Abstract
Quantum correlations, especially time correlations, are crucial in ghost imaging for significantly reducing the background noise on the one hand while increasing the imaging resolution. Moreover, the time correlations serve as a critical reference, distinguishing between signal and noise, which in turn enable clear visualization of biological samples. Quantum imaging also addresses the challenge involved in imaging delicate biological structures with minimal photon exposure and sample damage. Here, we explore the recent progress in quantum correlation-based imaging, notably its impact on secure imaging and remote sensing protocols as well as on biological imaging. We also exploit the quantum characteristics of heralded single-photon sources (HSPS) combined with decoy state methods for secure imaging. This method uses Quantum Key Distribution (QKD) principles to reduce measurement uncertainties and protect data integrity. It is highly effective in low-photon number regimes for producing high-quality, noise-reduced images. The versatility of decoy state methods with WCSs (WCS) is also discussed, highlighting their suitability for scenarios requiring higher photon numbers. We emphasize the dual advantages of these techniques: improving image quality through noise reduction and enhancing data security with quantum encryption, suggesting significant potential for quantum imaging in various applications, from delicate biological imaging to secure quantum imaging and communication.
1. Introduction
The field of quantum information science is at the forefront of the ongoing quantum revolution with fundamental concepts such as the no-cloning theorem, quantum correlation, and the inability to perfectly discriminate non-orthogonal states [,,,]. The no-cloning theorem posits the impossibility of accurately replicating an unknown quantum state. The correlation between the quantum states of two particles, regardless of their physical separation maintains this link even when they are located at a significant distance. When seen in the classical world, two noninteracting particles, A and B, are separated by a long distance; the measurements are not dependent on each other. However, in the quantum world, the measurement of B could depend on the measurement of A. Such a property is a quantum property, and particles A and B are called entangled []. From a fundamental standpoint, achieving perfect discrimination of non-orthogonal states with a single measurement is unachievable.
Nonclassical sources such as the Spontaneous Parametric Down-Conversion (SPDC)-based entangled and squeezed states possess photon number correlations. This can be useful when one of the two beams is used as a probe beam and the other as the reference beam to detect modifications in the signal beam when the two are compared to extract information about an object’s absorption, transmission, or reflective properties, which is a method used in quantum imaging for quantum ghost imaging []. In correlation-based quantum imaging, the interaction with the object involves only one photon, but both photons of a correlated pair are detected. This process relies on SPDC to generate pairs of correlated photons. These pairs are then divided into the signal beam and the idler beam. This methodology utilizes the entanglement of two distinct particles, wherein their location and momentum attributes exhibit correlation []. When one particle’s properties are measured, it instantaneously provides information about the corresponding properties of the other particle, suggesting the definite properties of the unmeasured particle.
The amount of information obtained about a variable A through the measurement of another variable B is measured by mutual information I (A: B) in information theory. For classical correlations, I(x:y) = 1, and for perfect quantum correlation by an entangled source, it is given by I(x,y) = 2 []. Even when the entanglement is lost, the correlation could still exist in the SPDC source because the photon pairs have photon number correlations and are generated simultaneously. To obtain a glimpse of the diverse approaches being implemented, Figure 1 displays the various schemes generally followed for advanced quantum photonic imaging; all these approaches will be dealt with in detail in later sections.
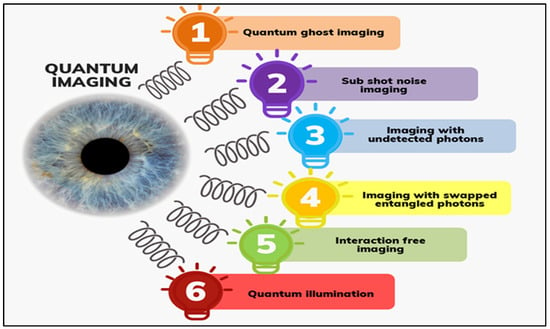
Figure 1.
Quantum imaging schemes.
In the domain of quantum imaging, the conventional understanding that entanglement was a prerequisite for ghost imaging was questioned with the successful use of classical light sources [,,,]. Further research led to the development and refinement of ghost imaging methodologies. A significant theoretical progression in the subject was the emergence of computational ghost imaging, which later paved the way for the practical realization of single-pixel cameras via structured light illumination [,]. Over the last decade, there were notable breakthroughs in quantum imaging. These advancements include sub-shot noise quantum imaging, quantum imaging with undetected photons, and quantum secure imaging that overcame the constraints imposed by traditional imaging approaches. These techniques are discussed in much detail in Section 3. Recent experimental research focused on the SPDC-based source to exploit the quantum correlations in them for biology and secure imaging applications [,,,,]. The improvements above solidified the importance of quantum imaging as a critical approach in modern imaging technology.
Quantum imaging experiments demonstrated enhancements in signal-to-noise ratio compared to traditional classical methods and reduced measurement uncertainty. These advancements are primarily attributed to sub-Poissonian statistics of the light source. In a light source exhibiting sub-Poissonian statistics, the variation (spread) in the number of detected photons is less than the mean of those occurrences []. However, the current challenge is translating the attributes of quantum imaging to real-world environments, which was a primary research focus in recent years. A unique quantum attribute is its behavior upon measurement: when an unknown quantum state is measured, it collapses, and the probability of accurately determining its actual state depends on the chosen measurement basis. This characteristic and sub-Poissonian statistics together give optimism for future real-world experiments to address challenges in the field of imaging sensitive objects and secure imaging. Furthermore, attention should be directed towards the wavelength of quantum light and real-time imaging. We aim to explore these topics, beginning with a general overview. When attempting to understand an experiment in the area of quantum optics and quantum-enhanced imaging [], it may be most beneficial to conceptualize the characteristics of the light field either in terms of its wave-like properties [] or as individual particles [,,].
Traditional imaging methods encounter constraints on the quality of their images. The restrictions mostly pertain to resolution and sensitivity since they are subject to the constraints imposed by the diffraction and shot noise limits. The restrictions result from the wave characteristics of light and the statistical variations in the arrival periods of photons. The diffraction limit is a constraint seen in imaging apparatus, such as microscopes and telescopes, arising from the wave characteristics shown by light. When light passes through an aperture or lens, it experiences diffraction, resulting in the dispersion of its propagation and creating a discernible pattern that may be seen. The diffraction phenomenon limits the attainable level of detail in the resolution of the imaging apparatus.
In practical terms, the diffraction limit establishes the minimum level of detail that the system may see. The equation often used to explain this phenomenon is , where represents the wavelength of the light utilized, and Numerical Aperture (NA) is the numerical aperture of the lens system []. This implies that two items positioned within proximity less than this threshold will not be distinguished. In contrast, shot noise is a kind of noise that is intrinsic to all imaging systems, arising from the discrete properties of light. Light is characterized by the presence of discrete units known as photons. Upon detection by devices such as camera sensors or photodetectors, the quantity of photons striking the detector exhibits fluctuations. The observed variation gives rise to shot noise. In imaging, shot noise limits the ability to distinguish delicate details, especially in reduced lighting conditions or when dealing with weak signals. The significance of shot noise decreases as the number of photons increases. However, when there is a small quantity of photons, shot noise may significantly affect the overall image quality. To address these constraints and augment the capabilities of imaging, researchers globally are actively involved in a persistent pursuit of better resolution and Signal-to-Noise Ratio (SNR) [,].
The principles of quantum information science present a diverse array of opportunities for manipulating quantum states to facilitate information processing and transmission. The quick advancement of our expertise drives the progressions in experimentally controlling and directing quantum dynamics across a wide range of systems. These entities span a wide range, including single photons, atoms, and ions, as well as isolated electron and nuclear spins [,,,,]. This extends to mesoscopic superconducting systems and nanomechanical devices [,]. Photons, considered as the fundamental constituents of light, are necessary in quantum information science due to their extraordinary characteristic of exhibiting little interaction with the surrounding environment. Photons possess a set of characteristics that make them very suitable for the purpose of conveying and encoding quantum information [,]. In addition, photons exhibit a range of degrees of freedom, including spatial, orbital angular momentum, frequency, polarization, and others, which may be used to encode and transport quantum information in a remarkably adaptable way. The development of commercial QKD systems is considered to be a fascinating application within the field of quantum information science [,]. These systems use the laws of quantum physics to provide unparalleled security for transmitting sensitive information [,,]. Quantum computing is an additional revolutionary field within quantum information science. Quantum computers can perform operations at an exponentially accelerated rate compared to conventional computers. Consequently, they provide a promising solution to issues, including factorization, database searches, and simulations of quantum systems, with unparalleled efficiency [,].
Furthermore, quantum sensing and imaging aims to attain exceptional levels of accuracy in measurements. This innovation has the potential to significantly transform other disciplines, particularly metrology, by empowering researchers and professionals to expand the limits of precise measurement [,]. Optical measurements using classical techniques are limited by uncertainties in scaling by a factor (N is the number of photons used to probe a system) and by power constraints (high power causes damage to the measured object). Quantum optical measurements, by utilizing non-classical sources such as squeezed or entangled states, can achieve maximum information at low power, improving the uncertainties in scaling to a factor of 1/N [,]. By incorporating quantum effects into traditional methods, it became possible to surpass the classical limitations [,]. Together, these achievements highlight the significant promise of quantum technologies in computing, communication, sensing, and imaging. These entities embody a combination of scientific interest, technological advancement, and the human inclination to go into the depths of understanding.
As we explore the domain of quantum imaging, a captivating fusion of quantum technologies arises called quantum secure imaging. This novel methodology incorporates QKD algorithms into the imaging procedure, introducing a change in thinking towards secure and tamper-resistant imaging. Using the fundamental laws of quantum physics, quantum secure imaging expands the limitations of our observational capabilities and guarantees the secrecy and integrity of the acquired pictures. In traditional imaging, the physical interaction involves the interaction between photons released by a light source and the object being seen. Nevertheless, this contact could disrupt the object or produce disruptions that compromise the precision of the imaging procedure. Quantum imaging systems provide the capacity to do interaction-free imaging, enabling the observation of objects without the need for direct contact. The versatility of wavelengths: Quantum imaging methods enable us to investigate things using wavelengths that closely correspond to their specific properties, augmenting our capacity to derive significant information. The ability to pick a variety of wavelengths enhances the efficacy of quantum imaging. The anti-jamming capabilities of the system are noteworthy. One notable characteristic of quantum imaging is its inherent resistance to the efforts at jamming. Conventional imaging systems are susceptible to interference and jamming, posing a threat to the integrity of the imaging procedure. Quantum secure imaging, which falls under the umbrella of quantum imaging, utilizes quantum encryption and communication methodologies to guarantee the confidentiality and authenticity of the imaging data. The anti-jamming characteristic of this feature provides a notable benefit in situations when the utmost importance is placed on ensuring the confidentiality and integrity of data.
The simultaneous presence of these benefits presents quantum imaging as a revolutionary technology with the potential to alter our methodology for perceiving and comprehending the environment fundamentally. The use of quantum secure imaging enhances the efficiency of imaging processes and guarantees the protection of data in a society that is becoming more linked and reliant on data. Absorption uncertainty is given by ; F is the Fano factor, and is the mean photon number []. Figure 2 illustrates a three-dimensional graph that represents the relation between the uncertainty in absorption of a material, the Fano factor, and the mean photon number. The absorption uncertainty is a critical statistic in photonics, particularly when dealing with the accuracy of measurements in biological samples or stealth imaging systems. The F values for mean photon number 0.3 are 0.7015, 0.714, and 0.85 for = 0.005, 0.05, and 0.5, respectively. Similarly, the F values for mean photon number 0.05 are 0.95025, 0.9525, and 0.975 for = 0.005, 0.05, and 0.5, respectively. SPDC-based single photon sources have the advantage of having sub-Poissonian statistics and quantum correlations. However, the photon production rate is three orders lower than the WCSs. When we have a lesser mean photon number, and if F is less than 1, such as the SPDC-based sub-Poissonian statistics source, then uncertainty is lower as compared to higher F values. This relationship is beneficial for applications that demand high levels of accuracy, such as biological imaging, where minimizing exposure to light is crucial to avoid any potential harm to the samples. Stealth imaging, which aims to evade detection by using low photon quantities, benefits from a lower Fano factor since it reduces statistical fluctuations in photon detection and enhances the system’s stealth characteristics.
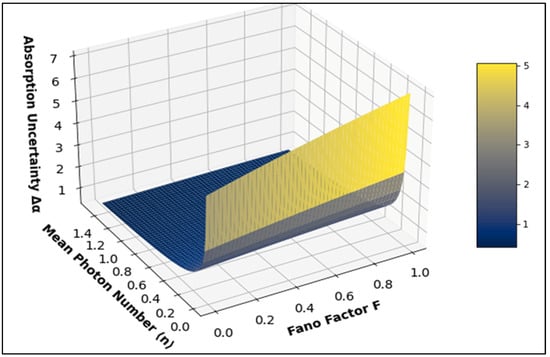
Figure 2.
3D representation of absorption uncertainty in relation to the Fano factor and mean photon number [].
In the present study, in Section 2, we first would start with the building blocks of quantum imaging involving quantum imaging protocol, quantum photonic sources, and detectors. This would clear the underlying principles, various approaches, and schemes involved in realizing quantum imaging. In the mean time, we will also highlight the capabilities within the field that would help us to solve the problems, especially of stealth imaging and biology, in the fields of interest to exploit the upper hand of quantum properties in the field of imaging and sensing. Later in Section 3, we explore in detail the advancements in various quantum-enhanced optical imaging techniques, particularly the progress in ghost imaging methods. The analysis aims to forecast the trajectory of quantum imaging advancements over the next decade, focusing on their implications for technical advancement.
2. Building Blocks of Quantum Optical Imaging
2.1. Quantum Optical Imaging Protocol
In general, quantum imaging experiments follow a structured sequence of steps, which is crucial for utilizing quantum mechanics principles to produce superior images with novel capabilities. As shown in Figure 3, the following is an overview of these typical procedures:
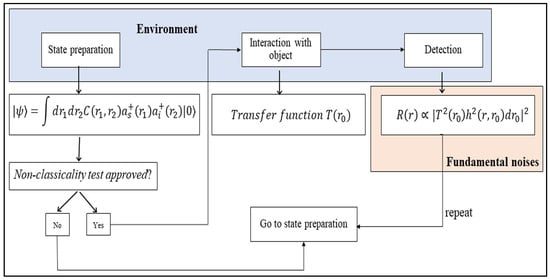
Figure 3.
Quantum optical imaging protocol (equations adopted from []).
- Generation of Non-Classical Quantum Light States: This initial step involves creating quantum light sources, for example, generating degenerate/nondegenerate photon pairs. A laser interacts with a nonlinear crystal to produce photon pairs with similar (degenerate) or different (nondegenerate) wavelengths. These entangled signals and idler photons are fundamental to quantum imaging. Techniques such as spatial light modulation may shape these photons’ wavefronts, aligning them with specific imaging needs.
- Object Illumination and Interaction: The object is illuminated with the “signal” photon, while the “idler” photon is used differently depending on the experiment. Some quantum imaging methods aim for minimal interaction with the object, aligning with specific imaging objectives.
- Detection and Image Reconstruction: Signal and idler photons are detected using sensitive single-photon detectors after illumination and interaction. The essence of quantum imaging lies in measuring the correlation between these detections, which reveals information about the object’s interaction with the signal photon.
2.2. Quantum Photonic Sources
Light sources in quantum imaging exhibit different photon number statistics, characterized by two key parameters: the average photon count and the variance. Classical light sources follow a super-Poissonian distribution, where the variance exceeds the mean photon count. In these cases, the photon count is highly variable. In contrast, non-classical light sources, a concept rooted in quantum optics, exhibit sub-Poissonian distribution, meaning that the variance is less than the mean photon count. Coherent states, commonly used to approximate laser radiation, occupy a unique position. They have Poissonian photon number statistics, where variance equals mean photon count [,]. Single-photon sources may be categorized into two types: deterministic and probabilistic. Deterministic sources, such as hexagonal boron nitride (hBN), provide single photons as wanted, ensuring reliability []. Probabilistic sources include both HSPS and WCS. Deterministic sources provide easy integration with current technology. However, their complex manufacturing process presents significant technical hurdles. Probabilistic sources, while they provide higher count rates, have efficiency challenges. This requires improvements in source purity and operational control. Table 1 summarizes various quantum states of light and highlights a few notable experiments.

Table 1.
Quantum states of light and respective a few notable experiments.
2.2.1. Quantum Entangled Photon Sources
Entangled states are a fundamental concept in quantum mechanics. They are multi-particle states that cannot be described as a simple product of individual states []. Entanglement can be created in various degrees of freedom, including polarization, time–energy, and position–momentum. In the context of quantum imaging, position–momentum entangled photons are particularly important. These photons can be described in momentum representation as , where represents the transverse component of the wave vector. The function is defined based on the paraxial approximation, and it is characterized by strong anti-correlation in momentum. Entangled photons found extensive applications in various domains, including quantum computing, quantum communication, quantum metrology, sensors, and quantum imaging [,,,,,].
