Big Data Privacy in Smart Farming: A Review
Abstract
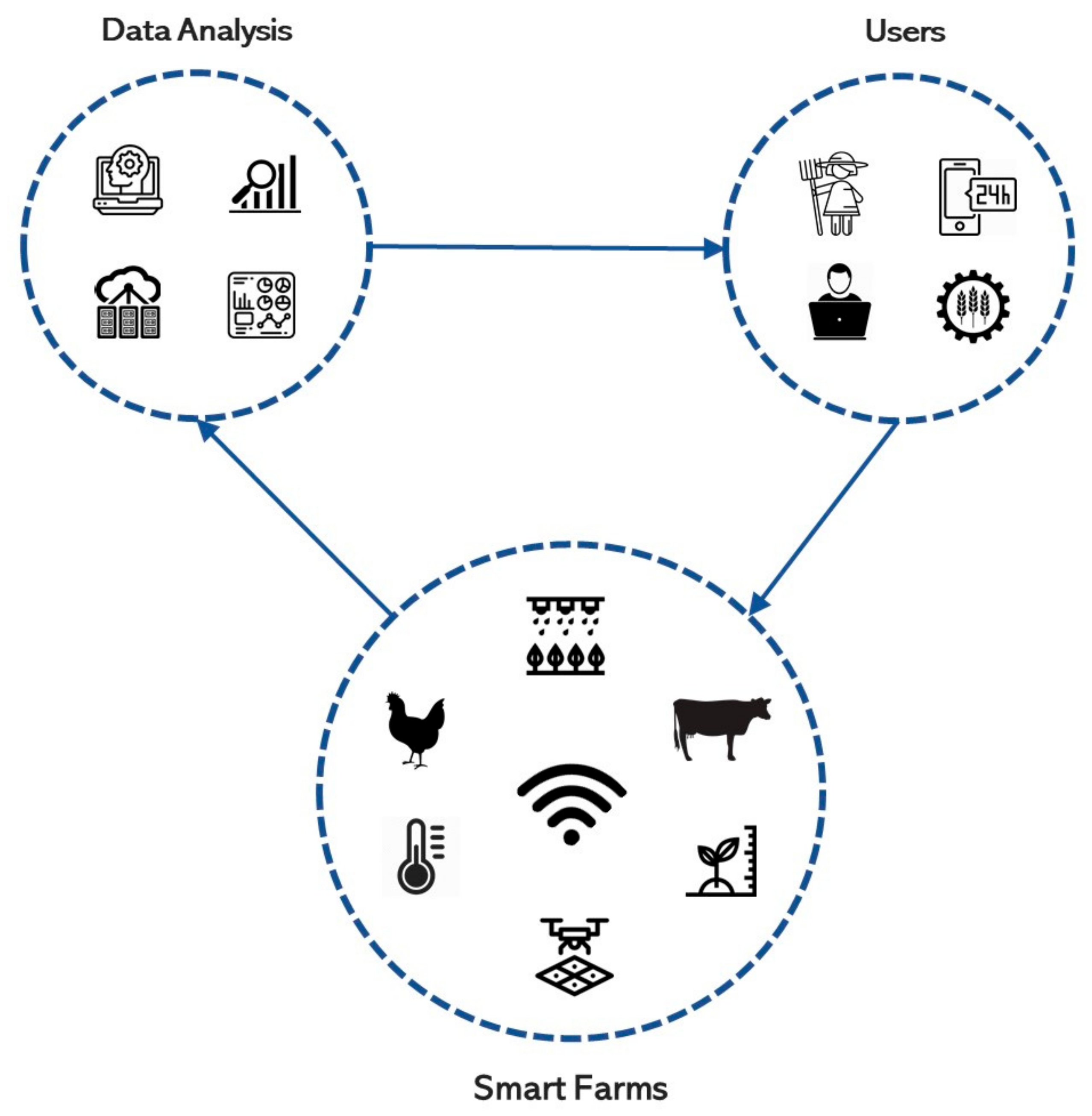
:1. Introduction
2. Big Data Lifecycle in Smart Farming
- -
- Data Collection: In this step, raw data are collected from devices such as sensors. These sensors can gather data from different aspects of farming, including weather, soil quality, animal movement, and harvest monitoring. Sensors deployed in smart farming applications are commonly limited in energy and computation resources; therefore, these devices are only capable of performing very simple data refinement and processing tasks [16].
- -
- Data Transfer: In this stage of the data lifecycle, the collected and aggregated data are transferred to the servers. These servers could be a local computer on the farm or a cloud service used by the technology provider [17]. To this end, a combination of different technologies is utilized including Wi-Fi, cellular, Local Area Network (LAN), and Bluetooth [18].
- -
- -
- Data Analytics: In this stage, data are analyzed and exploited to extract knowledge. This knowledge improves the farming decision-making processes through the use of analytics methods. Machine learning, statistical inference, and data mining are some of the common approaches for data analytics [21].
