Secure Information Sharing Approach for Internet of Vehicles Based on DAG-Enabled Blockchain
Abstract
:1. Introduction
- We propose an information sharing approach for IoV to provide a secure and efficient environment for information sharing between vehicles. In contrast to the DAG and consortium blockchain methods currently used in IoV networks, our proposed framework is completely decentralized and does not depend on centralized infrastructures to add transactions to the blockchain.
- We propose a lightweight DAG framework that uses DDB-TSA as tip selection algorithm to meet the time-sensitive requirements of the highly dynamic IoV environment. The proposed tip selection algorithm considers driving decisions, realizes rapid consensus, and increases the correlation between shared information. Through mathematical analysis, it is proved that the proposed lightweight DAG framework is feasible.
- A reputation-based rate control strategy is designed to resist parasitic chain attacks. Unlike the existing rate control strategy, the rate control strategy proposed in this paper will not affect the benign vehicle release sites. However, it can well prevent malicious vehicles from releasing many malicious sites to undermine the security of the DAG system. Experimental analysis shows that the proposed DDB-TSA and reputation-based rate control strategy achieve secure and efficient information sharing.
2. Related Work
3. Information Sharing Approach
3.1. Approach Overview
3.1.1. Information Extracting and Site Generation
3.1.2. Information Verifying and Appending
3.1.3. Information Sharing among Vehicles
- Local Information Sharing: Local information sharing refers to information shared in the same region. Each region usually contains multiple RSUs to cache and synchronize the local DAG ledger. Intelligent vehicles can check and exploit the ledger stored at their surrounding RSUs to make decisions.
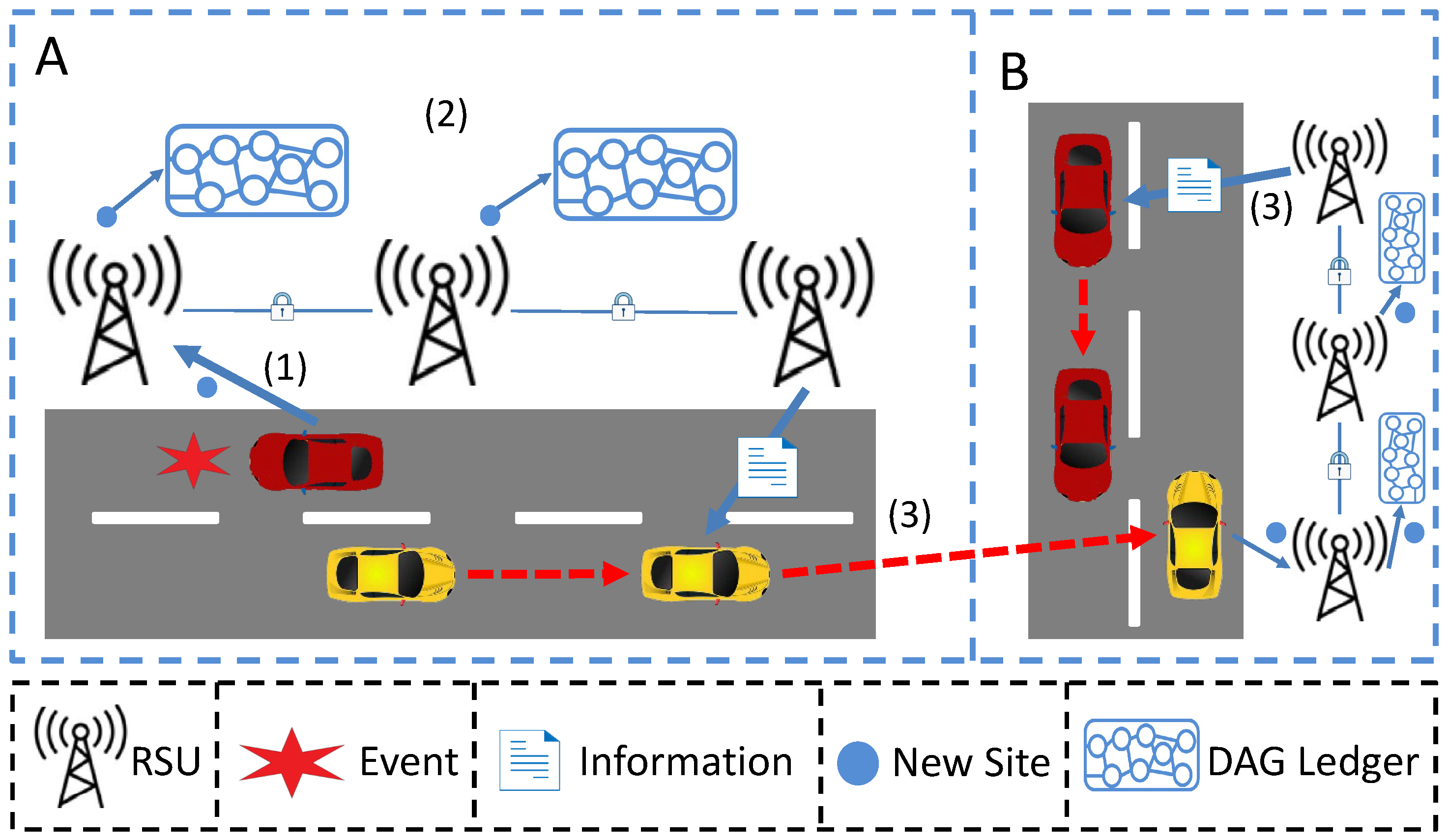
- Cross Region Information Sharing: Due to the large-scale characteristics of vehicular networks, information sharing among vehicles is more inclined to cross-region information sharing. Therefore, to ensure the trust and reliability of the shared information, it is crucial to design an identity authentication approach for those cross-region vehicles. Existing methods use identity tokens for the verification process [32], introducing extra storage consumption for information sharing. Therefore, we design a new identity authentication approach for cross-region vehicles, and the details are as follows. At first, we design a special site during the authentication process, i.e., cross-region site . The format of is expressed ashere, w is a number larger than 1 (e.g., 5). According to Equation (3), it is easier for this site to obtain approval from other sites with a large weight. In each region, RSUs maintain the DAG ledger, as illustrated in Figure 1, considering a cross-region scenario that vehicle z leaves region A to region B. If RSUs in region A decide to share some information with region B, they send it to y the cross-region site and sign with their private key, which I contains the information to be shared. As shown in Figure 1, the RSUs in this region encapsulate the valuable information to be shared in a site and send the site to vehicles with higher reputation values that are about to cross regions. After arriving at another area, the vehicle will send the site to the nearby RSUs. After the site joins the DAG Ledger, the cross-region information sharing is completed.
