Abstract
Internet of Things (IoT) systems are revolutionizing traditional living to a new digital living style. In the past, a lot of investigations have been carried out to improve the technological challenges and issues of IoT and have focused on achieving the full potential of IoT. The foremost requisite for IoT software system developers seeking a competitive edge is to include project-specific features and meet customer expectations effectively and accurately. Any failures during the Requirements Engineering (RE) phase can result in direct or indirect consequences for each succeeding phase of development. The challenge is far more immense because of the lack of approaches for IoT-based RE. The objective of this paper is to propose a requirements risk management model for IoT systems. The method regarding the proposed model estimates requirements risk by considering both customers’ and developers’ perceptions. It uses multiple criteria using intuitionistic fuzzy logic and analytical technique. This will help to handle the uncertainty and vagueness of human perception, providing a well-defined two-dimensional indication of customer value and risk. The validity of the approach is tested on real project data and is supported with a user study. To the best of our understanding, literature lacks the trade-off analysis at the RE level in IoT systems and this presented work fills this prerequisite in a novel way by improving (i) requirements risk assessment for IoT systems and (ii) handling developers’ subjective judgments of multiple conflicting criteria, yielding more concrete and more observable results.
1. Introduction
Internet of Things (IoT) devices and systems are touching every aspect of our society, ranging from their usage in smart and connected cities, smart nations, smart buildings/homes, smart mobility, transportation, ambient assisted living, smart farms, industry 4.0, and supply chain management, among others [1,2]. Furthermore, IoT technology offers its advantage in other sectors such as healthcare (e.g., IoT-based medical devices or smart health devices) and in the government sector, which uses IoT applications as national security applications. According to the latest report of Forbes [3], the market of IoT is expected to rise to $123 billion by 2021 and up to 25.1 billion units according to reports of [4]. This rapid increase in reliance on IoT devices, combined with the wide range of potential IoT applications, might dramatically amplify the potential vulnerabilities [2].
For the successful implementation and usage of any software system, requirements for elicitation, specification, and management play a key role in development. Requirement Engineering (RE) is the first phase of the software development lifecycle dealing with all kinds of anomalies such as inconsistencies and ambiguities in the requirements specification. This helps in reducing the after-effects of wrong requirement elicitation and specification leading to rework, increase in cost and time of development, and overall user satisfaction [5]. IoT system development is much more complex than traditional software development and presents new challenges to requirements engineering due to the involvement of heterogeneous technologies [6,7,8,9]. However, likewise, traditional software development IoT system development faces higher levels of ambiguity related to market demand, user expectations, working ecosystem (aptitude, tools, intellectual property), and technology. The majority of the existing work addresses attributes of IoT covering issues related to security and connectivity and its representation on the digital platform [10]. To the best of the authors’ awareness, the literature lacks studies dealing with requirement-related issues such as elicitation of hardware and software requirements, their mapping to a given platform, interaction and behavior-related issues between hardware and software for IoT system development, etc. [11].
Understanding, quantifying, and prioritizing threats to organizational assets and operations are all part of risk assessment [9]. However, there is a lack of studies addressing the issue of handling risk in IoT in requirements engineering. The presented work focuses on topics linked to requirements and their specification instead of assessing/examining requirements for risk (discussed in Section 2). Requirement risk assessment is one of the profound areas lacking such practices, particularly in the RE phase of development. Without formal techniques to make an informed decision on critical choices, software engineers can face surprising outcomes. The cost to repair a requirement anomaly varies with how far the development has progressed. The fixing expenditure is 3 times greater in design, 10 times greater during coding, 50 times greater during testing, and around 100 times higher subsequently at the release [12,13]. Well-defined, explicit knowledge about various risks in requirements helps software developers manage the project more effectively and efficiently. Especially in today’s time-to-market era, it is essential to know what risks requirements can have so that a corrective measure/decision can be taken to plan successive releases.
International standard systems and software engineering ISO/IEC/IEEE 15288:2015 [14] and ISO/IEC/IEEE 12207:2017 [15], which explain the software life cycle process, are applied to homogenous systems and can be integrated with other complex systems (e.g., IoT systems). However, these standards are not a one-fit model for all systems. A tailor-made system in this regard can be a good option to satisfy software development needs. Existing risk-based research indicates that a limited number of studies have addressed anomalies in requirements (also referred to as defects), their discovery, verification, and validation of requirements with existing defect taxonomy, and analysis of dependency between requirements, which is still to be explored for IoT systems [11]. The task of measuring risk becomes challenging as requirements interrelate and can have dissimilar dimensions concerning the integration of software and hardware components in IoT systems [6,7,8,9]. Therefore, multiple criteria should be considered while measuring the risk related to implementing requirements.
This paper presents a risk assessment framework that considers multiple criteria to support software developers in measuring and mapping the initial discovery of possible risks of executing requirements in IoT platforms. To interleave human actions, Intuitionistic Fuzzy Set (IFS) [16] is used to rank risks by combining several conflicting criteria. From the available catalog of multi-criteria decision models, IFS is a powerful method that leverages the benefits of uncertain and vague human decisions, noticeably and intuitively. It is a scalar value that considers both the best and worst choices with good computational competence. The main contribution of this paper is the presentation of a requirements risk assessment model for IoT systems that considers multiple criteria, in particular, requirements deficiencies, their inter-relationships, complexity, and customer priority to offer robust solutions with reduced overhead in software maintenance. Specifically, the following research questions are addressed: (a) How effective is a multi-criteria IFS-based requirements risk assessment method for IoT systems? Can it improve the expert’s manual judgment, in terms of minimizing software maintenance cost and time? (b) How valid, concrete, and feasible are the solutions provided by a proposed approach, from the human expert’s perspective?
