Wireless Battery Management Systems: Innovations, Challenges, and Future Perspectives
Abstract
1. Introduction
2. wBMS Communication Technologies
2.1. Short-Range Wireless Communication Technologies
2.1.1. Bluetooth Low Energy (BLE)
- The physical layer (PHY) operates at low power and transmits data over 40 channels, each 2 MHz wide, within the 2.4 GHz unlicensed ISM (industrial, scientific, and medical) frequency band. To enhance transmission reliability in this crowded frequency range, BLE employs Frequency-Hopping Spread Spectrum (FHSS), which improves resistance to interference and multipath fading by rapidly switching the transmission frequency among the available channels. Furthermore, BLE uses Gaussian frequency-shift keying (GFSK) for modulation, which optimizes the trade-off between spectral efficiency and power consumption. These features collectively contribute to BLE’s robust performance in environments with high electromagnetic interference.
- The link layer (LL) directly interfaces with the PHY layer and manages activities including advertising, scanning, connection creation, and maintenance.
- The Logic Link Control and Adaptation Protocol (L2CAP) acts as the initial interface linking the upper layer protocols with the controller. It handles channel multiplexing, which ensures packets from the LL are directed to the appropriate upper-layer protocol during channel setup and helps differentiate among various upper-layer entities using the same protocol. From Bluetooth Core Specifications Version 5.2, L2CAP has taken on additional responsibilities like controlling the size of the Protocol Data Unit (PDU) to improve data interleaving and reduce latency. L2CAP also supports controllers with limited transmission capabilities by managing the fragmentation and reassembly of L2CAP PDUs. Furthermore, it oversees error control and meets Quality of Service (QoS) requirements.
- The Security Manager Protocol (SMP) establishes a framework that facilitates the generation and distribution of security keys among devices. It also specifies security requirements and capabilities using distinct PDU fields.
- The Attribute Protocol (ATT), used by the Generic ATT Profile (GATT) as a transport mechanism and data organizer, stores services, characteristics, and related data using a lookup table with 16-bit IDs for each entry.
- The Generic Access Profile (GAP) oversees the methods and procedures for device access, including tasks such as device discovery, establishing and terminating connections, initiating security measures, and configuring devices.
- The Generic Attribute Profile (GATT) manages data exchange over established connections by utilizing the Attribute Protocol (ATT). It comprises services, characteristics, and descriptors that are systematically arranged in the attribute table.
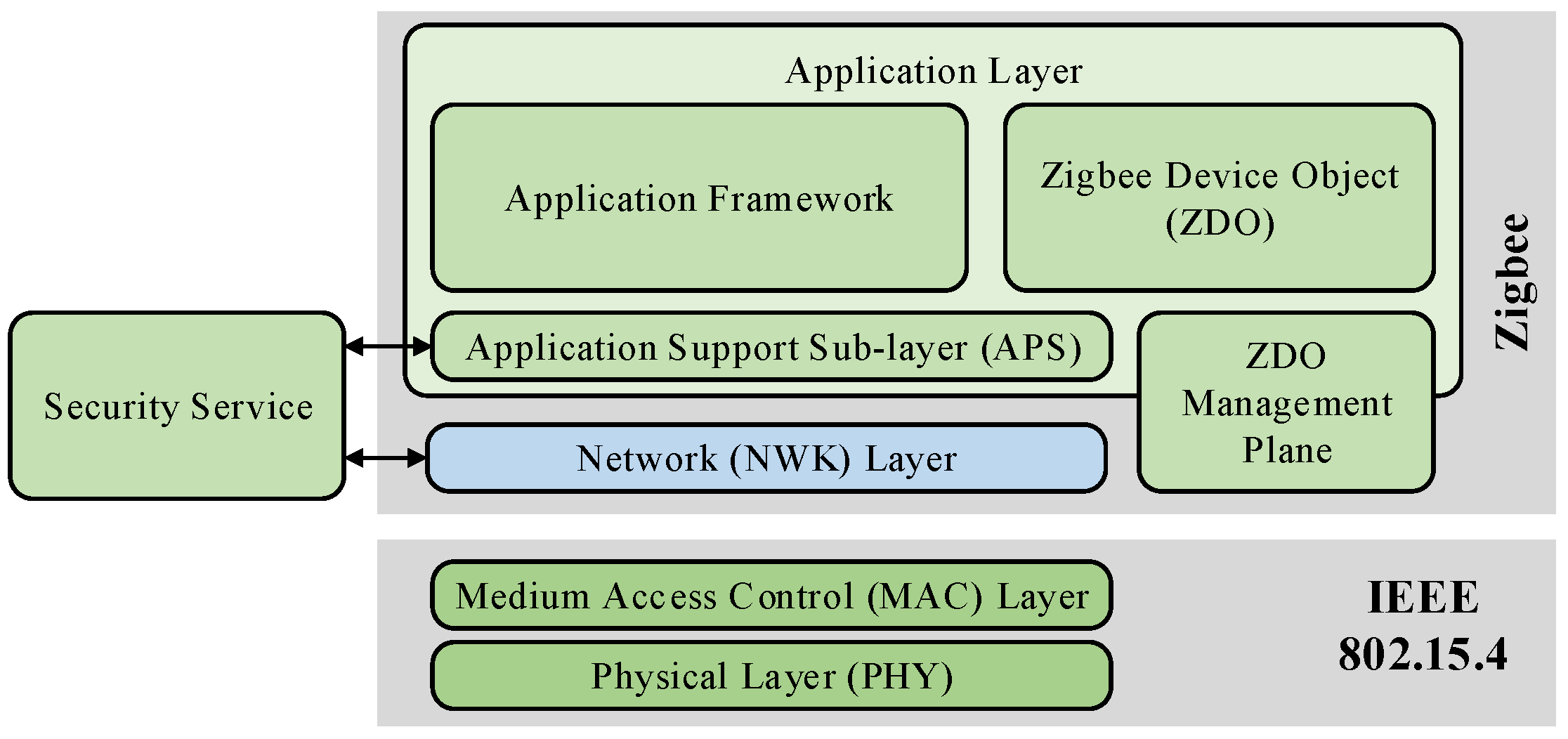
2.1.2. Zigbee
- Physical Layer (PHY): This layer operates on the 2.4 GHz frequency band globally, along with additional bands like 868 MHz in Europe and 915 MHz in North America. It uses direct sequence spread spectrum (DSSS) for modulation, which helps reduce interference and improve signal integrity across multiple channels in noisy environments.
