Hybrid Control Strategy for DC Microgrid Against False Data Injection Attacks and Sensor Faults Based on Lagrange Extrapolation and Voltage Observer
Abstract
:1. Introduction
- (i)
- The proposed detection algorithm effectively identifies both sensor faults and FDI attacks independently and simultaneously without affecting the detection accuracy of each other. In the proposed scheme, third-order Lagrange extrapolation and voltage observer are utilized to monitor the abnormalities in the DCLV sensors and DCLs, respectively. The proposed approach is simple and precise without mutual interference which degrades the accuracy of other detection algorithms. As a result, the proposed identification algorithms play a critical role in enhancing a DCMG system’s reliability against potential system disruptions.
- (ii)
- To maintain the DCMG system stability even under FDI attacks and DCLV sensor failures, a hybrid control strategy is proposed by combining the decentralized and distributed control methods for achieving power management. Upon detecting the FDI attacks, the power agent operation is changed to the decentralized control mode to eliminate the negative impact of FDI attacks. On the other hand, when the voltage sensor fault occurs in a power agent, the corresponding power agent shifts the operation to the current control mode because the voltage control is not possible. This hybrid approach enables the DCMG system to operate continuously even under such emergency conditions by properly changing the operation modes of power agents.
- (iii)
- Finally, a series of simulations and experimental tests are conducted to demonstrate the feasibility of the proposed hybrid control strategy. In particular, to highlight the robustness and reliability of the proposed strategy, the proposed DCMG system has been evaluated under various conditions, including normal operation, FDI attacks in DCLs, and DCLV sensor failures. It is confirmed from these test results that the proposed scheme effectively maintains voltage regulation and power balance in the presence of FDI cyber attacks and sensor faults.
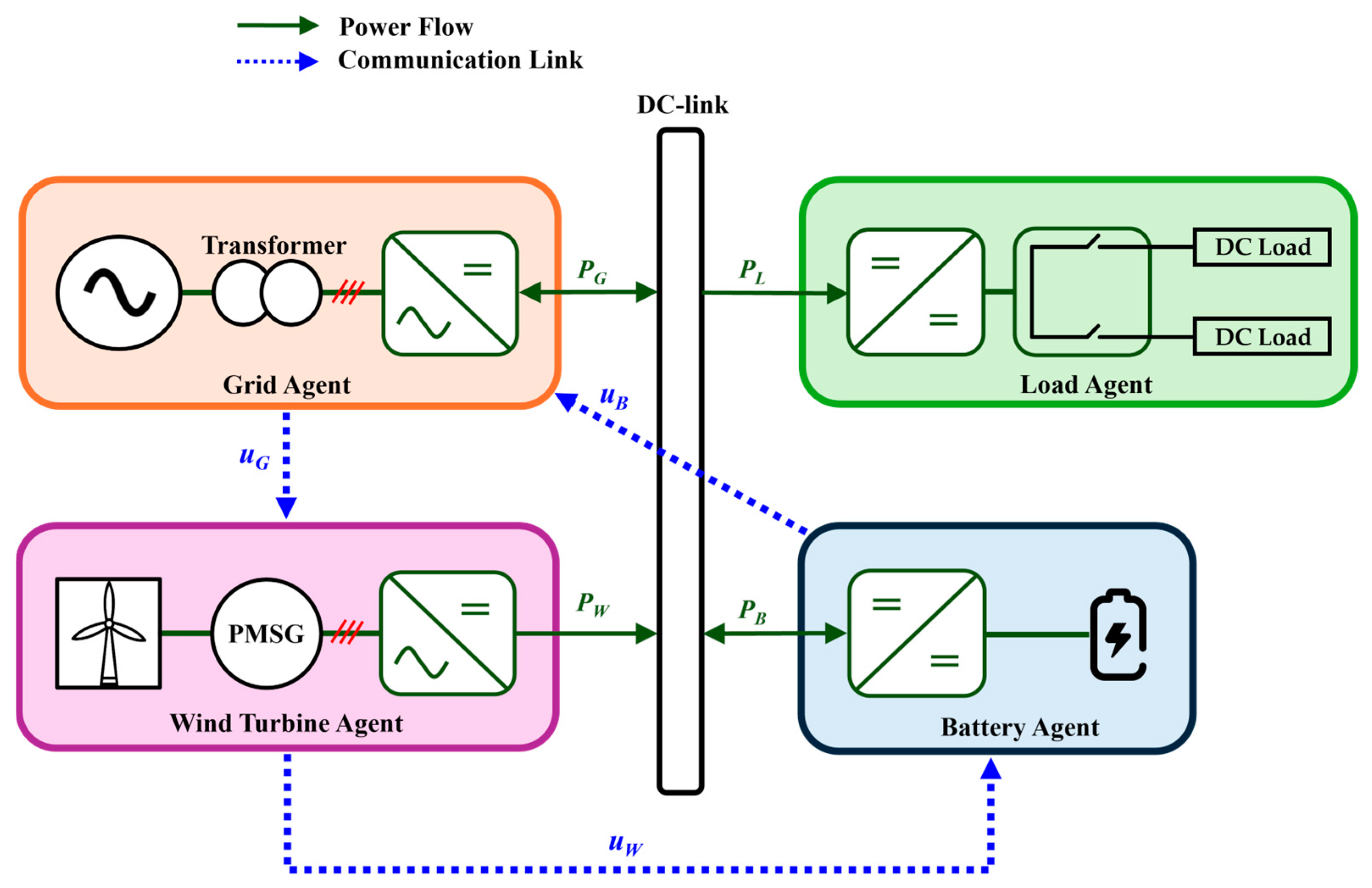
2. Description of Distributed DCMG System
3. Proposed Hybrid Control Strategy Under FDI Attacks and Sensor Faults
3.1. Hybrid Control Scheme of Power Agents
3.2. Detection of FDI Attacks Using Lagrange Extrapolation and Hybrid Control Method
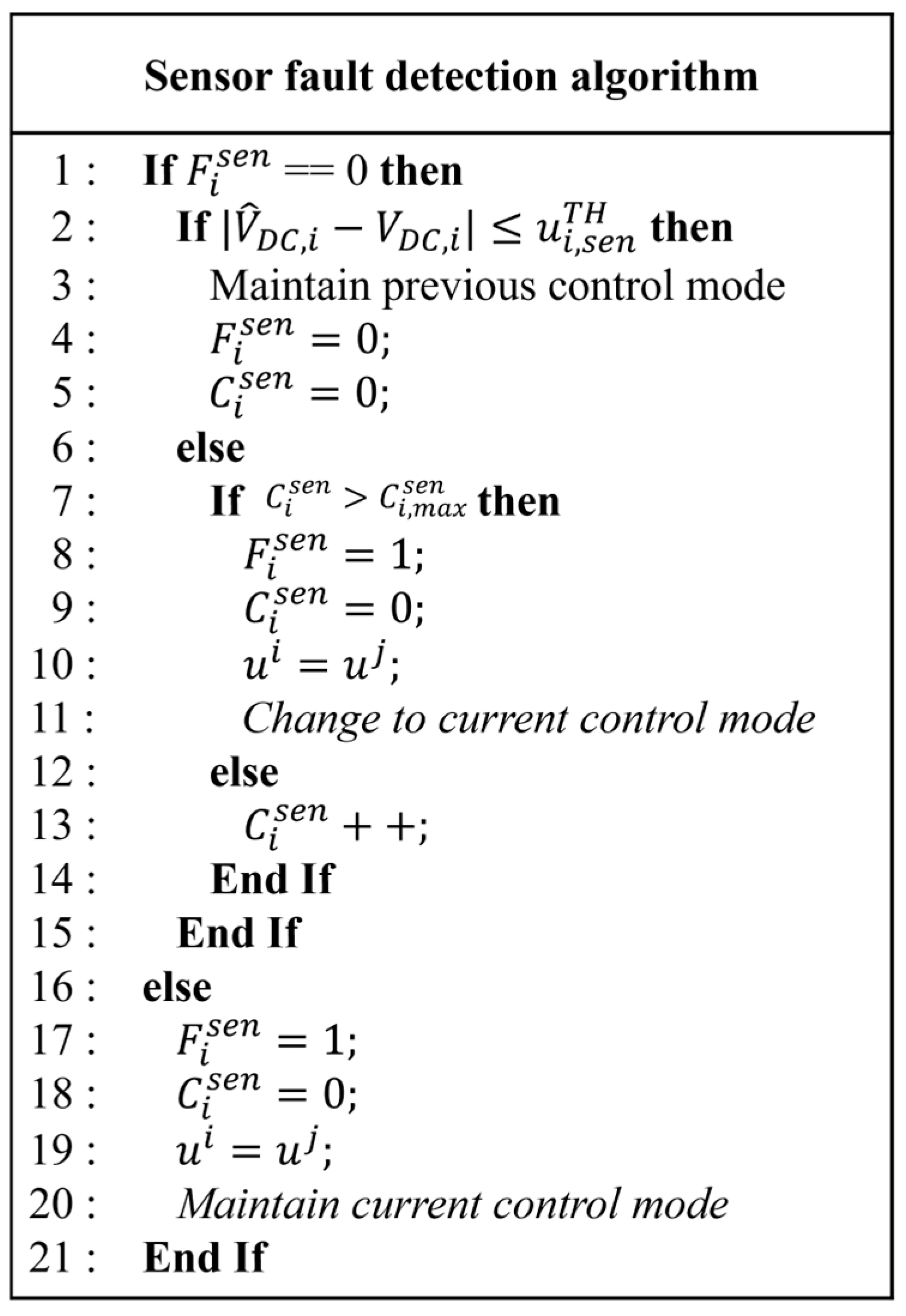
3.3. Detection of DCLV Sensor Failure and Hybrid Control Method
4. Simulation Results
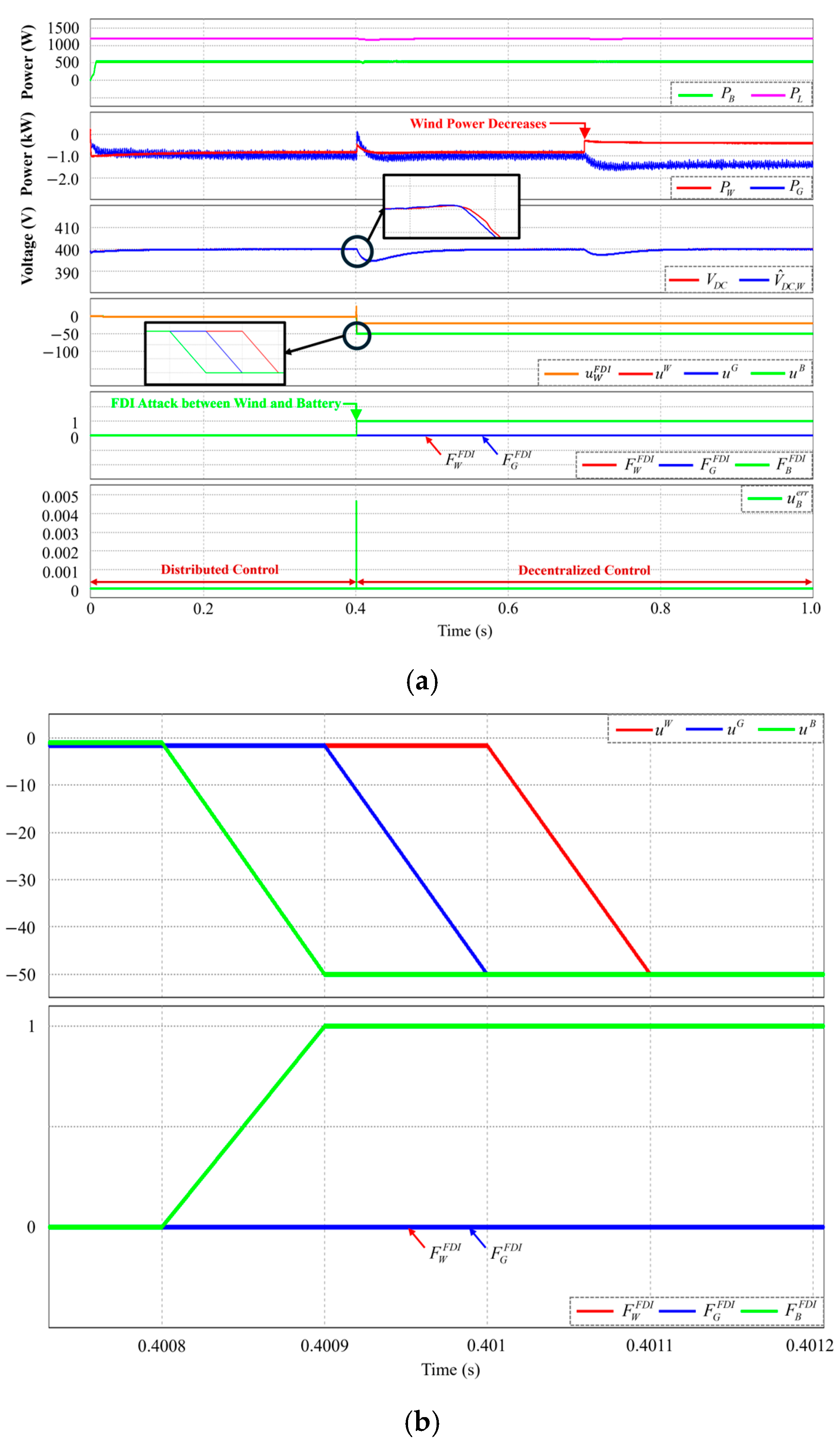
4.1. Power Variation in Wind Turbine Agent Under FDI Attack
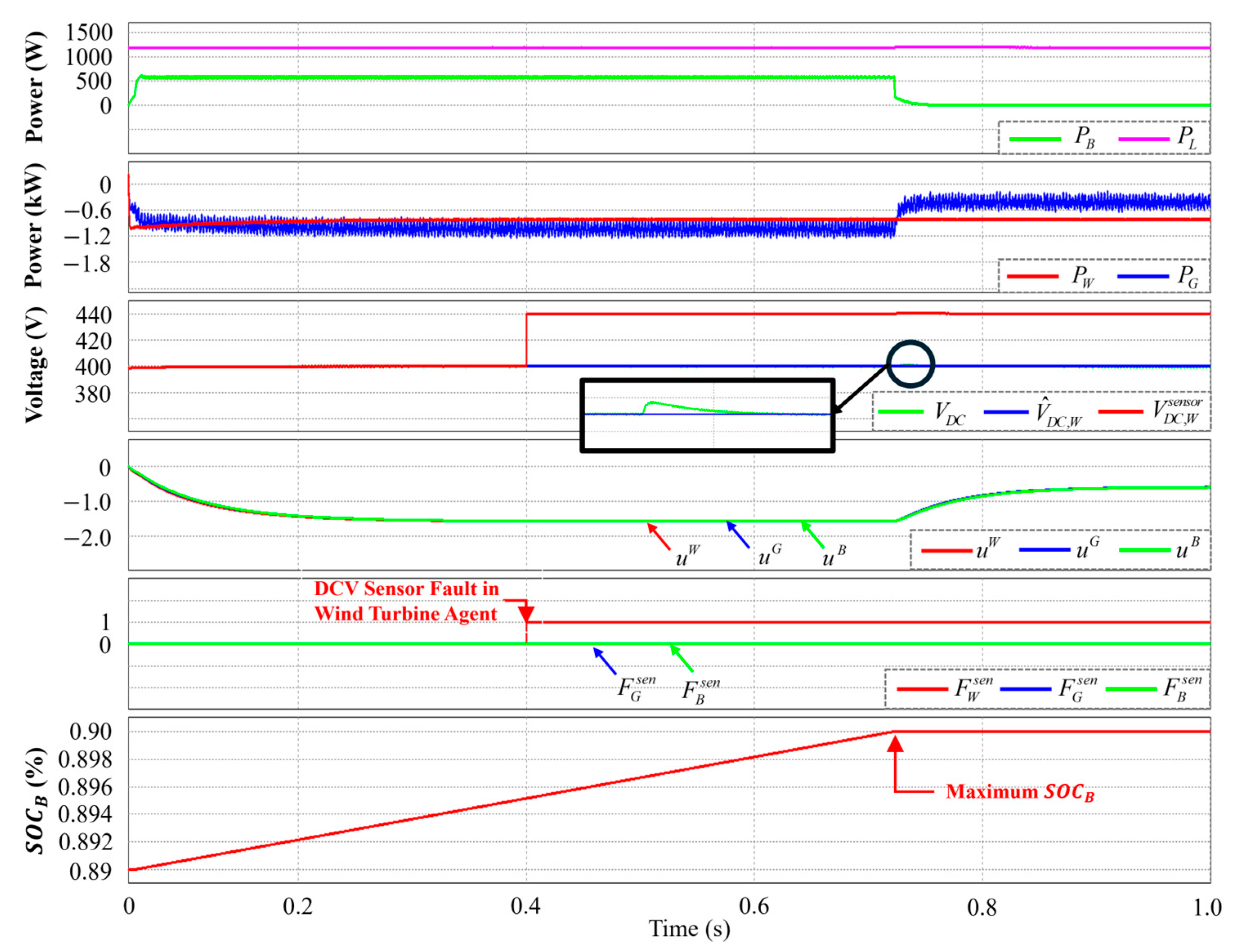
4.2. Case of Maximum Battery SOC Level Under DCLV Sensor Failure
4.3. Case of DCLV Sensor Failure and FDI Attack
4.4. Mode Transition Under FDI Attack
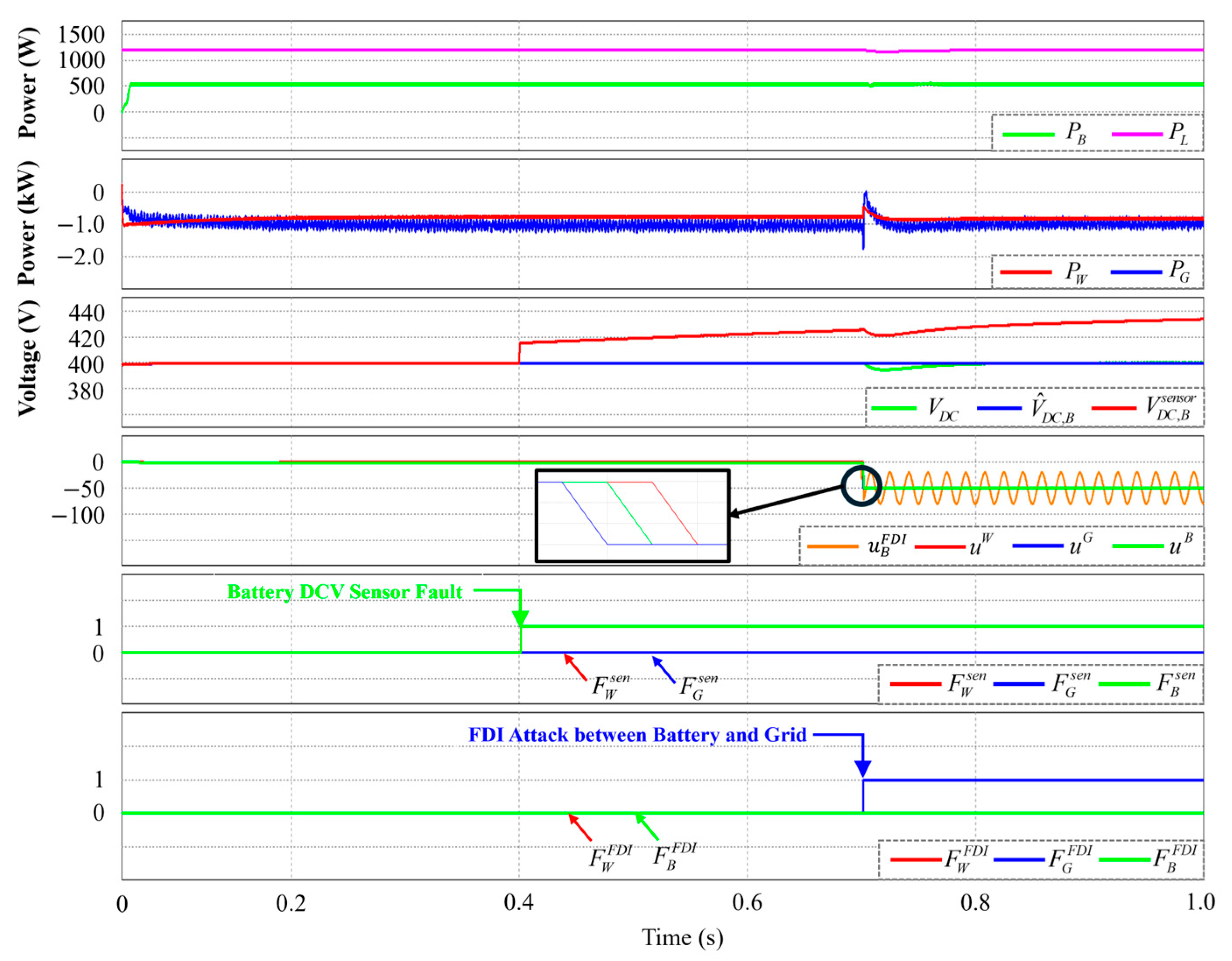
4.5. Simultaneous FDI Attack and DCLV Sensor Fault
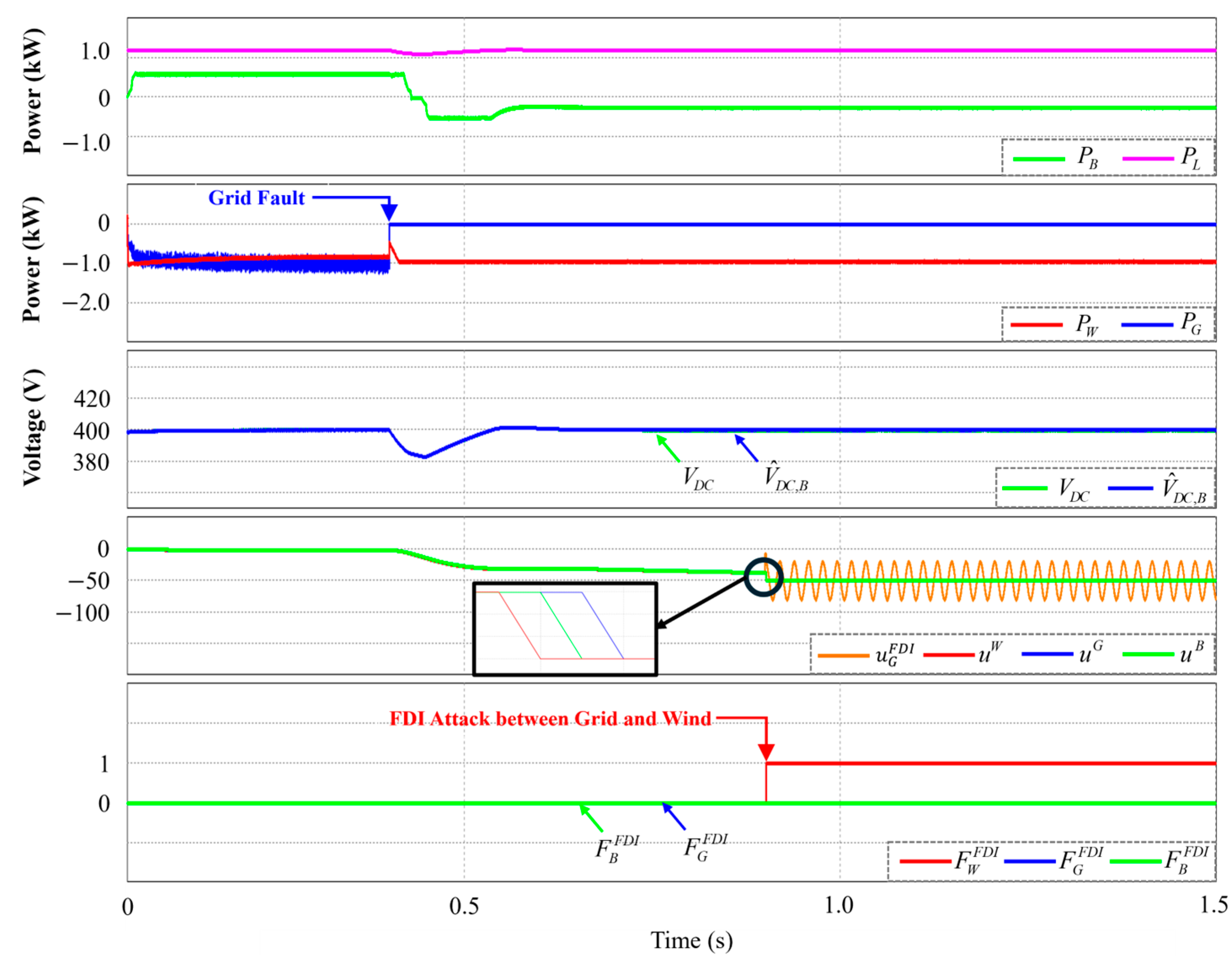
4.6. Grid Reconnection Under DCLV Sensor Failure
5. Experimental Results
5.1. Islanded Mode Under FDI Attack
5.2. Transition from Grid-Connected Mode to Islanded Mode
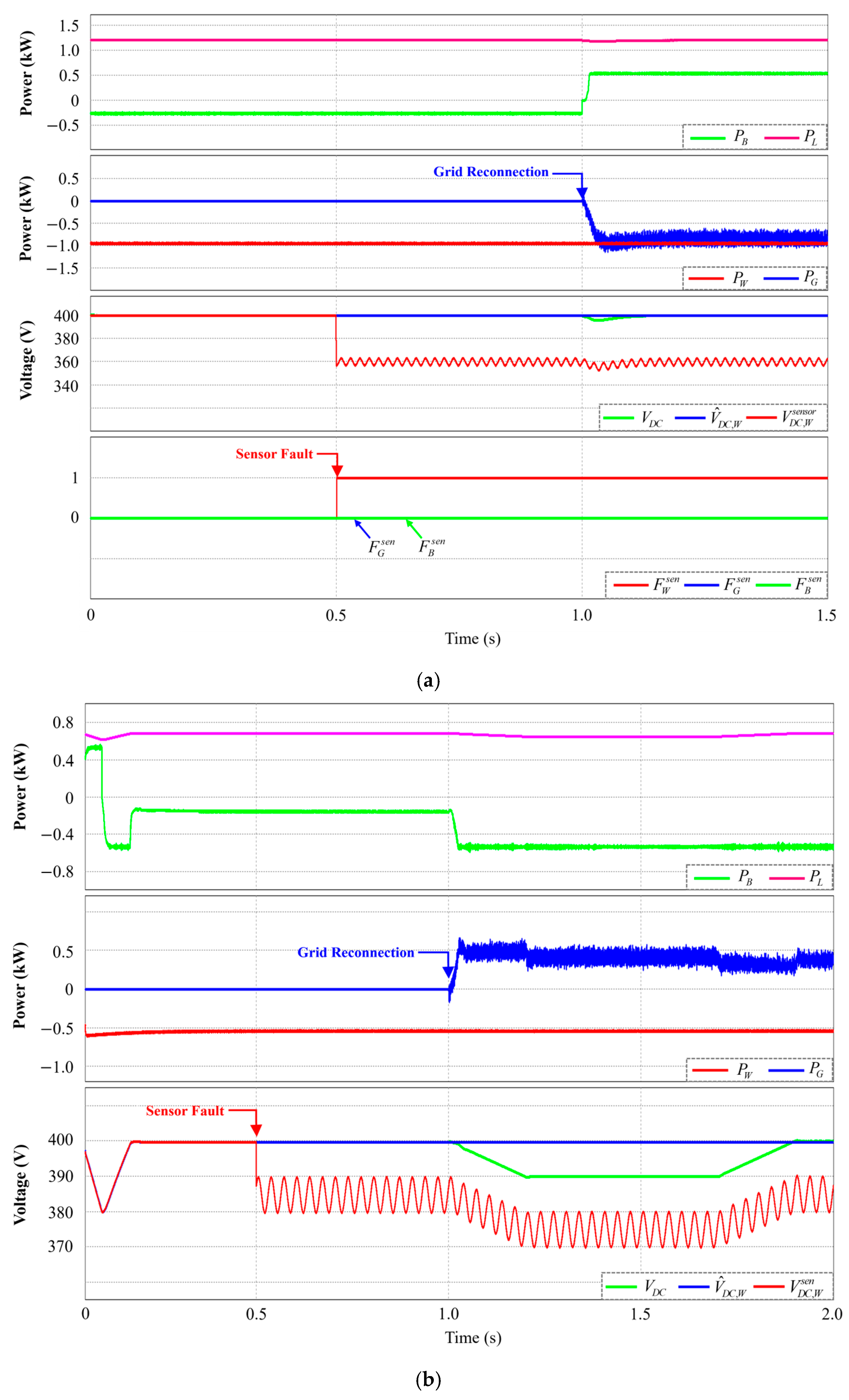
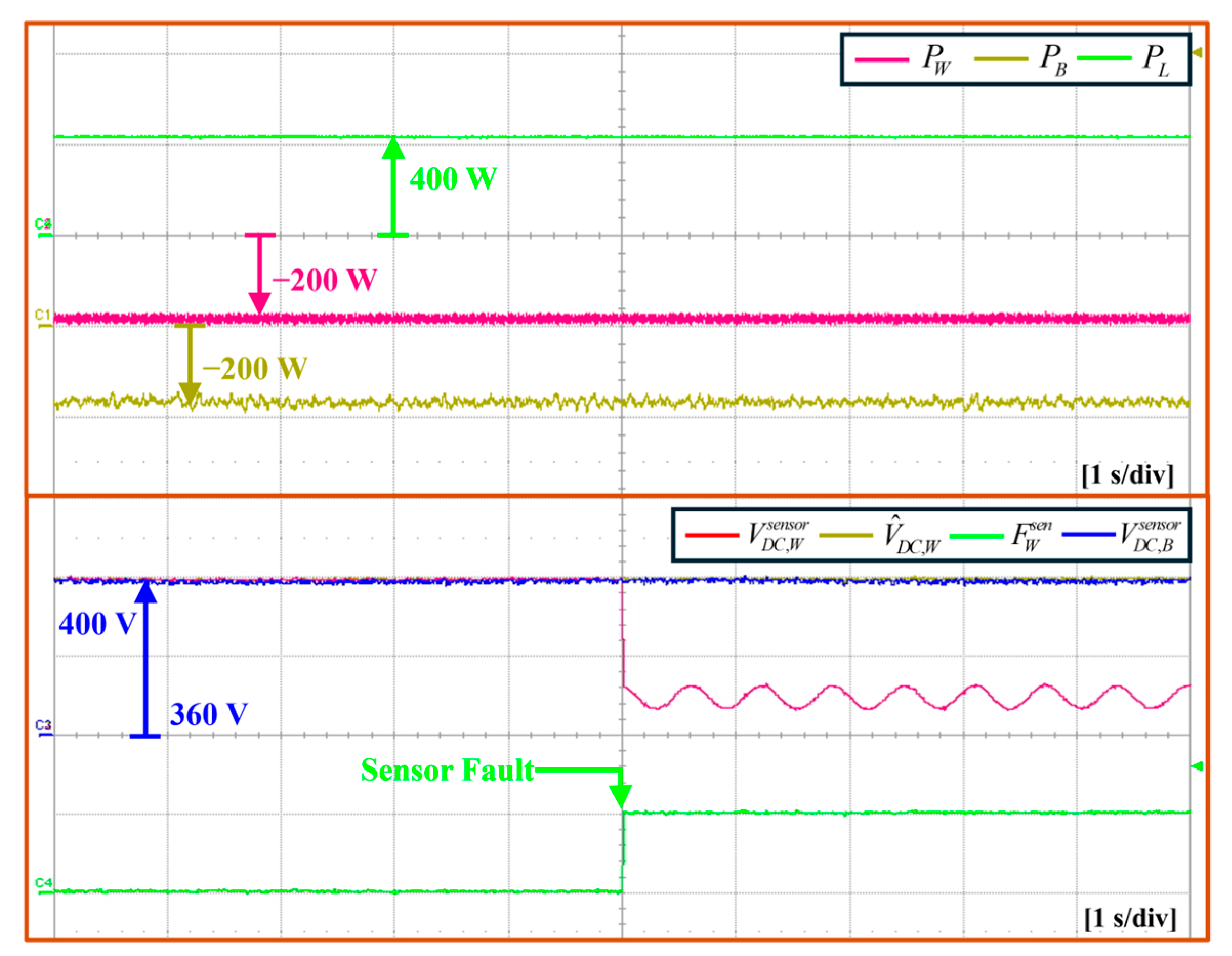
5.3. Grid-Connected Mode Under DCLV Sensor Failure
