Abstract
With superior computing power and efficient data collection capability, Internet of Medical Things (IoMT) significantly improves the accuracy and convenience of medical work. As most communications are over open networks, it is critical to encrypt data to ensure confidentiality before uploading them to cloud storage servers (CSSs). Public key encryption with keyword search (PEKS) allows users to search for specific keywords in ciphertext and plays an essential role in IoMT. However, PEKS still has the following problems: 1. As a semi-trusted third party, the CSSs may provide wrong search results to save computing and bandwidth resources. 2. Single-keyword searches often produce many irrelevant results, which is undoubtedly a waste of computing and bandwidth resources. 3. Most PEKS schemes rely on bilinear pairings, resulting in computational inefficiencies. 4. Public key infrastructure (PKI)-based or identity-based PEKS schemes face the problem of certificate management or key escrow. 5. Most PEKS schemes are vulnerable to offline keyword guessing attacks, online keyword guessing attacks, and insider keyword guessing attacks. We present a certificateless verifiable and pairing-free conjunctive public keyword searchable encryption (CLVPFC-PEKS) scheme. An efficiency analysis shows that the performance advantage of the new scheme is far superior to that of the existing scheme. More importantly, we provide proof of security under the standard model (SM) to ensure the reliability of the scheme in practical applications.
1. Introduction
The Internet of Things can connect any item to the Internet. It uses information-sensing devices such as radio frequency identification and infrared sensors to transmit data and communicate according to specific protocols, thus realizing intelligent identification, positioning, tracking, monitoring, and management functions [,,]. As shown in Figure 1, as an application of Internet of Things technology in the medical field, IoMT [] can closely connect medical staff, patients, and various medical devices to achieve real-time feedback on patient health status. It not only improves the speed of medical response and provides all-weather medical care but also alleviates the workload of medical staff. IoMT improves the precision and convenience of medical work, leading to a better quality of medical care. IoMT also plays a significant role in saving lives, helping to control costs, and improving efficiency.
Figure 1.
System model of IoMT.
Electronic medical records (EMRs) [,] play a crucial role in IoMT. With the acceleration of the digitization of medical data, the amount of EMR data has increased rapidly. Storing and managing EMRs has become a significant challenge. Fortunately, cloud computing technology offers a solution to this challenge. Hospitals can store EMRs in the cloud, eliminating the cost of local management and maintenance and enabling efficient data sharing and utilization.
Because EMRs contain private patient information, they often need to be encrypted to ensure patient privacy. However, this encryption method makes it inconvenient for users to search for specific keywords in EMRs. The simplest solution is for users to download all the ciphertext data, decrypt them individually, and then search among them. This approach is impractical. It leads to exceedingly high computational and communication costs. To solve this problem, researchers have proposed searchable encryption (SE) [] technology. SE is an encryption primitive that allows users to perform keyword searches on encrypted data.
In reality, we are more likely to encounter multi-data owner scenarios, such as a patient’s EMR, that often need to be co-managed by multiple doctors, departments, or healthcare organizations. If each party independently owns some of the data in an EMR, this scenario is a non-shared multi-owner scenario []. If, on the other hand, multiple parties jointly own the data of an EMR, then this scenario is a shared multi-owner scenario []. In a non-shared multi-owner scenario, each staff member is responsible for a specific portion of the EMR. Each part of the data is a separate record, requiring independent computation of indexes and signatures. This processing will result in a linear increase in the cost of storing indexes and signatures as the number of owners increases, as well as an increase in verification and encryption time, thus significantly increasing the overall computation and storage costs. In contrast, the shared multi-owner scenario allows multiple owners to sign on the same EMR, ultimately generating a multi-signature. The size of the multi-signature is constant and independent of the number of owners. Therefore, the verification time and storage overhead of signatures are independent of the number of owners. For indexing in the shared multi-owner setup, the whole EMR is given only a single index through which the retriever can search the multi-owner EMR. In this way, the shared multi-owner significantly saves time and space costs, which makes it more advantageous in real-world applications. In recent years, some research works have also verified the advantages of the shared multi-owner setting. Miao et al. [] proposed a keyword-searchable encryption scheme with a hidden access policy under the shared multi-owner setting. Padhya et al. [] proposed a new key aggregation-searchable encryption scheme supporting sorted queries on encrypted datasets and a multi-keyword multidimensional search on multi-owner datasets. However, most PEKS solutions deployed in shared multi-owner scenarios face significant computational and storage costs.
The current PEKS scheme leaves much to be desired in terms of efficiency and security: PKI-based or identity-based cryptosystems encounter certificate management and key escrow problems during system deployment; the use of secure channels leads to inefficiency in the PEKS scheme; single-keyword searches inevitably produce many irrelevant results, leading to a waste of bandwidth and computational resources; CSS, as a semi-trusted third party, may provide incorrect search results to save computational and bandwidth resources; a large number of pairing operations puts a heavy computational burden on the system; the PEKS scheme is vulnerable to offline keyword-guessing attacks, online keyword-guessing attacks, and internal keyword-guessing attacks; most of the searchable encryption schemes are proven to be secure in the random oracle model (ROM) but the ROM is not suitable in the idealized model, resulting in security that cannot be fully guaranteed in practical applications; most searchable encryption schemes incur significant computational and storage costs when deploying PEKS schemes in non-shared multi-owner setups. In reality, it is necessary to solve the above problems, which provides a new direction for our research.
1.1. Our Contribution
We construct a certificateless-based, verifiable, pairing-free, conjunctive keyword search encryption scheme (CLVPFC-PEKS). Specifically, the main contributions are as follows:
- Conjunctive multi-keyword search: The new solution allows users to search for multiple keywords without increasing the number of trapdoors and ciphertexts, significantly improving the accuracy of search results.
- Verifiability of the search results: The new scheme attaches a signature to each document. The signature will then be used to verify the search results, ensuring the accuracy of the search results and preventing users from wasting time and resources on invalid results.
- Certificateless-based: The new scheme overcomes the limitations of certificate management and key escrow in existing searchable encryption schemes.
- No pairing: Pairing operations take time, so the computational efficiency can be significantly improved by not using pairing operations.
- No need for a secure channel: The new solution eliminates the need for a secure channel and reduces system construction costs.
- Shared multi-owner settings: The new scheme allows users to search for document sets shared by multiple users using a single trapdoor.
- Proven security under the standard model: The new scheme is secure against offline keyword guessing attacks and chosen keyword attacks (CKAs) in the standard model. Meanwhile, based on the security of the Diffie–Hellman shared secret keys, the new scheme can also resist online keyword guessing attacks (e.g., file injection attack (FIA)) and insider keyword guessing attacks (IKGAs).
In Table 1, we compare the features of PKES schemes. Currently, no SE scheme can provide result verification, can provide a conjunctive keyword search, is secure channel-free, is certificateless-based, is pairing-free, and can provide support for shared multi-owners simultaneously. In particular, none of the pairing-free SE schemes support result verification and conjunctive keyword searches.

Table 1.
Functional comparison.
1.2. Organization
The following is the framework for the rest of this article. We summarize some related work in Section 2. We discuss preparatory knowledge in Section 3. We define the system model and the security model of the scheme in Section 4. We show the details of the CLVPFC-PEKS scheme in Section 5. We discuss the security of the CLVPFC-PEKS scheme in Section 6. We analyze the effectiveness of CLVPFC-PEKS in Section 7. Finally, we summarize this paper in Section 8.
2. Related Work
In 2004, Boneh et al. [] first proposed the concept and construction of public key encryption with keyword search(PEKS), which laid the foundation for research in this field. However, the early PEKS schemes still had many shortcomings in efficiency and safety. Baek [] points out that the PEKS scheme of [] is inefficient because [] uses safe channels. To eliminate the requirement for secure channels, Baek et al. [] proposed PEKS without secure channels (SCF-PEKS), also known as PEKS with designated servers/testers (dPEKS) []. However, most SCF-PEKS schemes are PKI-based or ID-based, which inevitably incurs problems with certificate management and key escrow. To overcome these challenges, Peng et al. [], based on the certificateless cryptosystem [], proposed a keyword-searchable encryption scheme (CL-SCF-PEKS) without a secure channel. Since then, many papers have studied certificateless searchable encryption schemes, which inject new vitality into the development of this field. It is worth noting that most PEKS schemes [,,,,] search for a single keyword. However, this single-keyword search method often produces irrelevant results, wasting bandwidth and computing resources. Golle et al. [] proposed the first conjunctive keyword-searchable encryption scheme to address the issue of resource waste. Subsequently, more searchable encryption schemes that support conjunctive keywords have been proposed in recent years [,,].
