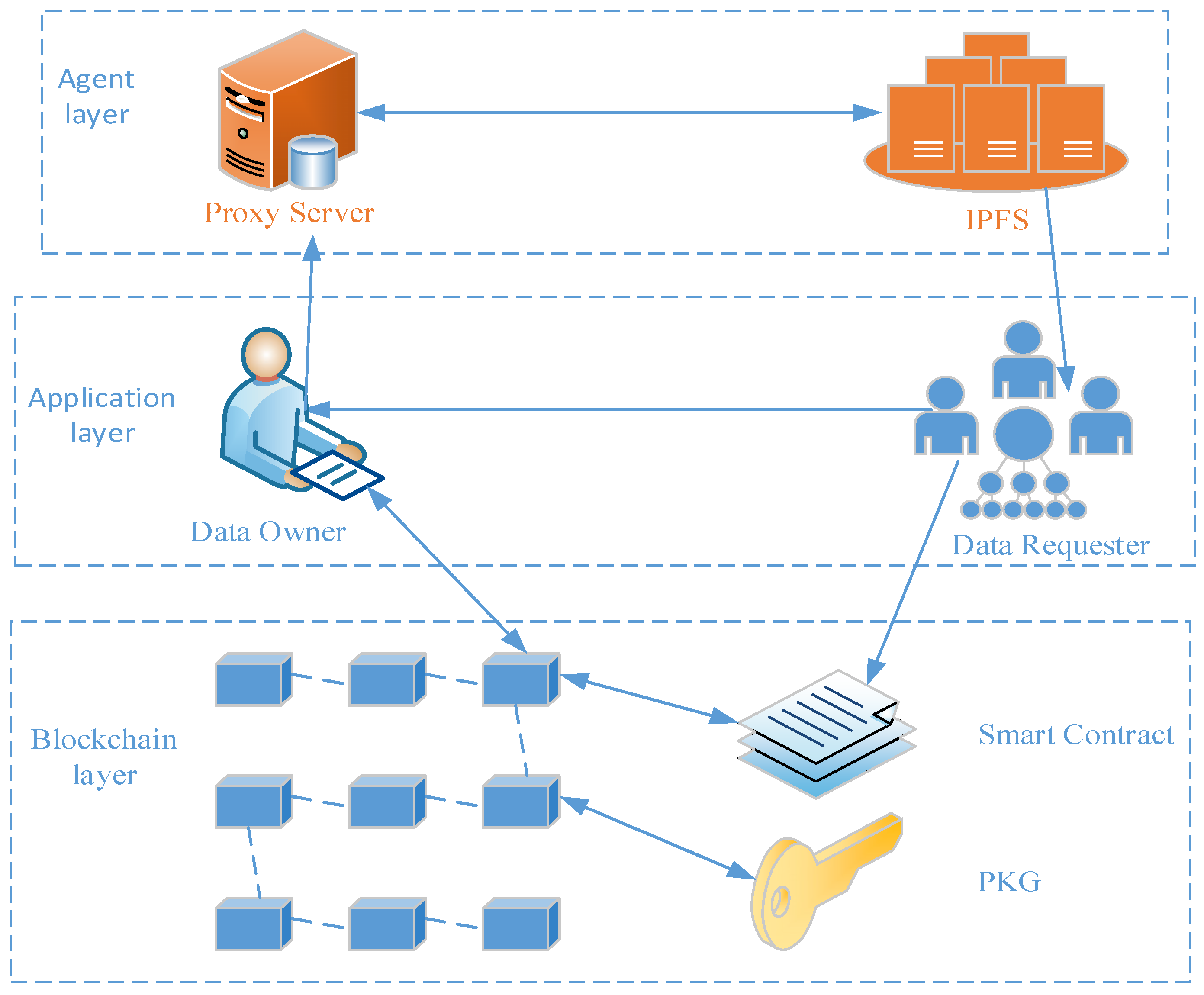
Taking the sharing between smart grid data centers as an example, this paper discusses a data-sharing model based on blockchain and identity conditional proxy re-encryption. The entities in the model include data owner A, data requester B, proxy server, Data Management Center, Hyperledger Fabric, and InterPlanetary File System. Before introducing the system model in detail, the main symbol definitions are first given. The symbols are shown in Table 1.

Table 1.
Symbol description table.
Data owner A: holds the data to be stored or shared. The smart grid data center scenario refers to all kinds of multi-source heterogeneous data collected by the edge server from various business systems of the smart grid.
Data requester B: data users from the same data center or other heterogeneous data centers. In the smart grid scenario, they are usually institutions such as electric power science academies or research institutes, or they can be other edge servers of homogeneous domains or heterogeneous domains in the edge environment.
Proxy server: The proxy server can be an ECS or an edge server with a certain storage capacity. As a semi-trusted third-party agent, it runs the re-encryption step in IBPRE. Specific functions include: (1) storing the ciphertext data and corresponding encryption parameters from data holder A, (2) searching the corresponding data according to the keywords provided by data requester B, and returning the address information and encryption parameters of data holder A to data requester B, (3) determining whether the data requester has the right to download data, and sending the address information and request information of the data requester to the blockchain. The blockchain verifies the permissions and generates logs of the request results to be uploaded.
