Cyber–Physical Resilience: Evolution of Concept, Indicators, and Legal Frameworks
Abstract
1. Introduction
- RQ1:
- How has the concept of resilience evolved in the context of cyber–physical complexities, and what is the current consensus?
- RQ2:
- What are the existing state-of-the-art indicators and methods available to assess and enhance resilience?
- RQ3:
- What are the most significant and emerging cyber–physical threats to critical infrastructures?
- RQ4:
- What is the impact of current European policies and initiatives on the security and resilience of critical infrastructures?
- Conceptual Evolution of Resilience: Provides a comprehensive synthesis of how the concept of resilience has evolved within cyber–physical systems, highlighting the shift from static robustness models to dynamic, adaptive, and systemic resilience frameworks.
- Assessment Methodologies: Reviews and classifies existing resilience indicators and assessment methods, emphasizing the need for standardized, real-time, and probabilistic models suitable for cyber–physical contexts.
- Threat Landscape Mapping: Identifies and categorizes emerging cyber–physical threats to critical infrastructures, including AI-driven attacks, supply chain vulnerabilities, and systemic risks arising from interdependencies across sectors.
- Policy and Governance Analysis: Evaluates the impact of key European policies such as the NIS-2 and CER Directives on critical infrastructure resilience, revealing gaps in harmonization, enforcement, and liability frameworks.
- Cross-Cutting Insight—Human–Machine Resilience: Proposes a novel research direction focusing on the integration of human oversight within automated resilience systems, bridging technical resilience with operational decision-making.
- Future-Oriented Contribution: Recommends the development of large-scale digital twin environments for resilience testing, enabling realistic simulation of cyber–physical threats and cross-sector cascading effects.
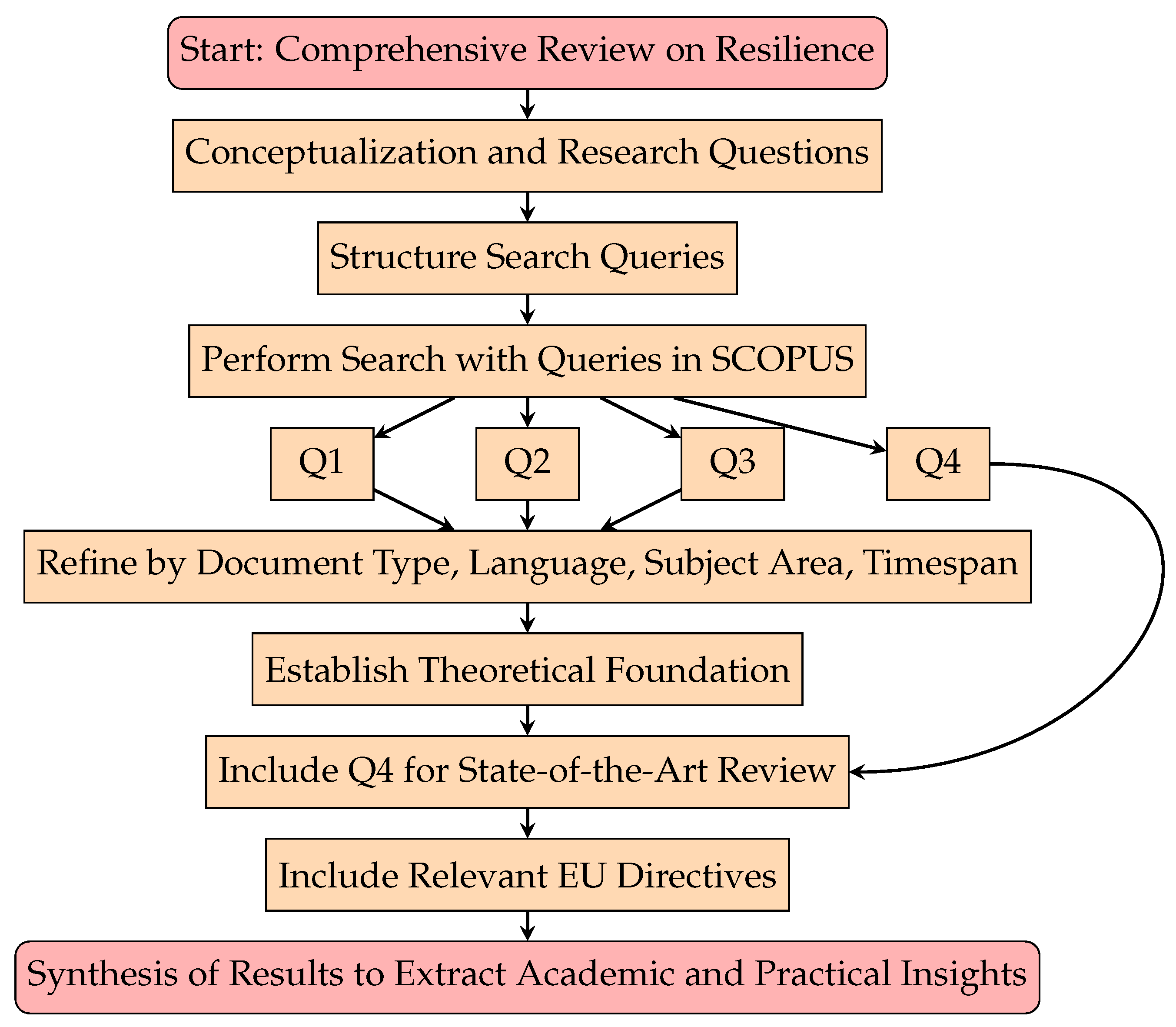
2. Methodology
- Q1
- TITLE-ABS-KEY (resilience AND (“Cyber*Physical” OR Complex System*)) Over 10,000 documents were initially identified; however, more than 2000 articles were not even cited one time (some after 10 years). On the other hand, many articles mentioned “resilience” superficially—often only in the abstract due to its trendiness—but this study focused on a more impactful subset. Specifically, only articles cited over 100 times were selected for review, resulting in a refined corpus of 273 publications.
- Q2
- TITLE-ABS-KEY ((resilience AND Protection) AND “Critical Infrastructure”) A total of 593 documents were identified; however, the majority exhibited a recurring issue—while the term “resilience” appeared in the abstract, it was not meaningfully discussed or even mentioned within the main body of the text.
- Q3
- TITLE-ABS-KEY ((Protection) AND “Critical Infrastructure”) Over 3000 documents were initially identified; articles cited over 100 times were selected for review, resulting in a refined corpus of 64 publications.
- Q4
- TITLE-ABS-KEY (resilience AND (“Critical Infrastructure” OR “critical entity”) AND (“Cyber*Physical” OR complex AND system*) AND (directive OR regulation OR policy))Refined by:
- Document Types: (Article or Review or Book)
- Languages: (English)
- Subject Areas: (LIMIT-TO (SUBJAREA, “ENGI”) OR LIMIT-TO (SUBJAREA, “COMP”) OR LIMIT-TO (SUBJAREA, “SOCI”) OR LIMIT-TO (SUBJAREA, “ENVI”) OR LIMIT-TO (SUBJAREA, “DECI”) OR LIMIT-TO (SUBJAREA, “ENER”) OR LIMIT-TO (SUBJAREA, “BUSI”) OR LIMIT-TO (SUBJAREA, “MATE”) OR LIMIT-TO (SUBJAREA, “ECON”) OR LIMIT-TO (SUBJAREA, “MEDI”) OR LIMIT-TO (SUBJAREA, “AGRI”) OR LIMIT-TO (SUBJAREA, “MULT”))
- Timespan: All years (Until the search was conducted in June 2024 for the current article)
3. Results and Discussion
3.1. Bibliometric Analysis of Cyber–Physical Resilience Research
| Title | Authors-Reference | Year | Cited by |
|---|---|---|---|
| Challenges in the vulnerability and risk analysis of critical infrastructures | Zio E. [27] | 2016 | 322 |
| Game-theoretic methods for robustness, security, and resilience of cyberphysical control systems: Games-in-games principle for optimal cross-layer resilient control systems | Zhu Q.; BaŞar T. [28] | 2015 | 315 |
| Understanding Compound, Interconnected, Interacting, and Cascading Risks: A Holistic Framework | Pescaroli G.; Alexander D. [29] | 2018 | 213 |
| Resilient control systems: Next generation design research | Rieger C.G.; Gertman D.I.; McQueen M.A. [30] | 2009 | 194 |
| Probabilistic framework to evaluate the resilience of engineering systems using Bayesian and dynamic Bayesian networks | Kammouh O.; Gardoni P.; Cimellaro G.P. [31] | 2020 | 178 |
| Resilience in railway transport systems: a literature review and research agenda | Bešinović N. [32] | 2020 | 177 |
| Review of major approaches to analyze vulnerability in power system | Abedi A.; Gaudard L.; Romerio F. [33] | 2019 | 162 |
| Complex approach to assessing resilience of critical infrastructure elements | Rehak D.; Senovsky P.; Hromada M.; Lovecek T. [34] | 2019 | 153 |
| Assessing and mapping urban resilience to floods with respect to cascading effects through critical infrastructure networks | Serre D.; Heinzlef C. [35] | 2018 | 134 |
| Performance and reliability of electrical power grids under cascading failures | Chang L.; Wu Z. [36] | 2011 | 109 |
| Doc | Title | Authors | Year |
|---|---|---|---|
| 1 | Building Resilience and Recoverability of Electric Grid Communications | Popik T.S.; Winks D. [37] | 2020 |
| 2 | Contextualizing resilience indicators–comparable across organizations yet specific to context | Sanne J.M.; Matschke Ekholm H.; Rahmberg M. [38] | 2021 |
| 3 | Systemic seismic vulnerability and risk assessment of urban infrastructure and utility systems | Poudel A.; Argyroudis S.; Pitilakis D.; Pitilakis K. [39] | 2022 |
| 4 | Input-output impact risk propagation in critical infrastructure interdependency | Owusu A.; Mohamed S.; Anissimov Y. [40] | 2019 |
| 5 | Indication of critical infrastructure resilience failure | Rehak D.; Hromada M.; Ristvej J. [41] | 2017 |
| 6 | City resiliency and underground space use | Sterling R.; Nelson P. [42] | 2013 |
| 7 | A middleware improved technology (MIT) to mitigate interdependencies between critical infrastructures | Balducelli C.; Di Pietro A.; Lavalle L.; Vicoli G. [43] | 2008 |
| 8 | An innovative approach for improving infrastructure resilience | Montgomery M.; Broyd T.; Cornell S.; Pearce O. [44] | 2012 |
| No. | Cluster | Included Docs | Description |
|---|---|---|---|
| 1 | Systems Engineering | Doc 9, Doc 37, Doc 97 | Focuses on algorithms and system surveys in CPS research |
| 2 | Vulnerability and Seismic Risks | Doc 34, Doc 69 | Deals with network analysis and seismic risk in infrastructure |
| 3 | Comprehensive Studies | Doc 187, Doc 39 | Estimation methods and comprehensive studies on infrastructure |
| 4 | Businesses, Community, and Inter-dependencies | Doc 57, Doc 219 | Impact of resilience in business and community settings |
| 5 | Sustainable Secure Systems | Doc 116, Doc 100 | Studies on sustainable systems and their resilience post-COVID |
| 6 | Critical Infrastructure | Doc 129, Doc 166, Doc 235, Doc 302, Doc 336, Doc 241, Doc 312, Doc 186 | Focuses on resilience in critical infrastructure systems |
| 7 | Resilience Network | Doc 138, Doc 140 | Network resilience and analysis of vulnerabilities |
| 8 | Advances and Shortages and Multi-level Planning | Doc 192, Doc 170 | Advances in resilience methodologies and addressing shortages |
| 9 | Regional Resilience | Doc 261, Doc 213 | Resilience studies focusing on regional infrastructures |
| 10 | Resilience Engineering and Risk Management | Doc 218, Doc 254 | Engineering solutions for critical infrastructure resilience |
3.2. Definitions and Terminology
3.2.1. Resilience Concept Evolution
Early Definitions (1970s–2000)
Mid-Period (2005–2014)
Recent Definitions (2015–2023)
3.2.2. Inferences on the Evolution
3.3. Resilience of Cyber–Physical Critical Infrastructures
- Adaptability and Flexibility: Definitions that encompass CP often emphasize the system’s ability to adapt to changes, absorb disturbances, and recover from disruptions. For instance, definitions by [50,55,60] highlight the system’s capacity for self-organization, learning, and adaptation, which are critical in cyber–physical systems where dynamic changes are frequent.
