Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols †
Abstract
:1. Introduction
1.1. Problem Statement, Goal and Contribution
1.2. Organization of This Paper
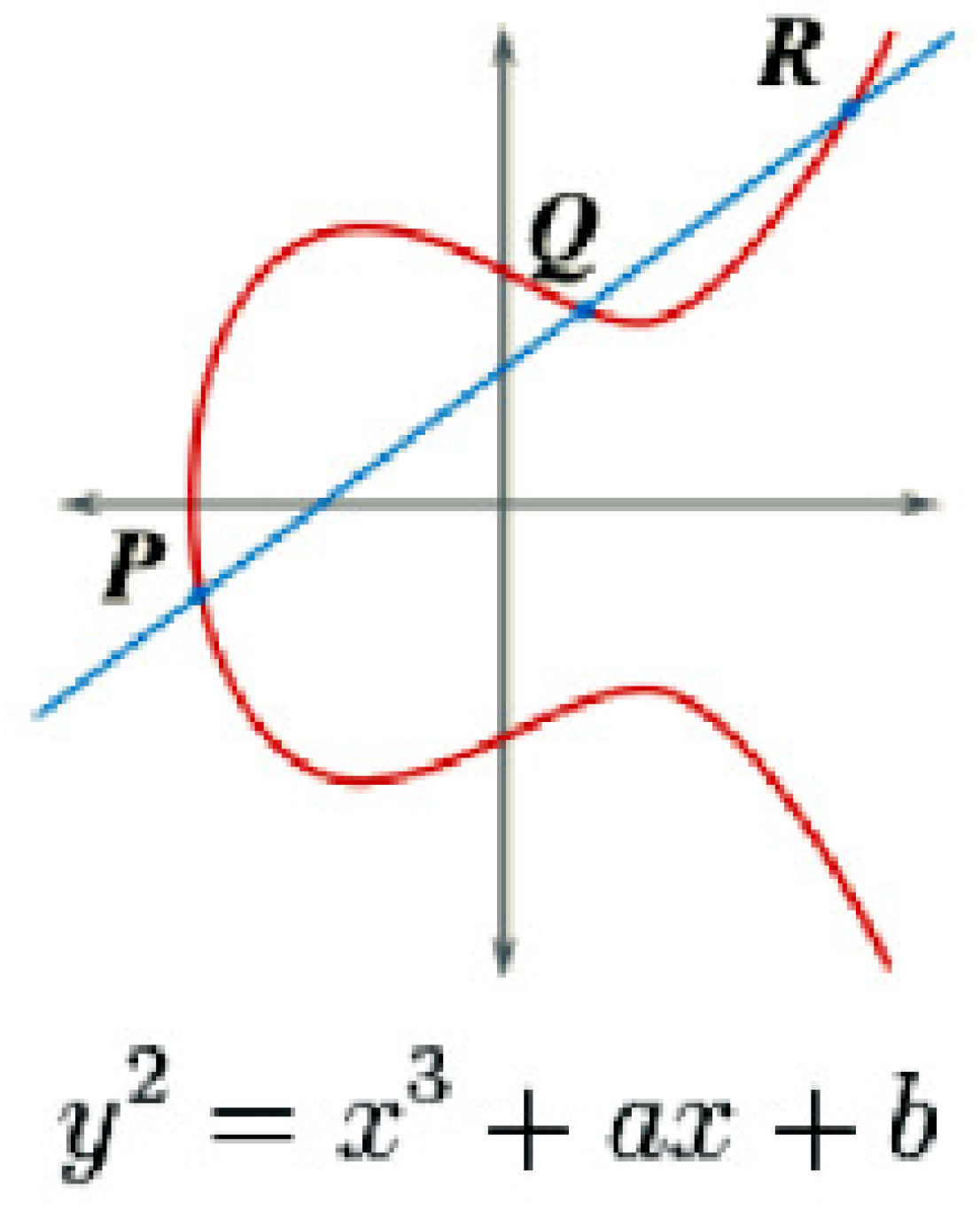
2. ECC Background
2.1. Computational Nature of ECC
3. Framework for Cryptanalysis
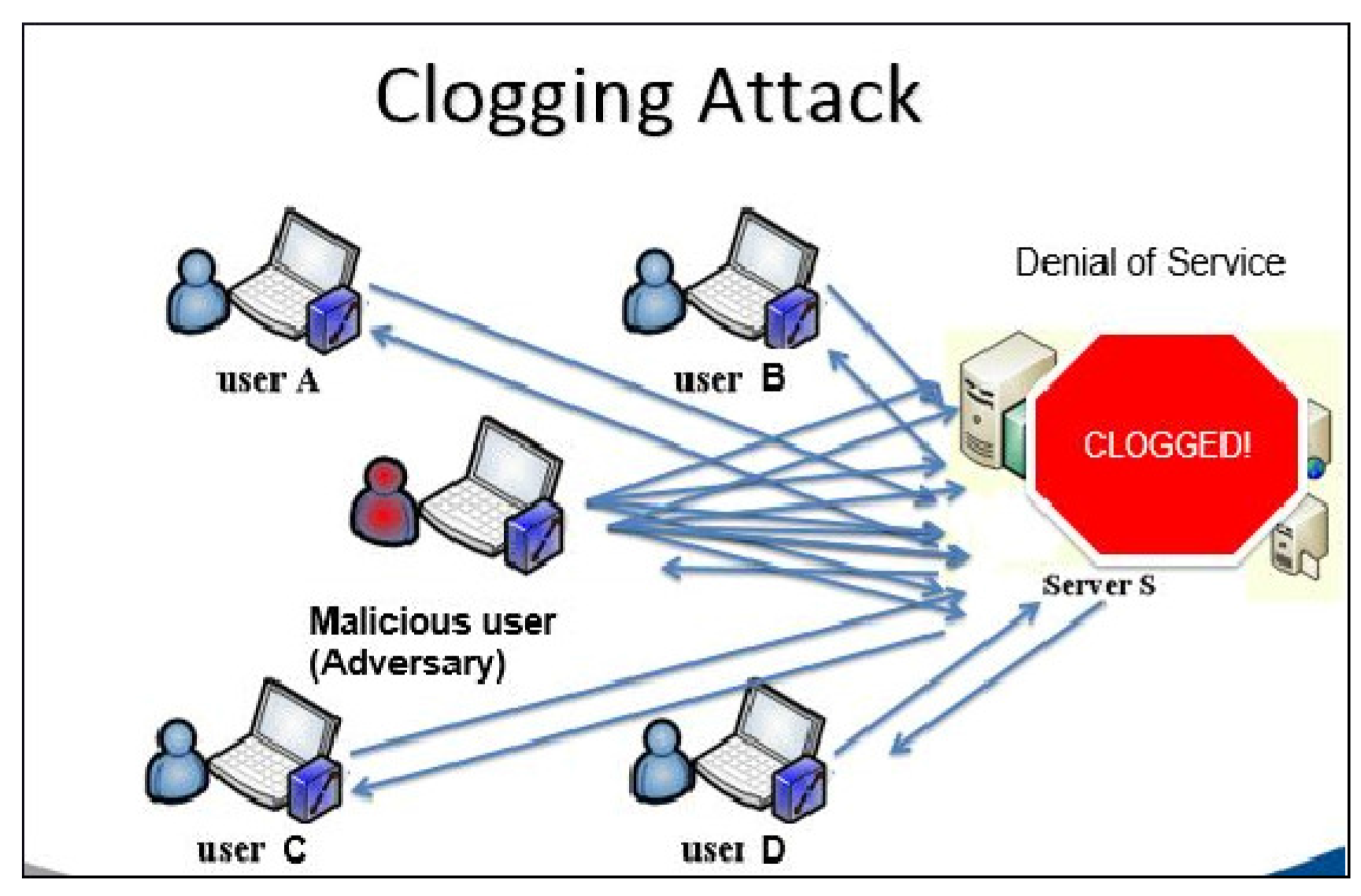
3.1. Clogging Attack
3.2. Application of Algorithm 1
- Bilinear pairing
- Scalar multiplication in group G
- Map-to-point conversion
| Algorithm 1: The general algorithm for the clogging attack [25]. |
| Intercept login message from client to server if Timestamp is present then Modify timestamp to match requirements else Keep message as is end if while The server is not completely clogged! do Replay the message to the server end while |
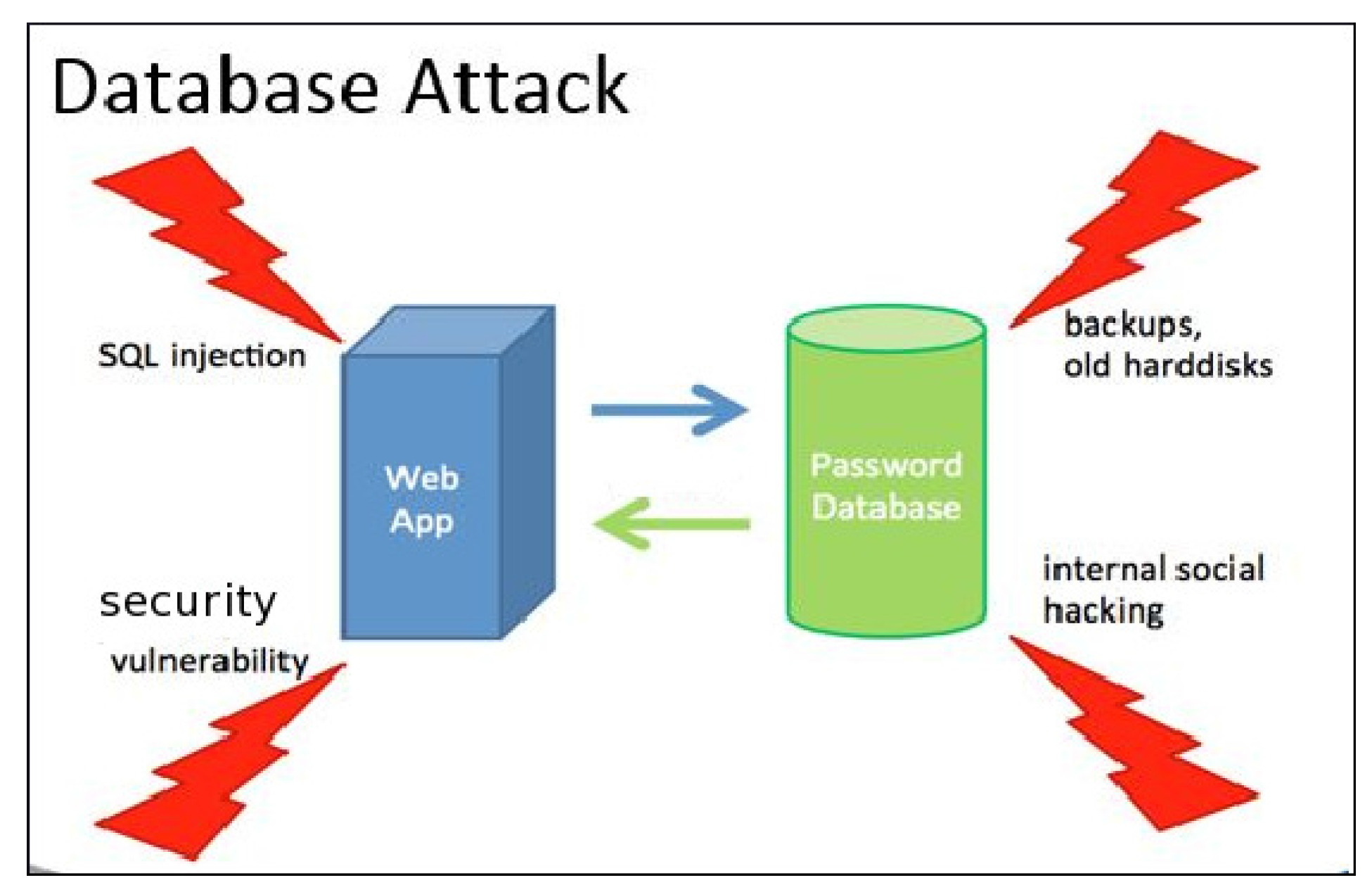
3.3. Database Attack
| Algorithm 2: The general algorithm for the database attack. |
| Intercept data access layer from application to back-end if Encryption is present then Break the encryption to gain access to the database else Access the database end if while The data is not corrupted and stolen do Inject malicious statements end while |