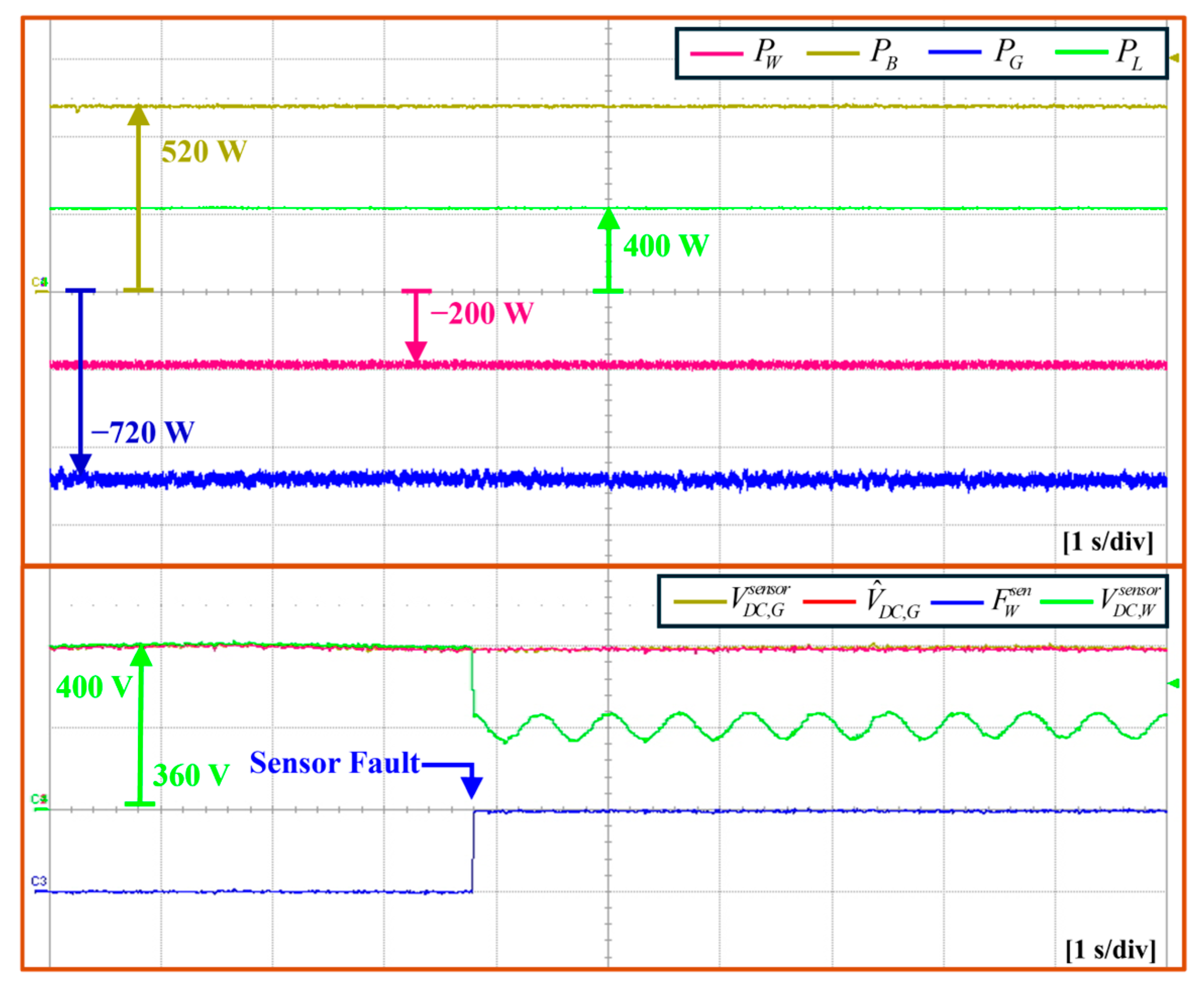
5.4. Islanded Mode Under DCLV Sensor Failure
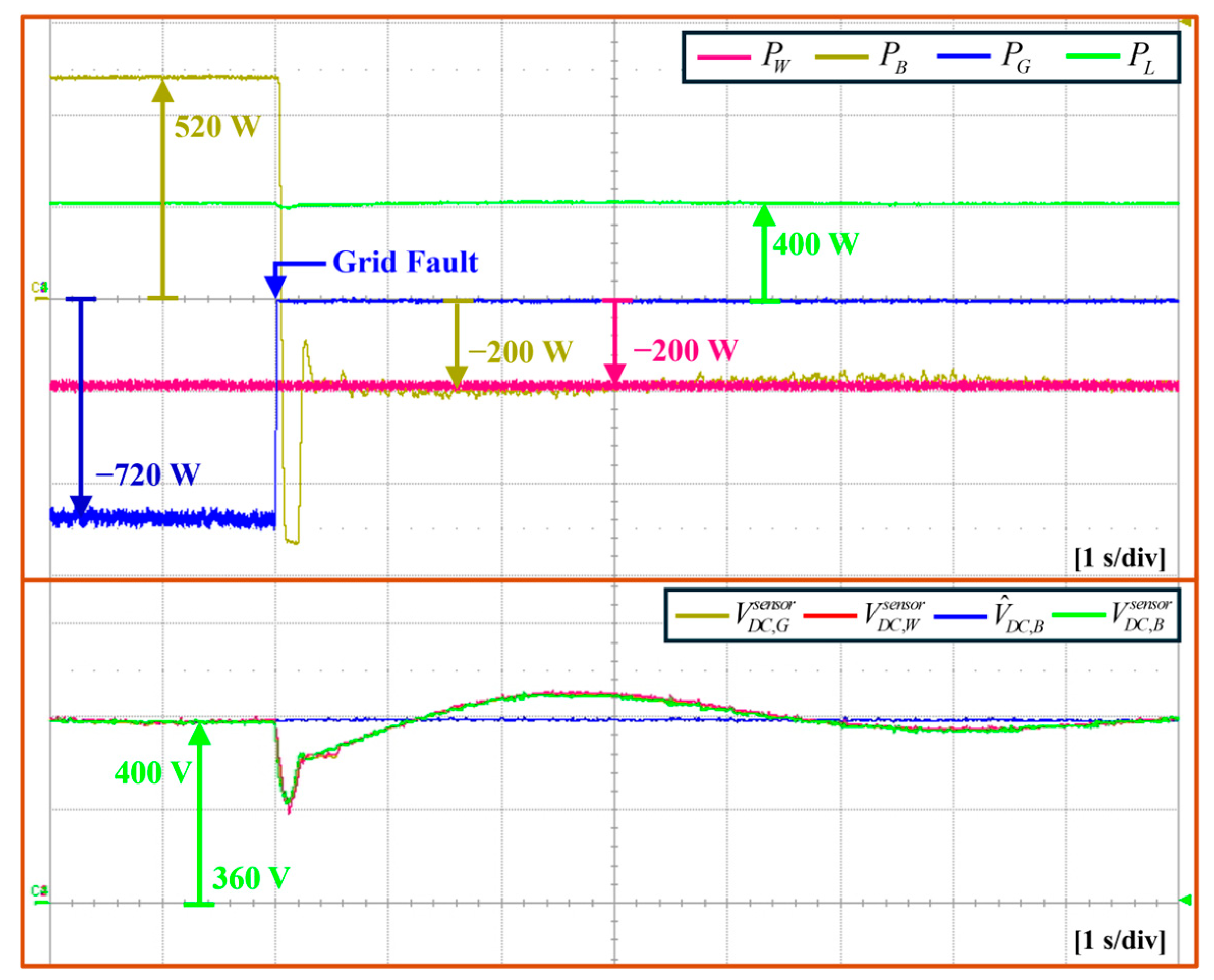
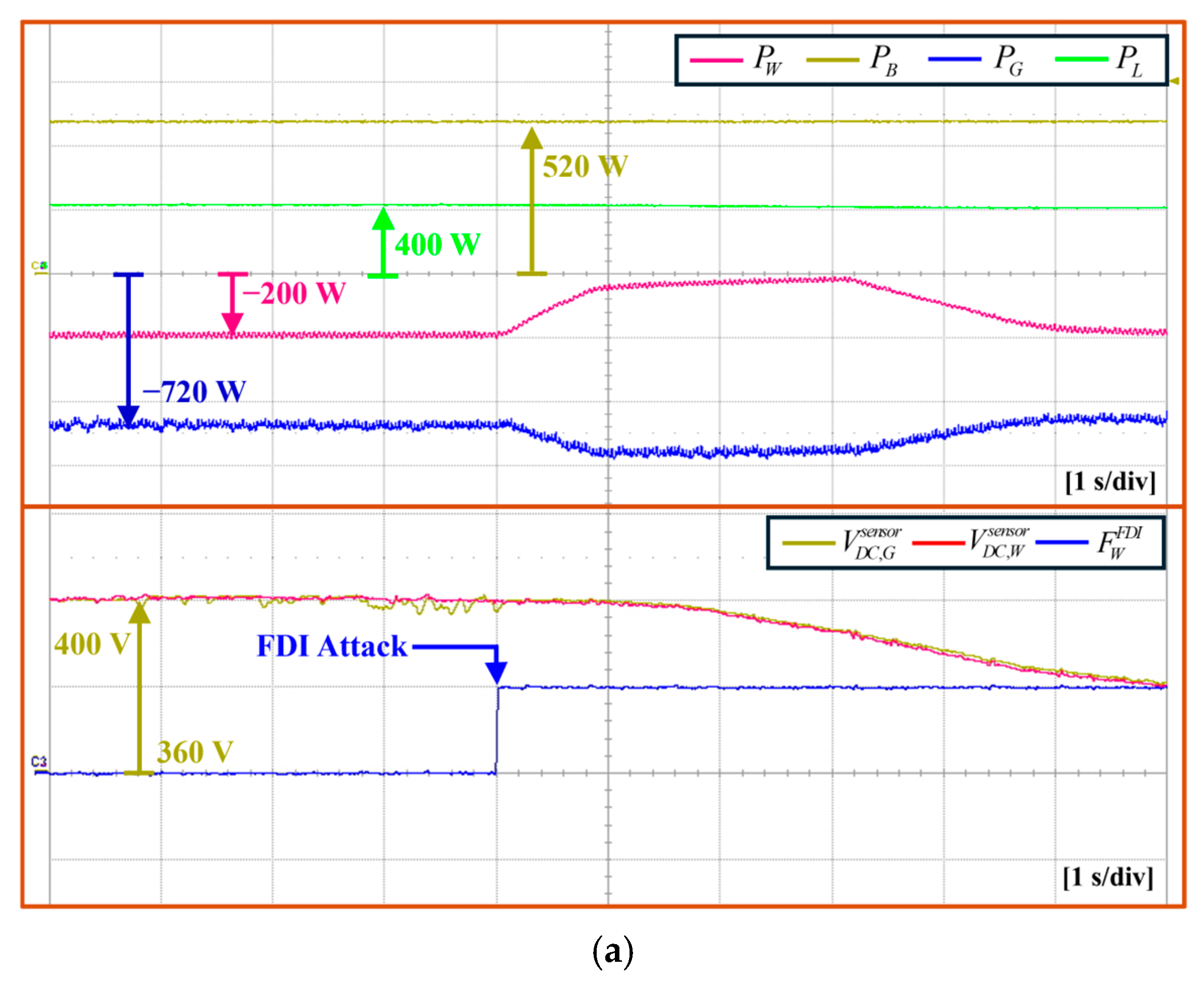
5.5. Gird-Connected Mode Under FDI Attack
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Qazi, A.; Hussain, F.; Rahim, N.A.; Hardaker, G.; Alghazzawi, D.; Shaban, K.; Haruna, K. Towards sustainable energy: A systematic review of renewable energy sources, technologies, and public opinions. IEEE Access 2019, 7, 63837–63851. [Google Scholar] [CrossRef]
- Ahlgren, W.L. The dual-fuel strategy: An energy transition plan. Proc. IEEE 2012, 100, 3001–3052. [Google Scholar] [CrossRef]
- Olivares, D.; Mehrizi-Sani, A.; Etemadi, A.; Canizares, C.; Iravani, R.; Kazerani, M.; Hajimiragha, A.; Gomis-Bellmunt, O.; Saeedifard, M.; Palma-Behnke, R.; et al. Trends in microgrid control. IEEE Trans. Smart Grid 2014, 5, 1905–1919. [Google Scholar] [CrossRef]
- Zhou, L.; Zhang, Y.; Lin, X.; Li, C.; Cai, Z.; Yang, P. Optimal sizing of PV and BESS for a smart household considering different price mechanisms. IEEE Access 2018, 6, 41050–41059. [Google Scholar] [CrossRef]
- Fan, Z.; Fan, B.; Liu, W. Distributed control of DC microgrids for optimal coordination of conventional and renewable generators. IEEE Trans. Smart Grid 2021, 12, 4607–4615. [Google Scholar] [CrossRef]
- Kumar, D.; Zare, F.; Ghosh, A. DC microgrid technology: System architectures, AC grid interfaces, grounding schemes, power quality, communication networks, applications, and standardizations aspects. IEEE Access 2017, 5, 12230–12256. [Google Scholar] [CrossRef]
