Security and Trust in the 6G Era: Risks and Mitigations
Abstract
1. Introduction
2. Motivations and Related Works
3. The Dawn of 6G
3.1. Technologies
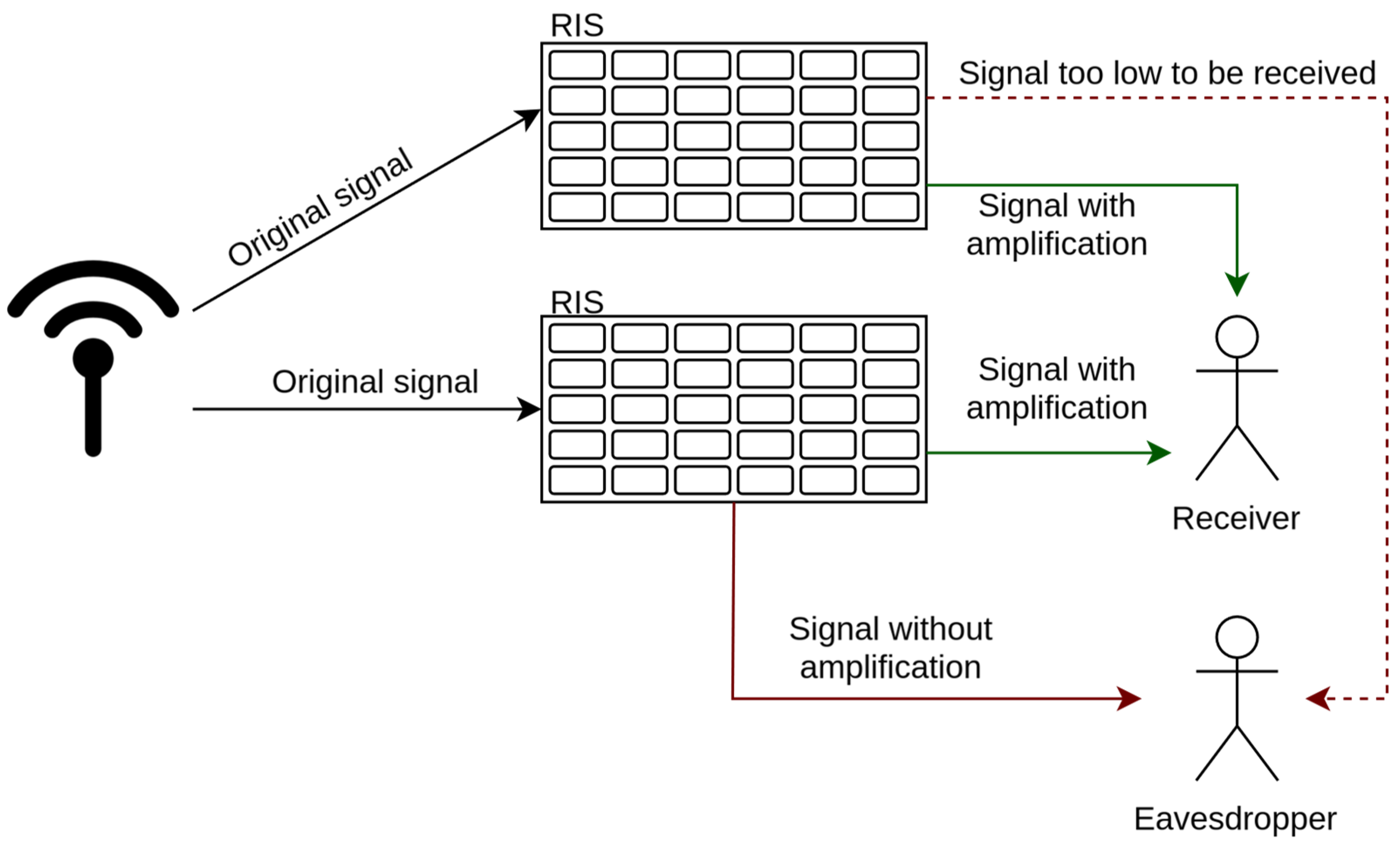
- Reconfigurable Intelligent Surfaces (RIS): very high frequencies, beyond 100 GHz and up to a few THz [14], will be used by 6G to achieve high-speed data transmission. However, this comes with some limitations from the coverage point of view. In fact, high frequencies have a lower range and they cannot penetrate obstructions as well as lower frequencies can. Thus, to address these limitations, reflective surfaces known as RIS could be employed. These surfaces reflect signals from the sender circumventing obstacles, redirecting them to the receiver intact. As depicted in Figure 1, RIS could be Reflective, meaning that they reflect the signal in a specific direction to improve the route of the signal, or Transmissive, that is they transmit the signal by modulating and controlling it with its constituent elements. Furthermore, thanks to their versatility and scalability, they would fit seamlessly into existing networks without changing any protocols or hardware components and would cost very little for their functionality. RIS can also be useful in trying to counteract the Doppler effect [15], thus allowing a stable connection even to fast-moving devices.
