Secure Internet Financial Transactions: A Framework Integrating Multi-Factor Authentication and Machine Learning
Abstract
1. Introduction
- First: offering a model that can be implemented in the banking sector, e-commerce purchasing websites, and online payment systems.
- Second: using ML as part of MFA will achieve the highest possible security.
- Third: it shows the best way to use MFA conveniently.
- Fourth: provide a comprehensive analysis of the most appropriate ML algorithms and training methods to use in combination with MFA for online transactions.
- Fifth: the possibility of modifying the ML algorithm to comply with the requirements of any electronic system and integrating this algorithm with MFA to provide secure access to data.
2. Materials and Methods
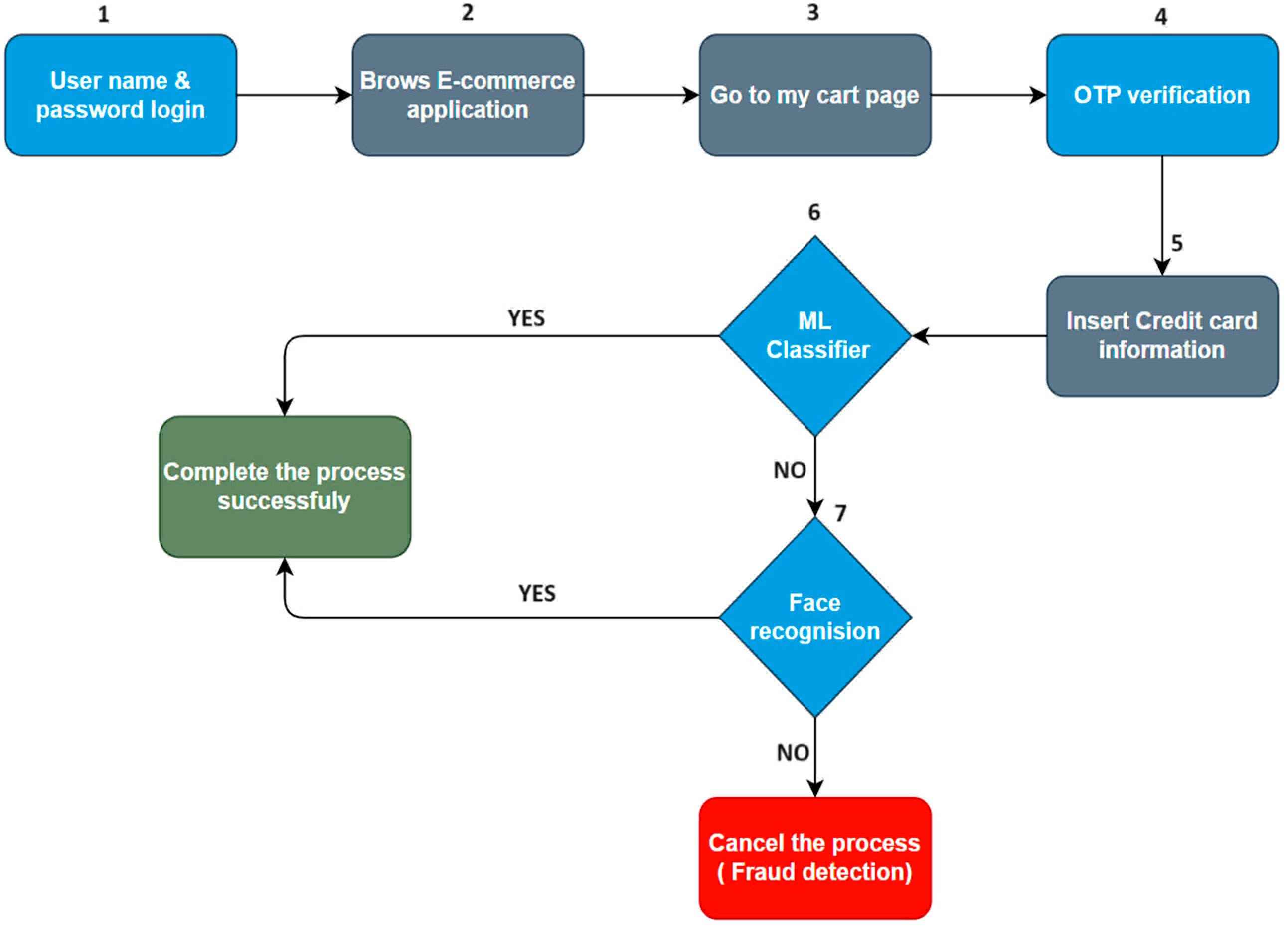
2.1. System Architecture
2.2. Methodology Used to Secure Internet Transactions
2.3. ML Phase
2.3.1. Experiment
2.3.2. Dataset
2.3.3. Data Preprocessing
2.3.4. The Choice of ML Classifiers
2.4. MFA Phase
2.5. Combining MFA with ML
2.5.1. Experiment
2.5.2. Proposed Framework
2.5.3. Application Design
3. Results
3.1. ML Results
3.1.1. Confusion Matrix
3.1.2. Classification Report
3.1.3. The ROC Curve
3.2. Mobile Application Results
4. Discussion
- Authentication factors: potential user resistance or discomfort with the chosen methods presents one challenge when choosing MFA for security purposes. Sometimes people feel that multi-factor authentication is too complicated and annoying to use, which can cause resistance or lower user acceptance of such systems. The challenge is to choose a secure factor to authenticate users along with taking into consideration the ease of use.
