1. Introduction
Ensuring the confidentiality of sensitive information in the digital era is a critical concern. Various research fields, such as cryptography and cyber forensics, aim to protect information from unauthorized access. Information security revolves around preventing unauthorized disclosure, maintaining data integrity, and ensuring accessibility when needed. Image encryption plays a crucial role in securely transmitting information through images, with applications ranging from medical imaging to military operations. With the advancement of technology, the need for robust image encryption algorithms has grown. Multimedia data, including images, are susceptible to attacks and alterations. In military operations, even a slight information leak can pose a significant risk to national security. Therefore, algorithms need to provide strong security measures against various attacks and prevent information detection. One technology that offers advanced data security is blockchain. Industries are exploring blockchain for secure record-keeping, as it replaces centralized systems with decentralized ones involving only the relevant parties in a transaction. Blockchain technology is not limited to financial transactions; it is used for energy transfers between neighbours, copyright verifications in the media industry, and supply chain management. Many industries are embracing blockchain technology due to its advantages.
The working process of blockchain can be explained in simple terms. Transaction data, including details of the parties, conditions, and assets exchanged, are recorded. Consensus is reached among the participants, and the information is securely stored as a block, forming a chain. A final ledger copy is shared with all participants.
Emerging technologies have encouraged industries to explore new methods for enhancing security and overcoming limitations. Blockchain technology offers high security, making it difficult for unauthorized changes to be made to transaction records. It also improves efficiency, transparency, and allows for quick data auditing. Researchers have explored the application of blockchain in secure image sharing [
1] and its integration with the Internet of Things (IoT) [
2].
Image encryption is a vast field with contributions from researchers across various disciplines. In simple terms, image encryption involves converting an image into an encrypted form using a secret key. The encrypted image is then decrypted by the receiver using the same secret key, but in reverse order. The key used in encryption is of utmost importance. Typically, there are two types of keys: private and public. A private key is a unique key used for both encryption and decryption processes, while public keys consist of separate keys for encryption and decryption. The literature on image encryption encompasses a wide range of algorithms developed to address security requirements. These algorithms aim to protect the confidentiality and integrity of images during transmission and storage. Some methods include the techniques of watermarking [
3], steganography [
4] and scrambling of images [
5]. Over the past few decades, there has been a growing interest in utilizing chaotic systems for cryptography. Chaotic systems have gained popularity due to their unique characteristics such as sensitivity to initial conditions, unpredictability, and randomness. Their implementation in cryptography offers advantages such as cost-effectiveness, computational efficiency, and complexity.
The study of chaos is not a recent development; it was first introduced by Poincare in the 1880s while investigating the three-body problem. However, at that time, there was no formal theory to support the observation of non-periodic oscillations, which hindered the progress of the field. It was in the later part of the twentieth century that Edward Lorenz discovered the sensitivity of chaotic systems to initial conditions, where even a small change can lead to a significantly different outcome. The advent of digital computers played a crucial role in advancing the field. The computational complexity of manually calculating repeated iterations for chaos theory was simplified by electronic computers. As a result, the field of chaos theory experienced significant growth, leading to the development of numerous chaotic systems with strange attractors and hidden attractors. The inherent randomness of chaotic systems makes them well-suited for image encryption processes. When it comes to encrypting images using chaotic maps, the selection of the system used to construct the algorithm becomes a critical task. During the initial phase of the study, logistic map [
6] and tent map [
7] are used for encryption. The limitations in implementing the system are that the key space is so small that a breach of security is possible. Later, to increase the level of security, higher-dimensional systems, such as the Henon map [
8], Tinkerbell map [
9], 5D hyperchaotic map [
10], are introduced for better key space. An image encryption scheme with a combined 1D map was discussed in [
11] and a coupled sine–logistic map was illustrated in [
12].