Blockchain: Blockchain includes two functions in this model. First, the encryption key and other important data are stored to achieve system security; second, log records are maintained during sharing for auditing and sourcing.
DMC: DMC is a trusted authority that assigns identity to users entering the system, returns the private key and level information to users through a secure channel, executes algorithms to generate proxy re-encryption keys embedded in the shared condition set for users, and uploads user information to the proxy server. DMC needs to monitor the level information and revocation information of users in the system in real-time. Once the user level changes, it needs to update the identity information for users in a timely manner.
IPFS: a point-to-point distributed file system. The encrypted file uploaded to IPFS will get a unique hash string after hash calculation, through which data can be quickly retrieved. Because of the limitations of storage space and transaction speed on the blockchain, IPFS is usually selected to achieve permanent distributed power data storage and sharing.
In this framework, the IBPRE algorithm is combined with the Fabric platform, and IBPRE is used in complex networks to achieve safe data-sharing between two entities. Fabric is used to store the IBPRE encryption key and record all the events that occur during the sharing process. It manages the PKG in IBPRE through Fabric CA, which is controlled by the CA and is only responsible for generating the key for the user. At the same time, Fabric CA is used to verify the user’s identity, send requests to the PKG, and receive responses from the PKG. The smart grid data-sharing system framework is shown in Figure 1.
Figure 1.
Smart grid data-sharing system framework.
3.2. Security Mode
The security of the scheme in this paper is based on the proxy re-encryption algorithm. This section first constructs the security model of the algorithm, which is described as follows:
(1) Initialization: Challenger C creates the IND-CPA system and sends the public key to the adversary A.
(2) Query stage 1: The enemy has known all public parameters and can query the following process: , , .
① Key query: the enemy can query the key from user , and can get the private key and the public key.
② Re-encryption key query: the enemy hand performs a re-encryption encryption key query to any two users.
③ Re-encryption query: the enemy re-encrypts any two users , and the challenger runs the re-encryption algorithm to output the ciphertext C.
(3) Adversary A selects two plaintexts of the same length to send to Challenger C, and Challenger C randomly selects and records the encryption as , and then sends the ciphertext to Adversary A.
(4) Query phase 2: The enemy hand queries as shown in the query phase 1.
(5) Adversary A guesses whether the plaintext encrypted by challenger C in the previous step is or , and outputs the guess result as . If , the Adversary A attack is successful. The advantage of an adversary’s attack can be defined as the following function:
where is the length of the encryption key. Since random guess has the probability of winning the IND-CPA game, it is the advantage that the adversary has obtained through hard work.
If there is an ignorable advantage for Adversary A at any polynomial time , satisfying then this encryption algorithm is said to be indistinguishable under the selected plaintext attack [26].
3.3. Formal Definition of Scheme
This section first gives the definition of an identity-based multi-conditional proxy re-encryption scheme [14]. This scheme includes ten basic algorithms:
(1) : The system inputs a security parameter , and outputs the key and public parameters .
(2) : the system inputs the user’s identity information , and the system outputs the user’s public key and private key
(3) : the system inputs plaintext m, proxy re-encryption conditions and user i’s public key , and the system outputs layer 2 ciphertext .
(4) : the system inputs the user i’s private key , the user j public key jpk and the proxy re-encryption condition , and the system outputs the proxy re-encryption key .
(5) : the system inputs the proxy re-encryption key and the layer 2 ciphertext for user i, and the system outputs the layer 1 ciphertext for user j.
(6) : the system inputs plaintext m, proxy re-encryption condition and user j’s public key , and the system outputs layer 1 ciphertext for user j.
(7) : the system inputs the user I private key and the layer 2 ciphertext , and the system outputs the plaintext m.
(8) : the system inputs the user j private key and the layer 1 ciphertext , and the system outputs the plaintext m.
(9) : enter user i information in the system, the proxy re adds the secret key and the condition , and the system outputs the new condition .
(10) : enter user j identity information and proxy re-encryption key in the system, and the system outputs null function.