3.2. Security Analysis and Threat Model
3.2.1. Lazy Workers
3.2.2. Malicious Information Attack
3.2.3. Splitting Attack
3.2.4. The Ledger Convergence
3.2.5. Parasite Chain Attack
3.2.6. Long Confirmation Delay
4. Lightweight DAG for Information Sharing
4.1. The DDB-TSA
4.2. The VFC
4.3. The Ledger Convergence
4.4. Parasitic Chain Attack Defense
Reputation-Based Rate Control Strategy
| Protocol 1 Reputation Value Management Smart Contrast |
|
5. Performance Evaluation
5.1. Comparison of the proposed DDB-TSA and RBRCS
5.1.1. TSA Comparison
5.1.2. RCS Comparison
5.2. Performance of the Proposed DAG-Enabled Blockchain
5.2.1. Tip Chosen Delay
5.2.2. Confirmation Delay of Sites
5.2.3. Ledger Convergence
5.2.4. Parasitic Chain Attack Protection Simulation
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zhang, L.; Luo, M.; Li, J.; Au, M.H.; Choo, K.K.R.; Chen, T.; Tian, S. Blockchain based secure data sharing system for Internet of vehicles: A position paper. Veh. Commun. 2019, 16, 85–93. [Google Scholar]
- Hassan, M.A.; Javed, A.R.; Hassan, T.; Band, S.S.; Sitharthan, R.; Rizwan, M. Reinforcing Communication on the Internet of Aerial Vehicles. IEEE Trans. Green Commun. Netw. 2022, 6, 1288–1297. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet Things J. 2018, 6, 4660–4670. [Google Scholar] [CrossRef]
- Xiong, K.; Leng, S.; Huang, C.; Yuen, C.; Guan, Y.L. Intelligent task offloading for heterogeneous V2X communications. IEEE Trans. Intell. Transp. Syst. 2020, 22, 2226–2238. [Google Scholar] [CrossRef]
- Rahman, S.A.; Tout, H.; Talhi, C.; Mourad, A. Internet of Things Intrusion Detection: Centralized, On-Device, or Federated Learning? IEEE Netw. 2020, 34, 310–317. [Google Scholar] [CrossRef]
- Kumaran, A.; Tyagi, A.K.; Kumar, S.P. Blockchain Technology for Securing Internet of Vehicle: Issues and Challenges. In Proceedings of the 2022 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 25–27 January 2022; IEEE: New York, NY, USA, 2022; pp. 1–6. [Google Scholar]
- Liu, W.; Watanabe, Y.; Shoji, Y. Vehicle-assisted data delivery in smart city: A deep learning approach. IEEE Trans. Veh. Technol. 2020, 69, 13849–13860. [Google Scholar] [CrossRef]
- Kamal, M.; Srivastava, G.; Tariq, M. Blockchain-based lightweight and secured v2v communication in the internet of vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 22, 3997–4004. [Google Scholar] [CrossRef]
- Javed, A.R.; Hassan, M.A.; Shahzad, F.; Ahmed, W.; Singh, S.; Baker, T.; Gadekallu, T.R. Integration of blockchain technology and federated learning in vehicular (iot) networks: A comprehensive survey. Sensors 2022, 22, 4394. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, J.; Zhao, H.; Wang, P.; Kato, N. Blockchain-based trust management for internet of vehicles. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1397–1409. [Google Scholar]
- Yang, Z.; Wang, R.; Wu, D.; Yang, B.; Zhang, P. Blockchain-enabled trust management model for the Internet of Vehicles. IEEE Internet Things J. 2021, 9, 616–632. [Google Scholar] [CrossRef]
- Chai, H.; Leng, S.; Wu, F. Secure Knowledge Sharing in Internet of Vehicles: A DAG-Enabled Blockchain Framework. In Proceedings of the ICC 2021—IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; IEEE: New York, NY, USA, 2021; pp. 1–6. [Google Scholar]