Generation of quantum entanglement between two or more photons long posed challenges. Historically, the entanglement of photons was achieved via sequential emissions from distinct atoms [,]. However, these methods were intricate and soon overshadowed by advancements in nonlinear optics. Through nonlinear optics, photon pairs can be produced in materials with nonlinear attributes, notably in nonlinear crystals. The feasibility of this approach was supported both theoretically and experimentally, where a singular pump photon in conjunction with a nonlinear medium was shown to generate photon pairs [,,]. Nonlinear optical processes grew in importance because they enable the creation of non-classical light states, now commonly used in quantum sensing. The optical medium’s polarization response can be described by the equation. indicates the nth-order susceptibility of that medium []. Hence, materials with susceptibilities beyond the first order can facilitate interactions between optical fields of varying frequencies. The second and third-order non-linear interactions are typical, often called three- and four-wave mixing. Examples include second harmonic generation, sum frequency generation, and difference frequency generation [,,]. Three-wave mixing, or SPDC is facilitated in non-centrosymmetric crystals with a non-zero , where a single pump frequency divides into two lower frequencies. Centrosymmetric crystals and non-crystalline materials might possess a non-zero , but to ensure efficient non-linear processes, a high susceptibility coefficient is preferable; otherwise, significant pump power becomes a necessity.
In quantum optics, the SPDC process can be visualized as the destruction of a pump photon and the birth of a photon pair. This is interesting due to the quantum-linked behaviors of the produced photon pair. The dominant method for photon pair production is SPDC in second-order nonlinear crystals, such as bismuth borate (BBO), lithium borate (LBO), lithium niobate (LN), and potassium titanyl phosphate (KTP). During SPDC, a powerful pump field induces a nonlinear polarization in a material, leading to the emission of two lower-energy photons, termed the signal () and idler (). The energy conservation principle establishes that . To achieve efficient pair creation, constructive interference of these photons is crucial, necessitating the phase-matching condition: where . Unfortunately, due to the dispersion inherent to materials, this condition often is not satisfied, leading to destructive interference and non-generation of photon pairs over a distance δc = 2π/Δk. Anisotropic nonlinear crystals can adjust for this phase mismatch via Birefringent Phase Matching (BPM), wherein one photon from the SPDC process must have orthogonal polarization with the pump. This can be achieved in two ways: type-I BPM, where signal and idler are co-polarized, and type-II BPM, where only the idler is co-polarized with the pump. In the context of Type 0 SPDC, it is observed that the signal and idler photons exhibit identical polarization characteristics as the pump photon. The phenomenon is distinguished by the polarization of photons, which may be either horizontally or vertically aligned. In the Type 1 SPDC process, the signal and idler photons are generated with identical polarization states. However, it is essential to note that this polarization state is perpendicular to the pump photon. For instance, in the scenario where the pump photon exhibits horizontal polarization, both the signal and idler photons will adopt vertical polarization. Type 2 SPDC is characterized by producing signal and idler photons with orthogonal polarizations. For example, if a single photon exhibits horizontal polarization, its counterpart will exhibit vertical polarization [].
Collinear configurations, where all the fields align along a single axis, are preferable as they optimize spatial overlap and enhance SPDC efficacy. However, Poynting vector walk-off can restrict the useful length of crystals in BPM. An alternative solution is Quasi-phase Matching (QPM) using poled nonlinear crystals, such as ppLN or ppKTP, periodically. Using QPM in a non-critical phase-matching setup can efficiently utilize longer nonlinear crystals and waveguide structures. For brevity, Figure 4 depicts two types of nonlinear optical processes known as parametric down-conversion. In this quantum optics process, a pump photon is converted into a pair of signal and idler photons within a nonlinear crystal.
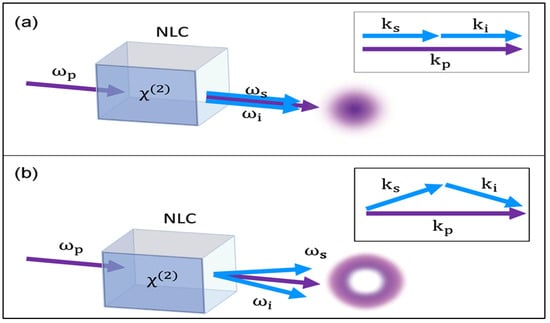
Figure 4.
(a) Collinear case, (b) non-collinear case [].
2.2.2. Squeezed States
Squeezed states are a specific class of quantum states that exhibit unique properties, especially in the context of photon statistics. The electric field operator in quantum optics can be expressed in terms of quadrature operators, namely and . These quadrature operators are defined as and where and are the creation and annihilation operators [].
Squeezed states are characterized by unequal variances in these quadrature operators V(Xi) < 1/4, for i = 1 or 2. The process of squeezing involves the application of a squeezing operator to a quantum state. This operator creates or destroys two photons at a time and is defined as [,]. The squeezing parameter quantifies the degree of squeezing. When > 0, amplitude squeezing occurs, leading to a reduction in amplitude fluctuations. This type of squeezing is associated with sub-Poissonian statistics. Conversely, when < 0, phase squeezing takes place, causing an increase in amplitude fluctuations and super-Poissonian statistics. A squeezed coherent state is created by applying both the displacement operator and the squeezing operator to the vacuum state. The displacement operator is defined as [,,].
The generation of squeezed states typically involves the use of a degenerate parametric amplifier, which consists of a second-order nonlinear crystal pumped by a powerful laser beam at an angular frequency A weak signal, often considered as the vacuum state, is introduced into the system. The nonlinear crystal then mixes the signal and pump, resulting in the production of an idler beam at . During degenerate parametric amplification, one of the quadratures of the resulting idler beam is amplified while the other is unamplified. The specific outcome depends on the relative phase between the signal and pump. Figure 5 illustrates key quantum light states in phase space.
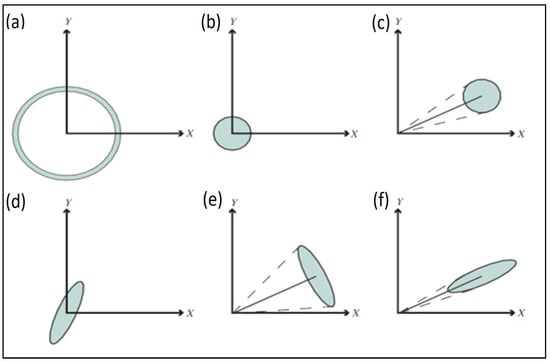
Figure 5.
Depictions of key quantum light states in phase space, each marked by dashed lines to represent the inherent phase uncertainty. The sections include: (a) the Fock state, (b) the vacuum state, (c) the coherent state, (d) the squeezed vacuum state, (e) the amplitude squeezed state, and (f) the phase squeezed state [].
Squeezed light states offer enhanced resolution compared to coherent infrared light. It is a powerful tool for overcoming the Rayleigh limit, reducing intrinsic noise in conventional super-resolution imaging techniques. Squeezed light was applied in various experiments, including monitoring the movement of particles within biological specimens, achieving significant enhancements in resolution. The system’s resolution obtained using squeezed light is approximately 1.43 times higher than coherent infrared light []. Lastly, it is important to highlight the application of squeezed light to overcome the Rayleigh limit, which reduces inherent noise in light that constrains conventional super-resolution methods. A total of 6 dB amplitude squeezed light was integrated with an imaging setup to monitor the movement of particles within a biological specimen []. This resulted in a 42 percent improvement over the standard quantum limit. The identical approach was subsequently utilized to implement photonic force microscopy, achieving a 14 percent enhancement in resolution compared to experiments conducted with coherent light [].
2.2.3. Weak Coherent Sources of Light
As an alternative to complex single-photon sources, using weak coherent laser pulses presents a simplified and efficient method for generating light at high repetition rates. These pulses are particularly appealing due to their straightforward production and capability to enable high-rate secure communication. These systems can operate at ambient room temperatures, negating the need for intricate cryogenic setups. Furthermore, weak coherent pulses afford the flexibility to employ a range of encoding variables beyond polarization, such as frequency, time bin, or orbital angular momentum. For practical use in secure communications, these pulses must be precisely identical across any characteristic not involved in information encoding, ensuring that potential side channels are mitigated. The main challenge with these pulses is their susceptibility to multiphoton occurrences, which threatens the confidentiality of communication. Mathematically, a coherent state with an average photon number and a phase is expressed through a series where the probability of obtaining n photons at a given time follows the Poisson distribution. Excess photons could escape from the pulse during transit, leading to vulnerabilities.
The provided Figure 6 highlights two distinct parts, (a) and (b), each illustrating various aspects of photon statistics in quantum optics.
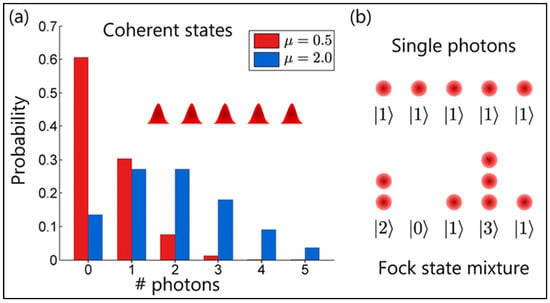
Figure 6.
(a) The photon count within weak coherent pulses follows a specific pattern, where the likelihood of any given photon number is determined by its distribution. (b) To reduce the chance of having multiple photons in the same pulse, the average number of photons per pulse is typically set below one [].
(a) Coherent States:
Part (a) presents a histogram comparing the probability distributions of photon numbers within coherent states of light for two different average photon numbers, denoted by . Coherent states are a type of quantum state of the electromagnetic field most closely resembling classical electromagnetic waves. The red bars represent a coherent state with a lower average photon number ( = 0.5), and the blue bars correspond to a coherent state with a higher average photon number ( = 2.0). The x-axis represents the number of photons, and the y-axis represents the probability of finding that number of photons in the state. As depicted, the probability distribution spreads out with an increase in the average photon number, indicating a higher probability of finding states with more photons.
(b) Single Photons and Fock State Mixture:
Part (b) displays two illustrations: the top shows an array of single photons, each in a quantum state |1⟩ indicating a single-photon state. This is ideal for quantum communication as each photon can securely carry a small amount of information. The bottom illustration shows a Fock state mixture, where each position may have a different number of photons, indicated by the states |2⟩, |0⟩, |1⟩, |3⟩, and |1⟩. A Fock state is a quantum state with a defined number of photons. The mixture of Fock states represents a more complex quantum state where multiple photons may be present at various positions, which is less ideal for secure communication due to the possibility of information leakage if multiple photons are detected simultaneously.
The equation describes that the photon number distribution for a WCS is given by , and a SPDC-based HSPS is given by ; is the mean photon number, and k is number of photons. represents the efficiency at the source end, is the dark count rate for the detectors, and is the post-selected probability given by []. Figure 7 compares the performance of HSPS and WCS in generating single photons. In scenarios where the mean photon number is low, HSPS shows a significantly higher likelihood of emitting single photons and demonstrates sub-Poissonian statistics, indicating that its variance in photon numbers is less than the mean. However, as the mean photon number approaches 0.6, the likelihood of emitting single photons from both sources converges, as shown by the green and yellow dotted curves in Figure 7b. This convergence is crucial for applications such as QKD, where the dominance of single-photon events over multi-photon events is critical to ensuring security. According to the data presented in Figure 7, for HSPS, maintaining the mean photon number at a maximum of around 0.2 is advised to reduce multi-photon events, whereas, for WCS, the mean photon number can be increased to approximately 1 to achieve a similar reduction in multi-photon occurrences.
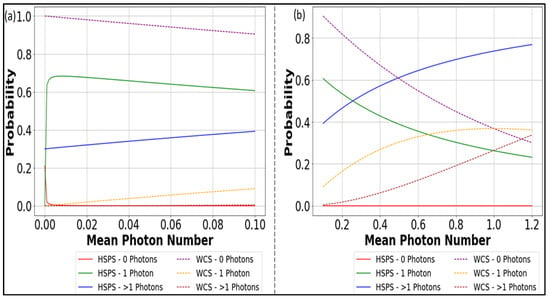
Figure 7.
Quantitative Analysis of Single-Photon Emissions from Heralded and WCSs: Implications for Secure QKD for (a) mean photon number 0 to 0.1, and (b) mean photon number > 0.1 to 1 [].
2.3. Qunatum Key Distribution (QKD)
In recent years, quantum computing garnered significant attention due to its potential to revolutionize computational capabilities. Quantum computers harness the unique properties of quantum mechanics to solve complex problems that are highly time-consuming to classical computers. At the heart of this technology are quantum bits, or qubits, which can exist in superpositions of states, allowing quantum computers to perform multiple calculations simultaneously. This quantum advantage holds tremendous promise in various domains, including cryptography, drug discovery, and optimization. For instance, algorithms such as Shor’s can efficiently factor large numbers, challenging classical cryptographic systems []. To realize the potential of quantum computers, specific criteria, as outlined by DiVincenzo, must be met []. Superconducting wires were early contenders in quantum computing, offering fast gate speeds and high fidelity []. However, they require extremely cold conditions and have short-lived coherence times. On the other hand, trapped ions boast high gate fidelity and longer coherence times, but need ultra-high vacuum conditions and precise laser setups. These systems are complex to scale and have slower gate operations []. Photons are promising candidates as qubits because of their rapid gate operations and impressive fidelities without deep cooling or ultra-high vacuum conditions. However, they have limitations: every program needs a unique chip, and photon loss can introduce noise. Additionally, 2-qubit operations are challenging with photons unless neutral atoms are used. While offering long coherence times and no need for external cooling, these atoms still come with challenges, such as the necessity for ultrahigh vacuums and scalability issues with lasers [,,,]. Quantum dots, benefiting from existing semiconductor tech, display strong gate fidelity and speeds. However, they come with the need for cryogenic conditions and face problems such as interference and crosstalk. Keeping DiVincenzo’s criteria, which stresses isolated and scalable qubit systems, each platform has strengths and challenges. For instance, while photons are great for transmitting quantum data, spin qubits are better suited for storing it, and superconducting qubits excel in processing. The crucial role photons play in quantum computing is worth highlighting. Their potential, especially in threatening classical cryptographic systems by potentially breaking traditional encryption, is immense as quantum technology progresses.
The Alice, Bob, and Eve framework is a common scenario in cryptography. Alice and Bob aim to establish a secure communication channel while facing the challenge of Eve, an eavesdropper who seeks to intercept and gain unauthorized access to their communication. This framework underscores the importance of achieving perfect secrecy, where the encryption key should be if the message is only used once, a concept known as the one-time pad []. This approach maximizes information entropy, making it extremely difficult for attackers such as Eve to decipher the key. QKD is a method employed to generate secure encryption keys between Alice and Bob using quantum channels. QKD capitalizes on the unique properties of quantum mechanics, such as the indivisibility of photons and the no-cloning theorem, to detect any attempts by eavesdroppers to compromise the security of communication. However, the security of QKD relies on specific assumptions. The effectiveness of QKD protocols is contingent on several critical assumptions, including trust between Alice and Bob, the absence of data loss in the quantum channel, secure random number generation, and the assurance of security in their physical locations and the devices they use. These assumptions are fundamental to ensuring the robustness of QKD in practice. Furthermore, there is an intriguing application of utilizing quantum states of light, modulated based on polarization, to detect intelligent jamming attacks in active imaging systems. In this context, quantum properties are harnessed to encode information, and any attempts by adversaries to manipulate or interfere with the quantum states of photons can be monitored. This innovative concept extends the principles of QKD to enhance security in imaging applications, particularly in scenarios where data integrity is of utmost importance.
If we examine a two-dimensional Hilbert space, the entities within it are referred to as quantum states, often referred to as qubits. Classical bits are denoted by: |0⟩ = and |1⟩ = then quantum bits, which are a superposition of classical bits, are denoted by the equation |ψ⟩ = α|0⟩ + β|1⟩. Standard basis is represented as|0⟩ and |1⟩, whereas Hadamard basis is represented by |+⟩ = |0⟩+|1⟩/2 and |-⟩ = |0⟩-|1⟩/2 []. Table 2 illustrates the encoding and decoding in the BB84 protocol, with X representing the Hadamard basis and Z representing the standard basis.

Table 2.
Encoding and Decoding in BB84 protocol (X: Hadamard basis, Z: Standard basis) [].
When Alice encodes her bits on a Hadamard basis, and Bob performs measurements on a Hadamard basis, the process results in deterministic key decoding. However, when Bob measures on the Standard basis, there is a 0.5 probability of correctly identifying the encoded bit. To address this, Alice and Bob must employ a classical communication channel to convey the selected measurement basis. This ensures that they maintain the generated keys on the same basis and discard keys if the bases used are different.
For a better understanding, the steps that are typically involved in a QKD protocol, such as BB84, are given below:
- Bit Selection by Alice: Alice randomly generates a bit, which can be either 0 or 1, using a random number generator.
- Basis Choice by Alice: she then randomly picks one of two quantum bases—the Standard basis or the Hadamard basis—for encoding her bit.
- Bit Encoding and Transmission: Alice encodes her bit in the selected basis into a qubit and sends it to Bob via a quantum channel.
