1. Introduction
With the rapid growth of network technologies, it is extremely important to pay close attention to any developing security concerns. As such, password-based authentication has become one of the best practically applied techniques used to problem-solve regarding various applications in wireless environments and other remote authentication systems. In 1981, Lamport [
1] proposed the first password-based remote authentication scheme for identifying a legal user using a hash-chain technique through insecure communication. In our scheme, all secret passwords are stored in a verifier’s table that is maintained by the remote server; in a situation such as this, there exists a potential threat such that all maintained records might be modified by attackers. In order to solve these problems, numerous undertakings in research [
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28,
29] have been executed during recent years.
In 1990, Hwang et al. [
12] proposed a non-interactive password authentication scheme without password tables using smart cards. Follow up research [
3,
6,
16,
18,
23,
24,
30,
31,
32,
33,
34,
35,
36,
37,
38,
39] has also been proposed. Because these schemes suffered from a susceptibility to ID-theft attack, an attacker could forge a legal user using an eavesdropped users’ identity documentation. Das et al. [
6] proposed a dynamic ID-based remote user authentication scheme that has significant advantages; most notably, the remote server does not need to maintain a verifier’s table. However, in 2009, Wang et al. [
25] pointed out that Das et al.’s scheme still exhibited several weaknesses. For example, it is susceptible to server counterfeit attack and provides poor password authentication. In the same year, Hsiang and Shih [
11] proposed a remote user authentication scheme using smart cards claiming that their scheme provided many security features, such as: mutual authentication, the ability to freely change passwords and protection from masquerade attack.
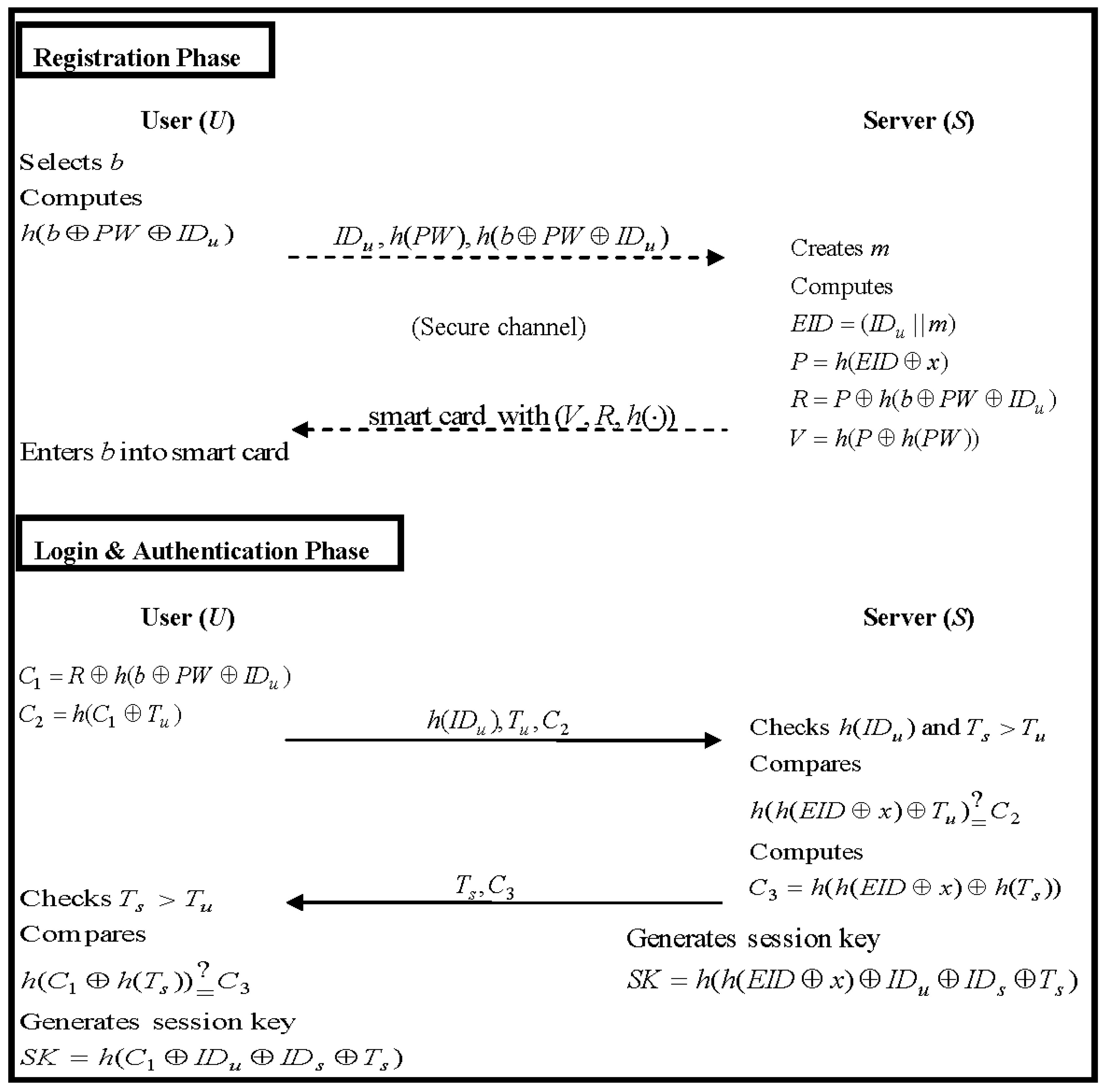
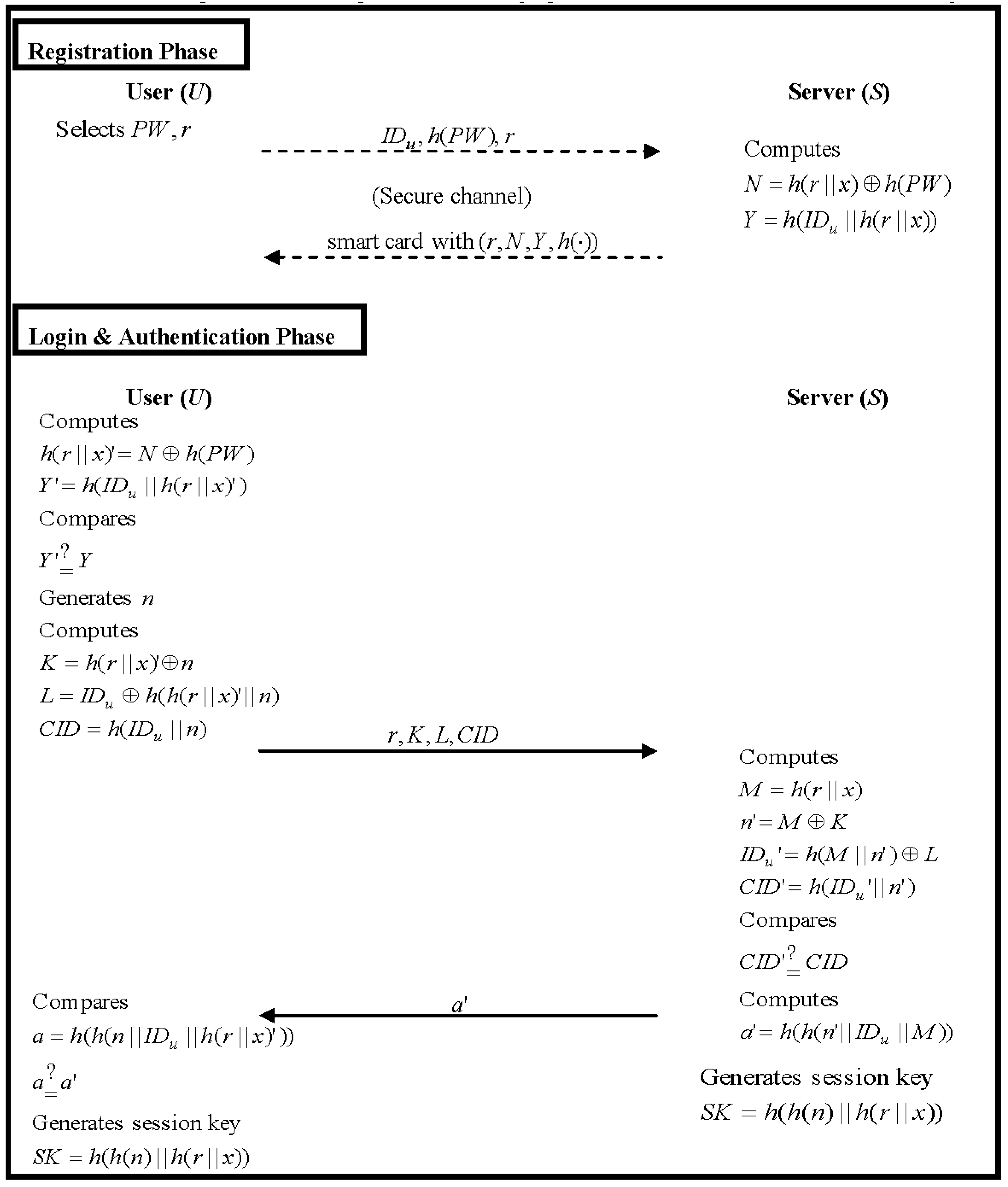
Next, Yeh et al. [
27] proposed two robust remote user authentication schemes using smart cards. Their schemes illustrated how Wang et al.’s scheme and Hsiang and Shih’s scheme were still susceptible to masquerade attack, off-line password guessing attacks and undetectable on-line password guessing attacks. Thus, Yeh et al. proposed two schemes to remedy these weaknesses that were more efficient than both Wang et al.’s scheme and Hsiang and Shih’s scheme. Nevertheless, according to our cryptanalysis, Yeh et al.’s schemes still have notable weaknesses to ID-theft attack, off-line password guessing attacks, undetectable on-line password guessing attacks and user impersonation attack. Moreover, the smart-card-based schemes [
6,
9,
11,
19,
25,
28] suffered in contexts involving a lost smart card. In fact, some researches [
15,
21] reveal the stored parameters of smart card. Therefore, we propose an improved scheme to overcome all of the security weaknesses mentioned above.