- Recovery and Restoration: Many definitions focusing on CP stress the importance of recovery and restoration of functionality post-disruption. Refs. [56,59] mention the need for the timely restoration of essential services, reflecting the critical nature of maintaining operational continuity in the face of cyber–physical threats.
3.3.1. Cyber Resilience and Prominent Cyber–Physical Threats to Critical Infrastructure
Actors of Cyberspace
- Nation-State Actors: Government-affiliated groups that engage in cyber activities for espionage, sabotage, or disruption to further national interests.
- Cybercriminals: Individuals or groups motivated by financial gain that engage in activities such as ransomware, phishing, and data theft.
- Hacktivists: Actors promoting political, social, or ideological causes through cyber attacks.
- Insiders: Disgruntled employees or contractors with access to sensitive information who may act out of malice or personal gain.
- Terrorist Groups: Groups using cyber attacks as part of their broader strategy to instill fear or further ideological goals.
- Script Kiddies: Less skilled individuals using pre-existing tools to carry out attacks, often for notoriety or thrill.
Cyberthreats
Attribution
Deterrence
3.4. The Role of AI and ML in Cyber–Physical Resilience
3.5. Conceptualizing Resilience: Frameworks, Indicators, and Assessment Methods
3.6. Quantitative Resilience Assessment Frameworks for Cyber–Physical Systems
3.7. Legal Frameworks In-Depth Synthesis
3.8. Current Consensus on Legal Frameworks
3.8.1. Case Studies and Practical Applications
- Air Navigation Systems
- Urban Resilience
- Energy Resilience
3.8.2. Emerging Trends and Future Directions
- Integration with Cybersecurity
- Technological Innovations
- Global Resilience Governance
3.9. Identified Gaps in Cyber–Physical Resilience Research
3.10. Future Research Directions in Cyber–Physical Resilience
- 1.
- AI-Driven Resilience ModelsFuture research should explore AI-powered frameworks capable of predicting, detecting, and mitigating cyber–physical threats in real time. AI-based autonomous response systems could dynamically adjust cybersecurity postures based on evolving threats, reducing the reliance on static resilience indicators.
- 2.
- Quantification of Cyber–Physical ResilienceA key research priority is the development of standardized resilience quantification metrics. Current approaches often rely on qualitative assessments, making it difficult to benchmark resilience levels across sectors. Research should focus on probabilistic models, Bayesian networks, and Monte Carlo simulations to create more data-driven resilience assessments.
- 3.
- Cross-Sector Resilience ModelingResearch should expand resilience frameworks beyond sector-specific models, focusing on multi-sector dependencies and how disruptions in one sector impact others. Cyber–physical resilience models should integrate supply chain vulnerabilities and systemic risk assessments.
- 4.
- Resilience Testing in Large-Scale Digital TwinsThe creation of realistic cyber–physical testing environments, such as digital twins, will be essential for advancing resilience research. These virtual environments should replicate large-scale infrastructure interdependencies, enabling the stress-testing of resilience measures against simulated cyber–physical attacks.
- 5.
- Human–Machine Collaboration in ResilienceResearch should explore the optimal balance between automated and human decision-making in resilience management. The growing use of AI-based cyber defenses raises concerns about over-reliance on automation, making it critical to study human oversight models for cyber–physical security.
3.11. Future Policy Directions for Cyber–Physical Resilience
- 1.
- Harmonization of Resilience StandardsA major policy challenge is the fragmentation of resilience regulations across different sectors and jurisdictions. Future policies should align resilience assessment frameworks globally, ensuring consistent cybersecurity and resilience standards across critical infrastructure sectors.
- 2.
- Public–Private Collaboration on Resilience FrameworksGovernments should strengthen collaborative resilience frameworks by incentivizing private-sector investment in cyber–physical security. This includes tax incentives for resilience-enhancing technologies, joint cybersecurity drills, and mandatory reporting of cyber–physical incidents.
- 3.
- Legislative Adaptation to Emerging Cyber–Physical RisksExisting legal frameworks, including NIS-2 and CER Directives, must evolve to address new risks such as AI-powered cyber threats, quantum computing vulnerabilities, and advanced supply chain attacks. Future policies should introduce mandatory resilience audits and dynamic regulatory adjustments based on emerging threats.
- 4.
- Cyber-Resilience Liability FrameworksFuture policies should establish liability frameworks for cyber–physical incidents, clarifying the responsibilities of critical infrastructure operators, software providers, and cloud service providers. Regulatory bodies should enforce compliance with resilience standards, imposing penalties for negligence in cybersecurity measures. A rigorous compliance assessment process is essential to reinforcing the resilience of critical infrastructure, ensuring that security measures align with evolving threats and regulatory requirements.
- 5.
- Development of Cyber-Resilience Insurance MarketsAs cyber–physical threats continue to evolve, cyber-resilience insurance will play a crucial role in mitigating financial risks for critical infrastructure operators. Policymakers should establish clear guidelines for cyber-insurance coverage, ensuring that resilience risk assessments are incorporated into insurance underwriting processes.
4. Conclusions and Potential Future Studies
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Alcaraz, C.; Zeadally, S. Critical infrastructure protection: Requirements and challenges for the 21st century. Int. J. Crit. Infrastruct. Prot. 2015, 8, 53–66. [Google Scholar] [CrossRef]
- Merabti, M.; Kennedy, M.; Hurst, W. Critical infrastructure protection: A 21 st century challenge. In Proceedings of the 2011 International Conference on Communications and Information Technology (ICCIT), Aqaba, Jordan, 29–31 March 2011; pp. 1–6. [Google Scholar]
- Ramadan, A.I.H.A.; Ardebili, A.A.; Longo, A.; Ficarella, A. Advancing Resilience in Green Energy Systems: Comprehensive Review of AI-based Data-driven Solutions for Security and Safety. In Proceedings of the 2023 IEEE International Conference on Big Data (BigData), Sorrento, Italy, 15–18 December 2023; pp. 4002–4010. [Google Scholar]
- Yusta, J.M.; Correa, G.J.; Lacal-Arántegui, R. Methodologies and applications for critical infrastructure protection: State-of-the-art. Energy Policy 2011, 39, 6100–6119. [Google Scholar] [CrossRef]
- Janke, R.; Tryby, M.E.; Clark, R.M. Protecting water supply critical infrastructure: An overview. In Securing Water and Wastewater Systems Global Experiences; Springer: Berlin/Heidelberg, Germany, 2013; pp. 29–85. [Google Scholar]
- Riegel, C. Risk Assessment and Critical Infrastructure Protection in Health Care Facilities: Reducing Social Vulnerability; German Federal Service of Interior: Berlin, Germany, 2008. [Google Scholar]
- Commission, E. Hybrid Threats: A Comprehensive Resilience Ecosystem. 2023. Available online: https://publications.jrc.ec.europa.eu/repository/handle/JRC129019 (accessed on 3 September 2024).
- Lazari, A. European Critical Infrastructure Protection; Springer: Cham, Switzerland, 2014. [Google Scholar]
- Li, C.; Sun, Y.; Chen, X. Analysis of the blackout in Europe on 4 November 2006. In Proceedings of the 2007 International Power Engineering Conference (IPEC 2007), Singapore, 3–6 December 2007; pp. 939–944. [Google Scholar]
- Satake, K. The 2011 Tohoku, Japan, earthquake and tsunami. Extreme Natural Hazards, Disaster Risks and Societal Implications; Cambridge University Press: Cambridge, UK, 2014; pp. 310–321. [Google Scholar]
- Longo, A.; Ardebili, A.A.; Zappatore, M.; Mulla, D.P. May SARS-CoV-2 be prevented by an indoor air monitoring smart data service? In Proceedings of the 2021 IEEE International Conferences on Internet of Things (iThings) and IEEE Green Computing & Communications (GreenCom) and IEEE Cyber, Physical & Social Computing (CPSCom) and IEEE Smart Data (SmartData) and IEEE Congress on Cybermatics (Cybermatics), Melbourne, Australia, 6–8 December 2021; pp. 365–371. [Google Scholar]
- Simoncini, M.; Lazari, A. Principles and Policies of Resilience in European Critical Infrastructures: Cases from the Sectors of Gas and Air Transport. Leg. Issues Econ. Integr. 2016, 43, 41–63. [Google Scholar] [CrossRef]
- Commission, E. Green Paper on a European Programme for Critical Infrastructure Protection. 2005. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:52005DC0576 (accessed on 3 September 2024).
- Lazari, A.; Simoncini, M. Critical Infrastructure Protection beyond Compliance. An Analysis of National Variations in the Implementation of Directive 114/08/EC. Glob. Jurist 2016, 16, 267–289. [Google Scholar] [CrossRef]
- Commission, E. On a New Approach to the European Programme for Critical Infrastructure Protection Making European Critical Infrastructures More Secure. 2013. Available online: https://home-affairs.ec.europa.eu/document/download/010f315a-96cd-4412-93dd-cc8afda499ac_en?filename=swd_2013_318_on_epcip_en.pdf (accessed on 3 September 2024).
- Grigalashvili, V. The Essence of Critical Infrastructure in the European Union, Nato and G7 Countries. Int. J. Innov. Technol. Econ. 2022, 1, 413193. [Google Scholar] [CrossRef]
- Taylor, J.S.; Morris, R.J. SCOPUS: A Database for Research Evaluation and Bibliometrics. J. Inf. Sci. 2011, 37, 723–734. [Google Scholar]
- Singh, M.A.; Patel, P.R. An Overview of the Scopus Database for Scientific Research. Libr. Manag. 2015, 36, 32–45. [Google Scholar]
- European Union. Council Directive 2008/114/EC on the Identification and Designation of European Critical Infrastructures and the Assessment of the Need to Improve Their Protection. 2008. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32008L0114 (accessed on 18 March 2025).
- European Union. Directive 2013/40/EU on Attacks Against Information Systems. 2013. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32013L0040 (accessed on 18 March 2025).
- European Union. Directive (EU) 2016/1148 Concerning Measures for a High Common Level of Security of Network and Information Systems Across the Union. 2016. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32016L1148 (accessed on 18 March 2025).
- European Union. Regulation (EU) 2019/881 of the European Parliament and of the Council of 17 April 2019 on ENISA (the European Union Agency for Cybersecurity) and on information and communications technology cybersecurity certification and repealing Regulation (EU) No 526/2013 (Cybersecurity Act). 2019. Available online: https://eur-lex.europa.eu/eli/reg/2019/881/oj/eng (accessed on 18 March 2025).
