Enhancing Urban Public Safety through UAS Integration: A Comprehensive Hazard Analysis with the STAMP/STPA Framework
Abstract
:1. Introduction
- To identify and analyze the potential hazards and challenges associated with integrating UAS into public safety/law enforcement systems in urban environments.
- To develop a comprehensive set of safety requirements and guidelines for the safe and effective deployment of UAS in public safety missions.
- To propose strategies for efficient infrastructure investment and resource allocation based on STAMP/STPA results.
2. Methods
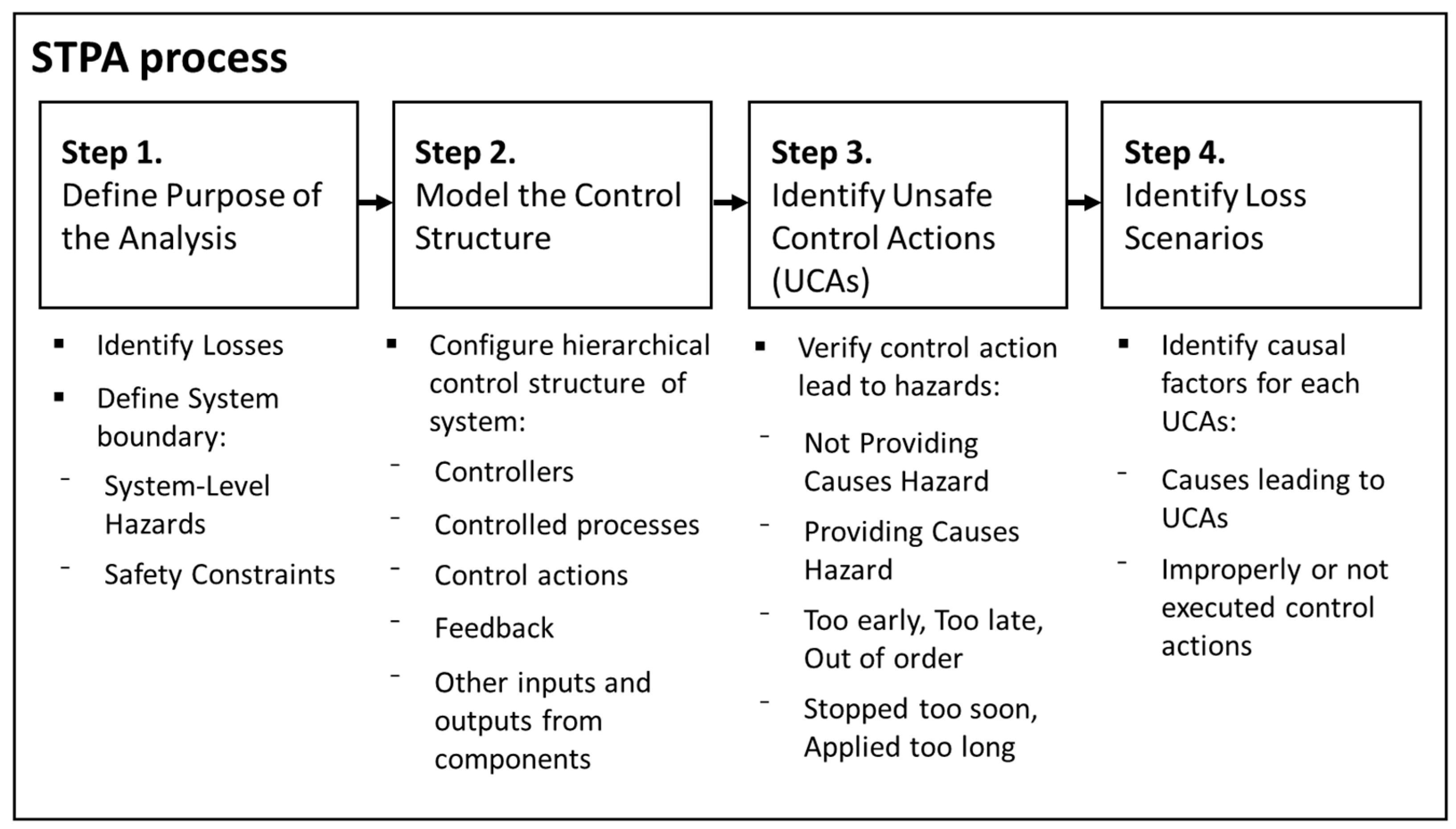
2.1. STAMP/STPA
- Safety constraints define the boundaries of safe system behavior. Accidents result from inadequate control and violation of these constraints.
- Complex systems are viewed as hierarchical control structures, where each level enforces safety constraints on the level below it.
- Control loops consisting of controllers, actuators, sensors, and controlled processes are the building blocks of the hierarchical control structure.
- Controllers must have accurate process models reflecting the state of the controlled processes. Flawed process models and inadequate feedback can lead to accidents.
- Continuous adaptation through feedback is necessary to cope with changes and maintain safety.