2. Related Work
Both academia and industry are expending effort regarding the effective depiction of IoT systems. The literature lacks studies particularly focusing on risk analysis in RE for IoT systems. The core of these systems is software and therefore in this section, both IoT and in general software systems are discussed. Past studies [17,18,19,20,21] have reported a review of the benefits, challenges, and impact of corrective requirements elicitation for IoT applications. Commercial and standardization bodies have also undertaken initiatives promoting IoT requirement analysis and related reference architectures (e.g., Industrial Internet Reference Architecture (IIRA) [22]). Existing systematic reviews on requirement elicitation [18,21,23,24,25,26] have summarized empirical evidence, challenges, methods, and outcomes of requirement elicitation, but the authors have not discussed the elicitation of IoT applications. Lim et al. [18] represent the survey on IoT-based elicitation techniques for a handful of methods and conclude that interviews and prototypes are commonly used elicitation techniques, and that users are the common sources of requirements. They also report a lack of methodical understanding of elicitation techniques for IoT where most of the studies are limited to requirements elicitation and specification, the importance and conflicting nature of functional and non-functional requirements, specification using use case diagrams, using modeling language for conceiving requirements, and a scenario-based technique [5,7,27,28,29,30,31]. IoTReq—a Unified Modeling Language (UML) modeling method that supports non-functional requirements is another approach proposed by Reggio [7] for elicitation and specification of IoT system requirements. The work reported by Laplante et al. [27] also focuses on non-functional requirements analysis in IoT systems. Costa et al. [30] reported conflicts between functional and non-functional requirements. A recent study by Ferraris et al. [28] has proposed a trust-based requirements elicitation method focusing on security, privacy, and usability to enhance the level of trust in IoT systems. A study presented by Hassan et al. [32] presents an outline and assessment of six development methods to address feasibility analysis, requirements engineering, analysis and design, and deployment, etc. The results of experimentation, conducted on real-world projects, stated that none of the six approaches covers all the stages necessary for IoT system development.
Requirements risk assessment is closely related to requirement elicitation. The majority of the methods listed in the literature perform quantitative and qualitative analysis on elementary risk processes, including risk discovery, investigation, planning, etc. to ascertain and control the risks [33,34,35,36,37]. These models are suitable for varied projects in small or large organizations used in different fields. According to [38,39], only 5% of the project budget is needed to commence risk management to prevent the probabilities of schedule overrun by 50–70%. Furthermore, researchers have also presented models of risk estimation using the analytic hierarchy process, Bayesian belief network, machine learning, risk metrics, fuzzy entropy, goal-oriented methodologies, decision trees, UML, etc. [40,41].These methods cumulatively state that evaluation of risk can efficiently help in producing software of quality by lessening the exposure to software risk. Furthermore, some researchers [42,43] have addressed in particular requirements risk management, risk-based testing, project risk dependencies, etc. These models have a negligible emphasis on considering software risks in the initial stage of the Software Development Life Cycle (SDLC). More recently, Fahmideh et al. [44] conducted a mixed quantitative and qualitative study on key tasks with industry experts to highlight the most important development process tasks, challenges, and recommendations related to the development of IoT systems. It can be concluded that the acceptance of early risk detection and mitigation can help in curtailing the loss in software projects.
3. Proposed Approach
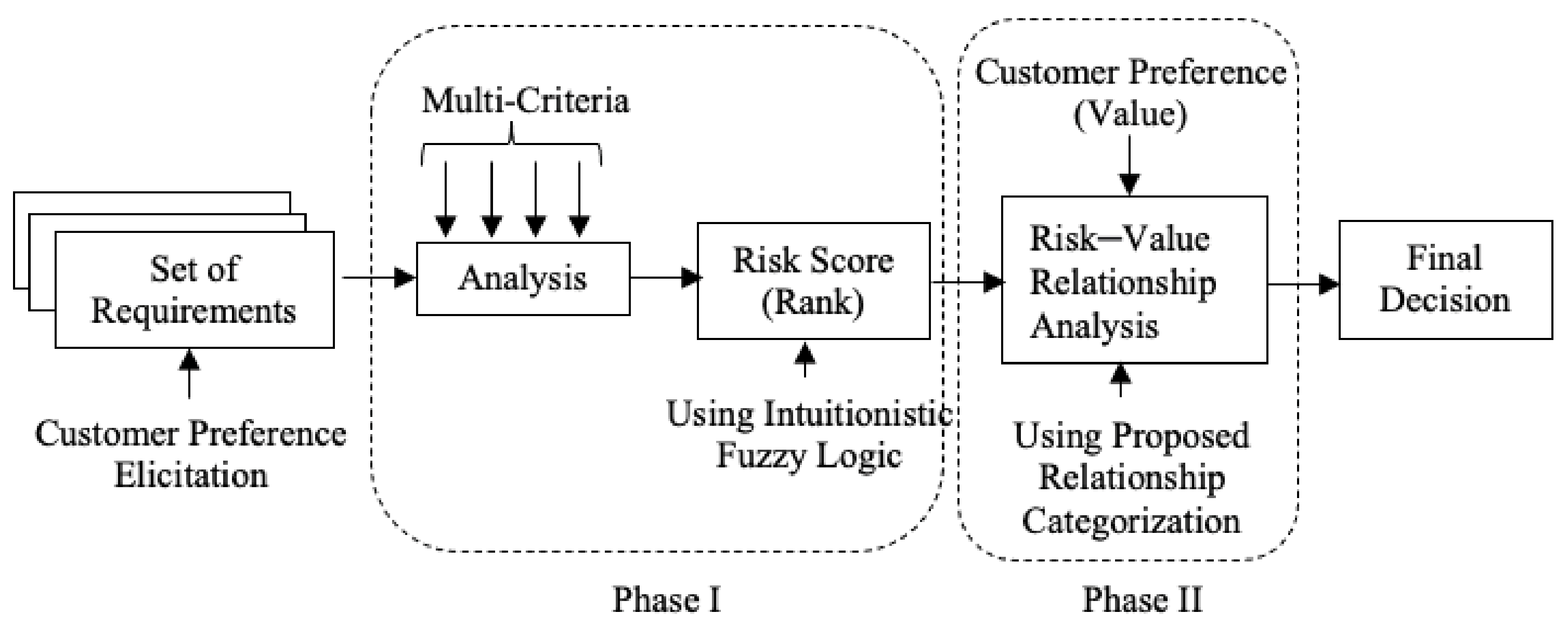
Multi-criteria decision-making techniques are beneficial in selecting choices in discrete problems. Risks can strike in any phase of the SDLC and should be controlled suitably using strategies designed for individual phases of SDLC. The IFS-based risk assessment framework will help in finding the best value of decision variables, which will be used as a measure of the effectiveness of a decision. The whole process is sketched in Figure 1.
