Abstract
This study addresses the problem of fractional-order nonlinear containment control of heterogeneous multi-agent systems within a leader–follower framework, focusing on the impact of False Data Injection (FDI) attacks. By employing adaptive mechanisms and fuzzy logic, the suggested method enhances system resilience, ensuring reliable coordination and stability even in the presence of deceptive disturbances. To deal with these uncertainties, our controller makes use of interval type-II (IT2) fuzzy sets, and we create matrix equalities and inequalities to account for the asymmetry of Laplace matrices. Also, we use the Lyapunov functions for the stability analysis of our system. Lastly, we explain the numerical simulations for the effectiveness of our theoretical results, and these simulated examples are used to verify the effectiveness of our approach and designed model.
1. Introduction
The rising incorporation of digital processing and communication technologies in the advanced era causes these systems to be more vulnerable to possible chance attacks, which may cause a loss [1,2]. If the control center uses these modified measurements, it might be misled about the real grid-operating circumstances, leading to poor control decisions [3,4]. In this work, we provide a multi-agent system specifically designed to detect FDI assaults intended to undermine the power-grid status estimation [5,6]. A major substation and its neighboring substations that are directly connected to it comprise each of the smaller systems that make up the electrical network [7]. Since substations make use of widely accessible computing and communication technologies, we can install software agents in each substation and make them interoperable [8,9]. These agents allow substations in the same sub-system to communicate meter readings [10]. For each unique sub-system, each agent evaluates the state [11]. The state-estimate findings from each sub-system should normally match the results for the entire grid in the absence of FDI assaults [12]. For the whole grid’s state estimate, the stolen data may, however, avoid Bad Data Detection (BDD) checks in the event of an FDI assault [13,14]. Inconsistencies and compromised measurements are identified with the aid of local state estimate performed by the agent of each sub-system [15,16,17]. FDI assaults are made more difficult by the fact that they depend on certain topological data about the power grid, such as transmission line characteristics and substation connections [18]. These data vary based on the sub-system [19,20]. Generally speaking, assaults against multi-agent dynamical systems fall into two types: damage and deception attacks, which modify the information that is communicated, and Denial of Service (DoS) attacks, which cause information to be lost or delayed [21]. Particularly known to do major harm are deception assaults [22,23]. Examining deception attacks is therefore essential, particularly FDI assaults, which entail the insertion of false data to modify transmitted information [24]. Support for online reprogramming and debugging via host computer-based unprotected communication protocols is required before multi-agent dynamical systems may be used in real-world applications [25,26]. Because of this flaw, attackers can reprogram control rules for several agents and discover cryptographic keys [27]. Because too many compromised agents make it hard to maintain system stability or reach consensus, it is helpful to study scenarios where the number of compromised agents is restricted [28,29]. Consequently, when attackers with limited skills damage many agents, it is crucial to investigate the possible effects of these adversaries on consensus [30]. Much research has been conducted on multi-agent dynamical systems under FDI assaults that aim at consensus, especially when the number of compromised actors is limited [31,32]. A few scholars have created models that restrict the overall quantity of compromised agents inside the network [33,34]. Others established models in which the neighbors of each agent can have a finite number of compromised agents by introducing the notion of network resiliency [35]. Furthermore, by compromising a small number of individuals in each iteration, some research has investigated non-convex optimization issues as a means of destabilizing systems. Most of the current research examines state interactions that are either unidimensional or two-dimensional, evaluating system performance in relation to particular assault tactics. Furthermore, not much research has been done on how adversaries with limited resources should choose which agents to compromise to cause the most harm possible while using FDI assaults. Though FDI attack design challenges in state estimation have been extensively studied, the nature of these difficulties differs. Hence, multi-agent dynamical systems cannot directly benefit from these insights. Researchers have focused much emphasis on FDI attacks since they are common in control systems. These attacks deliver false signals to the receiving terminal, compromising the accuracy and integrity of the data. The dynamics of the system under FDI assaults may be modeled by introducing the deviations brought about by incorrect info into the usual evolution equation of the system. In the early research, FDI assaults were examined in relation to power system state estimation issues. The situations in which FDI assaults can subvert a system that has a Linear-Quadratic-Gaussian (LQG) controller and a Kalman filter while avoiding failure detection systems were studied in more detail. A sufficient and required condition for networked control systems to be insecure to FDI assaults has been found in other work. This condition allows attackers to evade anomaly detectors and produce large estimate mistakes. To establish whether to trust the obtained information, additional research concentrated on distributed filtering under FDI assaults and created security measures for sensors connected via communication networks. A neural network structure was developed by some researchers to identify abnormalities brought on by FDI assaults, and they also built a Kalman filter-based observer to estimate the states of multi-agent systems [36,37]. The physical and cyber layers of the system are both affected by FDI and jamming assaults, which were the subject of further study. Resilient attack detection and estimation techniques were created to consistently identify FDI attacks and precisely estimate the status of the system [38,39].