Given that the computational complexity of pairing is much higher than that of scalar multiplication on the group of elliptic curves, designing schemes that do not require pairing will significantly improve the computational efficiency of the schemes. Current SE schemes that do not require pairing operations are still scarce, and these schemes [,,,,,,,,] remain to be improved. In 2019, Lu et al. [] proposed a PEKS scheme based on the certificateless cryptosystem, which is pairing-free, and proved the indistinguishability of keyword ciphertexts (CL-PF-PEKS). However, Ma et al. [] showed that the work of [] is insecure under user-simulated attacks and provided a new CL-PF-PEKS scheme. Recently, [,] proposed CL-PF-PEKS schemes that are both secure and effective, respectively, but unfortunately, they are single-keyword-searchable.
Existing SCF-PEKS schemes have significant shortcomings in terms of security, especially their vulnerability to offline keyword guessing attacks [], online keyword attacks (e.g., FIA) [,], and internal keyword attacks []. PEKS schemes typically use keywords from low-entropy spaces, making them vulnerable to offline keyword-guessing attacks. In this attack, both internal and external attackers can use a testing algorithm to accurately guess the keywords corresponding to the given keyword trapdoors. The attack works because the generation of trapdoors uses only keywords and public keys. Currently, the offline keyword guessing attack has become one of the most destructive attacks on PEKS schemes because it can lead to the leakage of encrypted data and information related to the keywords contained in the trapdoor. Unfortunately, Yang et al. [] showed that even after modifying the trapdoor structure of PEKS schemes, an attacker can still perform an online keyword guessing attack(e.g., FIA). Unlike external offline keyword attacks, external online keyword guessing attacks allow attackers to guess keywords by analyzing search results in the cloud in real time. Specifically, the external attacker first generates keyword ciphers and data ciphers containing all possible keywords and data ciphers using the public keys of the cloud server and the retriever and injects these ciphers into the cloud server. Subsequently, the external attacker monitors the communication between the cloud server and the retriever. Once the attacker finds that the search results returned by the server match the previously injected ciphertexts, they can determine the keywords that the retriever is searching for. In addition, the PEKS scheme is also vulnerable to internal malicious CSS attacks. Jeong et al. [] demonstrated that the PEKS framework is susceptible to internal offline keyword attacks initiated by malicious CSSs. Wang et al. [] pointed out that even though the trapdoor is indistinguishable, the SCF-PEKS scheme is still not able to defend against keyword-guessing attacks by malicious CSSs. More seriously, Shao et al. [] proposed a generic attack method and pointed out that it is almost impossible to construct a SCF-PEKS scheme that can defend against malicious CSSs. This is because malicious CSSs can perform keyword encryption and testing algorithms, making the SCF-PEKS scheme particularly vulnerable against offline keyword-guessing attacks from malicious internal servers.
In addition, CSSs, as semi-trusted entities, may selectively perform a few search operations and return some inaccurate search results to save computational and bandwidth resources. Therefore, PEKS schemes should provide an authentication mechanism to ensure the accuracy of search results without decryption. Reference [] proposed the first keyword-searchable encryption scheme that supports authentication. Since then, numerous researchers have explored keyword-searchable encryption schemes that support authentication [,,]. The authors of [] proposed a verifiable multiple keywords search(VMKS) scheme, claiming that it resists keyword guessing attacks under the standard model.
3. Preliminaries
Let be a large prime, be a prime field, and the elliptic curve E over the field satisfy the equation , where and . All points on E and the infinite point O form a cyclic group. The elliptic curve cryptosystem (ECC) has the following difficulties:
- The elliptic curve discrete logarithm problem (ECDLP): given , where P is the generator of the group and Q is the element in . It is difficult to calculate the integer k, such that , where .
- The elliptic curve computational Diffie–Hellman problem (ECDCHP): for any given in , it is difficult to calculate , where .
- The elliptic curve decisional Diffie–Hellman (ECDDDH) problem: given , where are unknown. The decisional Diffie–Hellman (DDH) problem is to decide whether X equals or a random element in G.
4. The System Model and Security Model of CLVPFC-PEKS
4.1. System Model
There are five core entities involved in the new scheme: the key generation center (KGC), the data owners (DOs, including patients and their doctors), CSSs, retrievers (e.g., authorized doctors or hospitals), and a private audit server (PAS), as shown in Figure 2.
- The KGC is responsible for generating the public parameters of the system and some of the private keys for the DOs, the CSSs, and the retrievers.
- DOs have many files to store and manage, but their resources and capabilities are limited. From the perspective of resource-saving and data security, the data owner chooses to upload the encrypted data files and indexes (keyword ciphertext) to the cloud storage server.
- The CSS, as a semi-trusted entity with powerful computing and storage capabilities, provides data storage and retrieval services to authorized cloud customers. When a retriever initiates a retrieval request, the cloud storage server looks up the keyword traps and returns the corresponding data files to the retriever.
- Retrievers can initiate a ciphertext retrieval request by sending a keyword trapdoor to the cloud storage server and decrypt the received ciphertext to obtain the required information.
- The PAS, as a fully trusted entity, is responsible for validating the search results to ensure that the data files received by the searcher are accurate.
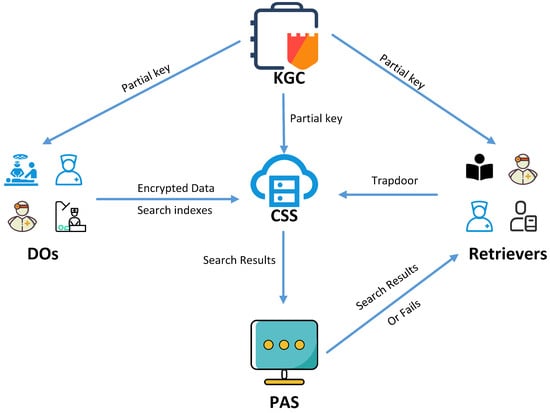
Figure 2.
System model of CLVPFC-PEKS.
The CSS is semi-trustworthy and curious. It may selectively perform a few search operations and provide some erroneous search results to conserve its resources. At the same time, CSSs try to snoop on valuable and sensitive information. The PAS is fully trusted to ensure the accuracy of search results. In addition, authorized retrievers can confidently initiate search requests without worrying about leaking valuable information to CSSs.
4.2. Solution Framework
To better understand the notations in our proposed scheme, Table 2 explains the pre-defined notations used throughout this paper. We set integer k as the security level and as the EMR file and the keyword set contained in EMR.

Table 2.
Notation descriptions.
Definition 1
(CLVPFC-PEKS). Our scheme is a tuple of six algorithms, as follows:
SetUp(): Given the security parameter k, the KGC outputs the public parameters Ω, the system public key , and the master secret key for the traditional public key algorithm.
KeyGen : For the data owner set O, the data user U, and the CSS, the KGC generates the public/secret key pairs ,, and , respectively.
Set-Secret-Value: After inputting the public parameters Ω, this probabilistic algorithm outputs data owners, data users, and CSS’s Secret-Value.
Partial-Private-Key-Extract: The KGC executes this algorithm, which accepts the identity of the data owner, data user, and CSS, then uses them in combination with the master key to generate a partial private key for the data owner, data user, and CSS.
Set-Private-Key: Set the full secret keys of the data owner, data user, and CSS.
Set-Public-Key: Set the full public keys of the data owner, data user, and CSS.
: DOs first conduct this probabilistic algorithm to generate the ciphertext set C for the set F. Then, DOs generate multiple signatures and index set I for ciphertext C. Then, they send the tuple to the CSS. ; given the keyword , the DO runs this algorithm to output trapdoor .
: Using the trapdoor as an input, the CSS matches it with the index set I, then returns the relevant ciphertext and signature set to PAS.
Verify : The PAS runs this algorithm by initiating interaction with the CSS to check the correctness of the search result . If passes the result validation, the PAS will return it to the retriever. Otherwise, it will abort the algorithm.
4.3. Security Model
Our scheme primarily considers security in the following two aspects: (1) The index corresponding to the keyword has security against choice keyword attacks. (2) The trapdoor used for queries should possess security.
Because our scheme is certificateless-based, there are two different classes of adversaries: and . Therefore, when discussing the security of the index and trapdoor, we must analyze and prove them from the angles of these two adversaries.
: does not know the master key, but can replace any user’s public key.
: knows the master key, but cannot replace any user’s public key.
We call these adversaries the adversary of type-1 and the adversary of type-2.
Mahmoud Ismail et al. [] articulated the basic principles of the zero-trust framework, delved into the threat landscape facing IoT systems, and assessed how the zero-trust principle can effectively address these threats. Jamal A. Alenizi et al. [] investigated various risks and vulnerabilities that may affect the operation of blockchain-based smart healthcare systems, especially ransomware, and proposed a framework for mitigating healthcare ransomware attacks. The framework proposed by Jamal A. Alenizi et al. has higher computational efficiency and lower communication overhead than similar existing frameworks.