- Visible Light Communication (VLC): VLC is a high-speed wireless communication technology based on the employment of visible light to transmit data. In particular, it uses LED lights to modulate visible light using a very high bandwidth with a frequency of 400–800 THz, which is much higher than the radio frequencies. VLC is a good alternative to standard wireless communication because it allows transfering large amounts of data with existing lighting systems with negligible costs and no harm to human health [16].
- Artificial Intelligence applied to 6G: The exponential development of AI in recent years will inevitably affect 6G technologies, bringing significant advantages to communication networks. In particular, Artificial Intelligence can be used to improve and automate various aspects of IT operations (AIOps-enabled) [17]. These solutions are designed to cope with the complexity and scale of modern IT environments, facilitating the management of infrastructure, applications, and services and allowing the detection of any anomalies. Furthermore, the application of Artificial Intelligence can be employed for real-time resource management and optimization within networks (Self-Optimizing Networks). This includes enhancing traffic flow, connection speed, and forecasting traffic peaks to proactively manage them. Additionally, it will enable dynamic frequency allocation planning (Dynamic Spectrum Management) [13] and mitigate interference issues. Finally, the application of AI on a large scale will result in a notable increase in the costs associated with training and the collection of large-scale datasets. Consequently, it becomes imperative to utilize specialized AI approaches such as federated learning [18], which facilitate the coordination of the learning process across millions of distributed devices to enhance the quality of the centralized learning model (global federated learning model).
3.2. Application Scenarios
- Multisensory XR: eXtended Reality (XR) is a generic term that is used to the combination of virtual reality (VR), augmented reality (AR) and mixed reality (MR). XR is applicable to rethink how many activities of real life can happen, starting with education, healthcare, and extending to entertainment, combining the physical and digital worlds and allowing users to immerse and interact with objects in a sort of hybrid universe between virtual reality and the real world [20].
- Connected Robotics and Autonomous Systems (CRAS): One of the main objectives of 6G is certainly to enable the maximum efficiency of CRAS. The term refers to a wide range of robotic and autonomous systems connected to each other and to a common network, enabling them to share data, collaborate, and perform tasks independently. CRAS will be crucial for the operation of new services such as autonomous vehicles, remote surgery, environmental and pollution monitoring, industrial automation, and remote rescue operations in disaster-stricken locations.
- Wireless Brain–Computer Interactions (BCI): BCIs are a disruptive technology with respect to how we interact with computers and other devices. Specifically, they are based on certain devices (worn or implanted) that transmit wireless signals corresponding to the user’s brain activity, thus allowing them to control local or remote devices without the need for physical contact and taking advantage of 6G connectivity. BCI was previously limited to healthcare contexts, but with 6G, its potential will increase to the point where it will be applicable in many sectors [21].
- Blockchain and Distributed Ledger Technologies (DLT): DLT is a type of decentralized technology that allows data to be recorded and shared among all participants in the network, guaranteeing authenticity and integrity without the need for a central, trusted authority. DLTs can benefit from 6G systems to provide highly scalable and secure networks that are capable of supporting the growing number of devices and data-intensive applications. In turn, DLTs would provide 6G systems with much more security and transparency in the transfer of data and interactions between devices [22].
3.3. Security and Privacy in 6G
3.4. Trust in 6G
- Direct: based on the past interactions between the user and the system;
- Indirect: based on third parties’ opinions or recommendations.
