1. Introduction
Today, with the popularization of personal communication systems, such as cellular phones, PDAs, notebook computers, etc., and with the rapid development of the Internet of things (IoT), people can share information or transmit sensitive data by using these communication systems. There are a lot of information and communication services in the surrounding areas of human lives at present. These services are combined with various applications, for example, voice over Internet protocols, electronic commerce, distance learning, video conferencing, etc. These real-time streaming technologies provide convenience in terms of people’s instant requirement for information and communication.
The IoT provides convenience in terms of information transmission, but it is unsafe when transmitting unencrypted data via the openness of wireless communications. It is easy to be overheard without protection on such systems. For this reason, the most effective method is to encrypt the transmitted content to prevent the information from being directly known by eavesdropping. Even if the transmitted content is overheard from the channel, they will be nonsensical data. In order to achieve secure communications, cryptography is applied to protect privacy and to avoid fraud in secure communications in the IoT.
The security of the IoT can be achieved by implementing Secure Shell (SSH) and Transport Layer Security (TLS) protocols. However, they have heavy overheads that are not suitable for the resource-constrained environment of the IoT [
1]. There are three basic popular communication protocols at the IoT application level; they are the CoAP (Constrained Application Protocol), MQTT (Message Queuing Telemetry Transport), and the XMPP (Advanced Message Queuing Protocol). The MQTT protocol is the most widely used protocol for the communication of these devices in IoT systems due to its low resource requirements [
2]. Some cryptosystems have been proposed in IoT systems that communicate using the MQTT protocol, but they have not been widely accepted because of their performances [
3,
4]. For confidentiality, the cipher of an asymmetric cryptosystem, e.g., RSA, ECC, etc., is not suitable for the IoT, due to the computational load. In symmetric cryptosystems, stream ciphers outperform block ciphers because of their simple encrypting operation.
The stream cipher is a class of symmetric encryption algorithms, and it is generally much faster than block ciphers, so stream ciphers are widely used in digital communications and real-time transmissions. For the security demands of real-time communications, stream ciphers are used to meet the necessary requirements [
5,
6,
7,
8]. For example, the stream cipher A5/1 supports the confidentiality of mobile communications [
9]. Similarly, in real-time communications of the IoT, security efficiency can benefit from using stream ciphers.
At the core of stream ciphers is the keystream generator. One of the basic structures of keystream generators is the linear feedback shift register (LFSR) [
10]. For the attack of the Berlekamp-Massey algorithm, the output of the sequences of LFSRs is straightforwardly predictable. To resist this attack and spoil the linearity properties of LFSRs, there are three basic schemes that can be achieved, which include: a nonlinear combining function on the outputs of several LFSRs, a nonlinear filtering function on the contents of a single LFSR, and using the output of one (or more) LFSRs to control the clock of one or more other LFSRs, which are the clock-controlled LFSRs. All of these schemes require a nonlinear function to combine the outputs of LFSRs or control the input clock for clock-controlled LFSRs [
10,
11,
12,
13,
14]. The clock-controlled based stream cipher A5/1 uses the nonlinear majority function as the nonlinear function to promote its security. Erguler and et al. proposed a clock-controlled stream cipher with dual modes, and that has two different clocking mechanisms to provide security enhancements [
15].
Regarding the hardware of stream ciphers, a cipher with a multiple working nonlinear circuit is a strategy by which to gain the security strength of the output keystream. To further the security strength of stream ciphers, in this paper, we design a key-based multi-mode clock-controlled stream cipher for real-time secure communications using the IoT. The cipher is equipped with a multi cipher mode, depending on the secret key. The different modes are shipped with different encryption circuits depending on the user’s session key. We analyze the period, linear complexity, evaluate the randomness, and use known attacks to verify the security strength of the cipher. From the experimental results, the proposed cipher passes the FIPS PUB 140-1 and SP800-22 tests, attaining at least 97.00%. The contributions of this study can be briefly stated as follows:
The proposed scheme employs multiple working modes depending on the user’s session key.
The multiple working modes of the different working circuits include different nonlinear selecting functions and different nonlinear output combining functions.
All of the nonlinear selecting functions and output combining functions provide the balance correlation probability. It prevents weakness for attackers to break through the stream cipher.
The proposed scheme is one of hardware security, and is easy to implement using hardware.
This paper is organized as follows.