4.3.1. Ciphertext Indistinguishability against Chosen Keyword Ciphertext Attack
A PEKS scheme with ciphertext indistinguishability against chosen keyword and ciphertext attacks (CKCA-CIND) feature can protect the data owner’s keyword ciphertext stored in the cloud from revealing relevant keyword information. When encrypted data are stored in the CSS, it will attach the corresponding keywords . Even if the keyword ciphertext is captured during transmission, no adversary can obtain keywords embedded in the keyword ciphertext.
We will define the definition of CKCA-CIND. There are two games to discuss the security of CKCA-CIND.
Game 1.
simulates malicious users, and B is the challenger. B and play this game together.
Setup: B runs the SetUp() program to obtain , and . B sends to and keeps . Then, B sets the key pair of and CSS, i.e., and . B sends the public keys and to , while and are unknown to .
Phase 1. executes the User-Public-Key query before executing other queries. It sets up lists to store the above queries and answers. All lists are initially empty. makes the queries to challenger B as follows:
- User-Public-Key query: When inputs the identity , B outputs the user’s public key .
- Replace-Public-Key query: inputs , B replaces with .
- Secret-Value query: When inputs the identity , B returns the secret value corresponding to the . If is replaced, B refuses to answer.
- Partial-Private-Key-Extract query: When enters the , if ( is the challenge identity), B fails and stops. Otherwise, B returns the corresponding Partial-Private-Key.
- Keyword Ciphertext Query: asks B for the keyword ciphertext of any keyword W it cares about. B runs the algorithm to answer W’s keyword ciphertext .
- Keyword Trapdoor Query: sends a keyword to B. B runs the algorithm to answer ’s trapdoor .
- Test Query: selects and sends the keyword ciphertext and trapdoor to B. B executes the algorithm to return the test result of whether the keyword ciphertext and the trapdoor match.
Challenge: submits a tuple to B, where and are challenging keywords not asked in the previous trapdoor and keyword ciphertext query. If , B aborts. Otherwise, B picks , randomly computes the keyword ciphertext , and returns the challenge ciphertexts to .
Phase 2. can perform many queries like Phase 1, but cannot query the keyword ciphertext and trapdoor of and .
Guess: outputs . wins if . Otherwise, it fails.
Next, the advantages of in Game 1 are given as
Game 2.
simulates the malicious server, and B is a challenger. B and play this game together. Setup: It only differs from the setup of Game 1 in the following steps. B sends the public keys , , and to , and is unknown to .
Phase 1. The steps are the same as in Phase 1 of Game 1, except for the Secret-Value query and Partial-Private-Key query. The changes in them are as follows:
- Secret-Value query: When enters the , if ( is the challenge identity), B fails and stops. Otherwise, B returns the secret value corresponding to .
- Partial-Private-Key-Extract query: When inputs the identity , B returns the partial private key corresponding to the . If is replaced, B refuses to answer.
Phase 2. Same as Phase 2 of Game 1.
Next, the advantages of in Game 2 are given as
Definition 2
(Security of CKCA-CIND). If the probability that any adversary will win the above two games in polynomial time is negligible, then we state that the CLVPFC-PEKS scheme is CKCA-CIND safe.
4.3.2. Safety of Trapdoor
The attack methods on the trapdoor include offline keyword-guessing attacks, online keyword-guessing attacks, and insider keyword-guessing attacks.
We first discuss how to defend against offline keyword-guessing attacks. References [,,] have made efforts to resist offline keyword-guessing attacks. They modified the structure of the trapdoor and claimed that if the attacker did not know the server’s private key or the receiver’s private key, then the scheme would be resistant to offline keyword-guessing attacks by external attackers. In [], the concept of trapdoor indistinguishability under a choose keyword attack (CKA-TIND) is proposed, and it is proven that CKA-TIND is a sufficient condition to prevent offline keyword guessing attacks. At the same time, ref. [] proposes a dPEKS scheme with trapdoor indivisibility. The above schemes are proven safe in the random oracle model, but the proof that the scheme is safe in the random oracle model does not necessarily mean that the scheme is safe in reality. Fang et al. [] proposed a new SCF-PEKS scheme that has no random prediction and asserts that the scheme can safely resist offline keyword guessing attacks by external attackers. However, Lu et al. [] pointed out that Fang’s scheme is insecure under the keyword guessing attack of external attackers.
In the following, we define the concept of CKA-TIND of CLVPFC-PEKS.
Game 3.
simulates malicious users, and B is the challenger. B and play this game together.
Setup: B runs the SetUp() program to obtain , and . B sends to and keeps secret. Then, B sets the key pair of the date user and CSS, i.e., and . Challenger B sends the public key and to , while and are unknown to .
Phase 1. executes the User-Public-Key query before executing other queries. The setup lists store the above queries and answers. All lists are initially empty. makes the queries to challenger B as follows:
- User-Public-Key query: When inputs the identity , B outputs the user’s public key .
- Replace-Public-Key query: Same as in Game 1.
- Secret-Value query: Same as in Game 1.
- Partial-Private-Key-Extract query: When enters the , if ( is the challenge identity), B fails and stops. Otherwise, B returns the corresponding Partial-Private-Key.
- Keyword Ciphertext Query: Same as in Game 1.
- Keyword Trapdoor Query: Same as in Game 1.
- Test Query: Same as in Game 1.
Challenge: submits a tuple ) to B, where and are challenging keywords that were not asked in the previous trapdoor and keyword ciphertext query. If , B aborts. Otherwise, B picks , randomly computes keyword trapdoor , and returns the challenge trapdoor to the adversary .
Phase 2. can perform many queries like Phase 1, but cannot query the keyword ciphertext or trapdoor of and .
Guess: outputs . Adversary wins if . Otherwise, it fails.
Next, the advantages of in Game 3 are given as
Game 4.
simulates the malicious server, and B is a challenger. B and play this game together.
Setup: This differs from the setup of Game 3 only in the following steps. B sends , , and to , and is unknown to .
Phase 1. The steps are the same as in Phase 1 of Game 3, except for the Secret-Value and Partial-Private-Key-Extract queries. The changes in them are as follows:
- Secret-Value query: When enters the , if ( is the challenge identity), B fails and stops. Otherwise, B returns the secret value corresponding to .
- Partial-Private-Key-Extract query: Same as in Game 2.
Phase 2. Same as Phase 2 of Game 3.
Next, the advantages of in Game 4 are given as
Definition 3
(Security of CKA-TIND). If the probability that any adversary will win the above two games in polynomial time is negligible, then we state that the CLVPFC-PEKS scheme is CKA-TIND safe.
Next, we will discuss how to resist online/insider keyword-guessing attacks. Lu et al. [] pointed out that the main reason for vulnerability to online keyword-guessing attacks is that any opponent can generate legitimate ciphertext for keywords. Shao et al. [] pointed out that SCF-PEKS inherently suffers from insider keyword-guessing attacks because malicious servers can run keyword encryption algorithms and test algorithms at the same time. To resist the above two attacks, Wu et al. [] proposed a searchable public key encryption (SPE-PP) scheme with a privacy protection function. In their plan, the Diffie–Hellman shared secret key is required for the generation of the keyword ciphertext and trapdoor. Specifically, the sender uses the shared key to calculate each keyword ciphertext, while the receiver uses the shared key to generate a trapdoor. An internal adversary (such as a malicious cloud server) cannot obtain the Diffie–Hellman shared secret key, so they cannot construct legal ciphertext to match the trapdoors sent by retrievers for testing. Then, internal adversaries will not be able to implement insider keyword-guessing attacks. On the other hand, only the retriever can use the Diffie–Hellman shared secret key to generate a legitimate trapdoor for each keyword, and the adversary of online keyword guessing cannot obtain the Diffie–Hellman shared secret key. Then, they cannot construct a legal trapdoor to upload to the cloud server. Even if they monitor all the files obtained by the retriever under the public channel, they cannot obtain any keyword-related information through comparison. In conclusion, the reason why the searchable encryption scheme can resist online and insider keyword-guessing attacks is that the keyword ciphertext is embedded in the shared key generated by the sender’s private key and the receiver’s public key.
In this section, we conduct a comprehensive analysis of the security of the scheme, focusing primarily on the security of the trapdoor and keyword ciphertext. The security of the keyword ciphertext only needs to demonstrate that the scheme is resistant to chosen keyword ciphertext attacks. Trapdoor security is categorized into three aspects: security against offline keyword-guessing attacks, security against online keyword-guessing attacks, and security against internal keyword-guessing attacks. Because CKCA-CIND is a sufficient condition to prevent offline keyword guessing attacks, as long as the scheme is trapdoor-indistinguishable under the chosen keyword attack, then the scheme is secure against the offline keyword guessing attack. Also, as long as the shared key embedded in the keyword ciphertext is generated from the sender’s private key and the receiver’s public key, the PESK scheme is resistant to both online keyword attacks and internal keyword guessing attacks.