- Data availability: one major obstacle is the absence of necessary data. Organizations may choose to hide financial transaction data according to privacy and security considerations, and the needed datasets may not be publicly accessible due to the sensitivity of this data.
- Data quality: this study is impacted by the quality of the accessible data. Data that is missing, incorrect, unbalanced, or inconsistent can make ML models and authentication systems less effective and possibly produce biased or incorrect results. In particular, most of the available datasets are transformed using the PCA transformation technique.
- Technical limitations: technical barriers, such as compatibility issues or limited storage capacity, and processing speed may restrict the power to handle, process, and store big data efficiently.
- Suitable MFA implementation: a user-centric strategy was used to gain adaptable, and secure system implementation. The adaptive implementation of the MFA system led to interaction with only two factors when put into practice. A third factor is required if the ML algorithm classifies the transaction as fraud. This preserves strong security standards while simultaneously improving usability.
- Data cleaning and preprocessing: using techniques to remove errors and deal with unbalanced datasets that could affect the models’ accuracy in cleaning and preparing data. This was conducted successfully and discussed in Section 2.3.3 (data preprocessing).
- Replication: conducting the ML analysis at different times to confirm and guarantee the reliability and consistency of the results while reducing the influence of anomalies or errors.
- Algorithm and analysis suitability: using the right statistical techniques and ML algorithms to analyze the data while taking hardware constraints into account. Identifying and evaluating the best algorithms for the particular use case of safe financial transactions was conducted carefully. The implemented ML algorithms were simple and accurate to overcome the hardware limitations and facilitate the integration of ML and MFA into one model.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Schueffel, P. Taming the Beast: A Scientific Definition of Fintech. J. Innov. Manag. 2016, 4, 32–54. [Google Scholar] [CrossRef]
- Ul, B.; Khan, I.; Olanrewaju, R.F.; Mehraj Baba, A.; Langoo, A.A.; Assad, S. A Compendious Study of Online Payment Systems: Past Developments, Present Impact, and Future Considerations. IJACSA Int. J. Adv. Comput. Sci. Appl. 2017, 8, 256–271. [Google Scholar] [CrossRef]
- Cherif, A.; Badhib, A.; Ammar, H.; Alshehri, S.; Kalkatawi, M.; Imine, A. Credit Card Fraud Detection in the Era of Disruptive Technologies: A Systematic Review. J. King Saud. Univ. Comput. Inf. Sci. 2023, 35, 145–174. [Google Scholar] [CrossRef]
- Meneses-Claudio, B.; Huamaní, E.L.; Yauri-Machaca, M.; Meneses-Claudio, J.; Perez-Siguas, R. Authentication and Anti-Duplication Security System for Visa and MasterCard Card. Repos. Inst. UTP 2022, 10, 1–5. [Google Scholar] [CrossRef]
- Nandalwar, P.J.I.; Gaikwad, P.V.; Kulkarni, P.S. A Survey and Comparison on User Authentication Methods. Int. J. Innov. Eng. Res. Technol. 2016, 3, 1–7. [Google Scholar]
- Bonneau, J.; Herley, C.; Van Oorschot, P.C.; Stajano, F. Passwords and the Evolution of Imperfect Authentication. Commun. ACM 2015, 58, 78–87. [Google Scholar] [CrossRef]
