A Comprehensive Survey of Cybersecurity Threats, Attacks, and Effective Countermeasures in Industrial Internet of Things
Abstract
:1. Introduction
- The objective is to promote a resilient industrial environment and provide a more efficient, cybersecurity-focused strategy.
- This study’s main contribution is to offer a thorough analysis of security hazards to manufacturing machinery and the most recent solutions to protect the infrastructure for researchers and organizations working with Industrial IoT technologies.
- It addresses these structures’ essential qualities and shortcomings and thoroughly analyzes all potential solutions to overcome the vulnerabilities, as recommended in recent research.
- The supplied evaluation and analytic paradigm set this research effort apart from other IIoT studies.
- It provides a thorough, current, and reliable standard for detecting and evaluating risks in the constantly changing workplace.
- This article offers a comprehensive analysis of the countermeasures that have been advanced in the most recent research articles.
- We examine many types of attacks and their possible consequences to understand the security landscape in the IIoT area.
2. Related Literature
- Intercepting communications on a wired or wireless network [19] between master terminal units (MTUs), sub-MTUs, or remote terminal units (RTUs) is known as passive or active monitoring. To exploit the collected data, an attacker with network access can install malware [20]. A man-in-the-middle (MitM) attack [21] is when an individual observes and intercepts network traffic to modify and deliver data to the intended recipient [22,23]. When a breach is successful, the attacker seizes control of the session and keeps the connection going while using a fake IP address to evade detection [24,25].
- Masquerading assaults happen when a hacker adopts an alias and uses a fake IP address to pretend to be an authorized network client to take data from the system or network [26,27]. Brute force attacks may use stolen credentials to access critical data without authorization [28]. After conducting MitM or hybrid assaults, intruders may use infectious agents, Trojan horses, or worms [29,30,31]. Unauthorized people may gain access to the compromised system through malicious code, maybe exploiting it to launch more attacks on other infrastructure. Alternatively, the code may infect more MSUs/MTUs across the network, leading to unstable behavior or system failure [32,33].
- Rogue RTUs overwhelm the MTU with arbitrary IP addresses during denial of service (DoS) or distributed denial of service (DDoS) threats, draining the framework’s resources and making it unusable [1,34,35,36,37,38,39]. These threats make use of internet packet-based fragmentation flaws. The MSU/MTU is unable to manage data transmissions that are larger than the maximum transmission unit size, which results in a loss of connectivity and system breakdown [3,40,41,42].
- A Cinderella-like attack happens when an evil individual modifies the system’s intrinsic schedule after gaining unauthorized access to a machine. The computer system’s vulnerability is increased by this early expiration of security software 4.7 [43,44]. Doorknob rattling entails preparations, including legal methods for system testing. To assess the readiness and responsiveness of security measures, for instance, a small number of efforts to enter the network using randomized criteria are attempted [45,46].
3. Security Attacks with Countermeasures
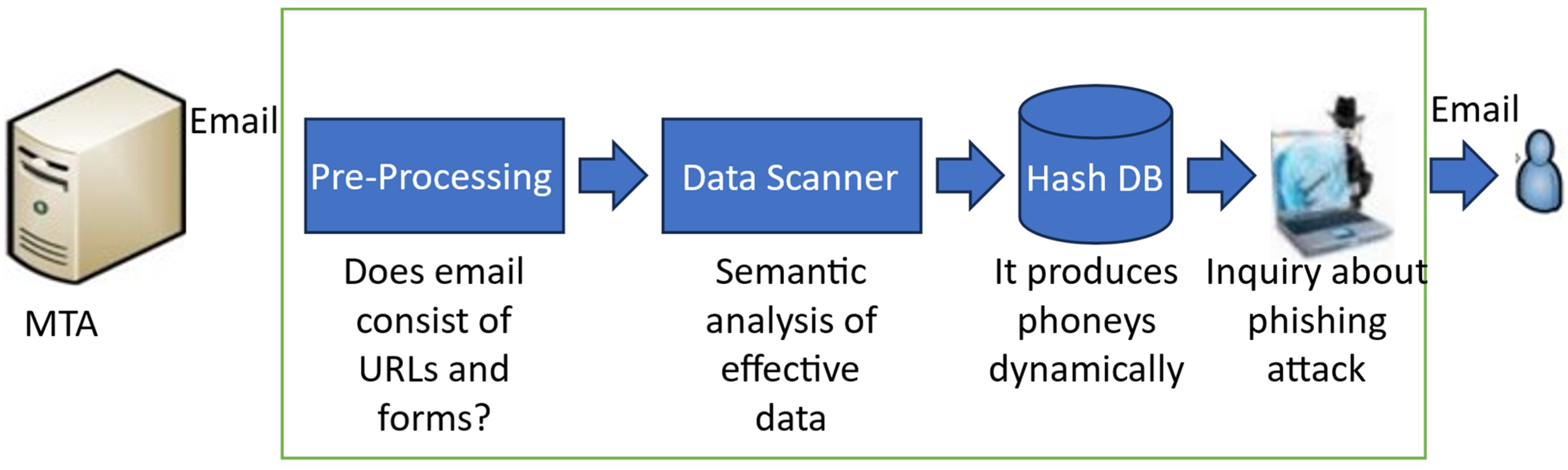
3.1. Attacks by Phishers
3.2. Attacks by Ransomware
3.3. Attacks on Protocols
3.3.1. Attacks on Physical and Data-Link Layers
3.3.2. Attacks on Network Layer
3.3.3. Attacks on Transport Layer
3.3.4. Attacks on Application Layer
3.4. Attacks by Supply-Chain
3.5. Attacks by Whole System
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Alcácer, V.; Cruz-Machado, V. Scanning the Industry 4.0: A Literature Review on Technologies for Manufacturing Systems. Eng. Sci. Technol. Int. J. 2019, 22, 899–919. [Google Scholar] [CrossRef]
- Banafa, A. The Industrial Internet of Things (IIoT): Challenges, requirements and benefits. In Secure and Smart Internet of Things (IoT): Using Blockchain and AI; River Publishers: Gistrup, Denmark, 2018; pp. 7–12. [Google Scholar]
- Soori, H.; Arezoo, B.; Dastres, R. Internet of things for smart factories in industry 4.0, a review. Internet Things Cyber-Phys. Syst. 2023, 3, 192–204. [Google Scholar] [CrossRef]
- Ani, U.P.D.; He, H.; Tiwari, A. Review of cybersecurity issues in industrial critical infrastructure: Manufacturing in perspective. J. Cyber Secur. Technol. 2016, 1, 32–74. [Google Scholar] [CrossRef]
- Yuan, X.-M. Impact of Industry 4.0 on Inventory Systems and Optimizations; IntechOpen: London, UK, 2020. [Google Scholar] [CrossRef]
- Qiu, B.; Gooi, H.B.; Liu, Y.; Chan, E.K. Internet-based SCADA display system, Computer Applications in Power. IEEE Comput. Appl. Power 2002, 15, 14–19. [Google Scholar]
- Williams, P.; Dutta, I.K.; Daoud, H.; Bayoumi, M. A survey on security in internet of things with a focus on the impact of emerging technologies. Internet Things 2022, 19, 100564. [Google Scholar] [CrossRef]