- Popov, S.; Moog, H.; Camargo, D.; Capossele, A.; Dimitrov, V.; Gal, A.; Greve, A.; Kusmierz, B.; Mueller, S.; Penzkofer, A.; et al. The coordicide. 2020. Available online: https://files.iota.org/papers/20200120_Coordicide_WP.pdf (accessed on 30 January 2020).
- Conti, M.; Kumar, G.; Nerurkar, P.; Saha, R.; Vigneri, L. A survey on security challenges and solutions in the IOTA. J. Netw. Comput. Appl. 2022, 203, 103383. [Google Scholar]
- Cullen, A.; Ferraro, P.; Sanders, W.; Vigneri, L.; Shorten, R. Access control for distributed ledgers in the internet of things: A networking approach. IEEE Internet Things J. 2021, 9, 2277–2292. [Google Scholar] [CrossRef]
- Zhao, L.; Vigneri, L.; Cullen, A.; Sanders, W.; Ferraro, P.; Shorten, R. Secure Access Control for DAG-based Distributed Ledgers. IEEE Internet Things J. 2021, 9, 10792–10806. [Google Scholar] [CrossRef]
- Attias, V.; Vigneri, L.; Dimitrov, V. Preventing denial of service attacks in IoT networks through verifiable delay functions. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; IEEE: New York, NY, USA, 2020; pp. 1–6. [Google Scholar]
- Zhong, C.; Liu, K.; Liang, Z.; Huang, Y.; Xiong, F.; Guo, Z. Research on Data Security Sharing in Blockchain: Challenges and Prospects. In Proceedings of the 2022 IEEE International Conference on Electrical Engineering, Big Data and Algorithms (EEBDA), Changchun, China, 25–27 February 2022; IEEE: New York, NY, USA, 2022; pp. 1322–1327. [Google Scholar]
- Lin, K.; Li, Y.; Deng, J.; Pace, P.; Fortino, G. Clustering-learning-based long-term predictive localization in 5G-envisioned Internet of connected vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 22, 5232–5246. [Google Scholar]
- Ruta, M.; Scioscia, F.; Gramegna, F.; Ieva, S.; Di Sciascio, E.; De Vera, R.P. A knowledge fusion approach for context awareness in vehicular networks. IEEE Internet Things J. 2018, 5, 2407–2419. [Google Scholar] [CrossRef]
- Chen, X.; Leng, S.; He, J.; Zhou, L. Deep-learning-based intelligent intervehicle distance control for 6G-enabled cooperative autonomous driving. IEEE Internet Things J. 2020, 8, 15180–15190. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Li, J.; Zhang, N.; Zhang, K.; Choo, K.K.R.; Liu, Y. Blockchain-based secure and cooperative private charging pile sharing services for vehicular networks. IEEE Trans. Veh. Technol. 2021, 71, 1857–1874. [Google Scholar] [CrossRef]
- Kakkar, R.; Gupta, R.; Agrawal, S.; Tanwar, S.; Sharma, R. Blockchain-based secure and trusted data sharing scheme for autonomous vehicle underlying 5G. J. Inf. Secur. Appl. 2022, 67, 103179. [Google Scholar] [CrossRef]
- Cui, J.; Ouyang, F.; Ying, Z.; Wei, L.; Zhong, H. Secure and efficient data sharing among vehicles based on consortium blockchain. IEEE Trans. Intell. Transp. Syst. 2021, 23, 8857–8867. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.; Xu, Q.; Zhang, N. LVBS: Lightweight vehicular blockchain for secure data sharing in disaster rescue. IEEE Trans. Dependable Secur. Comput. 2020, 19, 19–32. [Google Scholar] [CrossRef]
- Popov, S. The tangle. White Paper. 2018, 1. Available online: https://assets.ctfassets.net/r1dr6vzfxhev/2t4uxvsIqk0EUau6g2sw0g/45eae33637ca92f85dd9f4a3a218e1ec/iota1_4_3.pdf (accessed on 30 April 2018).
