Abstract
With the rise of the Internet of Things (IoT), maintaining data confidentiality and protecting user privacy have become increasingly challenging. End devices in the IoT are often deployed in unattended environments and connected to open networks, making them vulnerable to physical tampering and other security attacks. Different authentication key agreement (AKA) schemes have been used in practice; several of them do not cover the necessary security features or are incompatible with resource-constrained end devices. Their security proofs have been performed under the Random-Oracle model. We present an AKA protocol for end devices and servers. The proposal leverages the ECC-based key exchange mechanism and one-way hash function-based message authentication method to achieve mutual authentication, user anonymity, and forward security. A formal security proof of the proposed scheme is performed under the standard model and the eCK model with the elliptic curve encryption computational assumptions, and formal verification is performed with ProVerif. According to the performance comparison, it is revealed that the proposed scheme offers user anonymity, perfect forward security, and mutual authentication, and resists typical attacks such as ephemeral secret leakage attacks, impersonation attacks, man-in-the-middle attacks, and key compromise impersonation attacks. Moreover, the proposed scheme has the lowest computational and communication overhead compared to existing schemes.
1. Introduction
Thanks to advances in chipset production and embedding technologies, sensors and actuators (referred to as end devices) are pervasive in the Internet of Things (IoT), being integrated into intelligent agriculture, smart grid (SG), telemedicine, smart home, intelligent manufacturing, and many other fields to collect and disseminate the data [1]. According to the latest estimates, there will be 83 billion IoT connections by 2024 [2]. In IoT applications, the collected and transmitted data are sensitive. Privacy is another crucial issue, especially regarding user data such as consumption habits, location, and communication activities [3,4]. To ensure security, authentication key agreement (AKA) schemes for IoT applications have been widely used, which offer mutual authentication and privacy protection and ensure confidentiality, integrity, and non-repudiation of data transmissions based on the negotiated session keys [5]. End devices are often linked to open networks and deployed in unattended environments with limited computation, communication, and storage capabilities. As a result, mutual authentication and key agreement between end devices and servers to sustain efficiency is a critical challenge.
1.1. Related Work
Over the last few years, numerous AKA solutions have been developed for IoT applications. The symmetric cryptography-based AKA protocols [6,7,8,9] have the advantages of low computational complexity and high efficiency. On the other hand, such schemes necessitate sharing key parameters between end devices beforehand or each device transferring its key to the server. It is unrealistic for numerous end devices and significantly burdens the servers. Physical Unclonable Function (PUF) is a promising lightweight hardware security primitive adopted by many IoT AKA protocols [10,11,12]. Each participant in these schemes should record one or more Challenge–Response Pairs (CRPs) of its PUF with the registration server beforehand. When a registered device, Alice, wants to communicate with another registered device, Bob, it can only do so with the assistance of the server, which results in a lack of flexibility and efficiency. In contrast, the asymmetric cryptography-based AKA schemes requiring fewer restrictions have attracted increasing attention [13]. Elliptic Curve Cryptography (ECC) provides smaller key sizes than other asymmetric algorithms with the same security [14,15], which makes it introduced in IoT AKA protocols.
Numerous IoT AKA protocols based on ECC have been developed. In 2015, a bilinear pairing-based AKA protocol for wireless body area networks (WBAN) was put forward by Wang et al. [16], which requires a high computational overhead. They claimed that their scheme achieves absolute anonymity, perfect forward security (PFS), and overcomes the weaknesses of previous schemes. After analysis, it was found that the session key could be captured after temporary session information disclosure. In addition, Wu et al. [17] pointed out that the protocol is incapable of withstanding impersonation (IM) attacks. And then, they proposed an enhanced version for WBANs. However, the enhanced scheme also uses bilinear pairing and suffers from ephemeral secret leakage (ESL) attacks. Seo et al. [18] introduced an AKA scheme for dynamic WSNs. Later, Saeed et al. [19] pointed out that the scheme [18] could not provide PFS; then, they proposed a scheme for establishing an authenticated key between WSNs and cloud servers, whereas the proposal [19] is also not resistant to ESL attacks and cannot provide user anonymity. In 2020, an AKA scheme for IoT was introduced by Fang et al. [20]. In this scheme, heterogeneous-type IoT smart devices are deployed based on a trust model. Their solution requires higher computational and communication costs and is susceptible to ESL attacks [21]. In the same year, Dariush et al. [22] introduced an AKA protocol for SG that offers solutions to some of the previously mentioned problems, such as ESL attacks and private key leakage attacks. Unfortunately, in [22], the trusted authority (TA) is able to masquerade as a smart meter to agree on session keys with the server provider [23]. Moreover, the scheme needs more computational and communication costs for the bilinear pairing computation.
Recently, Srinivas et al. [24] designed an anonymous AKA protocol with Schnorr’s signature. Later, Baruah et al. [23] demonstrated that the scheme [24] is prone to man-in-the-middle (MIM) attacks and IM attacks. Cryptanalysis identifies that the protocol [24] is also vulnerable to key escrow problems and ESL attacks. Yang et al. [25] stated that Shen et al.’s scheme [26] suffers from MIM attacks and key compromise impersonation (KCI) attacks and is incapable of providing PFS, and then introduced an enhanced cloud-based scheme. Unfortunately, the enhanced scheme has key escrow problems and is incapable of providing user anonymity. Chaudhry et al. [27] presented an AKA scheme for SG using ECC and symmetric encryption. Unfortunately, this scheme [27] has key escrow problems and suffers from MIM attacks. Hajian et al. [28] examined the deficiencies of four existing AKA schemes and then proposed an improved device-to-device AKA scheme in the IoT. But the improved scheme suffers from MIM attacks and KCI attacks and is incapable of affording PFS. In 2023, Chen et al. [29] presented an AKA scheme for industrial control systems. However, the solution requires high computation and communication costs, suffers from ESL attacks, and cannot afford PFS.
1.2. Related Adversary Model
In 1993, Bellare and Rogaway [30] put forward an adversary model for the AKA scheme, the BR model, which formalized the attacker’s known-key attacks and IM attacks. Later, the BR model was modified by Blake-Wilson et al. [31] by introducing long-term private key corruption attacks. In 2001, Canetti and Krawczyk [32] proposed the CK model, which covers attacks on ephemeral private keys and intermediate result leakage. All these adversary models attempt to cover the essential safety and performance attributes required. In 2007, LaMacchia et al. [33,34] introduced a somewhat stronger adversary model, the extended CK model (eCK model), which incorporates weak PFS and KCI attacks.
1.3. Random-Oracle Model and Standard Model
Provable security theory, which employs formal language to describe the security of cryptographic protocols, has played a critical role in designing and analyzing AKA protocols. Most early cryptographic schemes for provable security were inefficient. Practically oriented provably secure cryptographic schemes were proposed only after the famous Random-Oracle model was introduced by Bellare and Rogaway [35]. In the Random-Oracle model, the hash function is treated as a completely randomized machine called R, and the adversary has no access to its information. A random oracle is a theoretical model that takes deterministic inputs and produces random outputs. Finding a genuinely random function to replace the random oracle R in the Random-Oracle model is impossible. Many scholars have suggested avoiding using hash functions as random oracles in favor of designing cryptographic protocols directly under realistic conditions [36,37,38]. This approach, called the standard model, avoids using idealized models such as hash functions. In general, cryptographic schemes that are provably secure under the standard model can provide more robust security than those that are provably secure under the randomized predicate model.