5. The Proposed CLVPFC-PEKS
This system uses a traditional public key encryption algorithm for keywords. However, we will not discuss them in detail here. Therefore, the following algorithms focus mainly on indexing and signature.
SetUp : Given a security parameter k, this deterministic algorithm outputs the global public parameters and KGC’s master secret key (). Given k, the KGC performs as follows:
- Choose a k bit prime number q and determine the tuple , where the point P is the generator of .
- Choose a number and compute the system public key . Set . Let .
- Select five hash functions ,,, , .
- Let .
KeyGen : Let each EMR have a fixed number of data owners . KGC generates the public/secret key pairs for the CSS, data owner , and retriever U.
- Set-Secret-Value: The participant with selects an element and generates the corresponding public key .
- Extract-Partial-Private-Key: To obtain the partial private key, the user sends to the KGC, and then the KGC executes the extraction as in the following steps.
- –
- Taking the participant’s as input, a random number is selected by KGC and calculates .
- –
- The KGC computes . The partial private key of the participant with is . The participant with can verify their partial private key by checking whether the equation holds, where . If the above equation is true, then the private key is accepted.
- Set-Private-Key: The partial private key of the participant with takes the pair as their full private key.
- Set-Public-Key: The participant with takes as their full public key.
Enc:
Step 1: Given the EMR set with corresponding identities , it will be encrypted as the ciphertext set through the traditional public key encryption algorithm. To generate the multi-signature on the encrypted file , each signer does the following:
- chooses a number and computes .
- broadcasts to other members of the group.
- Computes , , .
- Computes and .
- computes , generates a signature for , and then sends to the designated clerk .
- Upon receiving , computes and outputs the signature . Let , where .
Step 2: All users specify a user to generate an index, for example, . runs this algorithm to generate the index of file set F. Given the keyword set W, builds an index for each file . The index for each is generated based on the keyword field , where m is a fixed integer. randomly selects and calculates to through public key encryption. computes and sends it to through public key encryption. computes and sends it to through public key encryption, and so on until computes and sends it to through public key encryption. calculates , and calculates in the same way as . Let , . Construct an m-degree polynomial with the following equation:
so is the root of equation , where . Then, selects and computes , set , , , and the index set is , where . Finally, sends I to CSS.
TrapGen: The DO calculates the value of as follows: , , . Given the queried keywords set , the DO U first select an element and set ,
, where , . Finally, they send to the CSS.
Test: After gaining the search token , the CSS computes fist, and then verifies whether Equation (1) holds.
If Equation (1) holds, the CSS will return the relevant ciphertext set and its corresponding identity set to PAS. Otherwise, it returns ⊥. The specific test process is shown in Algorithm 1.
| Algorithm 1: Search over encrypted data | |
|
Input: Trapdoor , index I, ciphertext C, secret key , and public parameters . Output: Search results and corresponding identity set or ⊥.
| |
Verify : After receiving the search results , PAS computes the proof information and . Finally, PAS verifies whether Equation () holds. The specific verify process is shown in Algorithm 2.
| Algorithm 2: Results verification. | |
|
Input: Search results with corresponding identity set , public key set , signature , and public parameters , where . Output: “Accept” or “Reject”
| |
6. Security of Scheme
We will analyze the correctness and security of the CLVPFC-PEKS scheme in this section.
6.1. Correctness
Theorem 1.
The CLVPFC-PEKS scheme is computationally consistent.
Proof.
For the correctness of our CLVPFC-PEKS scheme, we do two things. First, we illustrate that the CSS can effectively ascertain a match between the keyword ciphertext’s index and the trapdoor when the keyword set , where is a set of keywords searched by a specific user and W is the keyword set of ciphertext. Subsequently, we elucidate that, given that the search outcomes successfully traverse the established result verification protocol, retrievers can ascertain the accuracy of the search results.
During the test phase, the CSS obtains the index and trapdoor . The CSS starts performing computations.
.
If , then are the root of the equation , where . Thus,
Equation (1) is satisfied, and thereby CSS can correctly test whether the keyword ciphertext matches the trapdoor.
In the test phase, the PAS obtains signature and ciphertext , computing
obtaining the proof information , and then continuing to calculate
.
If , then
where . So we have . Equation (2) in program 2 holds. We can also make sure that the ciphertext cannot be modified. □
6.2. Security
Lemma 1.
Assuming that adversary can triumph in Game 1, then it is feasible to devise algorithm B, aimed at resolving the ECDDDH problem.
Proof.
Let us hypothesize that the tuple constitutes an instance of the ECDDDH problem. In order to ascertain whether , algorithm B will assume the role of the challenger.
Setup: B executes the setup procedure to obtain public parameters along with and . B then forwards the parameter to while keeping secret. B selects , randomly and sets
, ,, and .
B sends , , and to , but and are unknown to .
Phase 1: Prior to conducting other queries, execute the user’s public key query utilizing the identity . Set up multiple lists to record the queries and corresponding responses. Each list starts off empty.
For a user public key query, B keeps a list of the tuple and, upon receiving an identity , performs the following steps.
Case 1. . , setting , and adding the tuple to the list , where ⟡ represents a null value.
Case 2. . B randomly chooses two different numbers , setting , and adds the tuple to the list .
Replace-Public-Key query: B keeps a list of tuple . When inputs , B replaces with and adds to the list .
Secret-Value query: When receives the request for the secret value associated with , B finds in the list and returns . If is replaced, B refuses to answer.
Partial-Private-Key query: B establishes a list of tuple when asks for the partial private key of . If , B fails and stops. Otherwise, B finds in the list , and runs the Extract-Partial-Private-Key algorithm, generating . B outputs and adds to the list .
Keyword Ciphertext Query: When asks for the keyword ciphertext, B operates the algorithm to generate keyword ciphertext .
Keyword Trapdoor Query: When asks for the trapdoor, B operates the algorithm to generate the trapdoor .
Test Query: gives the keyword ciphertext and keyword trapdoor , and B compares them using Algorithm 1.
Challenge: submits a tuple to B, where and are challenging keywords not requested in the previous trapdoor and keyword ciphertext query. If , B aborts. Otherwise, , B calculates and picks randomly. B computes
Let , which can obtain by combining similar terms. Then, B selects and computes . Set , . Thus, the corresponding keyword ciphertext of is . B returns the challenge ciphertexts to the adversary .
Phase 2: can continue to execute various queries, but there is a limitation that is not allowed to query the keyword ciphertext or trapdoor of or .
Guess: returns .
Solve CDH problem: If , B returns 1, otherwise 0. If , then
Therefore, is a valid keyword ciphertext. Suppose that the advantage of winning in the above game is . So,
.
If , then is an invalid keyword ciphertext. has no advantage in distinguishing from . Hence,
.
Probability: Let , and be the number of the user public key query, Replace-Public-Key query, and the Partial-Private-Key query, respectively. The two events are as follows:
: did not replace ’s public key and queried the partial-private-key for .
: .
It is not hard to obtain the following results.
,
, .
If wins Game 1 with an advantage of , then B has a probability greater than to determine whether . □
Lemma 2.
Assuming that adversary can win Game 2, algorithm B can constructed to solve the ECDDDH problem by exploiting the adversary’s ability.
Proof.
Suppose that the tuple is an example of an ECDDDH problem. To determine whether , B will play the part of the challenger.
Setup: B runs the setup program to obtain public parameters and . B selects , randomly, and sets
, ,, ,
B sends , , and to , while are unknown to .
Phase 1: Execute the user’s public key query before other queries using the identity . Set up multiple lists to store the queries and answers. All lists are initially empty.
User public key query: B maintains a list containing the tuple and takes the following actions when receiving an identity :
Case 1. . B chooses a number at random, sets , and adds the tuple to the list , where ⟡ represents a null value.
Case 2. . B chooses at random, sets , and adds the tuple to the list .
Replace-Public-Key query: Same as in Lemma 1.
Secret-Value query: B established a list of tuple . When asks the secret value for . If , B fails and stops. Otherwise, B finds in list , and returns .
Partial-Private-Key query: When asks the partial private key of , B finds in list , running the Extract-Partial-Private-Key algorithm and returning . If is replaced, B refuses to answer.
Keyword Ciphertext Query: Same as in Lemma 1.
Keyword Trapdoor Query: Same as in Lemma 1.
