A Framework for Communication–Compute–Control Co-Design in Cyber–Physical Systems
Abstract
:1. Introduction
2. Research Aims and Objectives
2.1. Definition of Communication–Compute–Control Co-Design and Its Ambition
2.2. Contributions of This Article
2.3. Structure of the Article
3. State of the Art, Observed Trends in Industry and Prior Work
3.1. State of the Art and Trends in Industry
3.1.1. Trend Towards Wireless Communication for CPSs
3.1.2. Trend Towards Cloudification and Cloud-Native Application Design for CPSs
3.1.3. Trend Towards Flexible Interaction and Interoperability
3.2. Related and Prior Work
3.2.1. Prior Work from the Compute Domain
3.2.2. Prior Work from Networked Control Systems (NCSs) and Wireless NCSs Domain
3.2.3. Prior Work from Practical Studies
3.2.4. Prior Work on Concept Level
4. The Framework of Communication–Compute–Control-Optimized Application Design
4.1. Co-Design Framework
4.1.1. Degree 0: Unawareness
- Additional knowledge utilized by the application: None.
- Type of application: This type of application design has its justification for, e.g., applications with unlimited access to computing resources, as well as for wireless non-critical applications when, e.g., usage of computing and communication resources is so limited that access to these can almost always be assumed feasible under perfect conditions.
4.1.2. Degree 1: Awareness
- Additional knowledge utilized by the application: Understanding of general characteristics of network/compute, e.g., awareness that resource constraints may occur;
- Type of application: Typical applications for which degree-1 design is suitable are non-critical applications that are using only very limited compute or network resources or that can be run with resource allocations following the default best-effort paradigm.
4.1.3. Degree 2: Interface Exposure
- Additional knowledge utilized by the application: information on the current or predicted operational status of the network/compute domains, including, e.g., upcoming resource constraints or resulting performance variations;
- Typical application: This type of application design is most suitable for applications solving moderate/critical tasks with a moderate degree of guaranteed accomplishment.
4.1.4. Degree 3: (Mutual) Interaction
- Additional knowledge utilized by the application: More detailed performance insights on specific network/compute infrastructure that can be provided. Moreover, the application can now rely on service assurance of communication/compute infrastructure and can work with a quantifiable assessment of their dependability;
- Typical application: This type of application design is most suitable for accomplishing tasks with high levels of required guaranteed accomplishment and/or applications that require significant amounts of resources and/or applications that need to operate with high levels of resource efficiency. By ensuring access to communication and/or compute resources via service requests, the highest degree of guaranteed task accomplishment can be achieved.
4.1.5. Degree 4: Negotiation
- Additional knowledge utilized by the application: Increased understanding of relations and resource dependencies towards other applications in a wider context.
- Typical applications in this degree could be part of a larger context, for which a higher-level task/application coordination exists. This could for instance be in the form of digital twins. The negotiation process would then take place or relate to a higher level, e.g., between some notion of network, compute, and system digital twin.
4.1.6. Summary
4.2. Examples of Use Case Realizations Using Co-Design with Different Degrees
4.2.1. AMR Use Case Scenario and Assumptions
- Localization: This component consists of a set of entities designed to provide an accurate localization system. It enables the robot to determine its position within the environment and detect obstacles. For example, Simultaneous Localization and Mapping (SLAM);
- Navigation: Building on the localization system, the navigation component comprises entities responsible for moving the robot within the environment. This includes trajectory and motion planning, allowing the robot to travel between points A and B;
- Hardware-dependent functions: This component contains entities that are specific to the hardware running on the robot and cannot be offloaded to the edge or cloud, such as servo control, sensors, and safety and emergency mechanisms.
- The AMR is navigating in an environment where there is a high density of connected cars, sensors, devices, humans, etc., competing for both communication and computing resources. (see Section 2 on trends towards wireless communication).
- The AMR is implemented in a cloud-native way, using container orchestration platforms to simplify the deployment and management of the application in the device-cloud continuum. (see Section 2 on trends towards cloudification).
4.2.2. AMR Co-Design with Awareness, Degree 1
4.2.3. AMR Co-Design with Interface Exposure, Degree 2
4.2.4. AMR Co-Design with Mutual Interaction, Degree 3
4.2.5. AMR Co-Design with Negotiations, Degree 4
4.2.6. AMR Co-Design with Different Degrees for Different Segments
4.2.7. Discussion
5. Building Blocks of 3Cs Co-Design
5.1. Self-Awareness, Decisions, and Actions
5.1.1. Application Self-Awareness, Decisions, and Actions
5.1.2. Network Self-Awareness, Decisions, and Actions
5.1.3. Compute Self-Awareness, Decisions, and Actions
5.2. Exposure Mechanisms and Interfaces
- Requests for specific connectivity and compute services or a change in these;
- Requests for network and compute information and requests for subscribing to a specific information channel from network and compute elements, e.g., notifications about changes in network and compute conditions.
5.3. Example Flow of Interactions
- Self-awareness: All entities (network, application, compute) evaluate their own needs and requirements with suitable time intervals, keeping an updated view. This is performed by each entity independently.
- Exposure of self-awareness information via a suitable method, thereby giving the other entities the possibility to consume this knowledge.