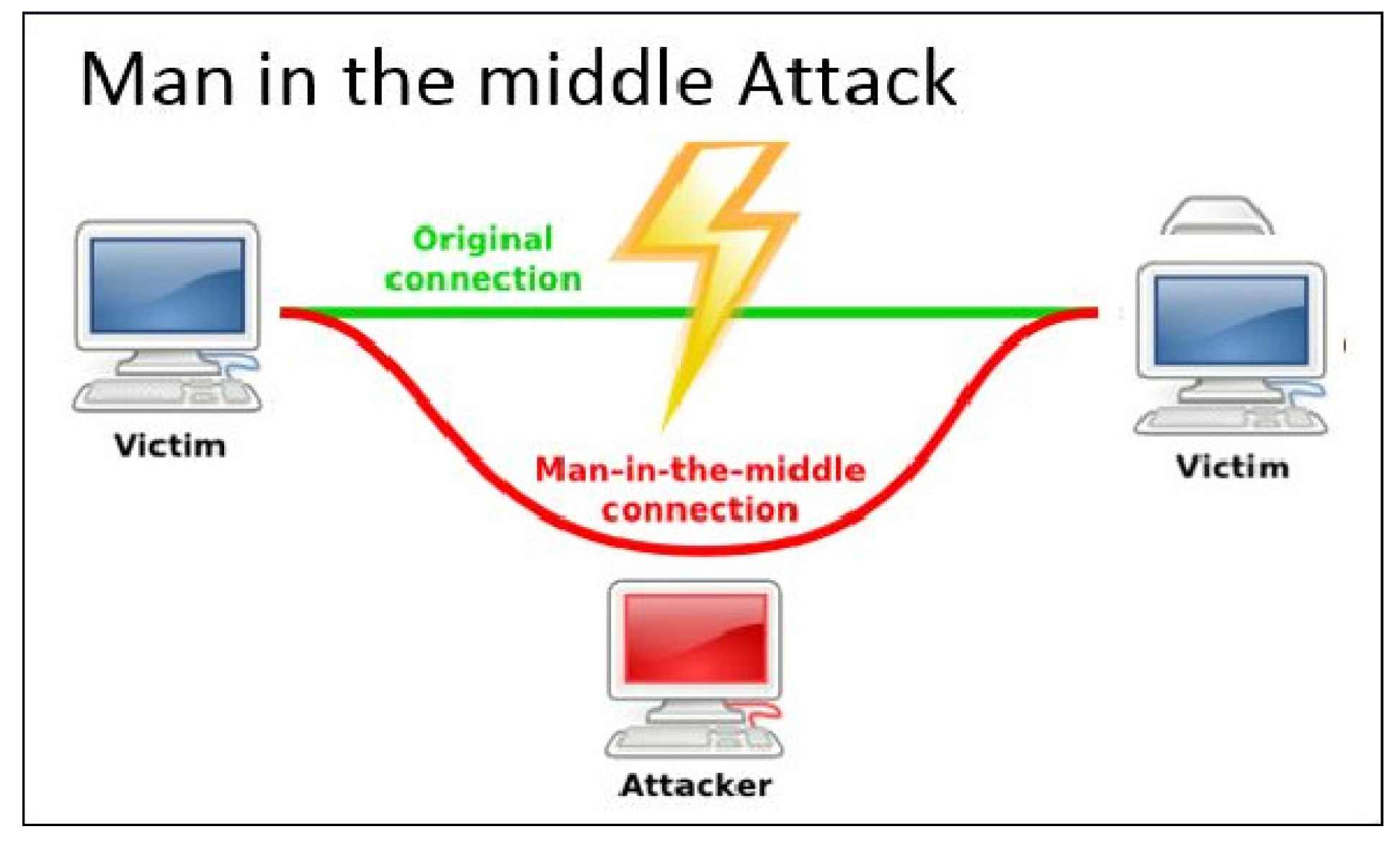
3.4. Man-In-The-Middle Attack
3.5. Application of Algorithm 3
| Algorithm 3: The general algorithm for the man-in-the-middle attack. |
| Intercept communication between two parties if TTP is present then Gains access and possibly alters the communication between two parties who believe they are directly communicating with each other else Acts as an intruder who relays and alters the communication between two parties end if while The communication is not ended do Relay end while |
4. Cryptanalysis of the Protocols
- denotes the finite field over q
- ⊗ denote (bitwise) exclusive OR
- A→B: M denotes the propagation of the message M from user A to user B
- ‖ denotes the concatenation operation
- In cryptography, a nonce is an arbitrary number that may only be used once
4.1. Choice of Protocols
4.2. Moosavi et al.’s Protocol for RFID Implant Systems
4.2.1. Review of the Protocol
| Algorithm 4: Moosavi et al.’s protocol for RFID implant systems. |
| Reader Authentication and Verification |
| Reader R |
|
| Tag T |