- Gunson, N.; Marshall, D.; Morton, H.; Jack, M. User Perceptions of Security and Usability of Single-Factor and Two-Factor Authentication in Automated Telephone Banking. Comput. Secur. 2011, 30, 208–220. [Google Scholar] [CrossRef]
- Ah Kioon, M.C.; Wang, Z.S.; Deb Das, S. Security Analysis of MD5 Algorithm in Password Storage. Appl. Mech. Mater. 2013, 347–350, 2706–2711. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Offline Dictionary Attack on Password Authentication Schemes Using Smart Cards. In Information Security: 16th International Conference, ISC 2013, Dallas, Texas, November 13–15, 2013, Proceedings; Springer International Publishing: New York, NY, USA, 2015; Volume 7807, pp. 221–237. [Google Scholar]
- Heartfield, R.; Loukas, G. A Taxonomy of Attacks and a Survey of Defence Mechanisms for Semantic Social Engineering Attacks. ACM Comput. Surv. (CSUR) 2015, 48, 1–39. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals Are Beyond Attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Petsas, T.; Tsirantonakis, G.; Athanasopoulos, E.; Ioannidis, S. Two-Factor Authentication: Is the World Ready? Quantifying 2FA Adoption. In Proceedings of the 8th European Workshop on System Security, EuroSec 2015, Bordeaux, France, 21 April 2015. [Google Scholar] [CrossRef]
- Schneier, B. Two-Factor Authentication. Commun. ACM 2005, 48, 136. [Google Scholar] [CrossRef]
- Dumortier, J. Regulation (EU) No 910/2014 on Electronic Identification and Trust Services for Electronic Transactions in the Internal Market (EIDAS Regulation). SSRN Electron. J. 2016, 48, 1–39. [Google Scholar] [CrossRef]
- Burr, W.; Dodson, D.; Polk, W.T. Archived NIST Technical Series Publication Electronic Authentication Guideline. 2004. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-63ver1.0.2.pdf (accessed on 7 December 2023).
- Ometov, A.; Bezzateev, S.; Mäkitalo, N.; Andreev, S.; Mikkonen, T.; Koucheryavy, Y. Multi-Factor Authentication: A Survey. Cryptography 2018, 2, 1. [Google Scholar] [CrossRef]
- Kennedy, E.; Millard, C. Data Security and Multi-Factor Authentication: Analysis of Requirements under EU Law and in Selected EU Member States. Comput. Law. Secur. Rev. 2016, 32, 91–110. [Google Scholar] [CrossRef]
- Dasgupta, D.; Roy, A.; Nag, A. Multi-Factor Authentication. In Advances in User Authentication; Deb, K., Gupta, R., Mehlhorn, K., Rao, V.R., Sharma, A., Eds.; Springer: Cham, Switzerland, 2017. [Google Scholar] [CrossRef]
- Bell, J. What Is Machine Learning? Mach. Learn. City Appl. Archit. Urban. Des. 2022, 209–216. [Google Scholar]
- Cohen, S. The Evolution of Machine Learning: Past, Present, and Future. In Artif. Intell. Deep. Learn. Pathol. 2021, 1–12. [Google Scholar] [CrossRef]
- Hafez, M.M.; Redondo, R.P.D.; Vilas, A.F. A Comparative Performance Study of Naïve and Ensemble Algorithms for E-Commerce. In Proceedings of the ICENCO 2018—14th International Computer Engineering Conference: Secure Smart Societies, Cairo, Egypt, 29–30 December 2018; pp. 26–31. [Google Scholar] [CrossRef]
- Lomba, E.; Severino, R.; Vilas, A.F. Work In Progress: Towards Adaptive RF Fingerprint-Based Authentication of IIoT Devices. In Proceedings of the IEEE International Conference on Emerging Technologies and Factory Automation, ETFA, Stuttgart, Germany, 6–9 September 2022. [Google Scholar] [CrossRef]
- Redondo, R.P.D.; Vilas, A.F.; Merino, M.R.; Rodríguez, S.M.V.; Guijarro, S.T.; Hafez, M.M. Anti-Sexism Alert System: Identification of Sexist Comments on Social Media Using AI Techniques. Appl. Sci. 2023, 13, 4341. [Google Scholar] [CrossRef]