- Planning and decision making: Each entity acts based on self-awareness and by consuming exposed information and potential requests from the other entities. If there are different alternatives of actions, conflicts, or a decision on an action is made an iterative process is foreseen, e.g., starting with updating self-awareness.
6. Navigating Co-Design, Tradeoffs, Considerations, and Next Steps
6.1. Complexity vs. Simplicity
6.2. Technology Specific Insights vs. Technology Agnosticism
6.3. Domain Interaction and Modeling of 3Cs Interaction
6.4. Open Interfaces vs. Proprietary Solutions
6.5. Scalibility Aspects of Co-Design
6.6. Conceptual vs. Practical Work
7. Summary and Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Alur, R. Principles of Cyber-Physical Systems; The MIT Press: Cambridge, MA, USA, 2015; ISBN 978-026-254-892-2. [Google Scholar]
- Karapantelakis, A.; Sahlin, B.; Balakrishnan, B.; Roeland, D.; Rune, G.; Wikström, G.; Wiemann, H.; Arkko, J.; Vandikas, K.; Coldrey, M.; et al. Co-Creating a Cyber Physical World with 6G. 2024. Available online: https://www.ericsson.com/en/reports-and-papers/white-papers/co-creating-a-cyber-physical-world (accessed on 3 December 2024).
- Zhao, G.; Imran, M.; Pang, Z.; Chen, Z.; Li, L. Toward Real-Time Control in Future Wireless Networks: Communication-Control Co-Design. IEEE Commun. Mag. 2019, 57, 138–144. [Google Scholar] [CrossRef]
- Noor-A-Rahim, M.; John, J.; Firyaguna, F.; Sherazi, H.; Kushch, S.; Vijayan, A.; O’Connell, E.; Pesch, D.; O’Flynn, B.; O’Brien, W.; et al. Wireless Communications for Smart Manufacturing and Industrial IoT: Existing Technologies, 5G and Beyond. Sensors 2023, 23, 73. [Google Scholar] [CrossRef]
- Yu, R.; Xue, G. Principles and Practices for Application-Network Co-Design in Edge Computing. IEEE Netw. 2023, 37, 137–144. [Google Scholar] [CrossRef]
- Guo, F.; Peng, M.; Li, N.; Sun, Q.; Li, X. Communication-Computing Built-in-Design in Next-Generation Radio Access Networks: Architecture and Key Technologies. IEEE Netw. 2024, 38, 100–108. [Google Scholar] [CrossRef]
- Tarkoma, S. Publish/Subscribe Systems: Design and Principles; John Wiley & Sons: Hoboken, NJ, USA, 2012; ISBN 978-111-995-154-4. [Google Scholar]
- 5G Use Cases, Ericsson. 2023. Available online: https://www.ericsson.com/4ac5b1/assets/local/cases/customer-cases/2016/documents/5g-use-cases-ericsson.pdf (accessed on 3 December 2024).
- Ansari, J.; Lange, D.; Overbeck, D. Report on 5G Capabilities for Enhanced Industrial Manufacturing Processes, Deliverable 3.4, 5G-SMART. 2022. Available online: https://5gsmart.eu/wp-content/uploads/5G-SMART-D3.4-v1.0.pdf (accessed on 3 December 2024).
- Grosjean, L.; Landernäs, K.; Sayrac, B.; Dobrijevic, O.; König, N.; Harutyunyan, D.; Patel, D.; Monserrat, J.F.; Sachs, J. 5G-Enabled Smart Manufacturing—A booklet by 5G-SMART. 2022. Available online: https://5gsmart.eu/wp-content/uploads/2022-5G-SMART-Booklet.pdf (accessed on 3 December 2024).
- Jonsson, M.; Kunert, K. Towards Reliable Wireless Industrial Communication with Real-Time Guarantees. IEEE Trans. Ind. Inform. 2009, 5, 429–442. [Google Scholar] [CrossRef]
- Park, P.; Coleri, E.S.; Fischione, C.; Lu, C.; Johansson, K.H. Wireless Network Design for Control Systems: A Survey. IEEE Commun. Surv. Tutor. 2018, 20, 978–1013. [Google Scholar] [CrossRef]
- Willig, A. Recent and Emerging Topics in Wireless Industrial Communications: A Selection. IEEE Trans. Ind. Inform. 2008, 4, 102–124. [Google Scholar] [CrossRef]
- Deng, S.; Zhao, H.; Huang, B.; Zhang, C.; Chen, F.; Deng, Y.; Yin, J.; Dustdar, S.; Zomaya, A.Y. Cloud-Native Computing: A Survey from the Perspective of Services. Proc. IEEE 2024, 112, 12–46. [Google Scholar] [CrossRef]
- Jin, J.; Yu, K.; Kua, J.; Zhang, N.; Pang, Z.; Han, Q. Cloud-Fog Automation: Vision, Enabling Technologies, and Future Research Directions. IEEE Trans. Ind. Inform. 2024, 20, 1039–1054. [Google Scholar] [CrossRef]