Test Query: Same as in Lemma 1.
Challenge: submits a tuple that meets the requirements of Game 2, where and are challenging keywords not asked in the previous trapdoor query and keyword ciphertext query. If , B aborts. Otherwise, , B computes , and picks randomly. B computes
.
Let , which can obtain by combining similar terms. Then, select at random and compute . Set , , and thus ’s keyword ciphertext is . B returns the challenge ciphertexts to the adversary .
Phase 2: Attacker can continue to execute various queries, but there is a limitation that attacker is not allowed to query the keyword ciphertext or trapdoor of or .
Guess: returns .
Solve the ECDDDH problem. If , B returns 1. Otherwise, 0. If , then
Therefore, is a valid keyword ciphertext. Suppose that the advantage of wins in the above game is , so
.
If , then is an invalid keyword ciphertext. has no advantage in distinguishing from . Hence,
.
Probability: Let , , be the number of user public key queries, Replace-Public-Key queries, and Secret-Value queries, respectively. The two events are as follows:
: did not replace ’s public key nor perform the Secret-Value query for .
: .
It is not hard to obtain the following results.
,
,
.
If has an advantage to win the game, then B has a probability greater than to determine whether . □
Theorem 2.
Our CLVPFC-PEKS scheme is CKCA-CIND secure in a standard model if the ECDDDH problem is hard.
Proof.
Theorem 2 holds from Lemma 1 and Lemma 2. □
Lemma 3.
Assuming the adversary can win Game 3, then algorithm B can be constructed to solve the ECDDDH problem.
Proof.
Suppose that the tuple is an example of an ECDDDH problem. To determine whether , B will play the part of the challenger.
Setup: B runs the setup program to obtain the public parameters , where and . Then, B randomly selects , and sets
, , ,
,
.
B sends , and to , but and are unknown to .
Phase 1: Execute the user’s public key query before other queries using the identity . Set up multiple lists to store the queries and answers. All lists are initially empty.
User public key query: B keeps a list of the tuple , and upon receiving an identity , performs the following steps.
Case 1. , B randomly chooses a number , setting , and adds the tuple to the list , where ⟡ represents a null value.
Case 2. , B randomly chooses two different numbers , setting , and adds the tuple to the list .
Replace-Public-Key query: Same as in Lemma 1.
Secret-Value query: Same as in Lemma 1.
Partial-Private-Key query: B establishes a list of tuple when asks for the partial private key of . If , B fails and stops. Otherwise, B finds in the list , and runs the Extract-Partial-Private-Key algorithm, generating . B outputs and adds to the list .
Keyword Ciphertext Query: Same as in Lemma 1.
Keyword Trapdoor Query: Same as in Lemma 1.
Test Query: Same as in Lemma 1.
Challenge: submits a tuple , where and are challenging keywords that are not requested in the previous trapdoor and keyword ciphertext query. If , B aborts. Otherwise, . Without losing generality, it is better to set as . B calculates . B picks randomly, and computes
B selects an element and sets ,
, where . Finally, B sends to the adversary .
Phase 2: Attacker can continue to execute various queries, but there is a limitation that attacker is not allowed to query the keyword ciphertext or trapdoor of or .
Guess: returns .
Solve CDH problem: If , B returns 1, otherwise 0. If , then
.
Therefore, is a valid keyword ciphertext. Suppose that the advantage of winning in the above game is . So,
.
If , then is an invalid trapdoor. has no advantage in distinguishing from . Hence,
.
Probability: Let , , and be the number of the User public key queries, Replace-Public-Key queries, and Partial-Private-Key queries, respectively. The two events are as follows:
: did not replace ’s public key and queries the partial-private-key for .
: .
It is not hard to obtain the following results.
,
,
.
If wins Game 1 with an advantage of , then B has a probability greater than to determine whether . □
Lemma 4.
Assuming that adversary can win Game 4, then algorithm B can be constructed to solve the ECDDDH problem.
Proof.
Suppose that the tuple is an example of an ECDDDH problem. To determine whether , B will play the part of the challenger.
Setup: B runs the setup program to obtain the public parameters , where and . Then, it randomly selects , and sets
, , ,
,
B sends , , and to , while are unknown to .
Phase 1: Execute the user’s public key query before other queries using the identity . Set up multiple lists to store the queries and answers. All lists are initially empty.
User public key query: B keeps a list of the tuple , and upon receiving an identity , performs the following steps.
Case 1. , B randomly chooses a number , setting , and adds the tuple to the list , where ⟡ represents a null value.
Case 2. , B randomly chooses two different numbers, , setting , and adds the tuple to the list .
Replace-Public-Key query: Same as in Lemma 1.
Secret-Value query: B establishes a list of tuple . When asks the secret value of , if , B fails and stops. Otherwise, B finds in the list , and returns . If is replaced, B refuses to answer.
Partial-Private-Key query: Same as in Lemma 2.
Keyword Ciphertext Query: Same as in Lemma 1.
Keyword Trapdoor Query: Same as in Lemma 1.
Test Query: Same as in Lemma 1.
Challenge: submits a tuple , where and are challenging keywords not requested in the previous trapdoor and keyword ciphertext query. If , B aborts. Otherwise, without losing generality, it is better to set as . B calculates . B picks randomly, and computes
B selects an element and sets ,
, where . Finally, B sends to adversary .
Phase 2: Attacker can continue to execute various queries, but there is a limitation that attacker is not allowed to query the keyword ciphertext or trapdoor of or .
Guess: returns .
Solve CDH problem: If , B returns 1, otherwise 0. If , then
.
Therefore, is a valid keyword ciphertext. Suppose that the advantage of winning the above game is . So,
.
If , then is an invalid keyword ciphertext. has no advantage in distinguishing from . Hence,
.
Probability: Let , , and be the number of user public key queries, Replace-Public-Key queries, and Secret-Value queries, respectively. The two events are as follows:
: did not replace ’s public key and queries the secret value for .
: .
It is not hard to obtain the following results.
,
,
.
If wins Game 4 with an advantage of , then B has a probability greater than to determine whether . □
Theorem 3.
Our CLVPFC-PEKS scheme is CKA-TIND safe in the standard model if the ECDDDH problem is hard.
Proof.
Theorem 3 holds from Lemma 3 and Lemma 4. □
Theorem 4.
Under the ECDLP assumption, it is not computationally feasible for the CSS to forge valid proof information through the result verification mechanism.
Proof.
The malicious CSS cannot forge a valid multi-signature on each returned record and pass the verification. Since it does not have the key of multiple data owners, it is computationally infeasible to forge a valid multi-signature. Therefore, the malicious CSS can only win the next security game by directly generating valid proof information according to the wrong search result instead of winning the next security game by forging multiple signatures. But, after the following analysis, this is also impossible.
Assume that the correct keyword ciphertext and its identity are and , where . The malicious CSS may forge wrong proof information on false search results , where
,
.
If the forged proof information can successfully pass the result verification mechanism, the malicious CSS will win the security game; otherwise, it will fail. Suppose a malicious CSS wins the game. We then know that
The proof information of the correct keyword ciphertext C is , where
,
.
The signature of the correct keyword ciphertext can pass the verification mechanism, so we have
Because is not equal to , then or . Set , , then or . Suppose is not zero, then . If the probability of is , then the probability that we can break the ECDLP problem is , where q is the length of . This means that if the malicious CSS can pass the verification, we can break the ECDLP problem. □
7. Performance Analysis
We will compare our scheme in depth with other certificateless-based or verifiable search schemes on computational complexity, storage overhead, and security.
7.1. Security Comparison
Table 3 details the comparison of our scheme with other schemes in terms of security, where RCCA denotes that the scheme resists the chosen ciphertext attack, ROFFKGA stands for resists the offline keyword guessing attack, RONKGA stands for resists the online keyword guessing attack, RIKGA denotes that the scheme protects against the insider keyword guessing attack, VER denotes that the scheme prevents malicious CSSs from returning incorrect search results, and PM denotes the model used for the proof. In Table 3, yes indicates that the scheme satisfies the property, no implies that it does not meet the property, unknown denotes that it is unknown (the scheme has neither been proven safe nor unsafe because of the lack of security proof), and “-” means that the scheme does not have the feature.

Table 3.
Comparison of security of different schemes.
It is clear from Table 3 that our solution has significant security advantages. Specifically, Theorem 2 shows that the new scheme is resistant to the adaptive keyword selection attack in the standard model, i.e., the new scheme is ciphertext-indistinguishable. Theorem 3 shows that our scheme is secure against offline keyword-guessing attacks in the standard model. Theorem 4 shows that our scheme prevents malicious CSSs from returning incorrect search results. Wu et al. [] constructed a PEKS scheme that can resist online keyword attacks and insider keyword guessing attacks based on the security of the Diffie–Hellman shared secret key. The new scheme’s shared key is only accessible to the DOs and retrievers. Therefore, any third party other than the retriever and the DO, including external attackers and malicious internal servers, cannot generate the correct keyword trapdoor and ciphertext. In other words, our scheme can resist online and insider keyword-guessing attacks.
