A Comprehensive Review of Face Morph Generation and Detection of Fraudulent Identities
Abstract
1. Introduction
- I.
- This research explains and analyzes different morph generation techniques, tools, and their limitations.
- II.
- It presents data repositories used for morph attack detection and their challenges and limitations.
- III.
- It shows the evaluation metrics used as standard practice in the field.
- IV.
- It also gives in-depth knowledge and analysis of morph detection techniques and their results on different datasets.
- V.
- It also gives the open challenges and future research prospects of the field.
2. Materials and Methods
2.1. Image Morphing
2.2. Source Databases
2.3. Evaluation Metrics
2.4. Methods of Morph Attack Detection
- Single Image MAD Method
- Differential MAD Method
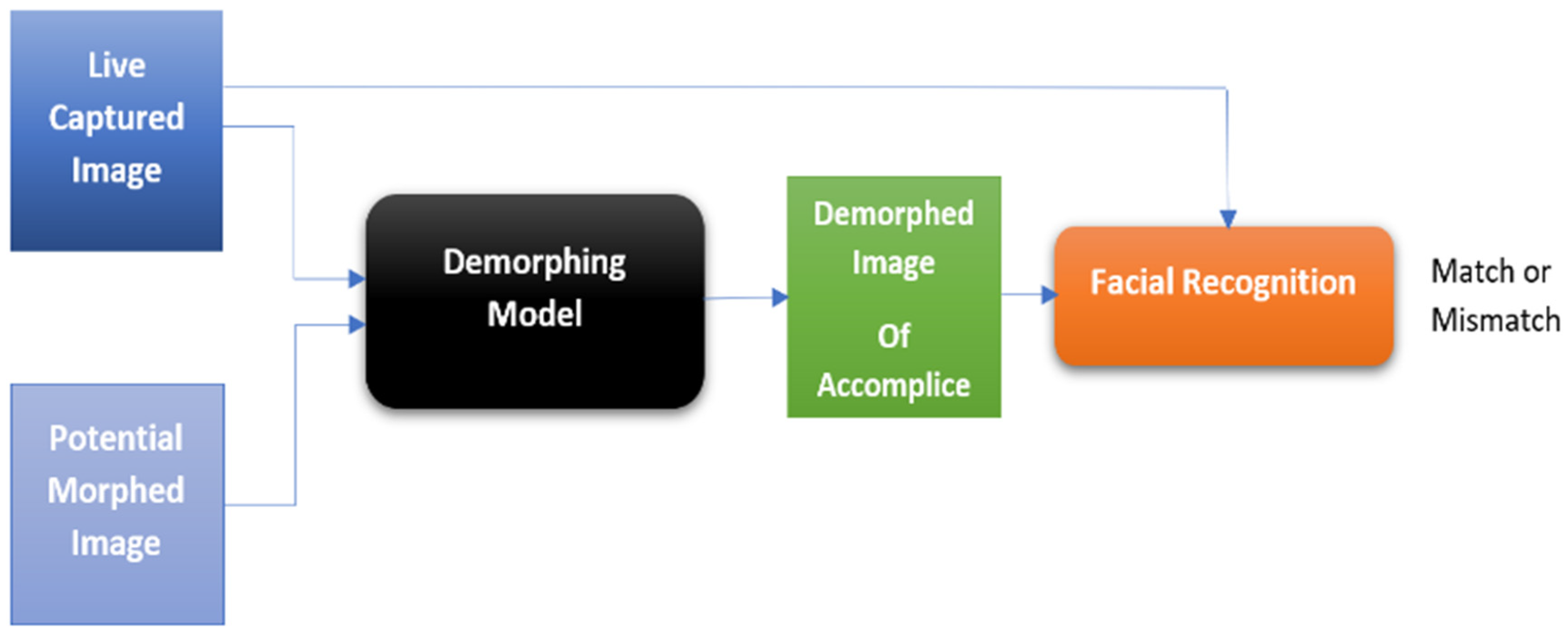
2.4.1. Image Demorphing
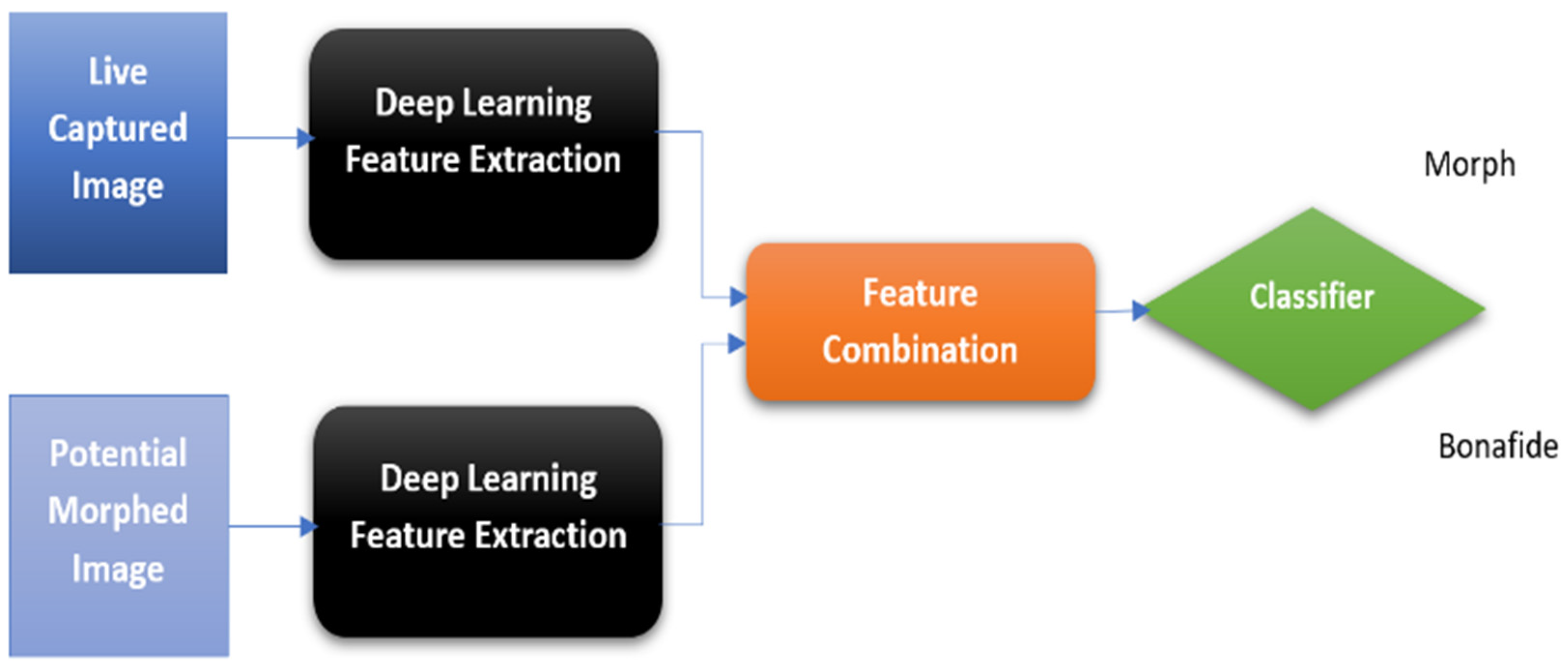
2.4.2. Feature Extraction and Comparison
3. Results
4. Conclusions and Future Research Direction
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Peng, F.; Zhang, L.B.; Long, M. FD-GAN: Face De-Morphing Generative Adversarial Network for Restoring Accomplice’s Facial Image. IEEE Access 2019, 7, 75122–75131. [Google Scholar] [CrossRef]
- Ferrara, M.; Franco, A.; Maltoni, D. Face Demorphing. IEEE Trans. Inf. Secur. 2018, 13, 1008–1017. [Google Scholar] [CrossRef]
- Scherhag, U.; Rathgeb, C.; Merkle, J.; Breithaupt, R.; Busch, C. Face Recognition Systems Under Morphing Attacks: A Survey. IEEE Access 2019, 7, 23012–23026. [Google Scholar] [CrossRef]
- Yip, A.W.; Sinha, P. Contribution of Color to Face Recognition. Perception 2002, 31, 995–1003. [Google Scholar] [CrossRef] [PubMed]
- Scherhag, U.; Rathgeb, C.; Merkle, J.; Busch, C. Deep Face Representations for Differential Morphing Attack Detection. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3625–3639. [Google Scholar] [CrossRef]
- Chen, B.C.; Chen, C.S.; Hsu, W.H. Face Recognition and Retrieval Using Cross-Age Reference Coding with Cross-Age Celebrity Dataset. IEEE Trans. Multimed. 2015, 17, 804–815. [Google Scholar] [CrossRef]
- Smythe, D.B. A Two-Pass Mesh Warping Algorithm for Object Transformation and Image Interpolation; Technical Report 1030; ILM Computer Graphics Department, Lucasfilm: San Rafael, CA, USA, 1990. [Google Scholar]
- Beier, T.; Neely, S. Feature-based image metamorphosis. In Proceedings of the SIGGRAPH’92: 19th Annual Conference on Computer Graphics and Interactive Techniques, Chicago, IL, USA, 26–31 July 1992; Volume 26, pp. 35–42. [Google Scholar]
- Zhang, H.; Venkatesh, S.; Ramachandra, R.; Raja, K.; Damer, N.; Busch, C. Mipgan—Generating strong and high quality morphing attacks using identity prior driven gan. IEEE Trans. Biom. Behav. Identity Sci. 2021, 3, 365–383. [Google Scholar] [CrossRef]