- -
- Data-Driven Services: These services can provide a wide range of recommendations to farmers regarding aspects such as selecting the most profitable product for the field, designing an optimized procedure from planting to harvesting, forecasting the affecting environmental events, and assessing the market for price negotiation. It is a major motivation for farmers to improve the profitability of their business using data-driven services [22]. Given that these services are usually publicly accessible to various clients, providing privacy protection in these services is a serious requirement [11].
- -
- Data Destruction: When the data are no longer useful or when it should be erased based on the preliminary agreements, data destruction needs to occur. For example, these preliminary agreements might set a retention time after which data should be deleted permanently, or at which time, the data owner may request a return of the data [23].
3. Privacy-Preserving Solutions in Big Data Lifecycle
3.1. Data Collection
3.2. Data Transfer
3.3. Data Storage
3.4. Data Analytics
3.5. Data-Driven Services
3.6. Data Destruction
4. Privacy-Preserving Technologies in Smart Farming
4.1. Machine Learning
4.2. Edge Computing
4.3. Blockchain
- (1)
- The permission mechanism which indicates the method that is utilized for authentication.
- (2)
- The consensus algorithm that is the mathematical algorithm to decide how to add a new block to the blockchain.
- (3)
- The smart contract/cryptocurrency which points out if the blockchain is used for smart contract deployment, financial payment, or both [98].
5. Legal Considerations
- 1.
- Ownership: Farmers own the information collected in the farming operations, but it is also their responsibility to negotiate and agree on data sharing with other parties. It is also the farmers’ responsibility to make sure only the data they own have been included in an agreement.
- 2.
- Collection, Access, and Control: Any access and use of farm data should be explicitly permitted by the farmer in the signed contracts or other types of legal agreements.
- 3.
- Notice: Not only should farmers be clearly informed that their data are being collected, but they must also be aware of how their data are going to be used and disclosed by the technology provider or any other third party. These notices should be provided in an easily located and readily accessible format.
- 4.
- Choice: Technology providers must provide choices for farmers to opt in, opt out, or cancel the services.
- 5.
- Portability: The farmers should be able to transfer their data to other systems, except for the data that have been aggregated or anonymized.
- 6.
- Disclosure, Use, and Sale Limitation: The technology provider should notify the farmer if they decide to sell or disclose the collected data, and they should also provide the chance for the farmer to cancel the service or remove the data. Working with a new third party should be based on the agreements consistent with the primary agreement between the parties.
- 7.
- Data Retention and Availability: Technology and service providers should provide mechanisms to erase or return farm data based on the farmer’s request, either immediately or after an agreed-upon timespan.
6. Discussion and Future Directions
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Coble, K.H.; Mishra, A.K.; Ferrell, S.; Griffin, T. Big data in agriculture: A challenge for the future. Appl. Econ. Perspect. Policy 2018, 40, 79–96. [Google Scholar] [CrossRef] [Green Version]
- Astill, J.; Dara, R.A.; Fraser, E.D.G.; Roberts, B.; Sharif, S. Smart poultry management: Smart sensors, big data, and the internet of things. Comput. Electron. Agric. 2020, 170, 105291. [Google Scholar] [CrossRef]
- Alzubi, J.; Nayyar, A.; Kumar, A. Machine Learning from Theory to Algorithms: An Overview. J. Phys. Conf. Ser. 2018, 1142, 012012. [Google Scholar] [CrossRef]
- Amiri-Zarandi, M.; Fard, M.H.; Yousefinaghani, S.; Kaviani, M.; Dara, R. A Platform Approach to Smart Farm Information Processing. Agriculture 2022, 12, 838. [Google Scholar] [CrossRef]
- Hubbard, R.; Haig, B.D.; Parsa, R.A. The Limited Role of Formal Statistical Inference in Scientific Inference. Am. Stat. 2019, 73, 91–98. [Google Scholar] [CrossRef] [Green Version]
- Jakku, E.; Taylor, B.; Fleming, A.; Mason, C.; Fielke, S.; Sounness, C.; Thorburn, P. ‘If they don’t tell us what they do with it, why would we trust them?’ Trust, transparency and benefit-sharing in Smart Farming. NJAS Wagen. J. Life Sci. 2019, 90, 100285. [Google Scholar] [CrossRef]
- Chen, D.; Zhao, H. Data security and privacy protection issues in cloud computing. In Proceedings of the 2012 International Conference on Computer Science and Electronics Engineering, Hangzhou, China, 23–25 March 2012; Volume 1, pp. 647–651. [Google Scholar]
- Shin, D.H. The effects of trust, security and privacy in social networking: A security-based approach to understand the pattern of adoption. Interact. Comput. 2010, 22, 428–438. [Google Scholar] [CrossRef]
- Shirey, R. Internet Security Glossary, Version 2 RFC 4949. Available online: https://www.rfc-editor.org/rfc/rfc4949 (accessed on 15 May 2022).