Lu et al. [] demonstrated that if an attacker can generate keyword ciphertext using the public keys of the CSS and the retriever, then they can perform an online keyword-guessing attack on PEKS schemes. Later, Shao et al. [] pointed out that if the SCF-PEKS scheme can generate keyword ciphertext with only the public keys of the CSS, DO, and retriever, while the insider attacker (malicious CSS) can run both the keyword encryption algorithm and the test algorithm, then the insider attacker can try online keyword guessing attacks on SCF-PEKS scheme. Since the keyword ciphertexts in schemes [,,,,] are all generated using public keys, all of them are insecure against insider keyword-guessing attacks and online keyword-guessing attacks.
PEKS schemes typically use keywords selected from a low-entropy keyword space. Therefore, based on this characteristic, offline keyword-guessing attacks can be launched naturally []. By performing this attack, any insider/outsider attacker can correctly guess the keywords in a given keyword trapdoor using a testing algorithm. Construct , where is the guessed keyword set. Verify that the equation holds. If the above equation is equal, the keyword set contained in in the trapdoor is the same as the guessed keyword set . Therefore, the scheme in [] is insecure under offline keyword attacks. According to a similar construction idea, the schemes in [,,,] are also insecure under offline keyword-guessing attacks.
From the above analysis and the security proof in Section 4, we can see that our scheme is resistant to offline keyword guessing attacks and keyword selection attacks in the standard model. Secondly, based on the security of the Diffie–Hellman shared secret key, our scheme is also secure against insider and online keyword-guessing attacks. In other words, of all the schemes, ours is the safest.
7.2. Computational Overhead Comparison
Next, we compare the computational complexity. To compare the computational complexity, we use the operation time of He et al.’s scheme [] as the benchmark. He et al. tested the time required for the relevant operations in the experimental environment of Samsung Galaxy S5 based on the Android 4.4.2 operating system, quad-core 2.45 G processor, and 2G byte memory. Table 4 shows the exact running time and symbols of the various operations. The mapping is a bilinear pair, where is an additive group of singular elliptic curves of order p defined on a finite field , and is a multiplicative group of order p. The lengths of p and q are 512 bits and 160 bits, respectively. G is an additive group of non-singular elliptic curves of order q defined on the prime finite field . The length of p and q is 160.

Table 4.
Symbol definition.
Because no SE scheme requires pairing and supports conjunctive keywords, we selected five SE schemes with similar functionalities for comparison. The results are shown in Table 5. Because each scheme has different settings, making direct horizontal comparisons is difficult. To ensure objectivity, we have established uniform parameter standards for comparison. The details are as follows: we assume that there are d data owners, u data consumers, n ciphertexts, m keywords contained in the keyword ciphertexts, l keywords contained in the trapdoors, and s keywords contained in the keyword ciphertexts obtained after the query. For algorithms that are not involved, we mark them with “-” in Table 5.

Table 5.
Comparison of calculation complexity of various schemes.
The data presented in Table 5 are theoretical calculations, but to more accurately evaluate the actual performance of our solution, we also need to simulate real-world scenarios. In the real world, there is a larger dataset and more participants. Therefore, it is worthwhile to set the number of ciphertexts from 1 to 100,000 (), the number of data owners (d), the number of keywords contained in trapdoors (l), and the number of data ciphertexts contained in query results (s) from 1 to 10,000.
The KeyGen algorithm’s computational overhead for VCKSM [], VMKS [], and our scheme is affected by d and u, while the computational overhead of VCSE [] is only affected by d. This is because the VCSE scheme’s signing is performed with the system’s private key and does not utilize the user’s private key. Additionally, the computational overhead of VMKDO [] is only influenced by u, as the keyword encryption of VCSE [] is performed using the CSS’s public key and not the user’s public key. For comparison, assume . Figure 3a illustrates that VMKS [] has a much higher computational overhead in KeyGen compared to the other schemes. Our scheme and VMKDO [] have roughly equal computational overhead in KeyGen and outperform the others.
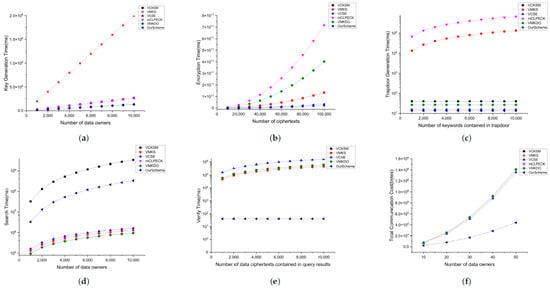
Figure 3.
Comparison results. (a) Computational overhead of the KeyGen algorithm. (b) Computational overhead of the Enc algorithm. (c) Computational overhead of the Trap algorithm. (d) Computational overhead of the Search algorithm. (e) Computational overhead of the Verify algorithm. (f) Communication overheads.
In Figure 3b, we evaluate the computational burden of the Enc algorithm in these schemes by varying the number of ciphertexts from 1 to 100,000 (), assuming and . The computational overhead of the Enc algorithm for all the schemes almost increases with the number of n. Note that the mCLPECK [] scheme has a much higher computational overhead in the Enc algorithm than the other schemes; our scheme and the VCSM [] scheme have roughly equal computational overheads in the Enc algorithm, and both outperform the others.
In the Trap algorithm, the computational overhead of the VCKSM [] scheme with the mCLPECK [] scheme is affected by l, and both grow linearly with l, whereas the computational overheads of the other schemes are fixed values. In Figure 3c, we evaluate the computational burden of the Trap algorithm by varying the number of keywords included in the trapdoor from 1 to 10,000 (). Note that the computational overheads of the VMKS scheme and the mCLPECK [] scheme in the Trap algorithm are much higher than those of the other schemes; the computational overheads of our scheme and the VCSM [] scheme in the Trap algorithm are roughly equal, and both outperform the others.
In the Search algorithm, the computational overhead of the VCKSM [] scheme and our scheme is affected by n and m, while the other schemes are only affected by n. In Figure 3d, for ease of discussion, we assume and evaluate the computational burden of the Search algorithm by varying the number of data owners from 1 to 10,000 (). It can be seen that the computational overhead of all schemes almost always increases with n. Note that the computational overhead of the VCKSM [] scheme with our scheme in the Search algorithm is slightly higher than that of the other schemes, which are roughly equal.
In the Verify algorithm, the computational overhead of all schemes except ours is affected by s. The computational overhead of our scheme is a fixed value, and the other schemes grow linearly with s. In Figure 3e, we evaluate the computational overhead of the Verify algorithm by varying the number of data ciphers contained in the query results from 1 to 10,000 (). Note that the computational overhead of the VCSE [] scheme in Verify’s algorithm is higher than that of the other schemes, while the computational overhead of our scheme is fixed. As l1 becomes larger, our scheme is more advantageous.
To sum up, except for the Search algorithm, our scheme has a lower storage cost in the KeyGen, Trap, and Verify algorithms than the other five schemes, among which our scheme has a much lower storage cost in the Verify algorithm than the other schemes. Considering the storage costs of all algorithms, our solution has the lowest storage cost of all solutions.
7.3. Storage Cost Comparison
Below, we compare storage costs. Let , , , and represent the sizes of elements in , , G, and , respectively. Then = 512 bytes, = 160 bytes, and = 160 bytes. If the conjunctive keyword-searchable encryption scheme has no verification function, fewer signatures for the keyword ciphertext will be stored. Therefore, we select only verifiable conjunctive-keyword-searchable encryption schemes to compare the size of storage costs. Table 6 illustrates the comparison results.

Table 6.
Storage cost comparison.
In the KeyGen algorithm, the storage costs of VCKSM [], VMKS [], and our scheme are all affected by d and u, while the storage cost of the VCSE scheme is only affected by d and the storage cost of VMKDO [] is only affected by u. For the sake of discussion, we assume . So, the storage cost for all scenarios grows linearly with u. Since , our solution has the lowest storage cost of all.
In the Trap algorithm, the storage cost of VCKSM [] and our scheme is affected by m1, while the storage cost of VMKS [], VCSE [], and VMKDO [] is affected by l. For the sake of discussion, we assume . Then, all the above schemes increase linearly with m. Since , our solution, VCSE [], and VMKDO [] are approximately the same and much lower than VCKSM [] and VMKS [].