3.4. Scheme Process
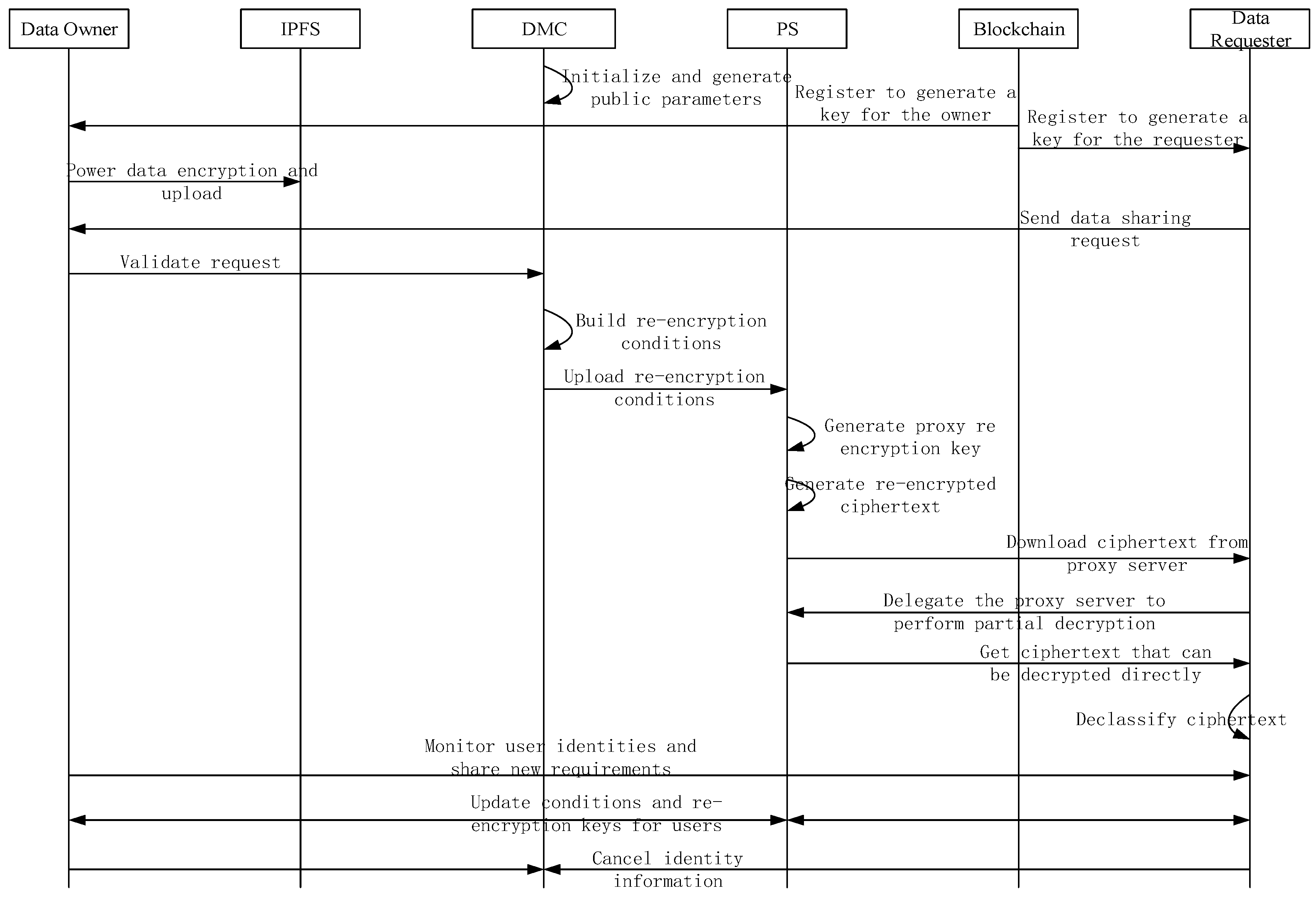
This scheme is based on the smart grid data center sharing model introduced in Section 3.1 and describes the sharing process when one data center user (data owner) and another data center user (data requester) have data-sharing needs. As shown in Figure 2.
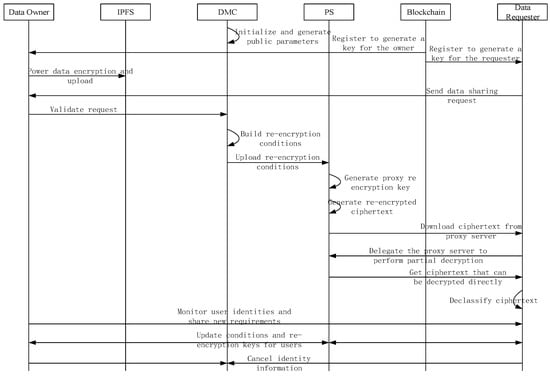
Figure 2.
Data-sharing process based on consortium chain.
3.4.1. Sharing Preparation Phase
In the preparation stage of data-sharing, three operations should be completed: system parameter generation, key generation, power data encryption, and upload [15]. The specific steps are as follows:
(1) According to the security parameters , the data management center performs the initialization algorithm to generate the system key msk and public parameters pp. A set of large primes q and integers , is two cycle groups based on the large prime bilinear pair of the order, where , g is the generation element G, constructing four collision-resistant hash functions , , , Output the system public parameters . Select the random number output as the system key, pp broadcast in the system, initialize the blockchain network, and complete the deployment and compilation of the smart contract. Once the deployment is completed, the smart contract will independently execute and participate in the whole process of data-sharing.
(2) Data owner and request to the data management center registration application, obtain its identity , data management center execution key generation algorithm for data-sharing to generate public and private key pair , through the security channel sent to the corresponding user , considering the block chain security regulatory issues, data management center to establish data-sharing mapping between user identity and private key mapping table for anonymous sharing process traceability. The data owner and data requester calculate the acquisition key , .
(3) The scheme defines that CPRE has two types of encryption. The second level of encryption generates a ciphertext that does not allow heavy encryption, so the second level of ciphertext is generated without a conditional value. The first level of ciphertext is used to generate a heavy encryption ciphertext, so it is necessary to embed the conditional value of the control decryption permission. Users can select the encryption level based on the importance of the data. The first and second level encryption algorithms are as follows:
① First the data owner performs the layer 2 encryption algorithm to generate the layer 2 ciphertext and upload it to the IPFS. Random selection , computational generation of layer 2 ciphertext , , , , .