- Perwej, Y.; Abbas, S.Q.; Dixit, J.P.; Akhtar, N.; Jaiswal, A.K. A Systematic Literature Review on the Cyber Security. Int. J. Sci. Res. Manag. 2021, 9, 669–710. [Google Scholar] [CrossRef]
- Wang, J.-W.; Rong, L.-L. Robustness of the western United States power grid under edge attack strategies due to cascading failures. Saf. Sci. 2011, 49, 807–812. [Google Scholar] [CrossRef]
- Alanazi, M.; Mahmood, A.; Chowdhury, M.J.M. SCADA vulnerabilities and attacks: A review of the state-of-the-art and open issues. Comput. Secur. 2023, 125, 103028. [Google Scholar] [CrossRef]
- Farman, H.; Khalil, A.; Ahmad, N.; Albattah, W.; Khan, M.A.; Islam, M. A Privacy Preserved, Trust Relationship (PTR) Model for Internet of Vehicles. Electronics 2021, 10, 3105. [Google Scholar] [CrossRef]
- Panchal, A.C.; Khadse, V.M.; Mahalle, P.N. Security issues in IIoT: A comprehensive survey of attacks on IIoT and its countermeasures. In Proceedings of the 2018 IEEE Global Conference on Wireless Computing and Networking (GCWCN), Lonavala, India, 23–24 November 2018; IEEE: New York, NY, USA, 2018; pp. 124–130. [Google Scholar]
- Ghori, M.R.; Wan, T.C.; Sodhy, G.C. Bluetooth low energy mesh networks: Survey of communication and security protocols. Sensors 2020, 20, 3590. [Google Scholar] [CrossRef]
- Yadav, G.; Paul, K. Architecture and security of SCADA systems: A review. Int. J. Crit. Infrastruct. Prot. 2021, 34, 100433. [Google Scholar] [CrossRef]
- Mekala, S.H.; Baig, Z.; Anwar, A.; Zeadally, S. Cybersecurity for industrial IoT (IIoT): Threats, countermeasures, challenges and future directions. Comput. Commun. 2023, 208, 294–320. [Google Scholar] [CrossRef]
- Zuhaib, M.; Shaikh, F.A.; Tanweer, W.; Alnajim, A.M.; Alyahya, S.; Khan, S.; Usman, M.; Islam, M.; Hasan, M.K. Faults Feature Extraction Using Discrete Wavelet Transform and Artificial Neural Network for Induction Motor Availability Monitoring—Internet of Things Enabled Environment. Energies 2022, 15, 7888. [Google Scholar] [CrossRef]
- Gerodimos, A.; Maglaras, L.; Ferrag, M.A.; Ayres, N.; Kantzavelou, I. IoT: Communication protocols and security threats. Internet Things Cyber-Phys. Syst. 2023, 3, 1–13. [Google Scholar] [CrossRef]
- Huda, S.; Yearwood, J.; Hassan, M.M.; Almogren, A. Securing the operations in SCADA-IoT platform based industrial control system using ensemble of deep belief networks. Appl. Soft Comput. 2018, 71, 66–77. [Google Scholar] [CrossRef]
- Pliatsios, D.; Sarigiannidis, P.; Lagkas, T.; Sarigiannidis, A.G. A Survey on SCADA Systems: Secure Protocols, Incidents, Threats and Tactics. IEEE Commun. Surv. Tutor. 2020, 22, 1942–1976. [Google Scholar] [CrossRef]
- Parker, D. Fighting Computer Crime; Wiley: New York, NY, USA, 1998; ISBN 0471163783. [Google Scholar]
- Spafford, E. Quotable Spaf, Gene Spafford’s Personal Pages. Available online: http://spaf.cerias.purdue.edu/quotes.html (accessed on 13 June 2023).
- Zhu, B.; Joseph, A.; Sastry, S. A taxonomy of cyber-attacks on SCADA systems. In Proceedings of the 2011 International Conference on Internet of Things and 4th International Conference on Cyber Physical and Social Computing, Dalian, China, 19–22 October 2011; pp. 380–388. [Google Scholar]
- Majeed, A.; Alnajim, A.M.; Waseem, A.; Khaliq, A.; Naveed, A.; Habib, S.; Islam, M.; Khan, S. Deep Learning-Based Symptomizing Cyber Threats Using Adaptive 5G Shared Slice Security Approaches. Future Internet 2023, 15, 193. [Google Scholar] [CrossRef]
- Setiadi, F.; Putra, P.H.; Sucahyo, Y.G.; Hasibuan, Z.A. Determining components of national cyber security framework using Grounded Theory. In Proceedings of the Second International Conference on Informatics and Computing, Jayapura, Indonesia, 1–3 November 2017; pp. 1–6. [Google Scholar]
- Trifonov, R.; Manolov, G.; Yoshinov, R.; Pavlova, G. A survey of artificial intelligence for enhancing the information security. Int. J. Dev. Res. 2017, 7, 16866–16872. [Google Scholar]
- Takiddin, A.; Ismail, M.; Zafar, U.; Serpedin, E. Deep autoencoder-based anomaly detection of electricity theft cyberattacks in smart grids. IEEE Syst. J. 2022, 16, 4106–4117. [Google Scholar] [CrossRef]
- Podder, P.; Bharati, S.; Mondal, M.; Paul, P.K.; Kose, U. Artificial neural network for cybersecurity: A comprehensive review. arXiv 2021, arXiv:2107.01185. [Google Scholar]
- Albattah, W.; Khel, M.H.K.; Habib, S.; Islam, M.; Khan, S.; Abdul Kadir, K. Hajj Crowd Management Using CNN-Based Approach. Comput. Mater. Contin. 2020, 66, 2183–2197. [Google Scholar] [CrossRef]
- Alnajim, A.M.; Habib, S.; Islam, M.; Albelaihi, R.; Alabdulatif, A. Mitigating the Risks of Malware Attacks with Deep Learning Techniques. Electronics 2023, 12, 3166. [Google Scholar] [CrossRef]
- Thomas, K.; Grier, C.; Ma, J.; Paxson, V.; Song, D. Design and evaluation of a real-time url spam filtering service. In Proceedings of the IEEE Symposium on Security and Privacy (SP), Oakland, CA, USA, 22–25 May 2011; IEEE: New York, NY, USA, 2011; pp. 447–462. [Google Scholar]
- Khan, K.; Khan, R.U.; Albattah, W.; Nayab, D.; Qamar, A.M.; Habib, S.; Islam, M. Crowd Counting Using End-to-End Semantic Image Segmentation. Electronics 2021, 10, 1293. [Google Scholar] [CrossRef]