|
| Reader R |
|
| Tag T |
|
| Tag Identification |
| Reader R |
|
| Tag T |
|
| Tag Verification |
| Reader R |
|
4.2.2. Analysis of Moosavi et al.’s Protocol
4.2.3. Clogging Attack on Moosavi et al.’s Protocol
- intercepts a valid message of T→R: from Step I10.
- Since the message is unencrypted, can always change the , such that holds (though might not need to).
- just relays to R.
- Step V1. Choose a random integer .
- Step V2. Compute public key .
- Step V3. Verify if .
- Step V4. If true, compute .
- Step V5. Compute , , and respectively.
- Step V6. Compute curve point .
- Step V7. Verify if . If true, authenticate tag T.
4.2.4. Proposed Countermeasures from the Attack
- The tag T chooses a pseudo-random number and sends it along with the message .
- The reader R, upon receiving the message, acknowledges the message and sends its own cookie to T.
- The next message from T must contain , else T rejects the message and the tag verification request.
4.3. Xu et al.’s Smart Card-Based Protocol
4.3.1. Review of the Protocol
4.3.2. Clogging Attack on Xu et al.’s Protocol
- intercepts a valid login request () from step Step A7.
- simply replays this login message to S.
| Algorithm 5: Xu et al.’s authentication protocol. |
| Registration Phase |
| User |
|
| Server S |
|
| User |
|
| Authentication |
| User |
|
| Server S |
|
| User |
|
- uses a time stamp T in Step A7, and S verifies it in Step A8. The time stamp also must be encrypted in some form, so that cannot tamper with it.
- S checks whether multiple login requests frequently comes from the same user. This reduces the chances of a reply.
4.3.3. Weak Authentication and SQL Injection Attack
4.3.4. Unauthorized Access Attack
4.4. He et al.’s RFID-Based Authentication Protocol
4.4.1. Clogging Attack on He et al.’s Protocol
- intercepts a valid login request from Step A4.
- Since the message is unencrypted, changes to any random garbage value .
- then sends to the server S.
- The server S calculates , and .
- The server searches its database for . It is not found, and therefore, the server terminates the session.
| Algorithm 6: He et al.’s protocol. |
| Set Up Phase |
|
| Authentication Phase |
| Server S |
|
| Tag T |
|
| Server S |
|
| Tag T |
|
4.4.2. Weak Authentication Attack
4.4.3. Desynchronization Attack
4.5. Hui et al.’s Protocol
4.5.1. Review of the Protocol
| Algorithm 7: Hui et al.’s protocol. |
| Registration Phase |
| Client C |
|
| Server S |
|
| Password Authentication Phase |
| Client C |
|
| Server S |
|
| Client A |
|
4.5.2. Clogging Attack on Hui et al.’s Protocol
- intercepts a valid login request from Step C9
- Since the message is unencrypted, changes to
- then sends to the server S
4.5.3. Unauthorized Access Attack
4.5.4. Unauthorized Tampering Attack
- Unauthorized modification of data
- Unauthorized modification of configuration information
- Alteration or cancellation of client’s request to the server
- Alteration of the server’s response to the client
4.6. Ammayappan et al.’s Protocol
4.6.1. Review of the Protocol
4.6.2. Man-In-The-Middle Attack on the Protocol
| Algorithm 8: Ammayappan et al.’s protocol. |
| Node A |
|
| Node B |
|
| Node A |
|
- When node A wants to communicate to B, it sends the following message to the TTP: : , where is the current timestamp of A’s system.
