1. Introduction
It is anticipated that by 2050, about 66% of the world’s population will be living in cities [
1]. The “smart city” concept focuses on ICT-based solutions to improve the everyday lives of people, government, economics, mobility, environment, and living conditions in urban areas [
2]. In a smart city, many disparate systems and services are involved in complex connections with other systems in order to provide new data-oriented intelligent functions that leverage physical and cyberspaces. Governments, institutions, and private companies are all interested in learning about the potential benefits of smart city initiatives, as they solve many of the existing issues that affect densely populated areas. Future smart cities will have more technology to facilitate and improve the quality of life of their citizens. On the technological side, smart city initiatives require systems that can support large numbers of people using a diverse range of devices. The environment of a smart city is characterized by heterogeneity, with many different systems that need to be able to interoperate with one another and efficiently accomplish their functions. The interoperability aspect in a smart city is still elusive. This is because smart cities are distributed architectures, which necessitate a certain degree of interoperability and interoperation for managing heterogeneous systems that comprise diverse platforms. The nature of smart cities necessitates this requirement. These heterogeneous systems are designed independently of one another, and each one features a unique operating system, programming platform, and tier of service.
These heterogeneous devices produce a significant amount of data on the network, thereby increasing the load on the gateways. The advancement of the internet of things (IoT) has spurred its adoption in domains like smart homes, smart cities, and related sectors, contributing to its exponential growth in recent years. Conversely, due to this development, IoT networks [
3,
4,
5,
6] are witnessing an upswing in security concerns, notably botnet attacks, often appearing as network anomalies. In a similar vein, providing security solutions proves challenging due to the limited resources accessible to devices connected to IoT networks in general. This challenge has been addressed through the utilization of the software-defined networking (SDN) computing paradigm, creating an environment that offers extra resources and adaptability for any anomaly mitigation systems.
This complexity and loading challenge can be surmounted by adopting SDN architecture for an efficient network management platform. The segregation of the control and data planes in SDN facilitates streamlined management, control, dynamic rule updates, analysis, and a broader network perspective from a centralized control point. Measurement stands out as one of the most pivotal and intricate aspects of centralized network management. The overarching objective is to identify DDoS attacks before smart city systems become inaccessible. DDoS attacks inundate a smart city device or a set of devices with a substantial number of packets, rendering them vulnerable. Smart city switches fail to identify a match if the incoming packet’s source addresses are spoofed, which is commonly the case, necessitating the transmission of the packet to the controller. There’s a possibility that the resources of the smart city controller could be depleted due to the constant processing of genuine and DDoS-spoofed packets. If the controller becomes incapable of receiving new legitimate packets, the SDN architecture might falter, rendering the controller unreachable. The use of SDN for network assessment in smart cities has been explored in various studies. Detecting DDoS attacks with speed and precision remains highly challenging. Some DDoS attackers employ packets that mimic normal traffic to disrupt the functioning of smart city systems. During a DDoS attack, the normal network conceals the traffic, leading traditional packet-based intrusion detection systems (IDS) to fail to identify it. Through the application of advanced machine learning algorithms and optimization approaches, a novel countermeasure will be devised through the monitoring and prompt identification of instantaneous network changes.
Cyber-attacks on smart cities are escalating, posing a threat to the advancements achieved in technological innovation. Smart cities are more susceptible to DDoS attacks, regardless of the nature of the targeted traffic. Smart cities that rely heavily on software-driven, complex digital networks to operate numerous city systems and services are vulnerable to cyber-attacks. When a DDoS attack is launched against a target in an SDN network, the controller triggers multiple flow entries due to the large volume of spoofed source addresses. This study addresses the following questions:
What is the best SDN framework and testbed for smart cities that can be used for evaluation?
How is the effectiveness of the anomaly mitigation schemes determined?
How is the best multiclass classification determined?
The failure of the controller can lead to the breakdown of entire or partial smart city systems. As a result, this study proposes a secure and intelligent framework based on an SDN scheme to protect smart cities from DDoS attacks.