1.4. Motivation and Contributions
To summarize, previous ECC-based AKA schemes suffer from more or less vulnerabilities, i.e., failure to provide user anonymity [19,25], PFS [18,24,28,29], and vulnerability to specific attacks [16,17,18,19,20,22,24,25,27,28,29]. Next, high computational and communication costs eliminate the suitability of some solutions for resource-limited IoT [10,16,17,20,22,29]. Their security proofs are performed in the Random-Oracle model model [22,24]. It is attractive to design an efficient AKA scheme for IoT and provide security proof under the standard model and eCK model.
We propose an improvement over the scheme of Srinivas et al. [24] with the ECC-based message exchange mechanism and the one-way hash function message authentication technique. During registration, the TA only possesses part of the entity’s private key, solving the key escrow issues. In addition, the proposals provide PFS and can resist ESL attacks since session keys are generated using both long-term and ephemeral credits. The protocol encrypts entity identities dynamically with random numbers and transmits them anonymously from session to session.
The paper’s contributions can be summarized as follows:
(1) As an example, the cryptanalysis of the protocol scheme of Srinivas et al. [24] for the previous scheme reveals security issues and vulnerabilities.
(2) A secure-enhanced AKA protocol for IoT is presented. Its security is formally proved under the standard model and the eCK model with the elliptic curve encryption computational assumptions and verified with ProVerif.
(3) The proposed protocol has better security features with lower communication and computational overheads than existing schemes.
1.5. Roadmap
The paper is structured as follows: Section 2 reviews the network model and the basics of elliptic curve encryption. In Section 3, we analyze a related AKA scheme. We then describe an improved ECC-based AKA protocol in Section 4. Section 5 provides a formal proof, descriptive security analysis, and validation with ProVerif of the proposed scheme security. In Section 6, we present a performance comparison with related schemes. Finally, we conclude the paper in Section 7.
2. Preliminaries
The following preliminaries and symbols are used to explain and analyze the schemes.
2.1. Network Model
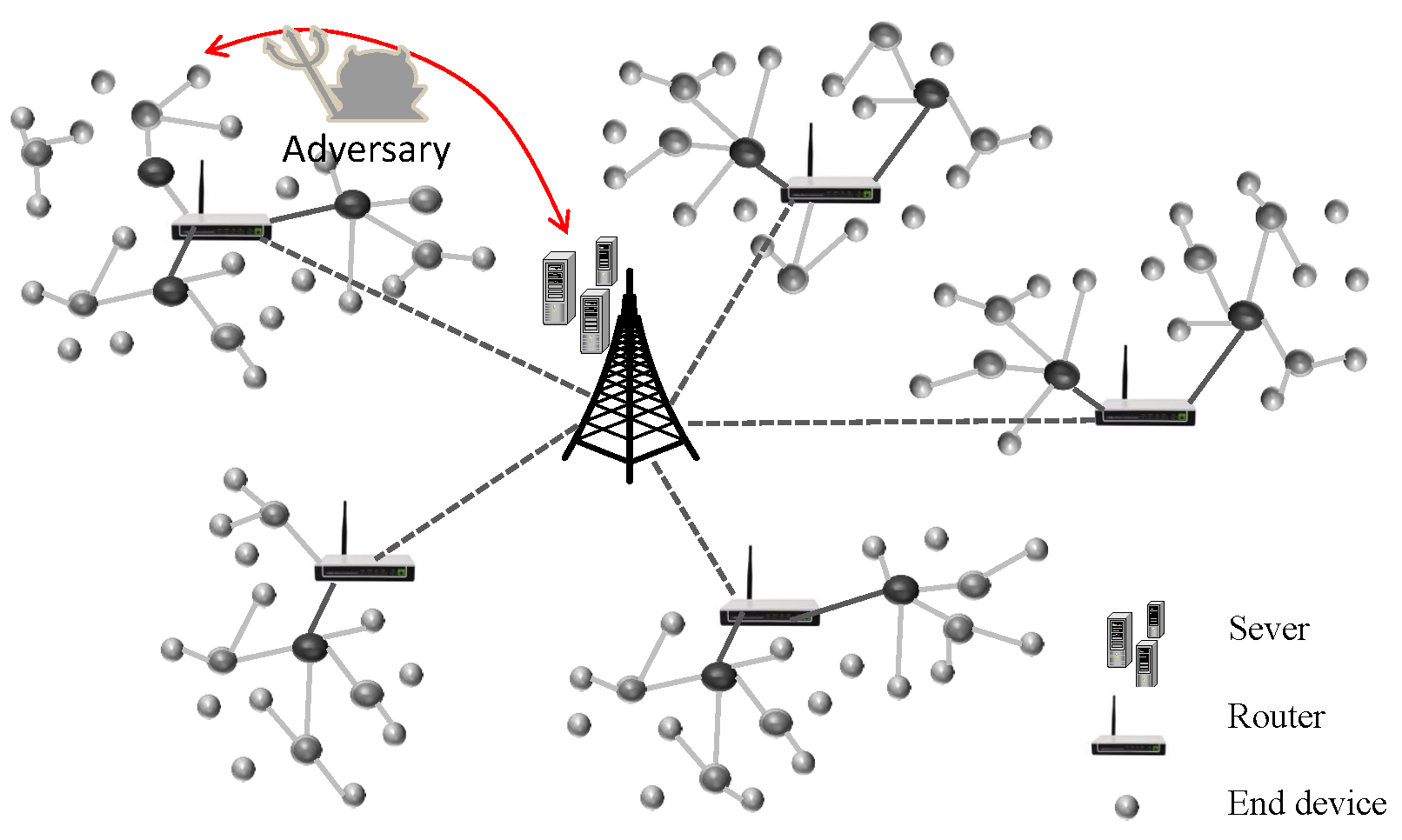
A typical IoT application is shown in Figure 1. It mainly involves three main components: end devices, routers, and servers. The end devices may be sensors, actuators, cell phones, etc. Routers include gateway nodes, base stations, and routers for relaying and passing messages. In addition, servers are in charge of managing devices and assigning security parameters.
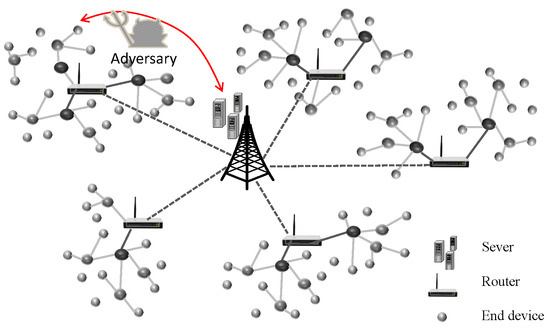
Figure 1.
Network model.