- Gil, G.; Corujo, D.; Pedreiras, P. Cloud Native Computing for Industry 4.0: Challenges and Opportunities. In Proceedings of the 26th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Västerås, Sweden, 7–10 September 2021; pp. 1–4. [Google Scholar]
- Yu, W.; Liang, F.; He, X.; Hatcher, W.; Lu, C.; Lin, J.; Yang, X. A Survey on the Edge Computing for the Internet of Things. IEEE Access 2018, 6, 6900–6919. [Google Scholar] [CrossRef]
- Liu, Y.; Hernandez, A. Enabling 5G QoS configuration capabilities for IoT applications on container orchestration platform. In Proceedings of the 14th IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Napoli, Italy, 4–6 December 2023; pp. 63–68. [Google Scholar]
- Skarin, P.; Tärneberg, W.; Årzen, K.; Kihl, M. Towards Mission-Critical Control at the Edge and Over 5G. In Proceedings of the IEEE International Conference on Edge Computing (EDGE), San Francisco, CA, USA, 2–7 July 2018; pp. 50–57. [Google Scholar]
- Abeni, L.; Andreoli, R.; Gustafsson, H.; Mini, R.; Cucinotta, T. Fault Tolerance in Real-Time Cloud Computing. In Proceedings of the 26th IEEE International Symposium on Real-Time Distributed Computing (ISORC), Nashville, TN, USA, 23–25 May 2023; pp. 170–175. [Google Scholar]
- Afrin, M.; Jin, J.; Rahman, A.; Wan, J.; Hossain, E. Resource Allocation and Service Provisioning in Multi-Agent Cloud Robotics: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2021, 23, 842–870. [Google Scholar] [CrossRef]
- Peres, R.; Jia, X.; Lee, J.; Sun, K.; Colombo, A.; Barata, J. Industrial Artificial Intelligence in Industry 4.0—Systematic Review, Challenges and Outlook. IEEE Access 2020, 8, 220121–220139. [Google Scholar] [CrossRef]
- Erl, T.; Monroy, E. Cloud Computing: Concepts, Technology, Security, and Architecture, 2nd ed.; Pearson Education: London, UK, 2023; ISBN 978-013-805-225-6. [Google Scholar]
- Boberg, C.; Kakhadze, G.; Axelsson, M. From CPaaS to a Global Network API Platform, Enabling CSPs to Monetize on 5G. 2024. Available online: https://www.ericsson.com/en/reports-and-papers/white-papers/global-network-api-platform-to-monetize-5g (accessed on 3 December 2024).
- Buerkle, A.; Eaton, W.; Al-Yacoub, A.; Zimmer, M.; Kinnell, P.; Henshaw, M.; Coombes, M.; Chen, W.-H.; Lohse, N. Towards industrial robots as a service (IRaaS): Flexibility, usability, safety and business models. Robot. Comput.-Integr. Manuf. 2023, 81, 102484. [Google Scholar] [CrossRef]
- OPC Foundation, OPC Unified Architecture (UA), Part 1: Overview and Concepts. 2022. Available online: https://reference.opcfoundation.org/Core/Part1/v105/docs/ (accessed on 3 December 2024).
- Plattform Industrie 4.0, Details of the Asset Administration Shell—Part 1. 2022. Available online: https://www.plattform-i40.de/IP/Redaktion/EN/Downloads/Publikation/Details_of_the_Asset_Administration_Shell_Part1_V3.pdf (accessed on 3 December 2024).
- TM Forum, Intent-Based Automation. Available online: https://www.tmforum.org/opendigitalframework/intent-based-automation/ (accessed on 3 December 2024).
- Linux Foundation, CAMARA—The Telco Global API Alliance. Available online: https://camaraproject.org/ (accessed on 3 December 2024).
- GSMA, Open Gateway. Available online: https://www.gsma.com/solutions-and-impact/gsma-open-gateway/ (accessed on 3 December 2024).
- GSMA, Operator Platform. Available online: https://www.gsma.com/solutions-and-impact/technologies/networks/operator-platform-hp/ (accessed on 3 December 2024).
- Lee, K.; Candell, R.; Bernhard, H.-P.; Cavalcanti, D.; Pang, Z.; Val, I. Reliable, High-Performance Wireless Systems for Factory Automation. NIST Interagency/Internal Report (NISTIR)–8317. 2020. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2020/NIST.IR.8317.pdf (accessed on 3 December 2024).