- Venkatesh, S.; Zhang, H.; Ramachandra, R.; Raja, K.; Damer, N.; Busch, C. Can GAN generated morphs threaten face recognition systems equally as landmark based morphs?-vulnerability and detection. In Proceedings of the IWBF 2020: 8th International Workshop on Biometrics and Forensics, Porto, Portugal, 29–30 April 2020; pp. 1–6. [Google Scholar]
- Panetta, K.; Wan, Q.; Agaian, S.; Rajeev, S.; Kamath, S.; Rajendran, R.; Rao, S.P.; Kaszowska, A.; Taylor, H.A.; Samani, A.; et al. A Comprehensive Database for Benchmarking Imaging Systems. IEEE Trans. Pattern Anal. Mach. Intell. 2020, 42, 509–520. [Google Scholar] [CrossRef]
- Sim, T.; Baker, S.; Bsat, M. The CMU pose, Illumination, and expression database. IEEE Trans. Pattern Anal. Mach. Intell. 2003, 25, 1615–1618. [Google Scholar]
- Martínez, A.; Benavente, R. The AR Face Database; Tech. Rep. #24; University Autònoma Barcelona: Bellaterra, Spain, 1998. [Google Scholar]
- Yin, L.; Chen, X.; Sun, Y.; Worm, T.; Reale, M. A high-resolution 3d dynamic facial expression database. In Proceedings of the 2008 8th IEEE international conference on automatic face gesture recognition, Amsterdam, The Netherlands, 17–19 September 2008; pp. 1–6. [Google Scholar] [CrossRef]
- Ma, D.S.; Correll, J.; Wittenbrink, B. The chicago face database: A free stimulus set of faces and norming data. Behav. Res. Methods 2015, 47, 1122–1135. [Google Scholar] [CrossRef] [PubMed]
- Kasiski, A.; Florek, A.; Schmidt, A. The PUT face database. Image Process. Commun. 2008, 13, 59–64. [Google Scholar]
- Grgic, M.; Delac, K.; Grgic, S. Scface—Surveillance cameras face database. Multimed. Tools Appl. 2011, 51, 863–879. [Google Scholar] [CrossRef]
- Senthilkumar, R.; Gnanamurthy, R.K. A detailed survey on 2D and 3D still face and face video databases part I. In Proceedings of the 2014 International Conference on Communication and Signal Processing, Melmaruvathur, India, 3–5 April 2014. [Google Scholar]
- Kannala, J.; Rahtu, E. BSIF: Binarized statistical image features. In Proceedings of the 21st International Conference on Pattern Recognition (ICPR2012), Tsukuba, Japan, 11–15 November 2012; pp. 1363–1366. [Google Scholar]
- Seibold, C.; Samek, W.; Hilsmann, A.; Eisert, P. Accurate and robust neural networks for face morphing attack detection. J. Inf. Secur. Appl. 2020, 53, 102526. [Google Scholar] [CrossRef]
- Ortega-Delcampo, D.; Conde, C.; Palacios-Alonso, D.; Cabello, E. Border Control Morphing Attack Detection with a Convolutional Neural Network De-Morphing Approach. IEEE Access 2020, 8, 92301–92313. [Google Scholar] [CrossRef]
- Kussul, E.; Baydyk, T. Face recognition using special neural networks. In Proceedings of the International Joint Conference on Neural Networks (IJCNN), Killarney, Ireland, 12–17 October 2015. [Google Scholar]