Section 2 introduces the related research regarding stream ciphers. Then, we present our proposed scheme, describe each component of the proposed stream cipher, and specify the details of the design in
Section 3. In
Section 4, we consider statistical properties and some attacks with respect to our design. In addition, we present the results regarding the period and linear complexity of our scheme.
Section 5 describes the test criteria and the experimental results for our proposed stream cipher. We use the Federal Information Processing Standards Publication 140-1 (FIPS PUB 140-1) [
16] and the Special Publication 800-22 (SP800-22) [
17] to perform the statistical tests for our scheme. Finally, we provide the conclusions in
Section 6.
3. The Proposed Scheme
To promote the randomness and the chaos of the output keystream, we propose a multi-mode keystream generator. The different working modes are dependent on the input key. In this section, we introduce the proposed stream cipher. We apply a clock-controlled stream cipher and propose a key-based multi-mode clock-controlled stream cipher. The structure of the proposed cipher is based on multi-LFSR and is equipped with multiple cipher modes to enhance security. The mode selection is dependent on the secret key bits. For each cipher mode, the output sequences have a large period and a high linear complexity. In the following subsections, we present our proposed scheme and describe each component of the proposed stream cipher. Furthermore, we specify the details of the design.
3.1. Keystream Generator
To match the AES, the proposed key-based multi-mode clock-controlled stream cipher takes a 128-bit secret key denoted
Ki, 0 ≤
i ≤ 127, and a 128-bit initialization vector denoted
IVi, 0 ≤
i ≤ 127, as its inputs. The cipher consists of four main building blocks, namely LFSRs, a clock controller, a mode controller, and an output generator. An overview of the blocks used in the stream cipher is illustrated in
Figure 4.
The size of the internal state of the proposed keystream generator is 318 bits, which consists of six LFSRs: LFSRα, LFSRβ, LFSRγ, LFSRa, LFSRb, and LFSRc, respectively. The main work of the LFSRa, LFSRb, LFSRc, and output generator is to produce the keystream. The main work of the LFSRα, LFSRβ, LFSRγ, and the nonlinear functions is to control when LFSRa, LFSRb or LFSRc, will be shifted. There are two clock operation modes in the clock controller and four output sequence generators in the output generator. They organize eight cipher operation modes. The responsibility of the mode controller is the selection of which cipher mode will operate; where the input of the mode controller is the part of secret key bits. The rightmost bits of LFSRa, LFSRb, and LFSRc are inputted to the output generator to produce the keystream.
3.2. The LFSRs
The size of the internal state of the keystream generator is 318 bits, which consists of six LFSRs, namely
LFSRα,
LFSRβ and
LFSRγ,
LFSRa,
LFSRb, and
LFSRc. The underlying
LFSRα,
LFSRβ,
LFSRγ,
LFSRa,
LFSRb, and
LFSRc are six maximum-length LFSRs of lengths 31, 17, 13, 61, 89, and 107, respectively. The primitive feedback polynomials of the registers are defined as follows [
26]:
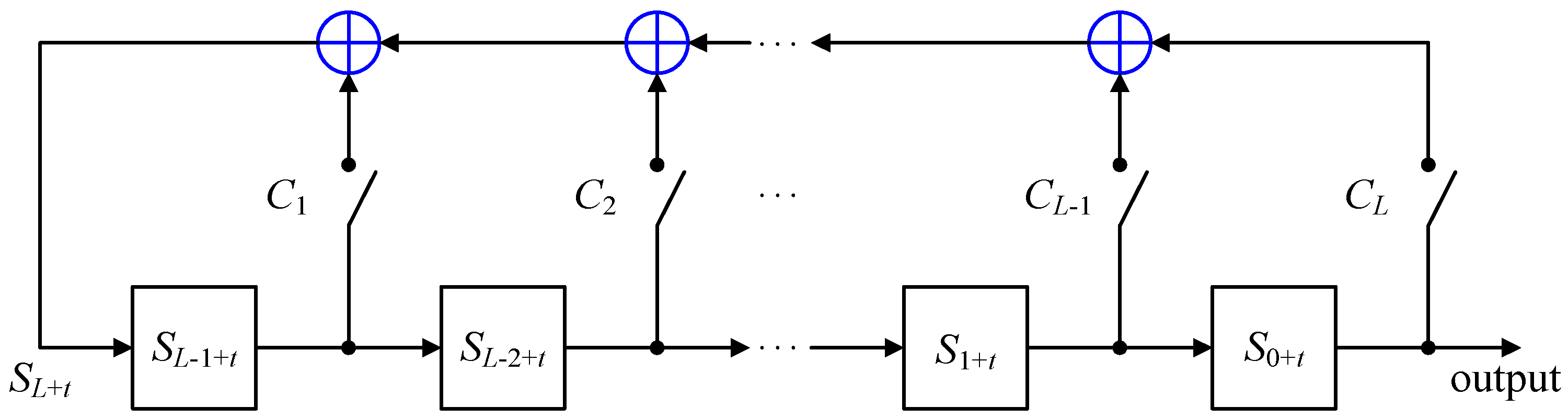
If the length of a LFSR is L and the LFSR is using the Fibonacci structure, it must be repeated L times to update each content of the register during initialization. In order to increase the efficiency of key initialization, we select different length LFSRs instead of a single LFSR. We use the Galois structure of a LFSR to speed up the operation of initialization.