- Media Access Control (MAC) Layer: The MAC layer ensures secure and organized communication across the physical radio, managing spectrum access, collision avoidance, and error detection and retransmission. The PHY layer and the MAC sub-layer are specified by the IEEE 802.15.4 standard as the foundational layers.
- Network (NWK) Layer: This layer is fundamental to Zigbee’s effectiveness in creating large-scale mesh networks. It manages routing, maintaining, initiating the network, and ensuring data reaches its destination across multiple nodes. The network layer in Zigbee is highly optimized for low-power operation and is capable of self-healing and self-organizing, which enhances network reliability and stability.
- Application Layer: This layer is composed of three sub-layers—the Application Support Sub-layer (APS), the Zigbee Device Objects (ZDOs), and the application framework itself. The APS provides the interface between the network and application layers, handling data transmission tasks and managing binding tables that link devices together. The ZDO handles device management and security, covering aspects like device roles, addressing, and the discovery of other devices within the network. Finally, the application framework hosts user applications, providing standard profiles for specific device controls.
2.1.3. Near-Field Communication (NFC)
- Reader/Writer Mode: In this mode, self-powered active devices initiate communication by energizing passive devices through energy harvesting. They detect, initiate, and maintain power supply to passive devices during communication. Once connected, passive devices respond to active devices using “load modulation”, a technique that modulates the existing electromagnetic field to transmit data. This mode is critical for applications like reading information from NFC tags embedded in products.
- Peer-to-Peer Mode: In this mode, both participating devices are active, each equipped with its power source. The initiator establishes the electromagnetic field and begins communication, while the second device is the target. Communication between the two devices uses Amplitude Shift Keying (ASK) modulation exclusively, facilitating a robust data exchange for transferring information like contacts, photos, or other media among smartphones or between a smartphone and another NFC-enabled device.
- Card Emulation Mode: Combining the principles of the previous modes, card emulation enables a passive device like a smartphone to function as a traditional NFC card. This is particularly useful in transactional applications where the smartphone emulates an NFC payment card or transit pass. In this mode, the passive device initiates communication without power, enabling interactions with powered readers like payment terminals or access control systems.
- Physical Layer (PHY) and Radio Frequency Interface (RFI): NFC operates within the 13.56 MHz frequency band. The PHY layer manages signal modulation and demodulation using Amplitude Shift Keying (ASK) to encode data. The RFI oversees the activation and deactivation of the radio frequency field, controlling the timing and ensuring accurate signal reception and processing between the initiator and target.
- Data Link Layer (DLL): Responsible for error detection and correction, the DLL ensures data transmission integrity, using protocols to detect and retransmit data if errors occur. This layer is crucial in environments prone to data corruption from interference.
- Protocol Layer: This layer manages the communication protocols that define how devices interact with each other in various NFC modes. It includes the NFC Data Exchange Format (NDEF), which standardizes the structure of messages exchanged among devices. The protocol layer ensures that NFC devices can interact seamlessly, regardless of the manufacturer.
- Transaction Layer: Critical for applications requiring secure communication, like payment systems, this layer manages secure transaction setup and execution, utilizing encryption and secure channel protocols to safeguard data and ensure communication privacy and integrity.
- Application Layer: The application layer includes the software applications that utilize NFC technology. These applications range from simple data exchange applications to complex payment and ticketing systems. The application layer interfaces with the underlying NFC technology to deliver a seamless user experience for various use cases.
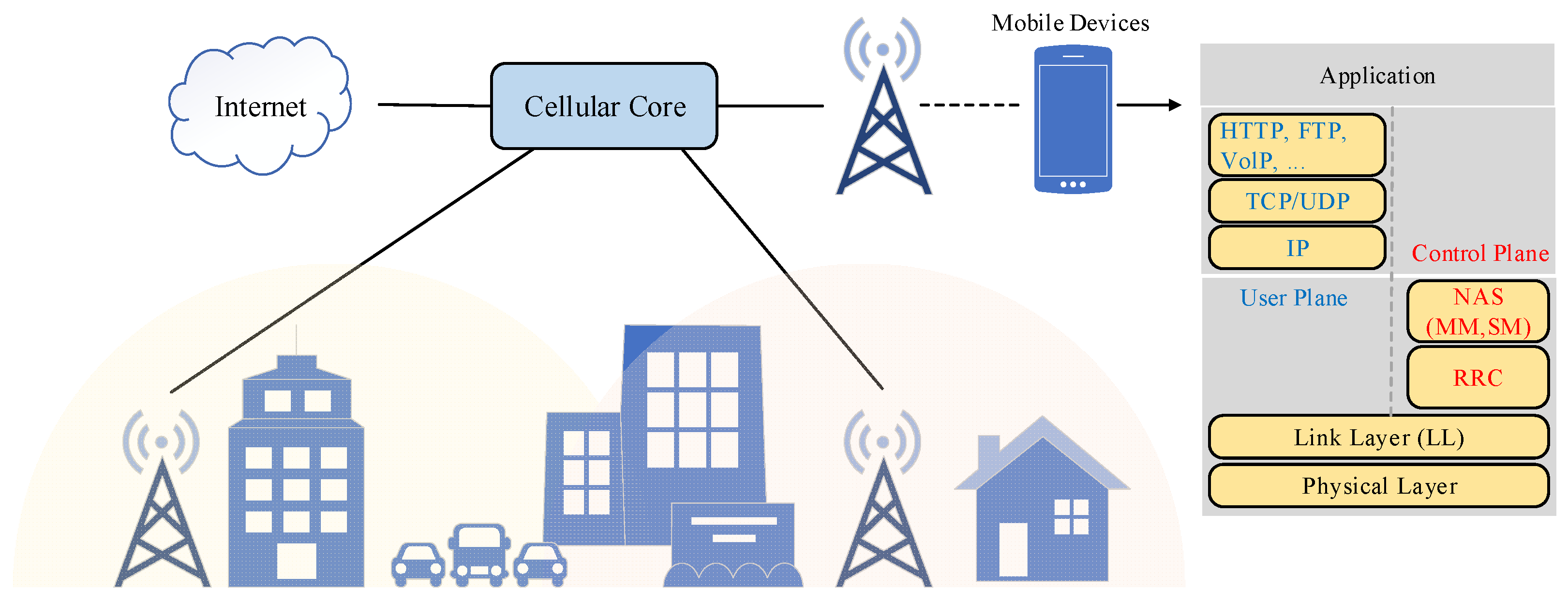
2.2. WLAN Technologies
- Physical Layer (PHY): Depending on the specific Wi-Fi version (e.g., 802.11a, 802.11b, 802.11g, 802.11n, 802.11ac), the physical layer operates at different frequencies, primarily 2.4 GHz or 5 GHz. The choice of frequency band affects the balance between range and data rate. The PHY layer uses various modulation techniques, such as Quadrature Amplitude Modulation (QAM) or Orthogonal Frequency-Division Multiplexing (OFDM), to optimize data transfer rates and bandwidth efficiency.