- European Union. Directive (EU) 2019/883 of the European Parliament and of the Council of 17 April 2019 on the Resilience of Critical Entities. Off. J. Eur. Union 2019. [Google Scholar]
- European Union. EU Cybersecurity Strategy for the Digital Decade. In Communication from the Commission to the European Parliament, the Council, the European Economic and Social Committee and the Committee of the Regions; European Union: Maastricht, The Netherlands, 2020. [Google Scholar]
- Liu, C.Z.; Sheng, Y.X.; Wei, Z.Q.; Yang, Y.Q. Research of text classification based on improved TF-IDF algorithm. In Proceedings of the 2018 IEEE International Conference of Intelligent Robotic and Control Engineering (IRCE), Lanzhou, China, 24–27 August 2018; pp. 218–222. [Google Scholar]
- Zhang, Y.; Ling, G.; Yong-cheng, W. An improved TF-IDF approach for text classification. J. Zhejiang-Univ.-Sci. A 2005, 6, 49–55. [Google Scholar] [CrossRef]
- Zio, E. Challenges in the vulnerability and risk analysis of critical infrastructures. Reliab. Eng. Syst. Saf. 2016, 152, 137–150. [Google Scholar] [CrossRef]
- Zhu, Q.; Basar, T. Game-theoretic methods for robustness, security, and resilience of cyber-physical control systems: Games-in-games principle for optimal cross-layer resilient control systems. IEEE Control. Syst. Mag. 2015, 35, 46–65. [Google Scholar]
- Pescaroli, G.; Alexander, D. Understanding compound, interconnected, interacting, and cascading risks: A holistic framework. Risk Anal. 2018, 38, 2245–2257. [Google Scholar] [CrossRef]
- Rieger, C.G.; Gertman, D.I.; McQueen, M.A. Resilient control systems: Next generation design research. In Proceedings of the 2009 2nd Conference on Human System Interactions, Catania, Italy, 21–23 May 2009; pp. 632–636. [Google Scholar]
- Kammouh, O.; Gardoni, P.; Cimellaro, G.P. Probabilistic framework to evaluate the resilience of engineering systems using Bayesian and dynamic Bayesian networks. Reliab. Eng. Syst. Saf. 2020, 198, 106813. [Google Scholar] [CrossRef]
- Bešinović, N. Resilience in railway transport systems: A literature review and research agenda. Transp. Rev. 2020, 40, 457–478. [Google Scholar] [CrossRef]
- Abedi, A.; Gaudard, L.; Romerio, F. Review of major approaches to analyze vulnerability in power systems. Reliab. Eng. Syst. Saf. 2019, 183, 153–172. [Google Scholar] [CrossRef]
- Rehak, D.; Senovsky, P.; Hromada, M.; Lovecek, T. Complex approach to assessing resilience of critical infrastructure elements. Int. J. Crit. Infrastruct. Prot. 2019, 25, 125–138. [Google Scholar] [CrossRef]
- Serre, D.; Heinzlef, C. Assessing and mapping urban resilience to floods with respect to cascading effects through critical infrastructure networks. Int. J. Disaster Risk Reduct. 2018, 30, 235–243. [Google Scholar] [CrossRef]
- Chang, L.; Wu, Z. Performance and reliability of electrical power grids under cascading failures. Int. J. Electr. Power Energy Syst. 2011, 33, 1410–1419. [Google Scholar] [CrossRef]
- Popik, T.S.; Winks, D. Building resilience and recoverability of electric grid communications. J. Crit. Infrastruct. Policy 2020, 1, 137–155. [Google Scholar] [CrossRef]
- Sanne, J.M.; Matschke Ekholm, H.; Rahmberg, M. Contextualizing resilience indicators–comparable across organizations yet specific to context. J. Risk Res. 2021, 24, 1652–1667. [Google Scholar] [CrossRef]
- Poudel, A.; Argyroudis, S.; Pitilakis, D.; Pitilakis, K. Systemic seismic vulnerability and risk assessment of urban infrastructure and utility systems. In Proceedings of the Lifelines 2022, Virtual, 31 January–11 February 2022; pp. 914–926. [Google Scholar]
- Owusu, A.; Mohamed, S.; Anissimov, Y. Input-output impact risk propagation in critical infrastructure interdependency. In Proceedings of the 13th International Conference on Computing in Civil and Building Engineering, Nottingham, UK, 30 June–2 July 2010. [Google Scholar]
- Rehak, D.; Hromada, M.; Ristvej, J. Indication of critical infrastructure resilience failure. In Safety and Reliability—Theory and Applications—Proceedings of the 27th European Safety and Reliability Conference, ESREL 2017, Portorož, Slovenia, 18–22 June 2017; CRC Press: London, UK, 2017; pp. 963–970. [Google Scholar]
- Sterling, R.; Nelson, P. City resiliency and underground space use. Adv. Undergr. Space Dev. 2013, 7, 43–55. [Google Scholar]
- Balducelli, C.; Di Pietro, A.; Lavalle, L.; Vicoli, G. A middleware improved technology (MIT) to mitigate interdependencies between critical infrastructures. In Architecting Dependable Systems V; Springer: Berlin/Heidelberg, Germany, 2008; pp. 28–51. [Google Scholar]
- Montgomery, M.; Broyd, T.; Cornell, S.; Pearce, O.; Pocock, D.; Young, K. An innovative approach for improving infrastructure resilience. Proc. Inst. Civ. Eng. Eng. 2012, 165, 27–32. [Google Scholar] [CrossRef]
- Holling, C.S. Resilience and stability of ecological systems. Annu. Rev. Ecol. Syst. 1973, 4, 1–23. Available online: https://www.jstor.org/stable/2096802 (accessed on 10 September 2024). [CrossRef]
- Adger, W.N. Social and ecological resilience: Are they related? Prog. Hum. Geogr. 2000, 24, 347–364. [Google Scholar] [CrossRef]
- Bruneau, M.; Chang, S.E.; Eguchi, R.T.; Lee, G.C.; O’Rourke, T.D.; Reinhorn, A.M.; Shinozuka, M.; Tierney, K.; Wallace, W.A.; Von Winterfeldt, D. A framework to quantitatively assess and enhance the seismic resilience of communities. Earthq. Spectra 2003, 19, 733–752. [Google Scholar] [CrossRef]
- Allenby, B.; Fink, J. Toward inherently secure and resilient societies. Science 2005, 309, 1034–1036. [Google Scholar] [CrossRef]
- Rose, A.; Liao, S.Y. Modeling regional economic resilience to disasters: A computable general equilibrium analysis of water service disruptions. J. Reg. Sci. 2005, 45, 75–112. [Google Scholar] [CrossRef]
- Pawlenty, T.; Archuleta, E.; Nicholson, J. Framework for Dealing with Disasters and Related Interdependencies. Final Report and Recommendations, The Honorable Tim Pawlenty, Governor, The State of Minnesota; Mr. Edmund Archuleta, President and CEO, El Paso Water Utilities; Mr. James Nicholson, President and CEO, PVS Chemicals, Inc. 2009. Available online: https://www.dhs.gov/xlibrary/assets/niac/niac_framework_dealing_with_disasters.pdf (accessed on 10 September 2024).
- ASME Innovative Technologies Institute, LLC (ASME-ITI). RAMCAPSM and RAMCAP PlusSM Framework. Final Report, 2009. Published by ASME Innovative Technologies Institute, LLC, 1828 L Street NW, Suite 906, Washington, DC 20036. A Wholly-Owned Subsidiary of the American Society of Mechanical Engineers (ASME). ISBN 978-0-7918-0287-8. ASME Order No.: 802878. Available online: https://www.asme.org (accessed on 2 April 2025).
- Terminology: Basic Terms of Disaster Risk Reduction. United Nations Office for Disaster Risk Reduction, UNISDR Geneva. 2009. Available online: https://www.undrr.org/publication/2009-unisdr-terminology-disaster-risk-reduction (accessed on 2 April 2025).
- Martin, R. Regional economic resilience, hysteresis and recessionary shocks. J. Econ. Geogr. 2011, 12, 1–32. [Google Scholar] [CrossRef]
- Gay, L.F.; Sinha, S.K. Resilience of civil infrastructure systems: Literature review for improved asset management. Int. J. Crit. Infrastructures 2013, 9, 330–350. [Google Scholar] [CrossRef]
- The Resilience Alliance is a Research Organization that Focuses on Resilience in Social–Ecological Systems as a Basis for Sustainability. 2019. Available online: https://www.resalliance.org/resilience (accessed on 2 April 2025).
- Bocchini, P.; Frangopol, D.M.; Ummenhofer, T.; Zinke, T. Resilience and sustainability of civil infrastructure: Toward a unified approach. J. Infrastruct. Syst. 2014, 20, 04014004. [Google Scholar] [CrossRef]
- Ouyang, M. Review on modeling and simulation of interdependent critical infrastructure systems. Reliab. Eng. Syst. Saf. 2014, 121, 43–60. [Google Scholar] [CrossRef]
- Mostafavi, A. A System-of-Systems Approach for Integrated Resilience Assessment in Highway Transportation Infrastructure Investment. Infrastructures 2017, 2, 22. [Google Scholar] [CrossRef]
- Pursiainen, C. Critical infrastructure resilience: A Nordic model in the making? Int. J. Disaster Risk Reduct. 2018, 27, 632–641. [Google Scholar] [CrossRef]
- Curt, C.; Tacnet, J.M. Resilience of critical infrastructures: Review and analysis of current approaches. Risk Anal. 2018, 38, 2441–2458. [Google Scholar] [CrossRef] [PubMed]
- Petersen, L.; Lundin, E.; Fallou, L.; Sjöström, J.; Lange, D.; Teixeira, R.; Bonavita, A. Resilience for whom? The general public’s tolerance levels as CI resilience criteria. Int. J. Crit. Infrastruct. Prot. 2020, 28, 100340. [Google Scholar] [CrossRef]
- Papic, M.; Ekisheva, S.; Cotilla-Sanchez, E. A risk-based approach to assess the operational resilience of transmission grids. Appl. Sci. 2020, 10, 4761. [Google Scholar] [CrossRef]
- Brugnetti, E.; Coletta, G.; De Caro, F.; Vaccaro, A.; Villacci, D. Enabling methodologies for predictive power system resilience analysis in the presence of extreme wind gusts. Energies 2020, 13, 3501. [Google Scholar] [CrossRef]
- Lim, S.; Kim, T.; Song, J. System-reliability-based disaster resilience analysis: Framework and applications to structural systems. Struct. Saf. 2022, 96, 102202. [Google Scholar] [CrossRef]
- Mentges, A.; Halekotte, L.; Schneider, M.; Demmer, T.; Lichte, D. A resilience glossary shaped by context: Reviewing resilience-related terms for critical infrastructures. Int. J. Disaster Risk Reduct. 2023, 96, 103893. [Google Scholar] [CrossRef]
- Ameli, S.R.; Hosseini, H.; Noori, F. Militarization of cyberspace, changing aspects of war in the 21st century: The case of Stuxnet against Iran. Iran. Rev. Foreign Aff. 2019, 10, 99–136. [Google Scholar]
- Booz Allen Hamilton. When the Lights Went Out: A Comprehensive Review of the 2015 Attacks on Ukrainian Critical Infrastructure. 2016. Available online: https://www.boozallen.com/content/dam/boozallen/documents/2016/09/ukraine-report-when-the-lights-went-out.pdf (accessed on 2 April 2025).
- Zetter, K. Inside the Cunning, Unprecedented Hack of Ukraine’s Power Grid. WIRED. 2016. Available online: https://www.wired.com/2016/03/inside-cunning-unprecedented-hack-ukraines-power-grid/ (accessed on 2 April 2025).