② The data requester then performs the layer 1 encryption algorithm to generate the layer 1 ciphertext and upload it to the IPFS server, and the IPFS returns the hash value to be stored on the blockchain. Specifically, randomly selected , computationally generated layer 1 ciphertext , , , , .
3.4.2. Shared Agent Phase
In the data-sharing request stage, sharing request submission and verification, re-encryption condition construction and upload, and agent re-encryption key generation should be completed. The specific steps are as follows:
(1) Data requester with its to the data holder sends a data request and attach his signature, the two sides negotiate to determine the Shared data F, and then the Shared data F hash calculation gets file hash, that is . Here adopted the SHA-512 hash algorithm for raw power data hash calculation generated file path storage to the blockchain to quickly verify the data integrity. The data management center invokes the smart contract to use the query blockchain to check whether there is a re-encryption key for the data requester, or to terminate operations if present, otherwise to proceed with step 2.
(2) The data management center determines the legality of the sharing and records it to the blockchain. Then the data management center builds the heavy encryption conditions according to the identities of both parties in the data-sharing, and then uploads the conditions secretly to the proxy server for preservation.
(3) The data owner private key generates the conditional agent re-encryption key. The process is divided into three parts: first, the data owner randomly selects , and then calculate ; second, the data owner obtains the identity information of the data requester for the calculation ; then the data holder performs the re-encryption key generation algorithm to generate the agent re-encryption key . The final trigger smart contract will be uploaded to the proxy server in a specific form.
3.4.3. Shared Execution Phase
The shared execution stage includes two steps: agent re-encryption, ciphertext download and decryption, as follows:
(1) The proxy server performs the re-encryption process, and generates the re-encryption ciphertext according to the sharing conditions of the data holder and the identity of the data requester . The initial ciphertext will be converted into the first level of ciphertext that can be decrypted by the data requestor details are as follows:
(2) After the proxy server to complete the encryption operation generate new ciphertext and notify the data requester, data requesters can entrust a proxy server for partial decryption, specifically, the data requester first calculate a random secret factor , and then calculate , and then sent to the proxy server, proxy server perform partial decryption . Data requestor decrypts the level 1 ciphertext: calculate , you can get the clear text, and then check whether it is true, if true, then the data requestor finally gets the required data. Similarly, the data requester can also use the same way to directly decrypt the secondary ciphertext: calculate , you can obtain the clear text, and then check whether it is valid to verify the validity of the data.
3.4.4. Sharing Condition Update and Undo Phase
When the user sharing requirements change, the data management center needs to update the user data-sharing scope by changing the re-encryption conditions . The specific steps are as follows:
(1) The data management center monitors the user identity and sharing requirements in real-time. If the shared object and scope change, the new user identity information will be uploaded to the proxy server, and the conditions will be rebuilt according to the new identity;
(2) The proxy server performs the condition update algorithm to update the agent-heavy encryption key for the user.
(3) When the data user needs to cancel the account, they shall submit the cancellation application to the data management center. The data management center needs to cancel the user’s sharing relationship in the proxy server in a timely manner to prevent the abuse of resources. Specifically, the proxy server performs the cancellation algorithm so that all user operations are outputted Null. At this time, the user identity information is still retained in the system, but no operation can be carried out.
4. Security Analysis
When the user-sharing requirements change, the data management center needs to update the user data-sharing scope by changing the re-encryption conditions . The specific steps are as follows:
Theorem 1:
If there exists an adversary A that breaks the encryption scheme of this paper in polynomial time (PPT) with a non-negligible advantage, then it must be possible to construct a PPT adversary that solves the DBDH hard problem in bilinear pair mapping with a non-negligible advantage.
Proof:
simulate the game process between the adversary A and the challenger C under the choice of explicit attack, as follows:
Initialization phase: The challenger C runs the Setup algorithm to create the system’s public parameters pp, which are subsequently sent to the adversary A.
Query Phase1: The adversary A submits the following query request to the challenger C:
Key generation query: For a randomly submitted identifier by the adversary A, if the corresponding tuple already exists on the list LK, the challenger directly sends skn to the adversary A; if it does not exist, the challenger C runs the algorithm to regenerate the private key skn and sends it to the adversary A, and then records it to the list .
Re-encryption key generation query: for an identifier submitted by the adversary above, if the corresponding tuple already exists on the list, the challenger sends it directly to the adversary; if not, the challenger C runs the algorithm to generate the re-encryption key and sends it to the adversary A, and then records it in the list .
Challenge phase: Adversary A chooses a public key and two messages , which have the same length and sends to the challenger C, challenger randomly chooses and executes an Enc algorithm to encrypt the with the above public key into a challenge ciphertext and then sends the challenge ciphertext to the adversary A.
Guessing phase: The adversary A outputs a guess . If , the adversary A advantage is , then . If , , so the challenger has the advantage in the game:
where is the length of the encryption key.
Therefore, if an adversary A defeats this scheme by a non-negligible advantage, there must exist a challenger C who can solve the DBDH hard problem in polynomial time and this scheme satisfies the CPA security.□
Theorem 2:
The scheme is proved to be CCA—secure by satisfying the security of the scheme to the DBDH problem under the random oracle model.