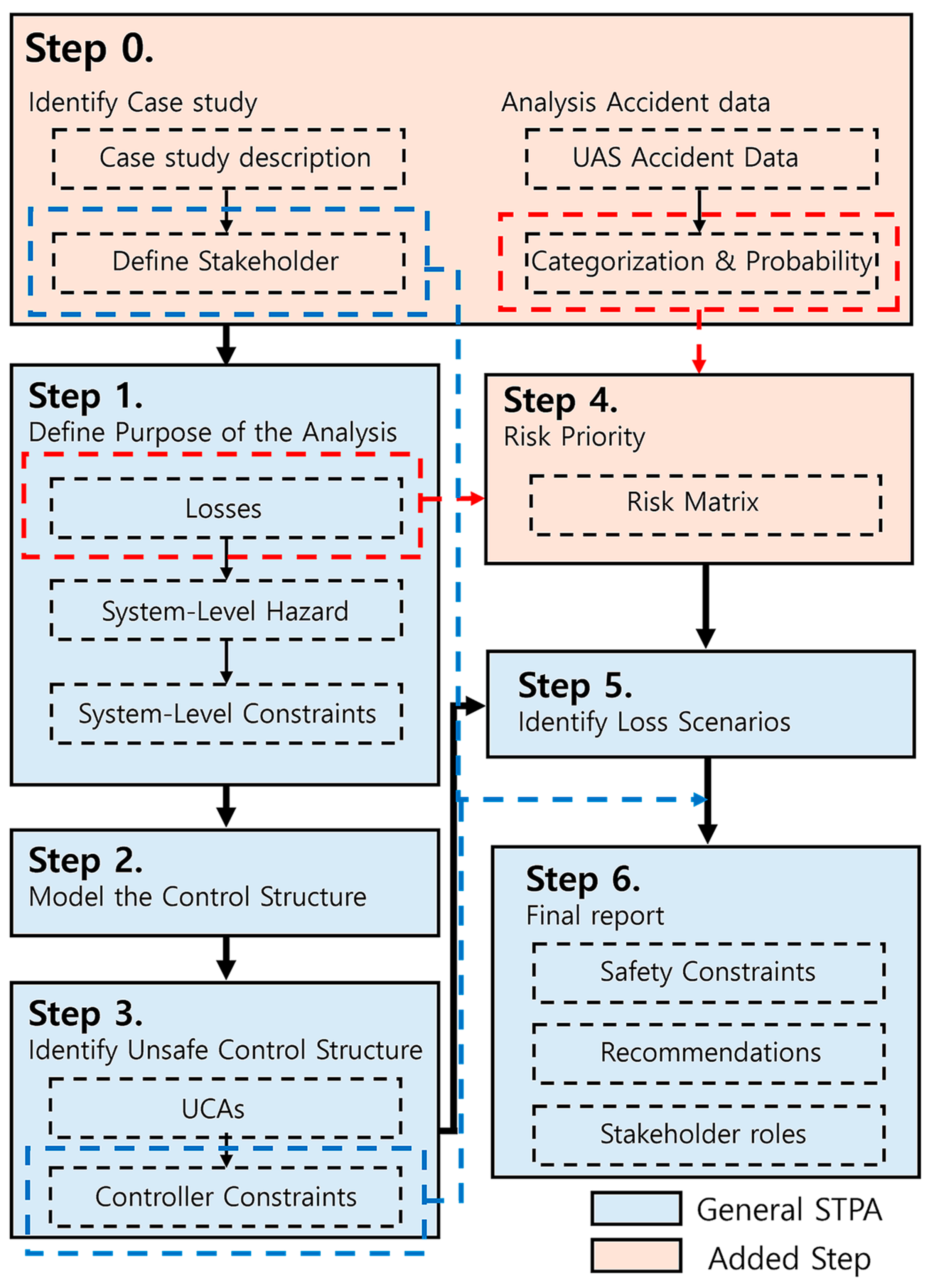
2.2. STAMP/STPA-Based Framework for UAS Integration in Public Safety
3. Results
3.1. Step 0: Identify Case Study and Analysis Accident Data
3.1.1. Case Study Description
3.1.2. Define Stakeholder
3.1.3. UAS Accident Data
3.1.4. Categorization and Probability
- Human Factors: 246 cases (Pilot error, inadequate training, fatigue, loss of situational awareness, etc.)
- Hardware: 80 cases (Mechanical failures, structural defects, engine malfunctions, loss of power, etc.)
- Procedure/Policy: 53 cases (Non-compliance with regulations, lack of standard operating procedures, etc.)
- Environment/Weather: 28 cases (Strong winds, turbulence, icing, bird strikes, etc.)
- Software: 22 cases (Autopilot glitches, navigation errors, software bugs, etc.)
3.2. Step 1: Define the Purpose of the Analysis
- SSC-1: UAS must be operated in a manner that does not harm people or property [H-1]
- SSC-2: UAS must be operated in authorized or unrestricted airspace [H-2]
- SSC-3: UAS must maintain safety distance during surveillance missions [H-3]
- SSC-4: UAS operations must not exacerbate emergency situations [H-4]
- SSC-5: UAS must maintain communication integrity under all operating conditions [H-5]
- SSC-6: UAS operations must not interfere with or degrade the effectiveness of emergency response [H-6]
3.3. Step 2: Model the Control Structure
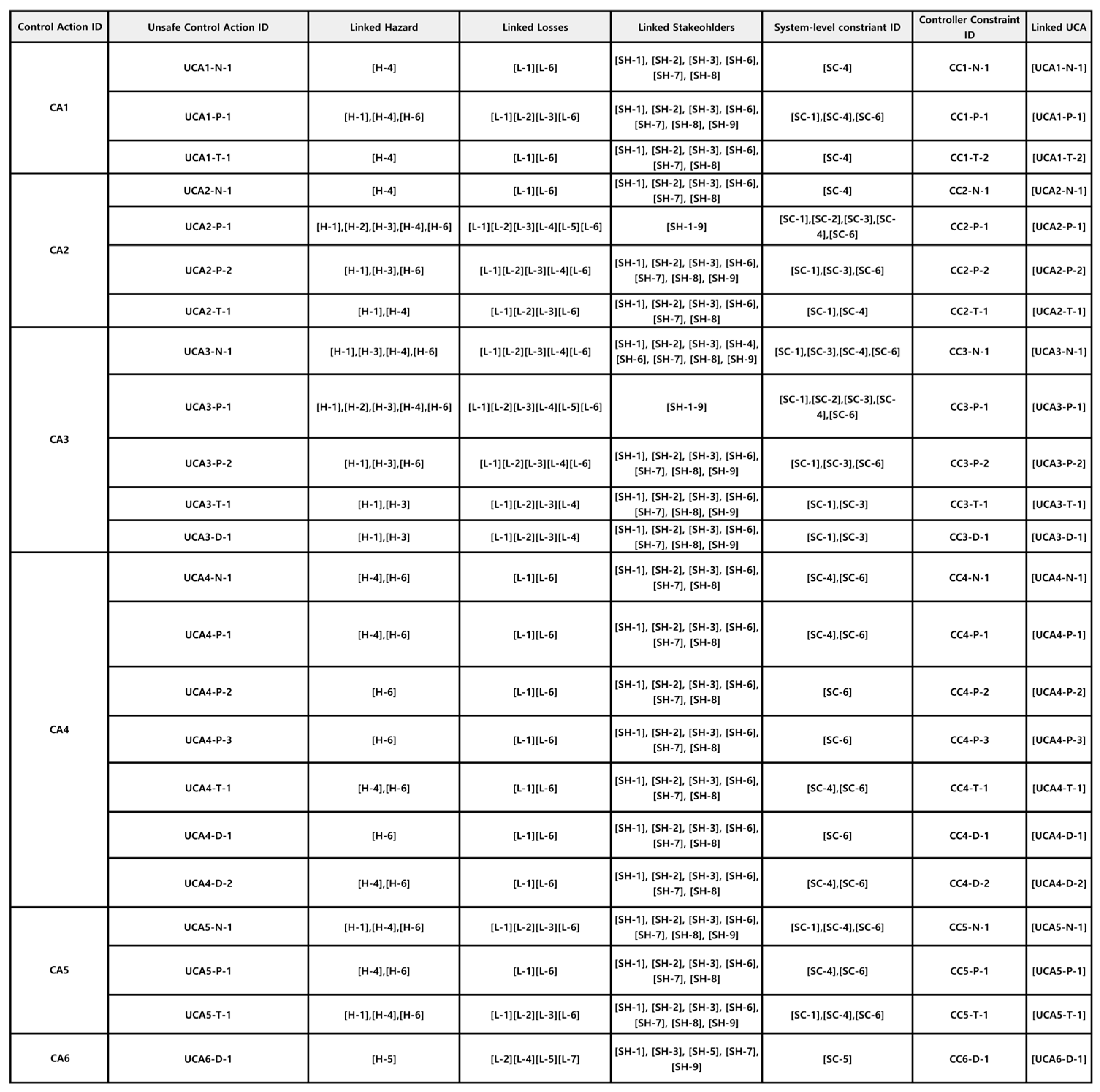
3.4. Step 3: Identify Unsafe Control Actions
- (1)
- Necessary control actions for safety are not taken or properly followed (occurring when required actions are omitted or ignored)
- (2)
- Control actions are taken when not needed (meaning controls are applied at inappropriate times)
- (3)
- Potentially safe control actions are taken too late, too early, or not in the correct sequence (happening when timing or sequence is incorrect)
- (4)
- Safe control actions are stopped too soon or continue for too long (problems with continuous or discontinuous control actions).
- CC1-N-1: Ensure that the GCS Administration Module always has the capability to provide GCS control. [UCA1-N-1]
- CC1-P-1: Implement validation and verification checks to ensure that the GCS control provided is correct. [UCA1-P-1]
- CC1-T-1: Establish timely responsiveness in the GCS control provision process to prevent delays. [UCA1-T-1]
- CC2-N-1: Ensure GCS always has the capability to provide UAV Flight Commands. [UCA2-N-1]
- CC2-P-1: Implement validation and error checking in the UAV Flight Command issuance process. [UCA2-P-1]