- Ferrag, M.A.; Shu, L.; Yang, X.; Derhab, A.; Maglaras, L. Security and Privacy for Green IoT-Based Agriculture: Review, Blockchain Solutions, and Challenges. IEEE Access 2020, 8, 32031–32053. [Google Scholar] [CrossRef]
- Gupta, M.; Abdelsalam, M.; Khorsandroo, S.; Mittal, S. Security and Privacy in Smart Farming: Challenges and Opportunities. IEEE Access 2020, 8, 34564–34584. [Google Scholar] [CrossRef]
- Barreto, L.; Amaral, A. Smart farming: Cyber security challenges. In Proceedings of the 2018 International Conference on Intelligent Systems (IS), Funchal, Portugal, 25–27 September 2018; pp. 870–876. [Google Scholar]
- Arass, M.E.; Souissi, N. Data Lifecycle: From Big Data to SmartData. In Proceedings of the 2018 IEEE 5th International Congress on Information Science and Technology (CiSt), Marrakech, Morocco, 22–24 October 2018; pp. 80–87. [Google Scholar]
- Xu, L.; Jiang, C.; Wang, J.; Yuan, J.; Ren, Y. Information security in big data: Privacy and data mining. IEEE Access 2014, 2, 1149–1176. [Google Scholar]
- Abouelmehdi, K.; Beni-Hessane, A.; Khaloufi, H. Big healthcare data: Preserving security and privacy. J. Big Data 2018, 5, 1. [Google Scholar] [CrossRef] [Green Version]
- Srbinovska, M.; Gavrovski, C.; Dimcev, V.; Krkoleva, A.; Borozan, V. Environmental parameters monitoring in precision agriculture using wireless sensor networks. J. Clean. Prod. 2015, 88, 297–307. [Google Scholar] [CrossRef]
- Anidu, A.; Dara, R. A review of data governance challenges in smart farming and potential solutions. In Proceedings of the 2021 IEEE International Symposium on Technology and Society (ISTAS), Waterloo, ON, Canada, 28–31 October 2021; pp. 1–8. [Google Scholar]
- Madushanki, R.; Wirasagoda, H.; Halgamuge, M. Adoption of the Internet of Things (IoT) in agriculture and smart farming towards urban greening: A review. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 11–28. [Google Scholar] [CrossRef] [Green Version]
- Zamora-Izquierdo, M.A.; Santa, J.; Martínez, J.A.; Martínez, V.; Skarmeta, A.F. Smart farming IoT platform based on edge and cloud computing. Biosyst. Eng. 2019, 177, 4–17. [Google Scholar] [CrossRef]
- Chukkapalli, S.L.L.; Piplai, A.; Mittal, S.; Gupta, M.; Joshi, A. A Smart-Farming Ontology for Attribute Based Access Control. In Proceedings of the 2020 IEEE 6th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing,(HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Baltimore, MD, USA, 25–27 May 2020; pp. 29–34. [Google Scholar]
- Adi, E.; Anwar, A.; Baig, Z.; Zeadally, S. Machine learning and data analytics for the IoT. Neural Comput. Appl. 2020, 32, 16205–16233. [Google Scholar] [CrossRef]
- Steup, R.; Dombrowski, L.; Su, N.M. Feeding the world with data: Visions of data-driven farming. In Proceedings of the 2019 on Designing Interactive Systems Conference, Online, 18 June 2019; pp. 1503–1515. [Google Scholar]
- Nandhini, M.; Jenila, S. Time Constrained Data Destruction in Cloud. Int. J. Innov. Res. Comput. Commun. Eng. 2014, 3, 2228–2231. [Google Scholar]
- Guan, Z.; Zhang, Y.; Wu, L.; Wu, J.; Li, J.; Ma, Y.; Hu, J. APPA: An anonymous and privacy preserving data aggregation scheme for fog-enhanced IoT. J. Netw. Comput. Appl. 2019, 125, 82–92. [Google Scholar] [CrossRef]
- Kho, J.; Rogers, A.; Jennings, N.R. Decentralized Control of Adaptive Sampling in Wireless Sensor Networks. ACM Trans. Sens. Netw. 2009, 5, 1–35. [Google Scholar] [CrossRef] [Green Version]
- Quinonero-Candela, J.; Rasmussen, C.E. A Unifying View of Sparse Approximate Gaussian Process Regression. J. Mach. Learn. Res. 2005, 6, 1939–1959. [Google Scholar]
- Masiero, R.; Quer, G.; Munaretto, D.; Rossi, M.; Widmer, J.; Zorzi, M. Data Acquisition through joint Compressive Sensing and Principal Component Analysis. In Proceedings of the GLOBECOM 2009–2009 IEEE Global Telecommunications Conference, Honolulu, HI, USA, 30 November–4 December 2009; pp. 1–6. [Google Scholar]
- Wold, S.; Esbensen, K.; Geladi, P. Principal component analysis. Chemom. Intell. Lab. Syst. 1987, 2, 37–52. [Google Scholar] [CrossRef]