Proof:
Given the multiplicative cyclic group and DBDH instances on , the scheme in this paper is CCA—secure if the DBDH assumption holds. □
Proof:
If there exists an attacker A who can break the scheme of this paper with a non-negligible advantage, then there must also exist an algorithm B who can break the DBDH assumption with a non-negligible advantage. According to the security model, the interaction between Algorithm B and Attacker A is as follows.
(1) Initialization. B randomly chooses , such that , , and B hands the system parameters to A. where is the random prediction machine controlled by B.
(2) query. B keeps an initially empty list with the record format . A enters the query, and B first queries Lwhether exists in , and if so, returns ; otherwise, B sets such that an . B randomly selects , and if , sets the public key to ; if , then sets . B stores into and returns to A.
(3) query. B query and return to A.
(4) query: B queries in . If , return the private key of . If , B returns ⊥ and exits the game.
(5) query. B keeps a list with records in the format . Algorithm B looks up and from . If , then , and B randomly chooses, and , where is the re-encryption condition. Compute , and , then and B stores into and returns to A; if , B returns ⊥ and exits the game.
(6) query. B queries from , if , then finds the re-encryption key by querying , then runs algorithm to get the layer 1 ciphertext and returns the result to A; if , B returns ⊥ and exits to A.
(7) query. re-encryption ciphertext , B query list of , if , then the private key of is , run decrypts and returns the plaintext to A. If , B returns ⊥ and exits the game.
The challenge phase. When A decides to end the query, it outputs an identity to be challenged (it must be guaranteed that A has not queried the private key of ), the re-encryption condition , and two equal plaintexts , to B. B generates the challenge ciphertext as follows.
(1) B queries from and if , then B exits the game, otherwise continue with the following steps.
(2) , B tosses a random coin , and B sets , , , . B returns the challenge ciphertext as to A. A can continue to query each of the above prediction machines, but to prevent A from decrypting frequently, B must make the following checks before answering A.
(1) A is not allowed to query the private key of .
(2) If A has queried the private key of and A sends query request, then B must avoid the re-encryption condition of when answering.
(3) If A has queried the private key of , then A is not allowed to query .
(4) If A has queried to get the re-encryption ciphertext , then A is not allowed to query .
(5) If A has queried and the re-encryption condition is . then A can use the re-encryption key to generate a re-encryption ciphertext, then A is not allowed to query ; otherwise, B still answers the query of A according to the original policy. If , such that , we can prove that is a re-encryption ciphertext by the following derivation:
if , and are independent of each other and is not a legitimate ciphertext.
Finally, A returns its guess for to B. If , then B outputs 1, i.e., B’s judgment abc holds; if , then B returns 0, i.e., B’s judgment does not hold. Let the number of times A asks is respectively, then the advantage of B in solving the DBDH hard problem is: .
If A can break this paper’s scheme, that is, Adv is non-negligible, then Adv DBDH is also non-negligible, that is, B can break the DBDH assumption holds with non-negligible advantage, which is contradictory to DBDH’s acknowledged hard solution, therefore, this paper’s scheme is CCA-secure. □
Theorem 3:
This scheme can effectively resist collusion attacks, the data holder DO and the proxy server cannot collude to get the data receiver DR private key, and the data receiver DR and the proxy server cannot collude to get the data holder DO private key.
Proof:
- Case 1: DO and proxy server collude. Due to the re-encryption key , it is known that the re-encryption key does not contain any private key information of the data recipient DR, so the two collude to obtain the DR private key.
- Case 2: The DR and the proxy server collude. Although the re-encryption key contains the data holder DO private key information, but the in the re-encryption key is calculated by DO and sent to the proxy server, because s is a random number, so the proxy server and the data recipient DR can get but DK cannot calculate , that is, they cannot get the DO private key.
Combining the above, this scheme can resist the collusion attack. □
5. Performance Analysis
5.1. Scheme Comparison
This scheme is compared with similar schemes in six aspects: cryptosystem, anti-collusion attack, condition-based, difficult problem, security level, and other characteristic functions. The results are shown in Table 2. The “√” in the table indicates that it meets the requirements “×” Indicates dissatisfaction.

Table 2.
Comparison of functions between this solution and similar solutions.
In terms of cryptosystems, our scheme adopts an identity-based encryption (IBE) system, while Xiong [23] and Li [26] adopt traditional public key encryption systems. Compared to IBE systems, IBE systems have higher security and flexibility, so our scheme and other schemes using IBE systems have an advantage in this regard. In terms of security level, all schemes have a high-security level, of which our scheme has security under selective ciphertext attack (CCA), while Wei’s scheme has security under selective plaintext attack (CPA). Although both security levels are high, CCA has a more general security guarantee. In summary, our conditional proxy re-encryption algorithm has an advantage in terms of computational cost compared to other schemes and is suitable for data-sharing scenarios.
In order to analyze the computational cost of the conditional proxy re-encryption algorithm in data-sharing, this scheme was compared with the other two schemes. The comparison results of the computational cost of the algorithms in each scheme are shown in Table 3, where “-” indicates that it was not covered in the text.

Table 3.
Comparison of Algorithm Calculation Costs for Various Schemes.