- Centre for Cyber Security (CFCS). The Cyber Threat Against the Danish Energy Sector, 1st ed.; Centre for Cyber Security: London, UK, 2023. [Google Scholar]
- National Academies; Policy and Global Affairs; Committee on Science, Engineering, and Public Policy; Committee on Increasing National Resilience to Hazards and Disasters. Disaster Resilience: A National Imperative; National Academies Press: Washington, DC, USA, 2012. [Google Scholar]
- Wied, M.; Oehmen, J.; Welo, T. Conceptualizing resilience in engineering systems: An analysis of the literature. Syst. Eng. 2020, 23, 3–13. [Google Scholar] [CrossRef]
- Panteli, M.; Mancarella, P. The grid: Stronger, bigger, smarter?: Presenting a conceptual framework of power system resilience. IEEE Power Energy Mag. 2015, 13, 58–66. [Google Scholar] [CrossRef]
- Aghazadeh Ardebili, A.; Martella, C.; Martella, A.; Lazari, A.; Longo, A.; Ficarella, A. Smart Critical Infrastructures Security management and governance: Implementation of Cyber Resilience KPIs for Decentralized Energy Asset. In Proceedings of the CEUR Workshop Proceedings, Boise, ID, USA, 5 October 2024; Volume 3731. [Google Scholar]
- Syrmakesis, A.D.; Alcaraz, C.; Hatziargyriou, N.D. Classifying resilience approaches for protecting smart grids against cyber threats. Int. J. Inf. Secur. 2022, 21, 1189–1210. [Google Scholar] [CrossRef]
- Mishra, D.K.; Eskandari, M.; Abbasi, M.H.; Sanjeevkumar, P.; Zhang, J.; Li, L. A detailed review of power system resilience enhancement pillars. Electr. Power Syst. Res. 2024, 230, 110223. [Google Scholar] [CrossRef]
- Anuat, E.; Van Bossuyt, D.L.; Pollman, A. Energy resilience impact of supply chain network disruption to military microgrids. Infrastructures 2021, 7, 4. [Google Scholar] [CrossRef]
- Afzal, S.; Mokhlis, H.; Illias, H.A.; Mansor, N.N.; Shareef, H. State-of-the-art review on power system resilience and assessment techniques. IET Gener. Transm. Distrib. 2020, 14, 6107–6121. [Google Scholar] [CrossRef]
- Bhusal, N.; Abdelmalak, M.; Kamruzzaman, M.; Benidris, M. Power system resilience: Current practices, challenges, and future directions. IEEE Access 2020, 8, 18064–18086. [Google Scholar] [CrossRef]
- Younesi, A.; Shayeghi, H.; Wang, Z.; Siano, P.; Mehrizi-Sani, A.; Safari, A. Trends in modern power systems resilience: State-of-the-art review. Renew. Sustain. Energy Rev. 2022, 162, 112397. [Google Scholar] [CrossRef]
- Umunnakwe, A.; Huang, H.; Oikonomou, K.; Davis, K. Quantitative analysis of power systems resilience: Standardization, categorizations, and challenges. Renew. Sustain. Energy Rev. 2021, 149, 111252. [Google Scholar] [CrossRef]
- MT, S.; Aminanto, A.E.; Aminanto, M.E. Empowering Digital Resilience: Machine Learning-Based Policing Models for Cyber-Attack Detection in Wi-Fi Networks. Electronics 2024, 13, 2583. [Google Scholar] [CrossRef]
- Bace, B.; Dubois, E.; Tatar, U. Resilience against Catastrophic Cyber Incidents: A Multistakeholder Analysis of Cyber Insurance. Electronics 2024, 13, 2768. [Google Scholar] [CrossRef]
- Cazares, M.; Fuertes, W.; Andrade, R.; Ortiz-Garcés, I.; Rubio, M.S. Protective factors for developing cognitive skills against cyberattacks. Electronics 2023, 12, 4007. [Google Scholar] [CrossRef]
- Blount, P. Reprogramming the World. Cyberspace and the Geography of Global Order; E-International Relations Publishing: Bristol, UK, 2019. [Google Scholar]
- Riordan, S. The Geopolitics of Cyberspace: A Diplomatic Perspective. In Brill Research Perspectives in Diplomacy and Foreign Policy; Brill: Leiden, The Netherlands, 2018. [Google Scholar]
- Ardebili, A.A.; Padoano, E.; Longo, A.; Ficarella, A. The Risky-Opportunity Analysis Method (ROAM) to Support Risk-Based Decisions in a Case-Study of Critical Infrastructure Digitization. Risks 2022, 10, 48. [Google Scholar] [CrossRef]
- Wilson, C. Cyber threats to critical information infrastructure. In Cyberterrorism: Understanding, Assessment, and Response; Springer: Berlin/Heidelberg, Germany, 2014; pp. 123–136. [Google Scholar]
- Choraś, M.; Kozik, R.; Flizikowski, A.; Hołubowicz, W.; Renk, R. Cyber threats impacting critical infrastructures. In Managing the Complexity of Critical Infrastructures: A Modelling and Simulation Approach; Springer: Berlin/Heidelberg, Germany, 2016; pp. 139–161. [Google Scholar]
- Rudner, M. Cyber-threats to critical national infrastructure: An intelligence challenge. Int. J. Intell. Counterintelligence 2013, 26, 453–481. [Google Scholar] [CrossRef]
- Pursiainen, C. The challenges for European critical infrastructure protection. Eur. Integr. 2009, 31, 721–739. [Google Scholar] [CrossRef]
- Bernardeschi, C.; Domenici, A.; Palmieri, M. Modeling and simulation of attacks on systems. In Proceedings of the ICISSP 2019-5th International Conference on Information Systems Security and Privacy SciTePress, Prague, Czech Republic, 23–25 February 2019; pp. 700–708. [Google Scholar]
- Bernardeschi, C.; Dini, G.; Palmieri, M.; Racciatti, F. A framework for formal analysis and simulative evaluation of security attacks in wireless sensor networks. J. Comput. Virol. Hacking Tech. 2021, 17, 249–263. [Google Scholar] [CrossRef]
- Moret, E.; Pawlak, P. The EU Cyber Diplomacy Toolbox: Towards a Cyber Sanctions Regime? JSTOR: New York, NY, USA, 2017. [Google Scholar]
- Bendiek, A. The European Union’s Foreign Policy Toolbox in International Cyber Diplomacy. Cyber, Intell. Secur. 2018, 2, 57–71. [Google Scholar]
- for Cyber Security, C.C. An Introduction to the Cyber Threat Environment. 2020. Available online: https://cyber.gc.ca/en/guidance/introduction-cyber-threat-environment (accessed on 5 June 2021).
- Latici, T. Cyber: How Big Is the Threat? 2019. Available online: https://www.europarl.europa.eu/thinktank/en/document.html?reference=EPRS_ATA(2019)637980 (accessed on 20 May 2021).
- Significant Cyber Incidents. 2025. Available online: https://www.csis.org/programs/strategic-technologies-program/significant-cyber-incidents (accessed on 23 April 2025).
- ENISA. Artificial Intelligence Cybersecurity Challenges. 2020. Available online: https://www.enisa.europa.eu/publications/artificial-intelligence-cybersecurity-challenges (accessed on 11 June 2021).
- Meyer, D. Vladimir Putin Says Whoever Leads in Artificial Intelligence Will Rule the World. 2017. Available online: https://fortune.com/2017/09/04/ai-artificial-intelligence-putin-rule-world/ (accessed on 23 May 2021).
- Tsagourias, N.; Farrell, M. Cyber Attribution: Technical and Legal Approaches and Challenges. Eur. J. Int. Law 2020, 20, 1–27. [Google Scholar] [CrossRef]
- Armstrong, H. Denial of Service and Protection of Critical Infrastructure. J. Inf. Warf. 2001, 1, 23–34. [Google Scholar]
- Su, Y.; Xiong, D.; Qian, K.; Wang, Y. A Comprehensive Survey of Distributed Denial of Service Detection and Mitigation Technologies in Software-Defined Network. Electronics 2024, 13, 807. [Google Scholar] [CrossRef]
- Sachdeva, M.; Singh, G.; Kumar, K.; Singh, K. DDoS Incidents and their Impact: A Review. Int. Arab J. Inf. Technol. 2010, 7, 14–20. [Google Scholar]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Hurst, W.; Shone, N.; Monnet, Q. Predicting the effects of DDoS attacks on a network of critical infrastructures. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; pp. 1697–1702. [Google Scholar]
- Booth, T.; Andersson, K. Critical infrastructure network DDoS defense, via cognitive learning. In Proceedings of the 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017; pp. 1–6. [Google Scholar]
- Poisel, R.; Rybnicek, M.; Tjoa, S. Game-based simulation of Distributed Denial of Service (DDoS) attack and defense mechanisms of Critical Infrastructures. In Proceedings of the 2013 IEEE 27th International Conference on Advanced Information Networking and Applications (AINA), Barcelona, Spain, 25–28 March 2013; pp. 114–120. [Google Scholar]
- Rao, Y.S.; Keshri, A.K.; Mishra, B.K.; Panda, T.C. Distributed denial of service attack on targeted resources in a computer network for critical infrastructure: A differential e-epidemic model. Phys. A Stat. Mech. Its Appl. 2020, 540, 123240. [Google Scholar] [CrossRef]
- Miao, Y.; Shao, Y.; Zhang, J. IRS Backscatter-Based Secrecy Enhancement against Active Eavesdropping. Electronics 2024, 13, 265. [Google Scholar] [CrossRef]
- Mallik, A. Man-in-the-middle-attack: Understanding in simple words. Cyberspace J. Pendidik. Teknol. Inf. 2019, 2, 109–134. [Google Scholar] [CrossRef]
- Pochmara, J.; Świetlicka, A. Cybersecurity of Industrial Systems—A 2023 Report. Electronics 2024, 13, 1191. [Google Scholar] [CrossRef]
- Bermejo Higuera, J.; Morales Moreno, J.; Bermejo Higuera, J.R.; Sicilia Montalvo, J.A.; Barreiro Martillo, G.J.; Sureda Riera, T.M. Benchmarking Android Malware Analysis Tools. Electronics 2024, 13, 2103. [Google Scholar] [CrossRef]
- Aslan, Ö.; Aktuğ, S.S.; Ozkan-Okay, M.; Yilmaz, A.A.; Akin, E. A comprehensive review of cyber security vulnerabilities, threats, attacks, and solutions. Electronics 2023, 12, 1333. [Google Scholar] [CrossRef]
- Li, D.; Zhang, Q.; Zhao, D.; Li, L.; He, J.; Yuan, Y.; Zhao, Y. Hardware Trojan Detection Using Effective Property-Checking Method. Electronics 2022, 11, 2649. [Google Scholar] [CrossRef]
- Sun, H.; Zhu, W.; Sun, Z.; Cao, M.; Liu, W. FMDL: Federated Mutual Distillation Learning for Defending Backdoor Attacks. Electronics 2023, 12, 4838. [Google Scholar] [CrossRef]
- He, J.; Hou, G.; Jia, X.; Chen, Y.; Liao, W.; Zhou, Y.; Zhou, R. Data Stealing Attacks against Large Language Models via Backdooring. Electronics 2024, 13, 2858. [Google Scholar] [CrossRef]
- Nguyen, T.N. A review of cyber crime. J. Soc. Rev. Dev. 2023, 2, 01–03. [Google Scholar]
- Payton, A.M. A review of spyware campaigns and strategies to combat them. In Proceedings of the 3rd Annual Conference on Information Security Curriculum Development, Kennesaw Georgia, 22–23 September 2006; pp. 136–141. [Google Scholar]
- Lee, J.; Yun, J.; Lee, K. A Study on Countermeasures against Neutralizing Technology: Encoding Algorithm-Based Ransomware Detection Methods Using Machine Learning. Electronics 2024, 13, 1030. [Google Scholar] [CrossRef]
- Drabent, K.; Janowski, R.; Mongay Batalla, J. How to Circumvent and Beat the Ransomware in Android Operating System—A Case Study of Locker. CB! tr. Electronics 2024, 13, 2212. [Google Scholar] [CrossRef]
- Krasznay, C. Case Study: The NotPetya Campaign. In Információ és Kiberbiztonság; Török, B., Ed.; Ludovika Egyetemi Kiadó: Budapest, Hungary, 2020; pp. 485–501. [Google Scholar]
- Baig, Z.; Mekala, S.H.; Zeadally, S. Ransomware attacks of the COVID-19 pandemic: Novel strains, victims, and threat actors. IT Prof. 2023, 25, 37–44. [Google Scholar] [CrossRef]
- Raiyn, J. A survey of cyber attack detection strategies. Int. J. Secur. Its Appl. 2014, 8, 247–256. [Google Scholar]
- Goranin, N.; Hora, S.K.; Čenys, H.A. A Bibliometric Review of Intrusion Detection Research in IoT: Evolution, Collaboration, and Emerging Trends. Electronics 2024, 13, 3210. [Google Scholar] [CrossRef]
- Liu, Y.; Guo, Y. Towards Real-Time Warning and Defense Strategy AI Planning for Cyber Security Systems Aided by Security Ontology. Electronics 2022, 11, 4128. [Google Scholar] [CrossRef]
- Schaffer, A. The Cybersecurity 202: Legal Scholars are Working on New Rules for International Hacking Conflicts. 2021. Available online: https://www.washingtonpost.com/politics/2021/06/21/cybersecurity-202-legal-scholars-are-working-new-rules-international-hacking-conflicts/ (accessed on 18 June 2021).