The main goals of this work are to introduce an intelligent learning-based DDoS detection framework that mitigates the DDoS attacks on smart cities. The detailed objectives of this work can be summarized as follows:
To propose an intelligent learning-based DDoS framework for eliminating DDoS attacks on smart cities.
To improve the efficiency of the smart cities’ SDN-enabled centralized network by further enhancing the model.
To simulate the proposed framework in smart city systems for evaluation and benchmarking.
The remainder of this paper is organized as follows.
Section 2 summarizes and discusses related work on DDoS attacks in smart cities.
Section 3 describes the framework, algorithm, and features of the proposed work.
Section 4 describes the evaluation and performance metrics of the proposed framework. In
Section 5, we make final remarks and directions for future work.
2. Background and Related Work
DDoS attacks, which have been extensively studied, are among the most prevalent and serious security concerns. A variety of projects are now using SDN-based security measures to prevent such assaults. Here is a summary of some important works in this area:
Jesús et al. [
7] proposed an SDN-based solution to combat DoS and DDoS attacks in IoT networks. The solution relies on OpenState, a potential technique for network monitoring, as it does not send packets to the controller. The SDN controller can identify DoS and DDoS attacks based on their entropy levels, as has been shown. The impact of this parameter was better understood by evaluating the application’s performance in three different scenarios. The first scenario measures the attack’s bandwidth and entropy values in a generic testbed, while the second and third scenarios are more focused on IoT scenarios. According to the experimental findings, an attack can be detected by comparing the entropy levels of different aspects. Chuanfeng et al. [
8] presented a method for improving DDoS protection and data management security in SDN-enabled smart cities. A DDoS attack defense approach based on traffic classification was presented in this paper. The authors used a software-defined network function, virtualization design, and traffic categorization approach to improve SDN flexibility and load against DDoS attacks. According to the experimental results, the suggested approach can not only identify DDoS attacks quickly, but it can also correctly pinpoint the origins of DDoS attacks. As a result, SDN controllers are less vulnerable to attack, and the system is more efficient.
Da et al. [
9] used the SDx paradigm to propose an overall framework for software-defined internet of things (SD-IoT). The controller pool in the proposed system consists of SD-IoT controllers, switches connected to an IoT gateway, and IoT devices. Researchers developed a method for identifying and mitigating DDoS attacks using the SD-IoT architecture. The similarity measured by the cosine of the packet message rates at the boundary SD-IoT switch ports is employed in the algorithm to assess whether DDoS attacks are present in the IoT. Experiments conducted in this study demonstrate that the suggested algorithm performs well and that the proposed framework can be easily adapted to increase IoT security for diverse and susceptible devices. Narmeen et al. [
10] proposed an efficient DDoS attack detection system based on DDoS detection techniques. According to the findings provided in this work, DDoS attacks may be detected and mitigated in a large-scale network that includes a smart city based on SDN architecture. This framework can meet all DDoS attack detection and mitigation requirements. This study first surveys and classifies SDN-based DDoS attack identification and resolution systems based on the detection approach. Second, the authors presented an SDN-based DDoS Framework, which utilizes the SDN’s properties for network security. Applications for smart cities may be secured with the framework presented here.
Application identification in network architecture has been advocated by Suh et al. [
11]. This can help to prevent distributed denial-of-service (DDoS) attacks by restricting data flow. YuHunag et al. [
12] proposed a DDoS attack identification technique that relies on network traffic statistics. The controller monitors the amount of traffic and the frequency of specific events that are associated with DoS attacks. Braga et al. [
13] introduced a technique based on self-organizing maps. Researchers have developed a way to detect fraudulent internet patterns using this method. Zhang et al. [
14] discussed the current state of prior network behavior and analysis. They developed a flow count identification technique for anomaly detection. This approach can be used to detect anomalous traffic flows that are associated with DDoS attacks. In another work, the authors compared the known testbeds to the one that is used to create the IoT-Bot dataset, which is a simulated network environment that simulates real-world traffic [
15].