- González-Soto, M.; Díaz-Redondo, R.P.; Fernández-Veiga, M.; Fernández-Castro, B.; Fernández-Vilas, A. Decentralized and Collaborative Machine Learning Framework for IoT. Comput. Netw. 2024, 239, 110137. [Google Scholar] [CrossRef]
- Malta, S.; Pinto, P.; Fernandez-Veiga, M. Using Reinforcement Learning to Reduce Energy Consumption of Ultra-Dense Networks With 5G Use Cases Requirements. IEEE Access 2023, 11, 5417–5428. [Google Scholar] [CrossRef]
- Paladino, L.M.; Hughes, A.; Perera, A.; Topsakal, O.; Akinci, T.C. Evaluating the Performance of Automated Machine Learning (AutoML) Tools for Heart Disease Diagnosis and Prediction. AI 2023, 4, 1036–1058. [Google Scholar] [CrossRef]
- Abumohsen, M.; Owda, A.Y.; Owda, M. Electrical Load Forecasting Based on Random Forest, XGBoost, and Linear Regression Algorithms. In Proceedings of the 2023 International Conference on Information Technology: Cybersecurity Challenges for Sustainable Cities, ICIT, Amman, Jordan, 9–10 August 2023; pp. 25–31. [Google Scholar] [CrossRef]
- Owess, M.M.; Owda, A.Y.; Owda, M. Decision Support System in Healthcare for Predicting Blood Pressure Disorders. In Proceedings of the 2023 International Conference on Information Technology: Cybersecurity Challenges for Sustainable Cities, ICIT, Amman, Jordan, 9–10 August 2023; pp. 62–67. [Google Scholar] [CrossRef]
- Kulatilleke, G.K.; Mary, Q. Challenges and Complexities in Machine Learning Based Credit Card Fraud Detection. arXiv 2022, arXiv:2208.10943. [Google Scholar]
- Gaikwad, J.R.; Deshmane, A.B.; Somavanshi, H.V.; Patil, S.V.; Badgujar, R.A. Credit Card Fraud Detection Using Decision Tree Induction Algorithm. Int. J. Innov. Technol. Explor. Eng. (IJITEE) 2014, 2278–3075. [Google Scholar]
- Ng, A.Y.; Jordan, M.I. On Discriminative vs. Generative Classifiers: A Comparison of Logistic Regression and Naive Bayes. Adv. Neural Inf. Process Syst. 2001, 14, 841–848. [Google Scholar]
- Rajak, I.; Mathai, K.J. Intelligent Fraudulent Detection System Based SVM and Optimized by Danger Theory. In Proceedings of the IEEE International Conference on Computer Communication and Control, IC4 2015, Indore, India, 10–12 September 2015. [Google Scholar] [CrossRef]
- Awoyemi, J.O.; Adetunmbi, A.O.; Oluwadare, S.A. Credit Card Fraud Detection Using Machine Learning Techniques: A Comparative Analysis. In Proceedings of the IEEE International Conference on Computing, Networking and Informatics, ICCNI 2017, Lagos, Nigeria, 29–31 October 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Khattri, V.; Singh, D.K. Implementation of an Additional Factor for Secure Authentication in Online Transactions. J. Organ. Comput. Electron. Commer. 2019, 29, 258–273. [Google Scholar] [CrossRef]
- Sanyal, S.; Tiwari, A.; Sanyal, S. A Multifactor Secure Authentication System for Wireless Payment. Adv. Inf. Knowl. Process. 2010, 53, 341–369. [Google Scholar] [CrossRef]
- Mohammed, M.M.; Elsadig, M. A Multi-Layer of Multi Factors Authentication Model for Online Banking Services. In Proceedings of the 2013 International Conference on Computer, Electrical and Electronics Engineering: “Research Makes a Difference”, ICCEEE 2013, Khartoum, Sudan, 26–28 August 2013; pp. 220–224. [Google Scholar] [CrossRef]
- Chetalam, L.J. Enhancing Security of Mpesa Transactions by Use of Voice Biometrics. Diss. United States Int. Univ. Africa. 2018. Available online: https://api.semanticscholar.org/CorpusID:69847257 (accessed on 7 December 2023).