- Data Link Layer: This layer includes the Media Access Control (MAC) and Logical Link Control (LLC). The MAC Layer manages access to the radio frequency channel, frame formatting, data encryption, and addressing using protocols like WPA and WPA2. It is crucial for securing the network and maintaining Quality of Service (QoS). The LLC Layer provides interface and flow control between the MAC sub-layer and the network layer.
- Network Layer: Wi-Fi does not define network layer functionalities, but it supports IP-based protocols such as IPv6, which enhance routing capabilities across complex networks with minimal power usage.
- Transport Layer: The transport layer offers end-to-end data transfer through lightweight protocols such as UDP, which is preferred for its simplicity and low overhead.
- Application Layer: The application layer includes user-end software that interfaces with Wi-Fi hardware, providing functionalities like network discovery, connection management, and user authentication. This layer enables the applications to utilize the network efficiently and securely.
2.3. MAN and WAN Technologies
2.4. Other Technologies
2.5. Summary of Wireless Communication Technologies
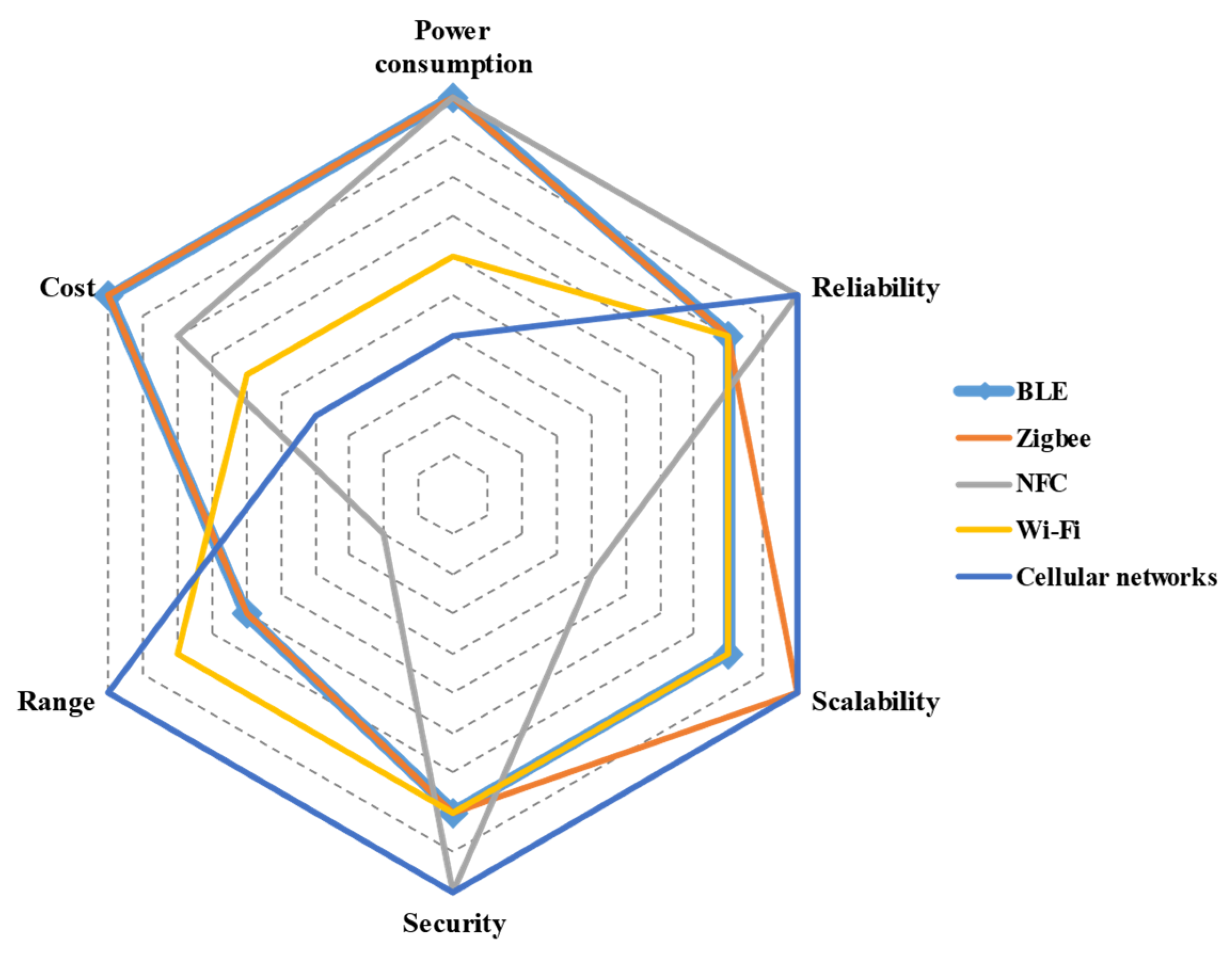
2.5.1. Efficiency and Power Consumption
2.5.2. Reliability
2.5.3. Scalability
2.5.4. Security
2.5.5. Environmental Conditions and System Architecture
2.6. Comparison to Wired BMSs
3. State-of-Art Commercial wBMS Solutions
3.1. Commercial wBMS Product Comparison
- Configuration of the cell measurement unit (CMU).