- Stewart, K.E.; Humphries, J.W.; Andel, T.R. Developing a virtualization platform for courses in networking, systems administration and cyber security education. In Proceedings of the 2009 Spring Simulation Multiconference, San Diego, CA, USA, 22–27 March 2009; SpringSim, Society for Computer Simulation International: San Diego, CA, USA, 2009. [Google Scholar]
- Stringhini, G.; Thonnard, O. That Aint You: Blocking Spearphishing through Behavioral Modelling. In Detection of Intrusions and Malware, and Vulnerability Assessment; Springer: Berlin/Heidelberg, Germany, 2015; pp. 78–97. [Google Scholar]
- Ibrahim, K.; Alnajim, A.M.; Naveed Malik, A.; Waseem, A.; Alyahya, S.; Islam, M.; Khan, S. Entice to Trap: Enhanced Protection against a Rate-Aware Intelligent Jammer in Cognitive Radio Networks. Sustainability 2022, 14, 2957. [Google Scholar] [CrossRef]
- Wang, Y. Statistical Techniques for Network Security, Modern StatisticallyBased Intrusion Detection and Protection; IGI Global: Hershey, PA, USA, 2008. [Google Scholar]
- Jin, D.; Nicol, D.M.; Yan, G. An event buffer flooding attack in DNP3 controlled SCADA systems. In Proceedings of the 2011 Winter Simulation Conference (WSC), Phoenix, AZ, USA, 11–14 December 2011; pp. 2614–2626. [Google Scholar]
- Ahmad, I.; Abdullah, A.B.; Alghamdi, A.S. Evaluating neural network intrusion detection approaches using Analytic Hierarchy Process. In Proceedings of the 2010 International Symposium on Information Technology, Kuala Lumpur, Malaysia, 15–17 June 2010; Volume 2, pp. 885–890. [Google Scholar]
- Yang, D.; Usynin, A.; Hines, J.W. Anomaly-Based Intrusion Detection for SCADA Systems; Technical Meeting on Cyber Security, Idaho; International Atomic Energy Agency (IAEA): Vienna, Austria, 2006. [Google Scholar]
- Linda, O.; Manic, M.; McQueen, M. Improving Control System Cyber-State Awareness using Known Secure Sensor Measurements. In Proceedings of the 7th International Conference on Critical Information Infrastructure Security, CRITIS 2012, Lillehammer, Norway, 17–18 September 2012. [Google Scholar]
- Wang, Y.-C.; Joshi, M.; Rose, C.P.; Fischer, F.; Weinberger, A.; Stegmann, K. Context Based Classification for Automatic Collaborative Learning Process Analysis; Artificial Intelligence in Education; IOS Press: Los Angeles, CA, USA, 2007. [Google Scholar]
- Papp, D.; Ma, Z.; Buttyan, L. Embedded systems security: Threats, vulnerabilities, and attack taxonomy. In Proceedings of the IEEE 13th Annual Conference on Privacy, Security and Trust (PST), Izmir, Turkey, 21–23 July 2015. [Google Scholar] [CrossRef]
- Marco, C.; Stavrou, I.; Dimmock, S.; Jhonson, C. Introducing a Forensics Data Type Taxonomy of Acquirable Artefacts from Programmable Logic Controllers; IEEE: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Ghosh, S.; Sampalli, S. A Survey of Security in SCADA Networks: Current Issues and Future Challenges. IEEE Access 2019, 7, 135812–135831. [Google Scholar] [CrossRef]
- Maglaras, L.A.; Jiang, J. Intrusion detection in SCADA systems using machine learning techniques. In Proceedings of the Science and Information (SAI) Conference 2014, London, UK, 27–29 August 2014; pp. 626–631. [Google Scholar]
- Hassan, Z.; Ali, H.; Badawy, M. Internet of Things (IoT): Definitions, Challenges, and Recent Research Directions. Int. J. Comput. Appl. 2015, 128, 975–8887. [Google Scholar]
- Gupta, A.; Christie, R.; Manjula, R. Scalability in Internet of Things: Features, Techniques and Research Challenges. Int. J. Comput. Intell. Res. 2017, 13, 1617–1627. [Google Scholar]
- Yu, X.; Guo, H. A Survey on IIoT Security. In Proceedings of the 2019 IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS), Singapore, 28–30 August 2019; pp. 1–5. [Google Scholar]
- Rondanini, C.; Carminati, B.; Ferrari, E. Confidential Discovery of IoT Devices through Blockchain. In Proceedings of the 2019 IEEE International Congress on Internet of Things (ICIOT), Milan, Italy, 8–13 July 2019; pp. 1–8. [Google Scholar]
- Ma, J.; Shang, B.; Song, H.; Huang, Y.; Fan, P. Reliability versus Latency in IIoT Visual Applications: A Scalable Task Offloading Framework. IEEE Internet Things J. 2022, 9, 16726–16735. [Google Scholar] [CrossRef]
- Iorga, M.; Feldman, L.; Barton, R.; Martin, M.J.; Goren, N.; Mahmoudi, C. Fog Computing Conceptual Model; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar]
- Chandrasekaran, M.; Chinchani, R.; Upadhyaya, S. PHONEY: Mimicking user response to detect phishing attacks. In Proceedings of the 2006 International Symposium on a World of Wireless, Mobile and Multimedia Networks(WoWMoM’06), Buffalo-Niagara Falls, NY, USA, 26–29 June 2006. [Google Scholar]
- Basit, A.; Zafar, M.; Liu, X.; Javed, A.R.; Jalil, Z.; Kifayat, K. A comprehensive survey of AIenabled phishing attacks detection techniques. Telecommun. Syst. 2020, 76, 139–154. [Google Scholar] [CrossRef]
- Khonji, M.; Iraqi, Y.; Jones, A. Phishing Detection: A Literature Survey. IEEE Commun. Surv. Tutor. 2013, 15, 2091–2121. [Google Scholar] [CrossRef]
- Abdelhamid, N.; Thabtah, F.; Abdel-jaber, H. Phishing detection: A recent intelligent machine learning comparison based on models content and features. In Proceedings of the 2017 IEEE International Conference on Intelligence and Security Informatics (ISI), Beijing, China, 22–24 July 2017; pp. 72–77. [Google Scholar] [CrossRef]