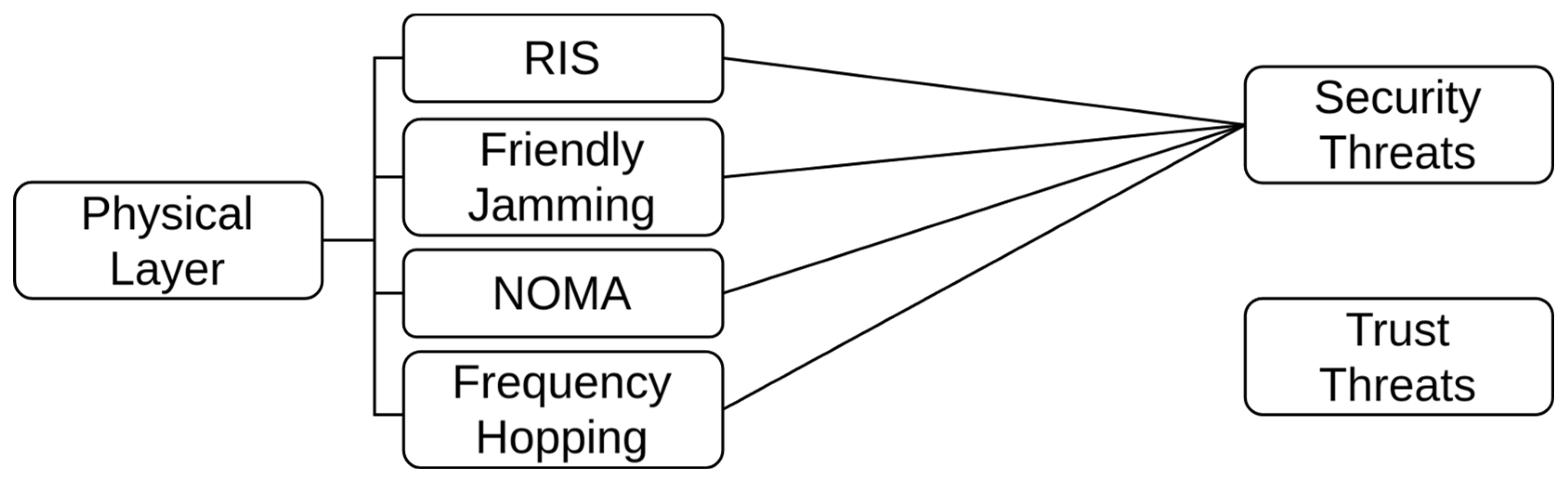
4. Physical Layer
4.1. Vulnerabilities and Threats
- Eavesdropping: this is a type of attack where the attacker eavesdrops on conversations between two parties without authorization and intercepts sensitive information [25].
- Jamming: this attack generates interference signals or noise in the communication channel, making the transmission of information unreliable and disrupting communication [26].
- Pilot Contamination Attack (PCA): this attack “contaminates” the pilot signal from a base station, compromising communications and network performance [27].
- Spoofing: this attack involves spoofing the identity of a person or device to deceive other users or systems and gain unauthorized access [26].
4.2. Mitigations
4.2.1. Reconfigurable Intelligent Surfaces
4.2.2. Friendly Jamming
4.2.3. NOMA
4.2.4. Frequency Hopping
4.2.5. Reinforcement Learning
5. Connection Layer
5.1. Vulnerabilities and Threats
- DoS (Denial of Service): this attack aims to make a service, resource, or network inaccessible to legitimate users by creating an excessive volume of requests, saturating the available traffic [35].
- Distributed Denial of Service (DDoS): this is a similar type of attack to DoS but uses multiple devices to achieve higher impact by increasing the number of requests and hampering defenses based on isolating the attacker’s address [36].
- MitM (Man-in-the-Middle): this is an active attack in which attackers are able to position themselves on the path between legitimate endpoints to intercept and alter communication without their knowledge [37].
- Replay Attack: in this attack, the attacker intercepts and stores communication data and then later reuses it to gain unauthorized access or to perform malicious operations [38].