Recent advancements in control systems have introduced several innovative approaches. In [40] researchers developed a hybrid reinforcement Q-learning method for fuzzy control of discrete-time nonlinear Markov jump systems, addressing system uncertainties. A fuzzy-model-based optimal control approach was proposed using integral reinforcement learning for nonlinear Markov jump systems, enhancing control accuracy [41]. Moreover, In [42] authors tackled composite anti-disturbance control in hidden Markov jump systems with multi-sensor setups, concentrating on resilience against replay attacks.
Motivated by our previous discussion, we contribute to the field by studying fractional-order nonlinear systems under false data injection attacks within the framework of weighted directed graphs. Notably, our research addresses a significant gap in the literature concerning containment control in fractional-order multi-agent systems under false data injection attacks. To fill this gap, we propose a novel approach utilizing fractional-order Lyapunov methods. Our contributions are listed below.
- The development of a novel fuzzy adaptive control strategy specifically designed for nonlinear multi-agent systems under FDI attacks
- A detailed stability analysis that validates the effectiveness of the proposed method
- Extensive simulations that compare our method with existing approaches show significant improvements in both adaptability and robustness.
The structure of the remaining content is as follows:
- We introduce our work in Section 1.
- In Section 2, graph theory is explained for the communication of agents. Some lemmas and definitions are provided.
- Section 3 provides a system model that explains the dynamic of leaders and followers.
- In Section 4, main results are presented.
- Section 5 provides a numerical experiment, and two examples are provided for the effectiveness of the results.
- In Section 6, we draw conclusions.
The framework of the proposed method is illustrated in Figure 1.
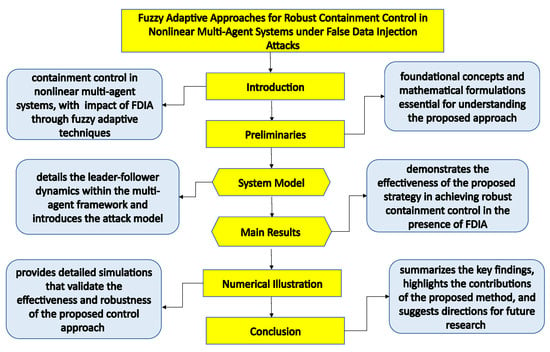
Figure 1.
Frame work of the proposed method.
2. Preliminaries
This study investigates a multi-agent system consisting of R followers and Q leaders. The system’s network is characterized by a weighted digraph where denotes the set of nodes, where node corresponds to the p-th participants. We proceed under the assumption that the set includes the initial R nodes, denoted as followers. Similarly, the set encompasses the remaining Q nodes, denoted as leaders. The set indicates the directed edges, where means that agent can receive information from agent , indicating a directed path from agent to agent . The adjacency matrix is defined such that if , then ; otherwise, . The point to the set , in terms of their separation, is denoted by , defined in the Euclidean norm sense as .
2.1. Definition and Lemmas
Definition 1
([43]). The Riemann-Liouville fractional integral with order γ is defined for an integrable function as
where is the Gamma function given by .
Definition 2
([43]). For a function , the Caputo derivative of fractional order γ is defined as
where and . When , the Caputo derivative simplifies to .
Lemma 1
([44]). If and , then
Lemma 2
([45]). Given that is a continuous function, then
where , .
Lemma 3
([43]). Assume is a differentiable vector function. For any , we have
where is a symmetric matrix that is positive definite, and γ is a fractional exponent satisfying .
2.2. Introduction to Interval Type-II Fuzzy Systems
When it comes to the interval type-II fuzzy logic system, the IF-THEN fuzzy rule for the -th case can be represented as:
and z represent the fuzzy logic system’s inputs and outputs, respectively. The IT2 fuzzy set for the antecedent portion is , while the weighing interval set for the consequent part is .
To determine the system’s ultimate output, we employ the enhanced Biglarbegian –Melek–Mendel (BMM) direct defuzzification approach [46]. The resultant system output is represented as:
where is a weighting factor. where and represent both the upper membership function (UMF) and the lower membership function (LMF). The regulatory factor meets the criterion . Construct the fuzzy fundamental functions as follows:
Finally, the fuzzy logic system can be stated as follows:
where , , , and .
Remark 1.
When implementing Integral Type-II fuzzy systems theory in practical scenarios, an essential phase involves model reduction and defuzzification. The conventional Karnik-Mendel (KM) algorithm is widely utilized for this purpose [47]. Nevertheless, practical applications of the KM algorithm are hindered by several limitations, including iterative requirements and challenges in conducting stability analyses for controllers. To address these shortcomings, Biglarbegian et al. introduced the BMM direct defuzzification method, which enhances its suitability for controller design and stability analysis. This study incorporates a tuning factor alongside unknown parameters, therefore alleviating specific constraints associated with tuning [46].
Lemma 4
([46]). Considering for and every τ, the following inequality is true:
where σ is a constant that satisfies , namely .