- Raghavendra, R.; Raja, K.B.; Busch, C. Exploring the usefulness of light field cameras for biometrics: An empirical study on face and iris recognition. IEEE Trans. Inf. Forensics Secur. 2016, 11, 922–936. [Google Scholar] [CrossRef]
- Venkatesh, S.; Ramachandra, R.; Raja, K.; Spreeuwers, L.; Veldhuis, R.; Busch, C. Detecting Morphing Face Attacks Using Residual Noise from Deep Multi-Scale Context Aggregation Network. In Proceedings of the IEEE Winter Conference on Applications of Computer Vision (WACV), Snowmass, CO, USA, 1–5 March 2020. [Google Scholar]
- AMSL Face Morph Image Data Set. Available online: https://omen.cs.uni-magdeburg.de/disclaimer/index.php (accessed on 20 December 2021).
- Sarkar, E.; Korshunov, P.; Colbois, L.; Marcel, S. Vulnerability analysis of face morphing attacks from landmarks and generative adversarial networks. arXiv 2020, arXiv:2012.05344. [Google Scholar]
- Raghavendra, R.; Raja, K.B.; Venkatesh, S.; Busch, C. Transferable deep-cnn features for detecting digital and print-scanned morphed face images. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), Honolulu, HI, USA, 21–26 July 2017; pp. 1822–1830. [Google Scholar]
- Hamza, M.; Tehsin, S.; Karamti, H.; Alghamdi, N.S. Generation and Detection of Face Morphing Attacks. IEEE Access 2022, 10, 72557–72576. [Google Scholar] [CrossRef]
- Pérez, P.; Gangnet, M.; Blake, A. Poisson image editing. In Proceedings of the SIGGRAPH ’03: ACM SIGGRAPH 2003 Papers, San Diego, CA, USA, 27–31 July 2003; pp. 313–318. [Google Scholar]
- Bach, S.; Binder, A.; Montavon, G.; Klauschen, F.; Müller, K.-R.; Samek, W. On pixel-wise explanations for non-linear classifier decisions by layer-wise relevance propagation. PLoS ONE 2015, 10, e0130140. [Google Scholar] [CrossRef]
- Lapuschkin, S.; Binder, A.; Montavon, G.; Müller, K.-R.; Samek, W. The layer-wise relevance propagation toolbox for artificial neural networks. J. Mach. Learn. Res. 2016, 17, 1–5. [Google Scholar]
- Samek, W.; Wiegand, T.; Müller, K.-R. Explainable artificial intelligence: Under-standing, visualizing and interpreting deep learning models. ITU J. ICT Discov. 2018, 1, 39–48. [Google Scholar]
- Ferrara, M.; Franco, A.; Maltoni, D. The magic passport. In Proceedings of the IEEE International Joint Conference on Biometrics, Clearwater, FL, USA, 29 September–2 October 2014; pp. 1–7. [Google Scholar]
- Hyvearinen, A.; Hurri, J.; Hoyer, P.O. Natural Image Statistics; Springer: Berlin/Heidelberg, Germany, 2009; Volume 39. [Google Scholar]
- van Hateren, J.H.; van der Schaaf, A. Independent component filters of natural images compared with simple cells in primary visual cortex. Proc. R. Soc. London. Ser. B Biol. Sci. 1998, 265, 359–366. [Google Scholar] [CrossRef] [PubMed]