An IoT system consists of many low-power, resource-limited end devices placed in unattended or open environments and typically connected to open networks. Through these terminal devices, real-time monitoring and control can be implemented remotely. The end sensors collect real-time data such as agricultural environment parameters, power consumption, biomedical data, and machine conditions and then send the data to remote servers. The servers receive and store the collected data, then extract and evaluate the data to provide the appropriate control measures. The end devices carry out control commands that are received from the server. There is a risk of the adversary controlling the communication channels and compromising the secret credentials of servers and end devices.
2.2. Elliptic Curve Encryption Mathematical Problems
Let be a big prime number, denote a non-singular elliptic curve over a finite field , and P be a generator point. The group operation is the usual multiplication of points on the elliptic curve, and G is a subgroup of order p, where [39]. Hence, the following applies.
Definition 1.
Elliptic curve discrete logarithm (ECDL) problem: For the given points X and , where and , it is computationally intractable to find a.
Definition 2.
Elliptic curve Diffie–Hellman (ECDH) problem: For the given points , where and , finding point is computationally intractable.
2.3. Symbols
Symbols for the schemes are cataloged in Table 1.

Table 1.
Symbols for the schemes.
3. Security Analysis of Srinivas et al.’s Scheme [24]
Srinivas et al. [24] put forward an AKA scheme for IoT smart grid systems with an
Schnorr signature mechanism based on ECC. Before being added to the network, TA is responsible for distributing secret credentials, including signatures, to each smart grid and service provider. Smart meters and service providers can authenticate each other to establish session keys for secret communication. Baruah et al. [23] point out that the scheme of Srinivas et al. [24] is insured against MIM attacks and IM attacks. Cryptanalysis shows that the protocol [24] also suffers from key escrow issues and ESL attacks. For the review of Srinivas et al. [24], please refer to the complete paper.
3.1. Key Escrow Problem
During the registration process, TA generates the private keys of and with Schnorr’s signature. calculates and for , and also , for . Then, the long-term private secrets, , , , and , are known to him/her.
3.2. No Resistance to ESL Attacks
An AKA protocol is designed to resist an ESL attack, meaning that even if all the session-specific information of the entities in a session is compromised, the secrecy of the session key would remain uncompromised. During the authentication process, once the ephemeral secrets and are compromised, can compromise the session key or by the following steps:
A1: obtains the messages , and by eavesdropping via the open channels;
A2: extracts and from the messages, then calculates ;
A3: For , gets then calculates .
A4: For , calculates .
4. The Proposed Protocol
The proposal involves three phases: initialization, registration, and authentication and key agreement. To begin, TA generates and releases parameters for the system during the initialization phase. In the registration phase, each end device or server acquires its private key and both parties’ public key with the assistance of . Ultimately, and will authenticate each other and negotiate a session key.
4.1. Initialization Phase
TA generates and releases parameters for the system as follows:
TA1: TA selects an elliptic curve over finite field with a base point P;
TA2: Then, TA picks as the collision-resistant one-way hash function;
TA3: TA issues publicly.
4.2. Registration Phase
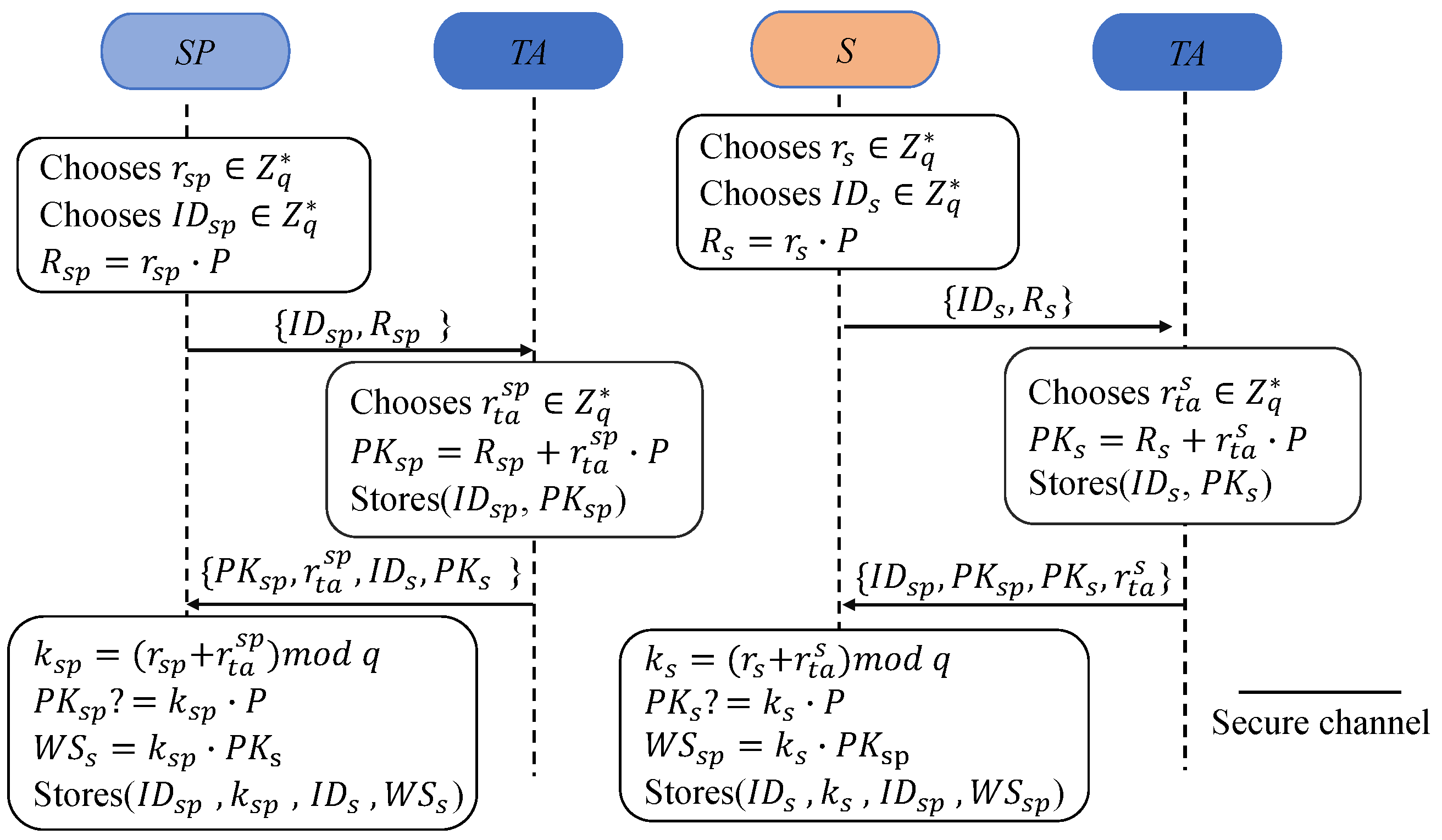
As shown in Figure 2, taking the registration of the server as an example, the processes are as follows:
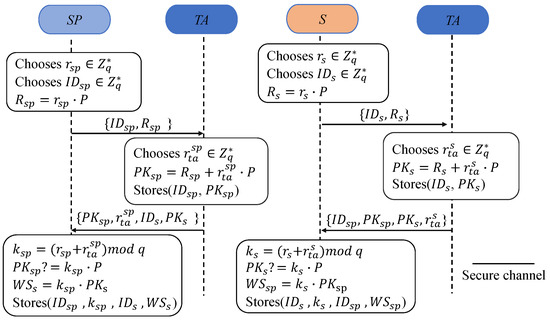
Figure 2.