3.3. Mode Controller
The responsibility of the mode controller is the selection of which cipher mode will operate in the system. We built a mode controller module, as shown in
Figure 5. There are five input signals and three output signals in the mode controller, where the inputs of the mode controller are
K0,
K1,
K2,
K3, and
K4 of the secret key and the outputs are
m0,
m1, and
m2.
The signal
m0 is taken to control which clock operation mode will be operated, and it is generated by XORing
K0,
K1,
K2,
K3, and
K4. Here, ⊕ denotes logic XOR, the Boolean function of
m0 is given by:
Another two output signals,
m1 and
m2, of the mode controller are taken to control which output sequence generator will operate. We use one of four quasigroups of Edon80 for a part of the mode controller. Since the four quasigroups are suitable for implementation, no hidden weaknesses can be imposed [
27]. The quasigroup is shown in
Table 1. We let
X be
K1K0 and let
Y be
K3K2. The value
X defines the row
r of the quasigroup, and the value
Y defines the column
c. For the data on the (
r,
c) in
Table 1, each
r and
c has a two-bit length, respectively. The result of (
r,
c) is a two-bit length, too. Then, we take the result of (
r,
c) to control which output sequence generator will operate.
In the hardware implementation, to reduce the gate numbers in order to store the quasigroup table, we use the Boolean functions and map the quasigroup table to logic [
28]. Here, ⊕ denotes logic XOR and…denotes logic AND. The output signals
m1 and
m2 are computed by the Boolean functions as follows:
Finally, we obtain the logic circuit to implement the mode controller. The circuit of the mode controller is shown in
Figure 6.
3.4. Clock Controller
The main work of the LFSRa, LFSRb, LFSRc, and output generator is to produce the keystream. The respective rightmost bits of LFSRa, LFSRb, and LFSRc are inputted into the output generator to produce the keystream, but the respective clock pulses of these three LFSRs are dependent on the clock controller. There are two clock operation modes in the clock controller, which are mode 0 and mode 1. Which outputs of the two modes will be outputted is determined according to the output signal m0 of the mode controller. If m0 = 0, then the outputs of mode 0 are outputted. On the other hand, if m0 = 1, then the outputs of mode 1 are outputted.
The clock controller consists of three LFSRs and some nonlinear Boolean functions. The three LFSRs are LFSRα, LFSRβ, and LFSRγ, and the respective rightmost bits of these LFSRs are inputted into nonlinear Boolean functions, and then the outputs of the nonlinear Boolean functions are used to control whether LFSRa, LFSRb, or LFSRc will be shifted. It means the clock controller controls respective clock pulses of the LFSRa, LFSRb, and LFSRc. We describe how the clock controller controls the respective clock pulses of the LFSRa, LFSRb, and LFSRc.