- Basis Selection by Bob: Bob, just as Alice, randomly chooses either the Standard or Hadamard basis using a random generator.
- Qubit Measurement by Bob: upon receiving the qubit, Bob measures it using the basis he selected.
- Repetition of the Process: Alice and Bob repeat the above steps multiple times to generate a series of bits and corresponding bases.
- Basis Disclosure over Classical Channel: after enough bits were exchanged, Alice and Bob share the bases they used for each bit over a classical communication channel.
- Bit Filtering Based on Basis Match: They discard any bits whose chosen bases do not match, retaining only the bits encoded and decoded on the same basis. This ensures that the remaining bits are more likely identical between Alice and Bob.
- Eavesdropping Detection and Post-Processing: Alice and Bob compare a sample of their bits over a public channel to detect potential eavesdropping. If the match is within an acceptable limit, they proceed with post-processing steps, such as error correction and privacy amplification, to secure communication. In the BB84 QKD (QKD) protocol, a Quantum Bit Error Rate (QBER) exceeding 11% typically indicates a high likelihood of eavesdropping, as this threshold is the upper limit for maintaining secure communication.
In QKD, the unambiguous state discrimination attack occurs when an eavesdropper (Eve) can identify the states transmitted by Alice. Eve leverages the inherent losses in the communication channel to her advantage [,]. When Eve successfully discriminates the states, she sends either single photon or multiphoton states; otherwise, she sends vacuum states. For non-orthogonal states (0 and 45 degrees), the probability of discrimination is 0.293. A specific condition must be met for security against such attacks in scenarios involving weak coherent states: the product of the channel’s transmission efficiency and Bob’s detection efficiency should equal 0.293. When the Mean Photon Number (MPN) is set to 1, there is a significant chance of single-photon emissions, but this also increases the likelihood of emitting multiple photons simultaneously. As the MPN increases beyond this point, the probability of single-photon emissions diminishes. On the other hand, when the MPN is reduced to 0.1, the risk of multiphoton emissions drops, which is beneficial for security as it hampers an eavesdropper’s ability to gain information about the cryptographic key. Additionally, with an MPN of 0.1, the probability of single-photon emissions is around 9%, which remains practical for generating the key. In the context of Photon Number Splitting (PNS) attacks in QKD, reducing the MPN is a crucial defensive strategy. In PNS attacks, an eavesdropper exploits multiphoton emissions: they can split these photons, keeping one for themselves and forwarding the rest to the intended recipient, thereby gaining partial information about the key without being detected. By minimizing multiphoton emissions, which happen at lower MPNs, the vulnerability to PNS attacks is significantly reduced, enhancing the overall security of the QKD system [,,].
The decoy state method was proposed by Hwang [], and security proofs were provided by Hoi Kwong Lo []. The technique is useful in practical situations when the source is not an ideal single-photon source, but can have multiple photons emitted with the same information. The decoy state protocol is a technique used in QKD to improve the security of information transmitted. In QKD, two parties, Alice and Bob, exchange quantum states to create a secure key. QKD’s security is based on quantum mechanics principles, which prevent eavesdropping without detection. On the other hand, attackers can use a technique known as PNS to intercept a photon from the transmitted state and store it for later use []. They then allow the remaining photons to continue to the receiver, avoiding detecting the eavesdropper’s actions. The attacker can then measure the stored photons to learn about the transmitted key while remaining undetected. To prevent this type of attack, the decoy state protocol is used. In this protocol, Alice sends the key states to Bob and a few “decoy states”, which are randomly chosen states with known photon numbers. Alice can then estimate the photon–number distribution of the transmitted states by measuring the decoy states. By comparing the measured photon–number distribution with the expected distribution, Alice and Bob can detect the presence of an eavesdropper. If the measured distribution differs significantly from the expected distribution, an eavesdropper will intercept some of the photons, and the key exchange will be aborted. The decoy state protocol is a method used to detect and prevent photon–number-splitting attacks in QKD. It enhances the security of the key exchange by allowing Alice and Bob to detect the presence of an eavesdropper [].
The decoy state method enhances security by allowing for a more accurate estimation of single-photon components in the transmission, which are inherently more secure than multi-photon components. The final key is derived as an XOR of the secure single-photon key () and the less secure multi-photon key (), resulting in an overall secure key []. Table 3 provides an overview of experiments conducted using the BB84 protocol in QKD (QKD). In the first experiment with optical fiber as the channel, the BB84 protocol was tested over 50 km, achieving a Quantum Bit Error Rate (QBER) of 2% and a secure key rate of 0.5 Kbits/s. The subsequent two experiments utilized the BB84 protocol with the addition of decoy states and were carried out in free space channels. In the 144 km experiment, the QBER rose to 6.48%, but the secure key rate was between 12.8 and 42 bps. Impressively, even at a much longer distance of 1200 km, the QBER was maintained between 1 and 3%, and the secure key rate was as high as 1.1 Kbps. This highlights the potential of the BB84 + decoy protocol for long-distance QKD in free-space channels.

Table 3.
Experiments in QKD with BB84 protocol.
2.4. Quantum Photonic Detectors
In quantum imaging, detectors play a pivotal role in capturing and recording visual information, akin to how the human eye perceives natural scenes. The eye, our primary organ for real-time perception, and cameras, our artificial optical instruments, share several fundamental components and functions []. The eye’s retina, a light-sensitive layer at the back, comprises multiple layers responsible for distinct functions. Cones and rods in the retina transform incoming light signals into neural signals. Cones excel at distinguishing colors in well-lit conditions, while rods are sensitive to faint light, motion, and variations in intensity. The fovea, a central indentation in the retina, is densely populated with cones, making it the focal point for detailed observation of objects. Digital cameras replicate some aspects of the human visual system. They employ lenses, apertures, image planes, and light sensors to record visual information. In digital cameras, photo sites, which are small light-sensitive cavities, serve as the analogs to the photoreceptor cells in the retina. These photo sites measure the strength of electrical signals, corresponding to the number of photons captured. A commonly used image sensor in cameras is the Charged Coupled Device (CCD). In CCDs, electrodes are grouped in threes, allowing the application of three distinct voltages. By manipulating these voltages, electrons generated by incoming photons can be collected and converted into a voltage signal at the edge of the silicon sheet [,].
2.4.1. Characteristics of Quantum Photonic Detectors
When evaluating detectors for quantum imaging applications, several key characteristics come into play [] as given below:
- Spectral Range: detectors must have high efficiency within the specific wavelength range of interest for quantum imaging.
- Dead Time: dead time represents the recovery period the detector requires after absorbing a photon before registering counts again.
- Dark Count Rate (DCR): DCR refers to the false count rate originating from various sources, including material properties of the detector, biasing conditions, or external noise. Low values for both dead time and DCR are crucial for accurate photon counting.
- Timing Jitter: Timing jitter quantifies the variation in the time interval between the absorption of photons and the generation of an electrical pulse from the detector. Minimal timing jitter is desirable for precise timing measurements.
- Ability to Resolve Photon Number: Conventional detectors often trigger the same response for single-photon and multi-photon pulses. Advanced detection methods, such as arrays of detectors or specialized detectors, are required to distinguish between these cases.
- Detection Efficiency: Detection efficiency is the probability of recording a count when a photon arrives at the detector. High detection efficiency is a fundamental requirement for sensitive photon detection.
Figure 8 shows the comparison of photon detection probabilities. The x-axis of the graph represents the wavelength of the light in nanometers, ranging from 300 nm to 1100 nm, covering the ultraviolet, visible, and near-infrared portions of the electromagnetic spectrum. The y-axis represents the Photon Detection Probabilities (PDP) in percentage, indicating the efficiency of each photodetector at each wavelength. The graph shows that each detector has its characteristic response curve, with varying sensitivity levels at different wavelengths. For instance, some detectors are more efficient in the visible spectrum, while others perform better in the near-infrared range. Figure 8 provides essential information for selecting a photodetector for a specific application, considering the required sensitivity and wavelength range.
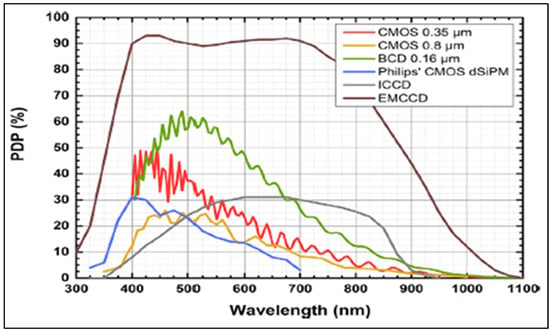
Figure 8.
Comparison of Photon Detection Probabilities (PDPs) [].
2.4.2. Important Detectors Used for Quantum Photonic Imaging Applications
Several types of detectors are commonly used in quantum imaging, where each one has its own set of characteristics, advantages and limitations.
- Intensified CCD (ICCD): Intensified CCD cameras (ICCDs) feature an image intensifier that boosts external photons that hit the intensifier through impact ionization. This results in effective signal enhancement and the ability to regulate exposure time []. ICCDs possess the potential for single photon detection, with current detection efficiencies hovering around 50 percent and maintaining minimal dark counts. Notably, the intensifier can be briefly gated, lasting durations in the picosecond range, making these cameras particularly suitable for photon correlation studies []. It is important to note that ICCD cameras only amplify external photons that reach the intensifier. This ensures low-noise signal amplification and nanosecond-level control over exposure to eliminate undesired light interference.
- Electron-Multiplying Charge-Coupled Devices (EMCCDs): Electron-Multiplying Charge-Coupled Devices (EMCCDs) amplify signals after a CCD detects light. They utilize a register specifically for electron multiplication, which boosts the detected electronic signal [,]. Regarding detection efficiency, EMCCDs outperform ICCDs and have reduced readout noise []. However, their signal-to-noise ratio (SNR) often falls short compared to ICCDs because of the amplified dark counts. EMCCDs necessitate cooling and are expensive.
- Single-Photon Avalanche Diodes (SPADs): SPADs are semiconductors that generate electron-hole pairs when photons strike a semiconductor material []. These devices work under reverse bias and use avalanche multiplication to boost their photoelectric response. They can achieve efficiencies close to 80 percent in the visible spectrum, but this drops to about 20 percent in the infrared spectrum. It is essential to understand that these detectors cannot precisely measure the number of photons. One of the intriguing features is their ability to form two-dimensional arrays of SPADs, such as 16 × 16 macro pixels, 64 × 64 pixels, and 256 × 256 pixels []. Each pixel acts as an individual SPAD in these configurations, which is especially advantageous for coincidence imaging. However, because of the adjacent electronic components, the fill factor (9.6, 26.5, and 61, respectively, for pixels above) is not optimal, leading to a reduction in the overall detection efficiency. A promising solution to this problem could be using microlens arrays [,,,,].
Superconducting Nanowire Single-Photon Detectors (SNSPDs): Superconducting nanowire Single-Photon Detectors (SNSPDs) depend on superconducting characteristics []. When a photon strikes the nanowire, it creates a localized temperature spike, increasing resistance at that spot. This change results in the superconducting material, primarily NbN, transitioning into a resistive state, with resistance surging to about 50 kiloohms. By pairing this with a lower-resistance impedance (close to 50 ohms), the ensuing current takes the route of least resistance. This mechanism allows for the identification of individual photons. These SNSPDs operate at temperatures near 2.1 Kelvin and show high efficiency in both the Visible (VIS) and Near-Infrared (NIR) spectrum, often surpassing 80 percent []. Table 4 provides a comparison of the parameters of various detectors. Higher efficiency values of detectors are in the visible region and lower in the IR region.

Table 4.
Comparison of the parameters of detectors.
In high-performance imaging systems such as EMCCDs and ICCDs, a critical aspect of noise management involves the Noise Factor (F) associated with the amplification process. For EMCCDs, this factor is typically or approximately 1.41, while for ICCDs it varies between 1.6 and 3.5, depending on the intensifier tube used. In deep-cooled, low-noise operational regimes with negligible dark and spurious noise, the Signal-to-Noise Ratio (SNR) can be simplified, focusing primarily on the readout noise () and the actual photon count. The SNR for these systems can be expressed as
where QE represents quantum efficiency, and P is the photon count. Notably, by increasing the Gain (G), the term involving the read-out noise becomes less significant compared to the intrinsic shot noise of the signal. This reduction in the relative impact of readout noise enhances the ultra-sensitive detection capability of these devices, making them particularly effective in low-light conditions and applications requiring high accuracy and precision [].
2.4.3. Computational Ghost Imaging
Computational ghost imaging relies on a fundamentally different process from traditional imaging. Instead of capturing an image through lenses, this technique employs a spatial light modulator to modulate a light source, which is then reflected off the target. The reflected light is captured not by a typical array of pixels, but by a single-pixel detector (SPAD/SNSPD). The experiment involves several key steps: [,]
- a.
- Modulation of Light: The light source is modulated using a Spatial Light Modulator (SLM). This modulation typically involves presetting intensity patterns of speckles.
- b.
- Reflection from the Target: The modulated light interacts with the target object. The properties of the object affect how this light is reflected.
- c.
- Detection: The reflected light is captured by a single-pixel detector. Unlike traditional detectors, which capture a complete image, this detector measures the total light intensity over time.
The core of computational ghost imaging lies in its unique way of image reconstruction:
- (i)
- Intensity Pattern Modulation: a Digital Micromirror Device (DMD) modulates numerous intensity patterns, denoted as where i ranges from 1 to N, the total number of patterns.
- (ii)
- Single-Photon Detection: Single-photon detectors measure the counts (denoted as ) corresponding to each pattern. These counts reflect the interaction of each pattern with the object.
- (iii)
- Image Reconstruction: The final image O(x,y) of the object is computed by summing the weighted intensities of each pattern. The weights are derived from the count and adjusted by the mean value of counts and intensities.
The reconstruction of the image is governed by a mathematical formula that integrates the measured counts and the corresponding intensity patterns. This involves calculating the mean values and correlating them with the transmission function of the object, symbolized as T(x,y).
where the mean value is
3. Quantum Imaging Schemes
In the introduction, we schematically showed in Figure 1 the several important schemes that were explored for quantum optical imaging and remote sensing, depending on diverse applications being reported. In this section we go through the state of art quantum optical imaging approaches based on their recent technological advancements.
3.1. Quantum Ghost and Swapped Entanglement Based Imaging
Quantum ghost imaging is a quantum technique that captures images of objects using photons that never interacted with the object itself. As shown in Figure 9, this method relies on the spatial correlations between pairs of photons generated through SPDC within a nonlinear medium. While the idler photons interact with the object and are detected by a non-spatially resolving (bucket) detector, the signal photons are detected by an imaging detector [,]. Neither the bucket nor the spatially resolving detector alone contains sufficient information to reconstruct the object’s image. The bucket detector detects all idler photons passing by the object without spatial resolution, and the spatially resolving detector merely measures the position of incident signal photons without object-specific information. However, by exploiting the correlation between these datasets and integrating numerous acquired events, it becomes possible to reconstruct an image of the object [,].
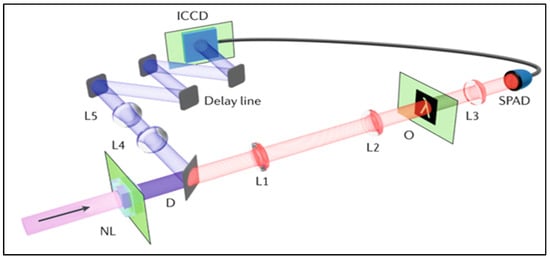
Figure 9.
Non-degenerate quantum ghost imaging uses signal and idler beams from a barium borate crystal. The infrared idler photon interacts with the object and is detected by SPAD. Signal photons are detected by an intensified ICCD camera triggered by SPAD photon arrival [].
The image reconstruction formula is given by . The scheme is robust to scattering and phase distortions, and propagation direction of photons scrambled after the sample does not make any difference to the bucket detector. The true detection events are given by ; efficiency of idler (signal) channel, P is the pairs production rate, and is the detection window. is the background counts and is the background count rate. True coincidence is given by ; probability of joint detection by two single photon detection. Accidental counts ; for the case when signal background rate is dominant ; and the quantum advantage is given by [].
The Figure 10 displays four panels labeled (a), (b), (c), and (d), demonstrating the effect of photon numbers on the imaging of a wasp wing. Panel (a) shows a weakly absorbing wasp wing captured with 40,419 detected photons; it appears dark and lacks detail. Panel (b) presents the reconstructed image from (a), showing improved clarity. Panels (c) and (d) represent the same wasp wing with a more significant number of photons used for imaging and its associated reconstruction, respectively. These latter images exhibit even more detail, highlighting the incremental improvement in image quality with increased photon numbers. The scale bar provided is 400 µm, which aids in understanding the actual size of the structures shown in the images. The concept of regularization is implied here, balancing fidelity of the recorded data with a solution that adheres to the sparsity condition—a method used to enhance these images.
