- 2.5Impact Factor
- 5.5CiteScore
- 17 daysTime to First Decision
Blockchain in Information Security and Privacy
This special issue belongs to the section “Computing and Artificial Intelligence“.
Special Issue Information
Dear Colleagues,
We are inviting submissions to a Special Issue on Blockchain in Information Security and Privacy.
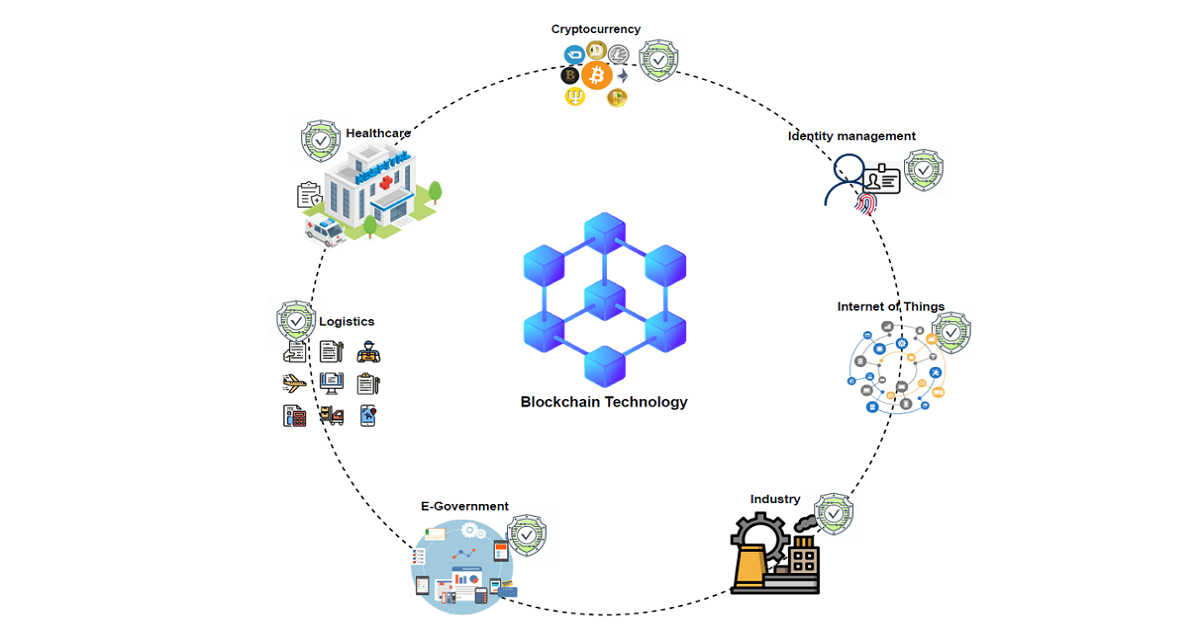
Information security and privacy are critical for governments, businesses, and individuals due to the fast-paced technological changes and changing cyberthreat landscape. Numerous solutions have been suggested to tackle these altering requirements, and one such solution is based on blockchain. Blockchain is an immutable, decentralized, and cryptography-based infrastructural technology that has the potential to be leveraged in many aspects of information security and privacy. However, we have yet to perceive its role in strengthening cybersecurity within various applications ranging from identity management to health data records, Internet of Things (IoT), vehicular networks, risk management, public and social services, and so forth.
In this Special Issue, we invite submissions exploring cutting-edge research and recent advances in the field of Blockchain in Information Security and Privacy. Both theoretical and experimental studies are welcome, as well as comprehensive review and survey papers
Prof. Dr. Hui Li
Dr. Shancang Li
Dr. Konstantinos Demertzis
Guest Editors
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the special issue website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 250 words) can be sent to the Editorial Office for assessment.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Applied Sciences is an international peer-reviewed open access semimonthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript. The Article Processing Charge (APC) for publication in this open access journal is 2400 CHF (Swiss Francs). Submitted papers should be well formatted and use good English. Authors may use MDPI's English editing service prior to publication or during author revisions.
Keywords
- blockchain technology
- smart contacts
- consensus mechanisms
- information security
- data privacy
- data management
- digital identity management
- artificial intelligence
- machine learning
- healthcare
- IoT
- digital forensics
Benefits of Publishing in a Special Issue
- Ease of navigation: Grouping papers by topic helps scholars navigate broad scope journals more efficiently.
- Greater discoverability: Special Issues support the reach and impact of scientific research. Articles in Special Issues are more discoverable and cited more frequently.
- Expansion of research network: Special Issues facilitate connections among authors, fostering scientific collaborations.
- External promotion: Articles in Special Issues are often promoted through the journal's social media, increasing their visibility.
- Reprint: MDPI Books provides the opportunity to republish successful Special Issues in book format, both online and in print.


