Cyber-Resilient Converter Control System for Doubly Fed Induction Generator-Based Wind Turbine Generators
Abstract
:1. Introduction
- A novel approach, i.e., a DDPG controller, is developed to mitigate cyber attacks on DERs.
- The proposed method offers a low-cost approach to maintain wind farm stability during malicious cyber attacks on converter management systems.
- This research analyzes the effects of different types of cyber attacks on the converter control system of a grid-connected DFIG-based wind farm.
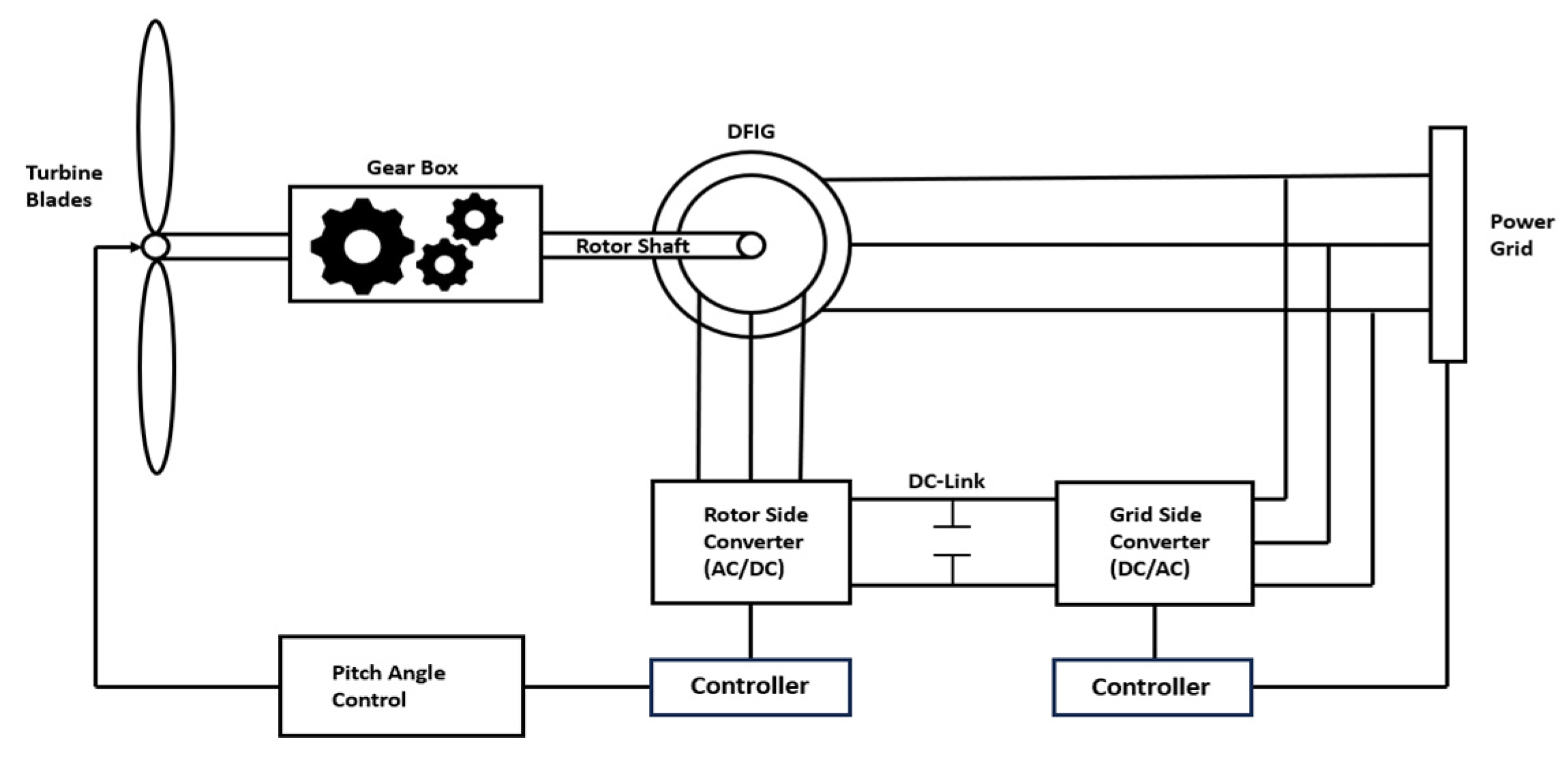
2. Problem Statement
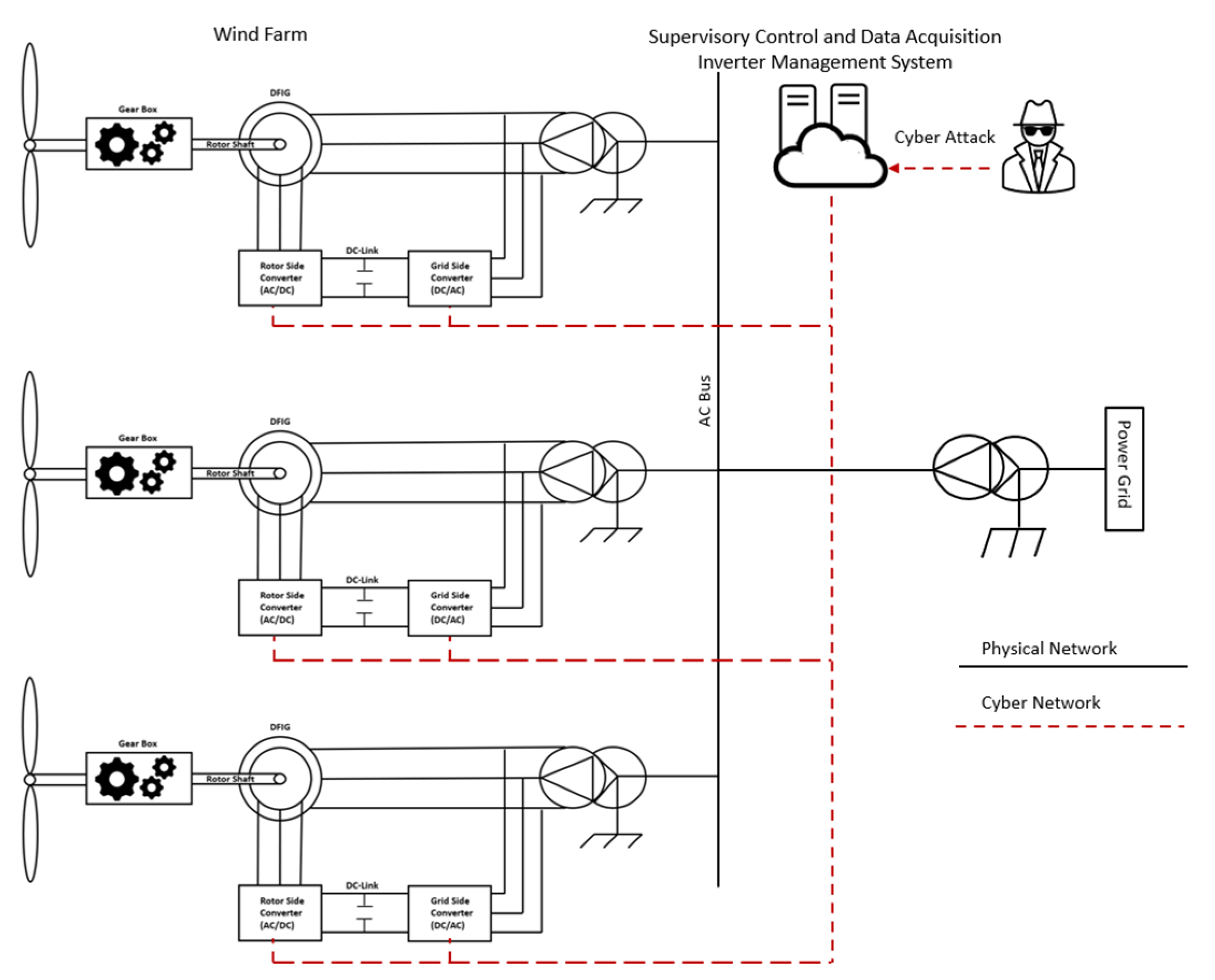
3. Cyber Attack Modeling
3.1. False Data Injection Attack
3.2. Denial of Service Attack
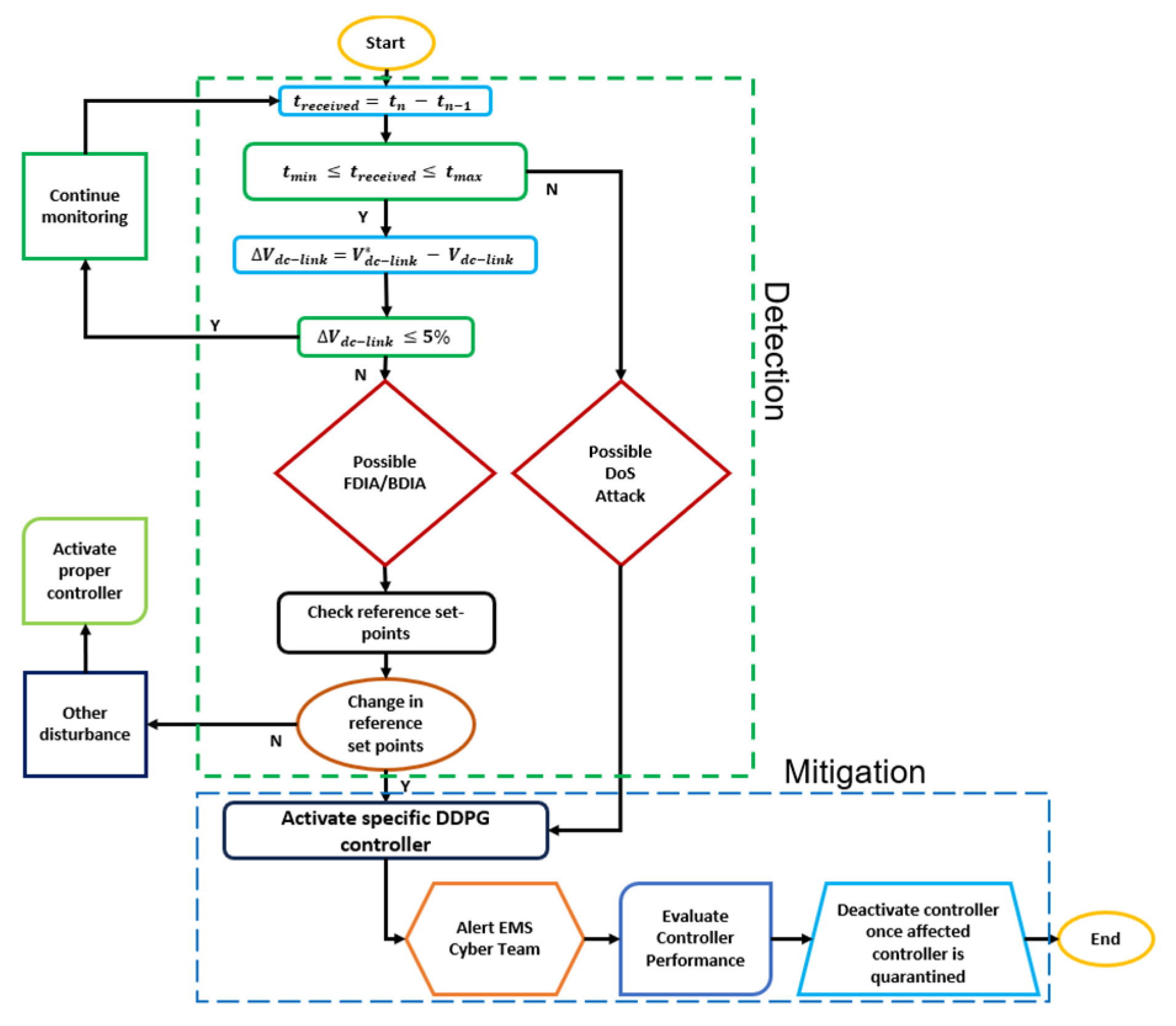
3.3. Cyber Attack Detection Method
4. Materials and Methods
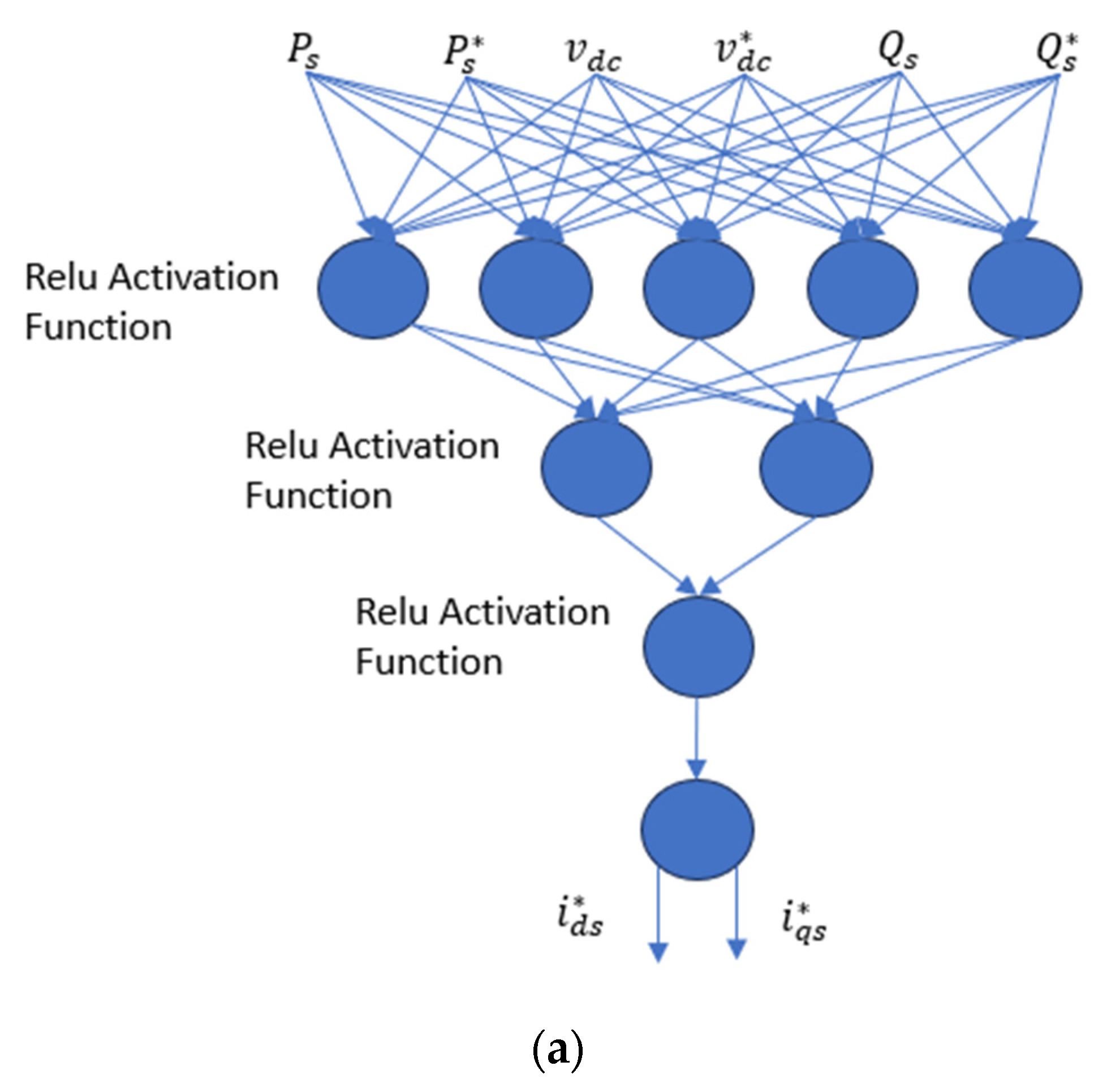
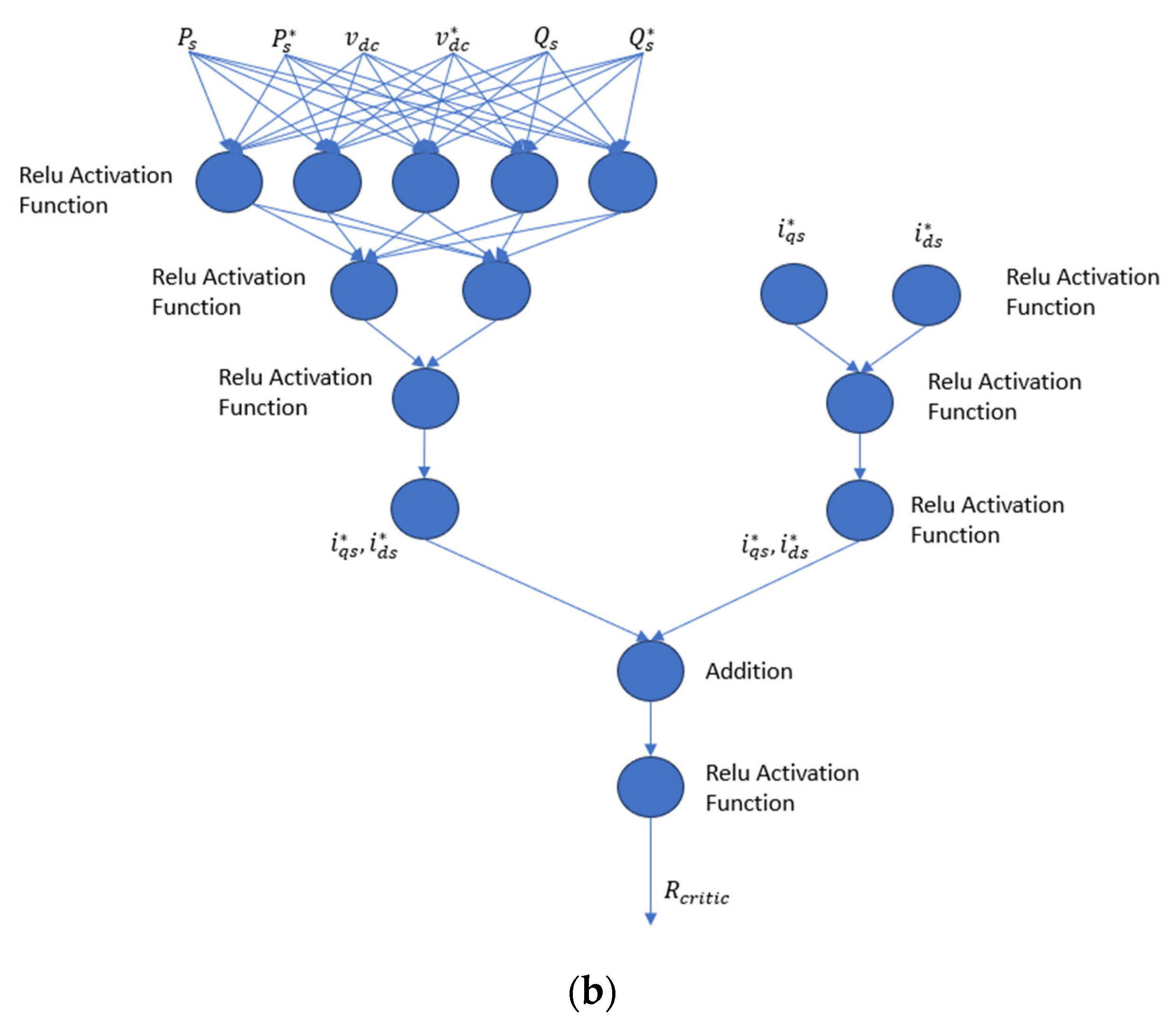