Registration processes of the proposed scheme.
R1: Firstly, SP chooses a random and its identifier and computes . Then, SP transmits a registration request, , to TA securely.
R2: In response, first, TA chooses randomly to calculate the public key of . . Next, TA sends to SP via a secure channel.
R3: In response, takes as part of its private key and obtains its private key, . Then, SP checks whether ; if it holds, then SP computes and stores .
Similarly, S stores after registration. When a new end device joins and registers the system, TA sends to SP securely.
4.3. Authentication and Key Agreement Phase
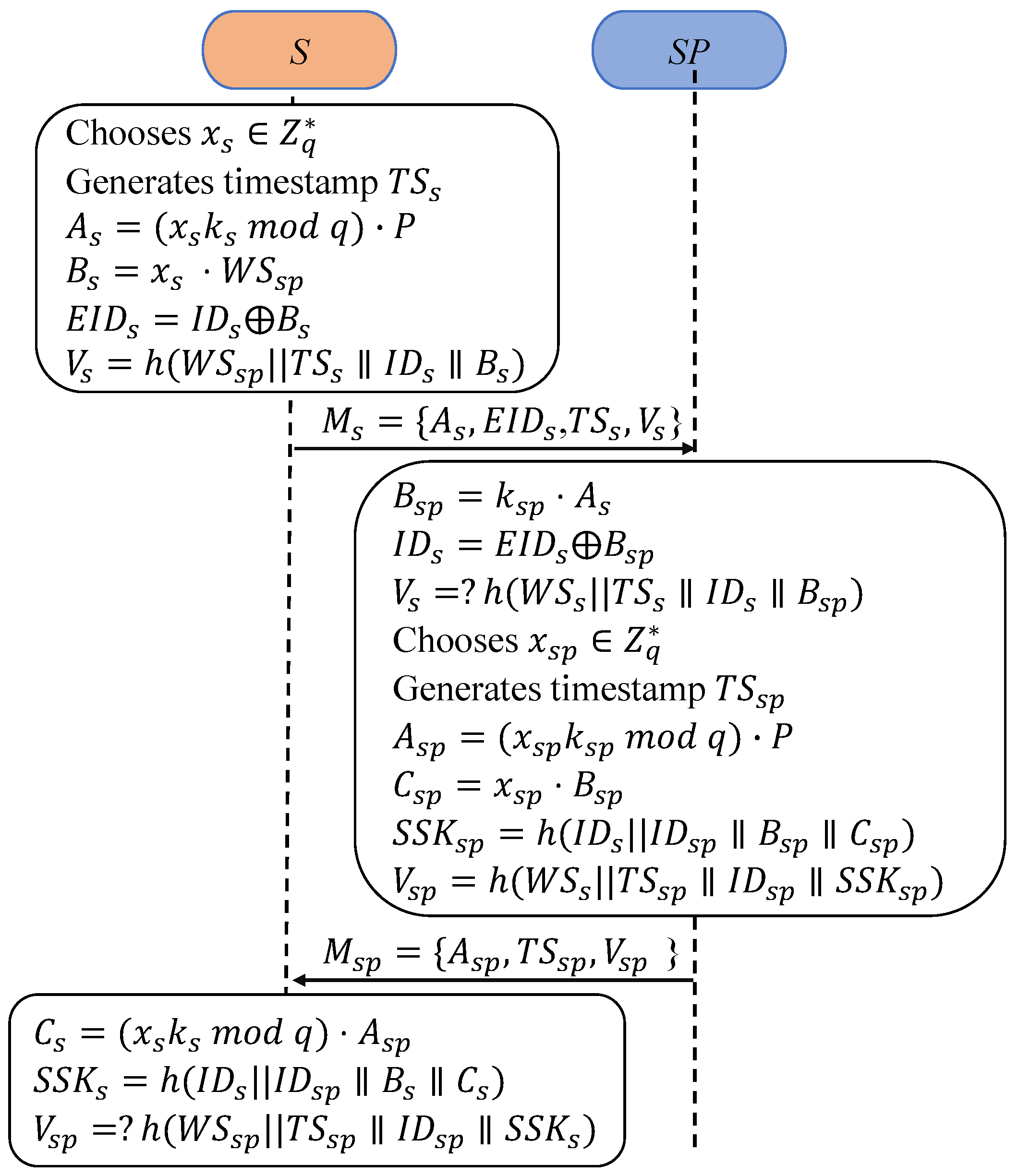
and will authenticate each other and negotiate a session key as shown in Figure 3.
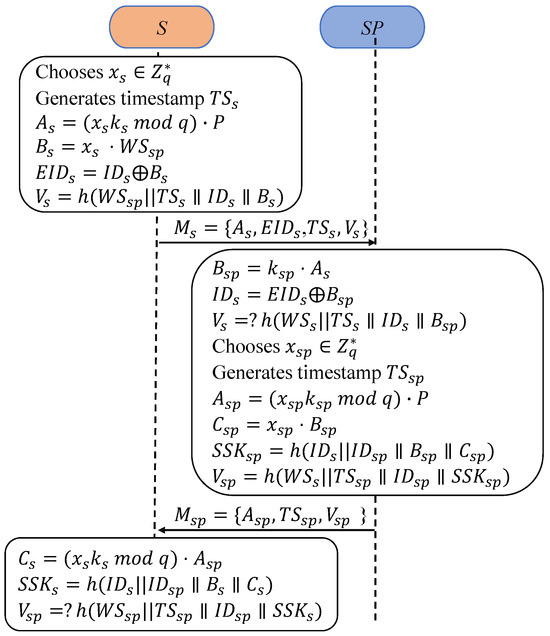
Figure 3.
Authentication and key agreement of proposed protocol.
S1: S first picks randomly and generates a timestamp . Next, S calculates and . Third, S encrypts , , and obtains a verifier . Finally, S transmits the authentication request to .
SP1: Upon receiving the request message, first examines its freshness against the timestamp . Next, SP calculates to decrypt . Thus, SP gains the S verifier and validates the equation of to assure the integrity of the incoming message and the validity of S.
SP2: Firstly, selects randomly and obtains a timestamp . Secondly, SP calculates and . SP obtains the session key as . Third, SP figures out a verifier: . and transmits authentication reply } to S.
S2: On receiving the message, S first examines its freshness against . Next, S calculates to obtain the session key . Thus, S gains the SP verifier and validates the equation of to assure the integrity of the incoming message and the validity of SP.
5. Security Analysis
This session provides a formal proof, descriptive security analysis and validation with ProVerif of the proposed scheme security.