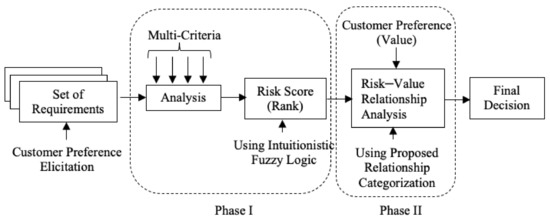
Figure 1.
Basic steps in the proposed risk assessment method.
The foremost prerequisite considered for the proposed approach is to simplify with a quick analysis process yielding accurate and trustworthy results. If both of these conditions are not met, the process is unlikely to be used in the requirements risk assessment process. To achieve this aim, a two-fold process is proposed.
Phase I: Development and application of an intuitionistic fuzzy logic-based model.
Real-world situations are frequently complex and the data gathered is not always complete. In many decision-making situations, we have more than two possibilities, yet we do not always have complete information about those options. Simple set theory and Boolean logic are insufficient to model these situations. Fuzzy set theory [45] and fuzzy logic are commonly used to deal with such circumstances [45]. Despite their wide range of applications [46], fuzzy sets are limited by the uncertainty element due to the lack of comprehensive information. In addition to membership values, Atanassov’s intuitionistic fuzzy sets [16] give an intuitive framework for dealing with vagueness from imprecise information by taking non-membership values into consideration. In this phase, the risk score using IFS on multiple criteria are computed, and later the analytical technique is used to analyze the relationship between the risk score and customer priority value for a specific requirement.
Brief Introduction of Intuitionistic Fuzzy Sets
The following section discusses a concise overview of IFS from Atanassov’s intuitionistic fuzzy sets [16,47].
Definition 1.
where the functionandrepresents the element’s degree of membership and non-membershiprespectively. For every,andsatisfy, 0 ≤. Contrary to traditional fuzzy sets, the sum ofanddoes not always have to be 1. This is especially important when the system does not have all of the information it requires. Besides, we haveas the intuitionistic fuzzy set index or the hesitation margin of. is the degree of indeterminacy ofto the IFS A andandfor every. represents a lack of understanding about whether or notbelongs to IFS A.
Let X be a non-empty set. An intuitionistic fuzzy set A in X represents an entity with the following form:
Definition 2.
Let A ∈ X be IFS, then;
- 1.
- π(x) = 1 − μA(x) − vA(x) is called the degree of indeterminacy of the element x ∈ A.
- 2.
- ∂(x) = μA(x) + πA(x)μA(x) is called the degree of favor of x ∈ A.
- 3.
- η(x) = vA(x) + πA(x)vA(x) is called the degree of opposition to x ∈ A.
For example, let A be an intuitionistic fuzzy set with μA(x) = 0.5 and vA(x) = 0.3. Then, πA(x) = 0.2, ∂A(x) = 0.6, and ηA(x) = 0.36. It can be interpreted as “the degree that the object x belongs to IFS A is 0.5, the degree that the object x does not belong to IFS A is 0.3, the degree of hesitancy or indeterminacy of x belonging to IFS A is 0.2, the degree of favor of x belonging to IFS A is 0.6, and the degree of opposition to x not belonging to IFS A x is 0.36”.
Definition 3.
Two IFS A and B are said to be similar or cognate if ∃μA(x) = μB(x) or vA(x) = vB(x).
Definition 4.
Two IFS A and B are said to be equal or comparable if μA(x) = μB(x) and vA(x) = vB(x).
Definition 5.
Two IFS A and B are said to be equivalent to each other i.e., A is equivalent to B, denoted by A~B if ∃ functions f: μ(x)→μB(x) and f: vA(x)→vB(x), which are both injection and surjection. Then, the functions define a one-to-one correspondence between A and B.
Definition 6
Let A and B be two IFS, A ⊆ B→μ(x) ≤ μB(x) and vA(x) ≥ vB(x) for . Then A is a subset of B and B is a superset of A.
Definition 7.
A is a proper subset of B, i.e., A⸦B if A ⊆ B and A ≠ B. It means μ(x) ≤ μB(x) and vA(x) ≥ vB(x) but μA(x) ≠ μB(x) and vA(x) ≠ vB(x) for.
Definition 8.
An IFS A is dominated by another IFS B (i.e., A≼B), if there exists an injection from A to B. A is strictly dominated by B (i.e., A≺B), if (i) A≼B and (ii) A is not equinumerous with B.
Definition 9.
LetA,B,andCbe IFSs. Then;
- i.
- A≼A, i.e., A is a reflexive relation,
- ii.
- A≼B and B≼A, i.e., a symmetric relation,
- iii.
- A≼B and B≼C⇒A≼C, i.e., a transitive relation.
Definition 10.
For every two IFSs A and B, the following operations can be defined:
A ⊆ B iff(∀x ∈ X)(µA(x) ≤ µB(x) and νA(x) ≥ νB(x));
A = B iff(∀x ∈ X)(µA(x) = µB(x) and νA(x) = νB(x));
Ac: = {<x, νA(x), µA(x) > |x ∈ X};
A∩B: = {<x, min(µA(x), µB(x)), max(νA(x),νB(x)) > |x ∈ X};
A∪B: = {<x, min (µA(x), µB(x)), max(νA(x),νB(x)) > |x ∈ X};
∪Ai: = {<x, max(µi), min(νi) > |x ∈ X} i ∈ I;
∩Ai: = {<x, min(µi), max(vi) > |x ∈ X} i ∈ I;
[]A: = {<x, µA(x), 1 − µA(x) > |x ∈ X} (Necessity operator);
⟨⟩A: = {<x, 1 − νA(x), νA(x) > |x ∈ X}(Possibility operator)
The intuitionistic fuzzy set Bij can be expressed as follows to obtain values from developers for criteria:
where, 0 ≤ µij ≤ 1, 0 ≤ υij ≤ 1 and 0 ≤ µij + υij ≤ 1.