- Assumpcao, C. The Problem of Cyber Attribution Between States. 2020. Available online: https://www.e-ir.info/2020/05/06/the-problem-of-cyber-attribution-between-states/ (accessed on 16 June 2021).
- Dévai, D. The International Cyberspace Policy of the European Union. In Információ és kiberbiztonság; Török, B., Ed.; Ludovika Egyetemi Kiadó: Budapest, Hungary, 2020; pp. 469–485. [Google Scholar]
- Gafni, R.; Levy, Y. The role of artificial intelligence (AI) in improving technical and managerial cybersecurity tasks’ efficiency. Inf. Comput. Secur. 2024, 32, 1–15. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kumar, G. Cybersecurity in Electric and Flying Vehicles: Threats, Challenges, AI Solutions & Future Directions. ACM Comput. Surv. 2024, 57, 1–34. [Google Scholar] [CrossRef]
- Nasr, A.N.; Leiger, R.; Zaitseva-Pärnaste, I.; Kujala, P. Exploring Historical Maritime Cyber-Attacks and Introducing Maritime Security Operations Center as a Solution to Mitigate Them; IOS Press: Amsterdam, The Netherlands, 2024; Volume 9, pp. 235–245. [Google Scholar] [CrossRef]
- Hiziroglu, O.A. Implementation of Artificial Intelligence for the Healthcare Supply Chain: Prospects and Challenges; CRC Press: Boca Raton, FL, USA, 2024; pp. 208–226. [Google Scholar] [CrossRef]
- Rezvani, S.M.H.S.; Silva, M.J.F.; de Almeida, N.M. Urban Resilience Index for Critical Infrastructure: A Scenario-Based Approach to Disaster Risk Reduction in Road Networks. Sustainability 2024, 16, 4143. [Google Scholar] [CrossRef]
- Khairnar, S.; Thepade, S.D.; Kolekar, S.; Gite, S.; Pradhan, B.; Alamri, A.; Patil, B.; Dahake, S.; Gaikwad, R.; Chaudhari, A. Enhancing semantic segmentation for autonomous vehicle scene understanding in indian context using modified CANet model. MethodsX 2025, 14, 103131. [Google Scholar] [CrossRef] [PubMed]
- Eleimat, M.; Alharasees, O.; Oszi, A. Advancements in Airport Security Technologies: A Patent Analysis. In Proceedings of the 2024 Mediterranean Smart Cities Conference (MSCC), Tetouan, Morocco, 2–4 May 2024. [Google Scholar] [CrossRef]
- Worland, J. How AI Is Making Buildings More Energy-Efficient. Time, 11 December 2024. [Google Scholar]
- Liu, M.; Wang, W.; Li, J.; Chen, T.; Zhang, Y.; Wu, L. Enhancing Cyber-Resiliency of DER-Based Smart Grid: A Survey. IEEE Trans. Smart Grid 2024, 15, 4998–5030. [Google Scholar] [CrossRef]
- Zhang, Z.; Xu, C.; Li, H.; Wang, P.; Ye, F. Vulnerability of Machine Learning Approaches Applied in IoT-Based Smart Grid: A Review. IEEE Internet Things J. 2024, 11, 18951–18975. [Google Scholar] [CrossRef]
- Bender, E.M.; Gebru, T.; McMillan-Major, A.; Shmitchell, S. On the Dangers of Stochastic Parrots: Can Language Models Be Too Big? In Proceedings of the 2021 ACM Conference on Fairness, Accountability, and Transparency, Toronto, ON, Canada, 3–10 March 2021; pp. 610–623. [Google Scholar] [CrossRef]
- Al-Humaiqani, M.M.; Al-Ghamdi, S.G. Robustness, redundancy, inclusivity, and integration of built environment systems: Resilience quantification from stakeholders’ perspectives. Front. Built Environ. 2024, 10, 1343334. [Google Scholar] [CrossRef]
- Liu, W.; Shan, M.; Zhang, S.; Zhao, X.; Zhai, Z. Resilience in infrastructure systems: A comprehensive review. Buildings 2022, 12, 759. [Google Scholar] [CrossRef]
- Pursiainen, C.; Gattinesi, P. Towards testing critical infrastructure resilience. In EUR—Scientific and Technical Research reports, European Commission, Joint Research Center; European Commission: Brussels, Belgium, 2014. [Google Scholar]
- Aghazadeh Ardebili, A.; Padoano, E. A literature review of the concepts of resilience and sustainability in group decision-making. Sustainability 2020, 12, 2602. [Google Scholar] [CrossRef]
- Guo, D.; Shan, M.; Owusu, E.K. Resilience assessment frameworks of critical infrastructures: State-of-the-art review. Buildings 2021, 11, 464. [Google Scholar] [CrossRef]
- Trivedi, K.S.; Goseva-Popstojanova, V. Stochastic Models for Reliability, Performance, and Availability of Systems. Ann. Oper. Res. 2002, 128, 85–108. [Google Scholar]
- Zio, E.; Aven, L. Industrial safety and reliability: Probabilistic models and maintenance methods. Reliab. Eng. Syst. Saf. 2013, 119, 95–107. [Google Scholar]
- Lonergan, K.; Sansavini, G. Impact of Distributed Decision-Making on Energy and Social Systems’ Resilience: A Case Study of Solar Photovoltaic in Switzerland. In Proceedings of the 31st European Safety and Reliability Conference (ESREL 2021), Angers, France, 19–23 September 2021; p. 611. [Google Scholar] [CrossRef]