- Keshavarzi, D.; Farjah, E.; Ghanbari, T. Hybrid DC circuit breaker and fault current limiter with optional interruption capability. IEEE Trans. Power Electron. 2018, 33, 2330–2338. [Google Scholar] [CrossRef]
- Lotfi, H.; Khodaei, A. AC versus DC microgrid planning. IEEE Trans. Smart Grid 2017, 8, 296–304. [Google Scholar] [CrossRef]
- Hossain, M.I.; Hamanah, W.M.; Alam, M.S.; Shafiullah, M.; Abido, M.A. Fault ride through and intermittency improvement of renewable energy integrated MMC-HVDC system employing flywheel energy storage. IEEE Access 2023, 11, 50528–50546. [Google Scholar] [CrossRef]
- Al-Ismail, F.S. DC microgrid planning, operation, and control: A comprehensive review. IEEE Access 2021, 9, 36154–36172. [Google Scholar] [CrossRef]
- Abbasi, M.; Abbasi, E.; Li, L.; Aguilera, R.P.; Lu, D.; Wang, F. Review on the microgrid concept, structures, components, communication systems, and control methods. Energies 2023, 16, 484. [Google Scholar] [CrossRef]
- Mehdi, M.; Kim, C.-H.; Saad, M. Robust centralized control for DC islanded microgrid considering communication network delay. IEEE Access 2020, 8, 77765–77778. [Google Scholar] [CrossRef]
- Dragičević, T.; Lu, X.; Vasquez, J.C.; Guerrero, J.M. DC microgrids—Part I: A review of control strategies and stabilization techniques. IEEE Trans. Power Electron. 2016, 31, 4876–4891. [Google Scholar]
- Guo, F.; Xu, Q.; Wen, C.; Wang, L.; Wang, P. Distributed secondary control for power allocation and voltage restoration in islanded DC microgrids. IEEE Trans. Sustain. Energy 2019, 9, 1857–1869. [Google Scholar] [CrossRef]