- Communication protocol.
- Network topology.
- Power consumption.
3.2. Real-World Examples and Case Studies
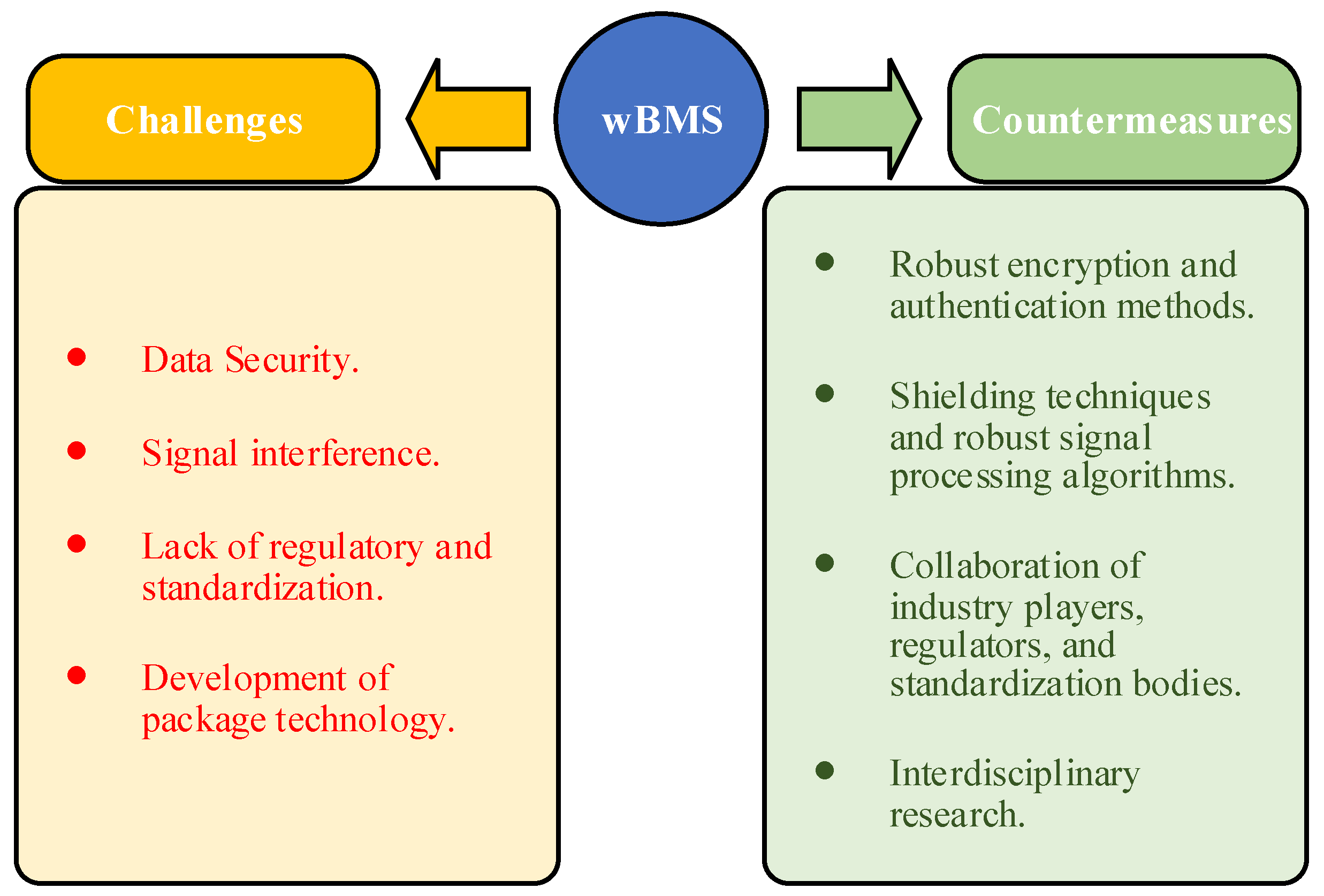
4. Challenges and Potential Countermeasures
4.1. Data Security
4.2. Signal Interference
4.3. Regulatory and Standardization Issues
4.4. Development of Package Technology
5. Conclusions
5.1. Key Findings
- Technological evolution: wBMSs have evolved with the development of advanced wireless communication technologies like BLE, Zigbee, NFC, Wi-Fi, and cellular networks. Each technology offers unique benefits and challenges in terms of efficiency, reliability, scalability, and security.
- Academic and commercial developments: Both academic research and commercial solutions have demonstrated promising results. Academic efforts have focused on enhancing the efficiency and reliability of wBMSs, while commercial products are beginning to achieve practical implementation, as evidenced by General Motors’ Ultium platform.
- Comparison with wired BMSs: Compared with traditional wired BMSs, wBMSs offer several advantages, including reduced weight, enhanced flexibility, and easier maintenance. However, challenges such as signal interference, data security, and regulatory issues must be addressed.
5.2. Future Directions
- Data security: Robust encryption and authentication methods are essential to protect against cybersecurity threats. Blockchain technology holds the potential to enhance the security of wBMSs.
- Signal interference: Advanced signal processing algorithms and improved shielding techniques can mitigate the effects of signal interference, ensuring reliable communication.
- Standardization: Collaboration among industry players, regulators, and standardization bodies is crucial to establishing universal standards for wBMSs, ensuring interoperability and scalability.