A variety of datasets have been presented in the literature to assist researchers in modeling botnet operations and generating attack traffic statistics [
16,
17,
18,
19]. These datasets were generated using a variety of testbeds. Alomari et al. [
17] built the DDoS Botnet traffic testbed using a high-tier server and virtual machine. The number of bots in their testbed was larger, but their produced botnet activities were restricted to HTTP DDoS attacks exclusively. They did not use machine learning algorithms. The data generated by this network testbed was intended to provide evidence of malicious activity on the internet. However, it is difficult to verify any results due to the lack of comprehensive network packet capture. The amount of data that can be retrieved and analyzed is also limited by network traces.
Bhatia et al. [
19] built their testbed using real devices connected to a local network in a different way. They used Botloader and IP-Aliasing, two pieces of specialist software, to replicate flash events and other DDoS attacks on their testbed. The decision to use physical computers instead of a virtualized testbed has some drawbacks. It is more expensive, more difficult to install, and does not offer the same level of robustness as a virtualized environment. However, their methodology also encompasses a wider range of botnet operations, including port scanning using machine learning methods. In another study, Sharafaldin et al. [
20] developed two independent testbeds based on physical computers. One testbed was for the network of the victim, and the other was for the network of the attacks. The authors chose to use the Ubuntu/Kali Linux platform for malware detection, and they used a wide range of popular operating systems in their approach. Moustafa et al. [
15] built their UNSW-NB15 dataset using IXIA’s Perfect Storm testbed to create both normal and malicious network traces. The researchers used IXIA to set up three virtual servers, two of which generated regular traffic and the third of which carried out attacks on the other two. Most of the existing work in this area has been addressing DoS/DDoS and IoT. However, there are fewer works that address the applicability of SDN to smart cities.
Jagtap et al. [
21] proposed a novel intrusion detection and prevention system to prevent DDoS attacks. The authors introduced a long short-term memory (LSTM) and graded rated unit (GRU) deep learning model as the “block–attack” model, where the LSTM and GRU contribute to enhancing the rate of accuracy in detecting DDoS attacks in an SDN environment. They used the CICDDoS2019 dataset for the experiments. They achieved 98.5% accuracy in detecting and preventing the DDoS attacks and 95.5% accuracy for the SVM-based method.
Recently, Negera et al. [
22] introduced a lightweight model for botnet attack detection in software-defined network-orchestrated IoT. The aim of this model is to enhance the security framework of IoT by harnessing the capabilities of IoT devices to efficiently thwart botnet malware attacks. By dynamically allocating computational resources, the model achieves rapid response times. Notably, empirical evaluation showcases the model’s exceptional performance, yielding remarkable metrics such as 99% precision, recall, and F1 score, in conjunction with an impressive accuracy rate of 99.4%. Furthermore, the model’s size, a mere 118 KB, coupled with its minimal parameter count of 19,414, contributes to its agile execution time of a mere 0.108 milliseconds. A comparative analysis of the existing work is presented in
Table 1.
3. Proposed SDN Simulation Framework
The proposed SDN simulation framework for smart cities is shown in
Figure 1. The framework has three layers: the infrastructure layer, the secure and intelligent SDN layer, and the service layer. The suggested architecture enables diverse networks that include IoT devices, RFID, WSN, ZigBee, sensors, and other network devices. The infrastructure layer includes both the IoT devices and the forwarding devices. The IoT devices, such as RFID, ZigBee, sensors, and WSN, create a variety of IoT applications suitable for smart cities. These wireless devices collect massive volumes of network data, which are then sent to an SDN-based smart city controller for processing. The forwarding devices sublayer consists of MQ telemetry transport (MQTT) gateways, which make it easier for the SDN controller to receive control and data packets. The secure and intelligent SDN layer consists of the global and local SDN controllers. The global SDN controller is responsible for controlling and monitoring communications between the global control center and the IoT application domains. The local SDN controller manages and monitors the communications within an application domain. The service layer makes IoT services possible through the use of SDN controllers. It also provides network services such as routing, security, and quality of service throughout the city. The control plane, which is the low-level details of the configuration and operation of typical network devices such as switches and routers, is traditionally dependent on the operating system of the device in question. This can make it difficult and time-consuming to dynamically reconfigure a network.