- Anand, S.; Fernandes, B.G.; Guerrero, J. Distributed control to ensure proportional load sharing and improve voltage regulation in low-voltage DC microgrids. IEEE Trans. Power Electron. 2012, 28, 1900–1913. [Google Scholar] [CrossRef]
- Lu, X.; Guerrero, J.M.; Sun, K.; Vasquez, J.C. An improved droop control method for dc microgrids based on low bandwidth communication with dc bus voltage restoration and enhanced current sharing accuracy. IEEE Trans. Power Electron. 2014, 29, 1800–1812. [Google Scholar] [CrossRef]
- Huang, P.H.; Liu, P.C.; Xiao, W.; El Moursi, M.S. A novel droop-based average voltage sharing control strategy for DC microgrids. IEEE Trans. Smart Grid 2015, 6, 1096–1106. [Google Scholar] [CrossRef]
- Sahoo, S.K.; Sinha, A.K.; Kishore, N.K. Control techniques in AC, DC, and hybrid AC-DC microgrid: A review. IEEE J. Emerg. Sel. Top. Power Electron. 2018, 6, 738–759. [Google Scholar] [CrossRef]
- Yazdanian, M.; Mehrizi-Sani, A. Distributed control techniques in microgrids. IEEE Trans. Smart Grid 2014, 5, 2901–2909. [Google Scholar] [CrossRef]
- Sahoo, S.; Mishra, S. An adaptive event-triggered communication-based distributed secondary control for DC microgrids. IEEE Trans. Smart Grid 2018, 9, 6674–6683. [Google Scholar] [CrossRef]
- Gao, F.; Bozhko, S.; Asher, G.; Wheeler, P.; Patel, C. An improved voltage compensation approach in a droop-controlled DC power system for the more electric aircraft. IEEE Trans. Power Electron. 2016, 31, 7369–7383. [Google Scholar] [CrossRef]
- Dong, M.; Li, L.; Nie, Y.; Song, D.; Yang, J. Stability analysis of a novel distributed secondary control considering communication delay in DC microgrids. IEEE Trans. Smart Grid 2019, 10, 6690–6700. [Google Scholar] [CrossRef]