Table 3 shows the time required for bilinear pairing, the time required for exponential operation, and the time required for multiplication operation. The size relationships between them are as follows: in fact, the time required for multiplication operations is only in microseconds, while the time for bilinear pairing and exponential operations is in milliseconds. Therefore, multiplication operations can be disregarded when comparing algorithm computational costs. In addition, the literature uses one-time authentication signature technology during encryption, so the table indicates the time required for performing one signature calculation and one authentication calculation.
According to the analysis of Table 3, the computational cost at each stage of this scheme is still relatively low after the introduction of conditional value support for data refinement sharing. Compared with Yao ’s scheme [24], this scheme only has slightly higher costs in the re-encryption and decryption stages, and the overall cost is basically the same. This is because this scheme needs to calculate the condition value during the re-encryption stage. Compared with Xiong’s scheme [23], this scheme has reduced computational costs in all stages. Therefore, this scheme has significant advantages in functionality and computational overhead compared to other schemes.
5.2. Performance Testing
Test the algorithm overhead of the proposed scheme in the Paired Based Cryptography Library (PBC), construct bilinear pairs on elliptic curves, and write the program in the Go language. Using two desktop computers to build an experimental environment, one simulates a proxy server node, and the other simulates a data holder and a data receiver user through a virtual machine. The system sets up a total of three node users. The hardware configuration is AMD R5 3600 CPU, 16 GB memory, and 500 GB hard disk.
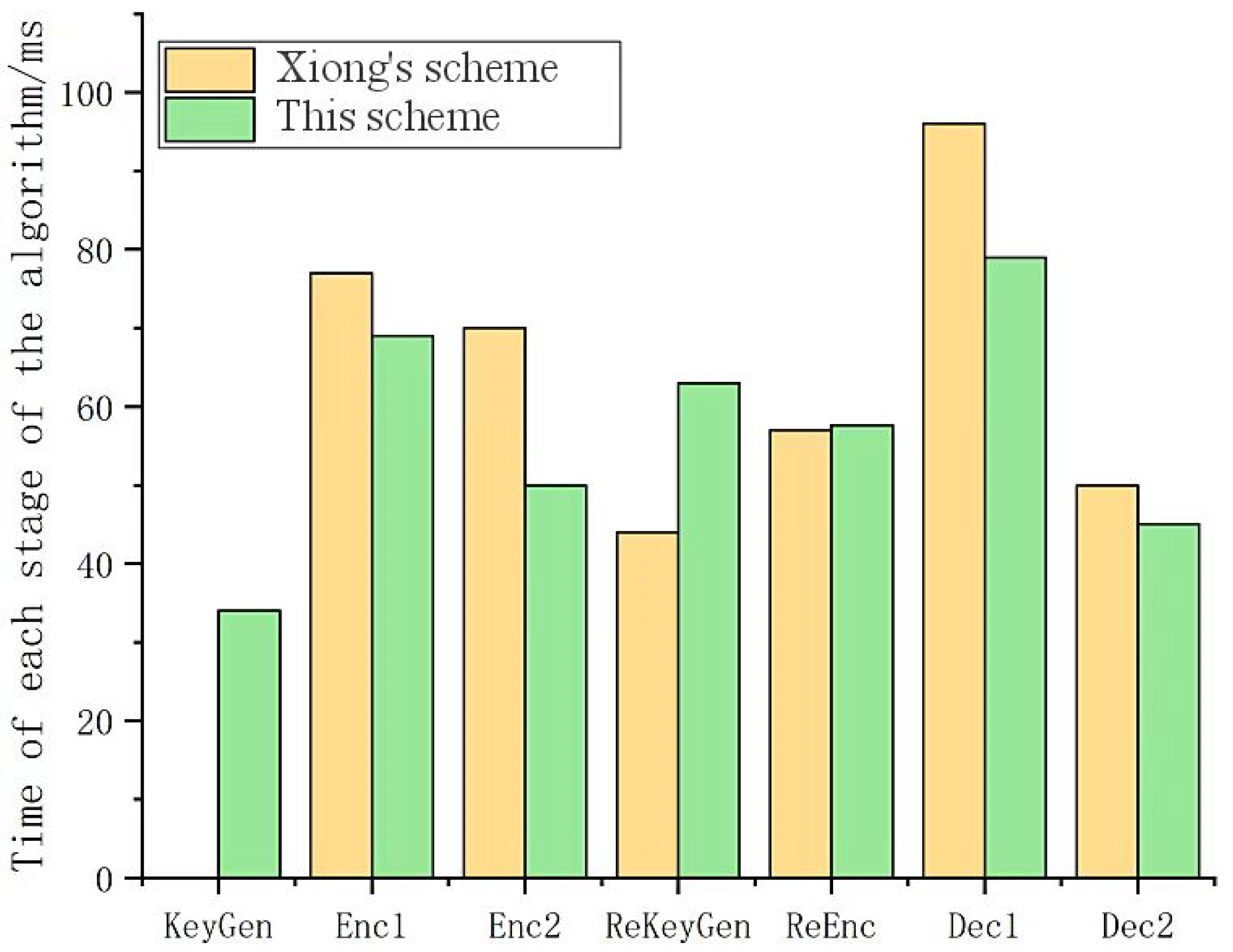
Using the fixed size user set mentioned above, with the number of conditions set to 3, the shared file size and encryption algorithm jointly affect the encryption time. Here, in order to simplify, it is set to a fixed value. During the execution of the algorithm from key generation, encryption, re-encryption key generation, re-encryption, decryption, and other stages, ten tests are conducted to obtain the average value. The experimental results are shown in Figure 3.