5.1. Formal Proof
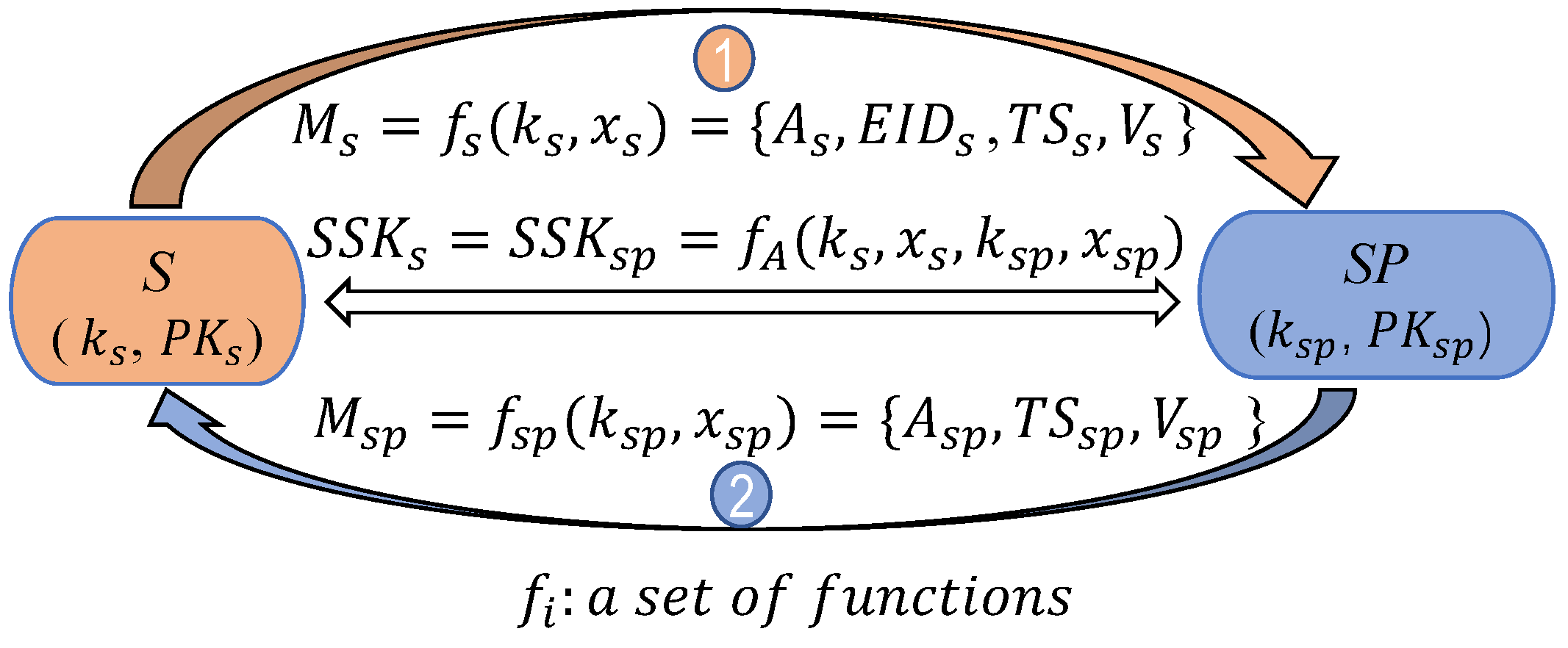
The eCK adversary model [33,34,40] is employed for the security proof. The system authentication model is shown in Figure 4. After registration, obtains its private and public keys . The private and public keys of are . During authentication and key agreement, they negotiate the session key () by exchanging authentication information and , where and , , and are random ephemeral secrets.
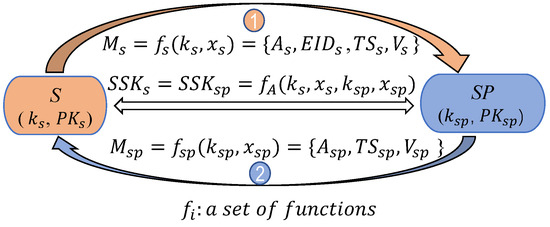
Figure 4.
Authentication model.
5.1.1. Security Model
Participants. There are n participants in the proposed protocol , which are uniformly denoted by the set , and each participant may have i instances involved in distinct, possibly concurrent executions of , where n and i are polynomial numbers.
Sessions. Let denote the mth protocol session running between entity and intended partner entity . A session is accepted if it has computed a session key , with a session identifier of , where is the outgoing information of , and is the outgoing information of .
Adversary. Firstly, the adversary has complete control of the communicating network. Namely, is able to eavesdrop on, alter, ascertain, and inject communication messages and . Secondly, can have knowledge of the participant’s long-term private key () and ephemeral secret () but not both. Thirdly, allows replacing the participant’s public key (). Finally, can obtain the session key () held by the participant. can interact with with the following Oracle queries:
(1) . can obtain the ephemeral secrets of with the query.
(2) . replaces the public key of using this query.
(3) . is available with this query for the public key of .
(4) . By running the query, is able to obtain the long-term private keys of , while the public key of has not yet been replaced.
(5) . Returns ⊥ if session was not accepted. If not, it returns the session key that holds.
(6) . represents sending the message M to in session then receiving a reply from according to .
(7) . The query does not simulate the adversary’s ability, but it simulates the indistinguishability between real session keys and random keys. Input session must be fresh. As a challenger, tosses a coin . If , returns the session key held by ; if , returns a random key from the distribution of the session key.
Matching session. If and have the same session , then is said to be a matching session for .
Freshness. Let denote an accepted session between honest participants and if and are matching sessions. is fresh if all the following conditions do not hold:
(1) issues or queries if exists.
(2) The matching session exists. makes and queries, or and queries.
(3) The matching session does not exist. makes and , or queries.
A game simulates the security of an AKA protocol. In the game, can issue multiple queries in any order. can issue the query only once for a fresh session . Next, a coin is flipped by . When the game ends, will guess the value of b as . If and the test session is still fresh, then wins the game. The advantage of to win the game is defined as .
eCK Security. To ensure the security of the AKA protocol in the eCK model, the following conditions must be met:
(1) If both parties complete a matching session, they will calculate the same session key, unless the probability is negligible.
(2) For any polynomial-time adversary , the advantage in breaking the AKA protocol, , must be negligible.
5.1.2. Formal Security Analysis
At first, three empty lists are created to hold the query and the corresponding answers.
L: input–output pairs of the hash function. Instead of being randomly chosen by , the real hash function computes the outputs. To complete the safety proof, needs to record the mapping between the inputs and outputs.
: Tuple for storing the queries–answers of , , and .
: Tuple for storing the queries–answers of .
To continue, it is essential to clarify a few fundamental configurations. Suppose that is activating no more than honest parties, and each party is engaged in no more than sessions. Assume that selects the as the test session. can distinguish a test session key from a random string in the three ways below:
A1. Guessing. guesses the session key correctly.
A2. Key replication. creates a mismatched session that has the same session key as . So is able to fetch the session key by querying the mismatched session.
A3. Forging. The value of is computed at some point by .
Theorem 1.
Since the or problem is intractable, the advantage of against the AKA scheme in the eCK model is negligible.
Proof.

Since the session key , there is only a chance of guessing the correct in the guessing attack.
The hash function should yield the same results for different input values in order to prevent the key replication attack. The probability of success of a key duplication attack is negligible.