Bij = {ri, cj, µij, υij}
Also, 0 < i ≤ n and 0 < j ≤ m, where n = total number of requirements in the given set; m = total number of criteria, µij and υij represent the degree of membership and the degree of non-membership for the requirements ri ∊ R for the criteria cj ∊ C. The greater the hesitation index number, the more hesitant the developers were to choose ri ∊ R for the criteria cj ∊ C.
where, 0 < i ≤ n and 0 < j ≤ m.
πij = 1 − µij − υij
Each criterion is given a weight based on intuitionistic fuzzy values. For each alternative requirement ri ∊ R, the optimal rank value can be computed using the following equation:
such that: i = (1, 2, 3, …, n).
The following linear programming equations are generated to obtain the optimal rank value using (4):
such that:
and
such that:
for each i = (1, 2, 3, …, n).
Using the Simplex Method, the following optimal weights of the criteria can be calculated.
and
With the help of these, the rank value of the requirements can be found as:
and
for each i = (1, 2, 3, …, n).
The objective function can be re-written for every requirement ri ∊ R as
also,
Using these weight vectors, the following formula can be used to obtain the final optimal value for all the alternatives:
Phase II: The relationships to be analyzed are divided into three distinct categories, discussed in Table 1.

Table 1.
Risk–value relationship categorization.
Using this analytical visualization, the relationship analysis can be performed in two dimensions: according to their development risk score computed and customer priority value elicited from customers. The proposed method is applied and tested on real project data, and later the results are compared to evaluate the effectiveness of the proposed approach. Based on the above-mentioned relationship categories, the software developers can effectively and accurately make an informed decision on the inclusion or exclusion of a particular requirement. It is a scalable framework wherein decisions on addition and omission of multiple criteria can be acquired subject to the project/organizational requirements. Let R represent a pool of requirements having n requirements such that ri ∈ R. Table 2 below presents the criteria for risk assessment used in this work.

Table 2.
Risk estimation criteria.
These risk estimation criteria are elected through knowledge abstraction from the Project Management Body of Knowledge (PMBOK), blogs, and discussion with software industry practitioners [49,50,51].
4. Empirical Validation
To perform and validate the proposed approach, it was tested on real project data from [52]. The summary of the project is as follows: it is a web portal assisting clients by providing on-demand and reserved parking slots through an application build over iPhone Operating System (IOS) and Android platforms. Currently, this allocation is performed manually. The company profile is shown in Table 3.

Table 3.
Company Profile.
This project was developed as a part of global software development in India and the US during 2018–2019.
A list of 12 high-level requirements comprising 84 lower-level requirements was finalized for the project during the RE phase. The customer priority value was elicited, and the developer’s analysis was recorded using IFS. The process started with the gathering of customers; preferences for each requirement (CPV (ri)). These preferences were recorded on a five-points Likert scale using interactive Graphical User Interface (GUI) support.
4.1. Results and Discussion
The steps below were performed to come to a conclusion on the utilization of the recommended method:
- (1)
- Using the intuitionistic inputs (discussed above) the criterion was calculated using linear programming.
- (2)
- The weights for the membership and non-membership values for the selected criteria were calculated using (8) and (9). The best rankings for each requirement were determined by utilizing (14).
- (3)
- Finally, these weights were used to calculate pu and pl using to (10) and (11). Thereafter, the normalized weights (WRs) were computed for each requirement.
- (4)
- The next risk–value relationship was conducted. Figure 2 shows the Risk–Customer priority value diagram for 10 requirements collected from a sub module of real project data. The relationships are analyzed within three distinct categories:
- ○
- Relationship depicting the high ratio of customer priority value to development risk score (a priority value–risk ratio exceeding 2).
- ○
- Relationships depicting the medium ratio of customer priority value to development risk score (a priority value–risk ratio between 0.5 and 2).
- ○
- Relationships depicting the low ratio of customer priority value to development risk score (a priority value–risk ratio lower than 0.5).
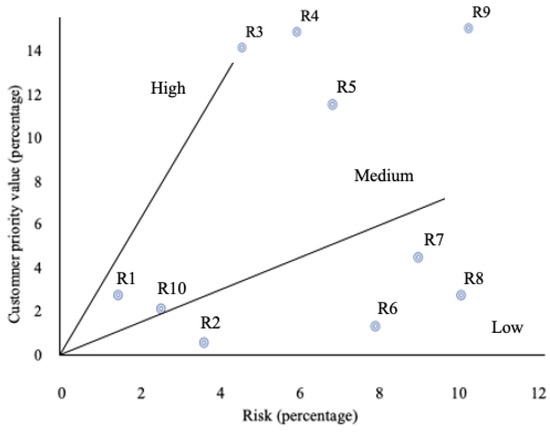
Figure 2.
Risk–Customer priority value diagram presenting relationship for project data. R1–R9 are the software requirements.
Figure 2.
Risk–Customer priority value diagram presenting relationship for project data. R1–R9 are the software requirements.