Lemma 5
([46]). (Barbalat’s Lemma) If is uniformly continuous over the interval , and exists and is bounded, then .
3. System Model
Consider an uncertain fractional-order nonlinear multi-agent system with Q leaders and R followers. The dynamics p-th follower are shown as follows:
where:
- denotes the fractional derivative of order ,
- is the state vector of the p-th follower,
- represents the nonlinear dynamics of the system,
- is the saturated control input,
- denotes false data injected by the adversary.
The saturation function is defined as:
Here and and are the known upper and lower bounds of (). The system block diagram is presented in Figure 2.
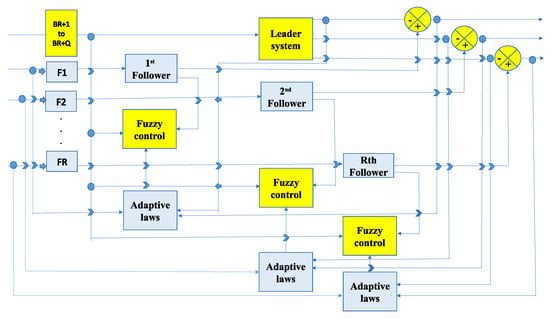
Figure 2.
System block diagram.
Figure 2 demonstrates the complete structure of the leader–follower dynamics within our multi-agent system, integrating the connection between the fuzzy controller and adaptive laws.
- Leader Dynamics: In the diagram, the leader dynamics are represented as the driving force of the system. The leader agents provide the desired trajectories or reference signals that guide the follower agents. These trajectories represent the target behaviors that the followers aim to achieve. The leader dynamics set the objectives for the system, which are tracked by the followers through feedback control mechanisms.
- Follower Dynamics: The follower agents are represented in the block diagram as systems that track the leaders’ behavior. Each follower adjusts its state based on both its local interactions and the leader’s state. The dynamics of these followers are influenced by the control inputs received from the fuzzy controller. Followers work together to reach the leaders’ trajectories while maintaining a desired formation or coordinated behavior.
- Fuzzy Controller: The fuzzy controller is shown as the primary decision-making block that processes input information from both the leaders and followers. It maps the input errors (the difference between the leader and follower states) to appropriate control actions using fuzzy logic rules. The fuzzy controller helps manage uncertainties and nonlinearities in the system by generating adaptive control signals that adjust the behavior of the followers.
- Adaptive Laws: The adaptive laws are depicted as a mechanism that adjusts the parameters of the fuzzy controller over time. They allow the system to adapt to unknown or changing dynamics within the leader–follower interactions, ensuring robustness against disturbances or modeling inaccuracies. Adaptive laws ensure that the control gains are modified continuously based on system performance, allowing the system to remain stable and achieve the desired tracking performance.
3.1. Attack Model
The false data injected by the adversary, denoted as , is defined as follows since the agents are compromised simultaneously by the adversary:
where represents the specific attack strategy. Furthermore, the dynamic interaction between agents with m-dimensional states significantly enlarges the attack space.
3.1.1. Nature of FDI Attacks
FDI attacks are characterized by the deliberate insertion of erroneous data into the system’s measurements or inputs. These attacks can originate from various sources and utilize different techniques to falsify data. The objective of the attacker is to degrade system performance or cause undesirable behavior.
3.1.2. Mechanisms of Injection
Attacks are typically implemented by altering the data transmitted to the system’s sensors or control inputs. For example, attackers may inject false readings that mislead the system’s estimation algorithms, leading to incorrect control actions and compromised system stability.
3.2. Impact on System Dynamics
The presence of FDI attacks can alter the system’s state variables and control inputs, causing deviations from expected behavior. Such disruptions can lead to significant performance degradation, including reduced accuracy in state estimation and control.
The dynamic of leader is described as follows:
where:
- is the state vector of the k-th leader,
- represents the dynamics of the leader.
In this context, denote the estimated values of , and , respectively, here is a positive number. The term represents the projected amount of the combined unknown parameter, which will be described further. The function meets the condition . The projection operator is defined as follows:
with
where specifies a boundary, and specifies a boundary tolerance.
Assumption 1.
The leader initiates at least one directed path for each follower. Furthermore, no other agent influences the leader, indicated by the absence of directed paths leading to the leader from any other agent.
Assumption 2.
The adversary can inject false data without being detected, and the false data are bounded.
Lemma 6.
Under Assumption 1, the Laplacian matrix L has the following structure:
where
- , , , ,
- , , , , .
- The set of values represents the adjacent neighbors of agents .
Remark 2.
The structure of the matrix is a nonsingular M-matrix. Each entry of is nonnegative with each row of sums to 1.
Remark 3.
Define
Based on Remark 2, one has
Assumption 3.
There exists a closed convex set , such that for any , there is a function for , Here is an uncertain quantity.
This paper aims to develop controllers for follower agents to attain containment control while respecting certain input constraints. Specifically, for each follower agent and any initial state :
- The position is guided to converge towards the convex hull defined by the positions of the leader agents. This convergence is expressed by:where denotes the convex hull formed by the positions of the leader agents.