The analysis of the forging attack is shown below.
Consider the tuple as an example of the problem, in which the ephemeral keys and are denoted by and , and the long-term keys and are represented by and . If is successful in forging attack with non-negligible probability, and can be computed by using .
First, creates a test session by randomly selecting and . Therefore, has no higher chance of correctly guessing the test session than . Let be the matching session of . There are six complementary events to consider as shown in Table 2. E1: does not obtain the ephemeral secret keys of and . E2: does not obtain the ephemeral secret key of and secret value of . E3: does not obtain the ephemeral secret keys and secret value of . E4: does not obtain the secret values of and . E5: There is no matching session for . obtains parameters similar to E2. E6: There is no matching session for . obtains parameters similar to E4.

Table 2.
Complementary events.
At least one event in the set, , happens with non-negligible probability if succeeds in faking attack with non-negligible probability.
- i.
- Analysis of E1
- (1)
- Setup. sends to the .
- (2)
- Query. will query the public key before an identity is used in any other queries, and all queries are different. answers the queries issued by as follows:
- (1)
- . submits an identity , picks at random , computes , then returns and adds to the list .
- (2)
- . submits a tuple for , replaces with , and update with in the list , where ∗ can be the secret value or be the symbol ⊥.
- (3)
- . submits an identity , looks up in the list and returns . If has replaced the public key and has not submitted a new one, will refuse to respond.
- (4)
- . submits a session , then processes as follows:
- If or , then fails and stops.
- If not, selects at random and appends to .
- (5)
- . submits a session , and processes as follows: If has replaced the public key (or ) and did not submit the new secret value (or ), then may refuse to reply, else
- If or , then fails and stops.
- If has made for will look up in , , or in , then figures out the session key according to the AKA scheme.
- Else, selects at random and appends to , then proceeds as in case 2.
- (6)
- . will answer the query as below.
- If , looks up in and then returns .
- If , looks up in and then returns .
- If and , looks up in and processes as follows:
- ·
- If has made for , looks up in , then computes and returns .
- ·
- If not, randomly selects and calculates and returns , then appends to .
- If , accepts .
- (7)
- . If the public key (or ) had been replaced with (or ), would have had to commit the new secret value (or ) to ; since is unable to generate the session key if he does not know the secret values for and . The responses of to are as follows:
- If fails and stops.
- If , randomly chooses and sends it back to .
- (3)
- Solve ECDH problems. To win the game by forging attack, would have to calculate , where and . finds and in and computes and by solving the problem.
- (4)
- Probability. If it is possible for to properly guess the test session , will not fail in the query phase. Thus, is able to calculate and with probability if wins in the game with advantage .
- ii.
- Analysis of E2
- (1)
- Setup. Same as that in the analysis of E1.
- (2)
- Query. responds to the queries from as those in the analysis of E1 except for the , , , and .
- (1)
- . submits an identity , will respond to the query as follows:
- If , computes , returns , and adds to the list .
- If not, C randomly selects and calculates , then returns and adds in .
- (2)
- . If , will fail and stop. If not, looks up in and returns .
- (3)
- . will respond to the query as follows:
- If or , randomly chooses and returns , then appends to .
- If not, randomly chooses and returns , then appends to .
- (4)
- . will respond to the query as follows:
- If , looks up in and returns .
- If , looks up in , and in , then sends back.
- Otherwise, the analysis is the same as for E1.
- (3)
- Solve ECDH problems. To win the game by forging attack, must compute , where and . finds in the list and in the list to compute and by solving problems.
- (4)
- Probability. If it is possible for to properly guess the test session , will not fail in the query phase. Thus, is able to calculate and with the same probability as E1 winning the game.
- iii.
- Analysis of E3can swap and in E3 and then carry out the analysis of E2.
- iv.
- Analysis of E4
- (1)
- Setup. This is the same as that in the analysis of E1.
- (2)
- Query. The responses of to the queries from are the same as in E1, except for , , , , and queries.
- (1)
- . submits an identity , process as follows:
- If , computes , then returns and appends to .
- If , computes , then returns and appends to .
- Else, C chooses randomly and calculates , then returns and adds in .
- (2)
- . If or , then fails and stops. If not, C looks up in and returns .
- (3)
- . submits a session , randomly chooses and returns , then appends to .
- (4)
- . finds in the list , then responds to queries as follows:
- If , performs as follows:
- ·
- If has made for , looks up in and returns .
- ·
- If has made for , looks up in and returns .
- ·
- Else, randomly chooses and returns , then appends to .
- accepts the session.
- (3)
- Solve ECDH problems. To win the game by forging attack, must compute , where and . looks up in to compute and by solving and problems.
- (4)
- Probability. If it is possible for to properly guess the test session , will not fail in the query phase. Thus, is able to calculate and with the same probability as E1 winning the game.
- v.
- Analysis of E5In E2, there is a matching session for the test session , whereas in E5, there is no matching session for . Therefore, the analysis for E5 is similar to that for E2.
- vi.
- Analysis of E6In E4, there is a matching session for the test session . However, in E6, there is no matching session for . Therefore, the analysis of E6 is similar to that of E4.
☐
5.2. Descriptive Security Analysis
5.2.1. No Key Escrow Issues
During registration, S obtains the long-term private key, . TA only generates the partial private key , which avoids the key escrow problems. The long-term private key of SP is similar.
5.2.2. ESL Attack Resistance
Resistance to ESL attacks means is unable to figure out the session key in spite of knowing ephemeral secrets and . For , where , even if and are revealed, cannot figure out because they do not know the long-term secrets and . Similarly, if knows the short-term secrets and , then he/she cannot calculate .
5.2.3. Anonymity
In this scheme, and are masked before being transmitted during the authentication process and change dynamically from session to session with the choice of the temporary random numbers and . is incapable of retrieving and tracing the identity from the transmitted messages. That is, the proposal guarantees anonymity.
5.2.4. Mutual Authentication
During authenticating, S verifies by checking the correctness of . For , where , cannot be figured out without long-term secrets of . Similarly, verifies S by checking .
5.2.5. Impersonation Attacks Resistance
Firstly, we analyze the S impersonation attack. If tries to impersonate S to generate the message } to make believe that the message is legitimate and generated by S, cannot generate valid information and impersonate S in polynomial time without knowing parameters such as and .
5.2.6. IoT Nodes Capture Attack Resistance
Some IoT end devices are placed in unattended environments and may be physically captured by an adversary. Thus, their credentials can be easily extracted by . The credentials for different end devices in the proposed scheme are different. Therefore, this will only lead to session key leakage between the captured and the server but not between the uncorrupted end device and the server . This implies that the proposal can withstand IoT node capture attacks.
5.2.7. KCI Attack Resistance
Resistance against KCI attacks refers to the inability of to impersonate another legitimate participant, Bob, to authenticate with Alice after Alice’s long-term private key disclosure. Suppose learns the long-term key of the end device S and wants to impersonate to produce } to convince S that the message is legitimate and generated by . For , where , and has not been compromised, cannot impersonate server to perform authentication and key agreement with S. Similarly, cannot carry out KCI attacks against .