- Che, H.; Liu, Q.; Zou, L.; Yang, H.; Zhou, D.; Yu, F. A Content-Based Phishing Email Detection Method. In Proceedings of the 2017 IEEE International Conference on Software Quality, Reliability and Security Companion (QRS-C), Prague, Czech Republic, 25–29 July 2017; pp. 415–422. [Google Scholar] [CrossRef]
- Rao, R.S.; Ali, S.T. PhishShield: A Desktop Application to Detect Phishing Webpages through Heuristic Approach. Procedia Comput. Sci. 2015, 54, 147–156. [Google Scholar] [CrossRef]
- Cuzzocrea, A.; Martinelli, F.; Mercaldo, F. A machine-learning framework for supporting intelligent web-phishing detection and analysis. In Proceedings of the 23rd International Database Applications & Engineering Symposium on-IDEAS ‘19, Athens, Greece, 10–12 June 2019; pp. 1–3. [Google Scholar] [CrossRef]
- Yadollahi, M.M.; Shoeleh, F.; Serkani, E.; Madani, A.; Gharaee, H. An Adaptive Machine Learning Based Approach for Phishing Detection Using Hybrid Features. In Proceedings of the 2019 5th International Conference on Web Research (ICWR), Tehran, Iran, 24–25 April 2019; pp. 281–286. [Google Scholar] [CrossRef]
- Sonowal, G.; Kuppusamy, K.S. PhiDMA–A phishing detection model with multi-filter approach. J. King Saud Univ.-Comput. Inf. Sci. 2020, 32, 99–112. [Google Scholar] [CrossRef]
- Gupta, B.B.; Jain, A.K. Phishing Attack Detection using a Search Engine and Heuristicsbased Technique. J. Inf. Technol. Res. 2020, 13, 94–109. [Google Scholar] [CrossRef]
- Zavarsky, M.P.; Lindskog, D. Experimental Analysis of Ransomware on Windows and AISLAMndroid Platforms. Evol. Charact. 2016, 94, 465–472. [Google Scholar]
- Skrzewski, M. Monitoring Malware Activity on the LAN Network; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Alliance for Community Empowerment. Lucrative Ransomware Attacks: Analysis of the CryptoWall Version 4 Threat; Cryptowall Version 4 Threat Report; Alliance for Community Empowermen: Bridgeport, CT, USA, 2016. [Google Scholar]
- Yar, H.; Hussain, T.; Khan, Z.A.; Koundal, D.; Lee, M.Y.; Baik, S.W. Vision sensor-based real-time fire detection in resource-constrained IoT environments. Comput. Intell. Neurosci. 2021, 2021, 5195508. [Google Scholar] [CrossRef] [PubMed]
- Yar, H.; Hussain, T.; Agarwal, M.; Khan, Z.A.; Gupta, S.K.; Baik, S.W. Optimized Dual Fire Attention Network and Medium-Scale Fire Classification Benchmark. IEEE Trans. Image Process. 2022, 31, 6331–6343. [Google Scholar] [CrossRef]
- Ali, H.; Farman, H.; Yar, H.; Khan, Z.; Habib, S.; Ammar, A. Deep learning-based election results prediction using Twitter activity. Soft Comput. 2021, 26, 7535–7543. [Google Scholar] [CrossRef]
- Yar, H.; Khan, Z.A.; Ullah, F.U.M.; Ullah, W.; Baik, S.W. A modified YOLOv5 architecture for efficient fire detection in smart cities. Expert Syst. Appl. 2023, 231, 120465. [Google Scholar] [CrossRef]
- Trend Micro. Ransomware Recap: New Families and Updated Variants in June; Trend Micro Incorporated Labs Report; Trend Micro: Tokyo, Japan, 2016. [Google Scholar]
- Yorkdale. Criminals Continue to Defraud and Extort Funds from Victims Using CryptoWall Ransomware Schemes; Federal Bureau of Investigation: Washington, DC, USA, 2015. [Google Scholar]
- Khan, Z.A.; Hussain, T.; Ullah, F.U.M.; Gupta, S.K.; Lee, M.Y.; Baik, S.W. Randomly Initialized CNN with Densely Connected Stacked Autoencoder for Efficient Fire Detection. Eng. Appl. Artif. Intell. 2022, 116, 105403. [Google Scholar] [CrossRef]
- Maiorca, D.; Mercaldo, F.; Giacinto, G.; Visaggio, C.A.; Martinelli, F. R-PackDroid: API package-based characterization and detection of mobile ransomware. In Proceedings of the Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017; pp. 1718–1723. [Google Scholar]
- Sgandurra, D.; Muñoz-González, L.; Mohsen, R.; Lupu, E.C. Automated Dynamic Analysis of Ransomware: Benefits, Limitations and Use for Detection. ArXiv160903020 Cs. September 2016. Available online: http://arxiv.org/abs/1609.03020 (accessed on 20 January 2021).
- Tseng, A.; Chen, Y.; Kao, Y.; Lin, T. Deep learning for ransomware detection. IEICE Tech. Rep. 2016, 116, 87–92. [Google Scholar]
- Abolhasan, M.; Wysocki, T.; Dutkiewicz, E. A review of routing protocols for mobile ad hoc networks. Ad. Hoc. Netw. 2004, 2, 1–22. [Google Scholar] [CrossRef]
- Hu, Y.C.; Perrig, A.; Johnson, D.B. Ariadne: A Secure On-Demand Routing Protocol for Ad Hoc Networks. Wirel. Netw. 2005, 11, 21–38. [Google Scholar] [CrossRef]
- Albattah, W.; Habib, S.; Alsharekh, M.F.; Islam, M.; Albahli, S.; Dewi, D.A. An Overview of the Current Challenges, Trends, and Protocols in the Field of Vehicular Communication. Electronics 2022, 11, 3581. [Google Scholar] [CrossRef]
- Ojetunde, B.; Shibata, N.; Gao, J. Securing Link State Routing for Wireless Networks against Byzantine Attacks: A Monitoring Approach. In Proceedings of the IEEE 41st Annual Computer Software and Applications Conference (COMPSAC), Torino, Italy, 4–8 July 2017. [Google Scholar]
- Philip, A.; Ibidun, O.; Nureni, A. Mitigation of Denial of Service Attacks in Fog-Based Wireless Sensor Networks Using Deep Neural Networks Techniques. Available online: https://ssrn.com/abstract=4372752 (accessed on 13 June 2023).