- Saha, O.; Dasgupta, P.A. Comprehensive Survey of Recent Trends in Cloud Robotics Architectures and Applications. Robotics 2018, 7, 47. [Google Scholar] [CrossRef]
- Savaglio, C.; Fortino, G.; Zhou, M.; Ma, J. Device-Edge-Cloud Continuum, Paradigms, Architectures and Applications; Springer: Berlin/Heidelberg, Germany, 2023; ISBN 978-303-142-193-8. [Google Scholar]
- Liu, Y.; Lan, D.; Pang, Z.; Karlsson, M.; Gong, S. Performance evaluation of containerization in edge-cloud computing stacks for industrial applications: A client perspective. IEEE Open J. Ind. Electron. Soc. 2021, 2, 153–168. [Google Scholar] [CrossRef]
- Bentaleb, O.; Belloum, A.S.; Sebaa, A.; El-Maouhab, A. Containerization technologies: Taxonomies, applications and challenges. J. Supercomput. 2022, 78, 1144–1181. [Google Scholar] [CrossRef]
- Liu, Y.; Hernandez, A.; Sundin, R.C. Robokube: Establishing a new foundation for the cloud native evolution in robotics. In Proceedings of the 10th International Conference on Automation, Robotics and Applications (ICARA), Athens, Greece, 22–24 February 2024; pp. 23–27. [Google Scholar]
- Zhang, X.M.; Han, Q.-L.; Ge, X.; Ding, D.; Ding, L.; Yue, D.; Peng, C. Networked control systems: A survey of trends and techniques. IEEE/CAA J. Autom. Sin. 2020, 7, 1–17. [Google Scholar] [CrossRef]
- Hespanha, J.P.; Naghshtabrizi, P.; Xu, Y.G. A survey of recent results in networked control systems. Proc. IEEE 2007, 95, 138–162. [Google Scholar] [CrossRef]
- Gupta, R.A.; Chow, M.Y. Networked control system: Overview and research trends. IEEE Trans. Ind. Electron. 2010, 57, 2527–2535. [Google Scholar] [CrossRef]
- Gungor, V.C.; Hancke, G.P. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef]
- Wildhagen, S.; Pezzutto, M.; Schenato, L.; Allgöwer, F. Self-triggered MPC robust to bounded packet loss via a min-max approach. In Proceedings of the 61st IEEE Conference on Decision and Control (CDC), Cancún, Mexico, 6–9 December 2022; pp. 7670–7675. [Google Scholar]
- Wang, Y.; Wu, S.; Lei, C.; Jiao, J.; Zhang, Q. A Review on Wireless Networked Control System: The Communication Perspective. IEEE Internet Things J. 2024, 11, 7499–7524. [Google Scholar] [CrossRef]
- Lyu, H.; Bengtsson, A.; Nilsson, S.; Pang, Z.; Isaksson, A.; Yang, G. Latency-Aware Control for Wireless Cloud Fog Automation: Framework and Case Study. IEEE Trans. Autom. Sci. Eng. 2023, 1–11. [Google Scholar] [CrossRef]
- Qiao, Y.; Fu, Y.; Yuan, M. Communication–Control Co-Design in Wireless Networks: A Cloud Control AGV Example. IEEE Internet Things J. 2023, 10, 2346–2359. [Google Scholar] [CrossRef]
- Lyu, H.; Pang, Z.; Bhimavarapu, K.; Yang, G. Impacts of Wireless on Robot Control: The Network Hardware-in-the-Loop Simulation Framework and Real-Life Comparisons. IEEE Trans. Ind. Inform. 2023, 19, 9255–9265. [Google Scholar] [CrossRef]
- Sharma, G.P.; Patel, D.; Sachs, J.; De Andrade, M.; Farkas, J.; Harmatos, J.; Varga, B.; Bernhard, H.-P.; Muzaffar, R.; Atiq, M.K.; et al. Towards Deterministic Communications in 6G Networks: State of the Art, Open Challenges and the Way Forward. IEEE Access 2023, 11, 106898–106923. [Google Scholar] [CrossRef]
- DETERMINISTIC6G. First Report on DETERMINISTIC6G Architecture. Deliverable D1.2, April 2024. Available online: https://deterministic6g.eu/images/deliverables/DETERMINISTIC6G-D1.2-v1.0.pdf (accessed on 5 December 2024).
- DETERMINISTIC6G. Report on Deterministic Service Design, Deliverable D1.3, January 2025. Available online: https://deterministic6g.eu/images/deliverables/DETERMINISTIC6G-D1.3-v1.0.pdf (accessed on 19 February 2025).
- DETERMINISTIC6G. First Report on 6G Centric Enabler. Deliverable D2.1, December 2023. Available online: https://deterministic6g.eu/images/deliverables/DETERMINISTIC6G-D2.1-v2.0.pdf (accessed on 5 December 2024).
- DETERMINISTIC6G, Digest on First DetCom Simulator Framework Release, Deliverable D4.1, December 2023. Available online: https://deterministic6g.eu/images/deliverables/DETERMINISTIC6G-D4.1-v1.0.pdf (accessed on 19 February 2025).
- Damigos, G.; Saradagi, A.; Sandberg, S.; Nikolakopoulos, G. Environmental Awareness Dynamic 5G QoS for Retaining Real Time Constraints in Robotic Applications. In Proceedings of the IEEE International Conference on Robotics and Automation (ICRA), Yokohama, Japan, 13–17 May 2024; pp. 12069–12075. [Google Scholar]
- 5G-ACIA, Exposure of 5G Capabilities for Connected Industries and Automation Applications. 2021. Available online: https://5g-acia.org/whitepapers/exposure-of-5g-capabilities-for-connected-industries-and-automation-applications-2/ (accessed on 5 December 2024).
- Seres, G.; Schulz, D.; Dobrijevic, O.; Karaağaç, A.; Przybysz, H.; Nazari, A.; Chen, P.; Mikecz, M.L.; Szabó, Á.D. Creating programmable 5G systems for the Industrial IoT. Ericsson Technol. Rev. 2022, 10, 2–12. [Google Scholar] [CrossRef]
- Karaagac, A.; Dobrijevic, O.; Schulz, D.; Seres, G.; Nazari, A.; Przybysz, H.; Sachs, J. Managing 5G Non-Public Networks from Industrial Automation Systems. In Proceedings of the 19th IEEE International Conference on Factory Communication Systems (WFCS), Pavia, Italy, 26–28 April 2023; pp. 1–8. [Google Scholar]
- Industry IoT Consortium. The Industrial Internet of Things Connectivity Framework. 2022. Available online: https://www.iiconsortium.org/iicf/ (accessed on 3 February 2025).