5.3. Automatic Formal Verification
The security of the proposal is formally validated with ProVerif [5]. Table 3 illustrates the codes of S, where is a secret channel used for S registration, and is a public channel used for S and authentication. Based on the following results, it can be concluded that both the authentication process and the session key are secure from adversary attacks.

Table 3.
Codes for end device S.
Here are the results of the queries in ProVerif:
- (1)
- RESULT inj-event(endAuthS) ==> inj-event(startAuthS) is true.
- (2)
- RESULT inj-event(endAuthSP) ==> inj-event(startAuthSP) is true.
- (3)
- RESULT inj-event(endAuthSP) ==> inj-event(endAuthS) is true.
- (4)
- RESULT inj-event(endAuthS) ==> inj-event(endAuthSP) is true.
- (5)
- RESULT not attacker(SSKs[]) is true.
- (6)
- RESULT not attacker(SSKsp[]) is true.
- (7)
- RESULT not attacker(ks[]) is true.
- (8)
- RESULT not attacker(ksp[]) is true.
6. Performance Comparison
6.1. Communication Cost
According to [22,41], suppose that is an additive cyclic group with order . is a multiplicative cyclic group with order q. The bilinear map is defined as . In addition, it is assumed that the lengths of an identifier (ID), a hash output (H), a timestamp (TS), and a random number (R) are 64, 128, 32, and 128 bits, respectively. Table 4 shows the communication overhead of each protocol during the authentication and key negotiation phases. It can be concluded that the proposed scheme has the lowest communication overhead in the authentication and key negotiation processes.

Table 4.
Communication cost.
6.2. Computation Cost
According to He et al. [41], Table 5 shows the run-time of the relevant encryption operation on a . Table 6 displays the run-time of each scheme during authentication and key agreement. It is evident that the proposed scheme requires the least computational overhead.

Table 5.
Run-time of related operations.

Table 6.
Computation cost.
6.3. Performance Comparison
The results of the comparison between the proposal and related schemes [22,24,25,27,28,29] in terms of security are shown in Table 7. Compared to the existing schemes, the proposed protocol provides better security and functionality, e.g., it is resistant to attacks such as IM, MIM, and ESL while providing anonymity, mutual authentication, and PFS without key escrow issues.

Table 7.
Performance comparison.
7. Conclusions
To begin, we reviewed the existing ECC-based AKA schemes. Then, we pointed out that the existing schemes failed to provide user anonymity and PFS and had no resistance to typical attacks (such as ESL, IM, MIM, KCI, etc.) with key escrow problems. The high computational and communication costs also made some of these solutions unsuitable for resource-limited IoT. Furthermore, the security proofs were conducted in the Random-Oracle model. It is widely recognized that cryptographic schemes proven secure in the Random-Oracle model may not necessarily provide the same level of security when implemented in real-world systems. We propose a security-enhanced AKA protocol for connecting IoT devices to servers to remedy the existing challenges. The session key security of the proposed scheme is rigorously proven under the eCK model with the elliptic curve encryption computational assumptions. The session key confidentiality and authentication properties are verified with ProVerif. Based on the performance comparison, it is found that the proposed scheme offers user anonymity, PFS, mutual authentication, and resistance to typical attacks such as ESL, IM, MIM, and KCI. Additionally, the proposed scheme has minimal computational and communication overhead compared to the existing schemes.
Author Contributions
Conceptualization, S.H., S.J. and Q.M.; methodology, S.H. and F.Y.; software, W.Z.; validation, S.H. and P.D.; formal analysis, S.H. and S.J.; investigation, S.H., S.J. and Q.M.; resources, S.H.; data curation, Q.M.; writing—original draft preparation, S.H. and F.Y.; writing—review and editing, S.H., S.J., Q.M., F.Y., W.Z. and P.D.; visualization, S.H.; supervision, S.H.; project administration, S.H.; funding acquisition, S.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported in part by the Natural Science Foundation of China (No. 62072319).
Data Availability Statement
The data presented in this study are available on request from the corresponding author. The data are not publicly available due to privacy.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| AKA | Authentication key agreement |
| TA | Trusted authority |
| ECC | Elliptic Curve Cryptography |
| PUF | Physical Unclonable Function |
| CRP | Challenge–Response Pair |
| BR | Bellare and Rogaway |
| mBR | Modified BR model |
| CK | Canetti and Krawczyk |
| WBAN | Wireless body area networks |
| WSN | Wireless sensor networks |
| SG | Smart grid |
| PFS | Perfect forward security |
| IM | Impersonation |
| KCI | Key compromise impersonation |
| MIM | Man-in-the-middle |
| ESL | Ephemeral secret leakage |
References
- Tedeschi, P.; Sciancalepore, S.; Eliyan, A.; Di Pietro, R. LiKe: Lightweight Certificateless Key Agreement for Secure IoT Communications. IEEE Internet Things J. 2020, 7, 621–638. [Google Scholar] [CrossRef]
- Whitepaper, J.R. IoT The Internet of Transformation 2020. [Online]. Available online: https://www.juniperresearch.com/whitepapers/iot-the-internet-of-transformation-2020 (accessed on 14 July 2022).