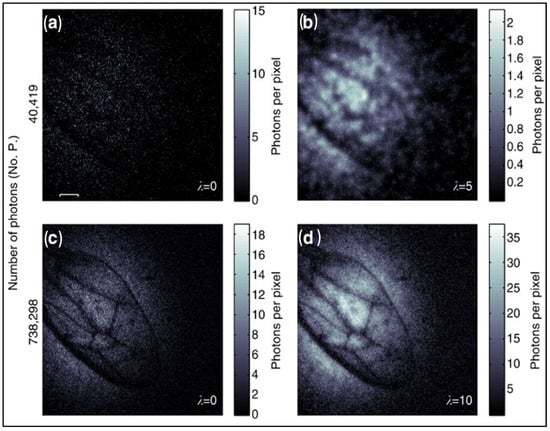
Figure 10.
Wasp wings imaged by ghost image method (a) Weakly absorbing wing with 40,419 detected photons; dark and lacks detail. (b) Reconstructed image from (a) with improved clarity. (c) The same wing with more photons is used for imaging. (d) Reconstructed image from (c) [].
Entanglement swapping is another intriguing phenomenon in which correlations are generated between particles that never directly interacted with each other. It involves taking two pairs of entangled photons and performing a Bell state measurement between particles in separate pairs, resulting in the entanglement of previously unentangled particles. This effect has applications in transmitting information over long distances through a quantum network []. A novel approach termed Quantum Secure Ghost Imaging unites temporal quantum ghost imaging with a security assessment []; by leveraging the unique properties of entangled photon pairs, the scheme can identify potential eavesdropping during the imaging procedure, thus safeguarding the integrity of object information. The imaging of two-dimensional patterns line by line over an optical fiber span of 50 km was achieved. Current research emphasis pivots towards the real-time imaging of objects in free space. This shift towards real-time free space imaging opens exciting possibilities for applying quantum imaging technologies in various fields, from remote sensing to secure communications.
3.2. Sub-Shot Noise Based Quantum Imaging (SSNQI)
Using paired photons provides a unique method for enhancing measurement accuracy by leveraging the correlation between the photons. In this technique, one photon from the pair interacts with a sample, while its twin acts as a reference to pinpoint quantum noise. This enables the differentiation and removal of random noise in the photon examining of the sample. Classical measurement methods also use a similar differential approach but only correlate fluctuations surpassing the Poissonian level, such as thermal noise. Thus, they are unable to address and remove shot noise. What sets photon pairs apart is their capability to achieve a reduction below the shot noise level, thanks to the non-classical correlations in their photon numbers.
In the depicted setup in Figure 11, both the signal and idler photons are directed and focused using a lens. An object is illuminated by a down-conversion mode comprising the correlated signal and idler photons. A CCD camera captures the photons transmitted in this mode. Concurrently, this CCD array also registers the photons from the second mode, which contains the correlated counterparts of the signal and idler photons. A specific procedure subtracts correlated pixels in the CCD array to refine the data and augment image quality. This process capitalizes on the intense correlation between the signal and idler modes, enhancing the image’s contrast and significantly reducing noise. Consequently, this method facilitates ghost imaging of superior quality, with heightened clarity and minimized disruption [].
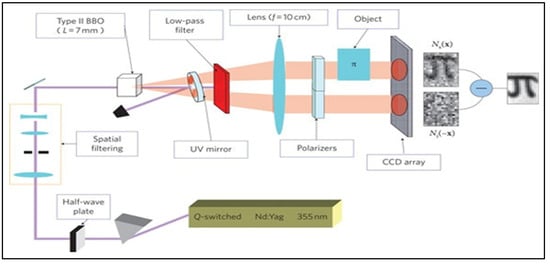
Figure 11.
Subshot noise imaging involves splitting signal and idler photons into two beams. One beam passes through the object, and both are detected by a CCD camera [].
is the variance of the photon number difference normalized to the sum of mean numbers.
= 1 − ; being the efficiency of detectors, when , and for classical case.
Improvements are as follows:
The Figure 12 presents two examples of images using different imaging methods: On the left, the SSNQI images are displayed, which are created by removing the noise that is quantum correlated. In the center, the differential classical images are shown, where the difference between two classical images is taken to reduce noise. On the right are the direct classical images, which are captured directly without any noise reduction techniques applied. The images are processed to have a pixel size of 480 μm squared by grouping the actual pixels of the CCD camera, a method known as hardware binning. This process ensures that each pixel is larger than the coherence area, which helps minimize electronic noise. In both image sets, the average photon count per pixel is approximately 7000. The parameter allows for calculating the noise reduction factor for classical differential imaging (Rcl) as approximately 1.2 and for direct classical imaging (Rdcl) as approximately 1.7.
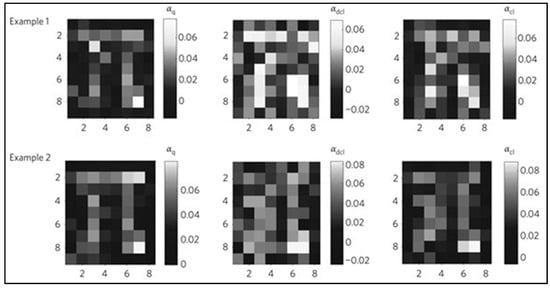
Figure 12.
Experimental imaging of a −shaped titanium deposition with 0.5 when 0.35 [].
Quantum illumination is a protocol that offers a quantum advantage in detecting targets, similar to a radar system, especially when dealing with a significant thermal background [,,]. The protocol involves sending a probe beam into a specific region of space where a weakly reflecting target may or may not be present. However, the reflection of the probe beam from the target is concealed within a much stronger background signal [,,]. A quantum receiver, which performs a joint measurement between the reflected probe beam and an ancillary quantum-correlated beam shown in Figure 11, is used to overcome this challenge. This joint measurement enables the discrimination of the faint signal component from the overwhelming noise, thereby revealing the presence of the target even amidst the dominant thermal background [,,]. The authors’ work involves using a quantum correlation imaging technique []. This arrangement makes it difficult for the target to determine it is being imaged, as the photons used for imaging are not easily distinguishable from natural background radiation. The environment contains actively controlled elements that can create misleading or “spoof” images. These could be sources of thermal illumination that overlay false images over the real ones. The challenge in such an environment is distinguishing between the actual image and the spoofed one. The novel aspect of the approach is subtracting the quantum AND image from the classical data. This is achieved by performing a pixel-by-pixel AND operation between the two regions of an Electron Multiplying CCD (EMCCD) array detector where the probe and reference beams are recorded. The quantum illumination AND image is calculated from the sum of these AND events over numerous frames, enhancing image quality. This process helps filter out the uncorrelated background light and sensor noise, which are more prominent in the classical image.
Figure 13 shows a schematic of a setup for a quantum illumination experiment. At the beginning of the setup, a UV laser emits light at 355 nm, which stimulates a Type II Beta Barium Borate (BBO) crystal. This crystal generates entangled photon pairs through SPDC. These pairs consist of a signal (probe) photon and an idler (reference) photon. The probe photon is directed towards a target, metaphorically described as a “bird target” in the far field, indicating that the target is far from the crystal. This photon interacts with the target and carries information about it. Simultaneously, the reference photon travels along an unobstructed optical path, which does not interact with the target. This path serves as a comparison to measure the changes to the probe photon upon interaction with the target. In the far field, the setup includes a thermally illuminated cage projected onto a camera. This thermal illumination is a background or reference for detecting the probe beam’s photons. The area projected onto the camera coincides with the detection area of the probe beam, which is critical for comparing the entangled pairs and extracting information about the target. A mask is also part of the setup, which is used to shape or limit the beam for better detection. The far-field EMCCD captures the incoming photons and allows for the observation and analysis of the quantum illumination process.
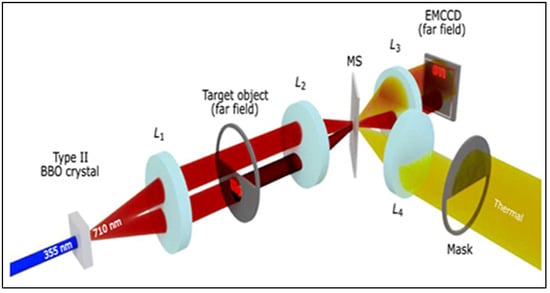
Figure 13.
The setup for quantum illumination involves a UV laser that stimulates a type-II phase matching BBO crystal, generating entangled photon pairs through SPDC. The probe beam engages with a bird target. The reference beam follows an unobstructed optical path. Additionally, a thermally illuminated cage is projected onto the camera, coinciding with the area where the probe beam’s detection occurs [].
Figure 14 shows the images obtained through a quantum illumination AND-image protocol and compares them against classically acquired images at different brightness levels. This comparison is quantified in the distinguishability ratio columns, which measure the clarity of the quantum images () against the classical ones (). The quantum images show enhanced contrast and clarity, especially as the brightness increases, which suggests that quantum illumination can provide better imaging under certain conditions. However, the presence of a bird figure in the quantum illumination AND-image subtracted column indicates a potential compromise. This suggests that while quantum illumination can improve image quality, it might still be possible for an adversary to introduce false data or images into the system, creating a spoofed image that can mislead observers. The author’s work marks a significant advancement in addressing the challenge of environment spoofing in quantum imaging. However, it is essential to recognize that the object being imaged can present its own challenges, potentially acting as a source of interference or deception. This aspect becomes particularly critical in scenarios where the object might have adaptive or responsive features designed to evade detection or mislead imaging systems. Consequently, recent research efforts shifted towards developing techniques that can effectively counteract such threats posed by the object.
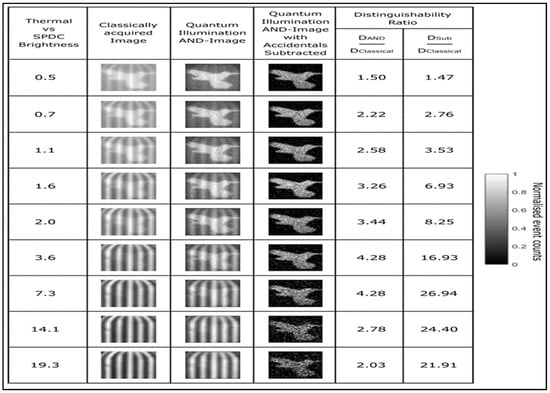
Figure 14.
Quantum illumination protocol-based environment spoofing proof image [].
An anti-jamming quantum radar imaging technique was introduced []. This method utilized the BB84 protocol for QKD based on polarization encoding. This approach enables the validation of imaging information authenticity by checking the consistency of photon polarization states between the sender and receiver. In this experiment, as shown in Figure 15, a HeNe laser is modulated by an Acousto-Optic Modulator (AOM) to generate pulses, each pulse typically containing a single photon. These photons’ polarization states are randomly altered between horizontal, vertical, diagonal, and anti-diagonal orientations using a half-wave plate () mounted on a motorized rotation stage. The photons are directed toward an object designed as a stealth aircraft silhouette on a mirror, and upon striking the object, they are specularly reflected towards the detection setup. An Interference Filter (IF) is employed in the setup to eliminate background noise. The photons’ polarization is then measured using a second rotating Half-Wave Plate () and a Polarizing Beam Splitter (). The orientation of the determines the measurement basis: Horizontal-Vertical (H/V) or Diagonal-Anti-Diagonal (D/A) basis. This approach ensures that the measurement basis aligns with the polarization state where the photons were sent, eliminating the need for additional sifting. Upon passing through the PBS, the photons are focused by two lenses, creating four distinct images on an EMCCD, corresponding to the four polarization states. This camera acts as a single-photon detector. The final image of the stealth aircraft is constructed by amalgamating these 10,000 individual images, each with its own random and orientations. The experiment also includes an error analysis. Errors occur when the detected polarization state is opposite to the expected state. For instance, if a Horizontally polarized (H) photon is sent and a Vertically polarized (V) photon is detected, it is counted as an error. In the absence of interference, an almost error-free image is expected. However, minor errors occur due to imperfections in the PBS, as reflected in our measurements. The low average error rate of 0.84% falls within the secure threshold.
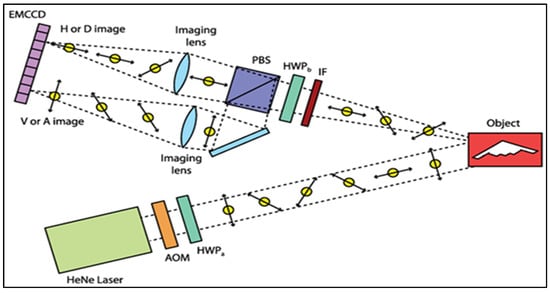
Figure 15.
Diagram of an experiment for imaging with quantum security measures []. It uses single-photon pulses generated by a polarized HeNe laser. These pulses are directed onto the object and then projected onto an Electron-Multiplying Charge-Coupled Device (EMCCD) camera through an Interference Filter (IF). It conducts measurements in the appropriate polarization bases by incorporating a Half-Wave Plate (HWP) and a Polarizing Beam Splitter (PBS). The process yields four images corresponding to the four polarizations measured [].
To test the system’s security, an intercept–resend jamming attack was simulated. In this scenario, the imaging photons are intercepted at the object and resent with a different image, in this case, a bird, all in horizontal polarization. The presence of an attack is indicated by a significant increase in the error rate, which we measure and find to be 50.44%, confirming the compromise of the received image. Additionally, the mutual information of the system drops to near zero, further substantiating the occurrence of an intercept–resend jamming attack.
A scheme based on the phase-encoding BB84 was recently performed with the decoy state method []. The quantum secure imaging system ingeniously merges phase-encoded BB84 QKD with Computational Ghost Imaging (CGI) technology. This system stands out due to its ability to detect and thwart intercept–resend jamming attacks, ensuring the security and authenticity of the imaging process. The experimental setup involved, as shown in Figure 16, a Digital Micro-mirror Device (DMD) to set specific spatial light intensity distributions and a Single-Photon Detector (SPD) to measure the total light intensity. By calculating both the intensity distribution and the total intensity, it successfully reconstructed images of objects. This QSI system, which effectively combines the security features of QKD with CGI’s imaging capabilities, outperforms traditional ghost imaging methods regarding data sampling rates, reduced complexity in imaging algorithms, and faster imaging times.
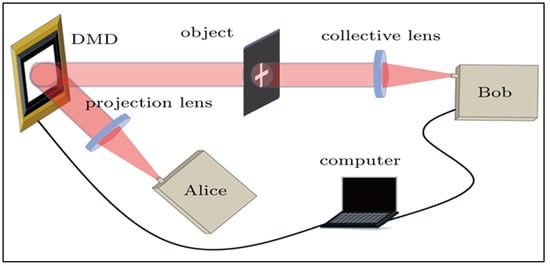
Figure 16.
Quantum secure imaging with QKD and CGI [].
The key to this system is using phase encoding BB84 protocol in QKD. The process involves Alice sending out attenuated coherent states with encoded key bit information, modulated through a DMD to create specific spatial light patterns. These patterns illuminate the object and are then detected and decoded. The security of the imaging is ensured by measuring the QBER and monitoring for any deviations that would indicate an intercept–resend attack. The experiment employed a pulsed laser operating at a specific frequency and wavelength, with the SPD operating in Geiger mode. The intensity of signal, decoy, and vacuum states were precisely controlled. The DMD was divided into blocks to manage the imaging algorithm’s complexity and enhance the imaging speed. The results are promising. There is a secure key rate of 571.0 bps and an average QBER of 3.99%, well below the lower error threshold of 14.51%. This confirmed the security and authenticity of the imaging process. However, it was noted that the image resolution was limited due to the diffraction effects of the DMD, especially with longer wavelengths of light. Despite this, methods to minimize these diffraction effects, such as adjusting the incident angle of light on the DMD, increasing the distance between the DMD and the detector, and matching the wavelength of the light to the DMD, were taken.
Figure 17 further depicts this concept by presenting two scenarios under a QKD protocol. The first image (a) shows a secure transmission with a deficient total average error, indicating that the image received is a faithful representation of the original object. The second image (b) shows a compromised scenario in which an intercept–resend jamming attack was executed. This is depicted by the manipulated image that appears as a bird, significantly different from the expected secure image. The average error rate jumps to over 50%, well above the 25% threshold, signaling an apparent compromise of the image. Together, these figures suggest that quantum illumination, coupled with QKD, can improve imaging capabilities, and provide a means to detect security breaches. The bird figure in the compromised images represents how an image can be altered by an active attack, thus demonstrating the importance of error rate analysis in confirming the integrity of quantum-secured images.
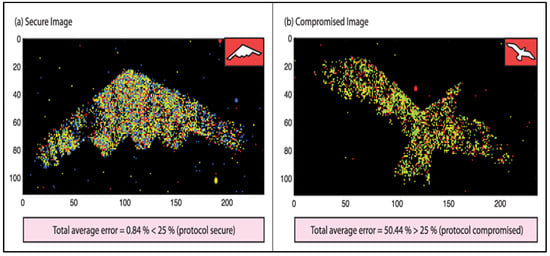
Figure 17.
In the first scenario (a), where no jamming attack was present, the received image faithfully replicated the real object. The error rate was measured at 0.84 percent (b), and an intercept–resend jamming attack was introduced. This led to the reception of a manipulated “spoof” image resembling a bird. However, the imaging system consistently identified the jamming attack due to the high error rate (surged to 50.44 percent) in the received polarization data. An error rate exceeding 25 percent clearly indicated that the image received was compromised [].