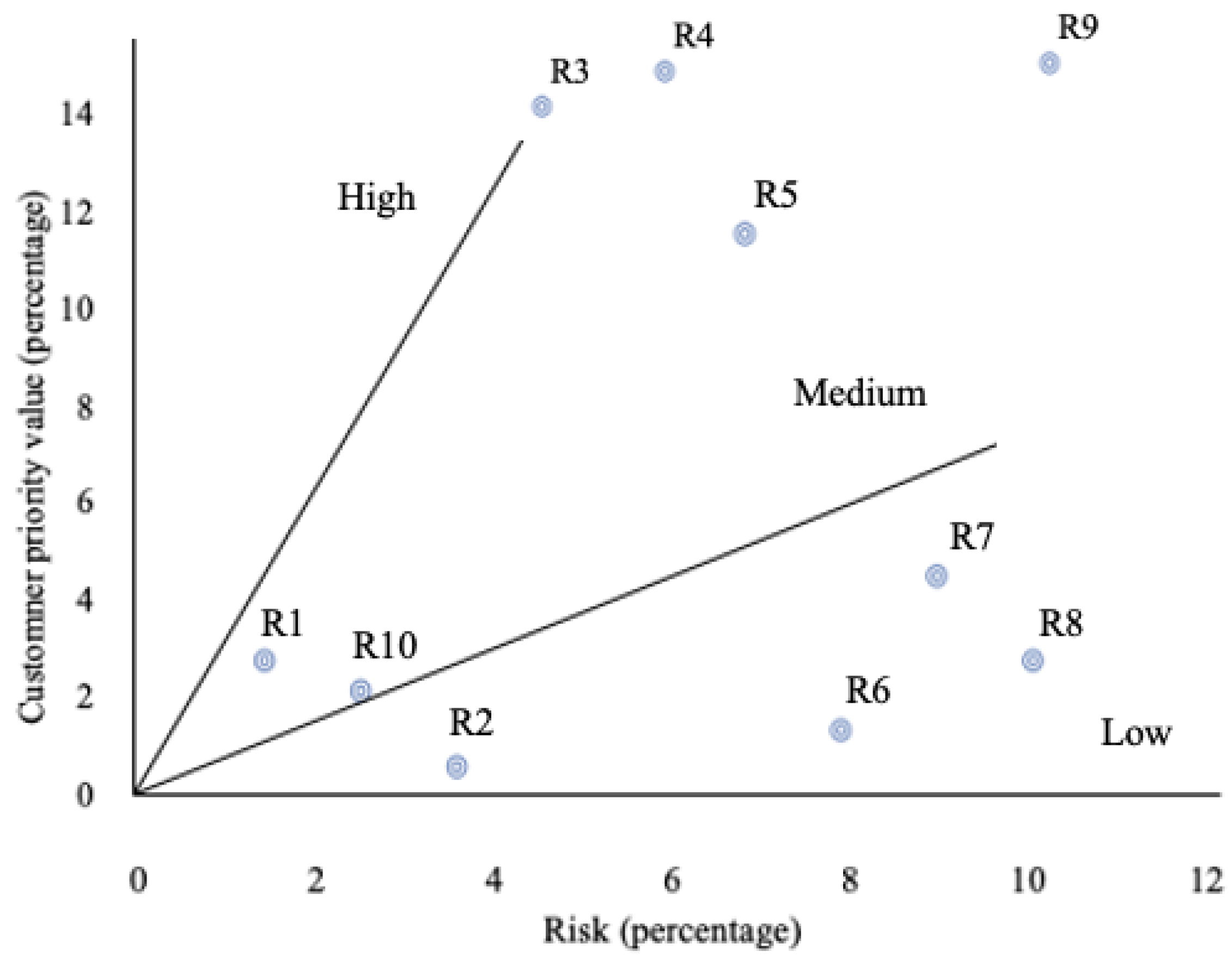
The customer priority value–risk value diagram helps requirements risk assessment. It can be concluded that if the requirements with high and medium ratios were selected for implementation over the requirements that contribute little to customers’ priority value, risk, cost, and duration of the project can be reduced significantly.
Generally, dependency is represented over time, which specifies that an activity or task cannot begin until a preceding activity has been completed. Analysts look at the data and keep track of the needs’ dependencies. There is a lack of trade-off analysis in software engineering, notably for requirements analysis for IoT software systems, which is a vital aspect of multidisciplinary systems engineering. The authors believe that employing IFS to implement a customer priority value–risk value approach is a good starting step toward meeting this requirement. However, due to the mathematical foundation of IFS, the proposed approach yields more concrete results complementing the win–win situation. The proposed method is a valuable addition to the literature because it is more observable, robust, and easier to use.
4.2. Survey and Feedback
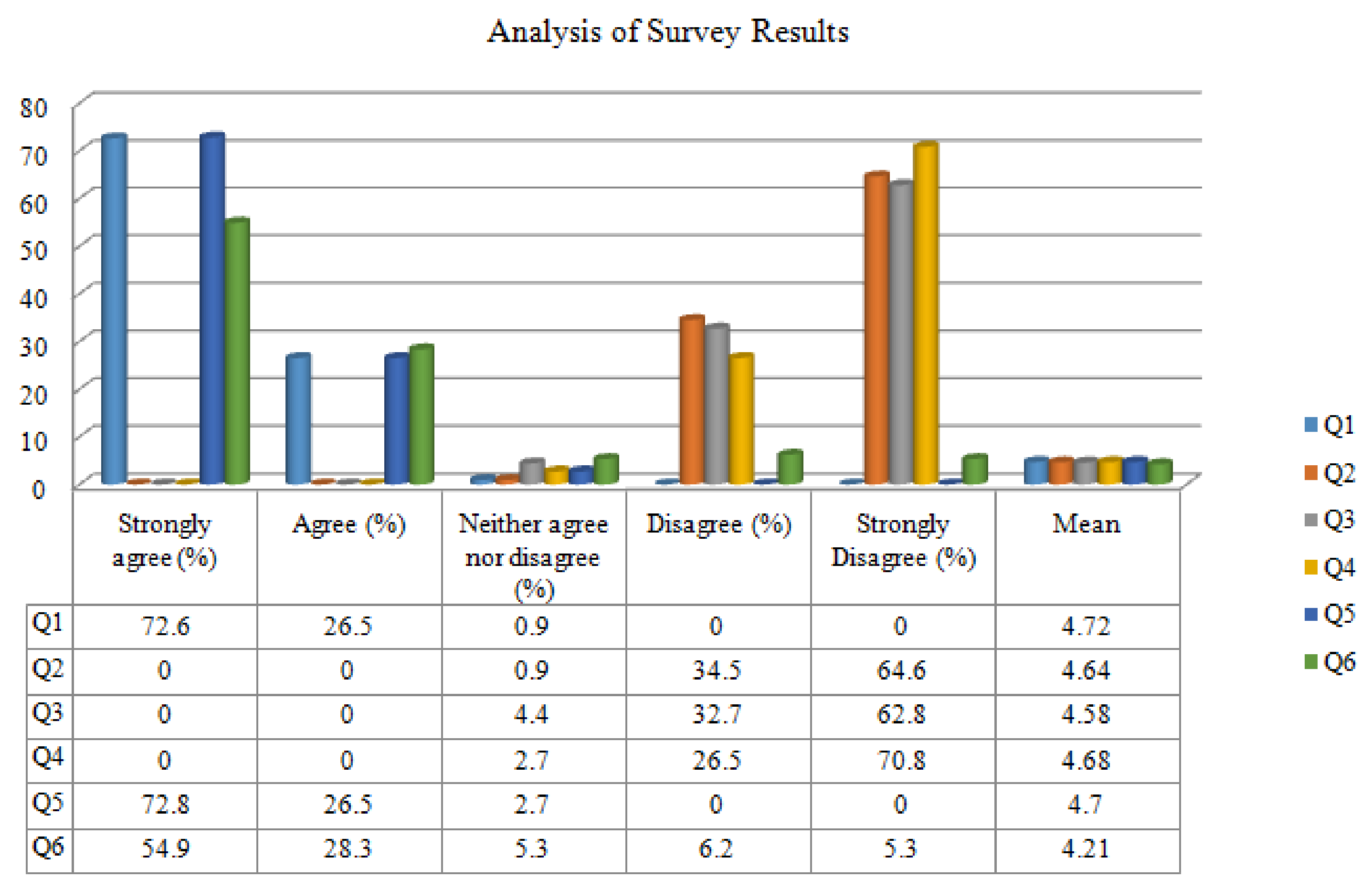
To answer the research question, a survey was conducted with 35 industry experts with more than 8 years of rich experience. Respondents’ scores were gathered on a five-point Likert scale. The purpose of the survey questionnaire was to gather information in order to answer the following question—“Can the proposed approach effectively be used to assess risk quantitatively and without ambiguity?”
The data was collected online and analyzed to see how well the proposed solution fits in real-world projects in producing the expected result. Figure 3 summarizes the results of the survey for formulated questions to capture the response. The following are the questions used in the survey:
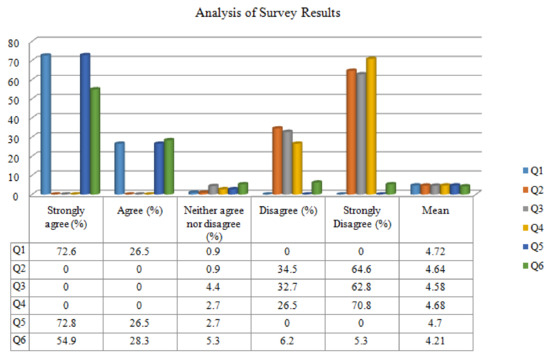
Figure 3.
Analysis of survey results.
- (1)
- Does the proposed solution for risk assessment make sense, in general?
- (2)
- Are there any constraints or dependencies that make the solution infeasible?
- (3)
- Is it costly to include the solution? Are there any difficulties that would make it a long process?
- (4)
- Is there any difficulty in terms of missing or misleading values?
- (5)
- Is it feasible to change your inputs? In such a situation, will it affect the solution? Do you find it positive?
- (6)
- In comparison to the approach followed in your workplace, will this solution have the potential to make a difference?
It can be concluded from the survey results that the majority of the respondents agreed that the proposed approach is a promising solution assisting developers to measure risk early in the RE phase, thereby reducing the overhead of cost and time of software maintenance.