The security requirements of a remote user authentication scheme based on smart cards are listed as follows:
- Mutual authentication
In the information transmission process, the message receiver must be able to verify the identity legitimacy of the sender. Thus, each party must be able to verify the identity legitimacy of the other parties in a remote user authentication environment. If the two parties have confirmed each other’s identities, then mutual authentication is achieved.
- Lost smart card
If the user’s smart card is stolen by an attacker, the attacker may use the smart card for future malicious communications, or use it to obtain previous messages. A secure remote user authentication environment should avoid these situations, when the smart card is stolen by an attacker.
- ID-theft attack
Malicious attacks may also attempt to get a person’s identification by tracing their transmitted messages. Thus, a secure remote user authentication scheme must prevent such ID-theft attack.
- Server counterfeit attack and user impersonation attack
Any information transferred in an unencrypted network environment is vulnerable to malicious attack in the form of modification, where the message delivered to the receiver is not the original message transmitted by the sender. The attacker may pretend a legal server or a legal user. The legality of the transmitted parties must therefore be ensured and protected against tampering in transit.
- Replay attacks
Malicious attacks may also intercept the transmitted message between the user and the server and then impersonate a legitimate transmitter in order to send the same message to the intended receiver. This constitutes a serious breach of personal data security and must be prevented by a secure remote user authentication environment.
The rest of this paper is organized as follows.
Section 2 provides a brief review of the weakness of Yeh et al.’s schemes.
Section 3 provides details of the proposed scheme.
Section 4 provides a security analysis of our scheme.
Section 5 shows a security and performance comparison with related research. We provide conclusions in the last section.
4. Security Analysis
In this section, we will discuss the security of our improved scheme and demonstrate how it is more secure than previous schemes.
4.1. Mutual Authentication
In the proposed scheme, when the personal reader wants to communicate with the medical reader, they must authenticate each other. In this subsection, we use the Burrows–Abadi–Needham (BAN) logic model [
40] to proof the correctness of our improved scheme. Recently, many authentication schemes [
41,
42,
43] have applied BAN logic to proof the correctness of an authentication and key establishment. The symbols
Ns and
Nu are nonces;
h(
x),
h(
x||
Ns) and
SK denotes the secret keys; the notation of Ban logic is described as follows:
| P believes X, or P would be entitled to believe X. |
| P sees X. Someone has sent a message containing X to P, who can read and repeat X. |
| P once said X. P at some time sent a message including X. |
| P has jurisdiction over X. P is an authority on X and should be trusted on this matter. |
| This represents X combined with Y. |
| The formula X is fresh, that is, X has not been sent in a message at any time before the current run of the protocol. |
| P and Q may use the shared key K to communicate. |
| The formula S is a secret known only to P and Q and possibly to principals trusted by them. |
The main goal of our scheme is to authenticate the session key establishment between a user U and the remote server S.
| G1 | |
| G2 | |
| G3 | |
| G4 | |
| G5 | |
| G6 | |
According to our authentication phase, we use BAN logic to produce an idealized form as follows:
| M1 | |
| M2 | |
To analyze our improved scheme, we make the following assumptions:
| A1 | |
| A2 | |
| A3 | |
| A4 | |
| A5 | |
| A6 | |
| A7 | |
According to those assumptions and the rules of BAN logic, we show the main proof of our authentication phase as follows:
By (Statement 5) to (Statement 8), (Statement 12) and (Statement 13), we can proof our improved scheme such that user U and the remote server S authenticate each other. Moreover, we are also able to prove that the improved scheme can establish a session key between the user U and the remote server S.