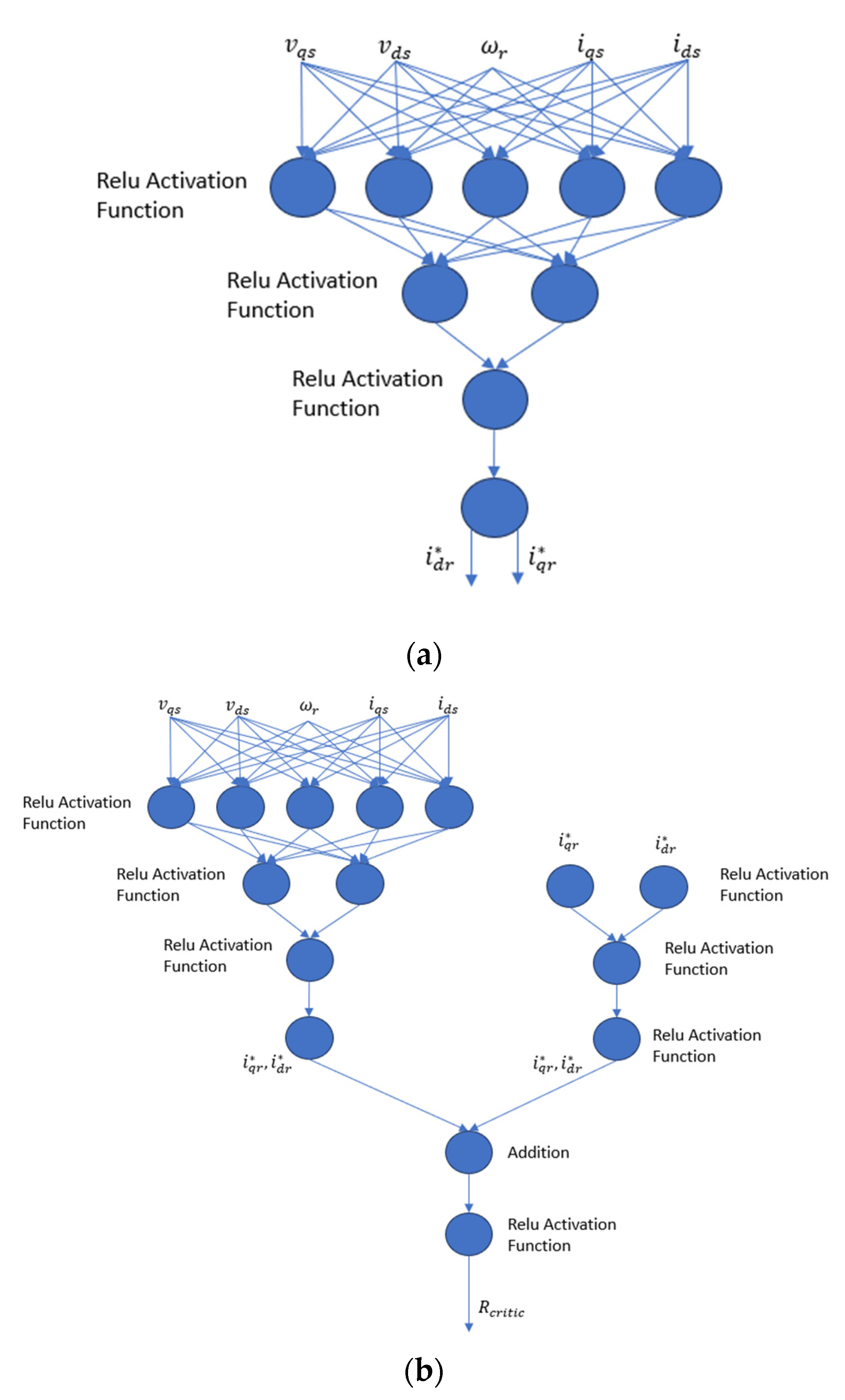
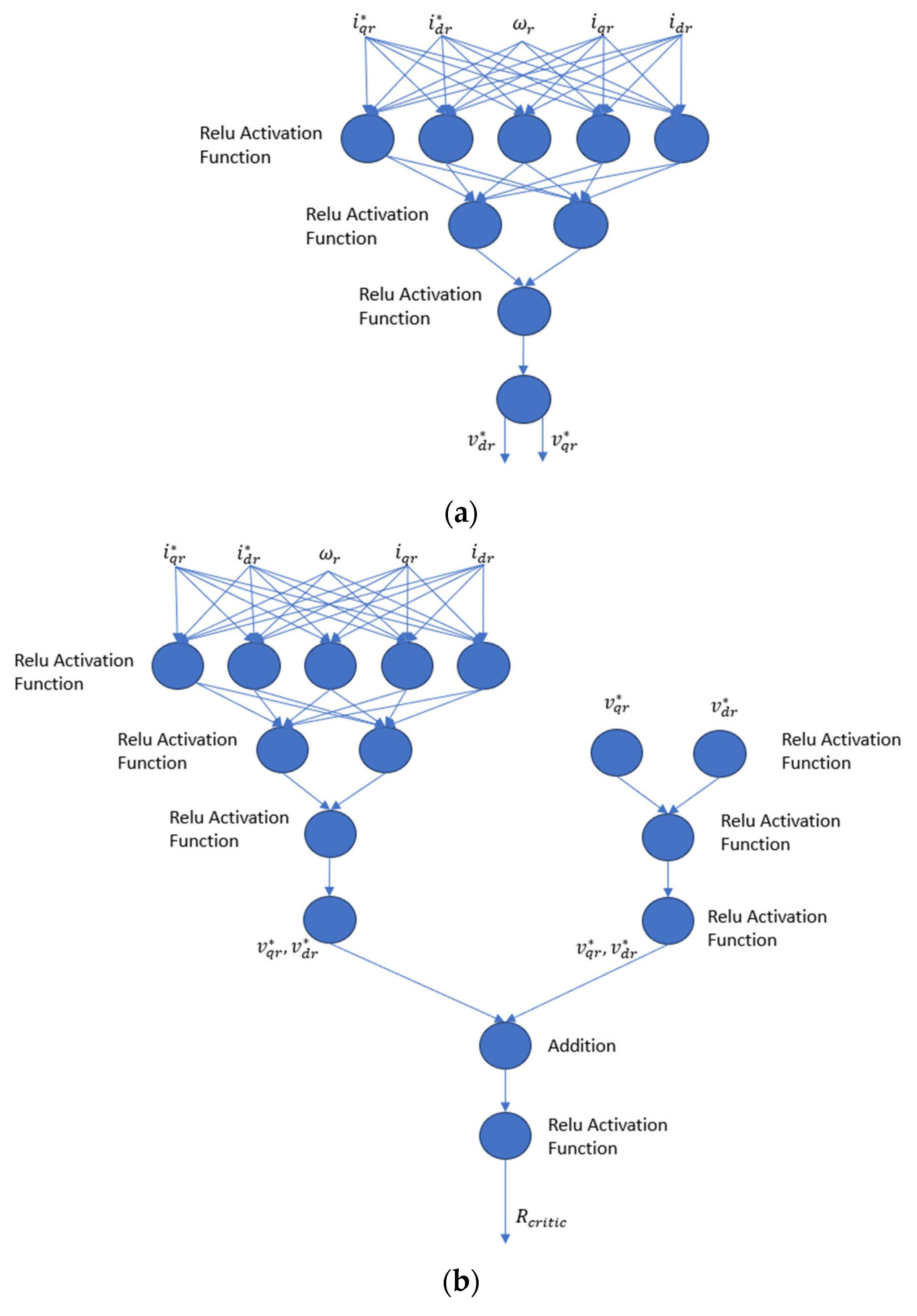
4.1. Deep Deterministic Policy Gradient (DDPG) Approach
- i.
- For the current observation S, select an action A = , where N is the stochastic noise.
- ii.
- Execute action A. Observe the reward and next observation .
- iii.
- Store the experience () in the experience buffer.
- iv.
- Sample a random mini batch of M experiences from the experience buffer.
- v.
- If is a terminal state, set the value function target to . Otherwise, set it to Equation (15).
- vi.
- Update the critic parameters by minimizing the loss, L, across all sampled experiences, as depicted in the following Equation (16).
- vii.
- Update the actor parameters using the following sampled policy gradient to maximize the expected discounted reward, as depicted in Equations (17)–(19).
- viii.
- Update the target actor and critic parameters depending on the target method.