First, the respective rightmost bits of the
LFSRα,
LFSRβ, and
LFSRγ are denoted by
α0t,
β0t, and
γ0t, respectively, at time
t. They are inputted into the
fmaj function and the
fand function, which are given by:
where, +denotes logic OR and⋯denotes logic AND. For the mode of
m0 = 0, then
fmaj function is selected. If
α0t =
fmaj, then
LFSRa is shifted. While
β0t =
fmaj and
γ0t =
fmaj, then
LFSRb and
LFSRc are shifted, respectively. Similarly, for another mode of
m0 = 1, the
fand function will be selected. If
α0t =
fand, then
LFSRa is shifted. While
β0t =
fand and
γ0t =
fand, then
LFSRb and
LFSRc are shifted, respectively. According to the above, we define
clkai,
clkbi, and
clkci as the clocking condition of
LFSRa,
LFSRb, and
LFSRc, respectively, where
i ∊ {0, 1}. For the mode of
m0 = 0, then
clka0,
clkb0, and
clkc0 are selected. If
clka0 = 1, then
LFSRa is shifted. While
clkb0 = 1 and
clkc0 = 1, then
LFSRb and
LFSRc are shifted, respectively. On the other hand, for the mode of
m0 = 1, then
clka1,
clkb1, and
clkc1 are selected. If
clka1 = 1, then
LFSRa is shifted. While
clkb1 = 1 and
clkc1 = 1, then
LFSRb and
LFSRc are shifted, respectively.
Next, we build two truth tables for the clocking conditions of the three LFSRs,
LFSRa,
LFSRb, and
LFSRc, which are shown in
Table 2 and
Table 3. Then, we can simplify
clka0,
clkb0, and
clkc0 into Boolean functions for clock operation mode 0, as well as
clka1,
clkb1, and
clkc1 for clock operation mode 1. The simplified Boolean functions of the two clock operation modes are shown as follows:
At each clock cycle, only one of the two clock operation modes will determine whether the LFSRa, LFSRb, or LFSRc are shifted or not, since the signal m0 is taken to switch which outputs of clock operation mode will output. Furthermore, each rightmost bit of LFSRa, LFSRb, and LFSRc will input to the output generator to generate the keystream.
3.5. Output Generator
The output generator takes sequence
a0t,
b0t, and
c0t as its input, which are the respective rightmost bits of
LFSRa,
LFSRb, and
LFSRc at time
t. There are four output sequence generators in the output generator. The sequence outputs are denoted by
z0t,
z1t,
z2t and
z3t. According to the selected mode, the output signals
m1 and
m2 of the mode controller are taken to control which output sequence generator will operate. For example, if
m2 = 0 and
m1 = 0, then output sequence generator 0 (OSG
0) will be operated, and so on.
Table 4 lists the operating conditions under
m2 and
m1.
The output sequence generators are given as follows:
Output Sequence Generator 0 (OSG
0): In this generator, we use exclusive-or operation with
a0t,
b0t, and
c0t to produce keystream
z0t, which is given by:
The output-inputs correlation probability of OSG
0 is demonstrated in
Table 5. All correlations between inputs and output are both 1/2.
Output Sequence Generator 1 (OSG
1): In this generator, we use two Dawson’s summation generators to produce the keystream. The diagram of Dawson’s summation generator (DSG) is shown in
Figure 7 and the functions are defined as follows [
29]:
Here
aj,
bj, and
cj−1 denote the input sequences of DSG, and
cj−1 is
cj delayed one clock. The initial state of the bit,
cj−1, is defined to be zero. In addition, the DSG has high resistance against correlation attacks [
29], due to all its output-inputs correlation probabilities being ½, as demonstrated in
Table 6.
In
Figure 1, we use two DSGs to generate keystream
z1t. The diagram of OSG
1 is shown in
Figure 8. The functions can be written as follows:
The initial state of the bits,
ft−1 and
et−1, are defined to be zero and the output function of the OSG
1 can be sorted as follows:
We also sort the respective correlation probabilities of the output-inputs, output-
dt and output-
et, of OSG
1. All of them are equal to 1/2, which is demonstrated in
Table 7.
Output Sequence Generator 2 (OSG
2): The OSG
2 is shown in
Figure 9. In this generator, we build a hybrid carry bit
gt and merge it with DSG to generate keystream
z2t, which can be defined as follows:
The initial state of the bits,
gt−1, is defined to be zero. All of the correlation probabilities of the output-inputs and the output-
gt of OSG
2 are equal to 1/2, which are demonstrated in
Table 8.
Output Sequence Generator 3 (OSG
3): The OSG
3 is shown in
Figure 10. In this generator, we establish another hybrid carry bit
ht, and output functions then merge them with DSG to generate keystream
z3t; which can be defined as follows:
The initial state of the bits,
ht−1, is defined to be 0. The correlation probabilities of the output-inputs and the output-
ht of OSG
3 are both 1/2, which are demonstrated in
Table 9.