- Scherhag, U.; Raghavendra, R.; Raja, K.; Gomez-Barrero, M.; Rathgeb, C.; Busch, C. On the vulnerability of face recognition systems towards morphed face attack. In Proceedings of the 5th International Workshop on Biometrics and Forensics (IWBF 2017), Coventry, UK, 4–5 April 2017; pp. 1–6. [Google Scholar]
- Viola, P.; Jones, M.J. Robust real-time face detection. Int. J. Comput. Vis. 2004, 57, 137–154. [Google Scholar] [CrossRef]
- Cai, S.; Zhang, L.; Zuo, W.; Feng, X. A probabilistic collaborative representation-based approach for pattern classifi-cation. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016. [Google Scholar]
- Donoho, D.L. De-noising by soft-thresholding. IEEE Trans. Inf. Theory 1995, 41, 613–627. [Google Scholar] [CrossRef]
- Dabov, K.; Foi, A.; Katkovnik, V.; Egiazarian, K. Image denoising by sparse 3-d transform-domain collaborative fil-tering. IEEE Trans. Image Process. 2007, 16, 2080–2095. [Google Scholar] [CrossRef] [PubMed]
- Zhang, M.; Gunturk, B.K. Multiresolution bilateral filtering for image denoising. IEEE Trans. Image Process. 2008, 17, 2324–2333. [Google Scholar] [CrossRef] [PubMed]
- Zhang, K.; Zuo, W.; Chen, Y.; Meng, D.; Zhang, L. Beyond a gaussian denoiser: Residual learning of deep CNN for image denoising. IEEE Trans. Image Process. 2016, 26, 3142–3155. [Google Scholar] [CrossRef] [PubMed]
- Zhang, N.; Deng, W. Fine-grained LFW database. In Proceedings of the International Conference on Biometrics (ICB), Halmstad, Sweden, 13–16 June 2016. [Google Scholar]
- Qin, L.; Peng, F.; Ventatesh, S.; Ramachandra, R.; Long, M.; Busch, C. Low Visual Distortion and Robust Morphing Attacks Based on Partial Face Image Manipulation. IEEE Trans. Biom. Behav. Identity Sci. 2021, 3, 72–88. [Google Scholar] [CrossRef]
- Georghiades, A.; Belhumeur, P.; Kriegman, D. From few to many: Illumination cone models for face recognition under variable lighting and pose. IEEE Trans. Pattern Anal. Mach. Intell. 2001, 23, 643–660. [Google Scholar] [CrossRef]
- Raghavendra, R.; Raja, K.B.; Busch, C. Detecting morphed face images. In Proceedings of the IEEE 8th International Conference on Biometrics Theory, Applications and Systems (BTAS), Niagara Falls, NY, USA, 6–9 September 2016; pp. 1–7. [Google Scholar]
- Mallick, S. Face Morph Using OpenCV. 2016. Available online: www.learnopencv.com/face-morph-using-opencv-cpp-python (accessed on 10 January 2022).
- Wolberg, G. Image Morphing: A Survey. Vis. Comput. 1998, 14, 360–372. [Google Scholar] [CrossRef]
- Gross, R.; Mathews, I.; Cohn, J.; Kanade, T.; Baker, S. Multi-PIE. In Proceedings of the 8th IEEE International Conference of Automatic Face and Gesture Recognition, Amsterdam, The Netherlands, 17–19 September 2008. [Google Scholar]
- Atallah, R.R.; Kamsin, A.; Ismail, M.A.; Abdelrahman, S.A.; Zerdoumi, S. Face Recognition and Age Estimation Implications of Changes in Facial Features: A Critical Review Study. IEEE Accesss 2018, 6, 28290–28304. [Google Scholar] [CrossRef]