SDN is intended to address this issue, according to the article [
23], by the idea of separation of control and data planes, which will allow for software-based device design, as seen in
Figure 1. As a result of these principles, a software-based element may be used to operate and configure the network, providing all accompanying benefits, such as dynamic control. Using a logically centralized controller, network performance may be monitored and dynamically adjusted.
3.1. Feature Space and Classification Model
The proposed test framework has three major components: the network platform, the simulated IoT services, and the feature extraction and attack analysis. The network platform consists of both normal and malicious virtual machines, including a firewall. The simulated IoT services include certain IoT services that sense the data in the network. The Node-RED tool [
24] is used to represent the flow model of MQTT. Node-RED is a flow-based visual programming tool built on NodeJS, which is commonly used in IoT system development. Developers have the freedom to use Node-RED in a variety of ways, and the same system can be constructed in a variety of methods. The BoT-IoT dataset [
25] has been used to obtain the data features. The XGBoost methods were then used to analyze the feature vectors to differentiate between normal and abnormal cases. The packets are collected using the pcap utility to produce the required network flow. The extracted features from the network flow, as shown in
Table 2, are stored in the database.
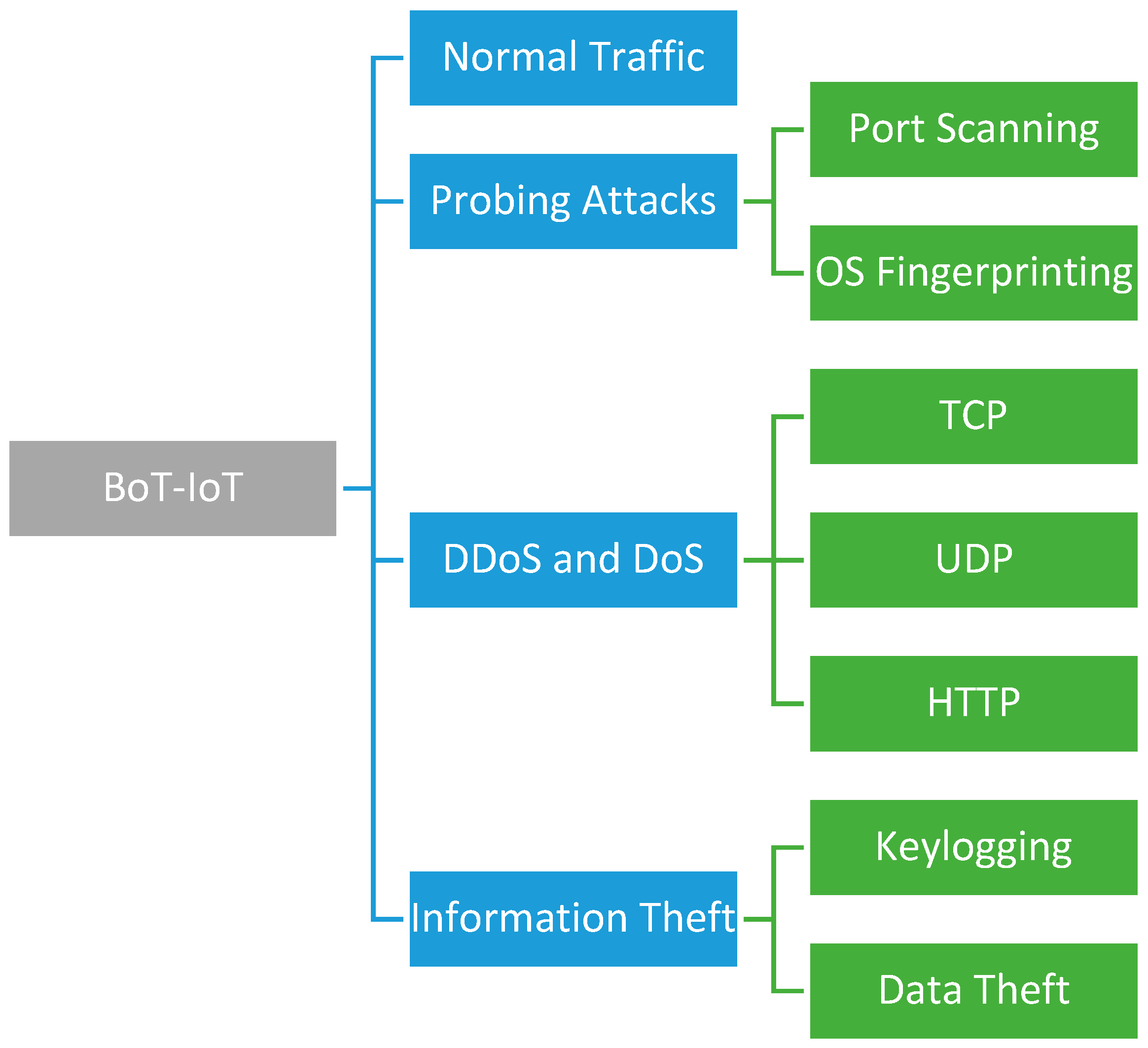
The BoT-IoT dataset is a composition of normal traffic, probing attacks, DDoS and DoS attacks, and information theft, as shown in
Figure 2. The normal traffic consists of legal network transactions. Virtual machine traffic flows are included in the data collection. The probing attack, also known as an information-gathering attack, is carried out by malicious individuals who use scanning or fingerprinting techniques to illegitimately obtain data from remote computers. Port scanning and OS fingerprinting are two forms of probing attacks found in the BoT-IoT dataset. In a DdoS attack, a malicious user overwhelms resources or services with invalid requests. Botnets, which are collections of hacked nodes on the network, are often used to carry out these attacks. The dataset includes HTTP, TCP, and UDP DdoS attacks.
While attackers can use an information theft attack to gain access to sensitive or secret information, malevolent users may also use it. Data theft and keylogging are two types of information theft attacks in the dataset. The BoT-IoT data collection contains 9543 legitimate instances and 73,360,900 non-legitimate traffic flow instances. In this experiment, only 740,637 randomly selected examples were used. However, the retrieved instances include all forms of attacks, except for theft attacks, which have a negligible number in the BoT-IoT dataset.