3.6. Key/IV Setup
The inputs of the keystream generator are called seeds. The requirements of these seeds are that they must be random and unpredictable before generating the keystream. For this reason, we must use the key initialization procedure to perform the requirement. In this subsection, we describe the computation of the initial inner state before starting the keystream generation. First, part bits of the secret key are collaterally loaded into the 318-bit initial state of the cipher. Then, the remaining bits of the secret key and the 128-bit initialization vector are fed into the 318-bit initial state of the cipher using the key initialization procedure. We generalize the Key/IV Setup into two phases, the initial filling phase and the key initialization procedure phase. It works as follows.
3.6.1. Initial Filling Phase
The 128-bit secret key
K is denoted by
K =
K0, …,
K127 and the 128-bit initialization vector
IV is denoted by
IV =
IV0, …,
IV127. The internal states of
LFSRα,
LFSRβ, and
LFSRγ are denoted by
αi,
βI, and
γI, respectively, where:
The internal states of
LFSRa,
LFSRb, and
LFSRc are denoted by
ai,
bi, and
ci, respectively, where:
The initial filling of each LFSR is carried out as follows:
Notice that only part bits of the secret key are collaterally loaded into the 318-bit initial state of the cipher. The 38-bit secret key and 128-bit initialization vector have not been used yet.
3.6.2. Key Initialization Procedure Phase
After part bits of the 128-bit secret key are collaterally loaded into the 318-bit initial state of the cipher, the remaining 38-bit secret key and the 128-bit initialization vector are fed into the cipher using the key initialization procedure, which is described in
Figure 11. We must use 166 cycles to perform this procedure. Here, we use the parameters
seedαt,
seedβt, and
seedγt to denote the remaining bits of the secret key and the initialization vector, for 0 ≤
t ≤ 165. The parameters
seedαt,
seedβt, and
seedγt are given as follows:
During the key initialization procedure, the respective rightmost bits of LFSRa, LFSRb, and LFSRc are still inputted to OSG1, OSG2, and OSG3. The output sequences z1t, z2t, and z3t of OSG1, OSG2, and OSG3, respectively, are fed back and XORed with seedαt, seedβt, and seedγt, respectively, into the leftmost bit of LFSRα, LFSRβ, and LFSRγ in parallel, where 0 ≤ t ≤ 165. Note that there is no bit of the keystream output during this initialization procedure, and each LFSR is clocked 166 times using the clk clock. It means that each LFSR is clocked in the normal way by ignoring the clocking controller.
4. Security Properties
The long period, high linear complexity, and good statistical properties are three of the basic requirements for pseudorandom binary sequences in cryptographic applications. In this section, we consider the period, linear complexity, statistical properties, and some attacks with respect to our design. Due to the proposed scheme, the multi-clocking keystream generator and the periods of each LFSR affect each other by current states. We provide the mathematical results regarding the period and linear complexity of our scheme.
4.1. Period
One of the important attributes to be considered for a stream cipher is the period of the keystream. The period of a keystream s = s0, s1, s2, … is the smallest positive integer N if si = si+N for all i ≥ 0. If the period of the keystream is too short, it will result in different parts of the plaintext being encrypted in the identical bits of the keystream. The long period can avoid the keystream being reused when encrypting long plaintexts.