5. Conclusions and Future Work
This paper presents a multi-criteria requirements risk estimation model for IoT systems, helping software developers to assess the probable risk of implementing gathered requirements. This will help in administering preventive actions to mitigate risk as early as possible. This model captures customer value and computes requirements risk using the intuitionistic fuzzy logic method, a multi-criteria decision analysis method. It is combined with an analytical method to analyze customer value and requirements risks. It is essential to balance customer satisfaction and risk associated with implementing requirements as both vary by order of magnitude. IFS is a powerful method to handle the uncertainty and vagueness of human perception. Results of experimentation and surveys on real project data and with IT experts conclude that the proposed method is an effective measure of assessing requirements risk by minimizing maintenance time and fostering customer value. The work presented is novel in improving (i) requirements risk assessment and (ii) handling the developers’ subjective judgments of multiple conflicting criteria to provide robust solutions.
As a part of future work, the authors plan to store the analysis using a cloud computing framework about the people responsible, their rationale, their assumptions, and their initial and final decision values to support software requirement reuse for distributed software development/global software development.
Author Contributions
Conceptualization, C.G; methodology, C.G. and V.G.; software, C.G. and V.G.; validation C.G. and V.G.; formal analysis, C.G.; investigation, C.G. and V.G.; resources, C.G. and V.G.; data curation, C.G. and V.G; writing—original draft preparation, C.G. and V.G.; writing—review and editing, C.G. and V.G; visualization, C.G. and V.G.; supervision, C.G. and V.G.; project administration, C.G. and V.G.; funding acquisition, C.G. and V.G. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to express their sincere thanks to the software industry practitioners for taking part in the validation. Their expertise has been very useful in the initial validation.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Baiyere, A.; Topi, H.; Venkatesh, V.; Wyatt, J.; Donnellan, B. Internet of Things (IoT)—A Research Agenda for Information Systems. Commun. Assoc. Inf. Syst. 2020, 47, 524–549. [Google Scholar] [CrossRef]
- Souri, A.; Hussien, A.; Hoseyninezhad, M.; Norouzi, M. A systematic review of IoT communication strategies for an efficient smart environment. Trans. Emerg. Telecommun. Technol. 2019, 33, e3736. [Google Scholar] [CrossRef]
- Forbes. Available online: https://www.forbes.com/sites/louiscolumbus/2018/06/06/10-charts-that-will-challenge-your-perspective-of-iots-growth/?sh=4ef917473ecc (accessed on 30 March 2022).