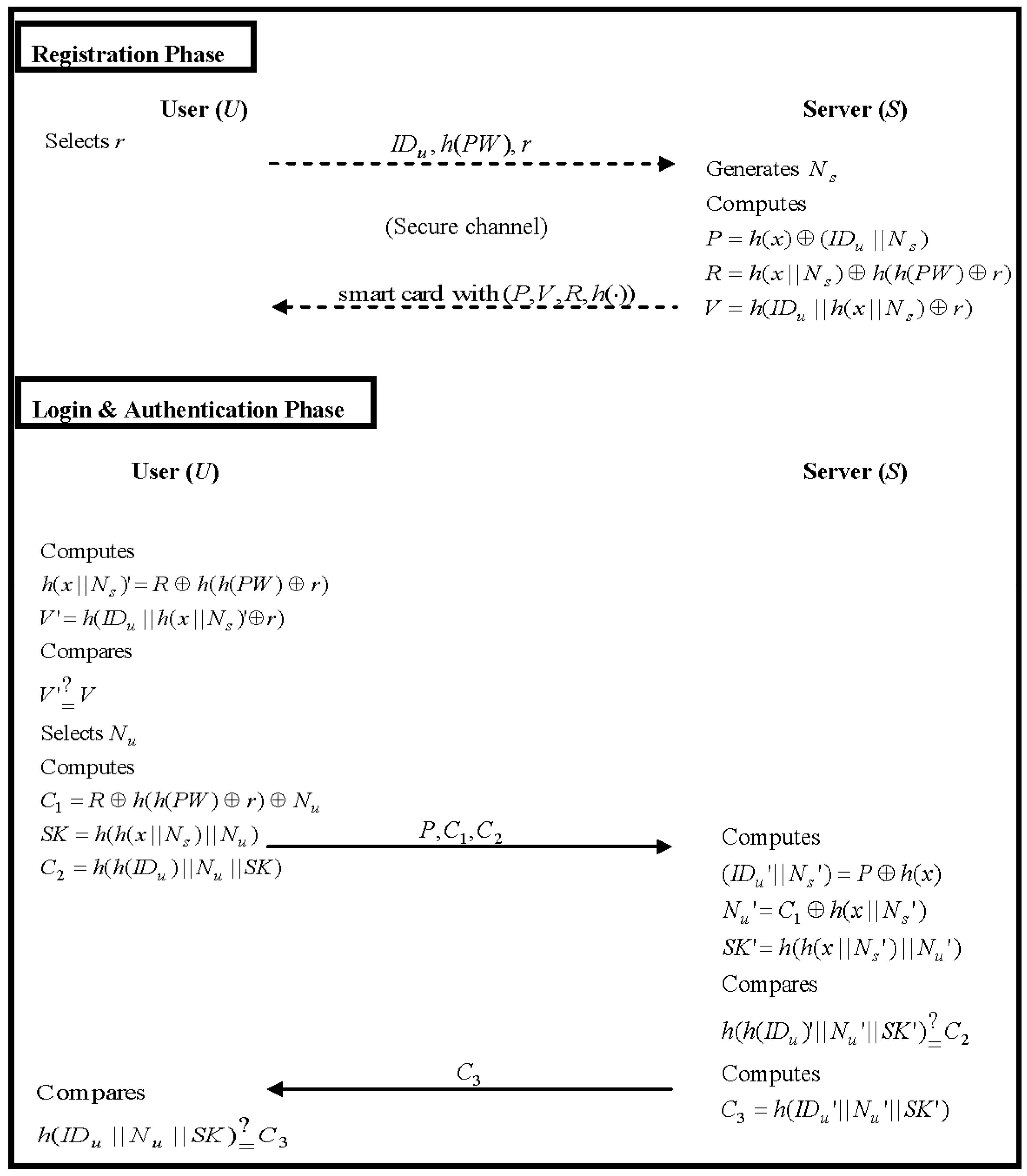
In our improved scheme, the server authenticates the user by checking the message C2. If server’s computed value h(h(IDu′)||Nu′||SK′) is equal to C2, the server proves that the user is valid. Then, server sends message C3 to the user. The user also compares C3 with his or her computation value h(IDu||Nu||SK′). If both of them are equal, the user confirms that the server is legitimate. Since the secret value h(x||Ns) is shared between user and server, they can authenticate each other with the login messages (P, C1, C2) and the reply message C3. Hence, mutual authentication obtains in our improved scheme.