- Raja, K.; Ferrara, M.; Franco, A.; Spreeuwers, L.; Batskos, I.; de Wit, F.F.; Gomez-Barrero, M.; Scherhag, U.; Fischer, D.; Venkatesh, S.; et al. Morphing Attack Detection—Database, Evaluation Platform and Benchmarking. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4336–4351. [Google Scholar] [CrossRef]
- Hong, D.; Yao, J.; Meng, D.; Xu, Z.; Chanussot, J. Multimodal GANs: Toward Crossmodal Hyperspectral–Multispectral Image Segmentation. IEEE Trans. Geosci. Remote Sens. 2021, 59, 5103–5113. [Google Scholar] [CrossRef]
- Hong, D.; Gao, L.; Yokoya, N.; Yao, J.; Chanussot, J.; Du, Q.; Zhang, B. More Diverse Means Better: Multimodal Deep Learning Meets Remote-Sensing Imagery Classification. IEEE Trans. Geosci. Remote Sens. 2021, 59, 4340–4354. [Google Scholar] [CrossRef]
- Raja, K.; Gupta, G.; Venkatesh, S.; Ramachandra, R.; Busch, C. Towards generalized morphing attack detection by learning residuals. Image Vis. Comput. 2022, 126, 104535. [Google Scholar] [CrossRef]
- Bhoj, N.; Bhadoria, R.S. Time-Series based Prediction for Energy Consumption of Smart Home Data Using Hybrid Convolution-Recurrent Neural Network. Telemat. Inform. 2022, 75, 101907. [Google Scholar] [CrossRef]


| Datasets | Publication Year | No. of Images | No. of Subjects | Images Per Subject | Feature Distinction | Research Work Reference | Morphing Tools |
|---|---|---|---|---|---|---|---|
| FRGCv2 | 2005 | 28,021 | 4003 | 7 | Illumination, expression, 3D | [5] | UBO Morpher [2], FaceMorpher (2018), OpenCV [18], FaceFusion (2012). |
| [2] | GIMP Software (2017), Sqirlz Morph (2017). | ||||||
| FERET | 1998 | 14,126 | 1199 | Variable | Grayscale and colored lighting, a variety of facial expressions and postures, subjects of variant races, facial hair and hair style | [5] | UBO Morpher, FaceMorpher (2018), OpenCV [18], FaceFusion (2012). |
| [2] | GIMP Software (2017), Sqirlz Morph (2017). | ||||||
| [20] | Triangle warp, Beier-Neely field morphing method [8], and Fotomorph (2014). | ||||||
| FM-DB (Custom Made) | 2019 | 1449 | 63 | 23 | Expression, occlusion, make-up, gender | [1] | Customized morphing process. (Script-Code based) |
| AR Face Database [13] | 1998 | 4000 | 126 | Variable | Eyewear, scarf, expression, illumination, gender | [2] | GIMP Software (2017), Sqirlz Morph (2017). |
| FRAV-ABC | 2020 | 2340 | 1170 | 2 | Age, gender | [21] | GIMP Software (2017), Sqirlz Morph (2017). |
| BU-4DFE [14] | 2008 | 60,600 | 101 | 600 | Expression, race, gender | [20] | Triangle warp, Beier-Neely field morphing method [8], and Fotomorph (2014). |
| CFD [15] | 2015 | 597 | 597 | 1 | Race, gender | [20] | Triangle warp, Beier-Neely field morphing method [8], and Fotomorph (2014). |