- TTP upon receipt of the message validates the timestamp.
- TTP then sends the public key of B to A using the following message: : , where is the current timestamp of ’s system, and S is a secret value shared between A and the .
- Upon receipt of the message, A validates the timestamp, recomputes , using the hash and the secret value, and verifies it with the received .
- Change A’s request to the to .
- Therefore, have the send back to A.
- Try to change the message to .
| Algorithm 9: Ammayappan et al.’s protocol under MITM attack. |
| Node A |
|
| Adversary E |
|
| Node B |
|
| Adversary E |
|
| Node B |
|
| Node A |
|
5. Summary of the Results
6. Conclusions
Directions of Future Research
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Khatwani, C.; Roy, S. Security Analysis of ECC Based Authentication Protocols. In Proceedings of the 2015 International Conference on Computational Intelligence and Communication Networks (CICN), Jabalpur, India, 12–14 December 2015; pp. 1167–1172. [Google Scholar]
- Burr, J. Elliptical Curve Cryptography (ECC). Available online: http://searchsecurity.techtarget.com/definition/elliptical-curve-cryptography/ (accessed on 19 July 2016).
- Abidi, A.; Bouallegue, B.; Kahri, F. Implementation of elliptic curve digital signature algorithm (ECDSA). In Proceedings of the 2014 Global Summit on Computer & Information Technology (GSCIT), Sousse, Tunisia, 14–16 June 2014; pp. 1–6. [Google Scholar]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef] [PubMed]
- Chuang, Y.H.; Hsu, C.L.; Shu, W.; Hsu, K.C.; Liao, M.W. A Secure Non-interactive Deniable Authentication Protocol with Certificates Based on Elliptic Curve Cryptography. In New Trends in Intelligent Information and Database Systems; Springer: Berlin, Germany, 2015; pp. 183–190. [Google Scholar]
- Jin, C.; Xu, C.; Zhang, X.; Zhao, J. A secure RFID mutual authentication protocol for healthcare environments using elliptic curve cryptography. J. Med. Syst. 2015, 39, 1–8. [Google Scholar] [CrossRef] [PubMed]
- Yeh, H.L.; Chen, T.H.; Shih, W.K. Robust smart card secured authentication scheme on SIP using elliptic curve cryptography. Comput. Stand. Interfaces 2014, 36, 397–402. [Google Scholar] [CrossRef]
- Zhang, L.; Tang, S.; Chen, J.; Zhu, S. Two-Factor Remote Authentication Protocol with User Anonymity Based on Elliptic Curve Cryptography. Wirel. Pers. Commun. 2015, 81, 53–75. [Google Scholar] [CrossRef]
- Chande, M.K.; Lee, C.C. An improvement of a elliptic curve digital signature algorithm. Int. J. Internet Technol. Secur. Trans. 2016, 6, 219–230. [Google Scholar] [CrossRef]
- Hwang, M.S.; Lee, C.C.; Lee, J.Z.; Yang, C.C. A secure protocol for bluetooth piconets using elliptic curve cryptography. Telecommun. Syst. 2005, 29, 165–180. [Google Scholar] [CrossRef]
- Lee, C.C.; Li, C.T.; Weng, C.Y.; Jheng, J.J.; Zhang, X.Q.; Zhu, Y.R. Cryptanalysis and Improvement of an ECC-Based Password Authentication Scheme Using Smart Cards; CSS. Springer: Milpitas, CA, USA, 2013; pp. 338–348. [Google Scholar]
- Lo, J.W.; Lee, C.C.; Hwang, M.S.; Chu, Y.P. A secure and efficient ECC-based AKA protocol for wireless mobile communications. Int. J. Innov. Comput. Inf. Control 2010, 6, 5249–5258. [Google Scholar]
- Chande, M.K.; Li, C.T.; Lee, C.C. A CAE Scheme Using ECC Based Self Certified PKC. J. Comput. Sci. 2016, 12, 527–533. [Google Scholar] [CrossRef]
- Guide, R. Elliptical Curve Cryptography (ECC). Available online: http://www.sysax.com/ftblog/windows-ftp/elliptic-curve-cryptography-ecc/ (accessed on 19 July 2016).