5.2. Mitigations
5.2.1. Quantum Key Distribution
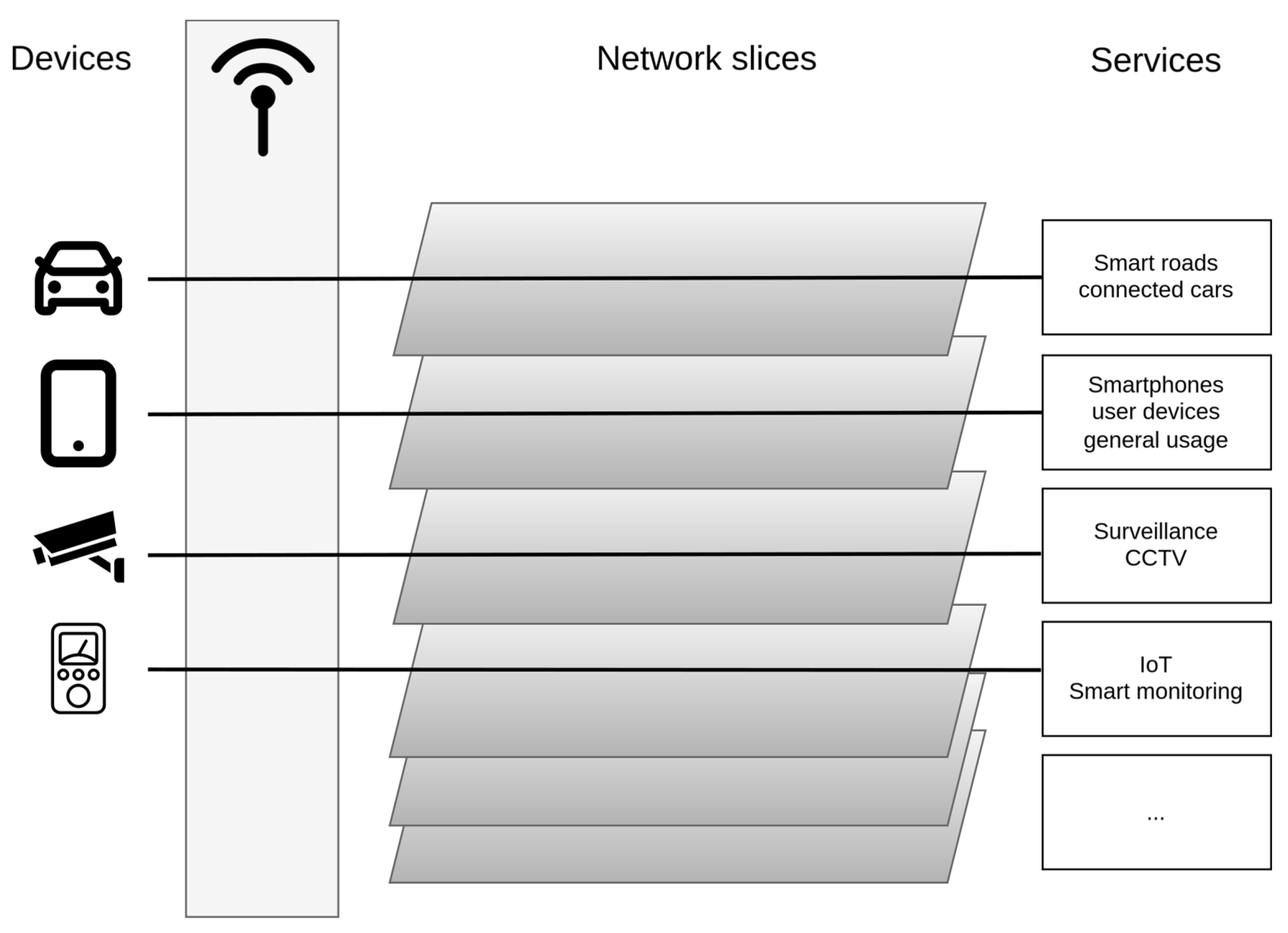
5.2.2. Network Slicing
5.2.3. IDS
5.3. Zero Trust Architecture (ZTA)
- Policy Engine: evaluates the validity of a user’s access request using a Trust Algorithm, which is a machine learning algorithm that greatly optimizes this process;
- Policy Administrator: cooperating with the Policy Engine, decides whether to allow or deny the access using a Trust Algorithm, automating access control with a minimal error rate;
- Policy Enforcement Point: monitors and manages links between users and resources.
6. Application Layer
6.1. Vulnerabilities and Threats
6.2. Mitigations
6.2.1. Biometric Authentication
- Biologic, based on genetic factors of the individual;
- Morphological, based on physical traits of the individual;
- Behavioral, based on the individual’s behavioral patterns.