The generalisation of integer-order chaotic systems with arbitrary real or complex orders provides enhanced complexity and non-linearity that highly suit the process of image encryption. Fractional-order derivatives, which are non-local, have the ability to bring the factor of memory into effect. The fractional Lorenz system was considered for the encryption scheme by Radwan et al. in [
13]. Application of the fractional-order neural network model was presented in [
13] and the authors analysed the characteristics of the complex chaotic system with fractional-order in the image encryption process in [
14]. A chaotic system with improper fractional-order is considered for image encryption in [
15] and the investigation with improper fractional laser systems was carried out by Yang et al. in [
16]. Encryption based on the coexisting attractors of the memristive fractional system was discussed in [
17] and the fractional system together with the Fisher–Yates algorithm was employed in [
18]. Consequently, during the last decade, discrete time fractional-order systems have gained importance due to their diverse applications. The development of the theory for the field of discrete fractional calculus was due to the pioneering works of Atici and Eloe in [
19], Igor Podlubny in [
20], and Anastassiou in [
21]. Application of discrete fractional calculus to tumour immune systems was discussed in [
22], and heat transfer fins and pantograph equations were investigated in [
23,
24]. Dynamic analysis of the fractional difference chemical reaction model was performed in [
25]. The implementation of fractional order in the discrete maps enhances the chaotic nature of the maps. Some recent research contributions based on fractional difference chaotic systems include image encryption with compression based on Bayesian sensing and the 2D fractional discrete time chaotic map in [
26]. The application of discrete fractional neural networks to encryption was presented in [
27]. The elliptic curve cryptosystem and the 2D fractional-order discrete map are employed for the process of encryption in [
28]. Wu et al. presented the technique of encryption of images with chaotic fractional discrete time series in [
29] and a novel technique was introduced in [
30]. Tempered-type fractional derivatives in discrete time were proposed, and the encryption was discussed in [
31]. Motivated by the investigations performed in the recent literature towards the field of image encryption [
32,
33,
34,
35,
36,
37,
38], this article aims to contribute the following.
Construction of a novel fractional difference sine chaotic map with long-term chaotic response illustrated with bifurcation diagrams, Lyapunov exponents, and approximate entropy.
The application of the proposed discrete fractional sine chaotic map to image encryption of greyscale images is presented by generating a chaotic matrix.
The watermarking of the secret images at different levels is performed using transform methods.
For secure transmission of information stored in images, a genesis block is generated to diffuse the pixels of the images that can only be recovered by the recipient with the same genesis block (blockchain concept).