- Islam, S.; Agarwal, S.; Shyam, A.B.; Ingle, A.; Thomas, S.; Anand, S.; Sahoo, S.R. Ideal current-based distributed control to compensate line impedance in DC microgrid. IET Power Electron. 2018, 11, 1178–1186. [Google Scholar] [CrossRef]
- Sahoo, S.; Mishra, S.; Peng, C.H.; Dragicevic, T. A stealth cyber attack detection strategy for DC microgrids. IEEE Trans. Power Electron. 2019, 34, 8162–8174. [Google Scholar] [CrossRef]
- Liu, X.K.; Wen, C.; Xu, Q.; Wang, Y.W. Resilient control and analysis for DC microgrid system under DoS and impulsive FDI attacks. IEEE Trans. Smart Grid 2021, 12, 3742–3754. [Google Scholar] [CrossRef]
- Zhang, G.; Tong, D.; Chen, Q.; Zhou, W. Sliding mode control against false data injection attacks in DC microgrid systems. IEEE Syst. J. 2023, 17, 6159–6168. [Google Scholar] [CrossRef]
- Chandra, M.V.S.S.; Mohapatro, S. Hybrid sensor fault tolerant control of low voltage DC microgrid. IEEE Trans. Ind. Appl. 2024, 60, 1705–1715. [Google Scholar] [CrossRef]
- Vafamand, N.; Arefi, M.M.; Asemani, M.H.; Javadi, M.S.; Wang, F.; Catalão, J.P. Dual-EKF-based fault-tolerant predictive control of nonlinear DC microgrids with actuator and sensor Faults. IEEE Trans. Ind. Appl. 2022, 58, 5438–5446. [Google Scholar] [CrossRef]
- Tan, S.; Xie, P.; Guerrero, J.M.; Vasquez, J.C.; Han, R. Cyberattack detection for converter-based distributed dc microgrids: Observer-based approaches. IEEE Ind. Electron. Mag. 2022, 16, 67–77. [Google Scholar] [CrossRef]