5.3. Implications
Author Contributions
Funding
Conflicts of Interest
References
- Mishra, S.; Swain, S.C.; Samantaray, R.K. A Review on Battery Management System and Its Application in Electric Vehicle. In Proceedings of the 2021 International Conference on Advances in Computing and Communications (ICACC), Kakkanad, India, 21–23 October 2021; pp. 1–6. [Google Scholar]
- Darwish, M.; Ioannou, S.; Janbey, A.; Amreiz, H.; Marouchos, C.C. Review of Battery Management Systems. In Proceedings of the 2021 International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME), Piscataway, NJ, USA, 7 October 2021; pp. 1–6. [Google Scholar]
- Gabbar, H.A.; Othman, A.M.; Abdussami, M.R. Review of Battery Management Systems (BMS) Development and Industrial Standards. Technologies 2021, 9, 28. [Google Scholar] [CrossRef]
- Balasingam, B.; Ahmed, M.; Pattipati, K. Battery Management Systems—Challenges and Some Solutions. Energies 2020, 13, 2825. [Google Scholar] [CrossRef]
- Lelie, M.; Braun, T.; Knips, M.; Nordmann, H.; Ringbeck, F.; Zappen, H.; Sauer, D.U. Battery Management System Hardware Concepts: An Overview. Appl. Sci. 2018, 8, 534. [Google Scholar] [CrossRef]
- Yong, J.Y.; Ramachandaramurthy, V.K.; Tan, K.M.; Mithulananthan, N. A Review on the State-of-the-Art Technologies of Electric Vehicle, Its Impacts and Prospects. Renew. Sustain. Energy Rev. 2015, 49, 365–385. [Google Scholar] [CrossRef]
- amkumar, M.S.; Reddy, C.S.R.; Ramakrishnan, A.; Raja, K.; Pushpa, S.; Jose, S.; Jayakumar, M. Review on Li-Ion Battery with Battery Management System in Electrical Vehicle. Adv. Mater. Sci. Eng. 2022, 2022, 3379574. [Google Scholar] [CrossRef]
- annan, M.A.; Lipu, M.S.H.; Hussain, A.; Mohamed, A. A Review of Lithium-Ion Battery State of Charge Estimation and Management System in Electric Vehicle Applications: Challenges and Recommendations. Renew. Sustain. Energy Rev. 2017, 78, 834–854. [Google Scholar] [CrossRef]
- Kassim, M.R.M.; Jamil, W.A.W.; Sabri, R.M. State-of-Charge (SOC) and State-of-Health (SOH) Estimation Methods in Battery Management Systems for Electric Vehicles. In Proceedings of the 2021 IEEE International Conference on Computing (ICOCO), Virtual, 17 November 2021; pp. 91–96. [Google Scholar]
- Klee Barillas, J.; Li, J.; Günther, C.; Danzer, M.A. A Comparative Study and Validation of State Estimation Algorithms for Li-Ion Batteries in Battery Management Systems. Appl. Energy 2015, 155, 455–462. [Google Scholar] [CrossRef]
- Lee, Y.-L.; Lin, C.-H.; Farooqui, S.A.; Liu, H.-D.; Ahmad, J. Validation of a Balancing Model Based on Master-Slave Battery Management System Architecture. Electr. Power Syst. Res. 2023, 214, 108835. [Google Scholar] [CrossRef]
- Ren, H.; Zhao, Y.; Chen, S.; Wang, T. Design and Implementation of a Battery Management System with Active Charge Balance Based on the SOC and SOH Online Estimation. Energy 2019, 166, 908–917. [Google Scholar] [CrossRef]
- Shet, V.V.; Ponangi, B.R.; Jacob, K. Design of a Thermal Management System for a Battery Pack in an Electric Vehicle Using Dymola. Heat Transf. 2020, 49, 2686–2705. [Google Scholar] [CrossRef]
- Kim, E.; Shin, K.G.; Lee, J. Real-Time Battery Thermal Management for Electric Vehicles. In Proceedings of the 2014 ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Berlin, Germany, 14–17 April 2014; pp. 72–83. [Google Scholar]
- Tran, M.-K.; Fowler, M. A Review of Lithium-Ion Battery Fault Diagnostic Algorithms: Current Progress and Future Challenges. Algorithms 2020, 13, 62. [Google Scholar] [CrossRef]
- Ma, Z.; Luan, Y.; Zhang, F.; Xie, S.; Coskun, S. A Data-Driven Energy Management Strategy for Plug-in Hybrid Electric Buses Considering Vehicle Mass Uncertainty. J. Energy Storage 2024, 77, 109963. [Google Scholar] [CrossRef]
- Vatanparvar, K.; Faezi, S.; Burago, I.; Levorato, M.; Al Faruque, M.A. Extended Range Electric Vehicle With Driving Behavior Estimation in Energy Management. IEEE Trans. Smart Grid. 2019, 10, 2959–2968. [Google Scholar] [CrossRef]
- John, P.C.; Kumar, B.P.N. Functional Safety Design and ISO26262 Compliance for BMS in EV and HEV. In Intelligent Solutions for Smart Grids and Smart Cities; Siano, P., Williamson, S., Beevi, S., Eds.; Springer Nature: Singapore, 2023; pp. 329–339. [Google Scholar]
- Marcos, D.; Garmendia, M.; Crego, J.; Cortajarena, J.A. Functional Safety BMS Design Methodology for Automotive Lithium-Based Batteries. Energies 2021, 14, 6942. [Google Scholar] [CrossRef]
- Krishna, G.; Singh, R.; Gehlot, A.; Akram, S.V.; Priyadarshi, N.; Twala, B. Digital Technology Implementation in Battery-Management Systems for Sustainable Energy Storage: Review, Challenges, and Recommendations. Electronics 2022, 11, 2695. [Google Scholar] [CrossRef]
- Yang, S.; Liu, X.; Li, S.; Zhang, C. Key Technologies of BMS. In Advanced Battery Management System for Electric Vehicles; Yang, S., Liu, X., Li, S., Zhang, C., Eds.; Springer Nature: Singapore, 2023; pp. 33–51. ISBN 978-981-19349-0-2. [Google Scholar]
- Krishnamoorthy, R.; Bharatiraja, C.; Krishnan, K. Review of Communication Network Interfaces and Battery Management for PHEV-ECU Materials and Components. Mater. Today Proc. 2021, 45, 3444–3448. [Google Scholar] [CrossRef]
- Lee, M.; Lee, J.; Lee, I.; Lee, J.; Chon, A. Wireless Battery Management System. In Proceedings of the 2013 World Electric Vehicle Symposium and Exhibition (EVS27), Barcelona, Spain, 17–20 November 2013; pp. 1–5. [Google Scholar]
- Shell, C.; Henderson, J.; Verra, H.; Dyer, J. Implementation of a Wireless Battery Management System (WBMS). In Proceedings of the 2015 IEEE International Instrumentation and Measurement Technology Conference (I2MTC) Proceedings, Pisa, Italy, 11–14 May 2015; pp. 1954–1959. [Google Scholar]
- Battery Management System Trends, Issues and Solutions|Renesas. Available online: https://www.renesas.com/us/en/blogs/battery-management-system-trends-issues-and-solutions (accessed on 19 March 2024).