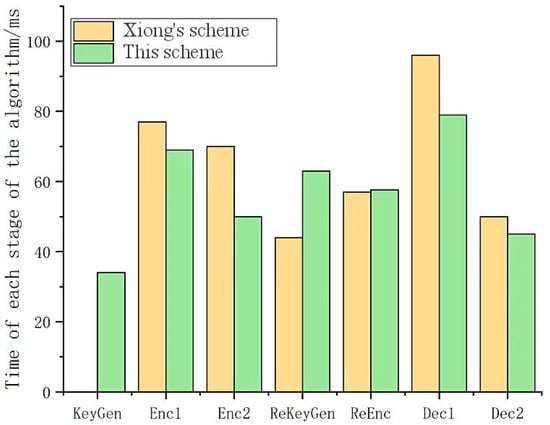
Figure 3.
Test results of execution time at each stage of the algorithm.
By analyzing Figure 3, it can be seen that the overall execution time of the algorithm in this scheme is shorter than that in the Xiong’s scheme [23] and only slightly higher than that in the Xiong’s scheme [23] during the generation and re-encryption stages of the re-encryption key. This is because the condition values need to be calculated and updated during re-encryption to achieve data granularity sharing, and in other stages, this scheme takes less time than that in the Xiong’s scheme [23]. At the same time, the execution time of the two stages in re-encryption is still relatively short, and the increase in computational cost for users who need frequent re-encryption is not significant.
6. Conclusions
Based on blockchain technology, we propose a high-value data-sharing model for smart grid data scenarios. Firstly, the model makes full use of blockchain’s decentralization, traceability, anti-tampering, and anti-repudiation features, which effectively improves the security and trustworthiness of the data and reduces the risk of data leakage and tampering; secondly, the model can effectively mobilize the participation and motivation of the data holders, and promote the sharing and utilization of high-value data; lastly, through in-depth research and comparative analysis, the model proposed in this paper is able to resist most of the known attacks commonly found in blockchain, and has the functions of traceable auditing, membership control, and secure sharing, which can meet the relevant needs of actual business and can be better applied to smart grid data-sharing scenarios. However, there are also some limitations in this study. In the smart grid data-sharing scheme based on conditional proxy re-encryption, we focus on the issue of fine-grained data access control and effectively trace the identity and behavior process of responsible persons. In the performance testing phase, only the algorithm execution time and computational overhead of each stage were considered, and other factors that affect performance were not deeply considered. In the next step, further research can be carried out on the data packet loss rate when multiple users share data.
Author Contributions
Conceptualization, L.Z.; methodology, L.Z. and S.C.; software, Q.Y.; investigation, L.Z.; resources, L.Z.; data curation, Q.Y.; writing—original draft preparation, Y.Y.; writing—review and editing, L.Z., Q.Y. and Y.Y.; supervision, L.Z. and S.C.; project administration, L.Z. and J.G.; funding acquisition, L.Z. All authors have read and agreed to the published version of the manuscript.
Funding
National Natural Science Foundation of China (No. 62261023, 72262014); Jiangxi Natural Science Foundation of China (20232BAB2).
Data Availability Statement
Some or all data, models, or codes generated or used during the study are available from the corresponding author by request.
Acknowledgments
The authors would like to acknowledge East China Jiaotong University for the lab facilities and necessary technical support.
Conflicts of Interest
All authors have no known or potential competing financial interest or personal relationship that could have appeared to influence the work reported in this paper.