An alternative approach with squeezed states for remote sensing also made some progress. If the amplitude is squeezed, the photons tend to arrive more evenly spaced than in a coherent field, which is a classically forbidden phenomena known as photon anti-bunching. This can be used to reduce the variance in amplitude or intensity measurements, and thus enable precision better than that possible with coherent states []. The squeezed state light source developed in the project is an orthogonal amplitude squeezed optical field [,,]. In the experiment, the degree of squeezing in the quantum light field achieved was 5.6 dB []. The proportion of optical noise to total noise was 73%. There was a reduction in noise by 3.27 dB. The phase-sensitive amplification without noise reached 7 dB. The enhancement in SNR was 11.2 dB, and there was a 300% improvement in resolution. In this experiment, a specialized laser system is employed that produces two distinct wavelengths of light: 532 nm green light and 1064 nm infrared light. Soon, squeezed light states seem to provide the most versatile option for quantum experiments. Up to this point, the use of entangled photon pairs resulted in notable progress in tackling various quantum imaging difficulties. Techniques such as spontaneous parametric down-conversion, which are used to produce entangled photons, often yield these photons concurrently across several electromagnetic modes. This characteristic is crucial for addressing the challenges associated with broad imaging problems.
3.3. Sub-Rayleigh Quantum Imaging
Correlation-based imaging is a pivotal technique in advanced microscopy, offering significant image resolution and quality improvements []. This approach leverages photon correlations and coincidence detection to overcome the limitations inherent in traditional imaging methods, such as broadening the point spread function due to diffraction from the finite size of microscope components. The essence of confocality in microscopy lies in its use of focused beams and pinholes. This setup allows for imaging light only from a specific focal plane, enhancing contrast and significantly reducing noise from out-of-focus areas. Confocal microscopy is particularly effective in minimizing the impact of stray light, including multiply scattered light, thus enhancing the SNR. Integrating the correlation and confocality in microscopy creates a synergistic effect.
Combining the precise localization capabilities of correlation-based methods with the high contrast and noise reduction of confocal microscopy makes it possible to achieve superior accuracy and clarity in imaging. This integration is crucial in fields where observing fine details is critical, such as in biological or material sciences. Integrating these techniques involves using entangled photon pairs produced by spontaneous parametric down-conversion. These photons, correlated at specific angles, create an effect similar to a pinhole when traced backward from the sample. The down-conversion crystal is positioned far enough from the lens, or the pump beam is made narrow enough to make the pump beam’s cross-section point-like. This method aligns with the imaging condition , where and are the distances from the lens to the object and image planes, respectively, and f is the lens’s focal length.
Another method involves collimating the illumination beam in a standard confocal microscope. The beam is focused to a point one focal length away from the lens. Spatial correlations are then introduced by directing pairs of narrow, well-localized beams of light to strike the lens at equal distances from its axis, satisfying the same imaging condition. Experiments achieved spatial resolution enhancement beyond the classical diffraction limit without applying the far-field condition []. Two-Photon Airy Disk Scheme (Figure 18): (a) This setup includes a UV pulse beam generated by a Ti:sapphire femtosecond laser, with a central wavelength of 400 nm and a repetition rate of 76 MHz. This beam pumps a type-II Beta-Barium-Borate (BBO) crystal to generate collinear orthogonally polarized photons through the SPDC process. In this scheme, a Circular Aperture (CA) with a specified radius is placed immediately after the BBO crystal and at the front focal plane of the lens. Sub-Rayleigh Quantum Imaging Scheme: (b) In this setup, an object mask (specifically, a United States Air Force (USAF) resolution target) is placed immediately after the BBO crystal. An aperture with a defined radius is attached to the lens. The orthogonally polarized photon pairs from the BBO crystal pass through the object and the lens and are then collected by a Multi-Mode Fiber (MMF) on the image plane. These photon pairs are separated by a Polarizing Beam Splitter (PBS), and the coincidence counts detected by two single-photon detectors ( and ) are proportional to the entangled photon pairs arriving at the image plane.
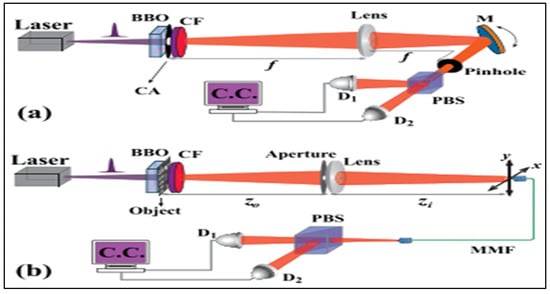
Figure 18.
(a) Two-Photon Airy Disk Scheme, (b) Sub-Rayleigh Quantum Imaging Scheme [].
Figure 19 shows the experimental results of the two-photon Airy disk scheme. It consists of two graphs, labeled (a) coincidence counts and (b) conventional imaging, across a spatial dimension (x-axis). The resulting two-photon Airy disk has a central spot with half the size of the classical Airy disk. This figure is instrumental in illustrating the enhancement in spatial resolution achievable with the two-photon Airy disk scheme compared to conventional imaging.
Figure 19.
Experimental results of the two-photon Airy disk scheme (a) Two photon Airy disk pattern and (b) conventional Airy disk pattern. [].
On the left column of Figure 20, the classical imaging results are displayed, while the right column shows quantum imaging results for comparison. Each row corresponds to an object with different aperture sizes, as indicated by A = 0.4 mm (a), A = 0.6 mm (b), and A = 0.8 mm (d). The uppermost part of the figure depicts the object used in the experiment (a USAF resolution target), and below are the corresponding imaging results. The graphs below the images represent the intensity profiles or coincidence counts for each case, with classical imaging on the left and quantum imaging on the right, demonstrating the resolution enhancement in quantum imaging.
Figure 20.
Classical (left column) vs. Quantum imaging (right column) (a) for object, with different apertures (b) A = 0.4 mm, (c) A= 0.6 mm, and (d) A= 0.8 mm [].
The classical Rayleigh criterion is a measure of the resolution limit of an imaging system, traditionally applied in the context of classical light sources. The formula provided in the paper for the Rayleigh criterion is: Here, represents the classical resolution limit, is the wavelength of light used, is the distance from the lens to the object, A is the aperture diameter, and M is the magnification factor. This formula calculates the minimum distance at which two points can be resolved as distinct in the classical imaging system. In the context of quantum imaging with a two-photon source, the resolution criterion is enhanced []. It was observed that the quantum resolution criterion is given by . It implies that the quantum imaging setup can resolve details smaller than what is possible with classical imaging techniques. The experiments described in the paper use an aperture of 0.4 mm. Using these criteria, they calculate the classical and quantum resolution limits as 488 μm and 345 μm, respectively. This means that while the classical imaging setup cannot resolve details smaller than 488 μm, the quantum imaging setup can resolve details as small as 345 μm. The authors demonstrate this by showing that stripes spaced 354 μm apart, which are not resolvable in classical imaging, can be resolved in the two-photon quantum imaging setup [].
3.4. Quantum Imaging Using Undetected Photons
A nonlinear quantum interferometer setup involves two nonlinear crystals. A laser beam is split into two beams, which coherently pump the crystals. The idler wave interacts with an object; another is generated and co-aligned with the first. The signal waves from both idler interactions are combined at a beam splitter. The interference of signal waves depends on the phase and transmission properties of the object probed by the first idler wave. Superposition of the idler waves makes it impossible to determine their origin crystal, inducing coherence between emitted photon pairs []. In induced coherence-based quantum imaging, photon pairs are created from two-photon sources. By aligning the paths of one photon (the idler) from both sources and ensuring their path identity, the other photon (the signal) exists in a superposition state. This superposition state encodes information about the phase and transmissivity of the idler photon. Placing an object on the idler path allows capturing images exclusively with the signal photons, which remain unaffected by any interaction with the object [,,].
Figure 21 illustrates a nonlinear quantum interferometer without direct photon detection for imaging purposes. At the beginning of the setup, a 532 nm laser (L1) is employed as the primary light source. The light from this laser is passed through Wave Plates (WPs) to control its polarization precisely, followed by a Half-Wave Plate (HWP) to adjust the polarization state further. A Polarizing Beam Splitter (PBS) divides the beam into two distinct optical paths. These paths pump two nonlinear crystals (NL1 and NL2) where the light interacts with the internal structure of the crystals to generate new light waves—typically known as parametric down-conversion. One of the paths is directed towards the first nonlinear crystal (NL1), and the generated idler wave interacts with an Object (O). In contrast, the signal wave is redirected towards a Beam Splitter (BS). The second path is similarly directed to another nonlinear crystal (NL2), generating a second idler wave co-aligned with the first one and a signal wave that also heads to the BS. Mirrors (M1, L2, L3, and L4) and lenses (L2′, L3′, L4′) are positioned to guide and focus the beams through the system. At the BS, the signal waves from both paths are combined, and their interference pattern is influenced by the phase and transmission properties of the object probed by the first idler wave. Since the idler waves are in a superposition state, it is impossible to determine their crystal of origin, which creates coherence between the emitted photon pairs. This interference is then passed through filters and directed towards an Electron-Multiplying CCD (EMCCD) camera for detection. The innovative aspect of this setup is that the image of the object can be obtained without directly detecting the photons that interact with it.
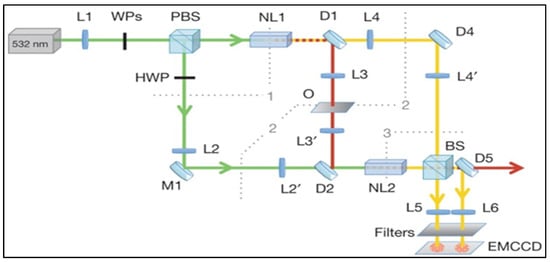
Figure 21.
The experimental setup for imaging without photon detection involves a nonlinear interferometer constructed by linking idler from the first nonlinear crystal (NL1) to a second nonlinear crystal (NL2). The interference pattern resulting from quantum interference between emitted photons’ wavefunctions appears at the beam splitter’s output. Inserting an object between NL1 and NL2 modifies the entire wave function, impacting signal wave interference after the beam splitter. This enables image acquisition without detecting interacting photons [].
Spirulina is mainly a phase object at the illumination wavelength used. At the same time, the fruit fly wing is predominantly an amplitude object due to its absorption characteristics in the visible and near IR range. The resolution of the images is emphasized as surpassing that of conventional methods by an order of magnitude or more. Figure 22 is divided into eight separate image panels labeled (a) through (h), which are grouped in pairs to show the amplitude and phase images of two different biological samples at various scales and step sizes. Panels (a) and (b) display the amplitude images of Spirulina filaments, a type of cyanobacteria with distinct helical structures. Now, panels (c) and (d) present the phase images of the same Spirulina cell culture, which appear to have higher contrast and possibly more detail compared to the amplitude images, which is in line with the inference about the quality of phase images. The next set of images relates to the wing of a fruit fly, illustrating its complex structural details at different scales, where panels (e) and (g) show conventional microscope images of the fruit fly wing, captured in the visible spectrum, displaying the wing’s hierarchical structure, including veins and hair-like formations. Finally, panels (f) and (h) offer the corresponding images, which are expected to have a significantly higher resolution due to the quantum imaging technique, revealing finer structural details.
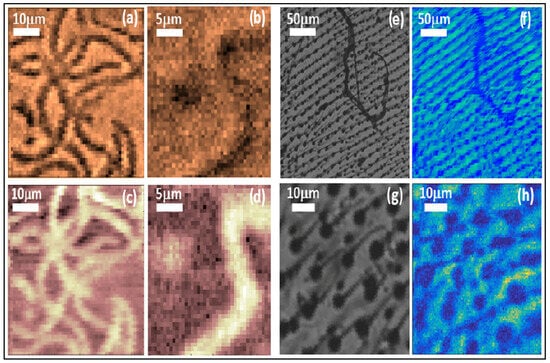
Figure 22.
Quantum imaging of biological sample from undetected imaging method, image panels (a–h) showing amplitude and phase images of biological samples. Panels (a,b) display amplitude images of Spirulina filaments. Panels (c,d) show phase images of Spirulina with higher contrast. Panels (e,g) present conventional microscope images of a fruit fly wing, illustrating structural details. Panels (f,h) depict the corresponding images with higher resolution from quantum imaging, revealing finer details [].
One of the captivating discoveries in quantum physics is the wave–particle duality of particles such as photons. This duality implies that photons can exhibit wave-like and particle-like behaviors, depending on whether we can distinguish their paths [,]. When two beams of light superimpose, they create an intensity pattern with interference fringes, demonstrating the wave-like nature of light [,]. However, when we make the paths of photons distinguishable, such as by altering their polarization, they behave more as individual particles than waves. The Mach–Zehnder Interferometer (MZI) is a critical tool that leverages the wave–particle duality of photons []. It involves splitting a beam of light and recombining it, leading to interference patterns when paths are indistinguishable. In the context of quantum imaging, the paths of photons can be intentionally made distinguishable, disrupting their wave-like behavior. However, this distinguishability can be reversed to regain coherence or wave-like behavior. This phenomenon forms the basis for induced coherence-based quantum imaging. MZI is at the core of this imaging technique. When dealing with single photons or coherent laser light, they exhibit wave-like behavior when their potential pathways cannot be distinguished. This leads to interference patterns in the form of fringes. However, altering the polarization of photons in one of the pathways makes their paths distinguishable, and they behave more as classical particles.
Figure 23a shows a setup where single photons or coherent laser light are not subjected to any distinguishing process. Here, the paths of the photons cannot be differentiated, which is a scenario conducive to wave-like behavior resulting in interference patterns. This is indicated by the single tall probability bar at detector D1, suggesting constructive interference at this point and no detection at D2. (b) A Half-Wave Plate (HWP) is introduced at a 45-degree angle in one of the pathways. This alteration changes the polarization of the photons in that path, which makes it possible to distinguish which path the photons took. As a result, the wave-like interference pattern is destroyed, and the photons are detected as if they were classical particles, indicated by the two smaller probability bars at detectors D1 and D2. This demonstrates the collapse of the interference pattern into two distinct probabilities corresponding to the two potential paths the photons can take. This experiment is a typical demonstration of the quantum mechanical principle where measurement (in this case, distinguishing the paths via polarization) affects the behavior of quantum particles.
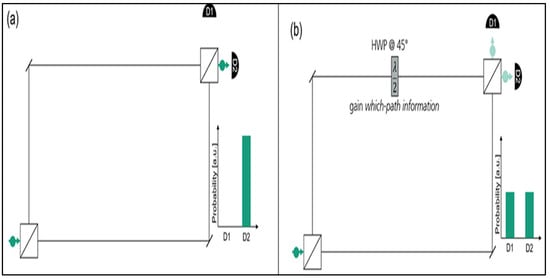
Figure 23.
(a) When dealing with single photons or coherent laser light, their behavior will resemble that of waves, given that both potential pathways cannot be differentiated. (b) By altering the polarization using a Half-Wave Plate (HWP) in one of the pathways, the ability to distinguish which path is taken becomes possible, causing the photons to behave as classical particles [].
In an interaction-free measurement setup using a MZI, detectors are placed to observe constructive and destructive interference. When a single photon is introduced, it should be detected at the constructive interference detector. However, if a perfectly absorbing object is placed in one arm of the interferometer, it can transmit a single photon through the system. Detection at the destructive interference detector indicates the presence of an object in one arm, even though the detected photon possibly never interacted with the object [,]. As shown in Figure 24, the photons first encounter a dichroic mirror (), which directs the beam into the interferometer’s arms. In one arm, another dichroic mirror () separates an undetected idler photon. The numbered circles represent different paths or arms within the interferometer. A Beam Splitter (BS) divides the photon’s path within the interferometer, creating two routes. In one of these routes, a perfectly absorbing object may be placed. The presence of this object can change the outcome of the interference pattern observed by the detectors. The two paths are recombined at a second beam splitter, and the interference pattern is observed. The phase difference introduced by the object (if present) and the system itself is denoted by for the signal photon and for the relative phase of the interaction-free measurement. The detectors , and are placed to observe constructive and destructive interference patterns. When a photon is detected at , it indicates the object’s presence in the other arm due to the destructive interference pattern despite the photon not directly interacting with the object. The system also includes an Intensified CCD (ICCD) camera represented by inset f, which detects the signal photon. This contrasts with the Single-Photon Detector (SPD) shown in inset e, another detection method not utilized in this setup. The SLM is employed to manipulate the phase or amplitude of the light in the system. The entire arrangement allows for quantum imaging by detecting the interference patterns, indirectly providing information about the object’s presence without the photon interacting.
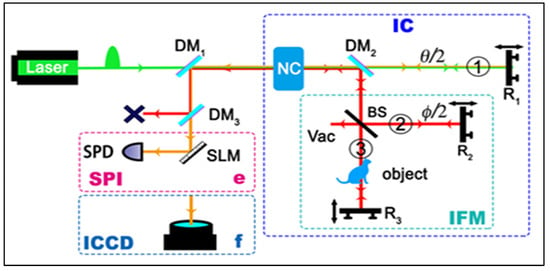
Figure 24.