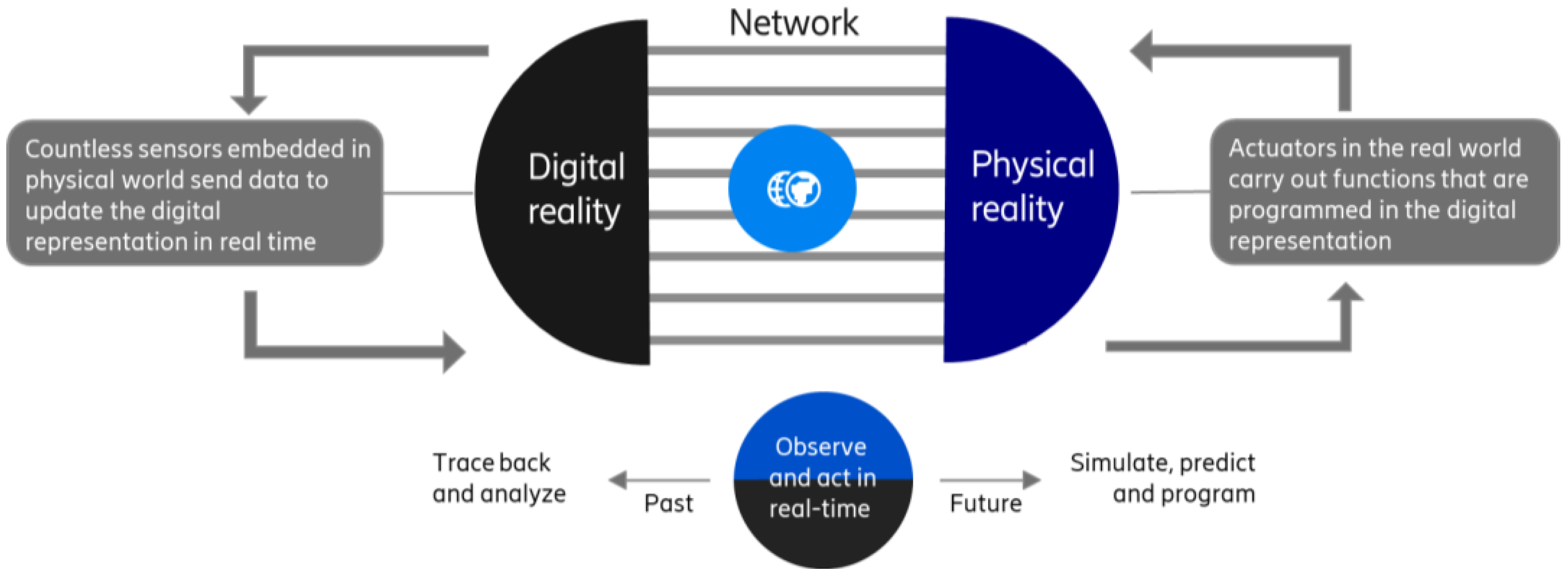
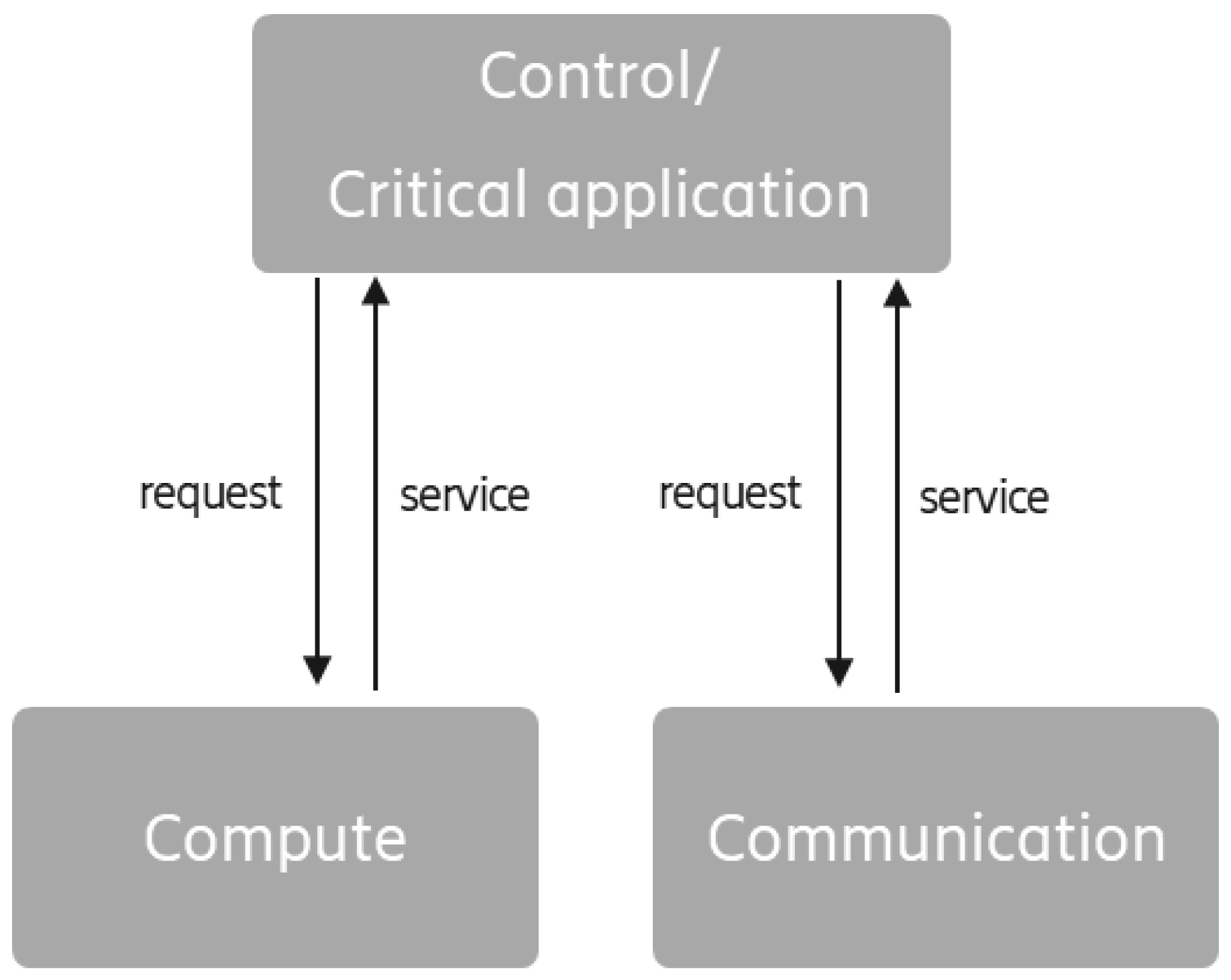


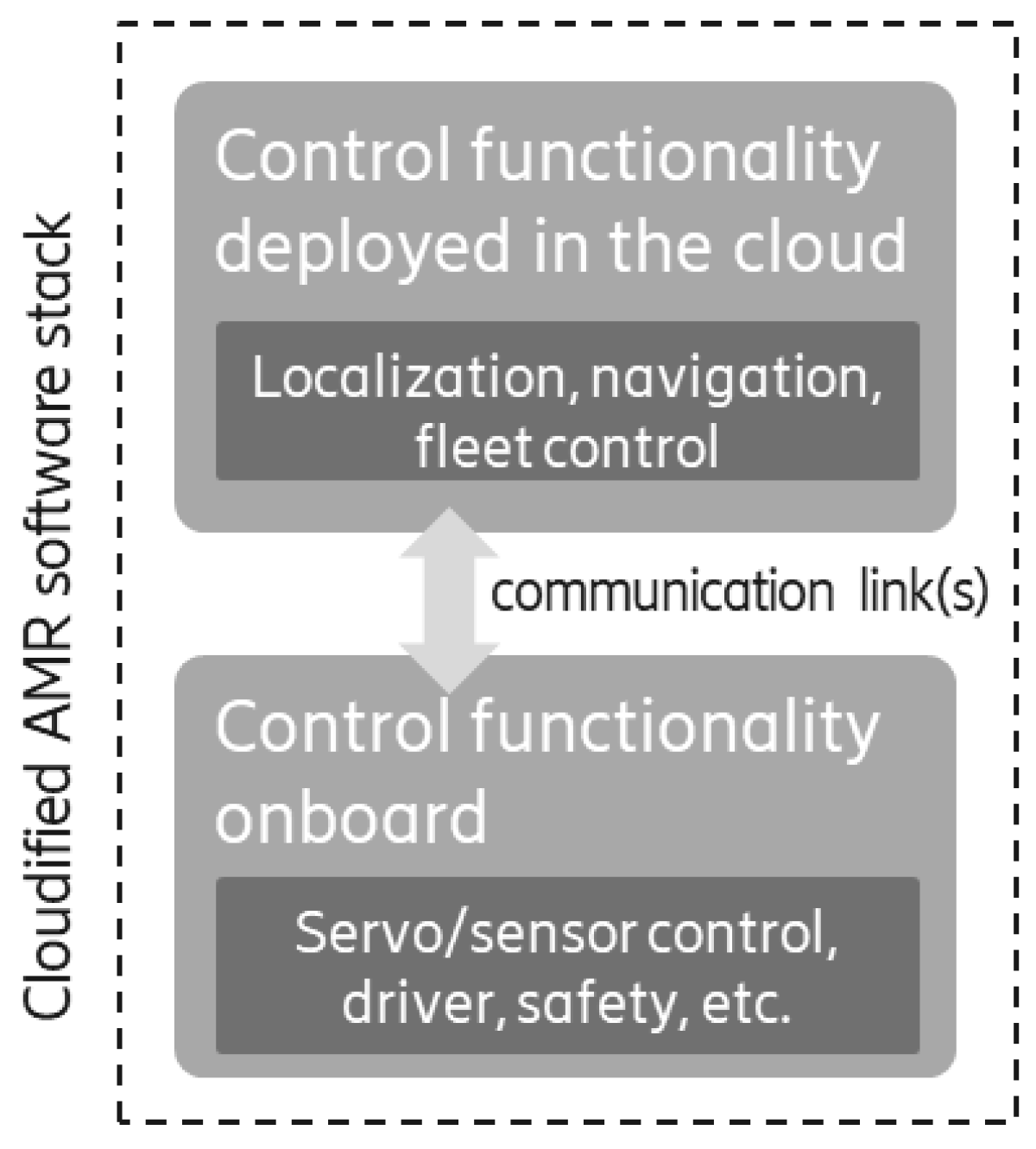
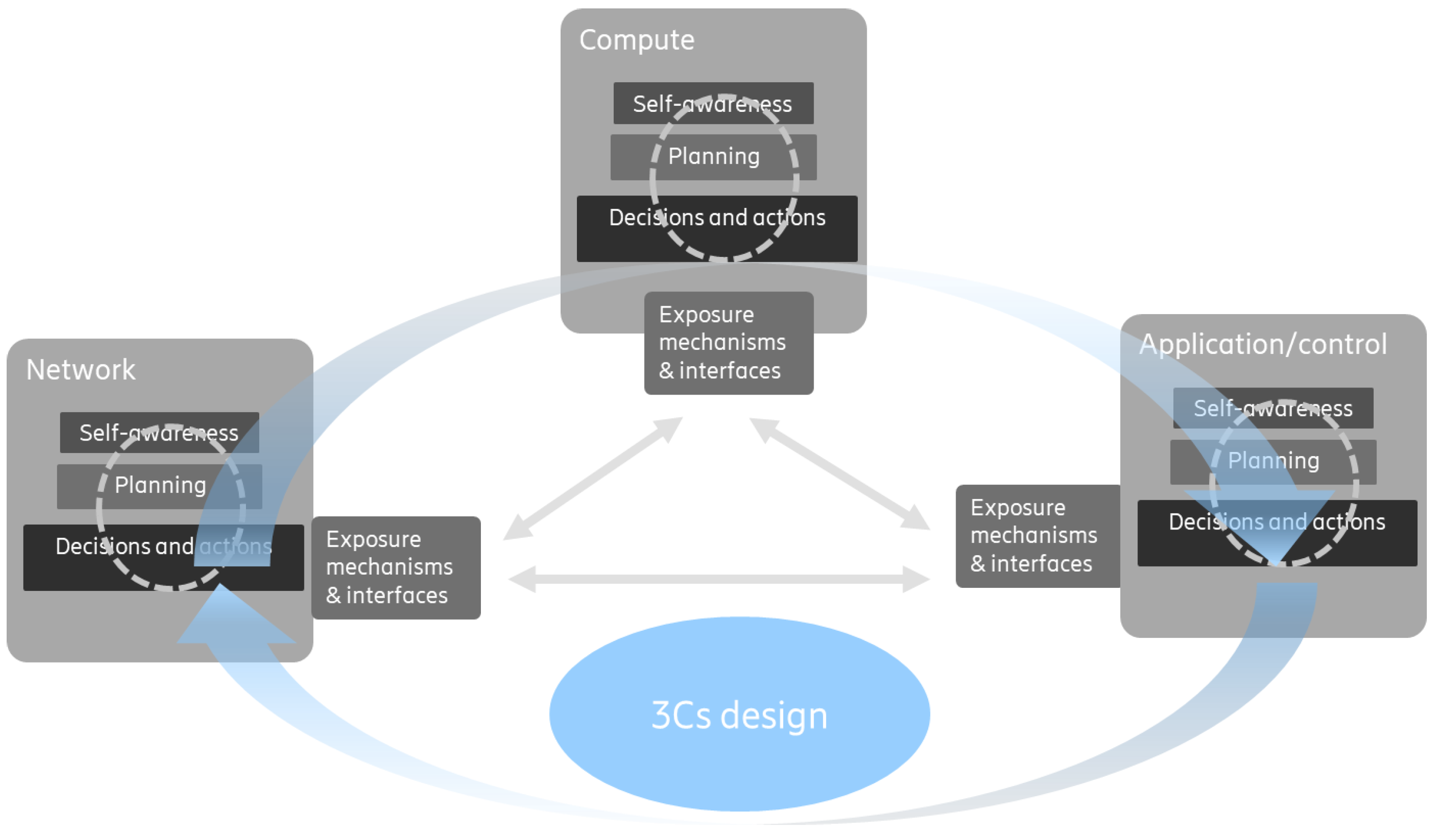
| Ref. | Domain | Theoretical/Concept Work | Practical Aspects | Findings |
|---|---|---|---|---|
| [15,32] | Compute | Cloud-Fog Automation (CFA) architecture | Measurements in real-time control systems | CFA is needed, but major challenges are still open (latency, reliability, time synch., etc.). Possible promising direction is control-communication co-design. |
| [33] | Compute (survey) | System-level architectures facilitating the collaboration of cloud computing with advanced robotics | Specific robotics applications and the corresponding domain knowledge | Gaps and future research directions are identified for higher utilization and inclusion of cloud-based robotic systems in real-life problems. |
| [35] | Compute | Performance evaluation methodology of containerized edge-cloud architecture | Edge-cloud connectivity models benchmarked | The performance of current edge-cloud implementations with respect to. concurrency, RTT and message sending interval must be improved. |
| [36] | Compute | Framework of RoboKube | Robot teleoperation | RoboKube accelerates CFA and facilitates the integration of cloud and ROS ecosystem. |
| [39,40] | NCS (survey) | Network imperfections impact on control performance | Mobile robots, drones | New communication solutions needed to improve the flexibility and decrease time-dependability. |
| [13] | NCS (survey) | Protocol design for wireless industrial communications | Ultra-wideband (UWB) and cognitive radios | Wireless sensor networks and UWB technologies are promising approaches. |