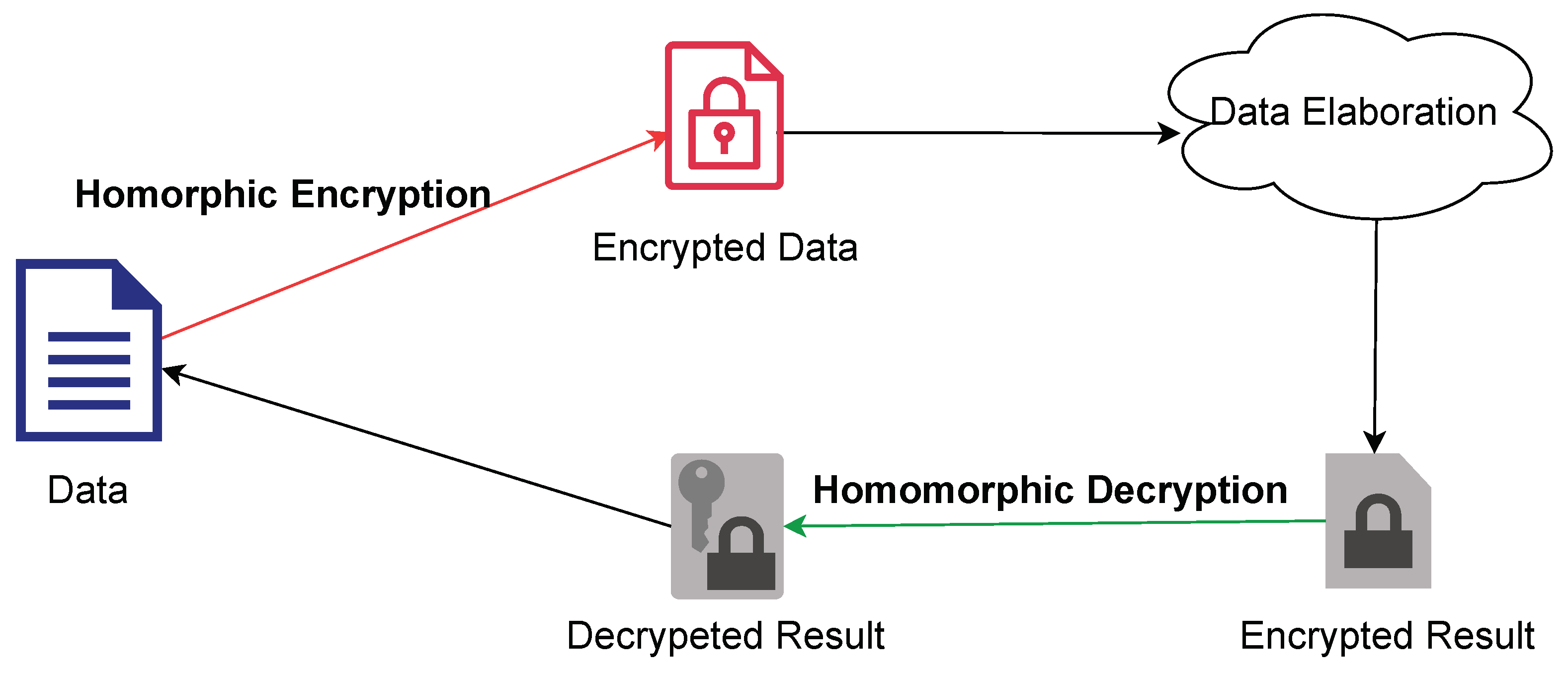
6.2.2. Quantum Homomorphic Cryptography (Qhc)
6.2.3. Authentication and Key Agreement (AKA)
6.3. Blockchain
6.4. Trust Anchors
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 3GPP | 3rd Generation Partnership Project |
| AI | Artificial Intelligence |
| AKA | Authentication Key Agreement |
| BCI | Wireless Brain–Computer Interactions |
| CRAS | Connected Robotics and Autonomous Systems |
| DDoS | Distributed Denial of Service |
| DL | Deep Learning |
| DLT | Distributed Ledger Technologies |
| DoS | Denial of Service |
| IDPS | Intrusion Detection and Prevention System |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| MIMO-OFDM | Multiple-Input, Multiple-Output Orthogonal Frequency-Division Multiplexing |
| MitM | Man-in-the-Middle |
| NOMA | Non-Orthogonal Multiple Access |
| PCA | Pilot Contamination Attacks |
| QHC | Quantum Homomorphic Cryptography |
| QKD | Quantum Key Distribution |
| QoS | Quality of Service |
| RIS | Reconfigurable Intelligent Surfaces |
| RL | Reinforcement Learning |
| TTFs | Trust and Traceability Functions |
| VLC | Visible Light Communication |
| XR | eXtended Reality |
| ZTA | Zero Trust Architecture |
References
- GSMA. The Mobile Economy 2024. 2024. Available online: https://www.gsma.com/solutions-and-impact/connectivity-for-good/mobile-economy/wp-content/uploads/2024/02/260224-The-Mobile-Economy-2024.pdf (accessed on 17 April 2024).