- CC2-P-2: Disable UAV Flight Command capabilities during abort/return flight unless specifically required under safe conditions. [UCA2-P-2]
- CC2-T-1: Implement real-time monitoring and alerts to ensure timely command delivery. [UCA2-T-1]
- CC3-N-1: Ensure ACM always provides necessary UAV direction and speed controls. [UCA3-N-1]
- CC3-P-1: Validate and calibrate UAV direction and speed controls to prevent incorrect control actions during flights. [UCA3-P-1]
- CC3-P-2: Prevent the ACM from altering UAV direction and speed during abort/return flight unless necessary. [UCA3-P-2]
- CC3-T-1: Ensure ACM controls are responsive and timely during active flights. [UCA3-T-1]
- CC3-D-1: Ensure ACM does not cease control prematurely and maintains functionality until the safe completion of the flight. [UCA3-D-1]
- CC4-N-1: Ensure GCS is always capable of issuing Danger Situation Alerts during emergencies. [UCA4-N-1]
- CC4-P-1: Validate the correctness of Danger Situation Alerts commands to ensure they are appropriate for the actual emergency situations. [UCA4-P-1]
- CC4-P-2: Implement checks to prevent the issuance of Danger Situation Alerts when no emergency is present. [UCA4-P-2]
- CC4-P-3: Introduce lifecycle management for speaker components with proactive replacements. [UCA4-P-3]
- CC4-T-1: Ensure timely delivery of Danger Situation Alerts to prevent late responses in emergencies. [UCA4-T-1]
- CC4-D-1: Configure GCS to cease Danger Situation Alerts once an emergency is adequately resolved. [UCA4-D-1]
- CC4-D-2: Ensure that Danger Situation Alerts are not discontinued prematurely during ongoing emergencies. [UCA4-D-2]
- CC5-N-1: Ensure that OMS is always capable of reporting dangerous situations. [UCA5-N-1]
- CC5-P-1: Implement accuracy checks in the reporting mechanism to ensure correct reporting of dangerous situations. [UCA5-P-1]
- CC5-T-1: Enhance the timeliness of the OMS’s danger reporting system to ensure prompt alerts. [UCA5-T-1]
- CC6-D-1: Set appropriate limits on the duration of the CCTV video requested by the OMS to avoid excessive demands. [UCA6-D-1]
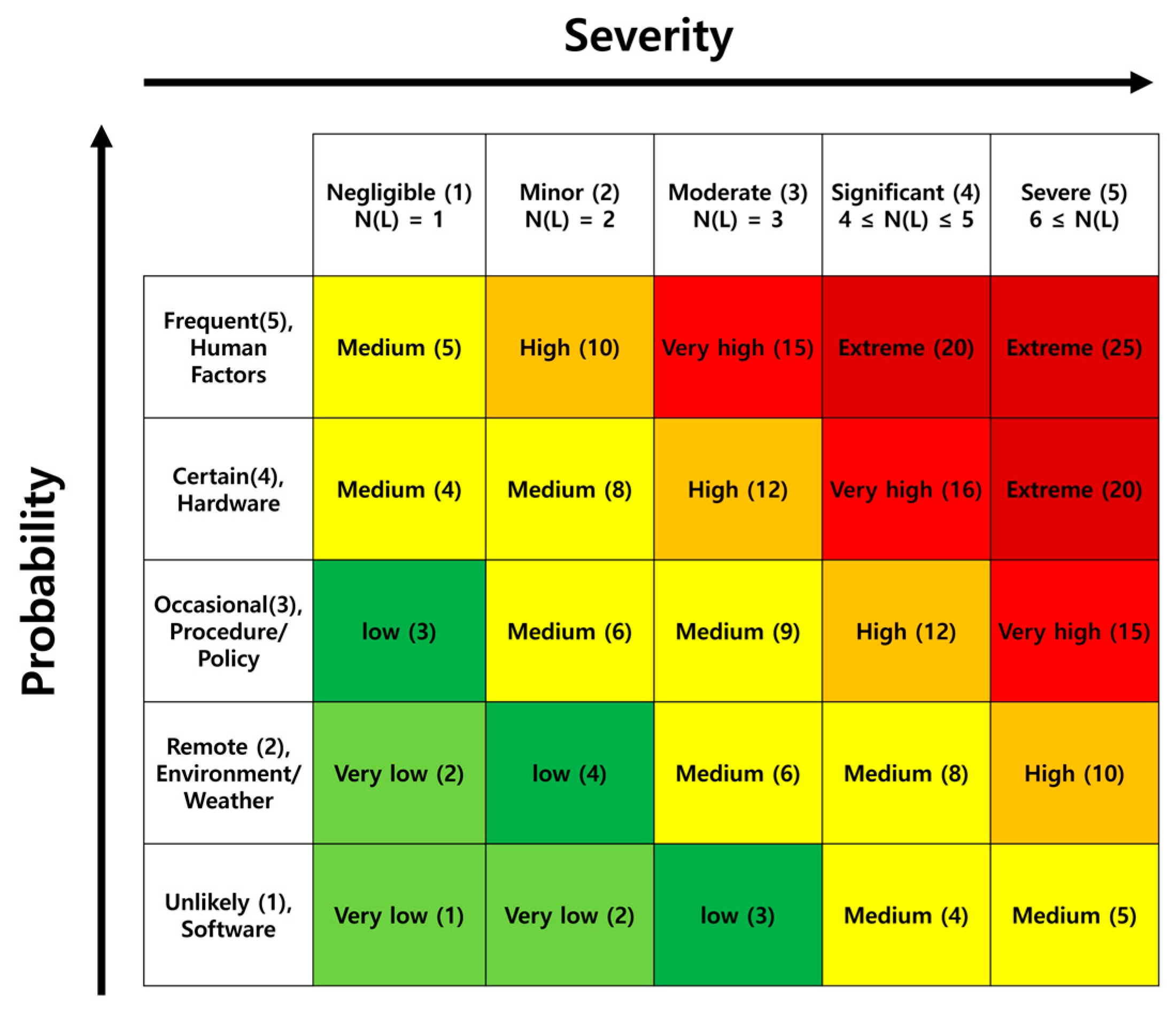
3.5. Step 4: Risk Priority
3.6. Step 5: Identify Loss Scenarios
- What could go wrong with the control loop components (controllers, actuators, sensors, etc.)?
- What might cause the controllers to have incorrect or incomplete information about the system?
- How could the control actions be applied in the wrong way or at the wrong time?
3.7. Step 6: Final Report
- SC1-P-1-1: External information such as weather, geography, and flight restriction zones must be accurate and updated in real time to ensure correct GCS control commands are generated.