- Esmaeili, M.; Goki, S.H.; Masjidi, B.H.K.; Sameh, M.; Gharagozlou, H.; Mohammed, A.S. ML-DDoSnet: IoT Intrusion Detection Based on Denial-of-Service Attacks Using Machine Learning Methods and NSL-KDD. Wirel. Commun. Mob. Comput. 2022, 2022, 1–16. [Google Scholar] [CrossRef]
- Salmi, S.; Oughdir, L. Performance evaluation of deep learning techniques for DoS attacks detection in wireless sensor network. J. Big Data 2023, 10, 17. [Google Scholar] [CrossRef]
- Alam, M.R.; Chan, K.S. RTT-TC: A topological comparison based method to detect wormhole attacks in MANET. In Proceedings of the IEEE 12th International Conference on Communication Technology, Nanjing, China, 11–14 November 2010. [Google Scholar]
- Antonopoulos, A.; Verikoukis, C.; Skianis, C.; Akan, O.B. Energy efficient network coding-based MAC for cooperative ARQ wireless networks. Ad. Hoc. Netw. 2013, 11, 190–200. [Google Scholar] [CrossRef]
- Paul, B. Internet of Things (IoT), Three-Layer Architecture, Security Issues and Counter Measures. In ICT Analysis and Applications; Lecture Notes in Networks and Systems; Fong, S., Dey, N., Joshi, A., Eds.; Springer: Singapore, 2022; Volume 314. [Google Scholar] [CrossRef]
- Nagarajan, G.; Simpson, S.V.; Minu, R.I. Chapter Thirteen-Edge computing security: Layered classification of attacks and possible countermeasures. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2022; Volume 127, pp. 359–377. ISSN 0065-2458. ISBN 9780128245064. [Google Scholar] [CrossRef]
- Rehman, E.; Haseeb-Ud-Din, M.; Malik, A.J.; Khan, T.K.; Abbasi, A.A.; Kadry, S.; Khan, M.A.; Rho, S. Intrusion detection based on machine learning in the internet of things, attacks and counter measures. J. Supercomput. 2022, 78, 8890–8924. [Google Scholar] [CrossRef]
- Mouaatamid, O.E.; Lahmer, M.; Belkasmi, M. Internet of Things Security: Layered Classification of Attacks and Possible Countermeasures. Electron. J. Inf. Technol. 2016, 9, 24–37. Available online: http://www.webmail.revue-eti.net/index.php/eti/article/view/98 (accessed on 20 January 2021).
- Usman, M.; Raponi, S.; Qaraqe, M.; Oligeri, G. KaFHCa: Key-Establishment via Frequency Hopping Collisions. arXiv201009642 Cs. October 2020. Available online: http://arxiv.org/abs/2010.09642 (accessed on 20 January 2021).
- Furstenau, L.B.; Rodrigues, Y.P.R.; Sott, M.K.; Leivas, P.; Dohan, M.S.; López-Robles, J.R.; Cobo, M.J.; Bragazzi, N.L.; Choo, K.-K.R. Internet of things: Conceptual network structure, main challenges and future directions. Digit. Commun. Networks 2023, 9, 677–687. [Google Scholar] [CrossRef]
- Ashrif, F.F.; Sundarajan, E.A.; Ahmed, R.; Hasan, M.K. SLAE6: Secure and Lightweight Authenticated Encryption Scheme for 6LoWPAN Networks. In Proceedings of the 12th International Conference on Sensor Networks (SENSORNETS 2023), Online, 23–24 February 2023; pp. 67–78. [Google Scholar]
- Hennebert, C.; Santos, J.D. Security protocols and privacy issues into 6LoWPAN stack: A synthesis. IEEE Internet Things J. 2014, 1, 384–398. [Google Scholar] [CrossRef]
- Adnan, A.H.; Abdirazak, M.; Shamsuzzaman Sadi, A.B.M.; Anam, T.; Khan, S.Z.; Rahman, M.M.; Omar, M.M. A comparative study of WLAN security protocols: WPA, WPA2. In Proceedings of the 2015 International Conference on Advances in Electrical Engineering (ICAEE), Dhaka, Bangladesh, 17–19 December 2015; pp. 165–169. [Google Scholar]
- Venkat, Y.; Chand, K.P.; Preethiya, T. An intrusion detection system for the Internet of Things based on machine learning. In Proceedings of the 2023 International Conference on Recent Advances in Electrical, Electronics, Ubiquitous Communication, and Computational Intelligence (RAEEUCCI), Chennai, India, 19–21 April 2023; IEEE: New York, NY, USA, 2023. [Google Scholar]
- Syed Ali, M.; Hussain, S.Z. Survey on intrusion detection system in iot network. In Proceedings of the International Conference on Innovative Computing and Communications: Proceedings of ICICC 2022, Delhi, India, 19–20 February 2022; Springer Nature: Singapore, 2022; Volume 2. [Google Scholar]
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-Time intrusion detection in the internet of things. Ad. Hoc. Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Ahmed, A.S.A.M.S.; Hassan, R.; Othman, N.E. IPv6 neighbor discovery protocol specifications, threats and countermeasures: A survey. IEEE Access 2017, 5, 18187–18210. [Google Scholar] [CrossRef]
- Unsal, E.; Çebi, Y. Denial of Service Attacks in WSN. In Proceedings of the International Symposium on Computing in Science & Engineering, Izmir, Turkey, 4–6 September 2013. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication protocols for internet of things: A comprehensive survey. Secur. Commun. Netw. 2017, 2017, 1–41. [Google Scholar] [CrossRef]