- The controller of each follower agent p is constrained to remain within a specified range, . Here, and are predetermined constants, with being negative and being positive.
Remark 4.
To address the challenge of robust containment control in nonlinear multi-agent systems under (FDI) attacks, the key issue is found in the system’s vulnerability to malicious data manipulation, which can severely affect stability and performance. Traditional control techniques often assume accurate data and linear system behavior, which are not realistic assumptions in the situation of FDI attacks and nonlinear dynamics. These problems necessitate a more advanced method that can adapt to uncertainties and maintain control targets even under adverse conditions.
4. Main Results
Since communication between agents in a multi-agent system is local, therefore the distributed controller () can only use the error between neighboring agents. The consensus signal of error for the p-th agent among neighboring nodes is defined as follows:
The vector-based type of the consensus tracking error can be stated as follows:
The function , where . The saturation function is denoted by .
The function , and
The approximation of the unknown smooth function () using (6)–(9) a type-II fuzzy logic system is given by:
where the ideal parameters and are determined by:
where is added to account for the discrepancy between the actual function and its approximation by the fuzzy logic system. The system of fuzzy logic has been demonstrated to have general approximation capabilities. Thus, it is safe to conclude that the approximation is restricted. Specifically:
where . To deal with the saturation function, we make a certain hypothesis [46]:
The function , and represent an unknown constant.
Theorem 1.
In fractional-order multi-agent system which is defined by (11)–(16), the followers can converge to the polyhedron formed by multiple leaders under controller (17) and corresponding parameters defined by (18) and (19) if there exist positive numbers , and a positive definite symmetric matrix W, satisfying the following condition:
Proof.
Let . using the definition of in (32), we obtain:
where , . Given the system (35), create the following Lyapunov candidate function:
where , , , .
First, for , taking the derivative on both sides and using Lemma 3 and condition (33) and also using controller (17), we obtain:
Given and , where the boundedness condition is known to exist such that
using above inequality in (39)
Now, taking derivative of :
By combining the parameters of the projection operator (19)–(20) as well as condition (34) and Lemma 4, we obtain:
Based on Lemma 1, integrating both sides of equation (44), we obtain:
Now using Definition 1, we have following result:
Thus,
Moreover,
Therefore,
is bounded.
According to Lemma 5, there exists
so
Using definition of we have
i.e.,
Theorem 2.
In a fractional-order multi-agent system, which is defined by (11)–(16) (considering undirected topology), the followers can converge to the polyhedron formed by multiple leaders under controller (17) and corresponding parameters defined by (18) and (19) if there exist positive numbers , and a positive definite symmetric matrix W, satisfying the following condition:
Proof.
The system leads to a weighted graph, which is a directed graph, too, in Theorem 1. If the system’s topology is connected undirected graph, then only the communication topology of the agents is changed, and the proof is completed similarly. □
Remark 5.
In [48,49], adaptive fuzzy containment control for nonlinear multi-agent systems is considered, which typically deals with integer-order derivatives in the system’s dynamics, emphasizing the handling of input delays. In contrast, our work involves fractional-order derivatives to model more complex dynamics and improve system robustness against data injection attacks. Compared to [50,51], which addresses adaptive containment control for fractional-order nonlinear multi-agent systems with time-varying parameters, our approach is better because it explicitly addresses the critical challenge of cybersecurity by enhancing system resilience against false data injection attacks, an important concern in securing advanced communication networks.
5. Numerical Illustration
Example 1.
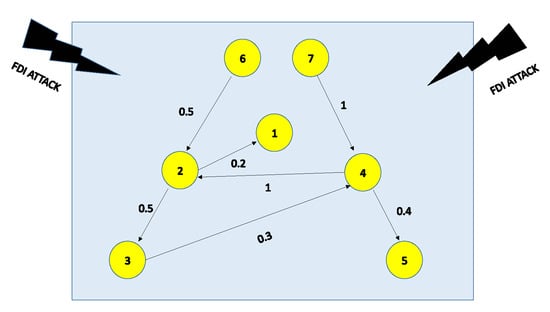
The following section showcases two leaders and five followers to highlight the efficacy of the containment control algorithm outlined in this study. The network structure graph is depicted in Figure 3. In this visual representation, nodes 1, 2, 3, 4, and 5 correspond to followers, while nodes 6 and 7 are indicative of leaders.

Figure 3.
Directed Network topology of agents.
According to Figure 3, we can obtain,
Now using Lemma 6 the Laplacian matrix is
let , and also take
Controller Design
Given the parameter boundaries and , and the control constraints for , the fuzzy membership functions are defined as follows:
There are constants , , , and a matrix W given by:
which ensures that conditions (33) and (34) are satisfied.
The simulation results are presented in Figures. Figure 4 demonstrates that the position tracking error and the velocity tracking error of the follower approaches zero, implying that the follower’s location will eventually align with the polyhedron created by the positions of the leaders. The follower velocity will ultimately align with the polyhedron formed by the velocities of the leaders.