| FEI (Faculty of Industrial Engineering) [22] | 2015 | 2800 | 200 | 14 | Different poses, facial expression variety, illumination change, eyewear, and varying races | [20] | Triangle warp, Beier-Neely field morphing method [8], and Fotomorph (2014). |
| PUT [16] | 2008 | 9971 | 100 | Variable | Posture, high resolution | [20] | Triangle warp, Beier-Neely field morphing method [8], and Fotomorph (2014). |
| [23] | OpenCV [24] | ||||||
| SC-Face [17] | 2011 | 4160 | 130 | Variable | Quality, illumination, gender, distance, posture | [20] | Triangle warp, Beier-Neely field morphing method [8], and Fotomorph (2014). |
| Utrecht (Hancock, 2008) | 2008 | 131 | 69 | Variable | Expression, gender, race | [20] | Triangle warp, Beier-Neely field morphing method [8], and Fotomorph (2014). |
| Custom Made Database (All morphed) | 2016 | 450 | 110 | Variable | Race, gender | [23] | GIMP Software (2017) |
| Custom Made (morphed included) | 2017 | 783 | 104 | Variable | Race, gender | [22] | GIMP Software (2017) |
| Custom Made from FRGC and private dataset. (Morphed Included) | 2020 | 11,293 | 747 | Variable | Illumination, expression | [23] | OpenCV [24] |
| AMSL [25] | 2018 | 6592 | 52 | variable | Gender | [26] | OpenCV, FaceMorpher, StyleGAN 2, WebMorpher |
| SOTAMD [27] | 2020 | 5748 morphed images | 150 | Variable | Gender, ethnicity | [28] | FaceMorpher, FaceFusion, FaceMorph, FantaMorph, Triangulation with STASM_landmark |
| Reference | Year of Publication | Methodology | Dataset | Results | Limitations |
|---|---|---|---|---|---|
| [2] | 2018 | Correlated points are used for the extraction of coconspirator’s face from morphed image. | PMDB and MorphDB (Self-built) | False positive rate of biometric system reduces from 66.4% to 6.1%. | Prior knowledge of morphing technique and parameters is required to certify proper extraction of accomplice’s image. It is also required to manually remove certain traces and artifacts. Moreover only two subjects are used. |
| [1] | 2019 | Abstraction of accomplice’s image is performed using double network architecture. Moreover, two restoration losses are also used. | FM-database (Self-built) | Accuracy raised 49.82% to 87.5% in simple cases. For complex cases like variety of facial expression or occluded faces, accuracy enhanced from 0.4691 to 0.649. | Only Morph-2 images are employed for experiments. Limited morphing tools are used for creation of morph images. |
| [21] | 2020 | Convolutional neural network (CNN) is employed for detection of morph attack | FRAV-ABC | Very high accuracy of 98.7% is attained for morph attack detection. DEER of 0.78% to 20.7% is also reported. | Variation in illumination, facial expressions, and bearings is not created. |