- Implement an automated system for collecting and updating external information in real time.
- Establish a dedicated team responsible for verifying and validating external information.
- Develop a protocol for handling discrepancies or inconsistencies in external information.
- SH-1: Local Government and Municipal Authorities
- Provide funding and resources for implementing the recommended automated systems, dedicated teams, and protocols (SC1-P-1-1a,b,c)
- Establish policies and guidelines for setting mission priorities and goals (SC1-P-1-4a)
- Facilitate coordination between relevant departments for smooth communication and cooperation (SC1-P-1-8a,b,c)
- SH-2: Emergency Service Agencies (Fire Departments, Emergency Medical Services, etc.)
- Participate in joint training and simulations to practice detecting and responding to changes in GCS status (SC1-P-1-11c)
- Collaborate with the UAS team to establish clear communication channels and protocols (SC1-P-1-7b)
- Provide input on mission objectives and situational changes to keep OMS administrators informed (SC1-P-1-7c)
- SH-3: Department Personnel (Administrator, Pilot, Manager, etc.)
- Undergo comprehensive training and certification on command entry, manipulation processes, and interpreting GCS status information (SC1-P-1-6a, SC1-P-1-10a)
- Adhere to standardized communication protocols and participate in joint training to improve communication and cooperation skills (SC1-P-1-8a,c)
- Regularly review and validate the GCS Administration Module’s algorithms and decision-making logic (SC1-P-1-3c)
- SH-6: Other Government Agencies (urban planning, transportation, public safety, etc.)
- Provide data and information for updating external information in real-time (SC1-P-1-1a)
- Collaborate in developing guidelines and criteria for setting mission priorities and goals (SC1-P-1-4a)
- Assist in establishing data exchange protocols and compatibility testing for interfaces with external systems (SC1-P-1-5a,c)
- SH-7: Media
- Disseminate accurate information to the public about the UAS operation’s safety measures and benefits (SC1-P-1-7a)
- Serve as a communication channel between the UAS team and the public during emergencies.
- Help build public trust and understanding of UAS operations through responsible reporting.
- SH-8: Citizens
- Provide feedback and report inconsistencies in external information (SC1-P-1-1c)
- Cooperate with UAS operations and comply with instructions from relevant agencies during emergencies.