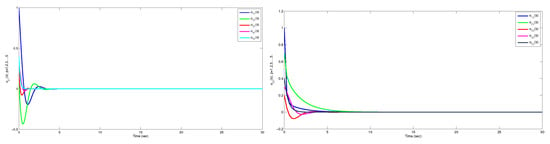
Figure 4.
Position tracking error and velocity tracking error using directed topology.
Example 2.
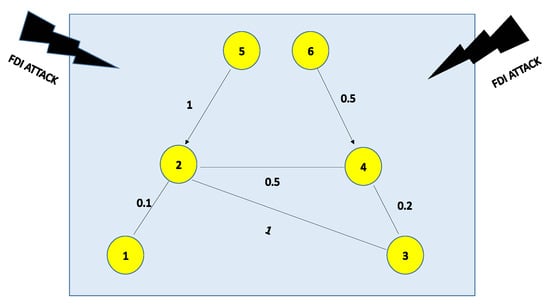
Consider a fractional-order system multi-agent system with 2 leaders and 4 followers. The undirected topology is described in Figure 5 in which nodes 5 and 6 represent leaders and 1, 2, 3, and 4 are followers.

Figure 5.
Undirected Network topology of agents.
According to Figure 5, we can obtain
Now using Lemma 6 the Laplacian matrix is
let , and also take
Controller Design
Given the parameter boundaries and , and the control constraints for , the fuzzy membership functions are defined as follows:
There are constants , , , and a matrix W given by:
which ensures that conditions (33) and (34) are satisfied.
The simulation results are presented in Figures. Figure 6 demonstrates that the position tracking error and the velocity tracking error of the follower approaches zero, implying that the follower’s location will eventually align with the polyhedron created by the positions of the leaders. The follower velocity will ultimately align with the polyhedron formed by the velocities of the leaders. Figure 7 shows the step response under the FDI attack and control performance under no attack. Figure 8 shows the time response for agents. The attack signal is present in Figure 9.
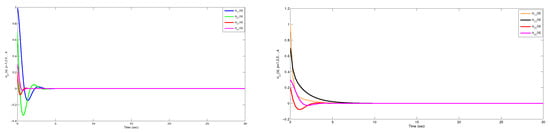
Figure 6.
Position tracking error and velocity tracking error using undirected topology.
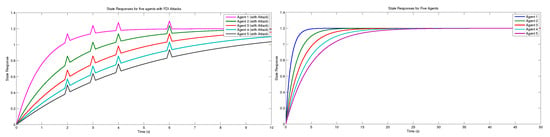
Figure 7.
Shows the state response of the system under FDI attack and control performance with no attack.
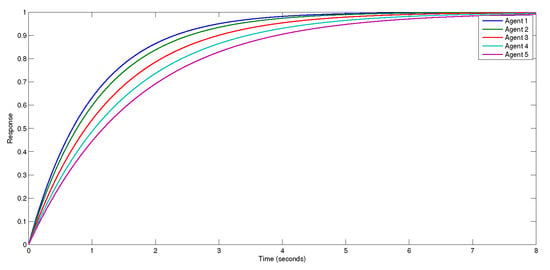
Figure 8.
Shows the time response for agents.
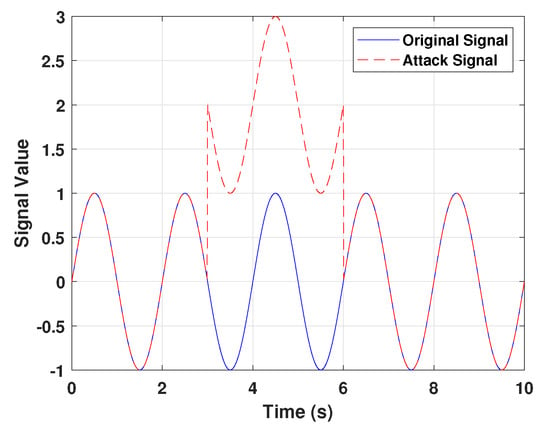
Figure 9.
False data injection attack signal.
6. Conclusions
In this paper, we have tackled the containment control issue in fractional-order nonlinear heterogeneous multi-agent systems operating within a leader–follower structure, particularly under the threat of FDI attacks. By developing a distributed fuzzy adaptive controller that employs interval type-II (IT2) fuzzy sets, we successfully addressed uncertainties introduced by these attacks. Our methodology incorporates matrix equalities and inequalities to manage the asymmetrical properties of Laplace matrices inherent in these systems. Through rigorous stability analysis using Lyapunov functions, we demonstrated the robustness of our controller design. The practicality and effectiveness of our approach are underscored by simulations, which show its capability to counteract the disruptive impact of FDI attacks and maintain stable containment control. This work highlights the importance of utilizing local information for each agent and its neighbors, proving that our strategy is both feasible and effective for real-world applications.