- Huo, R.; Zeng, S.; Wang, Z.; Shang, J.; Chen, W.; Huang, T.; Wang, S.; Yu, F.R.; Liu, Y. A Comprehensive Survey on Blockchain in Industrial Internet of Things: Motivations, Research Progresses, and Future Challenges. IEEE Commun. Surv. Tutor. 2022, 24, 88–122. [Google Scholar] [CrossRef]
- Babiker Mohamed, M.; Matthew Alofe, O.; Ajmal Azad, M.; Singh Lallie, H.; Fatema, K.; Sharif, T. A comprehensive survey on secure software-defined network for the Internet of Things. Trans. Emerg. Telecommun. Technol. 2022, 33, e4391. [Google Scholar] [CrossRef]
- El-hajj, M.; Chamoun, M.; Fadlallah, A.; Serhrouchni, A. Analysis of authentication techniques in Internet of Things (IoT). In Proceedings of the 2017 1st Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 18–20 October 2017; pp. 1–3. [Google Scholar]
- Eddy, W.M. Defenses against TCP SYN flooding attacks. Internet Protoc. J. 2006, 9, 2–16. [Google Scholar]
- Toyeer-E-Ferdoush, R.H.; Hasan, M. A convenient way to mitigate DDoS TCP SYN flood attack. J. Discret. Math. Sci. Cryptogr. 2022, 25, 2069–2077. [Google Scholar] [CrossRef]
- Şahin, M.E.; Demirci, M. ConPoolUBF: Connection pooling and updatable Bloom filter based SYN flood defense in programmable data planes. Comput. Netw. 2023, 231, 109802. [Google Scholar] [CrossRef]
- Roldán-Gómez, J.; Carrillo-Mondéjar, J.; Gómez, J.M.C.; Martínez, J.L.M. Security Assessment of the MQTT-SN Protocol for the Internet of Things. In Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2022; Volume 2224. [Google Scholar]
- Zeghida, H.; Boulaiche, M.; Chikh, R. Securing MQTT protocol for IoT environment using IDS based on ensemble learning. Int. J. Inf. Secur. 2023, 22, 1075–1086. [Google Scholar] [CrossRef]
- Hameed, S.; Minhas, Q.A.; Ahmed, S.; Habib, S.; Hasan, M.K.; Islam, M.; Khan, S. An improved iBAT-COOP protocol for cooperative diversity in FANETs. Comput. Mater. Contin. 2021, 67, 2527–2546. [Google Scholar] [CrossRef]
- Varghese, S.A.; Ghadim, A.D.; Balador, A.; Alimadadi, Z.; Papadimitratos, P. Digital twin-based intrusion detection for industrial control systems. In Proceedings of the 2022 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Atlanta, GA, USA, 21–25 March 2022; IEEE: New York, NY, USA, 2022. [Google Scholar]
- Wolsing, K.; Wagner, E.; Saillard, A.; Henze, M. IPAL: Breaking up silos of protocol-dependent and domain-specific industrial intrusion detection systems. In Proceedings of the 25th International Symposium on Research in Attacks, Intrusions and Defenses, Limassol, Cyprus, 26–28 October 2022. [Google Scholar]
- Lin, H.; Xue, Q.; Feng, J.; Bai, D. Internet of things intrusion detection model and algorithm based on cloud computing and multi-feature extraction extreme learning machine. Digit. Commun. Netw. 2023, 9, 111–124. [Google Scholar] [CrossRef]
- Gyamfi, E.; Jurcut, A.D. Novel online network intrusion detection system for industrial iot based on oi-svdd and as-elm. IEEE Internet Things J. 2022, 10, 3827–3839. [Google Scholar] [CrossRef]
- Abbasi, M.; Plaza-Hernández, M.; Prieto, J.; Corchado, J.M. Security in the Internet of Things Application Layer: Requirements, Threats, and Solutions. IEEE Access 2022, 10, 97197–97216. [Google Scholar] [CrossRef]
- Talaei Khoei, T.; Kaabouch, N. A Comparative Analysis of Supervised and Unsupervised Models for Detecting Attacks on the Intrusion Detection Systems. Information 2023, 14, 103. [Google Scholar] [CrossRef]
- Agarwal, U.; Rishiwal, V.; Tanwar, S.; Chaudhary, R.; Sharma, G.; Bokoro, P.N.; Sharma, R. Blockchain technology for secure supply chain management: A comprehensive review. IEEE Access 2022, 10, 85493–85517. [Google Scholar] [CrossRef]
- Najafi, S.E.; Nozari, H.; Edalatpanah, S.A. Artificial Intelligence of Things (AIoT) and Industry 4.0–Based Supply Chain (FMCG Industry). In A Roadmap for Enabling Industry 4.0 by Artificial Intelligence; Wiley: New York, NY, USA, 2022; pp. 31–41. [Google Scholar]
- Wei, Y. A Machine Learning Algorithm for Supplier Credit Risk Assessment Based on Supply Chain Management. Int. Trans. Electr. Energy Syst. 2022, 2022, 4766597. [Google Scholar] [CrossRef]
- Balta, S.; Zavrak, S.; Eken, S. Real-time monitoring and scalable messaging of scada networks data: A case study on cyber-physical attack detection in water distribution system. In International Congress of Electrical and Computer Engineering; Springer International Publishing: Cham, Switzerland, 2022. [Google Scholar]