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Sun, Y.; Liu, J.; Wang, J.; Cao, Y.; Kato, N. When machine learning meets privacy in 6G: A survey. IEEE Commun. Surv. Tutorials 2020, 22, 2694–2724. [Google Scholar] [CrossRef]
- Sheth, K.; Patel, K.; Shah, H.; Tanwar, S.; Gupta, R.; Kumar, N. A taxonomy of AI techniques for 6G communication networks. Comput. Commun. 2020, 161, 279–303. [Google Scholar] [CrossRef]
- Ylianttila, M.; Kantola, R.; Gurtov, A.; Mucchi, L.; Oppermann, I.; Yan, Z.; Nguyen, T.H.; Liu, F.; Hewa, T.; Liyanage, M.; et al. 6G white paper: Research challenges for trust, security and privacy. arXiv 2020, arXiv:2004.11665. [Google Scholar]
- Mitev, M.; Chorti, A.; Poor, H.V.; Fettweis, G.P. What Physical Layer Security Can Do for 6G Security. IEEE Open J. Veh. Technol. 2023, 4, 375–388. [Google Scholar] [CrossRef]
- Mucchi, L.; Jayousi, S.; Caputo, S.; Panayirci, E.; Shahabuddin, S.; Bechtold, J.; Morales, I.; Stoica, R.A.; Abreu, G.; Haas, H. Physical-Layer Security in 6G Networks. IEEE Open J. Commun. Soc. 2021, 2, 1901–1914. [Google Scholar] [CrossRef]
- Xie, N.; Chen, J.; Huang, L. Physical-layer authentication using multiple channel-based features. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2356–2366. [Google Scholar] [CrossRef]
- Porambage, P.; Gür, G.; Osorio, D.P.M.; Liyanage, M.; Gurtov, A.; Ylianttila, M. The roadmap to 6G security and privacy. IEEE Open J. Commun. Soc. 2021, 2, 1094–1122. [Google Scholar] [CrossRef]
- Nguyen, V.L.; Lin, P.C.; Cheng, B.C.; Hwang, R.H.; Lin, Y.D. Security and Privacy for 6G: A Survey on Prospective Technologies and Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 2384–2428. [Google Scholar] [CrossRef]
- David, K.; Berndt, H. 6G Vision and Requirements: Is There Any Need for Beyond 5G? IEEE Veh. Technol. Mag. 2018, 13, 72–80. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Ding, M.; Pathirana, P.N.; Seneviratne, A.; Li, J.; Niyato, D.; Dobre, O.; Poor, H.V. 6G Internet of Things: A Comprehensive Survey. IEEE Internet Things J. 2022, 9, 359–383. [Google Scholar] [CrossRef]
- Jiang, W.; Han, B.; Habibi, M.A.; Schotten, H.D. The Road Towards 6G: A Comprehensive Survey. IEEE Open J. Commun. Soc. 2021, 2, 334–366. [Google Scholar] [CrossRef]
- Rappaport, T.S.; Xing, Y.; Kanhere, O.; Ju, S.; Madanayake, A.; Mandal, S.; Alkhateeb, A.; Trichopoulos, G.C. Wireless Communications and Applications Above 100 GHz: Opportunities and Challenges for 6G and Beyond. IEEE Access 2019, 7, 78729–78757. [Google Scholar] [CrossRef]
- Bilotti, F.; Barbuto, M.; Hamzavi-Zarghani, Z.; Karamirad, M.; Longhi, M.; Monti, A.; Ramaccia, D.; Stefanini, L.; Toscano, A.; Vellucci, S. Reconfigurable intelligent surfaces as the key-enabling technology for smart electromagnetic environments. Adv. Phys. X 2024, 9, 2299543. [Google Scholar] [CrossRef]
- Chi, N.; Zhou, Y.; Wei, Y.; Hu, F. Visible Light Communication in 6G: Advances, Challenges, and Prospects. IEEE Veh. Technol. Mag. 2020, 15, 93–102. [Google Scholar] [CrossRef]
- Ziegler, V.; Schneider, P.; Viswanathan, H.; Montag, M.; Kanugovi, S.; Rezaki, A. Security and Trust in the 6G Era. IEEE Access 2021, 9, 142314–142327. [Google Scholar] [CrossRef]
- Liu, Y.; Yuan, X.; Xiong, Z.; Kang, J.; Wang, X.; Niyato, D. Federated learning for 6G communications: Challenges, methods, and future directions. China Commun. 2020, 17, 105–118. [Google Scholar] [CrossRef]
- Saad, W.; Bennis, M.; Chen, M. A vision of 6G wireless systems: Applications, trends, technologies, and open research problems. IEEE Net. 2019, 34, 134–142. [Google Scholar] [CrossRef]
- Minopoulos, G.; Psannis, K.E. Opportunities and Challenges of Tangible XR Applications for 5G Networks and Beyond. IEEE Consum. Electron. Mag. 2023, 12, 9–19. [Google Scholar] [CrossRef]
- Hu, H.; Chen, X.; Jiang, T. Guest editorial: Brain-computer-interface inspired communications. China Commun. 2022, 19, iii–v. [Google Scholar] [CrossRef]