- Nicanfar, H.; Hosseininezhad, S.; TalebiFard, P.; Leung, V.C. Robust privacy-preserving authentication scheme for communication between Electric Vehicle as Power Energy Storage and power stations. In Proceedings of the 2013 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Turin, Italy, 14–19 April 2013; pp. 55–60. [Google Scholar] [CrossRef]
- Showkat, D.; Som, S.; Khatri, S.K.; Ahluwalia, A.S. Security Implications in IoT using Authentication and Access Control. In Proceedings of the 2018 7th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 29–31 August 2018; pp. 689–694. [Google Scholar] [CrossRef]
- Zheng, Y.; Hu, S.; Wei, L.; Chen, Y.; Wang, H.; Yang, Y.; Li, Y.; Xu, B.; Huang, W.; Chen, L. Design and Analysis of a Security-Enhanced Three-Party Authenticated Key Agreement Protocol Based on Chaotic Maps. IEEE Access 2020, 8, 66150–66162. [Google Scholar] [CrossRef]
- Wong, K.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC’06), Taichung, Taiwan, 5–7 June 2006; Volume 1, p. 8-pp. [Google Scholar] [CrossRef]
- Wu, D.; Zhou, C. Fault-Tolerant and Scalable Key Management for Smart Grid. IEEE Trans. Smart Grid 2011, 2, 375–381. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J. Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 2016, 11, 2590–2601. [Google Scholar] [CrossRef]
- Gope, P.; Amin, R.; Hafizul Islam, S.; Kumar, N.; Bhalla, V.K. Lightweight and privacy-preserving RFID authentication scheme for distributed IoT infrastructure with secure localization services for smart city environment. Future Gener. Comput. Syst. 2018, 83, 629–637. [Google Scholar] [CrossRef]
- Aman, M.N.; Sikdar, B. ATT-Auth: A Hybrid Protocol for Industrial IoT Attestation with Authentication. IEEE Internet Things J. 2018, 5, 5119–5131. [Google Scholar] [CrossRef]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF Based Authentication and Key Exchange Protocol for IoT without Explicit CRPs in Verifier Database. IEEE Trans. Dependable Secur. Comput. 2019, 16, 424–437. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q.S. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Imam, R.; Areeb, Q.M.; Alturki, A.; Anwer, F. Systematic and Critical Review of RSA Based Public Key Cryptographic Schemes: Past and Present Status. IEEE Access 2021, 9, 155949–155976. [Google Scholar] [CrossRef]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer: Berlin/Heidelberg, Germany, 2003. [Google Scholar]
- Gura, N.; Patel, A.; Wander, A.; Eberle, H.; Shantz, S.C. Comparing Elliptic Curve Cryptography and RSA on 8-bit CPUs. In Cryptographic Hardware and Embedded Systems, Proceedings of the CHES 2004, Cambridge, MA, USA, 11–13 August 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 119–132. [Google Scholar]
- Wang, C.; Zhang, Y. New Authentication Scheme for Wireless Body Area Networks Using the Bilinear Pairing. J. Med. Syst. 2015, 39, 136. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Li, L.; Shen, J. Efficient and Anonymous Authentication Scheme for Wireless Body Area Networks. J. Med. Syst. 2016, 40, 134. [Google Scholar] [CrossRef] [PubMed]
- Seo, S.H.; Won, J.; Sultana, S.; Bertino, E. Effective Key Management in Dynamic Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2017, 10, 371–383. [Google Scholar]
- Saeed, M.E.; Liu, Q.Y.; Tian, G.; Gao, B.; Li, F. AKAIoTs: Authenticated Key Agreement for Internet of Things. Wirel. Netw. 2019, 25, 3081–3101. [Google Scholar] [CrossRef]
- Fang, D.; Qian, Y.; Hu, R.Q. A Flexible and Efficient Authentication and Secure Data Transmission Scheme for IoT Applications. IEEE Internet Things J. 2020, 7, 3474–3484. [Google Scholar] [CrossRef]
- Maurya, A.K.; Das, A.K.; Jamal, S.S.; Giri, D. Secure user authentication mechanism for IoT-enabled Wireless Sensor Networks based on multiple Bloom filters. J. Syst. Archit. 2021, 120, 102296. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Ostad-Sharif, A.; Nikooghadam, M.; Mazinani, S.M. A Secure and Efficient Key Establishment Scheme for Communications of Smart Meters and Service Providers in Smart Grid. IEEE Trans. Ind. Inform. 2020, 16, 1495–1502. [Google Scholar] [CrossRef]
- Baruah, B.; Dhal, S. An Authenticated Key Agreement Scheme for Secure Communication in Smart Grid. In Proceedings of the 2021 International Conference on COMmunication Systems NETworkS (COMSNETS), Bangalore, India, 5–9 January 2021; pp. 447–455. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Li, X.; Khan, M.K.; Jo, M. Designing Anonymous Signature-Based Authenticated Key Exchange Scheme for Internet of Things-Enabled Smart Grid Systems. IEEE Trans. Ind. Inform. 2021, 17, 4425–4436. [Google Scholar] [CrossRef]
- Yang, X.; Yi, X.; Nepal, S.; Khalil, I.; Huang, X.; Shen, J. Efficient and Anonymous Authentication for Healthcare Service with Cloud Based WBANs. IEEE Trans. Serv. Comput. 2022, 15, 2728–2741. [Google Scholar] [CrossRef]
- Shen, J.; Gui, Z.; Ji, S.; Shen, J.; Tan, H.; Tang, Y. Cloud-aided lightweight certificateless authentication protocol with anonymity for wireless body area networks. J. Netw. Comput. Appl. 2018, 106, 117–123. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Nebhan, J.; Yahya, K.; Al-Turjman, F. A Privacy Enhanced Authentication Scheme for Securing Smart Grid Infrastructure. IEEE Trans. Ind. Inform. 2022, 18, 5000–5006. [Google Scholar] [CrossRef]
- Hajian, R.; Haghighat, A.; Erfani, S. A Secure Anonymous D2D Mutual Authentication and Key Agreement Protocol for IoT. Internet Things 2022, 18, 100493. [Google Scholar] [CrossRef]
- Chen, Y.; Yin, F.; Hu, S.; Sun, L.; Li, Y.; Xing, B.; Chen, L.; Guo, B. ECC-Based Authenticated Key Agreement Protocol for Industrial Control System. IEEE Internet Things J. 2023, 10, 4688–4697. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Entity Authentication and Key Distribution. In Advances in Cryptology—CRYPTO’ 93; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1994; Volume 773, pp. 232–249. [Google Scholar]
- Blake-Wilson, S.; Johnson, D.; Menezes, A. Key agreement protocols and their security analysis. In Cryptography and Coding, Proceedings of the IMA International Conference on Cryptography and Coding, Cirencester, UK, 17–19 December 1997; Springer: Berlin/Heidelberg, Germany, 1997; Volume 1355, pp. 30–45. [Google Scholar]
- Canetti, R.; Krawczyk, H. Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels. In Advances in Cryptology-Eurocrypt 2001, Proceedings; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 453–474. [Google Scholar]
- Sun, H.; Wen, Q.; Zhang, H.; Jin, Z. A strongly secure identity-based authenticated key agreement protocol without pairings under the GDH assumption. Secur. Commun. Netw. 2015, 8, 3167–3179. [Google Scholar] [CrossRef]
- Deng, L.; Gao, R. Certificateless two-party authenticated key agreement scheme for smart grid. Inf. Sci. 2021, 543, 143–156. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the First ACM Conference on Computer and Communications Security, Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Gennaro, R.; Halevi, S.; Rabin, T. Secure hash-and-sign signatures without the random oracle. In Proceedings of the Advances in Cryptology—EUROCRYPT’99: International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Proceedings 18. Volume 1592, pp. 123–139. [Google Scholar]
- Cramer, R.; Shoup, V. A practical public key cryptosystem provably secure against adaptive chosen ciphertext attack. In Proceedings of the Advances in Cryptology—CRYPTO’98: 18th Annual International Cryptology Conference, Santa Barbara, CA, USA, 23–27 August 1998; Volume 1462, pp. 13–25. [Google Scholar]
- Canetti, R.; Goldreich, O.; Halevi, S. The random oracle methodology, revisited. J. ACM 2004, 51, 557–594. [Google Scholar] [CrossRef]
- Hu, S.; Chen, Y.; Zheng, Y.; Xing, B.; Li, Y.; Zhang, L.; Chen, L. Provably Secure ECC-Based Authentication and Key Agreement Scheme for Advanced Metering Infrastructure in the Smart Grid. IEEE Trans. Ind. Inform. 2023, 19, 5985–5994. [Google Scholar] [CrossRef]
- LaMacchia, B.; Lauter, K.; Mityagin, A. Stronger Security of Authenticated Key Exchange. In Proceedings of the 1st International Conference on Provable Security (ProvSec’07), Wollongong, NSW, Australia, 1–2 November 2007; pp. 1–16. [Google Scholar]
- He, D.; Wang, H.; Khan, M.K.; Wang, L. Lightweight anonymous key distribution scheme for smart grid using elliptic curve cryptography. IET Commun. 2016, 10, 1795–1802. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).