| [42] | WNCS, control theory | Robost MPC-based solution against packet loss | Evaluation against normal MPC | Solution incorporates explicit bandwidth constraints and is robust to bounded packet loss. |
| [44] | Co-design of communication and control | Internal model control-inspired latency-aware wireless control framework | Realistic evaluation using Ball-and-Beam case study | Proposed framework eliminates the efforts of building and tuning entire controller in real control system. |
| [45] | Co-design of communication and control | Existing co-design methods summarized | Cloud controlled AGV | Optimized AGV controller lowers resource consumption. |
| [46] | Co-design of communication and control | Network hardware-in-the-loop framework | Several realistic robot control use cases | Framework provides more trustworthy results than statistical modeling. |
| [3] | Co-design of communication and control | Co-design opportunities, challenges, and open issues | Packetized predictive control case study | Co-design can reduce the gap between the requirements of real-time control systems and the performance of today’s wireless systems. |
| [47,48,49] | Dependability of communication and compute | Dependability concept for critical real-time applications | Smart farming, adaptive manufacturing, XR | Dependability of communication and compute are required in infrastructures to support critical real-time applications. |
| Degree | Description of Application Design Approach | Type of Application |
|---|---|---|
| 0 | Unawareness Control applications with no awareness of network and computing resources. | Non-critical applications with no requirements towards dependability. |
| 1 | Co-design with awareness Control applications with awareness on general characteristics of network and compute. | Non-critical applications with limited requirements towards dependability. |