The manuscriptis planned with mathematical prerequisites in
Section 2, and novel discrete fractional sine chaotic map construction and comparison are illustrated in
Section 3. The scheme of encryption is presented in
Section 4, and the analysis of results with supporting figures is provided in
Section 5, with a conclusion in
Section 6.
4. Image Encryption and Decryption
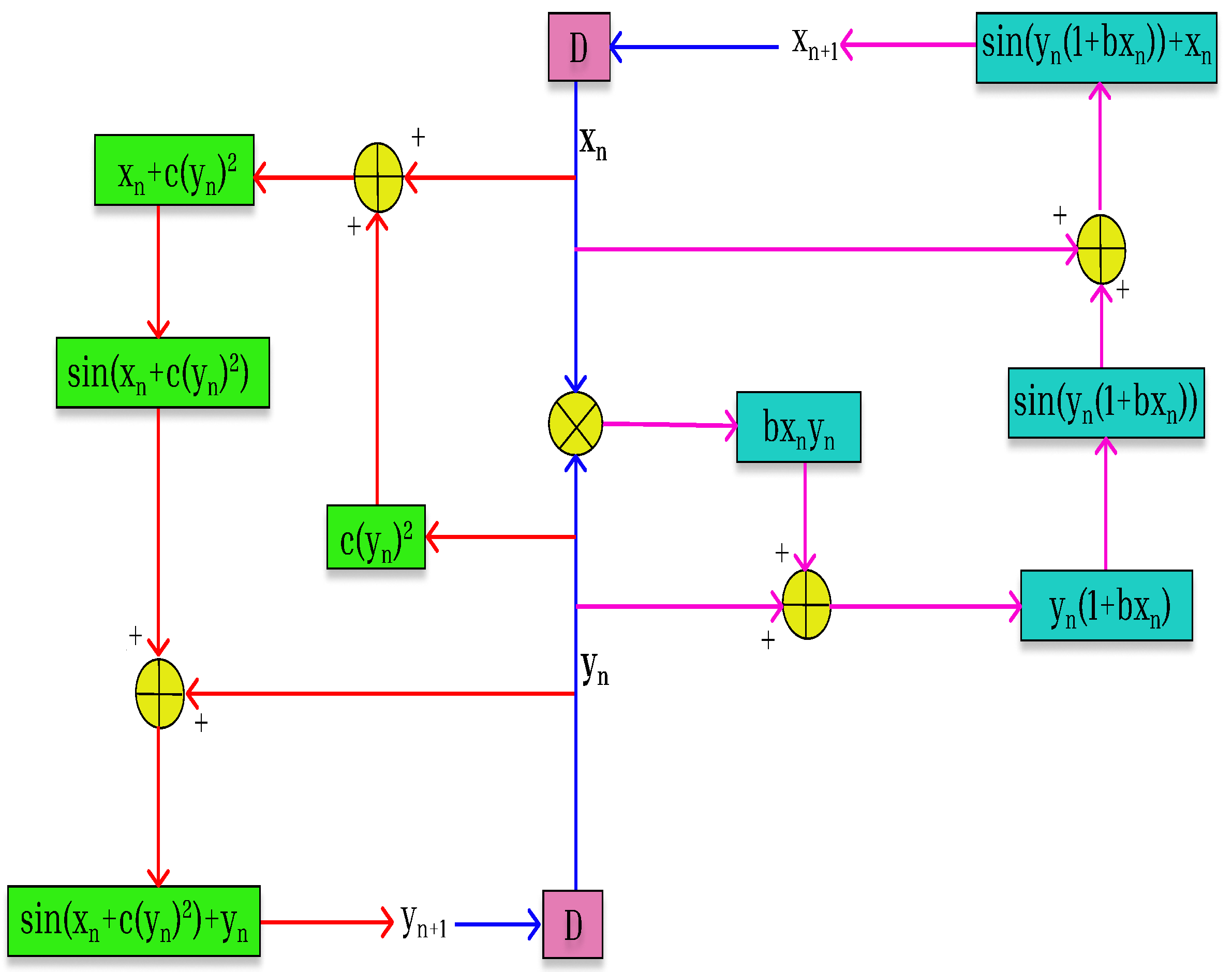
Based on the above results on the chaotic responses and non-linearity exhibited by the discrete fractional map, we employ the DFSCM (
8) to generate a chaotic sequence to perform image encryption. This section presents the application of the proposed encryption of images with a discrete time fractional sine map. To ensure the high level of security of the information transmission through images, the concept behind blockchain technology is adapted to ensure the decryption of the image by the authentic receiver. A schematic representation of the image encryption algorithm is presented in
Figure 6.
4.1. Scheme of Encryption
The entire process of image encryption is discussed in this section. Our encryption process can be split into three parts
Embedding secret images: Watermarking using discrete wavelet transforms.
Partial encryption and diffusion: Generating a chaotic matrix from the discrete fractional sine chaotic map for diffusion of pixels.
Encryption: Image is integrated into 256 bits and is bit-XORed with genesis block using SHA-256.
A step-by-step procedure of the encryption process is as follows.
Embedding secret images:
The objective image
of size
is selected and subjected to level 2 or 3 decomposition employing discrete wavelet transformation after converting the image to greyscale [
46]. In case of an image of size
, level 1 contains four sub-bands of size
containing approximation (LL), horizontal (HL), vertical (LH) and diagonal (HH) as shown in
Figure 7.
Figure 7.
Different levels of decomposition by discrete wavelet transforms.
Figure 7.
Different levels of decomposition by discrete wavelet transforms.
- 2.
Consider the LL sub-band for level 2 decomposition and similarly, the procedure can be followed for level 3 decomposition. The size of the sub-bands is halved at each decomposition.
- 3.
In our algorithm, we are interested in embedding watermarked images in different levels.
Case (i): Level 2 decomposition with secret images embedded in the LH sub-band of level 1 and the HL sub-band in level 2.
Case (ii): Level 3 decomposition with secret images embedded in the LH sub-band of level 2 and the HL sub-band in level 3.
Case (ii): Level 3 decomposition with secret images embedded in the LH sub-band of level 3 and the HL sub-band in level 3.
- 4.
Size of the level in which the secret images to be watermarked are selected and the secret images are processed to this size. Singular vector decomposition (SVD) and inverse discrete wavelet transform are employed to obtain watermarked image.
Partial encryption and diffusion:
- 1.
After the watermarked image is obtained, it is subjected to encryption of the selected portion of the image using the sum of the edge intensity values and respective inverse of the value for recovering the image.