References
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. A systematic review of data protection and privacy preservation schemes for smart grid communications. Sustain. Cities Soc. 2018, 38, 806–835. [Google Scholar] [CrossRef]
- Samuel, O.; Javaid, N.; Awais, M.; Ahmed, Z.; Imran, M.; Guizani, M. A blockchain model for fair data sharing in deregulated smart grids. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019. [Google Scholar]
- Khan, F.A.; Asif, M.; Ahmad, A.; Alharbi, M.; Aljuaid, H. Blockchain technology, improvement suggestions, security challenges on smart grid and its application in healthcare for sustainable development. Sustain. Cities Soc. 2020, 55, 102018. [Google Scholar] [CrossRef]
- Tao, Z.T.; Si, G.L. Achieving privacy-preserving big data aggregation with fault tolerance in smart grid. Digit. Commun. Netw. 2017, 3, 242–249. [Google Scholar]
- Cai, X.; Geng, S.; Zhang, J.; Wu, D.; Cui, Z.; Zhang, W.S.; Chen, J. A Sharding Scheme based Many-objective Optimization Algorithm for Enhancing Security in Blockchain-enabled Industrial Internet of Things. IEEE Trans. Ind. Inform. 2021, 17, 7650–7658. [Google Scholar] [CrossRef]
- Manzoor, A.; Liyanage, M.; Braeke, A.; Kanhere, S.S.; Ylianttila, M. Blockchain based proxy re-encryption scheme for secure IoT data sharing. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019. [Google Scholar]
- Agyekum, K.O.-B.O.; Xia, Q.; Sifah, E.B.; Cobblah, C.N.A.; Xia, H.; Gao, J. A proxy re-encryption approach to secure data sharing in the Internet of things based on blockchain. IEEE Syst. J. 2021, 16, 1685–1696. [Google Scholar] [CrossRef]
- Li, X.; Huang, K.; Yang, W.; Wang, S.; Zhang, Z. On the convergence of fedavg on non-iid data. arXiv 2019, arXiv:1907.02189. [Google Scholar]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet Things J. 2018, 6, 4660–4670. [Google Scholar] [CrossRef]
- Bhatia, T.; Verma, A.K.; Sharma, G. Towards a secure incremental proxy re-encryption for e-healthcare data sharing in mobile cloud computing. Concurr. Comput. Pract. Exp. 2020, 32, e5520. [Google Scholar] [CrossRef]
- Hu, H.; Zhou, Y.; Cao, Z.; Dong, X. Efficient and HRA Secure Universal Conditional Proxy Re-Encryption for Cloud-Based Data Sharing. Appl. Sci. 2022, 12, 9586. [Google Scholar] [CrossRef]
- Li, W.; Jin, C.; Kumari, S.; Xiong, H.; Kumar, S. Proxy re-encryption with equality test for secure data sharing in Internet of Things-based healthcare systems. Trans. Emerg. Telecommun. Technol. 2022, 33, e3986. [Google Scholar] [CrossRef]
- Li, R.; Song, T.; Mei, B.; Li, H.; Cheng, X.; Sun, L. Blockchain for large-scale internet of things data storage and protection. IEEE Trans. Serv. Comput. 2019, 12, 762–771. [Google Scholar] [CrossRef]
- Wang, J.; Gao, L.C.; Dong, A.; Guo, S.Y.; Chen, H.; Wei, X. Block Chain Based Data Security Sharing Network Architecture Research. Comput. Res. Dev. 2017, 54, 742–749. [Google Scholar]
- Li, H.; Han, D.; Li, K.-C.; Castiglione, A. EduRSS: A blockchain-based educational records secure storage and sharing scheme. IEEE Access 2019, 7, 179273–179289. [Google Scholar] [CrossRef]
- Wu, Z.Q.; Liang, Y.H.; Kang, J.W. Secure data storage and sharing system based on consortium blockchain in smart grid. Comput. Appl. 2017, 37, 2742–2747. [Google Scholar]
- Sun, E.; Meng, K.; Yang, R.; Zhang, Y.; Li, M. Research on distributed data sharing system based on Internet of Things and blockchain. J. Syst. Sci. Inf. 2021, 9, 239–254. [Google Scholar] [CrossRef]
- Lin, H.Y.; Hung, Y.M. An improved proxy Re-encryption scheme for IoT-based data outsourcing services in clouds. Sensors 2020, 21, 67. [Google Scholar] [CrossRef] [PubMed]
- Gao, Y.; Chen, Y.; Hu, X.; Lin, H.; Liu, Y.; Nie, L. Blockchain based IIoT data sharing framework for SDN-enabled pervasive edge computing. IEEE Trans. Ind. Inform. 2020, 17, 5041–5049. [Google Scholar] [CrossRef]
- Green, M.; Ateniese, G. Identity-based proxy re-encryption. In Proceedings of the Applied Cryptography and Network Security: 5th International Conference, ACNS 2007, Zhuhai, China, 5–8 June 2007; Proceedings 5. Springer: Berlin/Heidelberg, Germany, 2007; pp. 288–306. [Google Scholar]
- Qiu, J.; Lee, Y.; Lee, H. Identity-based conditional proxy re-encryption. In Proceedings of the 2011 IEEE International Conference on Communications (ICC), Busan, Republic of Korea, 22–24 October 2011; pp. 1–5. [Google Scholar]
- Paul, A.; Selvi, S.S.D.; Rangan, C.P. A provably secure conditional proxy re-encryption scheme without pairing. J. Internet Serv. Inf. Secur. 2019, 11, 1–21. [Google Scholar]
- Xiong, H.; Wang, Y.; Li, W.; Chen, C.M. Flexible, efficient, and secure access delegation in cloud computing. ACM Trans. Manag. Inf. Syst. 2019, 10, 1–20. [Google Scholar] [CrossRef]
- Yao, S.; Dayot, R.V.J.; Kim, H.-J.; Ra, I.-H. A novel revocable and identity-based conditional proxy re-encryption scheme with ciphertext evolution for secure cloud data sharing. IEEE Access 2021, 9, 42801–42816. [Google Scholar] [CrossRef]
- Ye, W.W.; You, Q.Y.; Wei, W. Provably Secure Identity-based Conditional Proxy Re-encryption Scheme. Comput. Eng. 2017, 43, 194–198. [Google Scholar]
- Li, Z.B.; Zhao, H.; Wei, Z.Z. Threshold-Based Pairing-free Conditional Anonymous Proxy Re-Encryption Scheme. J. Electron. Inf. 2021, 43, 3350–3358. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).