| 2 | Co-design with interfacing for information sharing Control applications designed using exposure interfaces towards network and/or compute. | Non-critical/critical applications with moderate requirements towards dependability. |
| 3 | Co-design with interaction for configuration Control applications designed using exposure interfaces as well as making service requests towards network and/or compute. | Critical applications with stringent requirements towards dependability. |
| 4 | Co-design with negotiation Control applications designed to negotiate with network and compute infrastructure to achieve a common overarching goal. | Critical applications with stringent requirements towards dependability optimized in a larger context. |
| Degree | Key Advantages of the Approach | Challenges of the Approach |
|---|---|---|
| 0 | Simplicity in application design. | Fails to support the application if resource constraints or variation in network/compute conditions may occur. |
| 1 | Simplicity in application design. Allows for handling of a very limited variation in resource conditions. | Requires a general high-level awareness of the application on the network/compute resources it needs. The application needs to implement simple handling of varying resource conditions. |
| 2 | Allows for more advanced handling of variations in resource conditions. No need to implement other than best-effort service requests. | Requires self-awareness of the application to understand own needs to respond to changing conditions in network/compute resources. The application needs to implement more advanced handling. |
| 3 | The application can rely on dependable communication and compute services via explicit requests. Dependability builds on “contractual” (explicit) interactions. Resilient application design for highest levels of dependability. Efficient use of compute and network resources. | Requires detailed self-awareness of application/network/compute on own needs and requirements to support and request future services. Additional implementation complexity to handle and switch between different operation modes and request other than best-effort services. |
| 4 | The application contributes in the most constructive way towards a larger context. | Automated negotiation principles with potentially conflicting interests. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Grosjean, L.; Sachs, J.; Ansari, J.; Reider, N.; Hernandez Herranz, A.; Holmberg, C. A Framework for Communication–Compute–Control Co-Design in Cyber–Physical Systems. Electronics 2025, 14, 864. https://doi.org/10.3390/electronics14050864
Grosjean L, Sachs J, Ansari J, Reider N, Hernandez Herranz A, Holmberg C. A Framework for Communication–Compute–Control Co-Design in Cyber–Physical Systems. Electronics. 2025; 14(5):864. https://doi.org/10.3390/electronics14050864
Chicago/Turabian StyleGrosjean, Leefke, Joachim Sachs, Junaid Ansari, Norbert Reider, Aitor Hernandez Herranz, and Christer Holmberg. 2025. "A Framework for Communication–Compute–Control Co-Design in Cyber–Physical Systems" Electronics 14, no. 5: 864. https://doi.org/10.3390/electronics14050864
APA StyleGrosjean, L., Sachs, J., Ansari, J., Reider, N., Hernandez Herranz, A., & Holmberg, C. (2025). A Framework for Communication–Compute–Control Co-Design in Cyber–Physical Systems. Electronics, 14(5), 864. https://doi.org/10.3390/electronics14050864