- Chafjiri, F.S.; Mehdi Esnaashari Esfahani, M. An Adaptive Random Walk Algorithm for Selecting Tips in the Tangle. In Proceedings of the 2019 5th International Conference on Web Research (ICWR), Tehran, Iran, 24–25 April 2019; pp. 161–166. [Google Scholar] [CrossRef]
- Aghania, M. Hybrid tip Selection Algorithm in IOTA. Ph.D. Thesis, Deptartment of Mathematics, University of Lethbridge, Lethbridge, AB, Canada, 2022. [Google Scholar]
- Lu, Y.; Huang, X.; Zhang, K.; Maharjan, S.; Zhang, Y. Blockchain empowered asynchronous federated learning for secure data sharing in internet of vehicles. IEEE Trans. Veh. Technol. 2020, 69, 4298–4311. [Google Scholar] [CrossRef]
- Cullen, A.; Ferraro, P.; King, C.; Shorten, R. On the resilience of DAG-based distributed ledgers in IoT applications. IEEE Internet Things J. 2020, 7, 7112–7122. [Google Scholar]
- Liu, Y.; Wang, Y.; Chang, G. Efficient privacy-preserving dual authentication and key agreement scheme for secure V2V communications in an IoV paradigm. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2740–2749. [Google Scholar]
- Liao, Y.; Wang, M.; Duan, L.; Chen, F. Cross-regional driver–vehicle interaction design: An interview study on driving risk perceptions, decisions, and ADAS function preferences. IET Intell. Transp. Syst. 2018, 12, 801–808. [Google Scholar] [CrossRef]
- Ross, S.M. Introduction to Probability Models; Academic Press: Cambridge, MA, USA, 2014. [Google Scholar]





| Notation | Description |
|---|---|
| the number of tips | |
| the number of newly issued sites | |
| the number of approved tips by in a approval round | |
| the time interval for issuing two sites | |
| h | average time for each approval |
| d | driving decision indicator |
| the selection probability from site x to tip y |
| Parameters | Values |
|---|---|
| Vehicle number | 18 |
| Hash algorithm | SHA-256 |
| Weight of each site w | 1 |
| q | 2 |
| Uniform distribution | Uni in (30, 40) |
| Poisson distribution | Poi with = 100 |
| Normal distribution | Nor with = 70, = 0 |
| MCMC | [27] | [28] | [29] | [30] | RTH-TSA in [12] | DDB-TSA in This Paper | |
|---|---|---|---|---|---|---|---|
| Correlation between shared information | × | × | × | × | √ | √ | √ |
| Lazy worker resistance | × | √ | √ | √ | √ | √ | √ |
| Without block packing and mining process | √ | √ | √ | × | √ | √ | √ |
| Parasitic chain attack defense | × | × | × | × | × | × | √ |
| PoW | Adaptive PoW | VDF | RBRCS | |
|---|---|---|---|---|
| Energy conservation | × | × | √ | √ |
| Friendly to LCP vehicles | × | × | √ | √ |
| Friendly to benign vehicles | × | × | × | √ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Du, G.; Cao, Y.; Li, J.; Zhuang, Y. Secure Information Sharing Approach for Internet of Vehicles Based on DAG-Enabled Blockchain. Electronics 2023, 12, 1780. https://doi.org/10.3390/electronics12081780
Du G, Cao Y, Li J, Zhuang Y. Secure Information Sharing Approach for Internet of Vehicles Based on DAG-Enabled Blockchain. Electronics. 2023; 12(8):1780. https://doi.org/10.3390/electronics12081780
Chicago/Turabian StyleDu, Gangxin, Yangjie Cao, Jie Li, and Yan Zhuang. 2023. "Secure Information Sharing Approach for Internet of Vehicles Based on DAG-Enabled Blockchain" Electronics 12, no. 8: 1780. https://doi.org/10.3390/electronics12081780