- Baskaran, S.B.M.; Faisal, T.; Wang, C.; Lopez, D.R.; Ordonez-Lucena, J.; Arribas, I. The Role of DLT for Beyond 5G Systems and Services: A Vision. IEEE Commun. Stand. Mag. 2023, 7, 32–38. [Google Scholar] [CrossRef]
- Cao, J.; Ma, M.; Li, H.; Ma, R.; Sun, Y.; Yu, P.; Xiong, L. A Survey on Security Aspects for 3GPP 5G Networks. IEEE Commun. Surv. Tutor. 2020, 22, 170–195. [Google Scholar] [CrossRef]
- López, O.L.A.; Alves, H.; Souza, R.D.; Montejo-Sánchez, S.; Fernández, E.M.G.; Latva-Aho, M. Massive Wireless Energy Transfer: Enabling Sustainable IoT Toward 6G Era. IEEE Internet Things J. 2021, 8, 8816–8835. [Google Scholar] [CrossRef]
- Wei, Z.; Liu, F.; Masouros, C.; Su, N.; Petropulu, A.P. Toward Multi-Functional 6G Wireless Networks: Integrating Sensing, Communication, and Security. IEEE Commun. Mag. 2022, 60, 65–71. [Google Scholar] [CrossRef]
- Vaishnavi, K.N.; Khorvi, S.D.; Kishore, R.; Gurugopinath, S. A Survey on Jamming Techniques in Physical Layer Security and Anti-Jamming Strategies for 6G. In Proceedings of the 2021 28th International Conference on Telecommunications (ICT), London, UK, 1–3 June 2021; pp. 174–179. [Google Scholar] [CrossRef]
- Akgun, B.; Krunz, M.; Koyluoglu, O.O. Pilot contamination attacks in massive MIMO systems. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017. [Google Scholar] [CrossRef]
- Zhang, S.; Gao, H.; Su, Y.; Cheng, J.; Jo, M. Intelligent Mixed Reflecting/Relaying Surface-Aided Secure Wireless Communications. IEEE Trans. Veh. Technol. 2024, 73, 532–543. [Google Scholar] [CrossRef]
- Cepheli, Ö.; Kurt, G.K. Efficient PHY layer security in MIMO-OFDM: Spatiotemporal selective artificial noise. In Proceedings of the 2013 IEEE 14th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Madrid, Spain, 4–7 June 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Furqan, H.M.; Hamamreh, J.; Arslan, H. Physical layer security for NOMA: Requirements, merits, challenges, and recommendations. arXiv 2019, arXiv:1905.05064. [Google Scholar]
- Zhang, W.; Lin, H.; Zhang, R. Detection of pilot contamination attack based on uncoordinated frequency shifts. IEEE Trans. Commun. 2018, 66, 2658–2670. [Google Scholar] [CrossRef]
- Kaelbling, L.P.; Littman, M.L.; Moore, A.W. Reinforcement learning: A survey. J. Artif. Intell. Res. 1996, 4, 237–285. [Google Scholar] [CrossRef]
- Xiao, L.; Li, Y.; Dai, C.; Dai, H.; Poor, H.V. Reinforcement learning-based NOMA power allocation in the presence of smart jamming. IEEE Trans. Veh. Technol. 2017, 67, 3377–3389. [Google Scholar] [CrossRef]
- Xiao, L.; Sheng, G.; Liu, S.; Dai, H.; Peng, M.; Song, J. Deep reinforcement learning-enabled secure visible light communication against eavesdropping. IEEE Trans. Commun. 2019, 67, 6994–7005. [Google Scholar] [CrossRef]
- Pelechrinis, K.; Iliofotou, M.; Krishnamurthy, S.V. Denial of service attacks in wireless networks: The case of jammers. IEEE Commun. Surv. Tutor. 2010, 13, 245–257. [Google Scholar] [CrossRef]
- Mirkovic, J.; Reiher, P. A taxonomy of DDoS attack and DDoS defense mechanisms. ACM Sigcomm Comput. Commun. Rev. 2004, 34, 39–53. [Google Scholar] [CrossRef]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Syverson, P. A taxonomy of replay attacks [cryptographic protocols]. In Proceedings of the Computer Security Foundations Workshop VII, Franconia, NH, USA, 14–16 June 1994; pp. 187–191. [Google Scholar]
- Bae, J.; Kwek, L.C. Quantum state discrimination and its applications. J. Phys. Math. Theor. 2015, 48, 083001. [Google Scholar] [CrossRef]
- 5G Americas. The Evolution of Security in 5G, a Slice of Mobile Threats; 5G Americas: Bellevue, MA, USA, 2019. [Google Scholar]