In our scheme, the internal state of the proposed cipher consists of
LFSRα,
LFSRβ,
LFSRγ,
LFSRa,
LFSRb, and
LFSRc, and all of these LFSRs are six maximum-length LFSRs of lengths 31, 17, 13, 61, 89, and 107, respectively. The respective periods of
LFSRα,
LFSRβ,
LFSRγ,
LFSRa,
LFSRb, and
LFSRc are denoted as
Pα,
Pβ,
Pγ,
Pa,
Pb, and
Pc, respectively, and they are equal to 2
31 − 1, 2
17 − 1, 2
13 − 1, 2
61 − 1, 2
89 − 1, and 2
107 − 1, respectively. Notice that all of these periods are prime numbers. The main work of
LFSRa,
LFSRb, and
LFSRc is to produce the keystream, but their respective clock pulses are dependent on the clock controller. The clock controller consists of
LFSRα,
LFSRβ,
LFSRγ, and some nonlinear Boolean functions, and its output sequences
clkai,
clkbi, and
clkci, where
i ∊ {0, 1}, are taken to control the respective clock pulses of
LFSRa,
LFSRb, and
LFSRc. It means the periods of
LFSRa,
LFSRb, and
LFSRc will be affected by the periods of
clkai,
clkbi, and
clkci. Let us define the periods of
clkai,
clkbi, and
clkci as
Pclkai,
Pclkbi, and
Pclkci, respectively. The periods
Pclkai,
Pclkbi, and
Pclkci can be written as [
30]:
where
lcm(·) denotes the function of the least common multiple. Since all of the periods
Pα,
Pβ, and
Pγ are prime numbers,
Pclkai,
Pclkbi, and
Pclkci can be simplified to:
Next, the sequences
clkai,
clkbi, and
clkci are taken to control the respective clock pulses of the
LFSRa,
LFSRb, and
LFSRc. If
clkai = 1 and the
clk edge trigger simultaneously occurs, then
LFSRa is shifted, and for
LFSRb and
LFSRc. Let us define
Sa,
Sb, and
Sc as the number of 1’s in the sequences
clkai,
clkbi, and
clkci, respectively, in every period. The
Ta,
Tb, and
Tc represent affected periods of
LFSRa,
LFSRb, and
LFSRc, respectively. Thus, the periods
Ta,
Tb, and
Tc can be written as [
15]:
Since all of the periods
Pa,
Pb, and
Pc are prime numbers, and they are greater than
Sa,
Sb, and
Sc, respectively, it means gcd(
Sk;
Pk) = 1 for
k ∊ {
a;
b;
c}. Thus,
Ta,
Tb, and
Tc can be simplified to:
Finally, the output generator takes the respective rightmost bits of
LFSRa,
LFSRb, and
LFSRc as its input to generate the keystream. The period
Tz of the keystream can be written as follows:
It can be seen that, for the period of our proposed method, each cipher is high by considering the security requirements for each cipher mode.
4.2. Linear Complexity
Any periodic sequence can be generated by a Linear Feedback Shift Register (LFSR), since a linear recurrence (or a characteristic polynomial) can be implemented by using a LFSR. Given a periodic sequence, the Berlekamp-Massey algorithm [
31] can be used to calculate this recurrence and linear complexity. The length of the shortest recurrence is defined as the linear complexity of a periodic sequence.
The linear complexity is also defined as the size of the shortest LFSR, which can reproduce the same sequence as the given sequence. If the keystream has a linear complexity LC = n, it can be reconstructed by a LFSR after examining only 2n bits of the keystream. Once the LFSR is generated by the attacker, they can break the stream cipher. Therefore, the high linear complexity of the keystream is a necessary condition and very important for the design of stream ciphers. The high linear complexity of a keystream means that it possesses higher non-predictability.
According to the Beth-Piper stop-and-go generator and the Gollmann cascade stop-and-go generator in [
30], we can provide the lower bound of the linear complexity of our scheme. For our scheme, we use the clock controller to control the respective clock pulses of the
LFSRa,
LFSRb, and
LFSRc. Their respective clock pulses are dependent on the output sequences
clkai,
clkbi, and
clkci of the clock controller, where
i ∊ {0, 1}. We use
Pclkai,
Pclkbi, and
Pclkci to represent the respective periods of
clkai,
clkbi, and
clkci. The primitive feedback polynomials of LFSR
1, LFSR
2, and LFSR
3 have degrees of
La,
Lb, and
Lc, respectively. The lower bound of the linear complexity
LC of the proposed cipher can be written as follows:
The linear complexity
LC and characteristic polynomial of a keystream can be computed by the Berlekamp-Massey algorithm to obtain the linear complexity
LC and characteristic polynomial of the keystream which costs approximately
O(
LC2) [
32].
The requirement of the linear complexity of the stream cipher is determined by different security levels. For example, when the computation cost of a stream cipher is required equal to the security strength of AES, it must to be approximately equal to
O(2
128). For our scheme, the linear complexity
LC of the proposed stream cipher is approximately equal to 2
69. According to the above, the computation cost of the proposed cipher can be written as follows:
It can be seen that the computation cost of our proposed cipher satisfies the security strength of AES, being even stronger than AES.
4.3. Statistical Properties
Good statistical properties for randomness are one of the basic important requirements for stream ciphers. The keystream of a good stream cipher not only has the feature of non-predictability, but also has good statistical properties for randomness. So, to implement a stream cipher, the capability to perform statistical tests for randomness must be incorporated. Randomness testing of random and pseudorandom number generators is used in many cryptographic, modeling, and simulation applications. The National Institute of Standards and Technology (NIST) has developed different criteria that may be employed to investigate the randomness of cryptographic applications.