- Masiero, R.; Quer, G.; Rossi, M.; Zorzi, M. A Bayesian Analysis of Compressive Sensing Data Recovery in Wireless Sensor Networks. In Proceedings of the 2009 International Conference on Ultra Modern Telecommunications & Workshops, St. Petersburg, Russia, 12–14 October 2009; pp. 1–6. [Google Scholar]
- Macua, S.V.; Belanovic, P.; Zazo, S. Consensus-based distributed principal component analysis in wireless sensor networks. In Proceedings of the IEEE 11th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Marrakech, Morocco, 20–23 June 2010; pp. 1–5. [Google Scholar]
- Ndzi, D.L.; Harun, A.; Ramli, F.M.; Kamarudin, M.L.; Zakaria, A.; Shakaff, A.Y.M.; Jaafar, M.N.; Zhou, S.; Farook, R.S. Wireless sensor network coverage measurement and planning in mixed crop farming. Comput. Electron. Agric. 2014, 105, 83–94. [Google Scholar] [CrossRef] [Green Version]
- Xie, M.; Huang, M.; Bai, Y.; Hu, Z. The Anonymization Protection Algorithm Based on Fuzzy Clustering for the Ego of Data in the Internet of Things. J. Electr. Comput. Eng. 2017, 2017, 2970673. [Google Scholar] [CrossRef] [Green Version]
- Casino, F.; Domingo-Ferrer, J.; Patsakis, C.; Puig, D.; Solanas, A. A k-anonymous approach to privacy preserving collaborative filtering. J. Comput. Syst. Sci. 2015, 81, 1000–1011. [Google Scholar] [CrossRef]
- Martin, M.K.; Helm, J.; Patyk, K.A. An approach for de-identification of point locations of livestock premises for further use in disease spread modeling. Prev. Vet. Med. 2015, 120, 131–140. [Google Scholar] [CrossRef]
- Anggorojati, B.; Mahalle, P.N.; Prasad, N.R.; Prasad, R. Capability-based Access Control Delegation Model on the Federated IoT Network. In Proceedings of the 15th International Symposium on Wireless Personal Multimedia Communications, Taipei, Taiwan, 24–27 September 2012; pp. 604–608. [Google Scholar]
- Anggorojati, B.; Mahalle, P.N.; Prasad, N.R.; Prasad, R.; Theoleyre, F.; Pang, A. Secure access control and authority delegation based on capability and context awareness for federated iot. In Internet of Things and M2M Communications; Aalborg University: Aalborg, Denmark, 2013; pp. 135–160. [Google Scholar]
- Mahalle, P.N.; Anggorojati, B.; Prasad, N.R.; Prasad, R.R. Identity Authentication and Capability Based Access Control (IACAC) for the Internet of Things. J. Cyber Secur. Mobil. 2013, 1, 309–348. [Google Scholar] [CrossRef]
- Hernández-ramos, J.L.; Jara, A.J.; Marín, L. DCapBAC: Embedding authorization logic into smart things through ECC optimizations. Int. J. Comput. Math. 2014, 93, 37–41. [Google Scholar] [CrossRef]
- Bernabe, J.B.; Ramos, J.L.H.; Gomez, A.F.S. TACIoT: Multidimensional trust-aware access control system for the Internet of Things. Soft Comput. 2016, 20, 1763–1779. [Google Scholar] [CrossRef]
- Zhang, G.; Tian, J. An extended role based access control model for the Internet of Things. In Proceedings of the 2010 International Conference on Information, Networking and Automation (ICINA), Kunming, China, 17–19 October 2010; Volume 1, pp. V1-319–V1-323. [Google Scholar]
- Jindou, J.; Xiaofeng, Q.; Cheng, C. Access Control Method for Web of Things based on Role and SNS. In Proceedings of the 2012 IEEE 12th International Conference on Computer and Information Technology, Chengdu, China, 27–29 October 2012; pp. 316–321. [Google Scholar]
- Barka, E.; Mathew, S.S.; Atif, Y. Securing the Web of Things with Role-Based Access Control; Springer: Cham, Switzerland, 2015; pp. 14–26. [Google Scholar]
- Gusmeroli, S.; Piccione, S.; Rotondi, D. A capability-based security approach to manage access control in the Internet of Things. Math. Comput. Model. 2013, 58, 1189–1205. [Google Scholar] [CrossRef]
- Hernández-Ramos, J.L.; Jara, A.J.; Marín, L.; Skarmeta, A.F. Distributed Capability-based Access Control for the Internet of Things. J. Internet Serv. Inf. Secur. 2013, 3, 1–16. [Google Scholar]