Author Contributions
Conceptualization, A.A. and A.U.K.N.; Methodology, M.M.A.A.-S.; Software, W.U.H.; Validation, W.U.H.; Formal analysis, M.M.A.A.-S.; Investigation, W.U.H.; Resources, S.R.; Writing—original draft, A.A. and S.R.; Visualization, S.R.; Supervision, A.U.K.N.;writing—review and editing, A.A. and A.U.K.N.; Project administration, M.M.A.A.-S.; Funding acquisition, M.M.A.A.-S. All authors have read and agreed to the published version of the manuscript.
Funding
This work is funded by Deanship of Research and Graduate Studies at King Khalid University through Large Research Project under grant number RGP2/302/45.
Data Availability Statement
No data was used for the reserch described in this article.
Acknowledgments
The authors extend their appreciation to the Deanship of Research and Graduate Studies at King Khalid University for funding this work through Large Research Project under grant number RGP2/302/45.
Conflicts of Interest
I declare that the authors have no competing interests as defined by Nature Research, or other interests that might be perceived to influence the results and/or discussion reported in this paper.
References
- Luo, X.; Zhao, C.; Fang, C.; He, J. Submodularity-based false data injection attack scheme in multi-agent dynamical systems. Automatica 2024, 160, 111426. [Google Scholar] [CrossRef]
- Li, J.; Sun, Y.; Su, Q. Security control of integral sliding modes for multi-agent systems under false data injection attacks. J. Frankl. Inst. 2024, 361, 106613. [Google Scholar] [CrossRef]
- Lv, Y.; Liu, Y.J.; Liu, L.; Yu, D.; Chen, Y. Distributed Nash equilibrium searching for multi-agent games under false data injection attacks. Neurocomputing 2024, 570, 127134. [Google Scholar] [CrossRef]
- Fei, C.; Shen, J.; Qiu, H.; Zhang, Z.; Xing, W. Learning Secure Control Design for Cyber-Physical Systems under False Data Injection Attacks. IEEE Trans. Ind.-Cyber-Phys. Syst. 2024, 2, 60–68. [Google Scholar] [CrossRef]
- Sun, L.; Wu, T.; Zhang, Y. A defense strategy for false data injection attacks in multi-agent systems. Int. J. Syst. Sci. 2023, 54, 3071–3084. [Google Scholar] [CrossRef]
- Yang, Y.; Wang, X.; Li, Y.; Gorbachev, S.; Yue, D. Adaptive resilient tracking control with dual-terminal dynamic-triggering for a linear multi-agent system against false data injection attacks. IEEE Trans. Signal Inf. Process. Over Netw. 2023, 9, 1–12. [Google Scholar] [CrossRef]
- Wang, M.; Hu, J.; Cao, J. Resilient Consensus Control for Linear Multi-agent System Against the False Data Injection Attacks. Int. J. Control. Autom. Syst. 2023, 21, 2112–2123. [Google Scholar] [CrossRef]
- Wang, Z.; Shi, S.; He, W.; Xiao, M.; Cao, J.; Gorbachev, S. Observer-based asynchronous event-triggered bipartite consensus of multi-agent systems under false data injection attacks. IEEE Trans. Control. Netw. Syst. 2023, 10, 1603–1615. [Google Scholar] [CrossRef]
- Duan, Z.; Wei, A.; Zhang, X.; Mu, R. Sampled-data consensus control for nonlinear time-delay multi-agent systems under false data injection attacks. Nonlinear Dyn. 2023, 111, 12253–12266. [Google Scholar] [CrossRef]
- Hu, J.; Sun, Q.; Zhai, M.; Wang, B. Privacy Preserving Consensus Strategy for Secondary Control in Microgrids Against Multi-link False Data Injection Attacks. IEEE Trans. Ind. Inform. 2023, 19, 10334–10343. [Google Scholar] [CrossRef]
- Burgos-Mellado, C.; Zuñiga-Bauerle, C.; Muñoz-Carpintero, D.; Arias-Esquivel, Y.; Càrdenas-Dobson, R.; DragiČević, T.; Watson, A. Reinforcement learning-based method to exploit vulnerabilities of false data injection attack detectors in modular multilevel converters. IEEE Trans. Power Electron. 2023, 38, 8907–8921. [Google Scholar] [CrossRef]
- Habib, A.A.; Hasan, M.K.; Alkhayyat, A.; Islam, S.; Sharma, R.; Alkwai, L.M. False data injection attack in smart grid cyber physical system: Issues, challenges, and future direction. Comput. Electr. Eng. 2023, 107, 108638. [Google Scholar] [CrossRef]
- Zhu, H.; Xu, L.; Bao, Z.; Liu, Y.; Yin, L.; Yao, W.; Wu, L. Secure Control Against Multiplicative And Additive False Data Injection Attacks. IEEE Trans. Ind.-Cyber-Phys. Syst. 2023, 1, 92–100. [Google Scholar] [CrossRef]