In the Search algorithm, the storage cost of VCKSM [] and our scheme is affected by m, the storage cost of VMKS [] is only affected by l, and the storage cost of VCSE [] and VMKDO [] is a fixed value. For the sake of discussion, we assume . Then, VCKSM [], VMKS [], and our scheme increase linearly with l. Because , VCKSM [], and VMKS [] have the highest storage costs, our solution is second, and VCSE [] and VMKDO [] have the lowest storage cost.
In the Search algorithm, the storage costs of VCKSM [] and our scheme are affected by m, the storage cost of VMKS [] is only affected by l, and the storage costs of VCSE [] and VMKDO [] are fixed. For the sake of discussion, let us assume . Then, VCKSM [], VMKS [], and our scheme all increase linearly with l. Because , VCKSM [] and VMKS [] have the highest storage costs, our solution is second, and VCSE [] and VMKDO [] have the lowest storage cost. In the Verify algorithm, the storage cost of all schemes except ours is affected by s. Therefore, the storage cost of their solutions increases linearly with s, and the storage cost of our solution is a fixed value. As a result, our solution has significantly lower storage costs than others.
To sum up, except for the Search algorithm, our scheme has a lower storage cost in all the algorithms (KeyGen, Trap, and Verify) than the other five schemes, among which our scheme has a much lower storage cost in the Verify algorithm than the other schemes. Considering the storage costs of all algorithms, our solution has the lowest storage cost of all solutions.
7.4. Comparison of Communication Costs
Finally, we compare the communication costs. If the conjunctive keyword-searchable encryption scheme has no verification function, the communication cost does not need to consider the signature communication cost in the communication cost. Therefore, we only select the conjunctive keyword-searchable encryption schemes that support verifiability for comparison. Table 7 shows the comparison results.

Table 7.
Comparison of communication costs.
As shown in Table 7, our scheme has the shortest signature length. The signature lengths of the other schemes are the same. VMKS [] and VMKDO [] have the longest index lengths because they are at least 5 bytes larger than the other schemes. The index lengths of the others are roughly the same. The trapdoor lengths of VCKSM [] are the longest, followed by our scheme, and the shortest is of the VMKDO [] scheme. Assuming , we compare the total communication cost of these schemes in Figure 3(f). According to Figure 3f, the total communication cost of our scheme is lower than the total communication cost of all schemes.
Overall, our solution is more efficient than others in computation, storage, and communication. Most importantly, it excels in security.
8. Conclusions
This article proposes a novel certificateless, verifiable, bilinear, pair-free, conjunctive keyword search encryption scheme (CLVPFC-PEKS), aiming to provide a secure and efficient data search method for the Internet of Things healthcare (IoMT) field. Our solution solves the problems in existing public key searchable encryption technologies, such as low computational efficiency and susceptibility to keyword guessing attacks. We have demonstrated under the standard model that the CLVPFC-PEKS scheme can resist both choosen keyword and ciphertext attacks and offline keyword guessing attacks, and based on the security of the Diffie–Hellman shared secret key to demonstrate that the CLVPFC-PEKS scheme can resist online/internal keyword guessing attacks. In addition, we also conducted a detailed analysis of the performance of the scheme. The results indicate that our scheme has significant advantages in terms of security, computational complexity, storage overhead, and communication costs compared to existing schemes. Overall, our solution provides a new solution for secure and efficient data search in the medical Internet of Things, meeting the urgent needs for data security and privacy protection.
Author Contributions
Methodology, W.L.; Formal analysis, W.L.; Data curation, Y.W. and H.Z.; Writing—original draft, W.L.; Writing—review & editing, W.L.; Visualization, Y.W. and Y.G.; Supervision, J.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This paper was supported by the National Natural Science Foundation of China (No.61962011); the Guiyang City Science and Technology Plan Project (No.[2021]43-8); Guizhou Normal University Academic New Seedling Fund Project (QianShiXinMiao[2021]B09).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Iera, L.A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of Things for Smart Cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Bellavista, P.; Cardone, G.; Corradi, A.; Foschini, L. Convergence of MANET and WSN in IoT Urban Scenarios. IEEE Sens. J. 2013, 13, 3558–3567. [Google Scholar] [CrossRef]
- He, D.J.; Ye, R.; Chan, S.; Guizani, M.; Xu, Y.P. Privacy in the Internet of Things for Smart Healthcare. IEEE Commun. Mag. 2018, 56, 38–44. [Google Scholar] [CrossRef]
- Chen, Y.; Lu, J.; Jan, J. A Secure EHR System Based on Hybrid Clouds. J. Med. Syst. 2012, 36, 3375–3384. [Google Scholar] [CrossRef]
- Jagadeeswari, V.; Subramaniyaswamy, V.; Logesh, R.; Vijayakumar, V. A study on medical Internet of Things and Big Data in personalized healthcare system. Health Inf. Sci. Syst. 2018, 6, 14. [Google Scholar] [CrossRef] [PubMed]
- Wagner, D.X.S.; Perrig, A. Practical Techniques for Searches on Encrypted Data. In Proceedings of the IEEE Symposium on Security & Privacy, Berkeley, CA, USA, 12–15 May 2002; pp. 44–55. [Google Scholar]
- Li, M.; Yu, S.; Ren, K.; Lou, W. Securing personal health records in cloud computing: Patient-centric and fine-grained data access control in multi-owner settings. In Proceedings of the ICST Conference Security and Privacy in Communication Networks PP, Singapore, 7–9 September 2010; pp. 89–106. [Google Scholar] [CrossRef]
- Wang, B.Y.; Li, H.; Liu, X.F.; Li, X.Q.; Li, F.H. Preserving identity privacy on multi-owner cloud data during public verification. Secur. Commun. Netw. 2014, 7, 2104–2113. [Google Scholar] [CrossRef]
- Miao, Y.; Liu, X.; Raymond Choo, K.; Deng, R.H.; Li, J.; Li, H.; Ma, J. Privacy-Preserving Attribute-Based Keyword Search in Shared Multi-owner Setting. IEEE Depend. Secur. 2021, 18, 1080–1094. [Google Scholar] [CrossRef]
- Padhya, M.; Jinwala, D.C. CRSQ-KASE: Key Aggregate Searchable Encryption Supporting Conjunctive Range and Sort Query on Multi-owner Encrypted Data. Arab. J. Sci. Eng. 2020, 45, 3133–3155. [Google Scholar] [CrossRef]
- Hwang, M.; Hsu, H.T.; Lee, C.C. A New Public Key Encryption with Conjunctive Field Keyword Search Scheme. Inf. Technol. Control. 2014, 43, 277–288. [Google Scholar] [CrossRef]
- Miao, Y.; Ma, J.; Wei, F.; Liu, Z.; Wang, X.A.; Lu, C. VCSE: Verifiable conjunctive keywords search over encrypted data without secure-channel. Peer Netw. 2017, 23, 995–1007. [Google Scholar] [CrossRef]
- Miao, Y.; Ma, J.; Liu, X.; Jiang, Q.; Zhang, J.; Shen, L.; Liu, Z. VCKSM: Verifiable conjunctive keyword search over mobile e-health cloud in shared multi-owner settings. Pervasive Mob. Comput. 2017, 40, 205–219. [Google Scholar] [CrossRef]
- Miao, Y.; Ma, J.; Liu, X.; Liu, Z.; Wei, F. VMKDO: Verifiable multi-keyword search over encrypted cloud data for dynamic data-owner. Peer Netw. Appl. 2018, 11, 287–297. [Google Scholar] [CrossRef]
- Miao, Y.; Weng, J.; Liu, X.; Choo, K.R.; Liu, Z.; Li, H. Enabling verifiable multiple keywords search over encrypted cloud data. Inform. Sci. 2018, 465, 21–37. [Google Scholar] [CrossRef]
- Fan, M.M.M.Q.; Feng, D.G. Multi-user certificateless public key encryption with conjunctive keyword search for cloud-based telemedicine. J. Inf. Secur. Appl. 2020, 55, 102652. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Ma, M.; Kumar, N.; He, D. Certificateless searchable public key authenticated encryption with designated tester for cloud-assisted medical Internet of Things. Ann. Telecommun. 2019, 74, 423–434. [Google Scholar] [CrossRef]
- Wang, Y.L.; Li, J.G. Keyword guessing attacks on a public key encryption with keyword search scheme without random oracle and its improvement. Inform. Sci. 2019, 479, 270–276. [Google Scholar] [CrossRef]