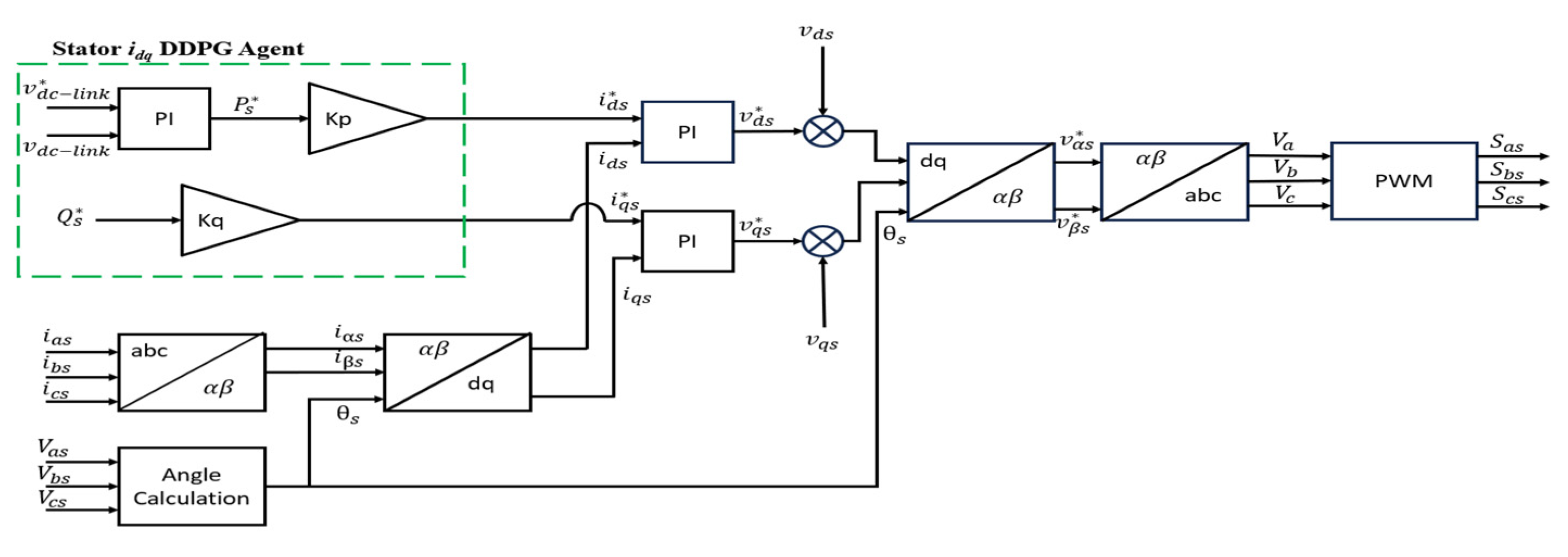
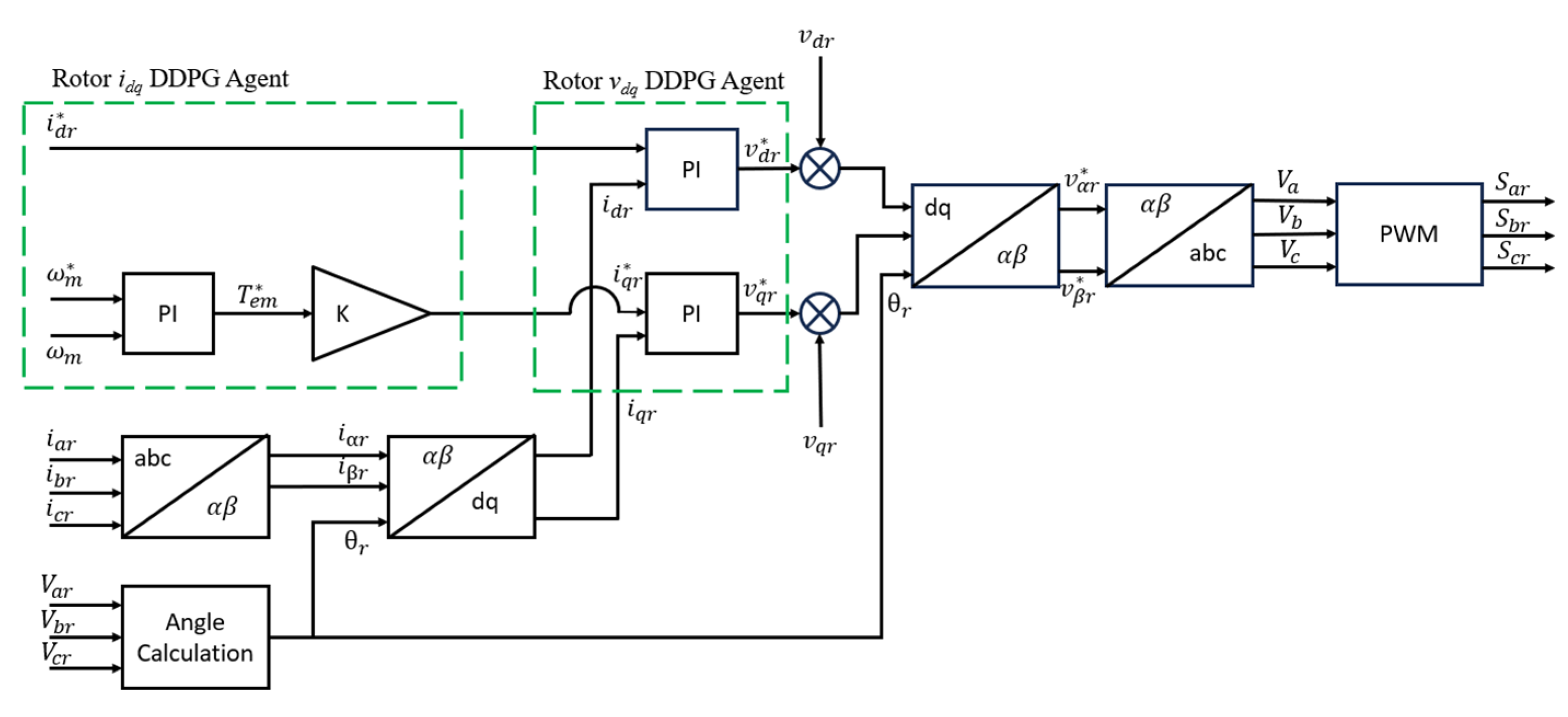
4.2. Proposed DDPG Control Methodology for Attack Mitigation
4.2.1. Stator Active and Reactive Power Measurement and Set Points
4.2.2. Stator Current Reference Point Sub-System
4.2.3. Rotor Current Set Point Sub-System
4.2.4. Rotor Voltage Set Point Sub-System
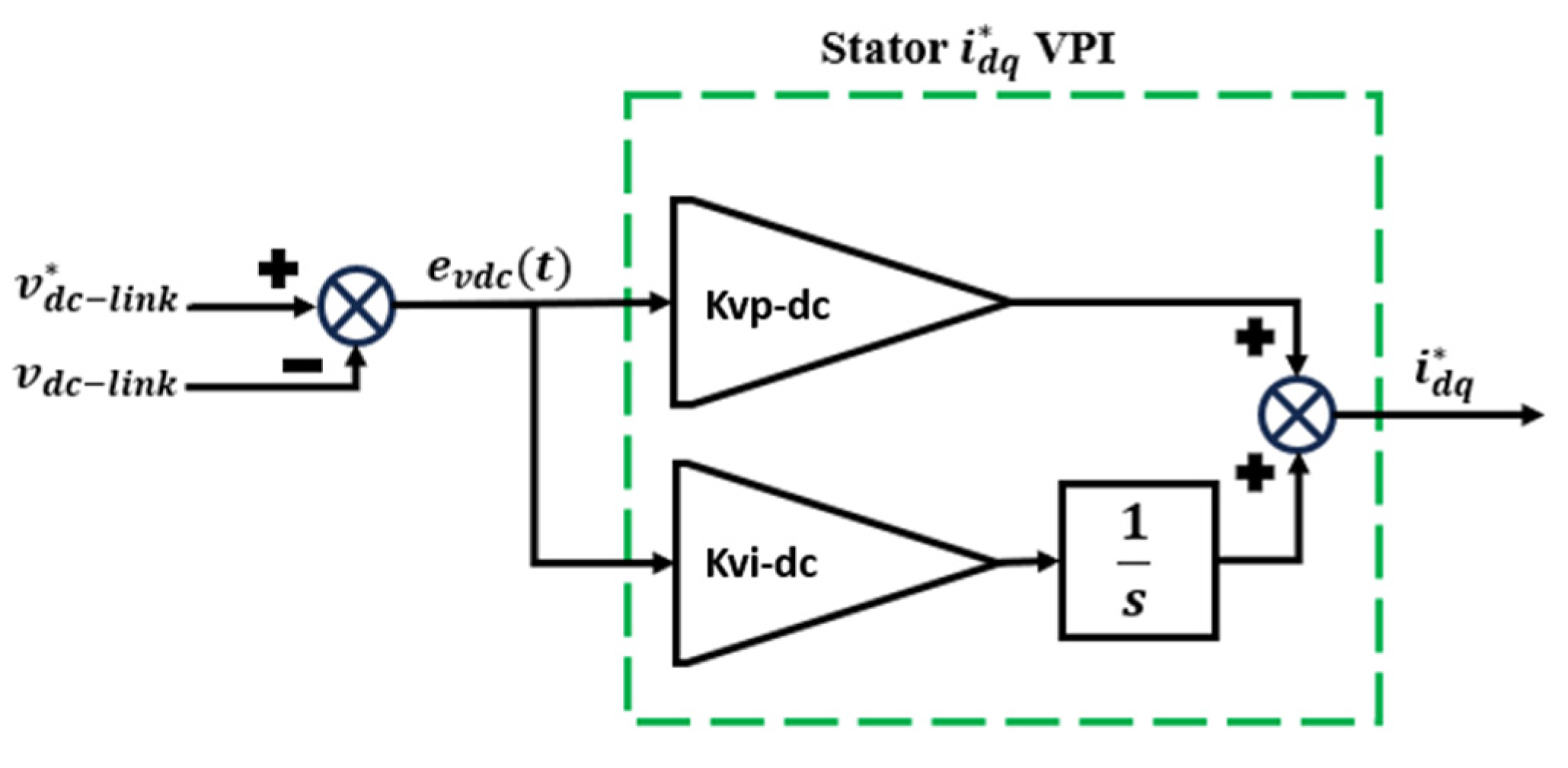
4.3. Proposed Variable Proportional–Integral (VPI) Control Methodology
evdc(t) = (Vdc_nom − Vdc)/Vdc-nom
[eidr(t); eiqr(t)] = [Idr_ref − Idr; Iqr_ref − iqr]
4.4. Conventional PI Controller
5. Results
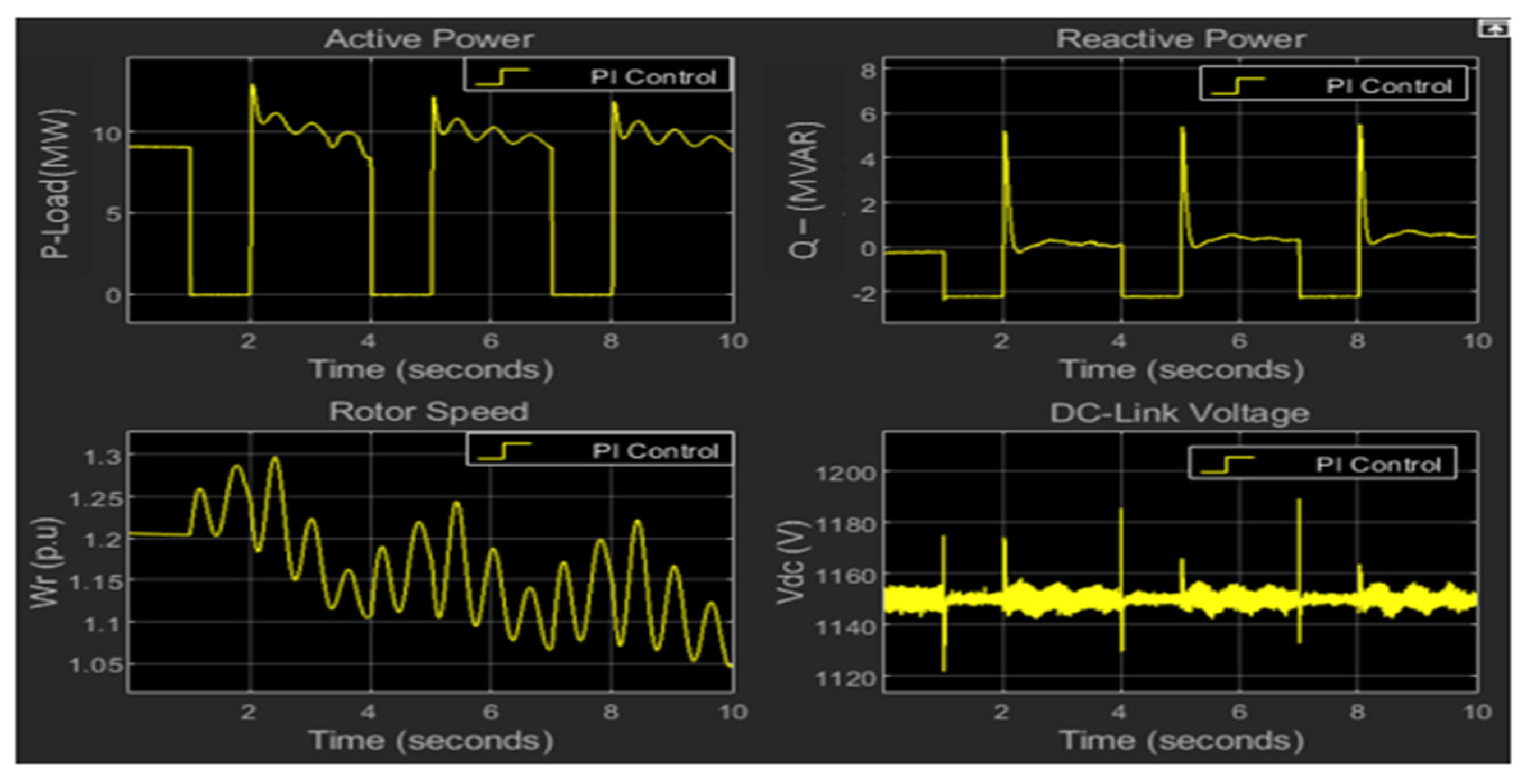
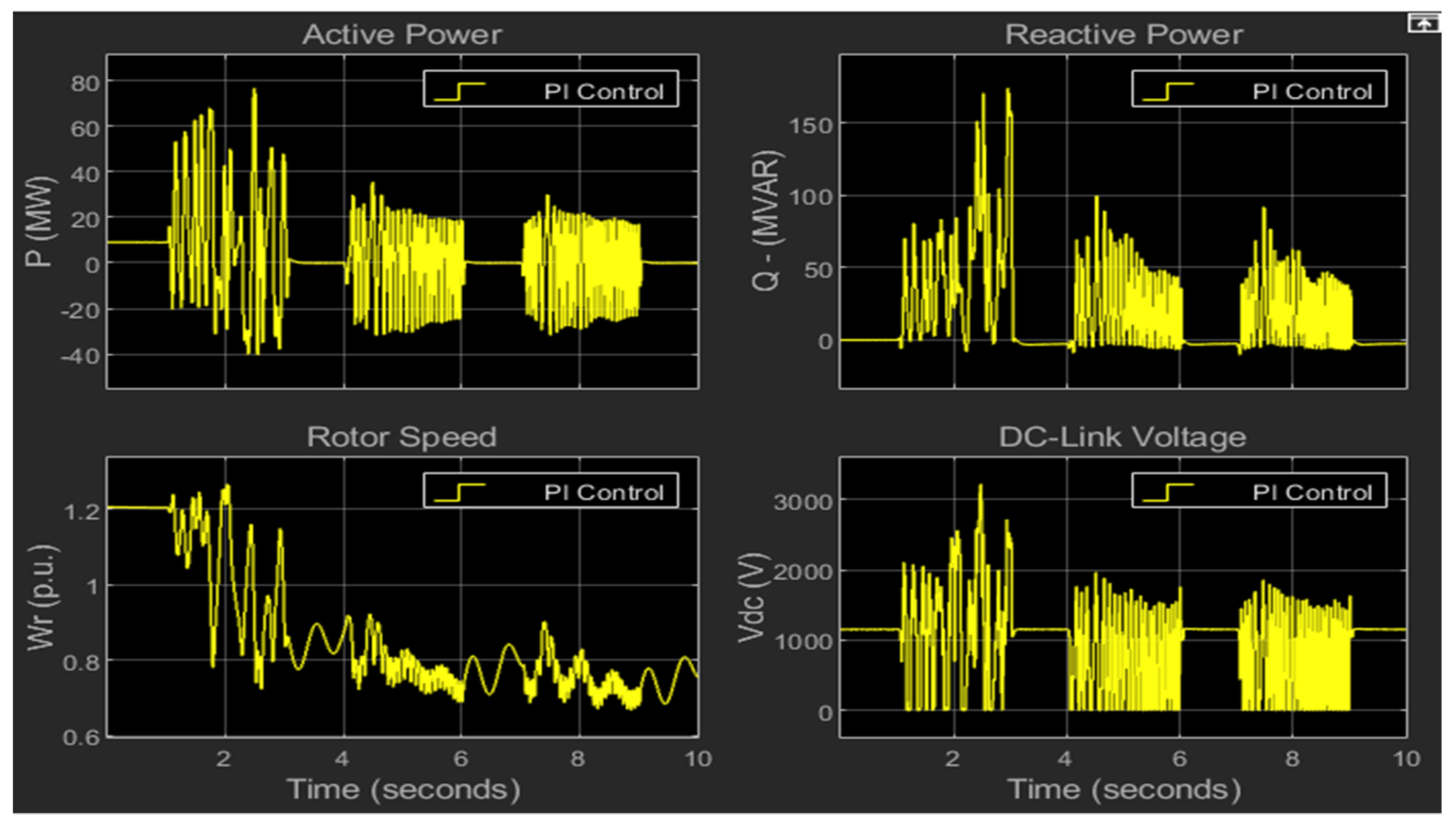
5.1. Cyber Attack Scenarios
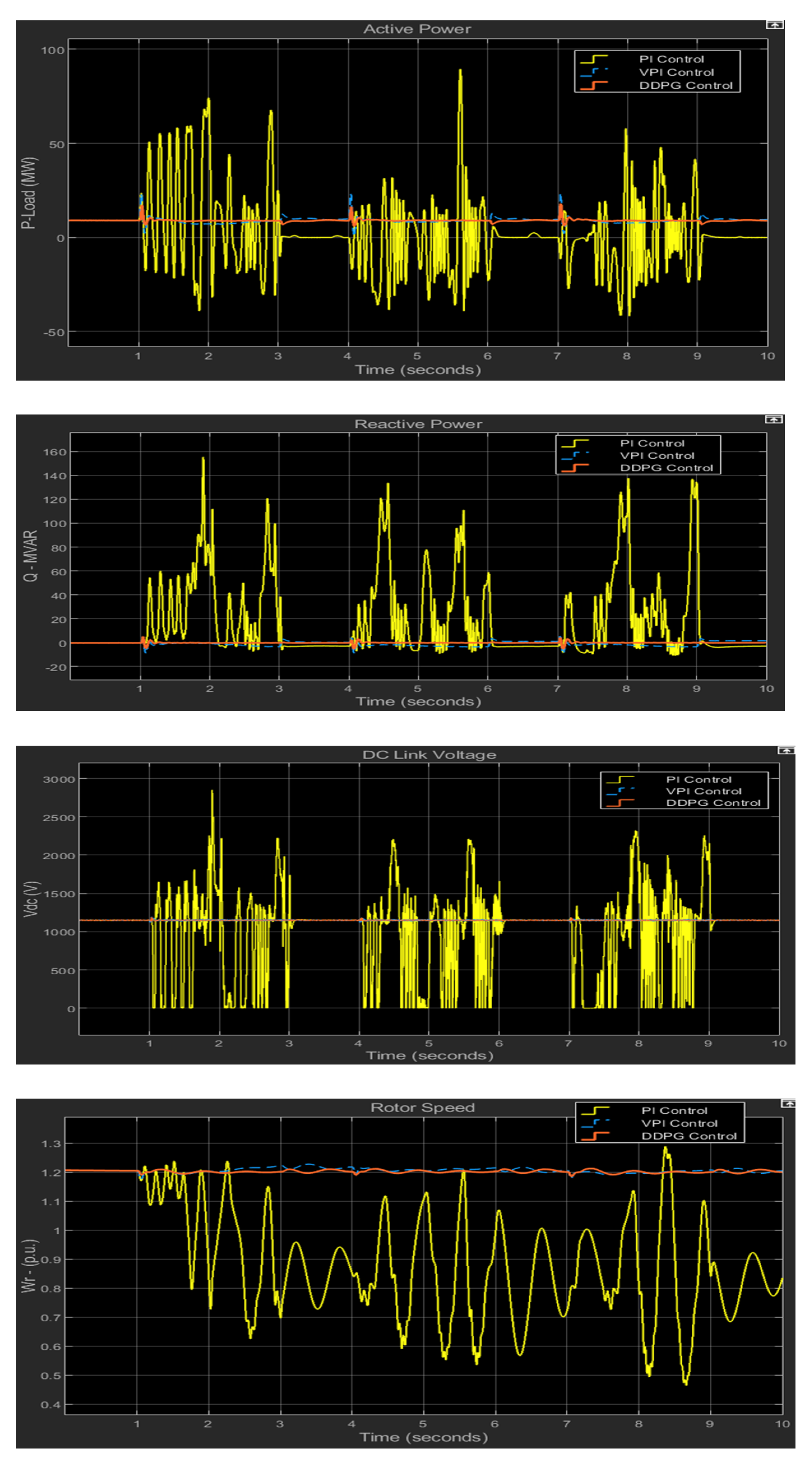
5.2. Effectiveness of Proposed Mitigation Method and Performance Comparison
5.3. Root Mean Square Error (RMSE) Performance Validation
6. Discussion
- The stator voltage controller can be replaced by a DDPG agent, allowing for the PWM signal to be replaced for the grid-side converter during a cyber-attack, like what was presented for the rotor-side control system.
- The method can be utilized for other DERs, such as ocean/wave energy production.