- Botezatu, U.E.; Bucovetchi, O.; Bucovetchi, O.; Stanciu, R.D. Strengthening Urban Resilience: Understanding the Interdependencies of Outer Space and Strategic Planning for Sustainable Smart Environments. Smart Cities 2023, 6, 2499–2518. [Google Scholar] [CrossRef]
- Schweikert, A.E.; Deinert, M.R. Vulnerability and resilience of power systems infrastructure to natural hazards and climate change. WIREs Clim. Chang. 2021, 12, e724. [Google Scholar] [CrossRef]
- Di Maio, F. Centralized security governance for air navigation services: Innovative strategies to confront emerging threats against Civil Aviation. In Proceedings of the 2014 International Carnahan Conference on Security Technology (ICCST), Rome, Italy, 13–16 October 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Ettouney, M.M. Objective Resilience; American Society of Civil Engineers: Reston, VA, USA, 2022. [Google Scholar] [CrossRef]
- Ani, U.D.; Watson, J.D.M.; Nurse, J.R.C.; Cook, A.; Maple, C. A review of critical infrastructure protection approaches: Improving security through responsiveness to the dynamic modelling landscape. In Proceedings of the Living in the Internet of Things (IoT 2019), London, UK, 1–2 May 2019; pp. 1–15. [Google Scholar] [CrossRef]
- Staddon, C.; Ward, S.; De Vito, L.; Zuniga-Teran, A.; Gerlak, A.; Schoeman, Y.; Hart, A.; Booth, G. Contributions of green infrastructure to enhancing urban resilience. Environ. Syst. Decis. 2018, 38, 330–338. [Google Scholar] [CrossRef]
- McBurnett, L.R.; Hinrichs, M.M.; Seager, T.P.; Clark, S.S. Simulation Gaming Can Strengthen Experiential Education in Complex Infrastructure Systems. Simul. Gaming 2018, 49, 620–641. [Google Scholar] [CrossRef]
- Malatji, M.; Marnewick, A.L.; von Solms, S. Cybersecurity Policy and the Legislative Context of the Water and Wastewater Sector in South Africa. Sustainability 2021, 13, 291. [Google Scholar] [CrossRef]
- Amodeo, D.C.; Francis, R.A. The role of protocol layers and macro-cognitive functions in engineered system resilience. Reliab. Eng. Syst. Saf. 2019, 190, 106508. [Google Scholar] [CrossRef]


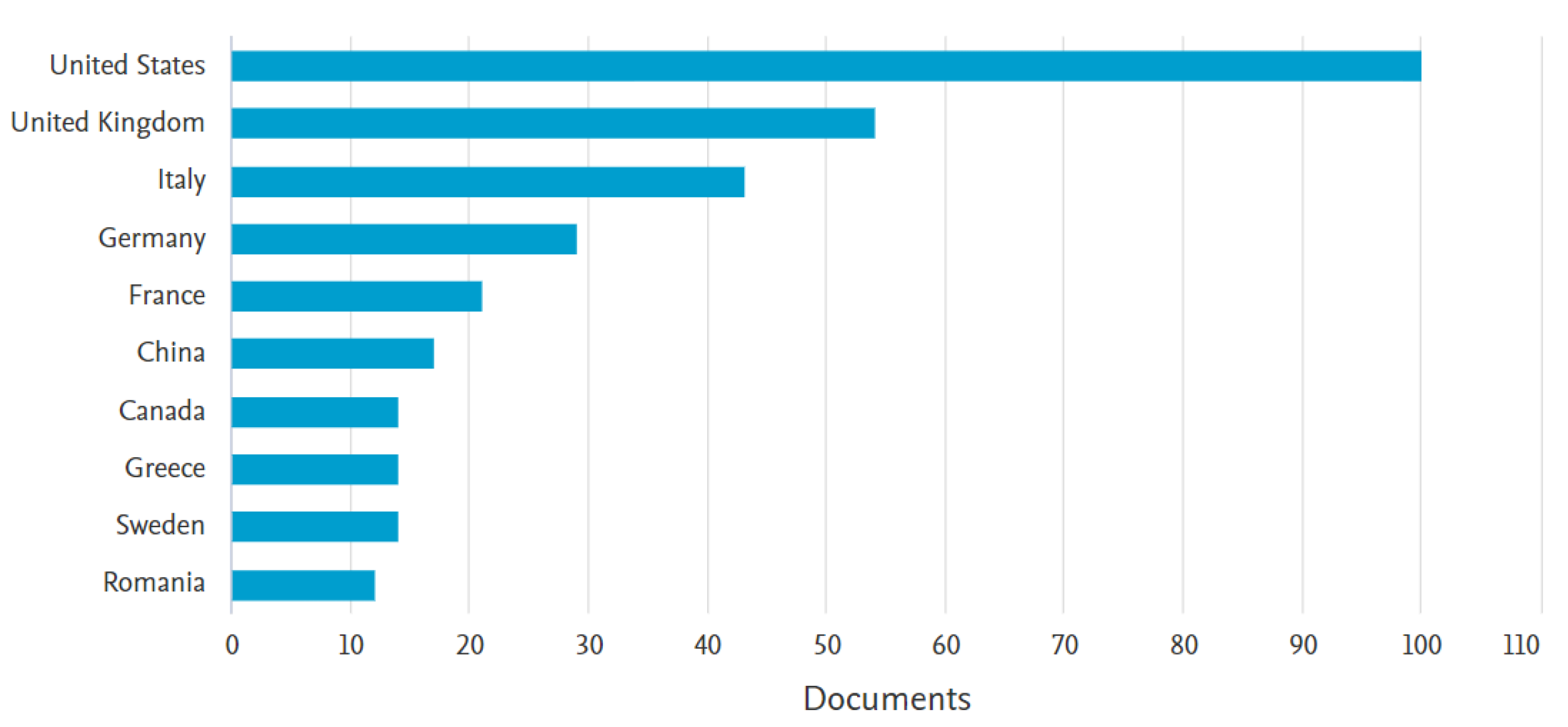

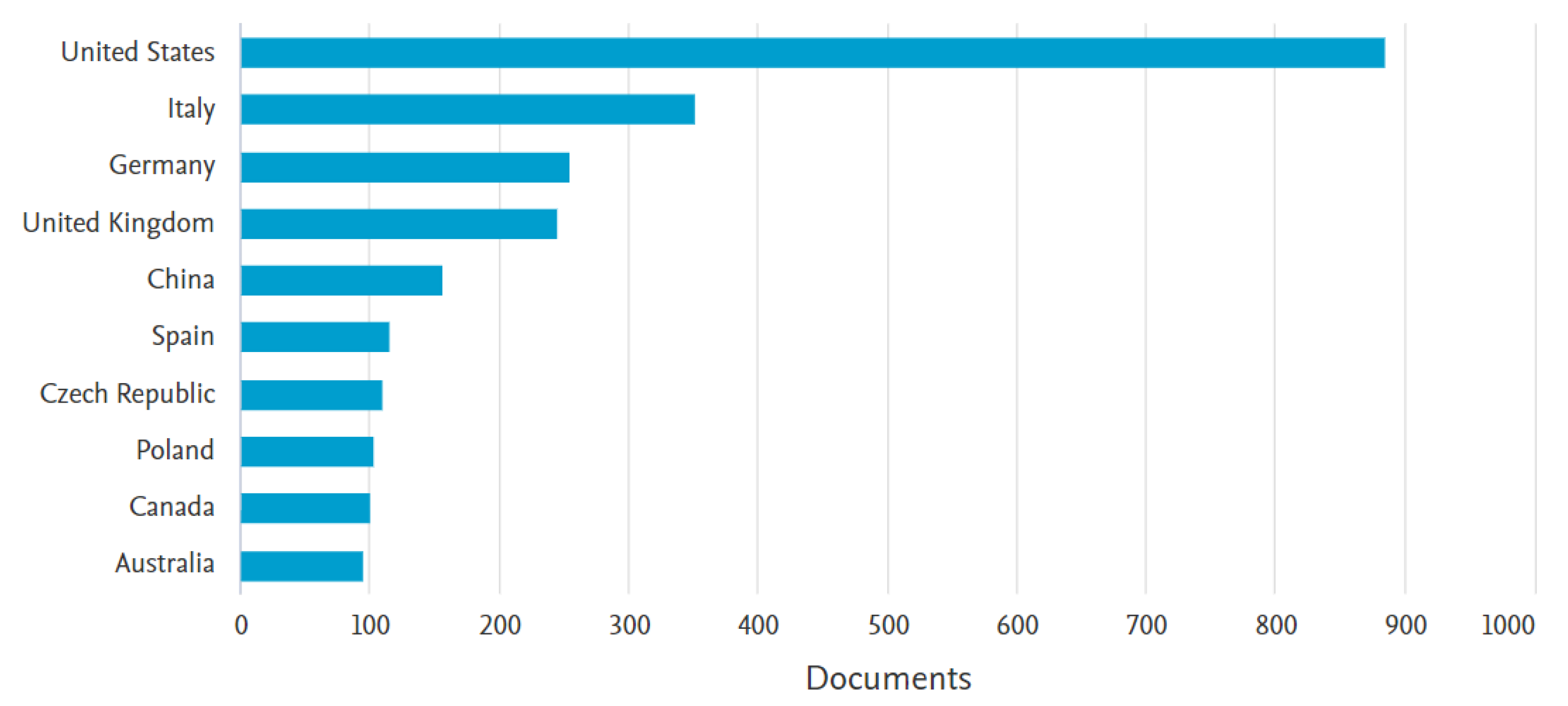
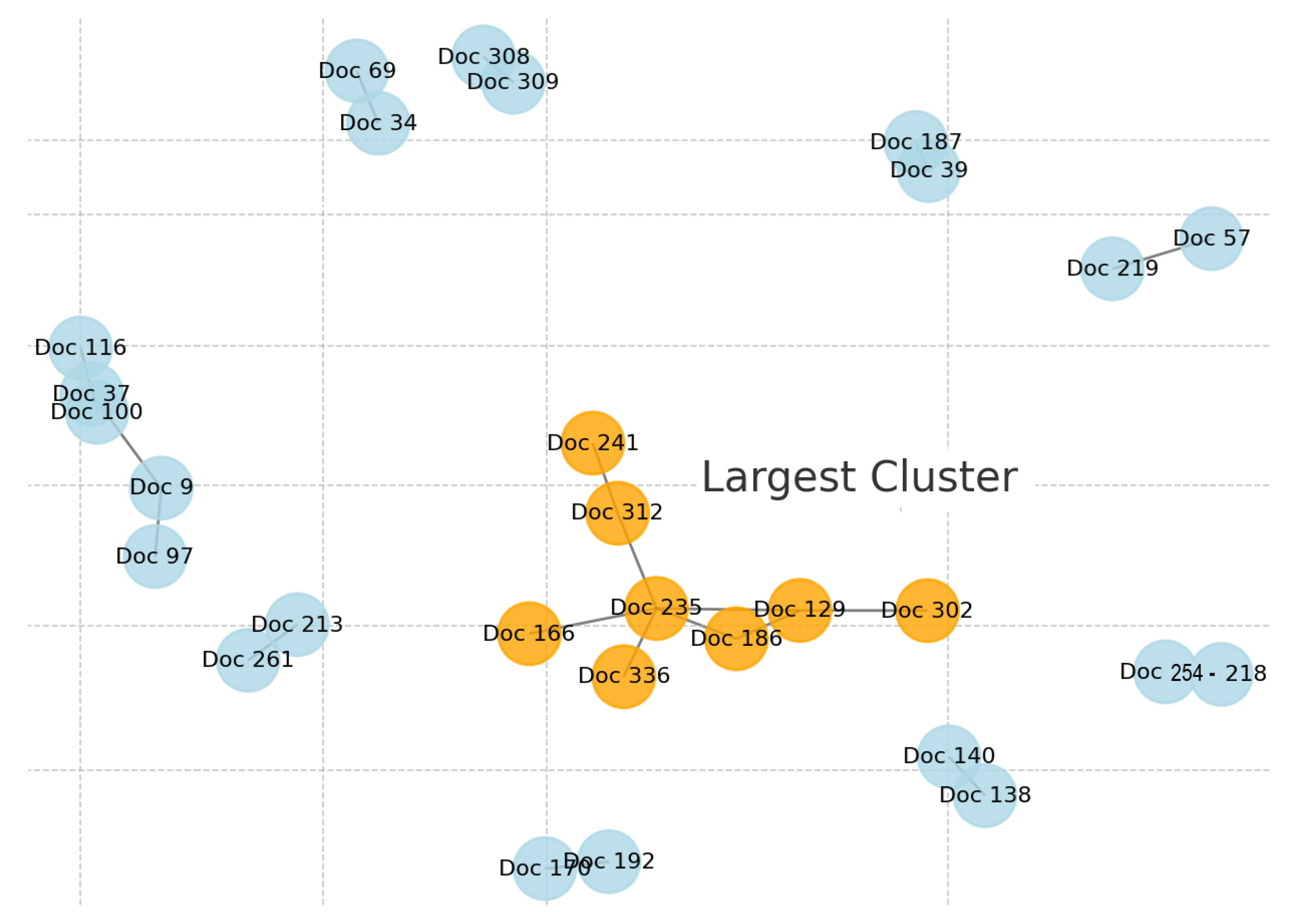
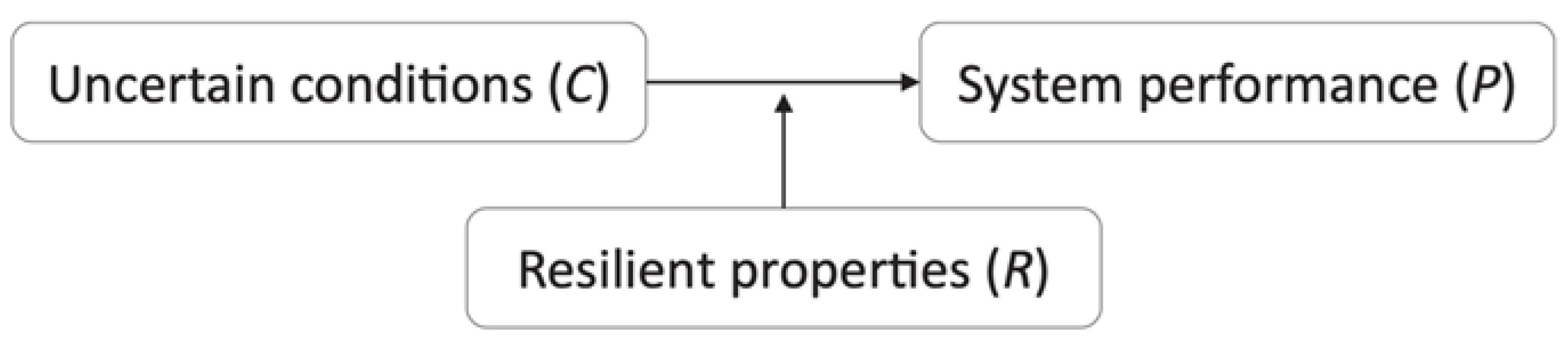

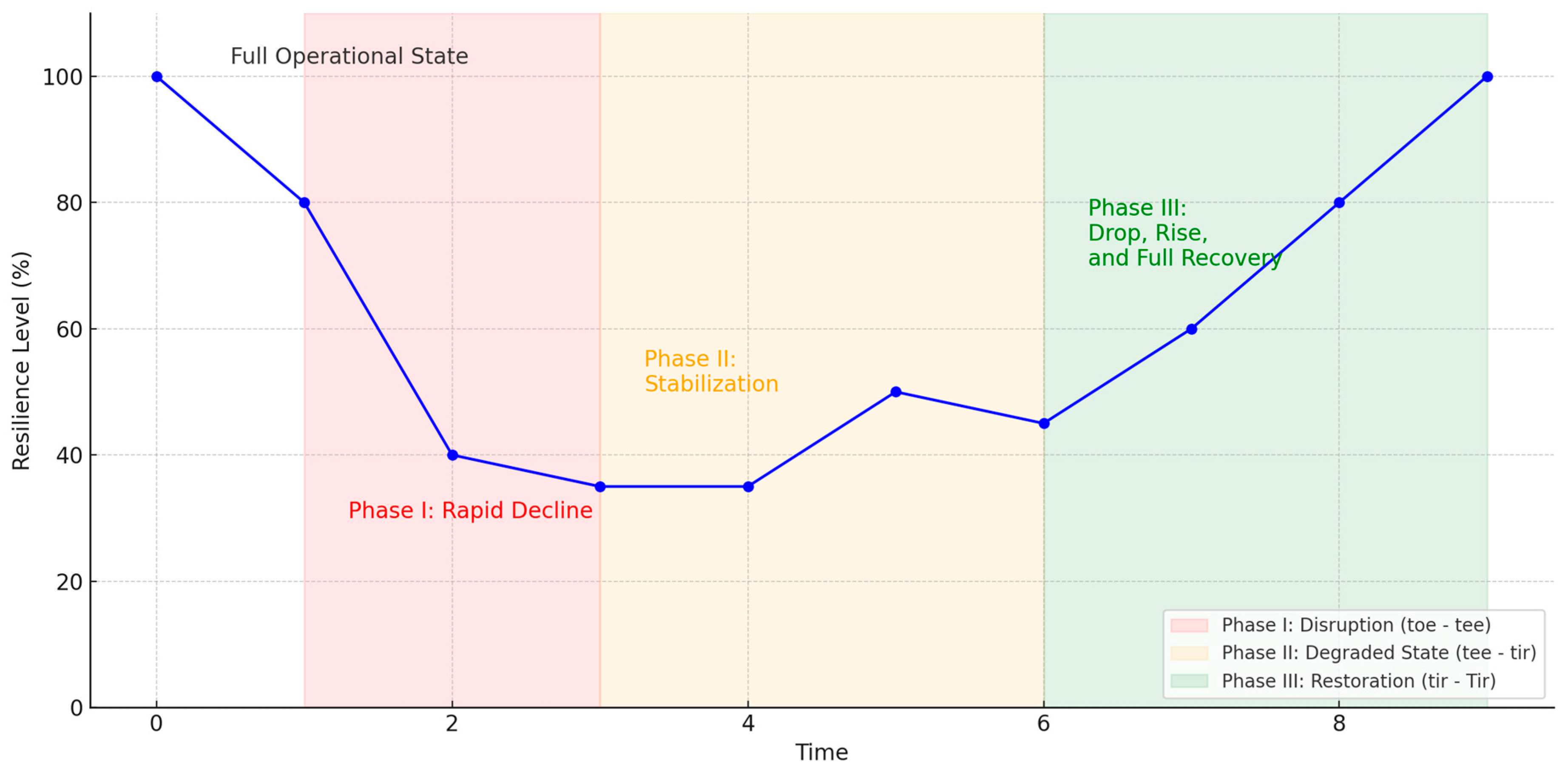
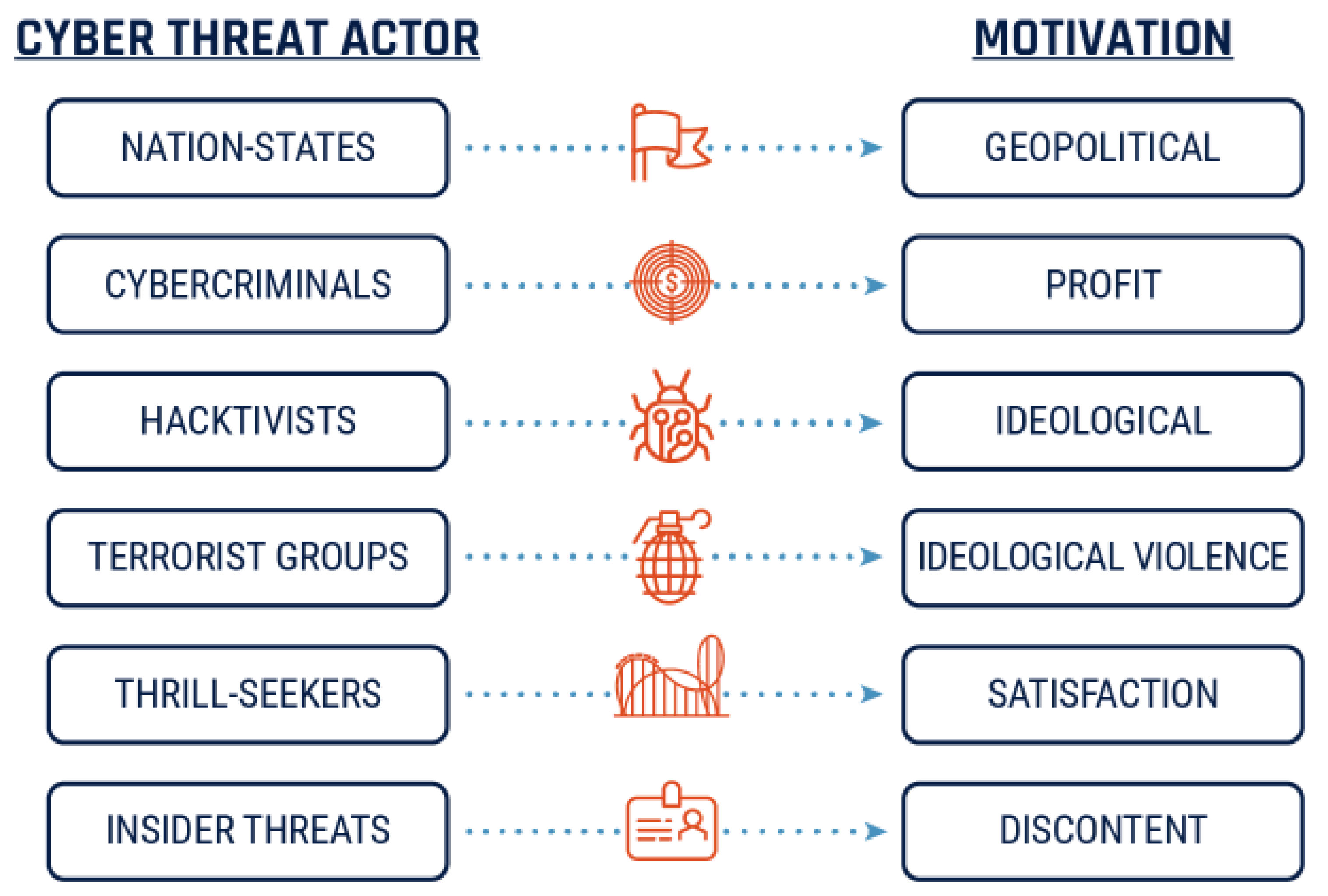
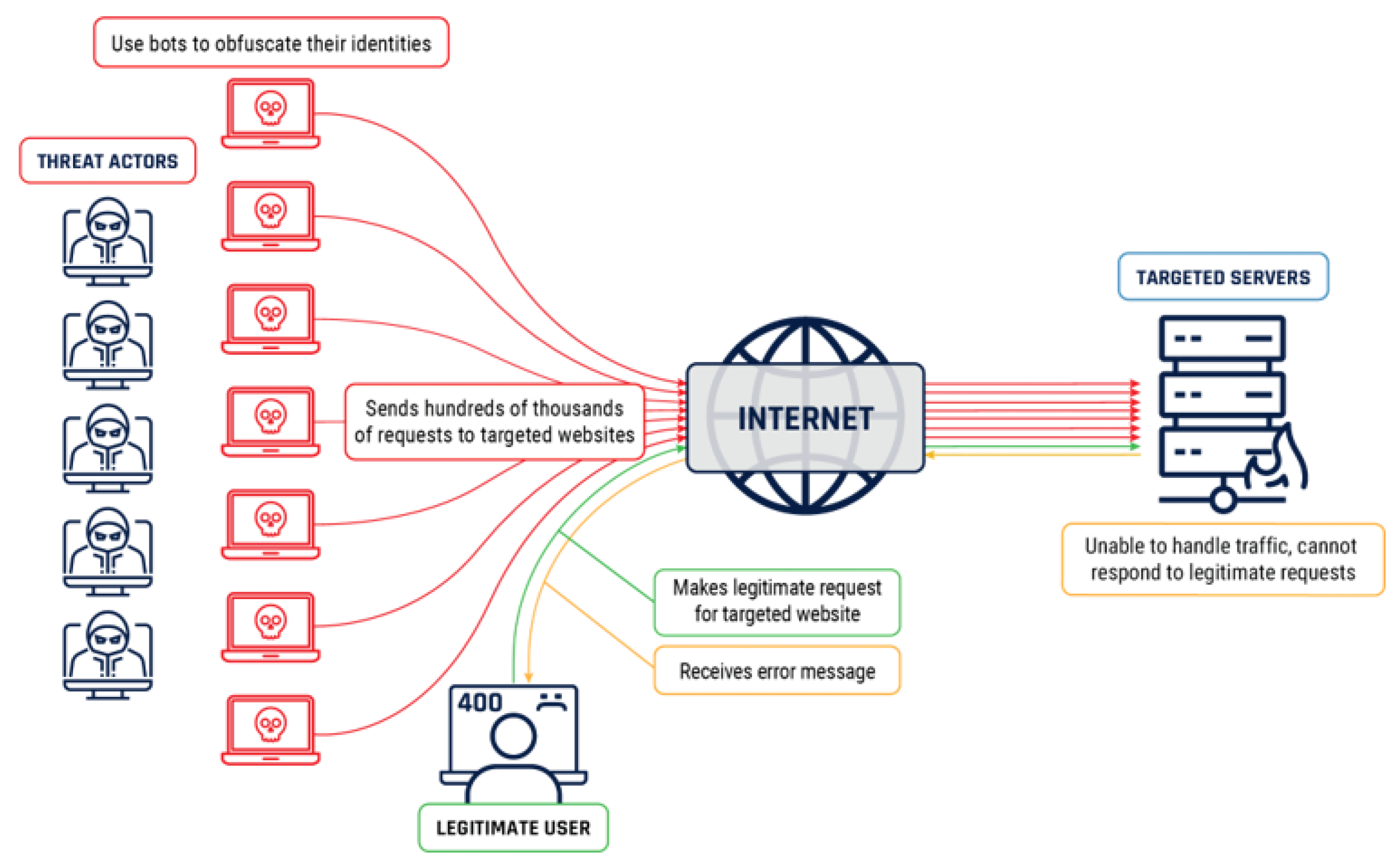

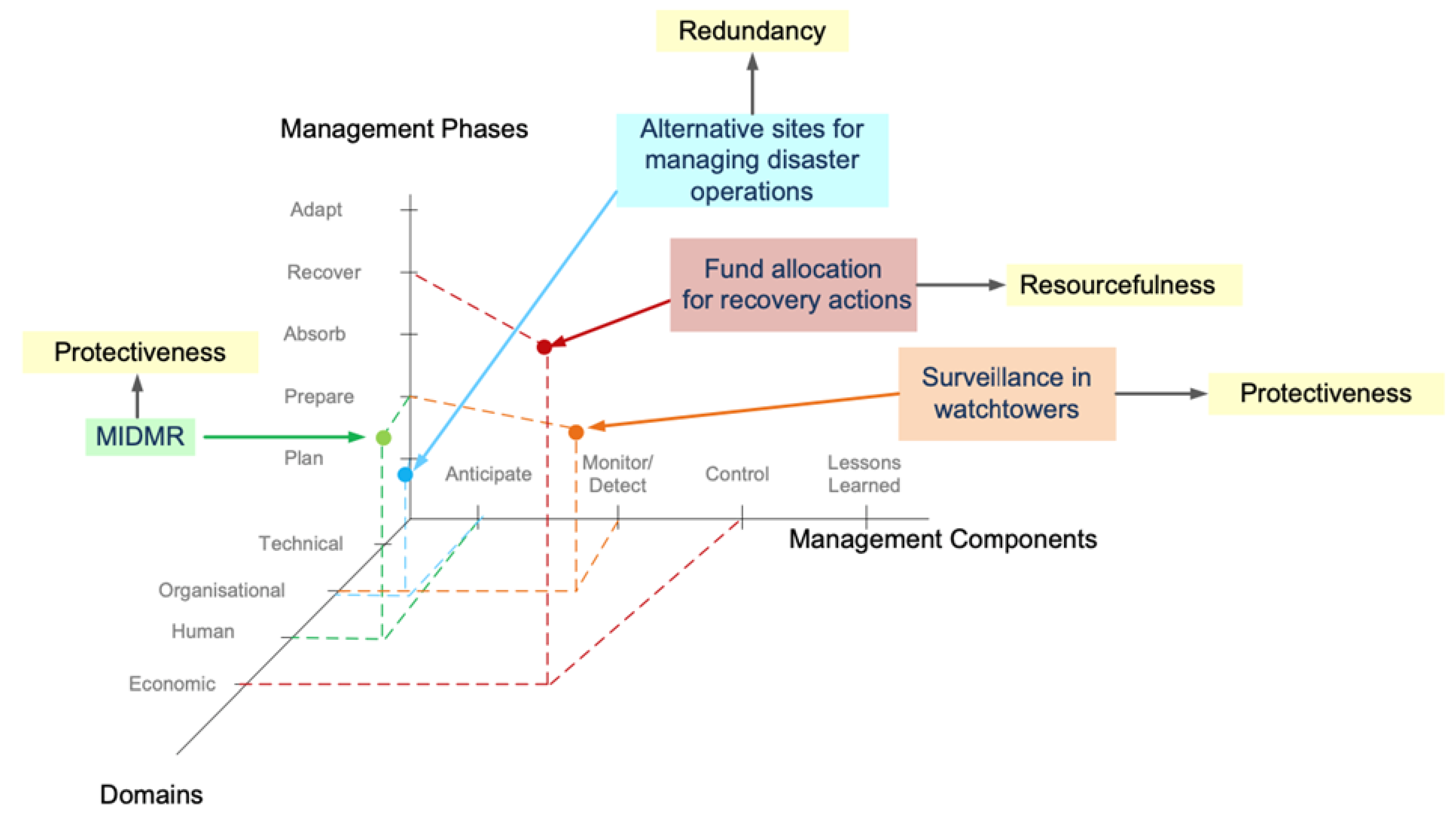
| No. | Definition | CP | Date |
|---|---|---|---|
| [45] | A measure of the persistence of systems and of their ability to absorb change and disturbance and still maintain the same relationships between populations or state variables. | 1973 | |
| [46] | Resilience is clearly related to other configurations of environment–society relationships such as vulnerability and criticality, some of which have an explicit spatial dimension to these social processes. | 2000 | |
| [47] | The ability of the system to reduce the chances of shock, to absorb a shock if it occurs, and to recover quickly after a shock (re-establish normal performance) | 2003 | |
| [48] | Resiliency is defined as the capability of a system to maintain its functions and structure in the face of internal and external change and to degrade gracefully when it must. | 2005 | |
| [49] | Resilience as the inherent ability and adaptive response that enables firms and regions to avoid maximum potential losses. | 2005 | |
| [50] | Infrastructure resilience is the ability to reduce the magnitude and/or duration of disruptive events. The effectiveness of a resilient infrastructure depends upon its ability to anticipate, absorb, adapt to, and/or rapidly recover from a potentially disruptive event. | ✓ | 2009 |
| [51] | Resilience is generally defined as the holistic ability or capacity of a system to sustain external and internal disruptions without discontinuity of the original functionality or, if discontinued, to recover fully and rapidly. | 2009 | |
| [52] | The capacity of a system, community, or society potentially exposed to hazards to adapt, by resisting or changing in order to reach and maintain an acceptable level of functioning and structure. This is determined by the degree to which the social system is capable of organizing itself to increase its capacity for learning from past disasters for better future protection and to improve risk reduction measures. | ✓ | 2009 |
| [53] | The capacity to reconfigure, that is adapt, its structure (firms, industries, technologies, institutions) so as to maintain an acceptable growth path in output, employment, and wealth over time. | 2011 | |