- Pannerselvam, S.; Narayanan, V.; Gireesh Kumar, T. Energy Efficient Machine Learning Based SMART-A-BLE Implemented Wireless Battery Management System for Both Hybrid Electric Vehicles and Battery Electric Vehicles. Procedia Comput. Sci. 2023, 218, 235–248. [Google Scholar] [CrossRef]
- Bansal, P.; Nagaraj, P.R. Wireless Battery Management System for Electric Vehicles. In Proceedings of the 2019 IEEE Transportation Electrification Conference (ITEC-India), Bengaluru, India, 17–19 December 2019; pp. 1–5. [Google Scholar]
- Vishnu, K.; Nema, R.K.; Ojha, A. Various Types of Wireless Battery Management System in Ev. In Proceedings of the 2020 IEEE International Students’ Conference on Electrical, Electronics and Computer Science (SCEECS), Bhopal, India, 19–20 February 2020; pp. 1–5. [Google Scholar]
- Samanta, A.; Williamson, S.S. A Survey of Wireless Battery Management System: Topology, Emerging Trends, and Challenges. Electronics 2021, 10, 2193. [Google Scholar] [CrossRef]
- Cristian, G.G.; Vicente, G.-D.; Pelayo, G.-B.; Cristina, B.; Cueva, L. Juan Manuel Protocols and Applications for the Industrial Internet of Things; IGI Global: Hershey, PA, USA, 2018; ISBN 978-1-5225-3806-6. [Google Scholar]
- Tosi, J.; Taffoni, F.; Santacatterina, M.; Sannino, R.; Formica, D. Performance Evaluation of Bluetooth Low Energy: A Systematic Review. Sensors 2017, 17, 2898. [Google Scholar] [CrossRef]
- Zhou, L.; Chen, X.; Li, Y.; Li, J. Bluetooth Low Energy 4.0-Based Communication Method for Implants. In Proceedings of the 2017 10th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI), Shanghai, China, 14 October 2017; IEEE: Shanghai, China, 2017; pp. 1–5. [Google Scholar]
- Lacava, A.; Zottola, V.; Bonaldo, A.; Cuomo, F.; Basagni, S. Securing Bluetooth Low Energy Networking: An Overview of Security Procedures and Threats. Comput. Netw. 2022, 211, 108953. [Google Scholar] [CrossRef]
- Rincon Vija, F.A.; Cregut, S.; Papadopoulos, G.Z.; Montavont, N. Enabling Robust Wireless Communication for BMS on Electric Vehicles. In Proceedings of the 2021 IEEE 46th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 4 October 2021; IEEE: Edmonton, AB, Canada, 2021; pp. 423–426. [Google Scholar]
- Rincon Vija, F.A.; Cregut, S.; Papadopoulos, G.Z.; Montavont, N. From Wired to Wireless BMS in Electric Vehicles. In Proceedings of the 2021 17th International Conference on Mobility, Sensing and Networking (MSN), Exeter, UK, 13–15 December 2021; IEEE: Exeter, UK, 2021; pp. 255–262. [Google Scholar]
- IEEE Std 802.15.4-2020 ; (Revision of IEEE Std 802.15.4-2015). IEEE Standard for Low-Rate Wireless Networks. IEEE: Piscataway, NJ, USA, 23 July 2020; pp. 1–800. [CrossRef]
- Ahamed, M.M.I.; Mateen, S.; Savadi, A.; Haroon, P.S.A.L.; Naushad, S. of the Wireless Charging and BMS for Optimizing Electric Vehicle Charging and Battery Management. In Proceedings of the 2023 International Conference on Distributed Computing and Electrical Circuits and Electronics (ICDCECE), Ballar, India, 29 April 2023; IEEE: Ballar, India, 2023; pp. 1–7. [Google Scholar]
- Spörk, M.; Boano, C.A.; Römer, K. Performance and Trade-Offs of the New PHY Modes of BLE 5. In Proceedings of the ACM MobiHoc Workshop on Pervasive Systems in the IoT Era, New York, NY, USA, 2 July 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 7–12. [Google Scholar]
- Huan, J.; Liu, X.; Li, H.; Wang, H.; Zhu, X. A Monitoring and Control System for Aquaculture via Wireless Network and Android Platform. Sens. Transducers 2014, 169, 250–256. [Google Scholar]
- Li, P.; Li, J.; Nie, L.; Wang, B. Research and Application of ZigBee Protocol Stack. In Proceedings of the 2010 International Conference on Measuring Technology and Mechatronics Automation, Changsha, China, 13–14 March 2010; Volume 2, pp. 1031–1034. [Google Scholar]
- Vallo, N.J. Design and Analysis of A Wireless Battery Management System for an Advanced Electrical Storage System; University of Dayton: Dayton, OH, USA, 2016. [Google Scholar]
- Rahman, A.; Rahman, M.; Rashid, M. Wireless Battery Management System of Electric Transport. IOP Conf. Ser. Mater. Sci. Eng. 2017, 260, 012029. [Google Scholar] [CrossRef]
- Coskun, V.; Ozdenizci, B.; Ok, K. The Survey on Near Field Communication. Sensors 2015, 15, 13348–13405. [Google Scholar] [CrossRef] [PubMed]
- Basic, F. Enabling Secure and Wireless Battery Management Systems; Graz University of Technology: Graz, Austria, 2023. [Google Scholar]
- Basic, F.; Gaertner, M.; Steger, C. Secure and Trustworthy NFC-Based Sensor Readout for Battery Packs in Battery Management Systems. IEEE J. Radio Freq. Identif. 2022, 6, 637–648. [Google Scholar] [CrossRef]
- Basic, F.; Laube, C.R.; Stratznig, P.; Steger, C.; Kofler, R. Wireless BMS Architecture for Secure Readout in Vehicle and Second Life Applications. In Proceedings of the 2023 8th International Conference on Smart and Sustainable Technologies (SpliTech), Bol, Hotel Elaphusa, 20 June 2023; pp. 1–6. [Google Scholar]