- The effects of a battery energy storage system on the DC-link circuit could be investigated to determine if better stability can be achieved.
- Exploring new AI detection and mitigation techniques based on the works presented in this paper could be explored.
7. Conclusions
- The proposed DDPG method can effectively mitigate the adverse effects of cyber attacks, regardless of which set point is manipulated or whether the PWM signal to the rotor-side converter is blocked.
- The performance of the proposed DDPG method is better than that of the VPI method, as shown in the plots and the RMSE table presented in the results section.
- This research offers a novel approach to mitigating cyber attacks on DERs by offering a low-cost approach to maintaining wind farm stability during a malicious cyber-attack on the converter management system.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial intelligence |
| ANN | Artificial neural network |
| BDIA | Bad data injection attack |
| CDM | Continuous diagnostics and mitigation |
| DT | Decision tree |
| DDPG | Deep deterministic policy gradient |
| DoS | Denial of service |
| DER | Distributed energy resource |
| DFIG | Double-fed induction generator |
| FDIA | False data injection attack |
| IGBT | Insulated-gate bipolar transistor |
| LAN | Local area network |
| MitM | Man in the middle |
| MaDIoT | Manipulation of data via IoT |
| NOAA | National Oceanic and Atmospheric Administration |
| PID | Proportional, integral, and derivative |
| PMSG | Permanent magnet synchronous generator |
| PIFPI | PI/fractional-order fuzzy/PI |
| PAC | Pitch angle controller |
| PLC | Programable logic controller |
| PWM | Pulse width modulated |
| RMSE | Root mean square error |
| SCADA | Supervisory control and data acquisition |
| SVM | Support vector machine |
| VSC | Voltage source converter |
| WAMPAC | Wide area monitoring, protection, and control |
| YAC | Yaw angle controller |
References
- Mahon, A. Wind Energy. Available online: https://www.pnnl.gov/wind-energy (accessed on 5 January 2024).
- U.S. Department of the Interior. Biden-Harris Administration Approves Sixth Offshore Wind Project. Available online: https://www.doi.gov/pressreleases/biden-harris-administration-approves-sixth-offshore-wind-project (accessed on 5 January 2024).