- Express concerns or provide feedback related to UAS operations to help identify areas for improvement.
- SH-9: Technology Providers
- Develop and update video analysis algorithms to enhance accuracy and reliability (SC1-P-1-2a)
- Provide technical support for implementing automated systems, data validation, and error-checking mechanisms (SC1-P-1-1a, SC1-P-1-5b, SC1-P-1-6b)
- Offer training and support services for UAS technology users (SC1-P-1-6a, SC1-P-1-10a)
4. Discussion
- To identify and analyze the potential hazards and challenges associated with integrating UAS into public safety/law enforcement systems in urban environments.
- To develop a comprehensive set of safety requirements and guidelines for the safe and effective deployment of UAS in public safety missions.
- To propose strategies for efficient infrastructure investment and resource allocation based on STAMP/STPA results.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- United Nations. The World’s Cities in 2018; United Nations: New York, NY, USA, 2018.
- Kuddus, M.A.; Tynan, E.; McBryde, E. Urbanization: A problem for the rich and the poor? Public Health Rev. 2020, 41, 1. [Google Scholar] [CrossRef]
- Henderson, J.V. Chapter 24 Urbanization and Growth. In Handbook of Economic Growth; Elsevier: Amsterdam, The Netherlands, 2005; Volume 1. [Google Scholar]
- Mattson, J. Relationships between Density and per Capita Municipal Spending in the United States. Urban. Sci. 2021, 5, 69. [Google Scholar] [CrossRef]
- Liddle, B. Urbanization and Inequality/Poverty. Urban. Sci. 2017, 1, 35. [Google Scholar] [CrossRef]
- Ha, N.M.; Le, N.D.; Trung-Kien, P. The Impact of Urbanization on Income Inequality: A Study in Vietnam. J. Risk Financ. Manag. 2019, 12, 146. [Google Scholar] [CrossRef]
- Cabrera-Barona, P.F.; Jimenez, G.; Melo, P. Types of crime, poverty, population density and presence of police in the metropolitan district of Quito. ISPRS Int. J. Geo-Inf. 2019, 8, 558. [Google Scholar] [CrossRef]
- Welsh, B.C.; Farrington, D.P. Science, politics, and crime prevention: Toward a new crime policy. J. Crim. Just 2012, 40, 128–133. [Google Scholar] [CrossRef]
- Engberts, B.; Gillissen, E. Policing from Above: Drone Use by the Police; T.M.C. Asser Press: The Hague, The Netherlands, 2016. [Google Scholar]
- Welsh, B.C.; Farrington, D.P. Making Public Places Safer: Surveillance and Crime Prevention; Oxford University Press: Oxford, UK, 2009. [Google Scholar]
- Yeganegi, K.; Moradi, D.; Obaid, A.J. Create a wealth of security CCTV cameras. J. Phys. Conf. Ser. 2020, 1530, 012110. [Google Scholar] [CrossRef]
- Welsh, B.C.; Farrington, D.P. Effects of Closed Circuit Television Surveillance on Crime. Campbell Syst. Rev. 2008, 4, 1–73. [Google Scholar] [CrossRef]
- Mohsan, S.A.H.; Othman, N.Q.H.; Li, Y.; Alsharif, M.H.; Khan, M.A. Unmanned aerial vehicles (UAVs): Practical aspects, applications, open challenges, security issues, and future trends. Intell. Serv. Robot. 2023, 16, 109–137. [Google Scholar] [CrossRef]
- Kim, H.; Mokdad, L.; Ben-Othman, J. Designing UAV Surveillance Frameworks for Smart City and Extensive Ocean with Differential Perspectives. IEEE Commun. Mag. 2018, 56, 98–104. [Google Scholar] [CrossRef]
- Mohd Daud, S.M.S.; Mohd Yusof, M.Y.P.; Heo, C.C.; Khoo, L.S.; Chainchel Singh, M.K.; Mahmood, M.S.; Nawawi, H. Applications of drone in disaster management: A scoping review. Sci. Justice 2022, 62, 30–42. [Google Scholar] [CrossRef] [PubMed]
- Mohsan, S.A.H.; Khan, M.A.; Noor, F.; Ullah, I.; Alsharif, M.H. Towards the Unmanned Aerial Vehicles (UAVs): A Comprehensive Review. Drones 2022, 6, 147. [Google Scholar] [CrossRef]
- Coldren, J.R.; Huntoon, A.; Medaris, M. Introducing Smart Policing: Foundations, Principles, and Practice. Police Q. 2013, 16, 275–286. [Google Scholar] [CrossRef]
- Klauser, F. Police Drones and the Air: Towards a volumetric geopolitics of security. Swiss Polit. Sci. Rev. 2021, 27, 158–169. [Google Scholar] [CrossRef]
- Kopardekar, P.H. Unmanned Aerial System (UAS) Traffic Management (UTM): Enabling Low-Altitude Airspace and UAS Operations; National Aeronautics and Space Administration: Washington, DC, USA, 2014.