To validate the proposed model, a typical smart parking configuration was selected using ten simulated IoT devices. The Node-RED root is used to establish the connection between smart devices and Amazon Web Services (AWS) that generate normal traffic using the MQTT protocol. MQTT was created to connect devices in remote locations where there is not much network bandwidth or where a “small code footprint” is required. It is a good choice for wireless networks with varying levels of latency due to sometimes limited bandwidth or unreliable connections.
MQTT started as an IBM-owned protocol that was used to communicate with SCADA systems in the Oil and Gas industry. It is now an open-source protocol that is run by the Organization for the Advancement of Structured Information Standards (OASIS). The MQ in MQTT stands for “message queuing,” but in MQTT communication, there is no longer any message queuing. The protocol now has publish-and-subscribe messaging, and smart automation systems are using it more and more. Today, MQTT is one of the most popular open-source protocols used in fog and edge computing and to connect the internet of things (IoT). Aside from MQTT, there are other well-known messaging protocols that IoT applications can use.
The gradient-boosted tree (GBT) approach is categorized as supervised learning based on the approximation method through the optimization of certain loss functions as well as the use of multiple regularization strategies [
27]. In our analysis, we are looking for a function that can improve the performance of the proposed model. Therefore, loss function
becomes a good indicator of how accurate our model’s predictions are. If the prediction results
are close to the actual values
, then the loss will be the smallest, and if the predictions are completely off from the original values, then the loss will be the greatest. The loss can be defined by using Equation (1).
Based on the value of
, the model is iterated for update until the best result is achieved. To obtain the classification, the binary cross-entropy (Log loss) has to be employed. In XGBoost, we have many numbers of trees [
23,
24]. Let us assume that we have
trees, then the prediction model can be defined as
. The
represents the prediction of the decision. We create predictions using all decision trees that we have, as shown in Equation (2):
The
represents the feature vector for the data point
. We can also define the prediction using this model at any step
, as shown in Equation (3).
We must optimize the loss function in order to train the model. For binary classification, we use LogLoss, as shown in Equation (4).