- MacIej, B.; Imed, E.F.; Kurkowski, M. Multifactor Authentication Protocol in a Mobile Environment. IEEE Access 2019, 7, 157185–157199. [Google Scholar] [CrossRef]
- Guma, A. Development of a Secure Multi-Factor Authentication Algorithm for Mobile Money Applications. Ph.D. Thesis, NM-AIST, Arusha, Tanzania, 2022. [Google Scholar] [CrossRef]
- Scaria, B.A.; Karman Megalingam, R. Enhanced E-Commerce Application Security Using Three-Factor Authentication. In Proceedings of the 2nd International Conference on Intelligent Computing and Control Systems, ICICCS 2018, Madurai, India, 14–15 June 2018; pp. 1588–1591. [Google Scholar] [CrossRef]
- Hassan, M.A.; Shukur, Z. A Secure Multi Factor User Authentication Framework for Electronic Payment System. In Proceedings of the 2021 3rd International Cyber Resilience Conference, CRC 2021, Langkawi Island, Malaysia, 29–31 January 2021. [Google Scholar] [CrossRef]
- Zadeh, M.J.; Barati, H. Security Improvement in Mobile Baking Using Hybrid Authentication. 2019 The 3rd International Conference on Advances in Artificial Intelligence, Istanbul, Turkey, 26–28 October 2019; 2019; pp. 198–201. [Google Scholar] [CrossRef]
- Jaspher, G.; Kathrine, W.; Kirubakaran, E. Four-Factor Based Privacy Preserving Biometric Authentication and Authorization Scheme for Enhancing Grid Security. Int. J. Comput. Appl. 2011, 30, 975–8887. [Google Scholar]
- Krol, K.; Philippou, E.; De Cristofaro, E.; Sasse, M.A. “They Brought in the Horrible Key Ring Thing!” Analysing the Usability of Two-Factor Authentication in UK Online Banking. arXiv 2015, arXiv:1501.04434. [Google Scholar] [CrossRef]
- Dutson, J.; Allen, D.; Eggett, D.; Seamons, K. Don’t Punish All of Us: Measuring User Attitudes about Two-Factor Authentication. In Proceedings of the 4th IEEE European Symposium on Security and Privacy Workshops, EUROS and PW 2019, Stockholm, Sweden, 17–19 June 2019; pp. 119–128. [Google Scholar] [CrossRef]
- Arnold, D.; Blackmon, B.; Gibson, B.; Moncivais, A.G.; Powell, G.B.; Skeen, M.; Thorson, M.K.; Wade, N.B. The Emotional Impact of Multi-Factor Authentication for University Students. In Proceedings of the Conference on Human Factors in Computing Systems, New Orleans LA, USA, 29 April–5 May 2022; 2022. [Google Scholar] [CrossRef]
- Eid Alanzi, T.; Naif Alatawi, M. A Secure Two-Factor Authentication Framework Based on Deep Learning. J. Res. Sci. Eng. (JRSE) 2022, 4, 2319–7064. [Google Scholar] [CrossRef]
- Kariapper, R. Attendance System Using RFID, IoT and Machine Learning: A Two Factor Verification Approach. J. Adv. Res. Dyn. Control. Syst. 2021, 12, 3285–3297. [Google Scholar] [CrossRef] [PubMed]
- Deridder, Z.; Siddiqui, N.; Reither, T.; Dave, R.; Pelto, B.; Vanamala, M.; Seliya, N. Continuous User Authentication Using Machine Learning and Multi-Finger Mobile Touch Dynamics with a Novel Dataset. In Proceedings of the 2022 9th International Conference on Soft Computing and Machine Intelligence, ISCMI 2022, Toronto, ON, Canada, 26–27 November 2022; pp. 42–46. [Google Scholar] [CrossRef]
- Misbahuddin, M.; Bindhumadhava, B.; Dheeptha, B. Design of a Risk Based Authentication System Using Machine Learning Techniques. In Proceedings of the 2017 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), San Francisco, CA, USA, 4–8 August 2017; pp. 1–6. [Google Scholar]
- Rodrigues, A.R.L. Enhanced Multi-Factor Authentication for Mobile Applications. Enhanc. Multi-Factor. Authentication Mob. Appl. 2023. Available online: https://estudogeral.uc.pt/handle/10316/107821 (accessed on 7 December 2023).