- Chen, L.; Tong, S. Observer-based adaptive fuzzy consensus control of nonlinear multi-agent systems encountering deception attacks. IEEE Trans. Ind. Informatics. 2023, 20, 1808–1818. [Google Scholar] [CrossRef]
- Zhang, Z.; Ma, T.; Su, X.; Ma, X. Impulsive Consensus of One-Sided Lipschitz Multi-Agent Systems with Deception Attacks and Stochastic Perturbation. IEEE Trans. Artif. Intell. 2023, 5, 1328–1338. [Google Scholar] [CrossRef]
- Pan, Z.; Chi, R.; Hou, Z. Distributed Model-Free Adaptive Predictive Control for MIMO Multi-Agent Systems With Deception Attack. IEEE Trans. Signal Inf. Process. Over Networks. 2024, 10, 32–47. [Google Scholar] [CrossRef]
- Ying, C.; Zheng, R.; Wu, Y.; Xu, M.; Zhang, W.A. Privacy-preserving adaptive resilient consensus for multi-agent systems under cyber attacks. IEEE Trans. Ind. Informatics. 2023, 20, 1630–1640. [Google Scholar] [CrossRef]
- Kharchouf, I.; Mohammed, O.A. Controller Hardware-in-the-Loop Testbed of a Distributed Consensus Multi-Agent System Control under Deception and Disruption Cyber-Attacks. Energies 2024, 17, 1669. [Google Scholar] [CrossRef]
- Niu, B.; Gao, Y.; Zhang, G.; Zhao, X.; Wang, H.; Wang, D.; Liu, C. Adaptive Prescribed-Time Consensus Tracking Control Scheme of Nonlinear Multi-Agent Systems Under Deception Attacks. IEEE Trans. Autom. Sci. Eng. 2024. [CrossRef]
- Wan, Q.; Chen, W.H.; Lu, X. Secure consensus tracking of multi-agent systems with network-induced delays under deception attacks via guaranteed performance impulsive control. Nonlinear Dyn. 2023, 111, 12213–12232. [Google Scholar] [CrossRef]
- Ahmed, Z.; Ali, R.; Zhang, W. H2 resilient consensus control of multiagent systems under deception attack. IEEE Trans. Circuits Syst. II Express Briefs 2023, 70, 2530–2534. [Google Scholar] [CrossRef]
- Janani, V.M.; Visakamoorthi, B.; Muthukumar, P.; Hur, S.H. Reachable set estimation of multi-agent systems under packet losses and deception attacks. J. Appl. Math. Comput. 2024, 70, 3555–3574. [Google Scholar] [CrossRef]
- Gao, Y.; Zhou, W.; Riu, B.; Kao, Y.; Wang, H.; Sun, R. Distributed Prescribed-Time Consensus Tracking for Heterogeneous Nonlinear Multi-Agent Systems Under Deception Attacks and Actuator Faults. IEEE Trans. Autom. Sci. Eng. 2023. [Google Scholar] [CrossRef]
- Han, S.; Zhu, H.; Zhong, Q.; Shi, K.; Kwon, O.M. Secure Sampled-Data Consensus of Multi-Agent Systems Under Asynchronous Deception Attacks With Application to Unmanned Surface Vehicles. IEEE Trans. Intell. Transp. Syst. 2023, 25, 5462–5473. [Google Scholar] [CrossRef]
- Sayghe, A.; Hu, Y.; Zografopoulos, I.; Liu, X.; Dutta, R.G.; Jin, Y.; Konstantinou, C. Survey of machine learning methods for detecting false data injection attacks in power systems. IET Smart Grid 2020, 3, 581–595. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A. Comprehensive survey and taxonomies of false data injection attacks in smart grids: Attack models, targets, and impacts. Renew. Sustain. Energy Rev. 2022, 163, 112423. [Google Scholar] [CrossRef]
- Aboelwafa, M.M.; Seddik, K.G.; Eldefrawy, M.H.; Gadallah, Y.; Gidlund, M. A machine-learning-based technique for false data injection attacks detection in industrial IoT. IEEE Internet Things J. 2020, 7, 8462–8471. [Google Scholar] [CrossRef]
- Choraria, M.; Chattopadhyay, A.; Mitra, U.; Ström, E.G. Design of false data injection attack on distributed process estimation. IEEE Trans. Inf. Forensics Secur. 2022, 17, 670–683. [Google Scholar] [CrossRef]
- Pang, Z.H.; Fan, L.Z.; Sun, J.; Liu, K.; Liu, G.P. Detection of stealthy false data injection attacks against networked control systems via active data modification. Inf. Sci. 2021, 546, 192–205. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. False data injection attacks against state estimation without knowledge of estimators. IEEE Trans. Autom. Control. 2022, 67, 4529–4540. [Google Scholar] [CrossRef]
- Li, Y.; Wei, X.; Li, Y.; Dong, Z.; Shahidehpour, M. Detection of false data injection attacks in smart grid: A secure federated deep learning approach. IEEE Trans. Smart Grid 2022, 13, 4862–4872. [Google Scholar] [CrossRef]