- Jo, S.-B.; Tran, D.T.; Jabbar, M.A.M.; Kim, M.; Kim, K.-H. Continuous power management of decentralized DC microgrid based on transitional operation modes under system uncertainty and sensor failure. Sustainability 2024, 16, 4925. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, G.; Ye, Z. Dynamic mode extrapolation to improve the efficiency of dual time stepping method. J. Comput. Phys. 2018, 352, 190–212. [Google Scholar] [CrossRef]
- Madichetty, S.; Mishra, S. Cyber attack detection and correction mechanisms in a distributed DC microgrid. IEEE Trans. Power Electron. 2022, 37, 1476–1485. [Google Scholar]







| Power Agents | Parameters | Value |
|---|---|---|
| DC-link | Nominal DCLV | 400 V |
| Capacitance | 4 mF | |
| Grid agent | Transformer Y/Δ | 380/220 V |
| Grid voltage | 220 V | |
| Grid frequency | 60 Hz | |
| Maximum absorbing power | 2000 W | |
| Maximum supporting power | −2000 W | |
| Wind turbine agent | PMSG number of poles | 6 |
| PMSG inertia | 0.111 kgm2 | |
| PMSG flux linkage | 0.18 Wb | |
| Converter filter inductance | 7 mH | |
| Maximum power | −1500 W | |
| Battery agent | Minimum level of SOC | 20% |
| Maximum level of SOC | 90% | |
| Maximum voltage | 180 V | |
| Rated capacity | 25 Ah | |
| Limitation level of charging power | 540 W | |
| Limitation level of discharging power | −540 W | |
| Maximum input voltage | 300 V | |
| Maximum input current | 6 A | |
| Maximum input power | 800 W | |
| Load agent | Load 1 | 200 W |
| Load 2 | 200 W | |
| Load 3 | 200 W |
| Distributed Control [26] | Distributed Control [27,28] | Decentralized Control [30] | Proposed Scheme | |
|---|---|---|---|---|