| [5] | 2020 | Deep learning solution is proposed for morph detection. | MAD database (Self-built) | DEER of 1% to 7% is reported | Variety of morphed images is created using four different tools, but those tools are not the state-of-the art tools. Does not deal well with headgear, eyewear, and illumination variation. |
| [20] | 2020 | Four training methods and layer-wise propagation are used for analyzing the morphed images. | Self-built | 2.8–3.1% DEER is reported for the method | Data do not includes the images with varying lighting conditions. Moreover headgear, eyewear, and facial hair variations are also not considered. |
| [46] | 2016 | Binary statistical image features (BSIF) are used for feature representation. Classification is carried out through Support Vector Machine (SVM). | Self-built | Reportedly, average classification error rate (ACER) reduced from 37.55% to 1.73% | Morphing tools used for creation of morphed images are very limited. Only morph-2 images were used. |
| [27] | 2017 | State-of-the-art deep learning models like VGG19 and Alexnet are used for transfer learning. For classification, P-CRC is used. | Self-built | DEER decreases from 26.7% to 15.05%. | Data do not includes images with varying lighting conditions. Moreover headgear, eyewear, and facial hair variations are also not considered. Morphing tools used for creation of morphed images are very limited. Only morph-2 images are employed. |
| [24] | 2020 | Residual noise is detected using deep architecture. P-CRC classifier is used for the classification of morphed images. | Derivative of PutDB and FRGC | DEER of 2.6–8% is achieved. Comparison with previous studies is also reported, showing their DEER value between 3.83–42.2%. Computational cost also enhanced four times. | Image data having front-facing pose, static facial expression, and constant radiance used only. Only morph-2 images are employed. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hamza, M.; Tehsin, S.; Humayun, M.; Almufareh, M.F.; Alfayad, M. A Comprehensive Review of Face Morph Generation and Detection of Fraudulent Identities. Appl. Sci. 2022, 12, 12545. https://doi.org/10.3390/app122412545
Hamza M, Tehsin S, Humayun M, Almufareh MF, Alfayad M. A Comprehensive Review of Face Morph Generation and Detection of Fraudulent Identities. Applied Sciences. 2022; 12(24):12545. https://doi.org/10.3390/app122412545
Chicago/Turabian StyleHamza, Muhammad, Samabia Tehsin, Mamoona Humayun, Maram Fahaad Almufareh, and Majed Alfayad. 2022. "A Comprehensive Review of Face Morph Generation and Detection of Fraudulent Identities" Applied Sciences 12, no. 24: 12545. https://doi.org/10.3390/app122412545
APA StyleHamza, M., Tehsin, S., Humayun, M., Almufareh, M. F., & Alfayad, M. (2022). A Comprehensive Review of Face Morph Generation and Detection of Fraudulent Identities. Applied Sciences, 12(24), 12545. https://doi.org/10.3390/app122412545