- Scenario:
A malicious attacker uses an illegal server to authenticate a legal user.
- Analysis:
The attacker will not succeed because the legal user has not been registered to the illegal server and the illegal server cannot calculate the correct session key SK. Thus, it will fail when the legal user attempts to authenticate the illegal server. In the proposed scheme, the attacker cannot achieve their purpose using an illegal server. In the same scenario, the proposed scheme can also defend against a malicious attack using an illegal user to connect to a legal server. This is why the illegal user has not been registered to the legal server and the illegal user cannot calculate the correct session key SK. Thus, the attack will fail when the legal server attempts to authenticate the illegal user.
4.2. Lost Smart Card
According to our improved scheme, if an attacker A obtains a legal user U’s smart card somehow, they cannot obtain any parameter without the user’s password; even if A extracts the parameters P, R and V (see Equations (42)–(44)) from the smart card, they still cannot obtain any sensitive information (such as IDu, PW, Ns or the server’s secret key x) with those parameters. Notably, A does not know U’s correct password and each parameter is always protected by two unknown factors of the smart card. Therefore, no one can use the stolen smart card to obtain authentication without U’s correct password and identity.
4.3. ID-Theft Attack
As regards the login and authentication phases of our improved scheme, U’s IDu is always protected by P and C2; it is impossible for an attacker A to acquire it from P and C2. Notably, it is difficult to reveal IDu from P without the server’s secret key x and the nonce Ns. Additionally, A cannot obtain IDu from C2 without the nonce Nu. Therefore, IDu cannot be known by the attacker.
4.4. Password Guessing Attacks
This situation involves an attacker A obtaining the U’s smart card and intercepting previous messages. In this case, A intends to guess the U’s PW from the stored parameter R of the smart card and must know the secret key x and the nonce Ns to compute similar parameters for comparison with parameter R. On the other hand, A can use R and the intercepted P to compute similar messages (P, C1′, C2′) and send it to S in an attempt to guess U’s PW. As A has two unknown values, IDu and PW, it is difficult to successfully complete this password guessing attack.
4.5. Server Counterfeit Attack and User Impersonation Attack
Notably, Yeh et al.’s schemes will compromise the server’s secret key x in the context of a malicious legal user, allowing forgery of another legal user and a remote server. Hence, in the registration phase of our improved scheme (see Equation (42)), the remote server S generates a nonce value Ns to compute parameter P with U’s identity IDu and its secret key x, where the nonce value Ns is different for each user. So, the malicious legal user cannot guess x with an unknown value Ns. As such, these two attacks will be prevented.
4.6. Replay Attack
In our improved scheme, we use a nonce mechanism to prevent the replay attack and to solve the synchronization problem. When an attacker intends to replay the previous messages (P, C1, C2) to achieve authentication, they cannot as the nonce value Nu is different in each session. For this reason, the attacker cannot achieve authentication using previous messages.
- Scenario:
A malicious attacker intercepts the transmitted message between the user and the server and sends the same message again to the user or the server.
- Analysis:
The attacker will not succeed because the legal user uses the nonce value Nu in each session. The attacker cannot get the correct nonce value Nu. Thus, the attack will fail when the legal server authenticates the received message. In the proposed scheme, the attackers cannot achieve their purpose by sending the same message again to the user or to the server. Therefore, attackers cannot achieve their purpose by replay attack.
6. Conclusions
In this paper, we first reviewed Yeh et al.’s two remote user authentication schemes using smart cards. They claimed that their schemes could defend against known attacks more effectively and more efficiently than previous related research. However, in our cryptanalysis, we find that Yeh et al.’s claims allow for further improvements and that their proposals exhibit serious security flaws, i.e., susceptibility to ID-theft attacks, off-line password guessing attacks, undetectable on-line password guessing attacks and user impersonation attacks. Moreover, based on other related researches [
15,
21], if an attacker can obtain a legal user’s smart card, they can extract the secret parameters from the smart card to successfully complete password guessing attacks. Additionally, in cases where an attacker is a malicious legal user, the attacker can use their smart card to impersonate any legal user. This factor results in the security flaws we discussed above; hence, many schemes will be insecure.
To remedy the specific security problems detailed in this paper, we have proposed an improved scheme. The proposed scheme consistently protects each secret parameter with two unknown factors in the smart card; thus, an attacker cannot obtain any sensitive information, even if he or she is a malicious legal user. Most notably, our scheme not only addresses more stringent security requirements and protects against known types of attacks, it also reduces computation costs more effectively than Yeh et al.’s scheme. Therefore, our scheme holds substantial value in the context of numerous applications in various network environments.