- Farash, M.S.; Ahmadian-Attari, M. A Pairing-Free ID-Based Key Agreement Protocol with Different PKGs. IJ Netw. Secur. 2014, 16, 143–148. [Google Scholar]
- Bhargav-Spantzel, A.; Squicciarini, A.C.; Modi, S.; Young, M.; Bertino, E.; Elliott, S.J. Privacy preserving multi-factor authentication with biometrics. J. Comput. Secur. 2007, 15, 529–560. [Google Scholar] [CrossRef]
- Owen, W.N.; Shoemaker, E. Multi-Factor Authentication System. U.S. Patent 7,373,515, 13 May 2008. [Google Scholar]
- Sabzevar, A.P.; Stavrou, A. Universal multi-factor authentication using graphical passwords. In Proceedings of the 2008 IEEE International Conference on Signal Image Technology and Internet Based Systems, Bali, Indonesia, 30 November–3 December 2008; pp. 625–632. [Google Scholar]
- Chang, R.; Jiang, G.; Ivancic, F.; Sankaranarayanan, S.; Shmatikov, V. Inputs of coma: Static detection of denial-of-service vulnerabilities. In Proceedings of the 2009 22nd IEEE Computer Security Foundations Symposium, Port Jefferson, NY, USA, 8–10 July 2009; pp. 186–199. [Google Scholar]
- Sullivan, N. A (Relatively Easy to Understand) Primer on Elliptic Curve Cryptography. Available online: https://arstechnica.com/security/2013/10/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography/ (accessed on 24 October 2013).
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: Berlin, Germany, 2006. [Google Scholar]
- Graham, J.; Olson, R.; Howard, R. Cyber Security Essentials; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Koc, C.K. Elliptic Curve Cryptography. Available online: https://koclab.cs.ucsb.edu/ (accessed on 2 February 2017).
- Garrett, K.; Talluri, S.R.; Roy, S. On vulnerability analysis of several password authentication protocols. Innov. Syst. Softw. Eng. 2015, 11, 167–176. [Google Scholar] [CrossRef]
- Xu, L.; Wu, F. An improved and provable remote user authentication scheme based on elliptic curve cryptosystem with user anonymity. Secur. Commun. Netw. 2015, 8, 245–260. [Google Scholar] [CrossRef]
- Higgins, K.J. Hacker’s Choice: Top Six Database Attacks. Available online: http://www.darkreading.com/risk/hackers-choice-top-six-database-attacks/d/d-id/1129481?/ (accessed on 19 July 2016).
- Winkler, D.C. Securing Your Password Database with Bcrypt. Available online: https://en.wikipedia.org/wiki/EllipticcurveDiffie-Hellman/ (accessed on 19 July 2016).
- Wikipedia. Elliptic Curve Diffie-Hellman. Available online: http://blog.mgm-tp.com/2013/02/securing-your-password-database-using-bcrypt/ (accessed on 19 July 2016).
- LaMacchia, B.A.; Manferdelli, J.L. New Vistas in elliptic curve cryptography. Inf. Secur. Tech. Rep. 2006, 11, 186–192. [Google Scholar] [CrossRef]
- Bos, J.; Kaihara, M.; Kleinjung, T.; Lenstra, A.K.; Montgomery, P.L. On the Security of 1024-Bit RSA and 160-Bit Elliptic Curve Cryptography, EPFL-REPORT-164549. 2009.