- Jiang, L.; Li, T.; Li, X.; Atiquzzaman, M.; Ahmad, H.; Wang, X. Anonymous Communication via Anonymous Identity-Based Encryption and Its Application in IoT. Wirel. Commun. Mob. Comput. 2018, 2018, 6809796. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, J.; Schooler, E.M.; Ion, M. Performance evaluation of Attribute-Based Encryption: Toward data privacy in the IoT. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 725–730. [Google Scholar]
- Belguith, S.; Kaaniche, N.; Laurent, M.; Jemai, A.; Attia, R. PHOABE: Securely outsourcing multi-authority attribute based encryption with policy hidden for cloud assisted IoT. Comput. Netw. 2018, 133, 141–156. [Google Scholar] [CrossRef] [Green Version]
- Davoli, L.; Protskaya, Y.; Veltri, L. An anonymization protocol for the Internet of Things. In Proceedings of the 2017 International Symposium on Wireless Communication Systems (ISWCS), Bologna, Italy, 28–31 August 2017; Volume 2017, pp. 459–464. [Google Scholar]
- Liang, K.; Susilo, W.; Liu., J.K. Privacy-preserving ciphertext multi-sharing control for big data storage. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1578–1589. [Google Scholar] [CrossRef] [Green Version]
- Li, S.; Li, M.; Xu, H.; Zhou, X. Searchable encryption scheme for personalized privacy in IoT-based big data. Sensors 2019, 19, 1059. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Li, J.; Zhang, Y.; Ning, J.; Huang, X.; Poh, G.S.; Wang, D. Attribute Based Encryption with Privacy Protection and Accountability for CloudIoT. IEEE Trans. Cloud Comput. 2020, 10, 762–773. [Google Scholar] [CrossRef]
- Anbuchelian, S.; Sowmya, C.M.; Ramesh, C. Efficient and secure auditing scheme for privacy preserving data storage in cloud. Cluster Comput. 2019, 22, 9767–9775. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, X.; Guo, W.; Liu, X.; Chang, V. Privacy-preserving smart IoT-based healthcare big data storage and self-adaptive access control system. Inf. Sci. 2019, 479, 567–592. [Google Scholar] [CrossRef]
- Huning, L.; Bauer, J.; Aschenbruck, N. A Privacy Preserving Mobile Crowdsensing Architecture for a Smart Farming Application. In Proceedings of the First ACM Workshop on Mobile Crowdsensing Systems and Applications, Delft, The Netherlands, 5 November 2017; Volume 2017, pp. 62–67. [Google Scholar]
- Dwork, C. Differential Privacy in Encyclopedia of Cryptography and Security; Springer: Cham, Switzerland, 2006; pp. 338–340. [Google Scholar]
- Udendhran, R.; Balamurugan, M. Towards secure deep learning architecture for smart farming-based applications. Complex Intell. Syst. 2020, 7, 659–666. [Google Scholar] [CrossRef]
- Xu, C.; Ren, J.; Zhang, D.; Zhang, Y. Distilling at the edge: A local differential privacy obfuscation framework for IoT Data Analytics. IEEE Commun. Mag. 2018, 56, 20–25. [Google Scholar] [CrossRef]
- Yan, Q.; Lou, J.; Vuran, M.C.; Irmak, S. Scalable Privacy-preserving Geo-distance Evaluation for Precision Agriculture IoT Systems. ACM Trans. Sens. Netw. 2021, 17, 1–30. [Google Scholar] [CrossRef]
- Niemitalo, O.; Koskinen, E.; Hyväluoma, J.; Lientola, E.; Lindberg, H.; Koskela, O.; Kunttu, I. A year acquiring and publishing drone aerial images in research on agriculture, forestry, and private urban gardens. Technol. Innov. Manag. Rev. 2021, 11, 5–16. [Google Scholar] [CrossRef]
- Zhang, Y.; Pan, J.; Qi, L.; He, Q. Privacy-preserving quality prediction for edge-based IoT services. Future Gener. Comput. Syst. 2021, 114, 336–348. [Google Scholar] [CrossRef]
- Xiong, J.; Ren, J.; Chen, L.; Yao, Z.; Lin, M.; Wu, D.; Niu, B. Enhancing Privacy and Availability for Data Clustering in Intelligent Electrical Service of IoT. IEEE Internet Things J. 2018, 6, 1530–1540. [Google Scholar] [CrossRef]
- Blum, A.; Dwork, C.; McSherry, F.; Nissim, K. Practical Privacy: The SuLQ Framework. In Proceedings of the Twenty-Fourth ACM SIGMOD-SIGACT-SIGART Symposium on Principles of Database Systems, Baltimore, ML, USA, 13–15 June 2005; pp. 128–138. [Google Scholar]
- Kyntäjä, J.; Frandsen, J.; Ilomäki, J.; Jafner, N.; Jóhannesson, G.; Mikalsen, V. Nordic Cattle Data eXchange-a shared standard for data transfer. ICAR Tech. Ser. 2018, 23, 99–100. [Google Scholar]
- Barto. Available online: https://www.barto.ch (accessed on 15 May 2022).