- IEEE Std 802.11-2020; (Revision of IEEE Std 802.11-2016). IEEE Standard for Information Technology–Telecommunications and Information Exchange between Systems—Local and Metropolitan area Networks–Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: Piscataway, NJ, USA, 2021; pp. 1–4379. [CrossRef]
- Ferro, E.; Potorti, F. Bluetooth and Wi-Fi Wireless Protocols: A Survey and a Comparison. IEEE Wirel. Commun. 2005, 12, 12–26. [Google Scholar] [CrossRef]
- Froiz-Míguez, I.; Fernández-Caramés, T.; Fraga-Lamas, P.; Castedo, L. Design, Implementation and Practical Evaluation of an IoT Home Automation System for Fog Computing Applications Based on MQTT and ZigBee-WiFi Sensor Nodes. Sensors 2018, 18, 2660. [Google Scholar] [CrossRef] [PubMed]
- Ricco, M.; Meng, J.; Gherman, T.; Grandi, G.; Teodorescu, R. Smart Battery Pack for Electric Vehicles Based on Active Balancing with Wireless Communication Feedback. Energies 2019, 12, 3862. [Google Scholar] [CrossRef]
- Huang, X.; Acharya, A.B.; Meng, J.; Sui, X.; Stroe, D.-I.; Teodorescu, R. Wireless Smart Battery Management System for Electric Vehicles. In Proceedings of the 2020 IEEE Energy Conversion Congress and Exposition (ECCE), Virtual, 11 October 2020; pp. 5620–5625. [Google Scholar]
- Zebrowski, D. Development and Evaluation of Prototype Wireless Battery Management System; KTH, School of Electrical Engineering and Computer Science: Stockholm, Sweden, 2022. [Google Scholar]
- Li, Y.; Peng, C.; Yuan, Z.; Deng, H.; Li, J.; Wang, T. MobileInsight: Analyzing Cellular Network Information on Smartphones. GetMobile Mob. Comput. Commun. 2017, 21, 39–42. [Google Scholar] [CrossRef]
- Li, Y.; Peng, C.; Yuan, Z.; Li, J.; Deng, H.; Wang, T. Mobileinsight: Extracting and Analyzing Cellular Network Information on Smartphones. In Proceedings of the 22nd Annual International Conference on Mobile Computing and Networking, New York City, NY, USA, 3–7 October 2016; p. 215. [Google Scholar]
- Lohar, G.V.; Kumar, M.S. Design and Implementation of IoT Based Wireless Battery Management System for Electric Vehicles. Int. J. Intell. Syst. Appl. Eng. 2023, 11, 360–369. [Google Scholar]
- Faika, T.; Kim, T.; Khan, M. An Internet of Things (IoT)-Based Network for Dispersed and Decentralized Wireless Battery Management Systems. In Proceedings of the 2018 IEEE Transportation Electrification Conference and Expo (ITEC), Long Beach, CA, USA, 13–15 June 2018; pp. 1060–1064. [Google Scholar]
- Faika, T.; Kim, T.; Ochoa, J.; Khan, M.; Park, S.-W.; Leung, C.S. A Blockchain-Based Internet of Things (IoT) Network for Security-Enhanced Wireless Battery Management Systems. In Proceedings of the 2019 IEEE Industry Applications Society Annual Meeting, Baltimore, MD, USA, 29 September 2019; pp. 1–6. [Google Scholar]
- Liu, J. Wireless BMS vs. Wired BMS: Who Is the Key Battery Technology? MokoEnergy: Shenzhen, China, 2023. [Google Scholar]
- Rahman, A.B.A.; Jain, R. Comparison of Internet of Things (IoT) Data Link Protocols. Available online: https://www.cse.wustl.edu/~jain/cse570-15/ftp/iot_dlc/ (accessed on 7 April 2024).
- Ohwo, O.; Olujimi, A. A Comparative Review of Emerging Wireless Technology. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2020, 7, 163–175. [Google Scholar] [CrossRef]
- Sikimic, M.; Amovic, M.; Vujovic, V.; Suknovic, B.; Manjak, D. An Overview of Wireless Technologies for IoT Network. In Proceedings of the 2020 19th International Symposium Infoteh-Jahorina (Infoteh), East Sarajevo, Bosnia and Herzegovina, 18–20 March 2020; IEEE: East Sarajevo, Bosnia and Herzegovina, 2020; pp. 1–6. [Google Scholar]
- Alobaidy, H.A.H.; Mandeep, J.S.; Nordin, R.; Abdullah, N.F. A Review on ZigBee Based WSNs: Concepts, Infrastructure, Applications, and Challenges. Int. J. Electr. Electron. Eng. Telecommun. 2020, 9, 189–198. [Google Scholar] [CrossRef]
- Abuelsamid, S. GM to Use First Wireless Battery Management System in Ultium Battery Packs; Forbes: Jersey City, NJ, USA, 2020. [Google Scholar]
- Sripad, S.; Kulandaivel, S.; Pande, V.; Sekar, V.; Viswanathan, V. Vulnerabilities of Electric Vehicle Battery Packs to Cyberattacks. arXiv 2019, arXiv:arXiv:1711, 4822. [Google Scholar]
- Kumbhar, S.; Faika, T.; Makwana, D.; Kim, T.; Lee, Y. Cybersecurity for Battery Management Systems in Cyber-Physical Environments. In Proceedings of the 2018 IEEE Transportation Electrification Conference and Expo (ITEC), Long Beach, CA, USA, 13–15 June 2018; pp. 934–938. [Google Scholar]
- Naseri, F.; Kazemi, Z.; Larsen, P.G.; Arefi, M.M.; Schaltz, E. Cyber-Physical Cloud Battery Management Systems: Review of Security Aspects. Batteries 2023, 9, 382. [Google Scholar] [CrossRef]
- Sofi, M. Bluetooth Protocol in Internet of Things (IoT), Security Challenges and a Comparison with Wi-Fi Protocol: A Review. Int. J. Eng. Res. 2016, V5, 42–56. [Google Scholar] [CrossRef]
- Cäsar, M.; Pawelke, T.; Steffan, J.; Terhorst, G. A Survey on Bluetooth Low Energy Security and Privacy. Comput. Netw. 2022, 205, 108712. [Google Scholar] [CrossRef]