- Sherwood, T.; Irvine, C.; Huffmire, T.; Levin, T.; Valamehr, J.; Kaya Koc, C.; Kastner, R. A Qualitative Security Analysis of a New Class of 3-D Integrated Crypto Co-processors. In Cryptography and Security: From Theory to Applications; Springer Verlag GmbH: Heidelberg, Germany, 2012. [Google Scholar]
- Moosavi, S.R.; Nigussie, E.; Virtanen, S.; Isoaho, J. An elliptic curve-based mutual authentication scheme for RFID implant systems. Procedia Comput. Sci. 2014, 32, 198–206. [Google Scholar] [CrossRef]
- Orman, H. The OAKLEY Key Determination Protocol; Technical Report; University of Arizona Tucson: Tucson, AZ, USA, 1998. [Google Scholar]
- Li, C.T. A new password authentication and user anonymity scheme based on elliptic curve cryptography and smart card. IET Inf. Secur. 2013, 7, 3–10. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N.; Lee, J.H. Lightweight ECC based RFID authentication integrated with an ID verifier transfer protocol. J. Med. Syst. 2014, 38, 1–6. [Google Scholar] [CrossRef] [PubMed]
- Liao, Y.P.; Hsiao, C.M. A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Netw. 2014, 18, 133–146. [Google Scholar] [CrossRef]
- Wang, S.-H.; Chang, S.-Q.; Wang, Z.W.; Sun, G.Z. A Password Authentication and Update Scheme Based on Elliptic Curve Cryptography. Int. J. Adv. Comput. Technol. 2012, 4, 84–90. [Google Scholar]
- Islam, S.H.; Biswas, G. Design of improved password authentication and update scheme based on elliptic curve cryptography. Math. Comput. Model. 2013, 57, 2703–2717. [Google Scholar] [CrossRef]
- Telelink Telecommunication Services Ltd. Unauthorized Access Attack. Available online: http://itsecurity.telelink.com/unauthorized-access-attack/ (accessed on 19 July 2016).
- Ammayappan, K.; Negi, A.; Sastry, V.; Das, A.K. An ECC-based two-party authenticated key agreement protocol for mobile ad hoc networks. J. Comput. 2011, 6, 2408–2416. [Google Scholar] [CrossRef]





| Protocol | Type | Factor Used | Confidentiality |
|---|---|---|---|
| Moosavi | Authentication | RFID | Usage of Random Numbers |
| Xu | Authentication | Smart Card | Usage of Random Numbers |
| He | Authentication | RFID | Usage of Random Numbers |
| Hui | Authentication | Password | Usage of Encryption |
| Ammayappan | Key Exchange | – | Trusted Third Party |
| Protocol | Clogging | MITM | Weak Authentication | SQL Injection | Unauth Access | DB Vulnerability | Desynch | Unauth Tampering |
|---|---|---|---|---|---|---|---|---|
| Moosavi et al. [33] | Yes | No | No | No | No | No | No | No |
| Xu et al. [26] | Yes | No | Yes | Yes | Yes | No | No | No |
| Xu et al. [36] | Yes | No | Yes | No | No | Yes | Yes | No |
| Hui et al. [38] | Yes | No | No | No | Yes | No | No | Yes |
| Ammayappan et al. [41] | No | Yes | No | No | No | No | No | No |
| Protocol | Mode of Attack | Countermeasure |
|---|---|---|
| Moosavi et al. [33] | Classical Clogging | Validity Checks |
| Xu et al. [26] | Classical Clogging, Weak Authentication, SQL Injection, Unauthorized Access | Efficient Algorithm, input validation, Timestamp |
| He et al. [36] | Classical Clogging, Weak Authentication, Database Protocol Vulnerability, Desynchronization | Input Validation, Updating of ID, Encryption, Timestamp |
| Hui et al. [38] | Classical Clogging, Unauthorized Access, Unauthorized Tampering | Usage of SSL, Timestamp, Network firewalls |
| Ammayappan et al. [41] | Man in the Middle | Securing Public Key Management |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Roy, S.; Khatwani, C. Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols. Cryptography 2017, 1, 9. https://doi.org/10.3390/cryptography1010009
Roy S, Khatwani C. Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols. Cryptography. 2017; 1(1):9. https://doi.org/10.3390/cryptography1010009
Chicago/Turabian StyleRoy, Swapnoneel, and Chanchal Khatwani. 2017. "Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols" Cryptography 1, no. 1: 9. https://doi.org/10.3390/cryptography1010009
APA StyleRoy, S., & Khatwani, C. (2017). Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols. Cryptography, 1(1), 9. https://doi.org/10.3390/cryptography1010009