- Maćkiewicz, A.; Ratajczak, W. Principal Components Analysis (PCA). Comput. Geosci. 1993, 19, 303–342. [Google Scholar] [CrossRef]
- Taha, A.A.; Malebary, S.J. An Intelligent Approach to Credit Card Fraud Detection Using an Optimized Light Gradient Boosting Machine. IEEE Access 2020, 8, 25579–25587. [Google Scholar] [CrossRef]
- Carcillo, F.; Le Borgne, Y.A.; Caelen, O.; Kessaci, Y.; Oblé, F.; Bontempi, G. Combining Unsupervised and Supervised Learning in Credit Card Fraud Detection. Inf. Sci. 2021, 557, 317–331. [Google Scholar] [CrossRef]
- Bin Sulaiman, R.; Schetinin, V.; Sant, P. Review of Machine Learning Approach on Credit Card Fraud Detection. Hum.-Centric Intell. Syst. 2022, 2, 55–68. [Google Scholar] [CrossRef]
- Tiwari, P.; Mehta, S.; Sakhuja, N.; Kumar, J.; Singh, A.K. Credit Card Fraud Detection Using Machine Learning: A Study. arXiv 2021, arXiv:2108.10005. [Google Scholar]
- Aburbeian, A.M.; Ashqar, H.I. Credit Card Fraud Detection Using Enhanced Random Forest Classifier for Imbalanced Data. In Proceedings of the 2023 International Conference on Advances in Computing Research (ACR’23), Springer Links, Orlando, FL, USA, 25–26 May 2023; pp. 605–616. [Google Scholar]
- Vargaftik, S.; Keslassy, I.; Orda, A.; Ben-Itzhak, Y. RADE: Resource-Efficient Supervised Anomaly Detection Using Decision Tree-Based Ensemble Methods. Mach. Learn. 2021, 110, 2835–2866. [Google Scholar] [CrossRef]
- Itoo, F.; Meenakshi; Singh, S. Comparison and Analysis of Logistic Regression, Naïve Bayes and KNN Machine Learning Algorithms for Credit Card Fraud Detection. Int. J. Inf. Technol. 2021, 13, 1503–1511. [Google Scholar] [CrossRef]
- Kaur, S.; Kaur, G.; Shabaz, M. A Secure Two-Factor Authentication Framework in Cloud Computing. Secur. Commun. Netw. 2022, 2022, 7540891. [Google Scholar] [CrossRef]
- Adjabi, I.; Ouahabi, A.; Benzaoui, A.; Taleb-Ahmed, A. Past, Present, and Future of Face Recognition: A Review. Electronics 2020, 9, 1188. [Google Scholar] [CrossRef]
- Muda, T.Z.T.; Wong, X.Y.; Teh, X.L. Designing a Mobile Apps: Savior. J. Inf. Syst. Technol. Manag. 2022, 7, 178–185. [Google Scholar] [CrossRef]
- Zeng, G. On the Confusion Matrix in Credit Scoring and Its Analytical Properties. Commun. Stat. Theory Methods 2020, 49, 2080–2093. [Google Scholar] [CrossRef]
- Davis, J.; Goadrich, M. The Relationship between Precision-Recall and ROC Curves. ACM Int. Conf. Proceeding Ser. 2006, 148, 233–240. [Google Scholar] [CrossRef]
- Zhang, Y.; Yu, G.; Yang, D. Predicting Non-Performing Loan of Business Bank by Multiple Classifier Fusion Algorithms. J. Interdiscip. Math. 2016, 19, 657–667. [Google Scholar] [CrossRef]
- Dighe, D.; Patil, S.; Kokate, S. Detection of Credit Card Fraud Transactions Using Machine Learning Algorithms and Neural Networks: A Comparative Study. In Proceedings of the 2018 4th International Conference on Computing, Communication Control and Automation, ICCUBEA 2018, Pune, India, 16–18 August 2018. [Google Scholar] [CrossRef]
- Dhankhad, S.; Mohammed, E.A.; Far, B. Supervised Machine Learning Algorithms for Credit Card Fraudulent Transaction Detection: A Comparative Study. In Proceedings of the 2018 IEEE 19th International Conference on Information Reuse and Integration for Data Science, IRI 2018, Salt Lake City, UT, USA, 6–9 July 2018; pp. 122–125. [Google Scholar] [CrossRef]