- SESAR Joint Undertaking. U-Space—Blueprint; Publications Office of the European Union: Luxembourg, 2017. [Google Scholar]
- Jiang, T.; Geller, J.; Ni, D.; Collura, J. Unmanned Aircraft System traffic management: Concept of operation and system architecture. Int. J. Transp. Sci. Technol. 2016, 5, 123–135. [Google Scholar] [CrossRef]
- Barrado, C.; Boyero, M.; Brucculeri, L.; Ferrara, G.; Hately, A.; Hullah, P.; Martin-Marrero, D.; Pastor, E.; Rushton, A.P.; Volkert, A. U-Space Concept of Operations: A Key Enabler for Opening Airspace to Emerging Low-Altitude Operations. Aerospace 2020, 7, 24. [Google Scholar] [CrossRef]
- Nunn, S. Police technology in cities: Changes and challenges. Technol. Soc. 2001, 23, 11–27. [Google Scholar] [CrossRef]
- Jackson, J.; Bradford, B. What is Trust and Confidence in the Police? Policing 2010, 4, 241–248. [Google Scholar] [CrossRef]
- Fox, S.J. Policing—The technological revolution: Opportunities & challenges! Technol. Soc. 2019, 56, 69–78. [Google Scholar] [CrossRef]
- Jensen, O.B. New ‘Foucauldian Boomerangs’: Drones and Urban Surveillance. Surveill. Soc. 2016, 14, 20–33. [Google Scholar] [CrossRef]
- Gohari, A.; Ahmad, A.B.; Rahim, R.B.A.; Supa’at, A.S.M.; Abd Razak, S.; Gismalla, M.S.M. Involvement of Surveillance Drones in Smart Cities: A Systematic Review. IEEE Access 2022, 10, 56611–56628. [Google Scholar] [CrossRef]
- Ison, D.; Terwilliger, B.; Vincenzi, D. Privacy, Restriction, and Regulation Involving Federal, State and Local Legislation: More Hurdles for Unmanned Aerial Systems (UAS) Integration? J. Aviat./Aerosp. Educ. Res. 2014, 24, 41–80. [Google Scholar] [CrossRef]
- Valdovinos, M.C.; Specht, J.; Zeunik, J. Community Policing & Unmanned Aircraft Systems (UAS): Guidelines to Enhance Community Trust; COPS Office: Washington, DC, USA, 2016.
- Mazur, A.M.; ten Thije, J.; Vreeken, J.; Hesselink, H.; Dziugieł, B.; Wyka, S.; Liberacki, A.; Idzikowska, T.; Stanczyk, A.D.; Utracka, A.; et al. Regulatory framework on the UAM operational concepts of the ASSURED-UAM project. Aircr. Eng. Aerosp. Technol. 2022, 94, 1491–1498. [Google Scholar] [CrossRef]
- Leveson, N.G. Engineering a Safer World: Systems Thinking Applied to Safety; The MIT Press: Cambridge, MA, USA, 2016. [Google Scholar]
- Ahn, S.I.; Kurt, R.E.; Turan, O. The hybrid method combined STPA and SLIM to assess the reliability of the human interaction system to the emergency shutdown system of LNG ship-to-ship bunkering. Ocean Eng. 2022, 265, 112643. [Google Scholar] [CrossRef]
- Bjerga, T.; Aven, T.; Zio, E. Uncertainty treatment in risk analysis of complex systems: The cases of STAMP and FRAM. Reliab. Eng. Syst. Saf. 2016, 156, 203–209. [Google Scholar] [CrossRef]
- Bensaci, C.; Zennir, Y.; Pomorski, D. A Comparative Study of STPA Hierarchical Structures in Risk Analysis: The Case of a Complex Multi-Robot Mobile System. In Proceedings of the 2018 2nd European Conference on Electrical Engineering and Computer Science (EECS), Bern, Switzerland, 20–22 December 2018; pp. 400–405. [Google Scholar]
- Abdulkhaleq, A.; Lammering, D.; Wagner, S.; Röder, J.; Balbierer, N.; Ramsauer, L.; Raste, T.; Boehmert, H. A Systematic Approach Based on STPA for Developing a Dependable Architecture for Fully Automated Driving Vehicles. Procedia Eng. 2017, 179, 41–51. [Google Scholar] [CrossRef]
- Chaal, M.; Valdez Banda, O.A.; Glomsrud, J.A.; Basnet, S.; Hirdaris, S.; Kujala, P. A framework to model the STPA hierarchical control structure of an autonomous ship. Saf. Sci. 2020, 132, 104939. [Google Scholar] [CrossRef]
- Khastgir, S.; Brewerton, S.; Thomas, J.; Jennings, P. Systems Approach to Creating Test Scenarios for Automated Driving Systems. Reliab. Eng. Syst. Saf. 2021, 215, 107610. [Google Scholar] [CrossRef]
- Yang, R.; Utne, I.B. Towards an online risk model for autonomous marine systems (AMS). Ocean Eng. 2022, 251, 111100. [Google Scholar] [CrossRef]
- Leveson, N. A new accident model for engineering safer systems. Saf. Sci. 2004, 42, 237–270. [Google Scholar] [CrossRef]
- Leveson, N.G.; Thomas, J.P. STPA Handbook; PSASS: Cambridge, MA, USA, 2018. [Google Scholar]
- Qazi, A.; Shamayleh, A.; El-Sayegh, S.; Formaneck, S. Prioritizing risks in sustainable construction projects using a risk matrix-based Monte Carlo Simulation approach. Sustain. Cities Soc. 2021, 65, 102576. [Google Scholar] [CrossRef]
- Sandino, J.; Vanegas, F.; Maire, F.; Caccetta, P.; Sanderson, C.; Gonzalez, F. UAV Framework for Autonomous Onboard Navigation and People/Object Detection in Cluttered Indoor Environments. Remote Sens. 2020, 12, 3386. [Google Scholar] [CrossRef]
- Abubakar, A.; Ahmad, I.; Omeke, K.; Ozturk, M.; Ozturk, C.; Abdel-Salam, A.; Mollel, M.; Abbasi, Q.; Hussain, S.; Imran, M. A Survey on Energy Optimization Techniques in UAV-Based Cellular Networks: From Conventional to Machine Learning Approaches. Drones 2023, 7, 214. [Google Scholar] [CrossRef]
- Richhariya, S.; Wanaskar, K.; Shrivastava, S.; Gao, J. Surveillance Drone Cloud and Intelligence Service. In Proceedings of the 2023 11th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Athens, Greece, 17–20 July 2023; pp. 1–10. [Google Scholar]
- Lappas, D.; Fessakis, G.; Karampelas, P. Recognizing the Threats of Drone Surveillance. A Case Study. In Proceedings of the 2022 IEEE 14th Image, Video, and Multidimensional Signal Processing Workshop (IVMSP), Nafplio, Greece, 26–29 June 2022; pp. 1–5. [Google Scholar]