- Karasmanoglou, A.; Antonakakis, M.; Zervakis, M. ECG-Based Semi-Supervised Anomaly Detection for Early Detection and Monitoring of Epileptic Seizures. Int. J. Environ. Res. Public Health 2023, 20, 5000. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L.; Pimenidis, E.; Kikiras, P. Variational restricted Boltzmann machines to automated anomaly detection. Neural Comput. Appl. 2022, 34, 15207–15220. [Google Scholar] [CrossRef]
- Habib, S.; Hussain, A.; Albattah, W.; Islam, M.; Khan, S.; Khan, R.U.; Khan, K. Abnormal Activity Recognition from Surveillance Videos Using Convolutional Neural Network. Sensors 2021, 21, 8291. [Google Scholar] [CrossRef]
- Yang, Z.; Wang, T.; Yuen, K.-V. Construction site information decentralized management using blockchain and smart contracts. Comput.-Aided Civ. Infrastruct. Eng. 2022, 37, 1450–1467. [Google Scholar]
- Rrushi, J.L. Physics-Driven Page Fault Handling for Customized Deception against CPS Malware. ACM Trans. Embed. Comput. Syst. 2022, 21, 1–36. [Google Scholar] [CrossRef]
- Alanazi, R.; Aljuhani, A. Anomaly Detection for Industrial Internet of Things Cyberattacks. Comput. Syst. Sci. Eng. 2022, 44, 2361–2378. [Google Scholar]
- Chander, N.; Kumar, M.U. Metaheuristic feature selection with deep learning enabled cascaded recurrent neural network for anomaly detection in Industrial Internet of Things environment. Clust. Comput. 2022, 26, 1801–1819. [Google Scholar] [CrossRef]
- Sgueglia, A.; Di Sorbo, A.; Visaggio, C.A.; Canfora, G. A systematic literature review of IoT time series anomaly detection solutions. Futur. Gener. Comput. Syst. 2022, 134, 170–186. [Google Scholar] [CrossRef]
- Al Samara, M.; Bennis, I.; Abouaissa, A.; Lorenz, P. A survey of outlier detection techniques in IoT: Review and classification. J. Sens. Actuator Netw. 2022, 11, 4. [Google Scholar]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 2022, 11, 198. [Google Scholar]
- Wang, Z.; Zhang, Y.; Chen, Y.; Liu, H.; Wang, B.; Wang, C. A Survey on Programmable Logic Controller Vulnerabilities, Attacks, Detections, and Forensics. Processes 2023, 11, 918. [Google Scholar]
- Marković-Petrović, J.D. A Model for Dynamic Cyber Security Risk Assessment in the Industrial IOT Environment. In Proceedings of the Sinteza 2022-International Scientific Conference on Information Technology and Data Related Research, Belgrade, Serbia, 16 April 2022. [Google Scholar]
- Xin, G.; Zhang, G.; Zhang, Y. A Comprehensive Review of Blockchain Technology-Enabled Smart Manufacturing: A Framework, Challenges and Future Research Directions. Sensors 2022, 23, 155. [Google Scholar]
- Gu, J.; Cao, X.Y.; Fu, Y.; He, Z.W.; Yin, Z.J.; Yin, H.L.; Chen, Z.B. Experimental measurement-device-independent type quantum key distribution with flawed and correlated sources. Sci. Bull. 2022, 67, 2167–2175. [Google Scholar]
- Yin, H.-L.; Fu, Y.; Li, C.-L.; Weng, C.-X.; Li, B.-H.; Gu, J.; Lu, Y.-S.; Huang, S.; Chen, Z.-B. Experimental quantum secure network with digital signatures and encryption. Natl. Sci. Rev. 2023, 10, nwac228. [Google Scholar] [CrossRef]
- Wan, X.; Ru, B.; Esperança, P.M.; Li, Z. On redundancy and diversity in cell-based neural architecture search. arXiv 2022, arXiv:2203.08887. [Google Scholar]
- Sangkhro, R.; Agrawal, A.K. Cybersecurity in Industrial Control Systems: A Review of the Current Trends and Challenges. In Proceedings of the 2023 10th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 15–17 March 2023; IEEE: New York, NY, USA, 2023. [Google Scholar]
- Bansal, S.R.; Wadhawan, S.; Goel, R. mrmr-pso: A hybrid feature selection technique with a multiobjective approach for sign language recognition. Arab. J. Sci. Eng. 2022, 47, 10365–10380. [Google Scholar]
- Shah, S.; Munir, A.; Waheed, A.; Alabrah, A.; Mukred, M.; Amin, F.; Salam, A. Enhancing Security and Efficiency in Underwater Wireless Sensor Networks: A Lightweight Key Management Framework. Symmetry 2023, 15, 1484. [Google Scholar]
- Salam, A.; Ullah, F.; Amin, F.; Abrar, M. Deep Learning Techniques for Web-Based Attack Detection in Industry 5.0: A Novel Approach. Technologies 2023, 11, 107. [Google Scholar]
- Islam, M.; Dukyil, A.S.; Alyahya, S.; Habib, S. An IoT Enable Anomaly Detection System for Smart City Surveillance. Sensors 2023, 23, 2358. [Google Scholar] [CrossRef]
- Habib, S.; Alyahya, S.; Islam, M.; Alnajim, A.M.; Alabdulatif, A.; Alabdulatif, A. Design and Implementation: An IoT-Framework-Based Automated Wastewater Irrigation System. Electronics 2023, 12, 28. [Google Scholar] [CrossRef]