- Join Data. Available online: https://www.join-data.nl (accessed on 15 May 2022).
- Wahyu, R.; Zuhri, I.; Jatra, A. HARA Token Whitepaper. Available online: https://www.scribd.com/document/392346486/HARA-Token-White-Paper-v20180923 (accessed on 15 May 2022).
- Reiter, M.K.; Rubin, A.D. Crowds: Anonymity for web transactions. ACM Trans. Inf. Syst. Secur. 1998, 1, 66–92. [Google Scholar] [CrossRef]
- Chen, J.; Tian, Z.; Cui, X.; Yin, L.; Wang, X. Trust architecture and reputation evaluation for internet of things. J. Ambient Intell. Humaniz. Comput. 2019, 10, 3099–3107. [Google Scholar] [CrossRef] [Green Version]
- Kreutz, D.; Ramos, F.M.; Verissimo, P.E.; Rothenberg, C.E.; Azodolmolky, S.; Uhlig, S. Software-Defined Networking: A Comprehensive Survey. Proc. IEEE 2014, 103, 14–76. [Google Scholar] [CrossRef] [Green Version]
- Atzori, L.; Iera, A.; Morabito, G. From “Smart Objects” to “Social Objects”: The Next Evolutionary Step of the Internet of Things. IEEE Commun. Mag. 2014, 52, 97–105. [Google Scholar] [CrossRef]
- Nitti, M.; Girau, R.; Atzori, L. Trustworthiness Management in the Social Internet of Things. IEEE Trans. Knowl. Data Eng. 2014, 26, 1253–1266. [Google Scholar] [CrossRef]
- Amiri-Zarandi, M.; Dara, R.A.; Fraser, E. LBTM: A lightweight blockchain-based trust management system for social internet of things. J. Supercomput. 2022, 78, 8302–8320. [Google Scholar] [CrossRef]
- Zhang, F.Z.; Chen, J.; Chen, H.B.; Zang, B. Lifetime privacy and self-destruction of data in the cloud. J. Comput. Res. Dev. 2011, 48, 1155. [Google Scholar]
- Amiri-Zarandi, M.; Dara, R.A.; Fraser, E. A survey of machine learning-based solutions to protect privacy in the Internet of Things. Comput. Secur. 2020, 96, 101921. [Google Scholar] [CrossRef]
- De Souza, P.S.S.; Rubin, F.P.; Hohemberger, R.; Ferreto, T.C.; Lorenzon, A.F.; Luizelli, M.C.; Rossi, F.D. Detecting abnormal sensors via machine learning: An IoT farming WSN-based architecture case study. Measurement 2020, 164, 108042. [Google Scholar] [CrossRef]
- Chukkapalli, S.S.L.; Ranade, P.; Mittal, S.; Joshi, A. A Privacy Preserving Anomaly Detection Framework for Cooperative Smart Farming Ecosystem. In Proceedings of the 2021 Third IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 13–15 December 2021; pp. 340–347. [Google Scholar]
- Das, R.; Gadre, A.; Zhang, S.; Kumar, S.; Moura, J.M.F. A Deep Learning Approach to IoT Authentication. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Shi, C.; Liu, J.; Liu, H.; Chen, Y. Smart User Authentication through Actuation of Daily Activities Leveraging WiFi-enabled IoT. In Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Chennai, India, 10–14 July 2017; pp. 1–10. [Google Scholar]
- Canedo, J.; Skjellum, A. Using machine learning to secure IoT systems. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 219–222. [Google Scholar]
- Ni, Q.; Lobo, J. Automating Role-based Provisioning by Learning from Examples. In Proceedings of the 14th ACM Symposium on Access Control Models and Technologies, Online, 3 June 2009; pp. 75–84. [Google Scholar]
- Kulkarni, R.V.; Venayagamoorthy, G.K. Neural network based secure media access control protocol for wireless sensor networks. In Proceedings of the 2009 International Joint Conference on Neural Networks, Atlanta, GA, USA, 14–19 June 2009; pp. 1680–1687. [Google Scholar]