In order to evaluate the randomness of the proposed keystream, we use the Federal Information Processing Standards Publication 140-1 (FIPS PUB 140-1) [
16] and the Special Publication 800-22 (SP800-22) [
17] to perform the statistical tests for our scheme. They are also issued by the NIST, where the FIPS PUB 140-1 standard is the security requirement for cryptographic modules and the SP800-22 is a statistical test suite for random and pseudorandom number generators for cryptographic applications.
For the FIPS PUB 140-1 standard, there are four test types in the random tests. The specifications of the recommended tests are based on a single bit stream of 20,000 consecutive output bits. To perform the FIPS PUB 140-1 tests, we sampled 100 different keystreams which were generated by 100 random keys and 100 random initialization vectors. Each keystream was a single bit stream of length 20,000 bits. The proposed cipher passed the FIPS PUB 140-1 tests by a proportion of at least 97.00%.
Furthermore, for the SP800-22 statistical test suite, there are fifteen test types in the statistical tests that were developed to test the randomness of binary sequences. These tests focus on a variety of different types of non-randomness that could exist in a sequence. For the SP800-22 statistical test suite, we sampled 100 different keystreams under the 100 secret keys, and initialization vectors were randomly chosen. Each sample was 10,000,000 bits in length. The proposed cipher passed the SP800-22 tests by a proportion of at least 98.00%, with a significance level of 0.01.
4.4. Time-Memory-Data Tradeoff Attack
In 1980, Hellman introduced a general technique for breaking arbitrary block ciphers called a time-memory tradeoff attack. It can also be generalized to the general problem of inverting one-way functions. Babbage and Golić, and later, Biryukov, Shamir, and Wagner, pointed out that a different tradeoff attack called a time-memory-data tradeoff attack is applicable to stream ciphers. Several stream ciphers have been broken by time-memory-data tradeoff attacks, including the famous GSM encryption scheme A5/1 [
31].
The time-memory-data tradeoff attack consists of two phases; i.e., the pre-computation phase and the online phase. In the pre-computation phase, the attacker builds large tables relating to the behavior of the system in question. During the online phase, the attacker obtains actual data produced from an unknown key, and his goal is to use the pre-computed tables to find the key as quickly as possible. There are five parameters for any time-memory-data tradeoff attack [
33,
34]:
- -
N denotes the size of the search space
- -
P denotes the time required for the pre-computation phase
- -
M denotes the size of memory used to store the pre-computed tables
- -
T denotes the time required for the online phase
- -
D denotes the amount of output data available to the attacker
The requirement for the attack is that T and M should be smaller than N, since the sum or maximum of T and M is usually signified by the complexity of the time-memory-data tradeoff attack.
For the Babbage-Golić tradeoff attack described in [
34], it assumes that the size of the internal state of the stream cipher in
N bits and
D different keystreams of length log
N are given. The goal of this attack is to recover one of the internal states from any one of the given keystreams. Once a state is found, the corresponding internal states are derived from the rest of the plaintext by running the generator forwards from this known state. For this time-memory-data tradeoff attack, the memory requirement is
M =
N/
D. It suffices to search the entries in the table
D times and the time complexity is
T =
D with the pre-computation time
P =
M. By ignoring some of the available data, the
T can be reduced from
T towards 1, and thus, generalize the tradeoff to
TM =
N and
P =
M for any 1 ≤
T ≤
D.
T =
M constitutes an attack of
T =
M =
D =
N1/2.
Another enhanced tradeoff attack, as described in [
34], was presented by Biryukov and Shamir. This attack combined the works of Hellman and Babbage-Golić to launch a new time-memory-data tradeoff attack on steam ciphers. It assumed that the internal state could take
N different values. As with the work of Babbage-Golić, the aim of this attack is to recover any one of the many internal states of the stream cipher for
D different keystreams that are given. In the tradeoff attack by Biryukov-Shamir, the parameters of which satisfy the relation
P =
N/
D and
TM2D2 =
N2 for 1 ≤
T ≤
D.
T =
M =
N1/2 with
D =
N1/4 constitutes an attack.
In fact, Babbage suggested that a secret key length of k bits is required and a state size of at least 2k bits is required as a design principle of stream ciphers. Similarly, Golić stated that a simple way of increasing security is to make the internal memory size larger.