- Gartner, I. Forecast: Internet of Things Endpoints and Associated Services, Worldwide. 2017. Available online: https://www.gartner.com/en/documents/3840665 (accessed on 30 March 2022).
- Mahalank, S.N.; Malagund, K.B.; Banakar, R.M. Non Functional Requirement Analysis in IoT based smart traffic management system. In Proceedings of the 2016 International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 12–13 August 2016; pp. 1–6. [Google Scholar]
- Nguyen-Duc, A.; Khalid, K.; Bajwa, S.S.; Lønnestad, T. Minimum Viable Products for Internet of Things Applications: Common Pitfalls and Practices. Future Internet 2019, 11, 50. [Google Scholar] [CrossRef] [Green Version]
- Reggio, G. A UML-based proposal for IoT system requirements specification. In Proceedings of the 10th International Workshop on Modelling in Software Engineering—MiSE ’18; Association for Computing Machinery (ACM): New York, NY, USA, 2018; pp. 9–16. [Google Scholar]
- Lepekhin, A.; Borremans, A.; Ilin, I.; Jantunen, S. A Systematic Mapping Study on Internet of Things Challenges. In Proceedings of the 2019 IEEE/ACM 1st International Workshop on Software Engineering Research & Practices for the Internet of Things (SERP4IoT), Montreal, QC, Canada, 27 May 2019; pp. 9–16. [Google Scholar]
- Giray, G.; Tekinerdogan, B.; Tüzün, E. IoT System Development Methods. In Internet of Things; CRC Press: Boca Raton, FL, USA, 2017; pp. 141–159. [Google Scholar]
- Mora, S.; Gianni, F.; Divitini, M. Tiles: A card-based ideation toolkit for the internet of things. In Proceedings of the 2017 Conference on Designing Interactive Systems; Association for Computing Machinery (ACM): New York, NY, USA, 2017; pp. 587–598. [Google Scholar]
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Boehm, B.; Basili, V.R. Defect reduction top 10 list. Computer 2001, 34, 135–137. [Google Scholar] [CrossRef]
- Al-Sarayreh, K.T.; Meridji, K.; Abran, A. Software engineering principles: A systematic mapping study and a quantitative literature review. Eng. Sci. Technol. Int. J. 2020, 24, 768–781. [Google Scholar] [CrossRef]
- ISO/IEC/IEEE 15288:2015; Systems and Software Engineering—System Life Cycle Processes. International Organization for Standardization (ISO): Geneva, Switzerland, 2015.
- ISO/IEC/IEEE 12207:2017; Systems and Software Engineering—Software Life Cycle Processes. International Organization for Standardization (ISO): Geneva, Switzerland, 2017.
- Atanassov, K. Intuitionistic fuzzy sets. Int. J. Bioautom. 2016, 20, 1. [Google Scholar]
- Yaqoob, I.; Ahmed, E.; Hashem, I.A.T.; Ahmed, A.I.A.; Gani, A.; Imran, M.; Guizani, M. Internet of Things Architecture: Recent Advances, Taxonomy, Requirements, and Open Challenges. IEEE Wirel. Commun. 2017, 24, 10–16. [Google Scholar] [CrossRef]
- Lim, T.Y.; Chua, F.F.; Tajuddin, B.B. Elicitation Techniques for Internet of Things Applications Requirements: A Systematic Review. In Proceedings of the 2018 VII International Conference on Network, Communication and Computing, Taipei City, Taiwan, 14–16 December 2018; Association for Computing Machinery (ACM): New York, NY, USA, 2018; pp. 182–188. [Google Scholar]
- Wnuk, K.; Murari, B.T. The Impact of Internet of Things on Software Business Models. In Proceedings of the Lecture Notes in Business Information Processing; Springer: Berlin/Heidelberg, Germany, 2016; pp. 94–108. [Google Scholar]
- Kalunga, J.; Tembo, S.; Phiri, J. Industrial internet of things common concepts, prospects and software requirements. Int. J. Internet Things 2020, 9, 1–11. [Google Scholar]
- Silva, D.; Gonçalves, T.G.; Da Rocha, A.R.C. A Requirements Engineering Process for IoT Systems. In Proceedings of the Proceedings of the XVIII Brazilian Symposium on Software Quality, Fortaleza, Brazil, 28 October–1 November 2019; Association for Computing Machinery (ACM): New York, NY, USA, 2019; pp. 204–209. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Pacheco, C.; García, I.; Reyes, M. Requirements elicitation techniques: A systematic literature review based on the maturity of the techniques. IET Softw. 2018, 12, 365–378. [Google Scholar] [CrossRef]
- Dar, H.S. Reducing Ambiguity in Requirements Elicitation via Gamification. In Proceedings of the 2020 IEEE 28th International Requirements Engineering Conference (RE), Zurich, Switzerland, 31 August–4 September 2020; pp. 440–444. [Google Scholar]
- Poth, A.; Riel, A. Quality Requirements Elicitation by Ideation of Product Quality Risks with Design Thinking. In Proceedings of the 2020 IEEE 28th International Requirements Engineering Conference (RE), Zurich, Switzerland, 31 August–4 September 2020; pp. 238–249. [Google Scholar]
- Carrizo, D.; Dieste, O.; Juristo, N. Contextual attributes impacting the effectiveness of requirements elicitation Techniques: Mapping theoretical and empirical research. Inf. Softw. Technol. 2017, 92, 194–221. [Google Scholar] [CrossRef] [Green Version]
- Laplante, N.L.; Laplante, P.A.; Voas, J.M. Stakeholder Identification and Use Case Representation for Internet-of-Things Applications in Healthcare. IEEE Syst. J. 2018, 12, 1589–1597. [Google Scholar] [CrossRef] [PubMed]