- Outchakoucht, A.; Hamza, E.S.; Leroy, J.P. Dynamic Access Control Policy based on Blockchain and Machine Learning for the Internet of Things. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 7. [Google Scholar] [CrossRef]
- Konečný, J.; McMahan, H.B.; Ramage, D.; Richtárik, P. Federated Optimization: Distributed Machine Learning for On-Device Intelligence. arXiv 2016, arXiv:1610.02527. [Google Scholar]
- Wang, X.; Han, Y.; Wang, C.; Zhao, Q.; Chen, X.; Chen, M. In-Edge AI: Intelligentizing Mobile Edge Computing, Caching and Communication by Federated Learning. IEEE Netw. 2019, 33, 156–165. [Google Scholar] [CrossRef] [Green Version]
- Wang, S.; Tuor, T.; Salonidis, T.; Leung, K.K.; Makaya, C.; He, T.; Chan, K. Adaptive Federated Learning in Resource Constrained Edge Computing Systems. IEEE J. Sel. Areas Commun. 2018, 37, 1205–1221. [Google Scholar] [CrossRef] [Green Version]
- Guardo, E.; Stefano, A.D.; Corte, A.L.; Sapienza, M.; Scatà, M. A fog computing-based IoT framework for precision agriculture. J. Internet Technol. 2018, 19, 1401–1411. [Google Scholar]
- Hsu, T.C.; Yang, H.; Chung, Y.C.; Hsu, C.H. A Creative IoT agriculture platform for cloud fog computing. Sustain. Comput. Inform. Syst. 2018, 28, 100285. [Google Scholar] [CrossRef]
- Malik, A.W.; Rahman, A.U.; Qayyum, T.; Ravana, S.D. Leveraging Fog Computing for Sustainable Smart Farming Using Distributed Simulation. IEEE Internet Things J. 2020, 7, 3300–3309. [Google Scholar] [CrossRef]
- Rezk, N.G.; Hemdan, E.E.D.; Attia, A.F.; El-Sayed, A.; El-Rashidy, M.A. An efficient IoT based smart farming system using machine learning algorithms. Multimed. Tools Appl. 2020, 80, 773–797. [Google Scholar] [CrossRef]
- Zhang, J.; Li, X.; Zhang, X.; Xue, Y.; Srivastava, G.; Dou, W. Service offloading oriented edge server placement in smart farming. Softw. Pract. Exp. 2020, 51, 2540–2557. [Google Scholar] [CrossRef]
- Caria, M.; Schudrowitz, J.; Jukan, A.; Kemper, N. Smart farm computing systems for animal welfare monitoring. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017; pp. 152–157. [Google Scholar]
- Taneja, M.; Byabazaire, J.; Davy, A.; Olariu, C. Fog assisted application support for animal behaviour analysis and health monitoring in dairy farming. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; Volume 2018, pp. 819–824. [Google Scholar]
- Taneja, M.; Jalodia, N.; Byabazaire, J.; Davy, A.; Olariu, C. SmartHerd management: A microservices-based fog computing–assisted IoT platform towards data-driven smart dairy farming. Softw. Pract. Exp. 2019, 49, 1055–1078. [Google Scholar] [CrossRef] [PubMed]
- Alonso, R.S.; Sittón-Candanedo, I.; García, Ó.; Prieto, J.; Rodríguez-González, S. An intelligent Edge-IoT platform for monitoring livestock and crops in a dairy farming scenario. Ad Hoc Netw. 2020, 98, 102047. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Privacy preservation in blockchain based IoT systems: Integration issues, prospects, challenges, and future research directions. Future Gener. Comput. Syst. 2019, 97, 512–529. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://www.debr.io/article/21260.pdf (accessed on 15 May 2022).
- Founder, G.W.; Gavin, E. Ethereum: A Secure Decentralised Generalised Transaction Ledger. Available online: https://files.gitter.im/ethereum/yellowpaper/VIyt/Paper.pdf (accessed on 15 May 2022).