| [54] | The capacity of a civil infrastructure system to minimize performance loss due to disruption, and to recover a specified performance level within acceptable predefined time and cost limits | 2013 | |
| [55] | Resilience is the capacity of a social–ecological system to absorb or withstand perturbations and other stressors such that the system remains within the same regime, essentially maintaining its structure and functions. It describes the degree to which the system is capable of self-organization, learning, and adaptation. | ✓ | 2014 |
| [56] | The ability to deliver a certain service level even after the occurrence of a disruptive event, such as an earthquake, and to recover the desired functionality as quickly as possible. | 2014 | |
| [57] | Resilience is determined by three system capacities: the resistant capacity as the ability to prevent any possible hazards and reduce the initial damage level if a hazard occurs, the absorptive capacity as the degree to which the systems absorb the impacts of initial damage and minimize associated consequences, such as cascading failures, and the restorative capacity as the ability to be repaired quickly and effectively. | 2014 | |
| [58] | Ability of an infrastructure asset to maintain its performance to serve the required functions before, during, and after the occurrence of a natural hazard. | 2017 | |
| [59] | Resilience is the ability of a system, community, or society exposed to hazards to resist, absorb, accommodate to, and recover from the effects of a hazard in a timely and efficient manner, including through the preservation and restoration of its essential basic structures and functions. | ✓ | 2018 |
| [60] | To plan and prepare for the adverse events (planification), to reduce the impact of events (absorption or resistance), to minimize the time to recovery (recovery), and to evolve through the development of specific processes (adaptability). | ✓ | 2018 |
| [61] | Resilience is the ability of a CIS exposed to hazards to resist, absorb, accommodate to, and recover from the effects of a hazard in a timely and efficient manner, for the preservation and restoration of essential services. | ✓ | 2020 |
| [62] | Resilience is the ability to limit the extent, severity, and duration of system degradation following an extreme event. | ✓ | 2020 |
| [63] | Resilience of an energy system is the capacity of an energy system to tolerate disturbance and to continue to deliver affordable energy services to consumers. A resilient energy system can speedily recover from shocks and can provide alternative means of satisfying energy service needs in the event of changed external circumstances. | ✓ | 2020 |
| [64] | Resilience is characterized by reliability, redundancy, and recoverability. | 2022 | |
| [65] | Resilience is the ability of a system to deal with the impacts of unspecific and possibly unforeseen disruptive events, and that this ability comprises three pillar capacities whose quality can be extracted from performance curves. | ✓ | 2023 |
| Question | Focus |
|---|---|
| Resilience of what? | The specific system or component being analyzed |
| Resilience to what? | The types of disturbances or threats considered |
| Resilience how? | The mechanisms or strategies employed for resilience |
| Phases | Time Frames | Significance | Description |
|---|---|---|---|
| Phase I | Initial Disruption | Rapid reduction in resilience and service availability. | |
| Phase II | Post-Event Degraded State | Stabilization at a lower operational level. | |
| Phase III | Restoration | Gradual recovery of resilience and operational capacity. |
| Indicator | Description |
|---|---|
| Robustness | The capacity of the system to withstand shock and critical events without compromising performance or functionality. |
| Maintenance | Includes preventive maintenance (preparing the system to withstand a disruptive event) and corrective maintenance (repairing damaged components after an event). |
| Safety Design and Construction | System design characteristics that ensure a high level of resilience. |
| Data Acquisition and Monitoring | Data acquisition systems collect data necessary for the functioning of critical parts. Monitoring equipment checks data values, triggering alarms if they deviate from the expected range. |
| Redundancy | Availability of alternative resources (backups, replicate systems, etc.) to replace damaged parts, allowing continued operations. |
| Recoverability | The ability to restore original functioning and performance, determined by financial, material, and human resources, as well as the recovery process characteristics. |