- Zohourian, A.; Dadkhah, S.; Neto, E.C.P.; Mahdikhani, H.; Danso, P.K.; Molyneaux, H.; Ghorbani, A.A. IoT Zigbee Device Security: A Comprehensive Review. Internet Things 2023, 22, 100791. [Google Scholar] [CrossRef]
- Bere, G.; Ochoa, J.J.; Kim, T.; Aenugu, I.R. Blockchain-Based Firmware Security Check and Recovery for Battery Management Systems. In Proceedings of the 2020 IEEE Transportation Electrification Conference & Expo (ITEC), Chicago, IL, USA, 23–26 June 2020; pp. 262–266. [Google Scholar]
- Je Lee, S.; Lee, Y.H.; Park, J.; Park, N. Analyzing RF Interference on Wireless BMS in High-Congestion Environments. In Proceedings of the 2023 IEEE Green Energy and Smart Systems Conference (IGESSC), Long Beach, CA, USA, 13–14 November 2023; pp. 1–6. [Google Scholar]
- Pampel, F.; Pischinger, S.; Teuber, M. A Systematic Comparison of the Packing Density of Battery Cell-to-Pack Concepts at Different Degrees of Implementation. Results Eng. 2022, 13, 100310. [Google Scholar] [CrossRef]
- Jin, C.; Sun, Y.; Yao, J.; Feng, X.; Lai, X.; Shen, K.; Wang, H.; Rui, X.; Xu, C.; Zheng, Y.; et al. No Thermal Runaway Propagation Optimization Design of Battery Arrangement for Cell-to-Chassis Technology. eTransportation 2022, 14, 100199. [Google Scholar] [CrossRef]
- Lian, Y.; Ling, H.; Jiang, L.; Yi, B.; Zhang, F.; Liu, J.; Song, G.; Tang, M. Development of Cell to Body Technology towards High Levels of Integration, High Strength and High Stiffness; SAE International: Warrendale, PA, USA, 2023. [Google Scholar]












| Technology | Frequency | Data Rate | Range | Latency | Power Consumption | Cost | Suitability |
|---|---|---|---|---|---|---|---|
| BLE | 2.4 GHz | 1 to 2 Mbps | Up to 100 m | Low | Low | Low |
|
| Zigbee | 2.4 GHz | Up to 250 kbps | Up to 100 m | Low | Low | Low |
|
| NFC | 13.56 MHz | Up to 424 kbps | Up to 10 cm | Low | Very Low | Low |
|
| Wi-Fi | 2.4 GHz, 5 GHz | 0.1 to 600 Mbps | Up to150 m | Low to Medium | Medium | Medium |
|
| Cellular networks | Cellular bands | Up to several hundred Mbps | Several kilometers | Medium | High | High |
|
| Technology | Wired BMS | Wireless BMS |
|---|---|---|
| Technical maturity | + Highly mature + Well-established standards | − Emerging − Lack of universal standards |
| Weight | − Increased due to cables and connectors | + Reduced due to eliminating physical connections |
| Complexity | + High due to extensive wiring | − Low with reduced wiring |
| Flexibility | − Limited | + High adaptability |
| Scalability | − Limited scalability | + Highly scalable |
| Reliability | − Prone to connection failures + High data reliability due to direct physical connection | + Improved reliability with fewer connection points − Data reliability challenges due to signal interference |
| Security | + Fully secure system communication | − Potentially vulnerable if not properly secured |
| Installation | − Complex and time-consuming | + Fast and simple installation |
| Maintenance | − Complex | + Easy |
| Power consumption | + Lower | − Higher for communication modules |
| Cost | + Potentially lower initial costs | − Higher initial investment |
| Repurpose and reuse | − Difficult | + Easy |
| Company | Analog Devices (ADI) | Texas Instruments (TI) | NXP Semiconductors | Dukosi |
|---|---|---|---|---|
| ICs | Master node: ADRF8850 Slave node: ADRF8800 | Master node: CC2662R Slave node: BQ79616+ CC2662R | Master node: 2 × KW38 + MPC5744P Slave node: MC33771 + KW37 | Master node: DK8202 Slave node: DK8102 |
| Protocol | SmartMesh | TI SimpleLink wBMS protocol | Optimized BLE 5.0 | Dukosi C-SynQ |
| Network topology | Mesh | Star | Star and Mesh | Star |
| CMU configuration | Standalone | Standalone | Standalone | 2-in-1 |
| Max nodes | - | Up to 100 | Up to 32 | Up to 220 |
| Operating frequency | 2.4 GHz | 2.4 GHz | 2.4 GHz | 2.4 GHz |
| Range | Far | Far | Far | Near |
| Data rate | 1 Mbps, 2 Mbps | Up to 1.2 Mbps | Up to 2 Mbps | 2 Mbps |
| Security features | Hardware accelerator supporting AES-128, AES-256, ECC-256, and SHA-256 True random number generator (TRNG) | Hardware acceleration supporting AES-128/256, ECC, RSA-2048, SHA-2. TRNG | AES-128 TRNG LE Secure Connections | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cao, Z.; Gao, W.; Fu, Y.; Mi, C. Wireless Battery Management Systems: Innovations, Challenges, and Future Perspectives. Energies 2024, 17, 3277. https://doi.org/10.3390/en17133277
Cao Z, Gao W, Fu Y, Mi C. Wireless Battery Management Systems: Innovations, Challenges, and Future Perspectives. Energies. 2024; 17(13):3277. https://doi.org/10.3390/en17133277
Chicago/Turabian StyleCao, Zhi, Wei Gao, Yuhong Fu, and Chris Mi. 2024. "Wireless Battery Management Systems: Innovations, Challenges, and Future Perspectives" Energies 17, no. 13: 3277. https://doi.org/10.3390/en17133277
APA StyleCao, Z., Gao, W., Fu, Y., & Mi, C. (2024). Wireless Battery Management Systems: Innovations, Challenges, and Future Perspectives. Energies, 17(13), 3277. https://doi.org/10.3390/en17133277