- Ferraris, D.; Fernandez-Gago, C. TrUStAPIS: A trust requirements elicitation method for IoT. Int. J. Inf. Secur. 2019, 19, 111–127. [Google Scholar] [CrossRef]
- Zambonelli, F. Key abstractions for IoT-oriented software engineering. IEEE Softw. 2017, 34, 38–45. [Google Scholar] [CrossRef]
- Costa, B.; Pires, P.F.; Delicato, F.C. Specifying Functional Requirements and QoS Parameters for IoT Systems. In Proceedings of the 2017 IEEE 15th Intl Conf on Dependable, Autonomic and Secure Computing, 15th Intl Conf on Pervasive Intelligence and Computing, 3rd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; pp. 407–414. [Google Scholar]
- De Souza, B.P.; Motta, R.C.; Travassos, G.H. Towards the Description and Representation of Smartness in IoT Scenarios Specification. In Proceedings of the XXXIII Brazilian Symposium on Software Engineering, Salvador, Brazil, 23–27 September 2019; Association for Computing Machinery (ACM): New York, NY, USA, 2019; pp. 511–516. [Google Scholar]
- Hassan, R.; Qamar, F.; Hasan, M.K.; Aman, A.H.M.; Ahmed, A.S. Internet of Things and Its Applications: A Comprehensive Survey. Symmetry 2020, 12, 1674. [Google Scholar] [CrossRef]
- Tupa, J.; Simota, J.; Steiner, F. Aspects of Risk Management Implementation for Industry 4. Procedia Manuf. 2017, 11, 1223–1230. [Google Scholar] [CrossRef]
- Fernández, D.M.; Tießler, M.; Kalinowski, M.; Felderer, M.; Kuhrmann, M. On evidence-based risk management in requirements engineering. In International Conference on Software Quality; Springer: Cham, Switzerland, 2018; pp. 39–59. [Google Scholar]
- Crossland, B.; Bennett, P.; Ellis, A.; Farmer, F.; Gittus, J.; Godfrey, E.; Hambly, E.; Kletz, T.; Lees, F. Estimating Engineering Risk. Risk Manag. 2019, II, 1–22. [Google Scholar] [CrossRef]
- Barafort, B.; Mesquida, A.-L.; Mas, A. Integrating risk management in IT settings from ISO standards and management systems perspectives. Comput. Stand. Interfaces 2017, 54, 176–185. [Google Scholar] [CrossRef]
- Menezes, J.; Gusmão, C.; Moura, H. Risk factors in software development projects: A systematic literature review. Softw. Qual. J. 2018, 27, 1149–1174. [Google Scholar] [CrossRef]
- Hughes, D.L.; Rana, N.; Simintiras, A.C. The changing landscape of IS project failure: An examination of the key factors. J. Enterp. Inf. Manag. 2017, 30, 142–165. [Google Scholar] [CrossRef]
- Gupta, S.K.; Gunasekaran, A.; Antony, J.; Gupta, S.; Bag, S.; Roubaud, D. Systematic literature review of project failures: Current trends and scope for future research. Comput. Ind. Eng. 2019, 127, 274–285. [Google Scholar] [CrossRef]
- Stevenson, J.D. Quality assurance. In Project Management: A Reference for Professionals; Routledge: Boca Raton, FL, USA, 2017. [Google Scholar] [CrossRef]
- Femmer, H.; Fernández, D.M.; Wagner, S.; Eder, S. Rapid quality assurance with Requirements Smells. J. Syst. Softw. 2017, 123, 190–213. [Google Scholar] [CrossRef] [Green Version]
- Alshazly, A.; Elfatatry, A.M.; Abougabal, M.S. Detecting defects in software requirements specification. Alex. Eng. J. 2014, 53, 513–527. [Google Scholar] [CrossRef] [Green Version]
- Travassos, G.H. Software Defects: Stay Away from Them Do Inspections! In Proceedings of the 2014 9th International Conference on the Quality of Information and Communications Technology, Guimaraes, Portugal, 23–26 September 2014; pp. 1–7. [Google Scholar]
- Fahmideh, M.; Abbasi, A.A.; Behnaz, A.; Grundy, J.; Susilo, W. Software Engineering for Internet of Things. IEEE Trans. Softw. Eng. 2021. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy sets. In Fuzzy Sets, Fuzzy Logic, and Fuzzy Systems: Selected Papers by Lotfi a Zadeh; World Scientific: Singapore, 1996; pp. 394–432. [Google Scholar]
- Singh, H.; Gupta, M.M.; Meitzler, T.; Hou, Z.-G.; Garg, K.K.; Solo, A.M.G.; Zadeh, L.A. Real-Life Applications of Fuzzy Logic. Adv. Fuzzy Syst. 2013, 2013, 581879. [Google Scholar] [CrossRef]
- Ejegwa, P.A.; Akowe, S.O.; Otene, P.M.; Ikyule, J.M. An overview on intuitionistic fuzzy sets. Int. J. Sci. Technol. Res. 2014, 3, 142–145. [Google Scholar]
- Hayes, J. Building a requirement fault taxonomy: Experiences from a NASA verification and validation research project. In Proceedings of the 14th International Symposium on Software Reliability Engineering, ISSRE 2003, Denver, CO, USA, 17–20 November 2005; pp. 49–59. [Google Scholar]
- Chen, J.-C.; Huang, S.-J. An empirical analysis of the impact of software development problem factors on software maintainability. J. Syst. Softw. 2009, 82, 981–992. [Google Scholar] [CrossRef]
- Abdelmoez, W.; Ibrahim, M.; Omar, M.A.; Ammar, H.H. Sensitivity analysis of maintainability-based risk factors for software architectures. In Proceedings of the 2012 8th International Conference on Informatics and Systems (INFOS), Giza, Egypt, 14–16 May 2012; p. SE-29. [Google Scholar]
- Tatnall, A. Encyclopedia of Education and Information Technologies; Springer: Cham, Switzerland, 2012. [Google Scholar]
- Chandani, P.; Gupta, C. Towards Risk Based Effort Estimation: A Framework to Identify, Analyze, and Classify Risk for Early Identification at Requirement Engineering Phase. Int. J. Inf. Syst. Model. Des. 2018, 9, 54–71. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).