- Muneem, I.A.; Fahim, S.M.; Khan, F.R.; Emon, T.A.; Islam, M.S.; Khan, M.M. Research and Development of Multipurpose Unmanned Aerial Vehicle (Flying Drone). In Proceedings of the 2021 IEEE 12th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 1–4 December 2021; pp. 402–406. [Google Scholar]
- Mojib, E.B.S.; Haque, A.K.M.B.; Raihan, M.N.; Rahman, M.; Alam, F.B. A Novel Approach for Border Security; Surveillance Drone with Live Intrusion Monitoring. In Proceedings of the 2019 IEEE International Conference on Robotics, Automation, Artificial-Intelligence and Internet-of-Things (RAAICON), Dhaka, Bangladesh, 29 November–1 December 2019; pp. 65–68. [Google Scholar]
- Manning, M.; Johnson, S.D.; Tilley, N.; Wong, G.T.; Vorsina, M. Economic Analysis and Efficiency in Policing, Criminal Justice and Crime Reduction: What Works? Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]




| Stakeholder ID | Stakeholders | Linked Stakeholders |
|---|---|---|
| SH-1 | Local Government and Municipal Authorities | Approve and oversee budgets for system implementation and operation, enact relevant policies and regulations, and monitor and evaluate system operation performance. |
| SH-2 | Emergency Service Agencies (Fire Departments, Emergency Medical Services, etc.) | Rapid response is based on information collected through the system, establishing system operating procedures, participating in drills, and effective collaboration with the system during on-site response. |
| SH-3 | Department Personnel (Administrator, Pilot, Manager, etc.) | System operation, maintenance, and data analysis, rapid response and reporting in the event of an abnormal situation, performing cooperative work with other departments and organizations. |
| SH-4 | Community Groups (Citizen Advisory Committees, Privacy Advocates, Community Members, etc.) | Providing opinions on system introduction and operation, monitoring activities to protect privacy and civil liberties, and acting as a communication channel between the community and the system operating organization. |
| SH-5 | Lawmakers and Policy Makers | Enact system-related laws and policies, oversee the legality and ethics of system operations, and mediate and arbitrate conflicts of interest among stakeholders. |
| SH-6 | Other Government Agencies (urban planning, transportation, public safety, etc.) | Coordination with policies and projects in related fields such as urban planning, transportation, public security etc., joint utilization, and cooperation of information collected through the system. |
| SH-7 | Media | Raising public awareness of system introduction and operation, objective reporting on system performance and issues, promoting communication among stakeholders, and shaping public opinion. |
| SH-8 | Citizens | Express opinions on system introduction and operation, participate in community safety and policing activities, monitoring and reporting system misuse and adverse events. |
| SH-9 | Technology Providers | Build and provide technical support for the system, identify the latest technology trends, and propose ways to apply them, as well as training and technical support for system operating organizations and end users. |
| Loss ID | Loss Description | Linked Stakeholders |
|---|---|---|
| L-1 | Loss of Human Life or Injury | [SH-2], [SH-3], [SH-8] |
| L-2 | Loss of or Damage to UAVs | [SH-3], [SH-9] |
| L-3 | Loss of or damage to objects outside the UAVs | [SH-3], [SH-6], [SH-8] |
| L-4 | Loss of Mission | [SH-1], [SH-3], [SH-9] |
| L-5 | Loss of Public Trust or Reputation | [SH-1], [SH-4], [SH-7] |
| L-6 | Loss of Coordination and Efficiency in Emergency Response | [SH-2], [SH-3], [SH-6] |
| L-7 | Loss of sensitive information | [SH-4], [SH-5], [SH-8] |
| Hazard ID | System-Level Hazards | Link to Losses | Linked Stakeholders |
|---|---|---|---|
| H-1 | UAS operate in a manner that causes harm to people or property | [L-1], [L-2], [L-3] | [SH-2], [SH-3], [SH-6], [SH-8], [SH-9] |
| H-2 | UAS operate in unauthorized or restricted airspace | [L-4], [L-5] | [SH-1], [SH-3], [SH-4], [SH-5], [SH-7] |
| H-3 | UAS does not maintain safety distance in surveillance mission | [L-1], [L-3], [L-4] | [SH-2], [SH-3], [SH-4], [SH-6], [SH-8], [SH-9] |
| H-4 | UAS operations exacerbate emergency situations | [L-1], [L-6] | [SH-1], [SH-2], [SH-3], [SH-6], [SH-7], [SH-8] |
| H-5 | UAS lost communication integrity | [L-2], [L-4], [L-5], [L-7] | [SH-1], [SH-3], [SH-5], [SH-7], [SH-9] |
| H-6 | UAS operations interfere with or degrade the effectiveness of emergency response | [L-1], [L-6] | [SH-1], [SH-2], [SH-3], [SH-6], [SH-7], [SH-8] |
| Control Actions (Controller/Controlled Process) | Unsafe Control Actions | |||
|---|---|---|---|---|
| Not Providing (N) | Providing Causes Hazard (P) | Too Early/Too Late (T) | Stop too Soon/ Applying Too Long (D) | |
| CA1: GCS Control (GCS Administration Module/GCS) | (UCA1-N-1) GCS Administration Module does not provide GCS control [H-4] | (UCA1-P-1) GCS Administration Module provides incorrect GCS control [H-1, H-4, H-6] | (UCA1-T-1) GCS Administration Module provides GCS control too late [H-4] | N/A |
| CA2: UAV Flight Command (GCS/Automatic Control Module) | (UCA2-N-1) GCS does not provide UAV Flight Command [H-4] | (UCA2-P-1) GCS provides incorrect UAV Flight Command [H-1, H-2, H-3, H-4, H-6] (UCA2-P-2) GCS provides UAV Flight Command during abort/return flight [H-1, H-3, H-6] | (UCA2-T-1) GCS provides UAV Flight Command too late [H-1, H-4] | N/A |