| Indicator | Description |
|---|---|
| Adaptability | The capacity of the critical infrastructure organization to dynamically adapt to undesirable circumstances and/or uncertain environments by undergoing necessary changes. |
| Government Preparation | A government’s preparedness to anticipate events that may lead to crises and its capacity to act swiftly when such events occur. |
| Crisis Regulation and Legislation | The level of maturity and compliance with laws and regulations, including the degree of crisis awareness and the recentness of these regulations. |
| First Responder Preparation | The level of preparation, training, commitment, and crisis awareness of first responders (e.g., firefighters, military, police, and emergency forces). |
| Change Readiness | The organization’s capacity to adapt to environmental changes and perturbations, including the ability to predict and identify risks, and develop alternative strategies accordingly. |
| Leadership and Culture | The organization’s ability to foster a resilient culture, promoting values like agility, flexibility, innovation, and a transparent commitment to resilience. |
| Title | Ref. | Year |
|---|---|---|
| Impact of Distributed Decision-Making on Energy and Social Systems’ Resilience: A Case Study of Solar Photovoltaic in Switzerland | [147] | 2021 |
| Strengthening Urban Resilience: Understanding the Interdependencies of Outer Space and Strategic Planning for Sustainable Smart Environments | [148] | 2023 |
| Vulnerability and resilience of power systems infrastructure to natural hazards and climate change | [149] | 2021 |
| Centralized security governance for air navigation services: Innovative strategies to confront emerging threats against Civil Aviation | [150] | 2014 |
| Objective Resilience: Objective Processes | [151] | 2022 |
| A review of critical infrastructure protection approaches: Improving security through responsiveness to the dynamic modelling landscape | [152] | 2019 |
| Contributions of green infrastructure to enhancing urban resilience | [153] | 2018 |
| Simulation Gaming Can Strengthen Experiential Education in Complex Infrastructure Systems | [154] | 2018 |
| Cybersecurity policy and the legislative context of the water and wastewater sector in South Africa | [155] | 2021 |
| The role of protocol layers and macro-cognitive functions in engineered system resilience | [156] | 2019 |
| Year | Reference | Title | Key contribution |
|---|---|---|---|
| 2014 | Di Maio [150] | Centralized security governance for air navigation | Integrated approach to security governance, focusing on compliance with international aviation standards. |
| 2021 | Schweikert and Deinert [149] | Energy infrastructure resilience policies | Differentiation between asset hardening and functional resilience to address interdependencies. |
| 2021 | Lonergan and Sansavini [147] | Distributed decision-making in energy systems | Policies promoting decentralized energy production and resilience in social and technical systems. |
| 2022 | Ettouney [151] | Objective resilience processes | Addressing legal and organizational complexities to adapt resilience strategies for future uncertainties. |
| 2023 | Botezatu et al. [148] | Urban and outer space resilience | Integration of urban resilience planning with critical space infrastructure governance. |
| 2021 | Malatji et al. [155] | Water sector cybersecurity governance | Development of sector-specific cybersecurity frameworks aligned with national policies. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Longo, A.; Aghazadeh Ardebili, A.; Lazari, A.; Ficarella, A. Cyber–Physical Resilience: Evolution of Concept, Indicators, and Legal Frameworks. Electronics 2025, 14, 1684. https://doi.org/10.3390/electronics14081684
Longo A, Aghazadeh Ardebili A, Lazari A, Ficarella A. Cyber–Physical Resilience: Evolution of Concept, Indicators, and Legal Frameworks. Electronics. 2025; 14(8):1684. https://doi.org/10.3390/electronics14081684
Chicago/Turabian StyleLongo, Antonella, Ali Aghazadeh Ardebili, Alessandro Lazari, and Antonio Ficarella. 2025. "Cyber–Physical Resilience: Evolution of Concept, Indicators, and Legal Frameworks" Electronics 14, no. 8: 1684. https://doi.org/10.3390/electronics14081684
APA StyleLongo, A., Aghazadeh Ardebili, A., Lazari, A., & Ficarella, A. (2025). Cyber–Physical Resilience: Evolution of Concept, Indicators, and Legal Frameworks. Electronics, 14(8), 1684. https://doi.org/10.3390/electronics14081684