The undetected idler photon is separated using a dichroic mirror DM3. The numbered circles indicate distinct interferometer arms. θ denotes the phase of the signal photon, while φ signifies the relative phase of the interaction-free measurement. Furthermore, interaction-free quantum imaging employs an Intensified CCD (ICCD) camera for detection, as seen in inset f of panel d, instead of utilizing SPI as displayed in inset e of panel d [].
Figure 25 shows the images obtained (a) with ICCD, and (b) with the single-pixel imaging method for the undetected imaging method, here the single-pixel imaging-based method enhances the brightness of the image. Table 5 summarizes the state-of-the-art techniques in quantum imaging.
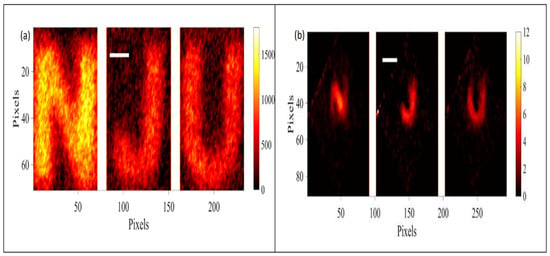
Figure 25.
(a) With ICCD, and (b) with the single-pixel imaging method for the undetected imaging method [].

Table 5.
State of art techniques in quantum imaging, PPKTP: Periodically Poled Potassium Titanyl Phosphate, EMCCD: Electron-Multiplying Charge-Coupled Device, BBO: Beta Barium Borate, CCD: Charge-Coupled Device, SPAD: Single Photon Avalanche Diode ICCD: Intensified Charge-Coupled Device, LN Type 1: Lithium Niobate Type 1, SPD: Single Photon Detector, and SLM: Spatial Light Modulator.
3.5. Key Breakthroughs and Advancements in Quantum Imaging Applications
Before we conclude, we outline below the key breakthroughs and advancements in quantum correlation enhanced remote sensing quantum biological imaging. The use of hyper-entangled photons emerged as a significant breakthrough in quantum imaging. Recent demonstration achieved a free-space distance of 16.91 m using BBO, type 2 crystals []. This advancement underscores the potential of hyperentanglement in enhancing the quantum imaging process, promising better performance in both near-field and long-range applications. The capability of object detection, even at an SNR as low as 0.03 using hyperentangled photons, represents a significant advancement []. Using a similar approach, the 12 dB improvement in the low noise regime reiterates its efficacy []. Though still in the early research phases, its utility in stealth object detection presents revolutionary potential. Using PPKTP (type 0) crystals, the remote sensing approach by quantum imaging projects a theoretical range from 75 m to 210 m []. This broadens the horizon for practical applications and sets a benchmark for what might be attainable in the coming years. Quantum holography is an innovative approach that uses hyper-entangled photon pairs to encode and decode images []. In this technique, Alice encodes an image onto the phase of the photons using a Spatial Light Modulator (SLM). On the other hand, Bob uses a phase mask to compensate for phase distortions. Through intensity correlation measurements, Bob reconstructs the encoded image by exploiting the spatial and polarization entanglement of photon pairs. HSPS recently found applications in quantum imaging experiments due to the reduced uncertainty in measurements and background suppression [,,]. This has potential advantage over laser-based sources and attenuated single-photon sources due to the correlation properties and sub-Poissonian statistics.
The use of entangled and heralded single photons from the SPDC process is becoming a crucial advancement in biological applications, showing great potential to increase accuracy, enhance signal-to-noise ratios by effectively suppressing background noise, and reduce cellular damage that results from lowlight exposure. The study on quantum diagnosis method using heralded single photons for cancer diagnosis presents enhancing precision and reducing measurement uncertainty []. This technique reduces staining and offers greater sensitivity for tumor identification. The study on a novel technique using quantum light presents Entangled Two-Photon Absorption (ETPA) to analyze breast cancer cells with much decreased light levels []. This method significantly decreases photobleaching and cellular damage by using an excitation strength one million times lower than that of traditional two-photon fluorescence microscopy. This technology enhances comprehension of cellular and molecular processes in biological systems, allowing for noninvasive and nondestructive biological imaging and offering valuable insights into cell dynamics important for cancer research. Furthermore, the Imaging by Coincidence from Entanglement (ICE) technique [] uses polarization entanglement to perform “ghost birefringence imaging”, allowing for the measurement of birefringence properties without altering the polarization state of incident photons. This quantum advantage allows for detailed material characterization, including biological specimens.
4. Discussion and Conclusions
Surveillance and remote sensing demand around-the-clock reliability in real world applications. This requirement poses a significant challenge in maintaining consistent performance, especially in varying environmental conditions that can impact quantum systems. The delay in the idler arm is another critical aspect, particularly crucial for preserving quantum correlations essential for practical imaging. This delay must be meticulously managed to ensure that the entangled pairs used in quantum imaging maintain their correlated states, which is fundamental for the accuracy and reliability of the imaging process. CGI emerges as a promising solution in this context. This technique simplifies the complex architecture of quantum systems, enabling more robust and efficient quantum imaging. Furthermore, integrating QKD systems operating at telecom wavelengths, specifically around 1550 nm, offers hope for the continuous operation of quantum imaging in free space. This integration aligns with existing telecommunications infrastructure and provides a secure method of transferring and storing images, which is crucial for applications requiring high confidentiality and data integrity. While free space secure quantum imaging faces significant challenges, integrating computational ghost imaging and QKD systems operating at 1550 nm presents a promising pathway toward achieving robust, continuous, and secure quantum imaging applications. Quantum secure imaging, particularly in free space applications, confronts unique challenges and opportunities. Among these, two key issues stand out: achieving continuous 24/7 operation and addressing the delay in the idler arm for maintaining quantum correlation. Exploring advanced imaging techniques in the current scenario, notably in biological imaging and imaging of stealth objects, led to significant insights and developments. The paramount requirement for quantum imaging techniques arises from minimizing damage to biological samples and enabling covert imaging operations while maintaining the integrity of the images against potential attacks. Detectors such as ICCD, EMCCD, and SPAD arrays showed their effectiveness, particularly in the visible region. EMCCD was a popular choice in many experiments, aligning well with techniques such as super resolution and sub-shot noise imaging of biological samples at low light levels. These advancements are critical as they align with the human eye’s sensitivity peak at 810 nm and the challenges posed by background radiation during nighttime operations. This necessitates the development of techniques that can efficiently utilize the detectors’ capabilities while probing objects at 1550 nm.
Ghost imaging emerged as a promising approach in this context. Experiments where EMCCD was used in the idler arm and signal photons at 1550 nm, probed the object, and detected with SPAD bucket detectors highlighted the potential of this technique. Furthermore, interference-based experiments offered solutions to bypass the need for bucket detectors. However, their application remains confined to laboratory settings due to the complex nature of interferometric arrangements. Correlation-based imaging techniques provided a solution for spoof-proof imaging, albeit limited to defending against passive attacks. Meanwhile, investigations into WCSs revealed their effectiveness against active attacks, with favorable results combined with EMCCD. The integration of WCS imaging with computational ghost imaging techniques marks a significant stride, facilitating the use of bucket detectors and thereby reducing system costs. Moreover, implementing the decoy state method with WCSs (WCS) assures enhanced security. This approach allows for higher mean photon numbers, leading to a higher rate of operational efficiency. Figure 26 graphically depicts the secure key rate versus transmission loss in decibels (dB) for systems without the decoy state method (blue curve) and with the decoy state method (orange curve). The introduction of the decoy state method significantly reduces the transmission loss, indicating an improvement in the secure key rate from O () to O (), where denotes the efficiency of the transmission channel. This means the decoy state method can effectively extend the secure range, making it more robust against transmission loss.
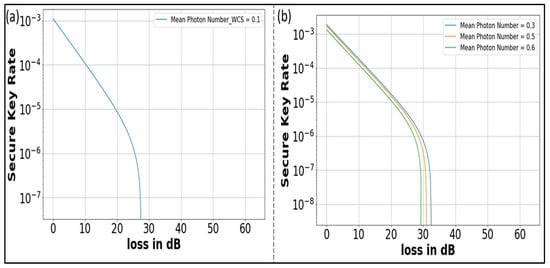
Figure 26.
(a) Without decoy state signal mean photon number 0.1 and (b) with decoy state with signal mean photon number 0.3, 0.5, and 0.6 with decoy state mean photon number 0.1, illustrates how using the decoy state method can extend the range.
However, WCS + decoy and CGI experiments did not mention the use of phase randomized lasers, which are essential for the experiments with WCS + decoy states, and the DMD used in the experiment which adds a global phase to the states could be set at random patterns. This also highlights that this is an illumination which has potential to reduce the speckle effect, and is hence comparable to the SPDC source. We forecast the use of the SPDC source instead of the WCS, which gives quantum correlation in the setup meaning SPDC + CGI + decoy states to reduce measurement uncertainty and background noise suppression. This source could be placed on the satellite and the ground station can use detectors such as SNSPD’s to image a stealth object with BB84+decoy protocol use.
In Figure 27a, we computationally show the relation between the secure key rate and loss in a QSI system with WCS and HSPS, considering low mean photon number with . The figure displays a series of curves representing the mean photon numbers of 0.01, 0.05, and 0.1 with decoy as 0.001 and 0. Each curve shows a noticeable decrease in the key rate as the distance increases. The figure illustrates variations in the secure rate at lower mean photon numbers for WCS, indicating a less stable performance across distance at these photon levels with WCS as compared to HSPS. Conversely, the Figure 27b depicts the graphs corresponding to higher mean photon numbers 0.2, 0.25, and 0.3 with decoys as 0.1 and 0. The curves are densely clustered and demonstrate a steady decrease for WCS, suggesting that the secure rate stays relatively constant across distance at a higher mean photon number with less variability for WCS. This implies that it is advantageous to maintain a greater mean photon number for long-distance QSI with WCS, since it leads to a more stable and reliable key rate as compared to HSPS.
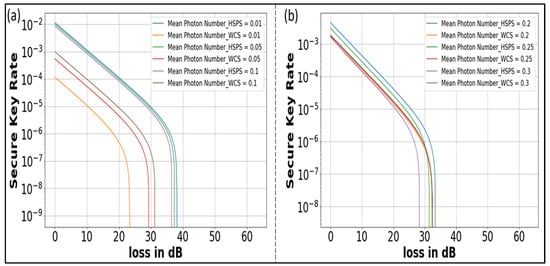
Figure 27.
(a) Relation between the secure key rate and loss in a Quantum Secure imaging system with WCS and HSPS at low mean photon numbers (0.01, 0.05, 0.1) with decoys as 0.001 and 0, showing a decrease in key rate with increasing distance ad stable performance for HSPS. (b) Secure key rate for higher mean photon numbers (0.2, 0.25, 0.3) with decoys as 0.1 and 0, displaying a more stable key rate across distance for WCS at [].
The advancements in imaging technology, particularly in the quantum domain, opened new avenues for efficient and secure imaging applications. These developments are pivotal for biological imaging and crucial for imaging in covert scenarios. The ongoing research and experimentation in this field promise further breakthroughs, potentially revolutionizing the landscape of imaging technology. In low-light situations, the efficiency of single-photon sources, especially SPDC and WCS, showed their unique benefits and constraints in quantum imaging. SPDC sources, which have sub-Poissonian statistics and quantum correlations, provide a potential method for improving measurement precision and reducing background noise despite their existing limits in photon efficiency. This highlights a potential route for future progress, underlining the need to investigate new materials and methods to enhance the efficiency of generating photon pairs using SPDC. In addition, research into the complex dynamics of interactions between quantum light and matter, emphasizing the possibility of using the idler arm of the SPDC source to extract meaningful information needs to be considered. Furthermore, the integration of machine learning and artificial intelligence has the potential to transform the area thoroughly, offering substantial improvements in both the speed and quality of imaging. The following evaluations [,] on these subjects are expected to provide more understanding and are likely a significant reference for directing future research in quantum-enhanced imaging and other related areas.