| CA3: UAV Direction and Speed Control (Automatic Control Module/Motor) | (UCA3-N-1) Automatic Control Module (ACM) does not provide UAV Direction and Speed Control during a flight mission [H-1, H-3, H-4, H-6] | (UCA3-P-1) ACM provides incorrect UAV Direction and Speed Control during a flight mission [H-1, H-2, H-3, H-4, H-6] (UCA3-P-2) ACM provides UAV Direction and Speed Control during abort/return flight [H-1, H-3, H-6] | (UCA3-T-1) ACM provides UAV Direction and Speed Control too late during a flight mission [H-1, H-3] | (UCA3-D-1) ACM stops providing UAV direction and speed control too soon during a flight mission [H-1, H-3] |
| CA4: Danger Situation Alerts (GCS/Speaker) | (UCA4-N-1) GCS does not provide Danger Situation Alerts commands during emergency situations [H-4, H-6] | (UCA4-P-1) GCS provides incorrect Danger Situation Alerts command [H-4, H-6] (UCA4-P-2) GCS provides incorrect Danger Situation Alerts commands when no emergency situations are present [H-6] (UCA4-P-3) GCS provides Danger Situation Alerts commands speakers at non-maximum volume settings [H-6] | (UCA4-T-1) GCS provides Danger Situation Alerts commands too late [H-4, H-6] | (UCA4-D-1) GCS continues to provide Danger Situation Alerts commands well after the emergency has been resolved [H-6] (UCA4-D-2) GCS Danger Situation Alerts command stops too soon during an emergency [H-4, H-6] |
| CA5: Reporting a dangerous situation (OMS/Government System) | (UCA5-N-1) OMS do not Report a dangerous situation [H-1, H-4, H-6] | (UCA5-P-1) OMS provides incorrect Reporting of a dangerous situation [H-4, H-6] | (UCA5-T-1) OMS provides Reporting a dangerous situation too late [H-1, H-4, H-6] | N/A |
| CA6: CCTV Video Request (OMS/Government System) | N/A | N/A | N/A | (UCA6-D-1) OMS requesting too long CCTV video [H-5] |
| UCA ID | Hazardous Causal Factor | HCF ID | Loss Scenarios |
|---|---|---|---|
| UCA1-N-1 | Absence or delay in decision-making by the administrator | HCF1-N-1-1 | The OMS administrator is absent, or there is a delay in approving commands, GCS control commands may not be delivered. |
| Malfunction or failure of the GCS Administration Module | HCF1-N-1-2 | The GCS Administration Module does not operate normally due to hardware or software problems, and GCS control functions may not be provided. | |
| Communication disruption or data transmission failure | HCF1-N-1-3 | GCS control commands may not be delivered due to communication disruptions or data transmission failures between OMS and GCS. | |
| Power supply interruption or instability | HCF1-N-1-4 | The GCS Administration Module may stop or intermittently operate due to a power outage or unstable power supply. | |
| Inattention or negligence of the administrator | HCF1-N-1-5 | The OMS administrator may fail to issue necessary commands due to a lack of concentration or responsibility. | |
| Lack of decision-making ability of the administrator | HCF1-N-1-6 | The OMS administrator may not be able to issue appropriate commands due to a lack of situation assessment or decision-making ability. | |
| Non-reception or loss of GCS status information | HCF1-N-1-7 | The GCS Administration Module may not issue control commands due to non-reception or loss of status information from the GCS. | |
| Failure to process or analyze GCS status information | HCF1-N-1-8 | The GCS Administration Module may not issue necessary control commands due to failure to process or analyze received GCS status information properly. | |
| UCA1-P-1 | Inaccuracy or lack of real-time updates in external information | HCF1-P-1-1 | GCS control commands may be incorrectly generated if external information such as weather, geography, or flight restriction zones is inaccurate or not updated in real time. |
| UCA6-D-1 | Excessive information requirements for situation assessment | HCF6-D-1-2 | The tendency to request more information than necessary for assessing dangerous situations may lead to requesting unnecessarily long video durations. |
| Absence of video storage and management policies | HCF6-D-1-3 | Without clear policies for storing and managing CCTV videos, unnecessarily long videos may be repeatedly requested and stored. |
| Risk Level | Total Scenarios | Human Factors | Hardware | Software | Procedures | Environment |
|---|---|---|---|---|---|---|
| Extreme (20~25) | 12 | 12 | N/A | N/A | N/A | N/A |
| Very high (15~16) | 7 | 1 | 4 | N/A | 2 | N/A |
| High (10~12) | 13 | 7 | N/A | N/A | 4 | 1 |
| Medium (4~9) | 56 | N/A | 7 | 34 | 14 | 1 |
| low (3~4) | N/A | N/A | N/A | N/A | N/A | N/A |
| Very low (1~2) | 12 | N/A | N/A | 12 | N/A | N/A |
| Years | Aircraft | Equipment Problem | Human Factors | Situational Awareness |
|---|---|---|---|---|
| 1993–2000 | 4 | 3 | 2 | N/A |
| 2001–2005 | 3 | 2 | 3 | N/A |
| 2006–2010 | 5 | 4 | 7 | N/A |
| 2011–2015 | 2 | 3 | 12 | 2 |
| 2016–2020 | 6 | 8 | 27 | 5 |
| 2021–2024: | 8 | 12 | 35 | 9 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Go, E.; Jeon, H.-C.; Lee, J.-S.; Lim, J.-Y. Enhancing Urban Public Safety through UAS Integration: A Comprehensive Hazard Analysis with the STAMP/STPA Framework. Appl. Sci. 2024, 14, 4609. https://doi.org/10.3390/app14114609
Go E, Jeon H-C, Lee J-S, Lim J-Y. Enhancing Urban Public Safety through UAS Integration: A Comprehensive Hazard Analysis with the STAMP/STPA Framework. Applied Sciences. 2024; 14(11):4609. https://doi.org/10.3390/app14114609
Chicago/Turabian StyleGo, Eutteum, Hee-Chang Jeon, Jong-Sup Lee, and Joong-Yeon Lim. 2024. "Enhancing Urban Public Safety through UAS Integration: A Comprehensive Hazard Analysis with the STAMP/STPA Framework" Applied Sciences 14, no. 11: 4609. https://doi.org/10.3390/app14114609