- Liu, X.; Sun, Y.; Dong, H. A pairing-free certificateless searchable public key encryption scheme for IoMT. J. Syst. Architect. 2023, 139, 102885. [Google Scholar] [CrossRef]
- Senouci, M.R.; Benkhaddra, I.; Senouci, A.; Li, F.G. A provably secure free-pairing certificateless searchable encryption scheme. Telecommun. Syst. 2022, 80, 383–395. [Google Scholar] [CrossRef]
- Hu, Z.Y.; Deng, L.Z.; Wu, Y.Y.; Shi, H.Y.; Gao, Y. Secure and Efficient Certificateless Searchable Authenticated Encryption Scheme without Random Oracle for Industrial Internet of Things. IEEE Syst. J. 2023, 17, 1304–1315. [Google Scholar] [CrossRef]
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public Key Encryption with Keyword Search. In Advances in Cryptology; Springer: Berlin/Heidelberg, Germany, 2004; pp. 506–522. [Google Scholar] [CrossRef]
- Safiavinaini, J.B.; Susilo, W. Public Key Encryption with Keyword Search Revisited. In Proceedings of the International Conference on Computational Science and Its Applications (ICCSA 2008), Perugia, Italy, 30 June–3 July 2008; pp. 1249–1259. [Google Scholar]
- Rhee, H.S.; Park, J.H.; Susilo, W.; Lee, D.H. Improved searchable public key encryption with designated tester. In Proceedings of the International Symposium on Information, Seoul, Republic of Korea, 28 June–3 July 2009; p. 376. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography. In Advances in Cryptology—ASIACRYPT 2003; Lecture Notes in Computer Science (LNCS, Volume 2894); Laih, C.S., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Xu, P.; Jin, H.; Wu, Q.; Wang, W. Public-Key Encryption with Fuzzy Keyword Search: A Provably Secure Scheme under Keyword Guessing Attack. IEEE Trans. Comput. 2013, 62, 2266–2277. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zeadall, S.; Kumar, N.; Liang, K. Certificateless Public Key Authenticated Encryption with Keyword Search for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3618–3627. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Khurram Khan, M.; Chen, J. Certificateless searchable public key encryption scheme for mobile healthcare system. Comput. Electr. Eng. 2018, 65, 413–424. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Fan, S.; Feng, D. Certificateless searchable public key encryption scheme secure against keyword guessing attacks for smart healthcare. J. Inf. Secur. Appl. 2020, 50, 102429. [Google Scholar] [CrossRef]
- Golle, P.; Stadon, J.; Waters, B. Secure Conjunctive Keyword Search over Encrypted Data. In Applied Cryptography and Network Security; Jakobsson, M., Yung, M., Zhou, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 31–45. [Google Scholar]
- Hwang, Y.H.; Lee, P.J. Public Key Encryption with Conjunctive Keyword Search and Its Extension to a Multi-User System. In Pairing-Based Cryptography—Pairing 2007; Lecture Notes in Computer Science (LNSC, Volume 4575); Springer: Berlin/Heidelberg, Germany, 2007; p. 2. [Google Scholar]
- Yang, Y.; Ma, M.D. Conjunctive Keyword Search With Designated Tester and Timing Enabled Proxy Re-Encryption Function for E-Health Clouds. IEEE Inf. Foren. Sec. 2016, 11, 746–759. [Google Scholar] [CrossRef]
- Heng, S.H.; Kurosawa, K. K-Resilient Identity-Based Encryption in the Standard Model. In Topics in Cryptology—CT-RSA 2004 2964; Lecture Notes in Computer Science (LNCS, Volume 2964); Okamoto, T., Ed.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 67–80. [Google Scholar]
- Khader, D. Public Key Encryption with Keyword Search Based on K-Resilient IBE. In Computational Science and Its Applications—ICCSA 2006; Lecture Notes in Computer Science (LNTCS, Volume 3982); Gavrilova, M., Ed.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 298–308. [Google Scholar]
- Xu, H.M.Y.X.; Zhao, H.T. An Efficient Public Key Encryption with Keyword Scheme Not Using Pairing. In Proceedings of the First International Conference on Instrumentation, Nagpur, Maharashtra, India, 21–22 April 2011. [Google Scholar]
- Vallent, T.F.; Kim, H. A Pairing-Free Public Key Encryption with Keyword Searching for Cloud Storage Services. In e-Infrastructure and e-Services for Developing Countries; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering (LNICST, Volume 135); Springer: Berlin/Heidelberg, Germany, 2014; p. 70. [Google Scholar]
- Yang, N.; Xu, S.; Quan, Z. An Efficient Public Key Searchable Encryption Scheme for Mobile Smart Terminal. IEEE Access 2020, 8, 77940–77950. [Google Scholar] [CrossRef]
- Lu, Y.; Li, J. Constructing pairing-free certificateless public key encryption with keyword search. Front. Inf. Technol. Electron. Eng. 2019, 20, 1049–1060. [Google Scholar] [CrossRef]
- Ma, M.; Luo, M.; Fan, S.; Feng, D. An Efficient Pairing-Free Certificateless Searchable Public Key Encryption for Cloud-Based IIoT. Wirel. Commun. Mob. Com. 2020, 2020, 8850520. [Google Scholar] [CrossRef]
- Byun, J.W.; Rhee, H.S.; Park, H.A.; Lee, D.H. Off-line keyword guessing attacks on recent keyword search schemes over encrypted data. In Secure Data Management; Lecture Notes in Computer Science (LNISA, Volume 4165); Jonker, W., Petkovic, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 75–83. [Google Scholar]
- Lin, X.J.; Sun, L.; Qu, H.P.; Liu, D.X. On the Security of Secure Server-Designation Public Key Encryption with Keyword Search. Comput. J. 2018, 61, 1791–1793. [Google Scholar] [CrossRef]
- Huang, Q.; Li, H.B. An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks. Inform. Sci. 2017, 403, 1–14. [Google Scholar] [CrossRef]
- Wang, Y.L.; Li, J. On Security of a Secure Channel Free Public Key Encryption with Conjunctive Field Keyword Search Scheme. Inf. Technol. Control 2018, 47, 56–62. [Google Scholar] [CrossRef]
- Jeong, I.R.; Kwon, J.O.; Hong, D.; Lee, D.H. Constructing PEKS schemes secure against keyword guessing attacks is possible? Comput. Commun. 2009, 32, 394–396. [Google Scholar] [CrossRef]
- Wang, B.J.; Chen, T.H.; Jeng, F.G. Security Improvement against Malicious Servers in dPEKS Scheme. Int. J. Inf. Educ. Technol. 2011, 1, 4. [Google Scholar]
- Shao, Z.Y.; Yang, B. On security against the server in designated tester public key encryption with keyword search. Inform. Process. Lett. 2015, 115, 957–961. [Google Scholar] [CrossRef]
- Chai, Q.; Gong, G. Verifiable symmetric searchable encryption for semi-honest-but-curious cloud servers. In Proceedings of the IEEE International Conference on Communications, Ottawa, ON, Canada, 10–15 June 2012. [Google Scholar]
- Sun, W.; Liu, X.; Lou, W.; Hou, Y.T.; Li, H. Catch You If You Lie to Me: Efficient Verifiable Conjunctive Keyword Search over Large Dynamic Encrypted Cloud Data. In Proceedings of the 34th IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015. [Google Scholar]
- Ismail, M.; Abd El-Gawad, A.F. Revisiting Zero-Trust Security for Internet of Things. Sustain. Mach. Intell. J. 2023, 3. [Google Scholar] [CrossRef]
- Alenizi1, J.A.; Alrashdi, I. SFMR-SH: Secure Framework for Mitigating Ransomware Attacks in Smart Healthcare Using Blockchain Technology. Sustain. Mach. Intell. J. 2023, 2, 1–19. [Google Scholar] [CrossRef]
- Hu, C.; Liu, P. An Enhanced Searchable Public Key Encryption Scheme with a Designated Tester and Its Extensions. J. Comput. 2012, 7, 716–723. [Google Scholar] [CrossRef]
- Rhee, H.S.; Park, J.H.; Susilo, W.; Lee, D.H. Trapdoor security in a searchable public-key encryption scheme with a designated tester. Syst. Softw. 2010, 83, 763–771. [Google Scholar] [CrossRef]
- Fang, L.; Susilo, W.; Ge, C.; Wang, J. Public key encryption with keyword search secure against keyword guessing attacks without random oracle. Inform. Sci. 2013, 238, 221–241. [Google Scholar] [CrossRef]
- Wu, L.; Chen, B.; Zeadally, S.; He, D. An efficient and secure searchable public key encryption scheme with privacy protection for cloud storage. Soft Comput. 2018, 22, 7685–7696. [Google Scholar] [CrossRef]
- He, D.B.; Wang, H.Q.; Wang, L.N.; Shen, J.; Yang, X.Z. Efficient certificateless anonymous multi-receiver encryption scheme for mobile devices. Soft Comput. 2017, 21, 6801–6810. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).