- Zhang, T.Y.; Ye, D. False data injection attacks with complete stealthiness in cyber–physical systems: A self-generated approach. Automatica 2020, 120, 109117. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, J.; Chen, B. Detecting false data injection attacks in smart grids: A semi-supervised deep learning approach. IEEE Trans. Smart Grid 2020, 12, 623–634. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. False data injection attacks against state estimation in the presence of sensor failures. Inf. Sci. 2020, 508, 92–104. [Google Scholar] [CrossRef]
- Lakshminarayana, S.; Kammoun, A.; Debbah, M.; Poor, H.V. Data-driven false data injection attacks against power grids: A random matrix approach. IEEE Trans. Smart Grid 2020, 12, 635–646. [Google Scholar] [CrossRef]
- Abbaspour, A.; Yen, K.K.; Noei, S.; Sargolzaei, A. Detection of fault data injection attack on uav using adaptive neural network. Procedia Comput. Sci. 2016, 95, 193–200. [Google Scholar] [CrossRef]
- Luo, X.; Bai, M.; Wang, X.; Sun, X. Square-root Extended Kalman Filter-based Detection of False Data Injection Attack in Smart Grids. In Proceedings of the 2021 IEEE 5th Conference on Energy Internet and Energy System Integration (EI2), Taiyuan, China, 22–24 October 2021; pp. 2376–2381. [Google Scholar]
- Ju, Z.; Zhang, H.; Li, X.; Chen, X.; Han, J.; Yang, M. A survey on attack detection and resilience for connected and automated vehicles: From vehicle dynamics and control perspective. IEEE Trans. Intell. Veh. 2022, 7, 815–837. [Google Scholar] [CrossRef]
- Zhou, J.; Chen, B.; Yu, L. Intermediate-variable-based estimation for FDI attacks in cyber-physical systems. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 2762–2766. [Google Scholar] [CrossRef]
- Wang, J.; Wu, J.; Shen, H.; Cao, J.; Rutkowski, L. Fuzzy H∞ control of discrete-time nonlinear Markov jump systems via a novel hybrid reinforcement Q-learning method. IEEE Trans. Cybern. 2022, 53, 7380–7391. [Google Scholar] [CrossRef]
- Shen, H.; Wang, Y.; Wang, J.; Park, J.H. A fuzzy-model-based approach to optimal control for nonlinear Markov jump singularly perturbed systems: A novel integral reinforcement learning scheme. IEEE Trans. Fuzzy Syst. 2023, 31, 3734–3740. [Google Scholar] [CrossRef]
- Wang, J.; Wang, D.; Yan, H.; Shen, H. Composite Anti-Disturbance H∞ Control for Hidden Markov Jump Systems With Multi-Sensor Against Replay Attacks. IEEE Trans. Autom. Control. 2023, 59, 1760–1766. [Google Scholar]
- Khan, A.; Niazi, A.U.K.; Rehman, S.; Ahmed, S. Hostile-based bipartite containment control of nonlinear fractional multi-agent systems with input delays: A signed graph approach under disturbance and switching networks. Aims Math. 2024, 9, 12678–12699. [Google Scholar] [CrossRef]
- Huong, D.C.; Thuan, M.V. Mixed H∞ and passive control for fractional-order nonlinear systems via LMI approach. Acta Appl. Math. 2020, 170, 37–52. [Google Scholar] [CrossRef]
- Srivastava, H.M. Fractional-order derivatives and integrals: Introductory overview and recent developments. Kyungpook Math. J. 2020, 60, 73–116. [Google Scholar]
- Xia, Z.; Mou, J. IT2 fuzzy adaptive containment control for fractional-order heterogeneous multi-agent systems with input saturation. J. Intell. Fuzzy Syst. 2023, 45, 4361–4370. [Google Scholar] [CrossRef]
- Mendel, J.M. Explainable Uncertain Rule-Based Fuzzy Systems; Springer: Berlin/Heidelberg, Germany, 2023. [Google Scholar]
- Deng, X.; Cui, Y. Adaptive fuzzy containment control for nonlinear multi-agent systems with input delay. Int. J. Syst. Sci. 2021, 52, 1633–1645. [Google Scholar] [CrossRef]
- Li, Y.; Qu, F.; Tong, S. Observer-based fuzzy adaptive finite-time containment control of nonlinear multiagent systems with input delay. IEEE Trans. Cybern. 2020, 51, 126–137. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, H.; Wang, Y.; Liang, H. Adaptive containment control for fractional-order nonlinear multi-agent systems with time-varying parameters. IEEE/CAA J. Autom. Sin. 2022, 9, 1627–1638. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, H.; Sun, J.; Wang, Y. Event-triggered adaptive finite-time containment control for fractional-order nonlinear multiagent systems. IEEE Trans. Cybern. 2022, 54, 1250–1260. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).