- 2.
After partial encryption, we employ Fourier transform for inter-block shifting in the image. Let us denote the shifted image by
- 3.
The discrete fractional chaotic map (
8) with parameters
and fractional order
with initial states
is considered to obtain the chaotic matrix. Chaotic sequences are generated from the map (
8) and the chaotic matrix is obtained by
for m = 1:K
for n = 1:L
end
end
- 4.
The chaotic matrix thus obtained from the previous step is employed for the process of diffusion with the shifted image obtained in Step 2. Let the diffused image be denoted by
Encryption:
The encryption process is based on the following concept: In a blockchain, the genesis block serves as the initial block upon which subsequent blocks are built. Each block in the blockchain depends on the hash values of the previous block, with the genesis block having a hash value of 0. A notable feature of the blockchain is that every block contains the complete transaction history from the previous block. Therefore, any slight modification in the transactions would lead to corruption of the entire data.
Applying this concept, the partially encrypted and block-shuffled image obtained in the previous step is divided into 256 blocks. A unique base block, known as the genesis block, is introduced. This genesis block is XORed with the image disintegrated into bits, resulting in blocks shuffled across different regions of the image. The procedure can be summarized as follows:
The image is divided into 256 small blocks and a genesis block required for construction of blockchain is considered.
The image blocks are then converted to strings by
c = 1
while
while
(p,q:q + 31)= B(c,:) (p,q:q + 31);
B(c + 1, :) = uint8(sha256hasher.ComputeHash ;
c = c + 1;
end
end
The encrypted image to be sent to the recipient is obtained.
4.2. Decryption Scheme
The procedure of obtaining the plain image from the encrypted image is a simple reverse process, starting with the extraction of the image with the same genesis block and then diffusion with the chaotic matrix . An inverse Fourier transform is applied to reshuffle the blocks, and the inverse value of the edge intensity can be used to retain our watermarked image. Once the watermarked image is obtained by applying a discrete wavelet transform to the sub-bands with secret images, the secret image can be obtained.
4.3. Significance of the Proposed Algorithm
Our proposed algorithm presents a two-layer defence mechanism against non-recipient decryption. The first layer of defence is the genesis block, a unique set of SHA-256 code accessible only to the receiver and sender. The diffusion of the encrypted image with a different genesis block than the original one results in a corrupted image, which, on further processing, will not yield any information about the image. The second layer of defence is the chaotic key of the DFSCM which is sensitive to high precision of , thus making it difficult to break into the algorithm. Thus, our algorithm developed with DFSCM and the concept of blockchain for encryption of images provides a high level of security for the transmission of information. The experimental evaluation of the results also supports our claim in comparison with some recent literature based on chaotic systems.
6. Conclusions
A novel discrete fractional sine chaotic map was developed and compared with existing chaotic maps, such as the Tent map, Tinkerbell map, and other fractional chaotic maps proposed in the literature. The comparison of dynamic characteristics confirms that the proposed map exhibits high non-linearity and complex behaviour, making it suitable for image encryption applications. The bifurcation diagrams demonstrate chaotic behaviour over a wide range of parameters, while the positive Lyapunov exponents further support the chaotic nature of the proposed algorithm. To assess the randomness of the chaotic time series generated by the map, approximate entropy results were calculated and tabulated for different tolerance values. These results highlight the randomness and unpredictability of the chaotic sequences. An image encryption algorithm based on the principles of blockchain logic was proposed to enhance the security of information transmission. This scheme ensures a higher level of security for authorized communication between senders and receivers. The incorporation of the transform methods for embedding secret images as watermarks at various levels enhances the transmission of secret messages.
For objective images of size
, the proposed encryption scheme significantly increases the randomness of pixel distribution, as evidenced by the entropy results presented in
Table 6 and
Table 7. The impact of the chaotic sequences generated by the fractional chaotic map is evident from the high entropy values and the
NPCR exceeding
for a single bit change in the input image. This demonstrates the effectiveness of the proposed encryption scheme for secure information communication through images. Additionally, the incorporation of watermarking techniques extends its applicability to areas such as copyright protection, e-voting, and securing medical and military data. In future research, the concept of genesis block-based encryption can be extended to RGB images, and the inclusion of multi-block image storage can be explored to further enhance the encryption scheme’s capabilities.