- Dornadula, V.N.; Geetha, S. Credit Card Fraud Detection Using Machine Learning Algorithms. Procedia Comput. Sci. 2019, 165, 631–641. [Google Scholar] [CrossRef]
- Kumar Trivedi, N.; Simaiya, S.; Kumar Sharma, S.; Kumar Lilhore, U. An Efficient Credit Card Fraud Detection Model Based on Machine Learning Methods. Int. J. Adv. Sci. Technol. 2020, 29, 3414–3424. [Google Scholar]
- Faraji, Z. A Review of Machine Learning Applications for Credit Card Fraud Detection with A Case Study. SEISENSE J. Manag. 2022, 5, 49–59. [Google Scholar] [CrossRef]
- Mohsen, O.R.; Nassreddine, G.; Massoud, M. Credit Card Fraud Detector Based on Machine Learning Techniques. J. Comput. Sci. Technol. Stud. 2023, 5, 16–30. [Google Scholar] [CrossRef]
- Homepage, J.; Unogwu, O.J.; Filali, Y. Fraud Detection and Identification in Credit Card Based on Machine Learning Techniques. Wasit J. Comput. Math. Sci. 2023, 2, 16–22. [Google Scholar] [CrossRef]
- Aftab, A.U.; Shahzad, I.; Anwar, M.; Sajid, A.; Anwar, N. Fraud Detection of Credit Cards Using Supervised Machine Learning. Pak. J. Emerg. Sci. Technol. (PJEST) 2023, 4, 38–51. [Google Scholar] [CrossRef]
- Ogbanufe, O.M.; Baham, C. Using Multi-Factor Authentication for Online Account Security: Examining the Influence of Anticipated Regret. Inf. Syst. Front. 2023, 25, 897–916. [Google Scholar] [CrossRef]
- Tanwar, R.; Samadi, B.; Khodadadi, T.; Chaudet, C.; Bellavista, P.; Prakash Otta, S.; Panda, S.; Gupta, M.; Hota, C. A Systematic Survey of Multi-Factor Authentication for Cloud Infrastructure. Future Internet 2023, 15, 146. [Google Scholar] [CrossRef]
- Braeken, A. Highly Efficient Bidirectional Multi-Factor Authentication and Key Agreement for Real-Time Access to Sensor Data. IEEE Internet Things J. 2023, 10, 21089–21099. [Google Scholar] [CrossRef]
- Marasco, E.; Albanese, M.; Vamsi, V.; Patibandla, R.; Vurity, A.; Sriram, S.S. Biometric Multi-Factor Authentication: On the Usability of the FingerPIN Scheme. Secur. Priv. 2023, 6, e261. [Google Scholar] [CrossRef]
- Ahmad, M.O.; Tripathi, G.; Siddiqui, F.; Alam, M.A.; Ahad, M.A.; Akhtar, M.M.; Casalino, G. BAuth-ZKP—A Blockchain-Based Multi-Factor Authentication Mechanism for Securing Smart Cities. Sensors 2023, 23, 2757. [Google Scholar] [CrossRef]
- Carrillo-Torres, D.; Pérez-Díaz, J.A.; Cantoral-Ceballos, J.A.; Vargas-Rosales, C. A Novel Multi-Factor Authentication Algorithm Based on Image Recognition and User Established Relations. Appl. Sci. 2023, 13, 1374. [Google Scholar] [CrossRef]






| Time | V1 | V2 | V3 | V4 | V5 | V6 | V7 |
| 0.0 | −1.359807 | −0.072781 | 2.536347 | 1.378155 | −0.338321 | 0.462388 | 0.239599 |
| 0.0 | 1.191857 | 0.266151 | 0.16648 | 0.448154 | 0.060018 | −0.082361 | −0.078803 |
| 1.00 | −1.358354 | −1.340163 | 1.773209 | 0.37978 | −0.503198 | 1.800499 | 0.791461 |
| 1.00 | −0.966272 | −0.185226 | 1.792993 | −0.863291 | −0.010309 | 1.247203 | 0.237609 |
| 2.00 | −1.158233 | 0.877737 | 1.548718 | 0.403034 | 0.407193 | 0.095921 | 0.592941 |