- Abdelmassih, G.; Al-Numay, M.; El Aroudi, A. Map optimization fuzzy logic framework in wind turbine site selection with application to the USA wind farms. Energies 2021, 14, 6127. [Google Scholar] [CrossRef]
- Chang-Chien, L.-R.; Sun, C.-C.; Yeh, Y.-J. Modeling of wind farm participation in AGC. IEEE Trans. Power Syst. 2013, 29, 1204–1211. [Google Scholar] [CrossRef]
- Adouni, A.; Chariag, D.; Diallo, D.; Hamed, M.B.; Sbita, L. FDI based on artificial neural network for low-voltage-ride-through in DFIG-based wind turbine. ISA Trans. 2016, 64, 353–364. [Google Scholar] [CrossRef] [PubMed]
- Al-Deen, K.A.N.; Hussain, H.A. Review of dc offshore wind farm topologies. In Proceedings of the 2021 IEEE Energy Conversion Congress and Exposition (ECCE), Vancouver, BC, Canada, 10–14 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 53–60. [Google Scholar]
- Stupp, C. European Wind-Energy Sector Hit in Wave of Hacks. The Wall Street Journal, 25 April 2022. Available online: https://www.wsj.com/articles/european-wind-energy-sector-hit-in-wave-of-hacks-11650879000 (accessed on 1 November 2022).
- Liu, J.; Gu, Y.; Zha, L.; Liu, Y.; Cao, J. Event-Triggered H∞ Load Frequency Control for Multiarea Power Systems Under Hybrid Cyber Attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1665–1678. [Google Scholar] [CrossRef]
- Singh; Kumar, V.; Sharma, R.; Govindarasu, M. Testbed-based performance evaluation of attack resilient control for wind farm scada system. In Proceedings of the 2020 IEEE Power & Energy Society General Meeting (PESGM), Montreal, QC, Canada, 2–6 August 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar]
- Yang, K.; Li, J.; Zhang, G.; Xing, Y.; Bamisile, O.; Huang, Q. A Cooperative Control Strategy against Cyber-attacks for Power System with High Penetration Wind Farm. In Proceedings of the 2022 4th Asia Energy and Electrical Engineering Symposium (AEEES), Chengdu, China, 25–28 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 321–327. [Google Scholar]
- Burgos-Mellado, C.; Donoso, F.; Dragičević, T.; Cardenas-Dobson, R.; Wheeler, P.; Clare, J.; Watson, A. Cyber-attacks in modular multilevel converters. IEEE Trans. Power Electron. 2022, 37, 8488–8501. [Google Scholar] [CrossRef]
- Sadi, H.M.A.; Zhao, D.; Hong, T.; Ali, M.H. Time Sequence Machine Learning-Based Data Intrusion Detection for Smart Voltage Source Converter-Enabled Power Grid. IEEE Syst. J. 2023, 17, 2477–2488. [Google Scholar] [CrossRef]
- Scott Rose Oliver Borchert Stu Mitchell Sean Connelly. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf (accessed on 7 August 2023).
- Mehdipour, C.; Hajizadeh, A.; Mehdipour, I. Dynamic modeling and control of DFIG-based wind turbines under balanced network conditions. Int. J. Electr. Power Energy Syst. 2016, 83, 560–569. [Google Scholar] [CrossRef]
- Chen, B.; Yim, S.I.; Kim, H.; Kondabathini, A.; Nuqui, R. Cybersecurity of wide area monitoring, protection, and control systems for hvdc applications. IEEE Trans. Power Syst. 2020, 36, 592–602. [Google Scholar] [CrossRef]
- De Carvalho, R.S.; Saleem, D. Recommended functionalities for improving cybersecurity of distributed energy resources. In Proceedings of the 2019 Resilience Week (RWS), San Antonio, TX, USA, 4–7 November 2019; IEEE: Piscataway, NJ, USA, 2019; Volume 1. [Google Scholar]
- Shekari, T.; Cardenas, A.A.; Beyah, R. {MaDIoT} 2.0: Modern {High-Wattage}{IoT} botnet attacks and defenses. In Proceedings of the 31st USENIX Security Symposium (USENIX Security 22), Boston, MA, USA, 10–12 August 2022; pp. 3539–3556. [Google Scholar]
- Wang, Z.; Zhang, H.; Cao, X.; Liu, E.; Li, H.; Zhang, J. Modeling and Detection Scheme for Zero-Dynamics Attack on Wind Power System. IEEE Trans. Smart Grid 2024, 15, 934–943. [Google Scholar] [CrossRef]
- Fallahnejad, M.; Kazemy, A.; Shafiee, M. Event-triggered H∞ stabilization of networked cascade control systems under periodic DoS attack: A switching approach. Int. J. Electr. Power Energy Syst. 2023, 153, 109278. [Google Scholar] [CrossRef]
- RlDDPGAgent. MathWorks. Available online: https://www.mathworks.com/help/reinforcement-learning/ug/ddpg-agents.html (accessed on 21 September 2023).
- Hodson, T.O. Root-Mean-Square Error (RMSE) or Mean Absolute Error (MAE): When to Use Them or Not. Geoscientific Model Development. Available online: https://gmd.copernicus.org/articles/15/5481/2022/ (accessed on 18 August 2023).




| Parameter | Value |
|---|---|
| Nominal power— | 10 MVA |
| Line-to-line nominal voltage— | 575 |
| Nominal rotor voltage— | 1975 |
| Nominal frequency— | 60 Hz |
| Stator resistance— | 0.023 p.u. |
| Stator inductance— | 0.18 p.u. |
| Rotor resistance— | 0.016 p.u. |
| Rotor inductance— | 0.16 p.u. |
| Mutual inductance— | 2.9 p.u. |
| Inertia constant—H | 0.685 s |
| Friction factor— | 0.01 p.u. |
| Number of pole pairs— | 3 |
| RSC PWM frequency— | 1620 Hz |
| GSC PWM frequency— | 2700 Hz |
| DC-link nominal voltage— | 1150 v |
| DC-link capacitor— | 10 mF |
| Nominal mechanical power— | 9 MW |
| Attack Type | Active Power RMSE | Reactive Power RMSE | Rotor Speed RMSE | DC-Link Voltage RMSE | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| DoS | FDIA | PI | VPI | DDPG | PI | VPI | DDPG | PI | VPI | DDPG | PI | VPI | DDPG | ||
| Case Study | 1 | ✓ | - | 6.97 | 7.07 | 0.88 | 1.78 | 1.87 | 1.10 | 0.119 | 0.120 | 0.006 | 2.07 | 1.89 | 2.32 |
| Case Study | 2 | - | ✓ | 8.08 | 0.94 | 0.08 | 2.12 | 1.08 | 1.81 | 0.20 | 0.004 | 0.003 | 14,459 | 264.62 | 57.14 |
| Case Study | 3 | - | ✓ | 18.3 | 0.75 | 0.79 | 29.65 | 0.80 | 0.77 | 0.423 | 0.005 | 0.001 | 582.43 | 2.23 | 2.22 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Farrar, N.; Ali, M.H. Cyber-Resilient Converter Control System for Doubly Fed Induction Generator-Based Wind Turbine Generators. Electronics 2024, 13, 492. https://doi.org/10.3390/electronics13030492
Farrar N, Ali MH. Cyber-Resilient Converter Control System for Doubly Fed Induction Generator-Based Wind Turbine Generators. Electronics. 2024; 13(3):492. https://doi.org/10.3390/electronics13030492
Chicago/Turabian StyleFarrar, Nathan, and Mohd. Hasan Ali. 2024. "Cyber-Resilient Converter Control System for Doubly Fed Induction Generator-Based Wind Turbine Generators" Electronics 13, no. 3: 492. https://doi.org/10.3390/electronics13030492