The multiclassification can be represented as shown in Equation (5):
where
represents the total rows, and
is the collection of classes. The objective function consists of a loss function and regularization at the iteration
that has to be minimized. We can define the objective function of XGBoost by Equation (6) [
27].
The simple approximation function can be computed by Equation (7). The
represents the loss function
, while
is the predicted value obtained from the previous step
. The
is defined as a new learner in this context for iteration
. Now, applying the second-order approximation, Equations (8) and (9) can be obtained as follows.
where
), and
).
To generalize the above equation, the constant parts can be removed, as shown in Equation (10).
Equation (10) is the sum of quadratic functions that has one variable, which can be minimized further, as shown in Equations (11) and (12).
3.2. Simulated Attack Model
To simulate the attack model, we deployed six virtual machines with the Kali Linux operating system to generate a botnet-simulated attack model, as shown in
Figure 3. In this work, we modeled denial-of-service (DoS) attacks [
17,
24,
26,
27,
28] that can disrupt normal service and make it unavailable to users. The virtual machines act as bots to target remote servers or machines. The attack can be identified by the large volume of data generated, which can prevent legitimate users from accessing the service. Additionally, the attack can crash the system by increasing the request load, making the provided service unavailable. This type of attack can also be carried out through a protocol that abuses the working of the internet protocol (IP) to deplete the computing resources of the target machines so that they cannot respond to requests from legitimate users. To set up the test scenario, TCP, UDP, and HTTP were used.
4. Results and Discussion
Anomaly mitigation schemes must be tested to ensure their effectiveness. Evaluating a plan helps to determine its effectiveness. Therefore, it is necessary to use a structured dataset that effectively represents the environmental trace flow characteristics in which the model will be implemented, as this cannot be achieved on a real-world network. The BoT-IoT dataset provides an appropriate setting for traffic flow in a connected IoT environment, so we will use it for this purpose [
26]. The dataset contains both real and simulated IoT traffic, as well as threats. The dataset was created on an IoT testbed using feature extraction methods and network platforms. Virtual machines were used to generate valid and malicious traffic on the network platforms. The MQTT protocol is used to simulate smart city network traffic [
29]. A temperature sensor station, humidity sensor, CO2, and smart lights are some of the scenarios simulated. Fourteen new features were derived from the thirty features to improve the predictive power of the classifiers that will be used. The BoT-IoT consists of normal traffic, probing attacks, DDoS, and information theft. The BoT-IoT contains 9543 instances of legitimate traffic flow, while it has 73,360,900 illegitimate instances. However, only 740,637 cases were randomly selected for this simulation. The theft attacks, which are negligible, are not included in the extracted occurrences. As illustrated in
Figure 4, the model’s performance is evaluated using the confusion matrix to quantify the accuracy of its predictions.
The performance of the model can be accessed through metrics such as accuracy, detection rate, false-positive rate, false-negative rate, F1 score, etc. We will present a brief definition of these metrics.
Accuracy: This is the measure of all positive classifications of all instances in the dataset of an intrusion detection system that can be derived as follows:
where
represents the total negative classified instances,
represents the positive classified instances,
represents false-positive classified, and
represents false-negative classification of the data.
Detection Rate (DR): The true-positive rate (TPR) is the number of properly recognized malicious observations to the total number of malicious observations in the dataset, which can be derived as follows:
False-Positive Rate (FPR): This is the percentage of normal observations to the total number of normal data that are incorrectly labeled as attacks:
False-Negative Rate (FNR): An attack’s misclassification rate, which is also known as precision, is calculated as follows:
F1: Recall and accuracy may be weighted averaged to calculate F1 using the formula:
To see how well it stacks up with existing classification algorithms, k-fold cross-validation tests validate that the XGBoost classifier performs supervisor decision tree, k-nearest neighbor, naïve Bayes, and gradient boosting.