According to the above, we know the time-memory-data tradeoff attack can be applied when the state size of the stream cipher is too small. A necessary condition on the state size of a stream cipher is that it has to be at least two times the secret key length. For our scheme, the proposed stream cipher takes the 128-bit secret key. In order to avoid time-memory-data tradeoff attacks, the size of the internal state must to be at least 256. However, the size of the internal state of the proposed cipher is 318 bits, which means that the size of the search space N = 2318 > 2256. This gives T = M = D = N1/2 = 2159 for the Babbage-Golić tradeoff and T = M = N1/2 = 2159, D = N1/4 = 279.5 for the Biryukov-Shamir tradeoff attack, respectively. The results show that they are not better than an exhaustive key search, so the proposed stream cipher can resist against these attacks.
4.5. Correlation Immunity Properties
Correlation immunity as a measure of resistance against ciphertext-only correlation attacks in stream ciphers was defined by Siegenthaler [
35]. As shown in
Figure 12, there is a nonlinear function
f with
n input sequences
x = {
x0,
x1, …,
xn−1}. If the correlation between output sequence
z and
m input sequences is statistically independent, then the function has correlation immunity of order
m, where
m ≤
n. Therefore, the mutual information between the output sequence
z and any subset of
m input sequences is zero.
The
m-th order correlation immune function
f with
n input sequences is defined as follows:
where the
xi1,
xi2, …,
xim denote the input variables for 0 ≤
i1 <
i2 < … <
im ≤
n − 1, and (
s1,
s2, …,
sm) ∊ {0, 1}
m. If
f is balanced, prob[
f(
x) = 1] = prob[
f(
x) = 0] = 1/2, then
f is also called the
m-resilient function.
For our scheme, we proposed four output sequence generators (OSGs) to produce the keystream, which was described in
Section 3.5. The four OSGs consist of nonlinear Boolean functions, except OSG
0. All of these OSGs satisfy the properties of being balanced and correlation immune of order one. The four OSGs, namely OSG
0, OSG
1, OSG
2, and OSG
3, take sequence
a0t,
b0t, and
c0t as their inputs, and their output sequences are denoted by
z0t,
z1t,
z2t, and
z3t, respectively. All of the output-inputs correlation probabilities of each OSG are listed as follows:
where
dt and
et are carry bits of Dawson’s method in OSG
1,
gt and
ht are respective hybrid carry bits of OSG
2 and OSG
3. After delaying one clock, they are fed back as extra inputs of OSG
1, OSG
2, and OSG
3, respectively.
It is apparent that the output bit is uncorrelated to all the individual input bits for each OSG. The proposed stream cipher is deemed secure and it can resist against some correlation attacks.
6. Conclusions
In this paper, we proposed a key-based multi-mode clock-controlled stream cipher to enhance the security of stream ciphers. The proposed multi-mode depended on the secret key. The different modes were shipped with different encrypting circuits depending on the user’s session key. We also analyzed the period, linear complexity, and used known attacks to verify the security strength of the cipher.
We presented the mathematical results regarding the period and linear complexity of the proposed cipher. The results showed that the period of the proposed stream cipher was enough to consider the security requirements for each cipher mode. On the other hand, the linear complexity of the proposed stream cipher satisfied the security strength of AES, and was even stronger than AES. For good statistical properties for randomness, the proposed cipher passed the FIPS PUB 140-1 tests by a proportion of at least 97.00% and passed the SP800-22 test suite by a proportion of at least 98.00%. The experimental results showed that the proposed stream cipher possessed a considerably good randomness property. Regarding security, the proposed cipher could resist against time-memory-data tradeoff attacks and some correlation attacks. In terms of the confidentiality of the IoT, the stream cipher outperformed other symmetric ciphers and asymmetric ciphers. Our proposed stream cipher with a multiple-mode encryption scheme could be applied to the actual IoT environment and promotes the security strength of ciphers.
LFSRs have the advantage of high operation speeds in hardware security. The eight operation modes and the output of 1-bit per clock in the proposed scheme represent its limitations, but these could be ingeniously extended. To elasticize the stream cipher, the designs of an optimized structure for secure hardware circuits will be an interesting research direction. Furthermore, the application of these circuits when merged with cellular automata, chaos, and multi-mode operations represent potential future works.