| V8 | V9 | ... | V21 | V22 | V23 | V24 | V25 |
| 0.098698 | 0.363787 | ... | −0.018307 | 0.277838 | −0.110474 | 0.066928 | 0.128539 |
| 0.085102 | −0.255425 | ... | −0.225775 | −0.638672 | 0.101288 | −0.339846 | 0.16717 |
| 0.247676 | −1.514654 | ... | 0.247998 | 0.771679 | 0.909412 | −0.689281 | −0.327642 |
| 0.377436 | −1.387024 | ... | −0.1083 | 0.005274 | −0.190321 | −1.175575 | 0.647376 |
| −0.270533 | 0.817739 | ... | −0.009431 | 0.798278 | −0.137458 | 0.141267 | −0.20601 |
| V26 | V27 | V28 | Amount | Class | |||
| −0.189115 | 0.133558 | −0.021053 | 149.62 | 0 | |||
| 0.125895 | −0.008983 | 0.014724 | 2.69 | 0 | |||
| −0.139097 | −0.055353 | −0.059752 | 378.66 | 1 | |||
| −0.221929 | 0.062723 | 0.061458 | 123.5 | 0 | |||
| 0.502292 | 0.219422 | 0.215153 | 69.99 | 0 |
| Classifier | Accuracy | Class | Precision | Recall | F1 Score | Support |
|---|---|---|---|---|---|---|
| Random Forest | 96.717% | 0 | 0.94 | 0.99 | 0.97 | 56,463 |
| 1 | 0.99 | 0.94 | 0.97 | 56,463 | ||
| Decision Tree | 97.881% | 0 | 0.97 | 0.99 | 0.98 | 56,463 |
| 1 | 0.99 | 0.97 | 0.98 | 56,463 | ||
| Logistic Regression | 97.938% | 0 | 0.97 | 0.99 | 0.98 | 56,463 |
| 1 | 0.99 | 0.97 | 0.98 | 56,463 | ||
| Naive Bayes | 92.354% | 0 | 0.88 | 0.98 | 0.93 | 56,463 |
| 1 | 0.97 | 0.87 | 0.92 | 56,463 |
| Reference | Year | Classifier | Accuracy | Precision | Recall |
| [34] | 2013 | LR | 0.54 | 0.38 | 0.58 |
| NB | 0.97 | 0.97 | 0.95 | ||
| [66] | 2016 | DT | 0.90 | 0.83 | 0.83 |
| [67] | 2018 | LR | 0.96 | - | - |
| DT | 0.96 | - | - | ||
| NB | 0.97 | - | - | ||
| [68] | 2018 | LR | 0.94 | 0.95 | 0.95 |
| DT | 0.90 | 0.91 | 0.91 | ||
| RF | 0.94 | 0.95 | 0.95 | ||
| NB | 0.90 | 0.91 | 0.91 | ||
| [69] | 2019 | LR | 0.97 | 0.98 | - |
| DT | 0.97 | 0.98 | - | ||
| RF | 0.99 | 0.99 | - | ||
| [70] | 2020 | LR | 0.90 | 0.92 | 0.93 |
| DT | 0.91 | 0.90 | 0.92 | ||
| RF | 0.95 | 0.96 | 0.95 | ||
| [71] | 2022 | LR | 0.96 | 0.98 | 0.93 |
| DT | 0.77 | 0.77 | 0.76 | ||
| RF | 0.85 | 0.93 | 0.78 | ||
| [72] | 2023 | LR | 0.69 | 0.59 | 0.82 |
| RF | 0.64 | 0.77 | 0.55 | ||
| [73] | 2023 | RF | 0.99 | 0.99 | 0.99 |
| NB | 0.99 | 0.99 | 0.99 | ||
| [74] | 2023 | DT | 0.51 | 0.38 | 0.75 |
| RF | 0.84 | 0.87 | 0.81 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aburbeian, A.M.; Fernández-Veiga, M. Secure Internet Financial Transactions: A Framework Integrating Multi-Factor Authentication and Machine Learning. AI 2024, 5, 177-194. https://doi.org/10.3390/ai5010010
Aburbeian AM, Fernández-Veiga M. Secure Internet Financial Transactions: A Framework Integrating Multi-Factor Authentication and Machine Learning. AI. 2024; 5(1):177-194. https://doi.org/10.3390/ai5010010
Chicago/Turabian StyleAburbeian, AlsharifHasan Mohamad, and Manuel Fernández-Veiga. 2024. "Secure Internet Financial Transactions: A Framework Integrating Multi-Factor Authentication and Machine Learning" AI 5, no. 1: 177-194. https://doi.org/10.3390/ai5010010
APA StyleAburbeian, A. M., & Fernández-Veiga, M. (2024). Secure Internet Financial Transactions: A Framework Integrating Multi-Factor Authentication and Machine Learning. AI, 5(1), 177-194. https://doi.org/10.3390/ai5010010