Author Contributions
All Authors contributed equally to the manuscript. All the authors have accepted the responsibility for the entire content of this submitted manuscript and approved submission. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding. SV gratefully acknowledges PhD research financial support from MHRD, Government of India.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2010. [Google Scholar]
- Wootters·, W.K.; Zurek, W.H. A Singe Quantum Cannot Be Cloned. Nature 1982, 299, 39–42. [Google Scholar] [CrossRef]
- Brandsema, M.J.; Narayanan, R.M.; Lanzagorta, M.O. Correlation Properties of Single Photon Binary Waveforms Used in Quantum Radar/Lidar. In Radar Sensor Technology XXIV; SPIE: Bellingham, WA, USA, 2020; Volume 11408, pp. 113–126. [Google Scholar] [CrossRef]
- Dirac, P.A.M. Principles of Quantum Mechanics, 3rd ed.; Oxford at the Clarendon Press/Oxford University Press: Oxford, UK, 1947. [Google Scholar]
- Lanzagorta, M.; Uhlmann, J. Opportunities and Challenges of Quantum Radar. IEEE Aerosp. Electron. Syst. Mag. 2020, 35, 38–56. [Google Scholar] [CrossRef]
- Meda, A.; Losero, E.; Samantaray, N.; Scafirimuto, F.; Pradyumna, S.; Avella, A.; Ruo-Berchera, I.; Genovese, M. Photon-Number Correlation for Quantum Enhanced Imaging and Sensing. J. Opt. 2017, 19, 094002. [Google Scholar] [CrossRef]
- Brassard, G.; Méthot, A.A. Can Quantum-Mechanical Description of Physical Reality Be Considered Correct? Found. Phys. 2010, 40, 463–468. [Google Scholar] [CrossRef]
- Pittman, T.B.; Shih, Y.H.; Strekalov, D.V.; Sergienko, A.V. Optical Imaging by Means of Two-Photon Quantum Entanglement. Phys. Rev. A 1995, 52, R3429–R3432. [Google Scholar] [CrossRef] [PubMed]
- Strekalov, D.V.; Sergienko, A.V.; Klyshko, D.N.; Shih, Y.H. Observation of Two-Photon Ghost Interference and Diffraction. Phys. Rev. Lett. 1995, 74, 3600–3603. [Google Scholar] [CrossRef] [PubMed]
- Abouraddy, A.F.; Saleh, B.E.A.; Sergienko, A.V.; Teich, M.C. Role of Entanglement in Two-Photon Imaging. Phys. Rev. Lett. 2001, 87, 123602. [Google Scholar] [CrossRef] [PubMed]
- Bennink, R.S.; Bentley, S.J.; Boyd, R.W. “Two-Photon” Coincidence Imaging with a Classical Source. Phys. Rev. Lett. 2002, 89, 9–12. [Google Scholar] [CrossRef] [PubMed]
- Shapiro, J.H. Computational Ghost Imaging. Phys. Rev. A—At. Mol. Opt. Phys. 2008, 78, 061802. [Google Scholar] [CrossRef]
- Bromberg, Y.; Katz, O.; Silberberg, Y. Ghost Imaging with a Single Detector. Phys. Rev. A—At. Mol. Opt. Phys. 2009, 79, 053840. [Google Scholar] [CrossRef]
- Brida, G.; Genovese, M.; Berchera, I.R. Experimental Realization of Sub-Shot-Noise Quantum Imaging. Nat. Photonics 2010, 4, 227–230. [Google Scholar] [CrossRef]
- Lemos, G.B.; Borish, V.; Cole, G.D.; Ramelow, S.; Lapkiewicz, R.; Zeilinger, A. Quantum Imaging with Undetected Photons. Nature 2014, 512, 409–412. [Google Scholar] [CrossRef] [PubMed]
- Malik, M.; Magaña-Loaiza, O.S.; Boyd, R.W. Quantum-Secured Imaging. Appl. Phys. Lett. 2012, 101, 241103. [Google Scholar] [CrossRef]
- Zhang, Y.; He, Z.; Tong, X.; Garrett, D.C.; Cao, R.; Wang, L.V. Quantum Imaging of Biological Organisms through Spatial and Polarization Entanglement. Sci. Adv. 2023, 10, eadk1495. [Google Scholar] [CrossRef] [PubMed]
- Heo, J.; Kim, J.; Jeong, T.; Ihn, Y.S.; Kim, D.Y.; Kim, Z.; Jo, Y. Quantum-Secured Single-Pixel Imaging with Enhanced Security. Optica 2023, 10, 1461. [Google Scholar] [CrossRef]
- Berchera, I.R.; Degiovanni, I.P. Quantum Imaging with Sub-Poissonian Light: Challenges and Perspectives in Optical Metrology. Metrologia 2019, 56, 024001. [Google Scholar] [CrossRef]
- Gregory, T. Quantum Enchanced Imaging. Ph.D. Thesis, University of Glasgow, Glasgow, UK, 2022. [Google Scholar]
- Decem, R. A Dynamical Theory of the Electromagnetic Field. Nature 1927, 119, 125–127. [Google Scholar] [CrossRef]
- Planck, M. On the Law of Distribution of Energy in the Normal Spectrum. Ann. Phys. 1901, 4, 533. [Google Scholar]
- Qian, W. On the Physical Process and Essence of the Photoelectric Effect. J. Appl. Math. Phys. 2023, 11, 1580–1597. [Google Scholar] [CrossRef]
- Broglie, L. A Tentative Theory of Light Quanta. Lond. Edinb. Dublin Philos. Mag. J. Sci. 1924, 47, 446–458. [Google Scholar] [CrossRef]
- Pérez-Delgado, C.A.; Pearce, M.E.; Kok, P. Fundamental Limits of Classical and Quantum Imaging. Phys. Rev. Lett. 2012, 109, 123601. [Google Scholar] [CrossRef] [PubMed]
- Aspuru-Guzik, A.; Walther, P. Photonic Quantum Simulators. Nat. Phys. 2012, 8, 285–291. [Google Scholar] [CrossRef]
- Bloch, I.; Dalibard, J.; Nascimbène, S. Quantum Simulations with Ultracold Quantum Gases. Nat. Phys. 2012, 8, 267–276. [Google Scholar] [CrossRef]
- Blatt, R.; Roos, C.F. Quantum Simulations with Trapped Ions. Nat. Phys. 2012, 8, 277–284. [Google Scholar] [CrossRef]
- Morton, J.J.L.; Lovett, B.W. Hybrid Solid-State Qubits: The Powerful Role of Electron Spins. Annu. Rev. Condens. Matter Phys. 2011, 2, 189–212. [Google Scholar] [CrossRef][Green Version]
- Pla, J.J.; Tan, K.Y.; Dehollain, J.P.; Lim, W.H.; Morton, J.J.L.; Zwanenburg, F.A.; Jamieson, D.N.; Dzurak, A.S.; Morello, A. High-Fidelity Readout and Control of a Nuclear Spin Qubit in Silicon. Nature 2013, 496, 334–338. [Google Scholar] [CrossRef] [PubMed]
- Houck, A.A.; Türeci, H.E.; Koch, J. On-Chip Quantum Simulation with Superconducting Circuits. Nat. Phys. 2012, 8, 292–299. [Google Scholar] [CrossRef]
- Poot, M.; van der Zant, H.S.J. Mechanical Systems in the Quantum Regime. Phys. Rep. 2012, 511, 273–335. [Google Scholar] [CrossRef]
- Kurizki, G.; Bertet, P.; Kubo, Y.; Mølmer, K.; Petrosyan, D.; Rabl, P.; Schmiedmayer, J. Quantum Technologies with Hybrid Systems. Proc. Natl. Acad. Sci. USA 2015, 112, 3866–3873. [Google Scholar] [CrossRef]
- Moreau, P.A.; Toninelli, E.; Gregory, T.; Padgett, M.J. Imaging with Quantum States of Light. Nat. Rev. Phys. 2019, 1, 367–380. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G. Quantum Cryptography: Public Key Distribution and Coin Tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Ekert, A.K. Quantum Cryptography and Bell’s Theorem; Oxford University: Oxford, UK, 1992; pp. 413–418. [Google Scholar] [CrossRef]
- Bennett, C.H. Quantum Cryptography Using Any Two Nonorthogonal States. Phys. Rev. Lett. 1992, 68, 3121–3124. [Google Scholar] [CrossRef] [PubMed]
- Wiesner, S. Conjugate Coding. ACM Sigact News 1983, 15, 78–88. [Google Scholar] [CrossRef]
- Gisin, N.; Thew, R. Quantum Communication. Nat. Photonics 2007, 1, 165–171. [Google Scholar] [CrossRef]
- DiVincenzo, D.P. The Physical Implementation of Quantum Computation. Fortschritte Phys. 2000, 48, 771–783. [Google Scholar] [CrossRef]
- Ladd, T.D.; Jelezko, F.; Laflamme, R.; Nakamura, Y.; Monroe, C.; O’Brien, J.L. Quantum Computers. Nature 2010, 464, 45–53. [Google Scholar] [CrossRef] [PubMed]
- Giovannetti, V.; Lloyd, S.; Maccone, L. Quantum-Enhanced Measurements: Beating the Standard Quantum Limit. Science 2004, 306, 1330–1336. [Google Scholar] [CrossRef] [PubMed]
- Agarwal, G.S.; Boyd, R.W.; Nagasako, E.M.; Bentley, S.J. Comment on “Quantum Interferometric Optical Lithography: Exploiting Entanglement to Beat the Diffraction Limit”. Phys. Rev. Lett. 2001, 86, 1389. [Google Scholar] [CrossRef] [PubMed]
- Taylor, M.A.; Bowen, W.P. Quantum Metrology and Its Application in Biology. Phys. Rep. 2016, 615, 1–59. [Google Scholar] [CrossRef]
- Xavier, J.; Yu, D.; Vollmer, F.; Jones, C.; Zossimova, E. Quantum Nanophotonic and Nanoplasmonic Sensing: Towards Quantum Optical Bioscience Laboratories on Chip. Nanophotonics 2021, 10, 1387–1435. [Google Scholar] [CrossRef]
- Unternährer, M.; Bessire, B.; Gasparini, L.; Perenzoni, M.; Stefanov, A. Super-Resolution Quantum Imaging at the Heisenberg Limit. Optica 2018, 5, 1150. [Google Scholar] [CrossRef]
- Vernekar, S.; Xavier, J. Secure Quantum Imaging with Decoy State Heralded Single Photons. arXiv 2024, arXiv:2402.11675. [Google Scholar]
- Xu, D.Q.; Song, X.B.; Li, H.G.; Zhang, D.J.; Wang, H.B.; Xiong, J.; Wang, K. Experimental Observation of Sub-Rayleigh Quantum Imaging with a Two-Photon Entangled Source. Appl. Phys. Lett. 2015, 106, 10–15. [Google Scholar] [CrossRef]
- Fox, M. Quantum Optics: An Introduction; Oxford University Press: Oxford, UK, 2006. [Google Scholar]
- Gilaberte Basset, M.; Setzpfandt, F.; Steinlechner, F.; Beckert, E.; Pertsch, T.; Gräfe, M. Perspectives for Applications of Quantum Imaging. Laser Photonics Rev. 2019, 13, 1900097. [Google Scholar] [CrossRef]
- Jones, C.; Xavier, J.; Kashanian, S.V.; Nguyen, M.; Aharonovich, I.; Vollmer, F. Time-Dependent Mandel Q Parameter Analysis for a Hexagonal Boron Nitride Single Photon Source. Opt. Express 2023, 31, 10794–10804. [Google Scholar] [CrossRef] [PubMed]
- Barsotti, L.; Harms, J.; Schnabel, R. Squeezed Vacuum States of Light for Gravitational Wave Detectors. Rep. Prog. Phys. 2019, 82, 016905. [Google Scholar] [CrossRef]
- Taylor, M.A.; Janousek, J.; Daria, V.; Knittel, J.; Hage, B.; Bachor, H.A.; Bowen, W.P. Subdiffraction-Limited Quantum Imaging within a Living Cell. Phys. Rev. X 2014, 4, 011017. [Google Scholar] [CrossRef]
- Basset, F.B.; Valeri, M.; Roccia, E.; Muredda, V.; Poderini, D.; Neuwirth, J.; Spagnolo, N.; Rota, M.B.; Carvacho, G.; Sciarrino, F.; et al. Quantum Key Distribution with Entangled Photons Generated on Demand by a Quantum Dot. Sci. Adv. 2021, 7, eabe6379. [Google Scholar] [CrossRef] [PubMed]
- Crespi, A.; Lobino, M.; Matthews, J.C.F.; Politi, A.; Neal, C.R.; Ramponi, R.; Osellame, R.; O’Brien, J.L. Measuring Protein Concentration with Entangled Photons. Appl. Phys. Lett. 2012, 100, 233704. [Google Scholar] [CrossRef]
- Malik, M.; Boyd, R.W. Quantum Imaging Technologies; Springer: Berlin/Heidelberg, Germany, 2014; Volume 37, ISBN 2014101000. [Google Scholar]
- Hey, T. Quantum Computing: An Introduction. Comput. Control Eng. J. 1999, 10, 105–112. [Google Scholar] [CrossRef]
- Kok, P.; Munro, W.J.; Nemoto, K.; Ralph, T.C.; Dowling, J.P.; Milburn, G.J. Linear Optical Quantum Computing with Photonic Qubits. Rev. Mod. Phys. 2007, 79, 135–174. [Google Scholar] [CrossRef]
- Degen, C.L.; Reinhard, F.; Cappellaro, P. Quantum Sensing. Rev. Mod. Phys. 2017, 89, 035002. [Google Scholar] [CrossRef]
- Polino, E.; Valeri, M.; Spagnolo, N.; Sciarrino, F. Photonic Quantum Metrology. AVS Quantum Sci. 2020, 2, 024703. [Google Scholar] [CrossRef]
- Kocher, C.A.; Commins, E.D. Polarization Correlation of Photons Emitted in an Atomic Cascade. Phys. Rev. Lett. 1967, 18, 575–577. [Google Scholar] [CrossRef]
- Aspect, A.; Dalibard, J.; Roger, G. Experimental Test of Bell’s Inequalities Using Time-Varying Analyzers. Phys. Rev. Lett. 1982, 49, 1804–1807. [Google Scholar] [CrossRef]
- Louisell, W.H.; Yariv, A.; Siegman, A.E. Quantum Fluctuations and Noise in Parametric Processes. I. Phys. Rev. 1961, 124, 1646–1654. [Google Scholar] [CrossRef]
- Harris, S.E.; Oshman, M.K.; Byer, R.L. Observation of Tunable Optical Parametric Fluorescence. Phys. Rev. Lett. 1967, 18, 732–734. [Google Scholar] [CrossRef]
- Burnham, D.C.; Weinberg, D.L. Observation of Simultaneity in Parametric Production of Optical Photon Pairs. Phys. Rev. Lett. 1970, 25, 84–87. [Google Scholar] [CrossRef]
- Boyd, R. Nonlinear Optics. In Springer Handbook of Atomic, Molecular and Optical Physics; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Franken, P.A.; Hill, A.E.; Peters, C.W.; Weinreich, G. Generation of Optical Harmonics. Phys. Rev. Lett. 1961, 7, 118–119. [Google Scholar] [CrossRef]
- Maker, P.D.; Terhune, R.W.; Nisenoff, M.; Savage, C.M. Effects of Dispersion and Focusing on the Production of Optical Harmonics. Phys. Rev. Lett. 1962, 8, 21–22. [Google Scholar] [CrossRef]
- Bass, M.; Franken, P.A.; Hill, A.E.; Peters, C.W.; Weinreich, G. Optical Mixing. Phys. Rev. Lett. 1962, 8, 18. [Google Scholar] [CrossRef]
- Moodley, C.; Forbes, A. All-Digital Quantum Ghost Imaging: Tutorial. JOSA B 2023, 40, 3073–3095. [Google Scholar] [CrossRef]
- Gerry, C.C.; Knight, P.L. Introudctory Quantum Optics; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Walls, D.F. Squeezed States of Light. Nature 1983, 306, 141–146. [Google Scholar] [CrossRef]
- Mehmet, M.; Vahlbruch, H. The Squeezed Light Source for the Advanced Virgo Detector in the Observation Run O3. Galaxies 2020, 8, 79. [Google Scholar] [CrossRef]
- Dwyer, S. Quantum Noise Reduction Using Squeezed States in LIGO. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2013; p. 223. [Google Scholar]
- Chen, M.R.; Bi, S.W.; Dou, X.B.; Liu, W.Y. Study of Non-Classical Light Imaging Technology. Nucl. Instrum. Methods Phys. Res. Sect. A Accel. Spectrometers Detect. Assoc. Equip. 2011, 637, S130–S133. [Google Scholar] [CrossRef]
- Taylor, M.A.; Janousek, J.; Daria, V.; Knittel, J.; Hage, B.; Bachor, H.A.; Bowen, W.P. Biological Measurement beyond the Quantum Limit. Nat. Photonics 2013, 7, 229–233. [Google Scholar] [CrossRef]
- Paraïso, T.K.; Woodward, R.I.; Marangon, D.G.; Lovic, V.; Yuan, Z.; Shields, A.J. Advanced Laser Technology for Quantum Communications (Tutorial Review). Adv. Quantum Technol. 2021, 4, 2100062. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, S.L.; Li, H.W.; Yin, Z.Q.; Zhao, Y.B.; Chen, W.; Han, Z.F.; Guo, G.C. Decoy-State Theory for the Heralded Single-Photon Source with Intensity Fluctuations. Phys. Rev. A—At. Mol. Opt. Phys. 2009, 79, 062309. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Sen, A.; Rezai, K. Comparing Qubit Platforms in the Race to Feasible Quantum Computing. J. Stud. Res. 2021, 10, 1–18. [Google Scholar] [CrossRef]
- Lancaster, G.P.T.; Guide, S.; Riebe, M.; Becher, C.; Häffner, H.; Eschner, J.; Schmidt-Kaler, F.; Chuang, I.L.; Blatt, R. Implementation of the Deutsch-Josza Algorithm on an Ion Trap Quantum Computer. Nature 2003, 421, 388. [Google Scholar] [CrossRef]
- Levine, H.; Keesling, A.; Omran, A.; Bernien, H.; Schwartz, S.; Zibrov, A.S.; Endres, M.; Greiner, M.; Vuletić, V.; Lukin, M.D. High-Fidelity Control and Entanglement of Rydberg-Atom Qubits. Phys. Rev. Lett. 2018, 121, 123603. [Google Scholar] [CrossRef] [PubMed]
- Xia, T.; Lichtman, M.; Maller, K.; Carr, A.W.; Piotrowicz, M.J.; Isenhower, L.; Saffman, M. Randomized Benchmarking of Single-Qubit Gates in a 2D Array of Neutral-Atom Qubits. Phys. Rev. Lett. 2015, 114, 100503. [Google Scholar] [CrossRef]
- Isenhower, L.; Urban, E.; Zhang, X.L.; Gill, A.T.; Henage, T.; Johnson, T.A.; Walker, T.G.; Saffman, M. Demonstration of a Neutral Atom Controlled-NOT Quantum Gate. Phys. Rev. Lett. 2010, 104, 8–11. [Google Scholar] [CrossRef] [PubMed]