- Liao, H.J.; Lin, C.H.R.; Lin, Y.C.; Tung, K.Y. Intrusion detection system: A comprehensive review. J. Netw. Comput. Appl. 2013, 36, 16–24. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine learning and deep learning methods for cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Aldweesh, A.; Derhab, A.; Emam, A.Z. Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues. Knowl. Based Syst. 2020, 189, 105124. [Google Scholar] [CrossRef]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A survey on zero trust architecture: Challenges and future trends. Wirel. Commun. Mob. Comput. 2022, 2022, 6476274. [Google Scholar] [CrossRef]
- Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero Trust Architecture (ZTA): A Comprehensive Survey. IEEE Access 2022, 10, 57143–57179. [Google Scholar] [CrossRef]
- Vanickis, R.; Jacob, P.; Dehghanzadeh, S.; Lee, B. Access Control Policy Enforcement for Zero-Trust-Networking. In Proceedings of the 2018 29th Irish Signals and Systems Conference (ISSC), Belfast, UK, 21–22 June 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Salahdine, F.; Kaabouch, N. Social engineering attacks: A survey. Future Inter. 2019, 11, 89. [Google Scholar] [CrossRef]
- Weaver, A. Biometric authentication. Computer 2006, 39, 96–97. [Google Scholar] [CrossRef]
- Arnau-González, P.; Katsigiannis, S.; Arevalillo-Herráez, M.; Ramzan, N. BED: A new data set for EEG-based biometrics. IEEE Internet Things J. 2021, 8, 12219–12230. [Google Scholar] [CrossRef]
- Arteaga-Falconi, J.S.; Al Osman, H.; El Saddik, A. ECG authentication for mobile devices. IEEE Trans. Instrum. Meas. 2015, 65, 591–600. [Google Scholar] [CrossRef]
- Zeuner, J.; Pitsios, I.; Tan, S.H.; Sharma, A.N.; Fitzsimons, J.F.; Osellame, R.; Walther, P. Experimental quantum homomorphic encryption. Npj Quantum Inf. 2021, 7, 25. [Google Scholar] [CrossRef]
- Fei, T.; Wang, W. The vulnerability and enhancement of AKA protocol for mobile authentication in LTE/5G networks. Comput. Net. 2023, 228, 109685. [Google Scholar] [CrossRef]
- Du, M.; Ma, X.; Zhang, Z.; Wang, X.; Chen, Q. A review on consensus algorithm of blockchain. In Proceedings of the 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Banff, AB, Canada, 5–8 October 2017; pp. 2567–2572. [Google Scholar] [CrossRef]
- Schär, F. Decentralized Finance: On Blockchain- and Smart Contract-Based Financial Markets. In Proceedings of the Federal Reserve Bank of St. Louis Review, Second Quarter 2021, 31 March 2021. pp. 153–174. Available online: https://ssrn.com/abstract=3571335 (accessed on 30 May 2024).
- Cinque, M.; Esposito, C.; Russo, S. Trust Management in Fog/Edge Computing by Means of Blockchain Technologies. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canda, 30 July–3 August 2018; pp. 1433–1439. [Google Scholar] [CrossRef]
- Zhaofeng, M.; Xiaochang, W.; Jain, D.K.; Khan, H.; Hongmin, G.; Zhen, W. A Blockchain-Based Trusted Data Management Scheme in Edge Computing. IEEE Trans. Ind. Inform. 2020, 16, 2013–2021. [Google Scholar] [CrossRef]
- Krummacker, D.; Veith, B.; Lindenschmitt, D.; Schotten, H.D. DLT architectures for trust anchors in 6G. Ann. Telecommun. 2023, 78, 551–560. [Google Scholar] [CrossRef]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tripi, G.; Iacobelli, A.; Rinieri, L.; Prandini, M. Security and Trust in the 6G Era: Risks and Mitigations. Electronics 2024, 13, 2162. https://doi.org/10.3390/electronics13112162
Tripi G, Iacobelli A, Rinieri L, Prandini M. Security and Trust in the 6G Era: Risks and Mitigations. Electronics. 2024; 13(11):2162. https://doi.org/10.3390/electronics13112162
Chicago/Turabian StyleTripi, Giulio, Antonio Iacobelli, Lorenzo Rinieri, and Marco Prandini. 2024. "Security and Trust in the 6G Era: Risks and Mitigations" Electronics 13, no. 11: 2162. https://doi.org/10.3390/electronics13112162
APA StyleTripi, G., Iacobelli, A., Rinieri, L., & Prandini, M. (2024). Security and Trust in the 6G Era: Risks and Mitigations. Electronics, 13(11), 2162. https://doi.org/10.3390/electronics13112162