In the 10-fold cross-validation procedure, a random number generator divides the dataset into ten equal pieces. Only a component of the split dataset is used for each assessment, and the remaining portions of the dataset are used for training purposes. Once for each segment of the partitioned dataset, the procedure is repeated to obtain superior results. The ratio of features in the dataset and the ratio of the training instances have been balanced to avoid overfitting. It ensures low variance and bias, as well as the avoidance of overfitting. In light of the dataset’s asymmetry in terms of instances of traffic flows, the classifiers are evaluated in terms of the entire classification report, rather than on individual instances. The classifier’s classification capability will be captured this way, allowing us to categorize distinct instances of binary classification (normal and attack instances), multiclass classification, and port scan. The classification report contains information on the accuracy, precision, recall, and F1 score.
Regarding detection accuracy, all classifiers achieved a satisfactory level of success, with XGBoost achieving the highest level of success and NB achieving the lowest level of success. Conversely, the XGBoost classifier achieved the lowest false-positive rate (FPR) with a value of 0.06, as shown in
Table 3. This demonstrates that it is able to categorize network traffic cases with the lowest possible number of false positives. A detailed performance analysis of the multiclass classification performance is shown in
Appendix A.
Figure 5 depicts the performance of the classifiers in binary classes, such as normal and attack examples, which provides a better insight into the classifier’s performance. The XGBoost classifier outperformed the other classifiers in terms of average recall, F1 score, and precision. It is possible to have a better understanding of how well the classifiers work by looking at the average performance of the binary classifiers in two classes. With respect to average recall accuracy and F1 score, the XGBoost classifier is found to be superior to other classifiers.
Figure 6 shows the classification accuracy for multiclass classification. A high percentage of attacks are detected by all classifiers in multiclass classification, where the performance is similar to the binary class classification. The k-NN and NB classifiers have the lowest detection accuracy for TCP, UDP, OS fingerprinting, and keylogging. Both the XGBoost and DT produced similar findings; however, the XGBoost had the best detection accuracy for both attack and nonattack.
The precision of the classifiers in multiclass classification is presented in
Figure 7. In all attacks and typical cases, the XGBoost, GRB, and DT classifiers attained a precision of between 84 and 99.99. The naïve Bayes and k-NN have obtained a precision of 5–72 percent in all types of attack and normal instances, excluding the exception of DDoS TCP attacks, where naïve Bayes has reached a precision of 82.1 percent, and keylogging attacks, where k-NN achieved a precision of 98.7.
A multiclass classification system, except for keylogging attacks and normal cases, achieved recalls of 83–100% in all attacks and normal cases, respectively, in
Figure 8, depicting the results of the multiclass classification system. There was a negligible difference in recall value between the two methods, except in the case of keylogging attacks (NB reported an 86% rate of recall).
Regarding attacks and regular situations, classifiers such as the XGBoost, GRB, and DT classifiers all earned F1 scores of 82–100%, whereas NB and k-NN only received F1 scores of 4–70% in all but OS fingerprinting assaults, when k-NN scored an impressive 88%, as shown in
Figure 9.
The proposed model is compared with the existing work, as shown in
Figure 10. In the reinforced learning approach, the random forest method [
8] is applied, which has obtained an accuracy of 99.54%. In another work, the authors have applied ANN to obtain a high accuracy of 99.84% in the SDN environment. In our proposed work, we obtained slightly better than the existing work [
8], which is 99.9%, as shown in
Figure 10.
5. Conclusions
The heterogeneity and interoperability requirements must be met when designing a smart city application. These stringent requirements must be met by all smart city components, including devices, network equipment, vendor-proprietary software, communication technologies and protocols, and a variety of other smart services and smart city applications. SDN has emerged as a possible resilient future internet architecture in recent years. Numerous recent studies have shed light on how SDN can be used to improve the resilience and security of communication networks in smart cities. This work conducted a comprehensive and in-depth study to explain the essentials of SDN from the resilience perspective, followed by a proposal of a secure and intelligent framework. XGBoost achieved an accuracy of 99.99%, a precision of 97%, a recall of 99%, an F1 score of 98%, and an FPR of 0.05 using binary classification. In multiclass classification, the average accuracy was 99.29%, precision 97.7%, recall 96.69%, and F1 score 97.51%.
In our future work, we will explore and try the DDoS attack on high-performance targets.