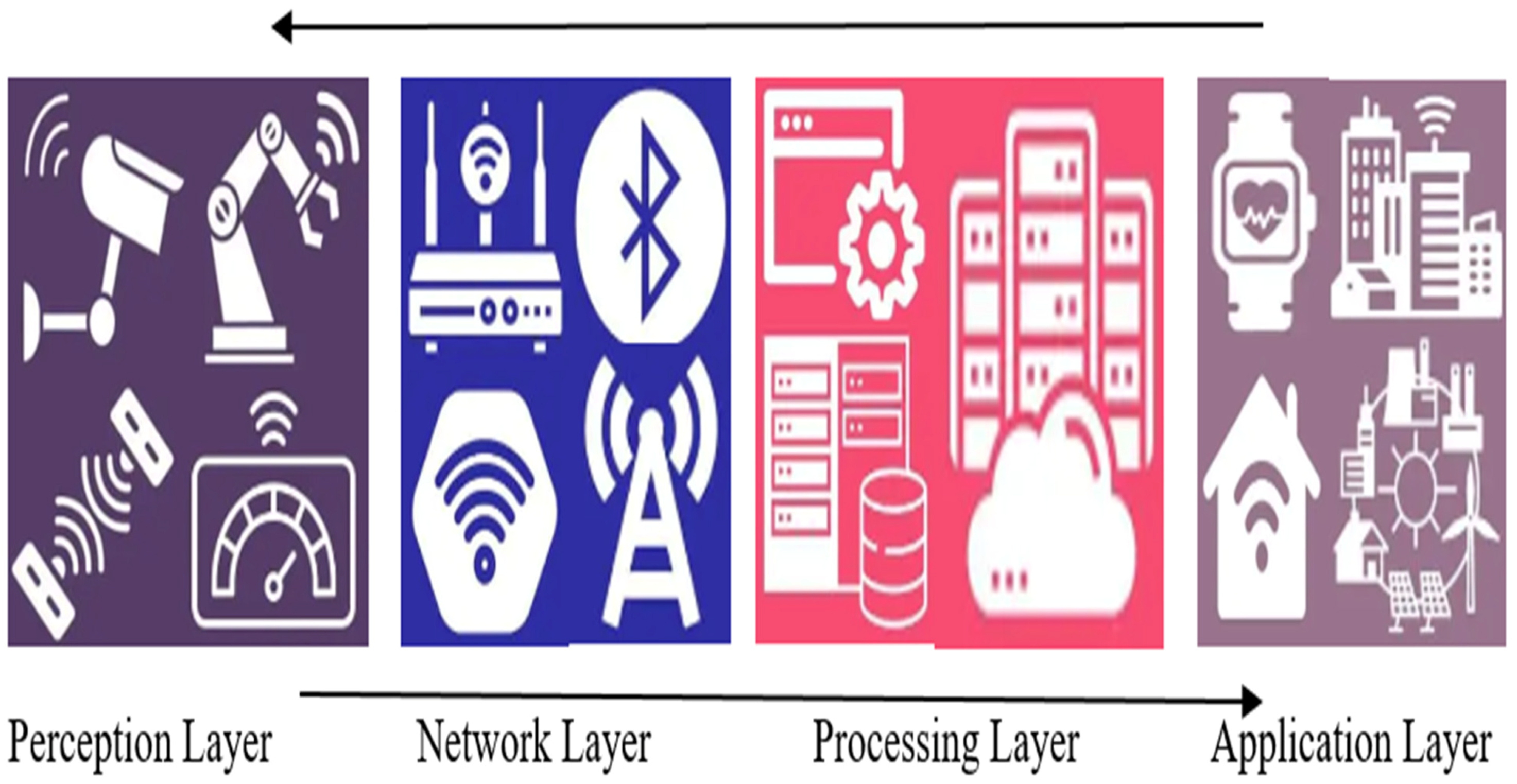
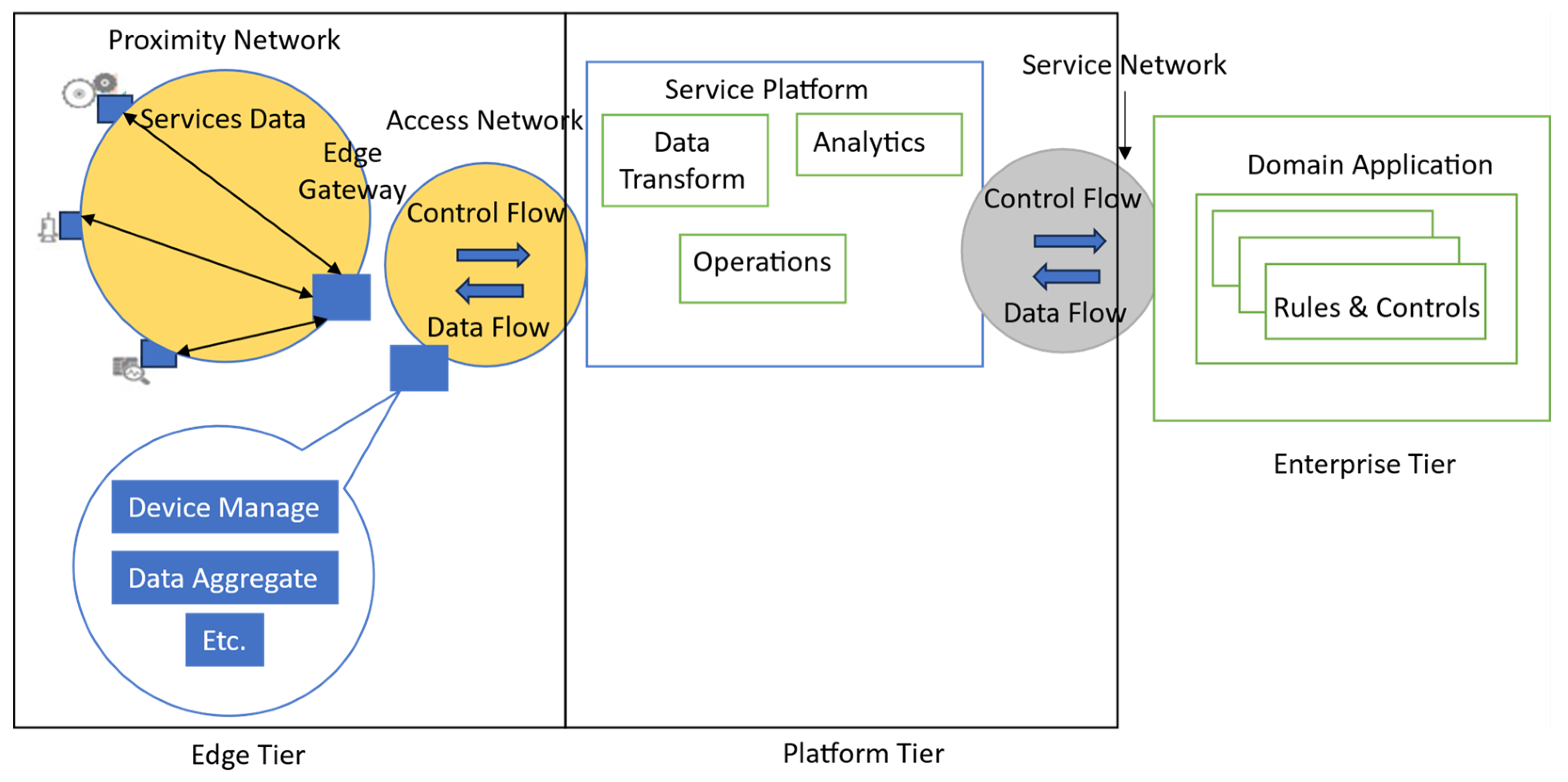


| Layer | Components | Possible Attacks | |
|---|---|---|---|
| Operational Technology | 1 | Sensors, actuators, transmitters, and motors embedded in devices | Eavesdropping, brute-force search assaults, crafted packets or input, reverse engineering, and even malware [12] |
| 2 | Systems for distributed control, PLCs, and gateways | Attacks on replays, MitM threats, sniffing, assaults on wireless devices, guessing passwords with brute force [13] | |
| 3 | Stations for the control room, operator, HMI, and SCADA systems | Malware, data snooping, IP spoofing, and data manipulation [14] | |
| Abandoned Region | |||
| Information Technology | 4 | Office applications, data centers, an intranet, emails, and internet services | Web application assaults, hacking assaults. Phishing, SQL injections, malware, DNS poisoning, remote code execution, along with other threats [15] |
| 5 | Cloud services, applications for business, analysis of information, the web, and cellphones | Threats such as denial-of-service, man-in-the-middle (MitM), back channel, internet spyware injection, identification, and intermediate gadget [16] | |
| IoT Protocol Stack | TCP/IP Protocol Stack | |
|---|---|---|
| Application Layer | IETF COAP | NTP, HTTP, DNS, SSH, FTP, SMTP, etc. |
| Transport Layer | UDP | TCP, UDP |
| Network Layer | IPV6, IETF RPL | IPv6, IPv4 |
| Adaption Layer | IETF 6LoWPAN | Not applicable |
| MAC Layer | IEEE 802.15.4 MAC | Availability of the network |
| Physical Layer | IEEE 802.15.4 PHY |
| Layers | Protocols | Threats | Countermeasures |
|---|---|---|---|
| Physical layer and data link layer | IEEE 802.15.4 BLE WiFi LTE | Buzzing DoS assaults | Packet rerouting to alternative routes [68,69,75,76] |
| Conflict, fatigue, and harshness assaults | FHSS techniques [78,79,80,81,82] | ||
| Attempted information transfer | Information encrypting methods [83,84,85,86] | ||
| Network layer | IP v4/IPv6 RPL 6LoWPAN | DoS assaults and routing | IDS and intrusion filtering techniques [87,88,89] |
| Data transit attacks | Protocols for condensed logistics, like DTL [84,89] | ||
| Threats to neighbor discovery protocol (IPv4/IPv6) | IPsec and SEND protocol usage [90] | ||
| Transport layer | Desynchronization | delivering synchronization-related command flags to destinations | Content authentication [92,93,94] |
| SYN-flooding | During the SYN handshaking stage, the network floods | The networking filter is applied through transport layer enhancements. [95,96,97] | |
| MQTT | Affordable information transit assaults key administration | MQTT security [98], ABE method [99,100,101] |
| Protocol | Threats | Solutions |
|---|---|---|
| MQTT | Authentication issues Authorization issues Message delivery failures Message integrity | Client or device authentication Authorization client’s access to server Message privacy-preserving mechanisms Message integrity-checking mechanisms |
| CoAP | IP spoofing Coaching and proxying vulnerabilities Block attack Parsing attacks | Adopting DTLS security modes Access control mechanisms Secure communication Confirmable message |
| XMPP | Unauthorized access Stanza modification Stanza deletion/replacing | Protocol improvement SASL authentication |
| mDNS | DoS attacks Poisoning attacks Remote attacks | Limitation on mDNS services Closing port |
| SSDP | Reflection/amplification attacks Passive attacks Eavesdropping attacks Poisoning attacks | Limitation on SSDP services Message monitoring and blocking Encryption techniques |
| Levels | Working Parts |
|---|---|
| Device level |
|
| Network level |
|
| Organization or policy level |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alnajim, A.M.; Habib, S.; Islam, M.; Thwin, S.M.; Alotaibi, F. A Comprehensive Survey of Cybersecurity Threats, Attacks, and Effective Countermeasures in Industrial Internet of Things. Technologies 2023, 11, 161. https://doi.org/10.3390/technologies11060161
Alnajim AM, Habib S, Islam M, Thwin SM, Alotaibi F. A Comprehensive Survey of Cybersecurity Threats, Attacks, and Effective Countermeasures in Industrial Internet of Things. Technologies. 2023; 11(6):161. https://doi.org/10.3390/technologies11060161
Chicago/Turabian StyleAlnajim, Abdullah M., Shabana Habib, Muhammad Islam, Su Myat Thwin, and Faisal Alotaibi. 2023. "A Comprehensive Survey of Cybersecurity Threats, Attacks, and Effective Countermeasures in Industrial Internet of Things" Technologies 11, no. 6: 161. https://doi.org/10.3390/technologies11060161