| FDI attack | Considered | Not considered | Not considered | Considered |
| Sensor fault | Not considered | Considered | Considered | Considered |
| Performance Parameter | Specification |
|---|---|
| Clock frequency | 150 MHz |
| Cycle time | 6.67 ns |
| Floating-point precision | IEEE 754 single precision |
| ADC resolution | 12-bit |
| Conversion rate | 80 ns |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jo, S.-B.; Tran, D.T.; Nguyen, H.X.; Kim, M.; Kim, K.-H. Hybrid Control Strategy for DC Microgrid Against False Data Injection Attacks and Sensor Faults Based on Lagrange Extrapolation and Voltage Observer. Electronics 2025, 14, 1087. https://doi.org/10.3390/electronics14061087
Jo S-B, Tran DT, Nguyen HX, Kim M, Kim K-H. Hybrid Control Strategy for DC Microgrid Against False Data Injection Attacks and Sensor Faults Based on Lagrange Extrapolation and Voltage Observer. Electronics. 2025; 14(6):1087. https://doi.org/10.3390/electronics14061087
Chicago/Turabian StyleJo, Seong-Bae, Dat Thanh Tran, Hieu Xuan Nguyen, Myungbok Kim, and Kyeong-Hwa Kim. 2025. "Hybrid Control Strategy for DC Microgrid Against False Data Injection Attacks and Sensor Faults Based on Lagrange Extrapolation and Voltage Observer" Electronics 14, no. 6: 1087. https://doi.org/10.3390/electronics14061087
APA StyleJo, S.-B., Tran, D. T., Nguyen, H. X., Kim, M., & Kim, K.-H. (2025). Hybrid Control Strategy for DC Microgrid Against False Data Injection Attacks and Sensor Faults Based on Lagrange Extrapolation and Voltage Observer. Electronics, 14(6), 1087. https://doi.org/10.3390/electronics14061087