- Ge, L.; Brewster, C.; Spek, J.; Smeenk, A.; Top, J.; Diepen, F.V.; Klaase, B.; Graumans, C.; Wildt, M.D.R.D. Blockchain for Agriculture and Food: Findings from the Pilot Study; Wageningen University & Research: Wageningen, The Netherlands, 2017. [Google Scholar]
- Bordel, B.; Martin, D.; Alcarria, R.; Robles, T. A Blockchain-based Water Control System for the Automatic Management of Irrigation Communities. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 17–18. [Google Scholar]
- Bodkhe, U.; Tanwar, S.; Bhattacharya, P.; Kumar, N. Blockchain for precision irrigation: Opportunities and challenges. Trans. Emerg. Telecommun. Technol. 2020, 1, e4059. [Google Scholar] [CrossRef]
- Lin, J.; Zhang, A.; Shen, Z.; Chai, Y. Blockchain and IoT based food traceability for smart agriculture. In Proceedings of the 3rd International Conference on Crowd Science and Engineering, Singapore, 28–31 July 2018; pp. 1–6. [Google Scholar]
- Casado-Vara, R.; Prieto, J.; Prieta, F.D.L.; Corchado, J.M. How blockchain improves the supply chain: Case study alimentary supply chain. Procedia Comput. Sci. 2018, 134, 393–398. [Google Scholar] [CrossRef]
- Kamble, S.S.; Gunasekaran, A.; Sharma, R. Modeling the blockchain enabled traceability in agriculture supply chain. Int. J. Inf. Manag. 2020, 52, 101967. [Google Scholar] [CrossRef]
- Geethanjali, B.; Muralidhara, B.L. A Framework for Banana Plantation Growth Using Blockchain Technology. In ICT Analysis and Applications; Springer: Cham, Switzerland, 2020; pp. 615–620. [Google Scholar]
- Amiri-Zarandi, M.; Dara, R.A. Blockchain-based Trust Management in Social Internet of Things. In Proceedings of the 2020 IEEE International Conference on Dependable, Autonomic and Secure Computing, International Conference on Pervasive Intelligence and Computing, International Conference on Cloud and Big Data Computing, International Conference on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Calgary, AB, Canada, 17–22 August 2020; pp. 49–54. [Google Scholar]
- Tahar, M.; Hammi, B.; Bellot, P. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar]
- Wu, H.T.; Tsai, C.W. An intelligent agriculture network security system based on private blockchains. J. Commun. Netw. 2019, 21, 503–508. [Google Scholar] [CrossRef]
- Shahid, A.; Almogren, A.; Javaid, N.; Al-Zahrani, F.A.; Zuair, M.; Alam, M. Blockchain-Based Agri-Food Supply Chain: A Complete Solution. IEEE Access 2020, 8, 69230–69243. [Google Scholar] [CrossRef]
- Salah, K.; Nizamuddin, N.; Jayaraman, R.; Omar, M. Blockchain-Based Soybean Traceability in Agricultural Supply Chain. IEEE Access 2019, 7, 73295–73305. [Google Scholar] [CrossRef]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Towards a Novel Privacy-Preserving Access Control Model Based on Blockchain Technology in IoT. In Europe and MENA Cooperation Advances in Information and Communication Technologies; Springer: Cham, Switzerland, 2017; pp. 523–533. [Google Scholar]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. FairAccess: A new Blockchain-based access control framework for the Internet of Things: FairAccess: A new access control framework for IoT FairAccess: A new Blockchain-based access control framework for the Internet of Things. Secur. Commun. Netw. 2016, 9, 5943–5964. [Google Scholar] [CrossRef]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2018, 6, 1594–1605. [Google Scholar] [CrossRef] [Green Version]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Internet Things J. 2017, 5, 1184–1195. [Google Scholar] [CrossRef]
- Wiseman, L.; Sanderson, J.; Zhang, A.; Jakku, E. Farmers and their data: An examination of farmers’ reluctance to share their data through the lens of the laws impacting smart farming. NJAS Wagen. J. Life Sci. 2019, 90, 100301. [Google Scholar] [CrossRef]
- Regan, Á. “Smart farming” in Ireland: A risk perception study with key governance actors. NJAS Wagening. J. Life Sci. 2019, 90, 100292. [Google Scholar] [CrossRef]
- Van der Burg, S.; Wiseman, L.; Krkeljas, J. Trust in farm data sharing: Reflections on the EU code of conduct for agricultural data sharing. Ethics Inf. Technol. 2021, 23, 185–198. [Google Scholar] [CrossRef]
- AFBF. Privacy and Security Issues for Farm Data. Available online: https://www.fb.org/issues/technology/dataprivacy/privacyandsecurityprinciplesforfarmdata (accessed on 15 May 2022).
- Wang, L.; Near, J.P.; Somani, N.; Gao, P.; Low, A.; Dao, D.; Song, D. Data Capsule: A New Paradigm for Automatic Compliance with Data Privacy Regulations. In Heterogeneous Data Management, Polystores, and Analytics for Healthcare; Springer: Cham, Switzerland, 2019; Volume 11721, pp. 3–23. [Google Scholar]

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amiri-Zarandi, M.; Dara, R.A.; Duncan, E.; Fraser, E.D.G. Big Data Privacy in Smart Farming: A Review. Sustainability 2022, 14, 9120. https://doi.org/10.3390/su14159120
Amiri-Zarandi M, Dara RA, Duncan E, Fraser EDG. Big Data Privacy in Smart Farming: A Review. Sustainability. 2022; 14(15):9120. https://doi.org/10.3390/su14159120
Chicago/Turabian StyleAmiri-Zarandi, Mohammad, Rozita A. Dara, Emily Duncan, and Evan D. G. Fraser. 2022. "Big Data Privacy in Smart Farming: A Review" Sustainability 14, no. 15: 9120. https://doi.org/10.3390/su14159120
APA StyleAmiri-Zarandi, M., Dara, R. A., Duncan, E., & Fraser, E. D. G. (2022). Big Data Privacy in Smart Farming: A Review. Sustainability, 14(15), 9120. https://doi.org/10.3390/su14159120