- Debnath, S.; Linke, N.M.; Figgatt, C.; Landsman, K.A.; Wright, K.; Monroe, C. Demonstration of a Small Programmable Quantum Computer with Atomic Qubits. Nature 2016, 536, 63–66. [Google Scholar] [CrossRef] [PubMed]
- Shannon, C.E. Communication Theory of Secrecy Systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in Quantum Cryptography. Adv. Opt. Photonics 2020, 12, 1012. [Google Scholar] [CrossRef]
- Dušek, M.; Jahma, M.; Lütkenhaus, N. Unambiguous State Discrimination in Quantum Cryptography with Weak Coherent States. Phys. Rev. A—At. Mol. Opt. Phys. 2000, 62, 9. [Google Scholar] [CrossRef]
- Clarke, R.B.M.; Chefles, A.; Barnett, S.M.; Riis, E. Experimental Demonstration of Optimal Unambiguous State Discrimination. Phys. Rev. A—At. Mol. Opt. Phys. 2001, 63, 040305. [Google Scholar] [CrossRef]
- Huttner, B.; Imoto, N.; Gisin, N.; Mor, T. Quantum Cryptography with Coherent States. Phys. Rev. A 1995, 51, 1863–1869. [Google Scholar] [CrossRef]
- Lütkenhaus, N.; Jahma, M. Quantum Key Distribution with Realistic States: Photon-Number Statistics in the Photon-Number Splitting Attack. New J. Phys. 2002, 4, 44. [Google Scholar] [CrossRef]
- Gottesman, D.; Hoi-Kwonglo, L.O.; Lütkenhaus, N.; Preskill, J. Security of Quantum Key Distribution with Imperfect Devices. Quantum Inf. Comput. 2004, 4, 325–360. [Google Scholar] [CrossRef]
- Hwang, W.Y. Quantum Key Distribution with High Loss: Toward Global Secure Communication. Phys. Rev. Lett. 2003, 91, 057901. [Google Scholar] [CrossRef]
- Lo, H.K.; Ma, X.; Chen, K. Decoy State Quantum Key Distribution. Phys. Rev. Lett. 2005, 94, 15–18. [Google Scholar] [CrossRef]
- Engle, R.D.; Mailloux, L.O.; Grimaila, M.R.; Hodson, D.D.; McLaughlin, C.V.; Baumgartner, G. Implementing the Decoy State Protocol in a Practically Oriented Quantum Key Distribution System-Level Model. J. Def. Model. Simul. 2019, 16, 27–44. [Google Scholar] [CrossRef]
- Duplinskiy, A.; Ustimchik, V.; Kanapin, A.; Kurochkin, V.; Kurochkin, Y. Low Loss QKD Optical Scheme for Fast Polarization Encoding. Opt. Express 2017, 25, 28886. [Google Scholar] [CrossRef]
- Schmitt-Manderbach, T.; Weier, H.; Fürst, M.; Ursin, R.; Tiefenbacher, F.; Scheidl, T.; Perdigues, J.; Sodnik, Z.; Kurtsiefer, C.; Rarity, J.G.; et al. Experimental Demonstration of Free-Space Decoy-State Quantum Key Distribution over 144 Km. Phys. Rev. Lett. 2007, 98, 010504. [Google Scholar] [CrossRef]
- Liao, S.K.; Cai, W.Q.; Liu, W.Y.; Zhang, L.; Li, Y.; Ren, J.G.; Yin, J.; Shen, Q.; Cao, Y.; Li, Z.P.; et al. Satellite-to-Ground Quantum Key Distribution. Nature 2017, 549, 43–47. [Google Scholar] [CrossRef]
- Atchison, D. Optics of the Human Eye; CRC Press: Boca Raton, FL, USA, 2023. [Google Scholar]
- Jenkins, F.A.; White, H.E. Fundamental of Optics. Indian J. Phys. 1957, 25, 265–266. [Google Scholar] [CrossRef]
- Smith, S. Digital Signal Processing: A practical Guide for Engineers and Scientists; Elsevier: Amsterdam, The Netherlands, 2013. [Google Scholar]
- Hadfield, R.H. Single-Photon Detectors for Optical Quantum Information Applications. Nat. Photonics 2009, 3, 696–705. [Google Scholar] [CrossRef]
- Madonini, F.; Severini, F.; Zappa, F.; Villa, F. Single Photon Avalanche Diode Arrays for Quantum Imaging and Microscopy. Adv. Quantum Technol. 2021, 4, 2100005. [Google Scholar] [CrossRef]
- Lampton, M. The Microchannel Image Intensifier. Sci. Am. 1981, 245, 62–71. [Google Scholar] [CrossRef]
- Cester, L.; Lyons, A.; Braidotti, M.C.; Faccio, D. Time-of-Flight Imaging at 10 Ps Resolution with an ICCD Camera. Sensors 2019, 19, 180. [Google Scholar] [CrossRef] [PubMed]
- Lantz, E.; Blanchet, J.L.; Furfaro, L.; Devaux, F. Multi-Imaging and Bayesian Estimation for Photon Counting with EMCCDs. Mon. Not. R. Astron. Soc. 2008, 386, 2262–2270. [Google Scholar] [CrossRef]
- Jerram, P.; Pool, P.J.; Bell, R.; Burt, D.J.; Bowring, S.; Spencer, S.; Hazelwood, M.; Moody, I.; Catlett, N.; Heyes, P.S. The LLCCD: Low-Light Imaging without the Need for an Intensifier. Sens. Camera Syst. Sci. Ind. Digit. Photogr. Appl. II 2001, 4306, 178. [Google Scholar] [CrossRef]
- Robbins, M.S.; Hadwen, B.J. The Noise Performance of Electron Multiplying Charge-Coupled Devices. IEEE Trans. Electron Devices 2003, 50, 1227–1232. [Google Scholar] [CrossRef]
- Izhnin, I.I.; Lozovoy, K.A.; Kokhanenko, A.P.; Khomyakova, K.I.; Douhan, R.M.H.; Dirko, V.V.; Voitsekhovskii, A.V.; Fitsych, O.I.; Akimenko, N.Y. Single-Photon Avalanche Diode Detectors Based on Group IV Materials. Appl. Nanosci. 2022, 12, 253–263. [Google Scholar] [CrossRef]
- Gyongy, I.; Calder, N.; Davies, A.; Dutton, N.A.W.; Duncan, R.R.; Rickman, C.; Dalgarno, P.; Henderson, R.K. A 256 × 256, 100-Kfps, 61% Fill-Factor SPAD Image Sensor for Time-Resolved Microscopy Applications. IEEE Trans. Electron Devices 2018, 65, 547–554. [Google Scholar] [CrossRef]
- Portaluppi, D.; Conca, E.; Villa, F.A.; Zappa, F. Time-Gated CMOS SPAD Array in 0.16 Μm BCD with Shared Timing Electronics and Background Light Rejection for LIDAR Applications. Adv. Photon Count. Tech. XII 2018, 10659, 33–40. [Google Scholar] [CrossRef]
- Perenzoni, M.; Perenzoni, D.; Stoppa, D. A 64 × 64-Pixels Digital Silicon Photomultiplier Direct TOF Sensor with 100-MPhotons/s/Pixel Background Rejection and Imaging/Altimeter Mode with 0.14% Precision up to 6 km for Spacecraft Navigation and Landing. IEEE J. Solid-State Circuits 2017, 52, 151–160. [Google Scholar] [CrossRef]
- Jin, R.B.; Fujiwara, M.; Yamashita, T.; Miki, S.; Terai, H.; Wang, Z.; Wakui, K.; Shimizu, R.; Sasaki, M. Efficient Detection of an Ultra-Bright Single-Photon Source Using Superconducting Nanowire Single-Photon Detectors. Opt. Commun. 2015, 336, 47–54. [Google Scholar] [CrossRef][Green Version]
- Gili, V.F.; Piccinini, C.; Safari Arabi, M.; Kumar, P.; Besaga, V.; Brambila, E.; Gräfe, M.; Pertsch, T.; Setzpfandt, F. Experimental Realization of Scanning Quantum Microscopy. Appl. Phys. Lett. 2022, 121, 104002. [Google Scholar] [CrossRef]
- Sensitivity and Noise of Ccd, Emccd, and Scmos Sensors. Available online: https://andor.oxinst.com/learning/view/article/sensitivity-and-noise-of-ccd-emccd-and-scmos-sensors (accessed on 25 January 2024).
- Zhao, Y.B.; Zhang, W.L.; Wang, D.; Song, X.T.; Zhou, L.J.; Ding, C.B. Proof-of-Principle Experimental Demonstration of Quantum Secure Imaging Based on Quantum Key Distribution. Chin. Phys. B 2019, 28, 104203. [Google Scholar] [CrossRef]
- Aspden, R.S.; Tasca, D.S.; Boyd, R.W.; Padgett, M.J. EPR-Based Ghost Imaging Using a Single-Photon-Sensitive Camera. New J. Phys. 2013, 15, 073032. [Google Scholar] [CrossRef]
- Morris, P.A.; Aspden, R.S.; Bell, J.E.C.; Boyd, R.W.; Padgett, M.J. Imaging with a Small Number of Photons. Nat. Commun. 2015, 6, 5913. [Google Scholar] [CrossRef] [PubMed]
- Aspden, R.S.; Gemmell, N.R.; Morris, P.A.; Tasca, D.S.; Mertens, L.; Tanner, M.G.; Kirkwood, R.A.; Ruggeri, A.; Tosi, A.; Boyd, R.W.; et al. Photon-Sparse Microscopy: Visible Light Imaging Using Infrared Illumination. Optica 2015, 2, 1049. [Google Scholar] [CrossRef]
- Moreau, P.-A.; Toninelli, E.; Morris, P.A.; Aspden, R.S.; Gregory, T.; Spalding, G.; Boyd, R.W.; Padgett, M.J. Resolution Limits of Quantum Ghost Imaging. Opt. Express 2018, 26, 7528. [Google Scholar] [CrossRef] [PubMed]
- Bornman, N.; Agnew, M.; Zhu, F.; Vallés, A.; Forbes, A.; Leach, J. Ghost Imaging Using Entanglement-Swapped Photons. NPJ Quantum Inf. 2019, 5, 63. [Google Scholar] [CrossRef]
- Yao, X.; Liu, X.; You, L.; Wang, Z.; Feng, X.; Liu, F.; Cui, K.; Huang, Y.; Zhang, W. Quantum Secure Ghost Imaging. Phys. Rev. A 2018, 98, 063816. [Google Scholar] [CrossRef]
- Lloyd, S. Enhanced Sensitivity of Photodetection via Quantum Illumination. Science 2008, 321, 1463–1465. [Google Scholar] [CrossRef]
- Tan, S.H.; Erkmen, B.I.; Giovannetti, V.; Guha, S.; Lloyd, S.; Maccone, L.; Pirandola, S.; Shapiro, J.H. Quantum Illumination with Gaussian States. Phys. Rev. Lett. 2008, 101, 253601. [Google Scholar] [CrossRef] [PubMed]
- Shapiro, J.H.; Lloyd, S. Quantum Illumination versus Coherent-State Target Detection. New J. Phys. 2009, 11, 063045. [Google Scholar] [CrossRef]
- Shapiro, J.H. Defeating Passive Eavesdropping with Quantum Illumination. Phys. Rev. A—At. Mol. Opt. Phys. 2009, 80, 022320. [Google Scholar] [CrossRef]
- Guha, S.; Erkmen, B.I. Gaussian-State Quantum-Illumination Receivers for Target Detection. Phys. Rev. A—At. Mol. Opt. Phys. 2009, 80, 052310. [Google Scholar] [CrossRef]
- Lopaeva, E.D.; Ruo Berchera, I.; Degiovanni, I.P.; Olivares, S.; Brida, G.; Genovese, M. Experimental Realization of Quantum Illumination. Phys. Rev. Lett. 2013, 110, 153603. [Google Scholar] [CrossRef]
- Lopaeva, E.D.; Ruo Berchera, I.; Olivares, S.; Brida, G.; Degiovanni, I.P.; Genovese, M. A Detailed Description of the Experimental Realization of a Quantum Illumination Protocol. Phys. Scr. 2014, 2014, 014026. [Google Scholar] [CrossRef]
- Ragy, S.; Berchera, I.R.; Degiovanni, I.P.; Olivares, S.; Paris, M.G.A.; Adesso, G.; Genovese, M. Quantifying the Source of Enhancement in Experimental Continuous Variable Quantum Illumination. J. Opt. Soc. Am. B 2014, 31, 2045. [Google Scholar] [CrossRef]
- Sanz, M.; Las Heras, U.; García-Ripoll, J.J.; Solano, E.; Di Candia, R. Quantum Estimation Methods for Quantum Illumination. Phys. Rev. Lett. 2017, 118, 070803. [Google Scholar] [CrossRef] [PubMed]
- Gregory, T.; Moreau, P.A.; Mekhail, S.; Wolley, O.; Padgett, M.J. Noise Rejection through an Improved Quantum Illumination Protocol. Sci. Rep. 2021, 11, 21841. [Google Scholar] [CrossRef]
- Bi, S.; Sheng, Z.; Zhou, Z.; Zhang, S.; Yao, J.; Deng, K. Technology Research of 1 km Quantum Lidar System. In Infrared Remote Sensing and Instrumentation XXXI; SPIE: Bellingham, WA, USA, 2023; Volume 12686, pp. 133–143. [Google Scholar] [CrossRef]
- Bi, S. Quantum Remote Sensing Theory and Practice. In Proceedings of the Infrared Remote Sensing and Instrumentation XXVI, San Diego, CA, USA, 20–22 August 2018; Volume 1076505, p. 6. [Google Scholar] [CrossRef]
- Bi, S.; Zhang, Y. The Study of Quantum Remote Sensing Principle Prototype. In International Conference on Optical and Photonic Engineering (icOPEN 2015); SPIE: Bellingham, WA, USA, 2015; Volume 9524, pp. 389–411. [Google Scholar] [CrossRef]
- David, S.S.; Gregg, J.; Alexander, V.S. Quantum Metrology, Imaging, and Communication; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar]
- Hochrainer, A.; Lahiri, M.; Lapkiewicz, R.; Lemos, G.B.; Zeilinger, A. Interference Fringes Controlled by Noninterfering Photons. Optica 2017, 4, 341. [Google Scholar] [CrossRef]
- Lahiri, M.; Lapkiewicz, R.; Lemos, G.B.; Zeilinger, A. Theory of Quantum Imaging with Undetected Photons. Phys. Rev. A—At. Mol. Opt. Phys. 2015, 92, 013832. [Google Scholar] [CrossRef]
- Lahiri, M.; Hochrainer, A.; Lapkiewicz, R.; Lemos, G.B.; Zeilinger, A. Nonclassicality of Induced Coherence without Induced Emission. Phys. Rev. A 2019, 100, 053839. [Google Scholar] [CrossRef]
- Buzas, A.; Wolff, E.K.; Benedict, M.G.; Ormos, P.; Der, A. Biological Microscopy with Undetected Photons. IEEE Access 2020, 8, 107539–107548. [Google Scholar] [CrossRef]
- Mandel, L. Coherence and Indistinguishability. Opt. Lett. 1991, 16, 1882. [Google Scholar] [CrossRef]
- Englert, B.G. Fringe Visibility and Which-Way Information: An Inequality. Phys. Rev. Lett. 1996, 77, 2154–2157. [Google Scholar] [CrossRef]
- Hariharan, P. Basics of Interferometry; Elsevier: Amsterdam, The Netherlands, 2010. [Google Scholar]
- Born, M.; Wolf, E. Principles of Optics: Electromagnetic Theory of Propagation, Interference and Diffraction of Light; Elsevier: Amsterdam, The Netherlands, 2013. [Google Scholar]
- Zetie, K.P.; Adams, S.F.; Tocknell, R.M. How Does a Mach-Zehnder Interferometer Work? Phys. Educ. 2000, 35, 46–48. [Google Scholar] [CrossRef]
- Yang, Y.; Liang, H.; Xu, X.; Zhang, L.; Zhu, S.; Ma, X.S. Interaction-Free, Single-Pixel Quantum Imaging with Undetected Photons. NPJ Quantum Inf. 2023, 9, 2. [Google Scholar] [CrossRef]
- Zhang, Y.; Gao, L.; Sit, A.; Amit, G.; Larocque, H.; Grenapin, F.; Harden, J.L.; Boyd, R.W.; Elitzur, A.C.; Cohen, E.; et al. Interaction-Free Quantum Imaging. In Nanoscale Imaging, Sensing, and Actuation for Biomedical Applications XVII; SPIE: Bellingham, WA, USA, 2020; Volume 11254, pp. 11–17. [Google Scholar] [CrossRef]
- Fuenzalida, J.; Hochrainer, A.; Lemos, G.B.; Ortega, E.A.; Lapkiewicz, R.; Lahiri, M.; Zeilinger, A. Resolution of Quantum Imaging with Undetected Photons. Quantum 2022, 6, 646. [Google Scholar] [CrossRef]
- Walter, D.; Pitsch, C.; Paunescu, G.; Lutzmann, P. Quantum Ghost Imaging for Remote Sensing. Phys. Environ. Sci. Eng. 2019, 2023, 32. [Google Scholar] [CrossRef]
- Kaur, M.; Singh, M. Quantum Imaging of a Polarisation Sensitive Phase Pattern with Hyper-Entangled Photons. Sci. Rep. 2021, 11, 23636. [Google Scholar] [CrossRef]
- Shafi, K.M.; Padhye, A.; Chandrashekar, C.M. Quantum Illumination Using Polarization-Path Entangled Single Photons for Low Reflectivity Object Detection in a Noisy Background. Opt. Express 2023, 31, 32093. [Google Scholar] [CrossRef]
- Prabhu, A.V.; Suri, B.; Chandrashekar, C.M. Hyperentanglement-Enhanced Quantum Illumination. Phys. Rev. A 2021, 103, 052608. [Google Scholar] [CrossRef]
- Defienne, H.; Ndagano, B.; Lyons, A.; Faccio, D. Polarization Entanglement-Enabled Quantum Holography. Nat. Phys. 2021, 17, 591–597. [Google Scholar] [CrossRef]
- Yang, J.Z.; Li, M.F.; Chen, X.X.; Yu, W.K.; Zhang, A.N. Single-Photon Quantum Imaging via Single-Photon Illumination. Appl. Phys. Lett. 2020, 117, 214001. [Google Scholar] [CrossRef]
- Kim, J.; Jeong, T.; Lee, S.Y.; Kim, D.Y.; Kim, D.; Lee, S.; Ihn, Y.S.; Kim, Z.; Jo, Y. Heralded Single-Pixel Imaging with High Loss-Resistance and Noise-Robustness. Appl. Phys. Lett. 2021, 119, 244002. [Google Scholar] [CrossRef]
- Johnson, S.; McMillan, A.; Torre, C.; Frick, S.; Rarity, J.; Padgett, M. Single-Pixel Imaging with Heralded Single Photons. Opt. Contin. 2022, 1, 826. [Google Scholar] [CrossRef]
- Lotfipour, H.; Sobhani, H.; Khodabandeh, M. Quantum Diagnosis of Cancer with Heralded Single Photons. Laser Phys. Lett. 2022, 19, 105603. [Google Scholar] [CrossRef]
- Varnavski, O.; Gunthardt, C.; Rehman, A.; Luker, G.D.; Goodson, T. Quantum Light-Enhanced Two-Photon Imaging of Breast Cancer Cells. J. Phys. Chem. Lett. 2022, 13, 2772–2781. [Google Scholar] [CrossRef]
- Moodley, C.; Forbes, A. Advances in Quantum Imaging with Machine Intelligence. Laser Photonics Rev. 2024, 2300939. Available online: https://onlinelibrary.wiley.com/doi/full/10.1002/lpor.202300939 (accessed on 25 January 2024). [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).